
OCTOBER
2014
Robotics on the Battleeld Part II
The Coming Swarm
By Paul Scharre

Cover Image
A ock of auklet birds exhibit swarm behavior.
(U.S. FISH AND WILDLIFE SERVICE)
Also in this series:
“20YY: Preparing for War in the Robotic Age” by Robert O. Work and Shawn Brimley
“Robotics on the Battleeld Part I: Range, Persistence and Daring” by Paul Scharre
Acknowledgements
I would like to thank the numerous colleagues at CNAS and elsewhere who assisted in the development of this report. Liz
Fontaine led the production and design of this report. Adam Elkus provided invaluable assistance in understanding animal
and robotic swarms. CNAS research interns James Marshall and Matthew Seeley assisted in background research. In addi-
tion, a number of outside experts provided valuable insights on a range of issues. I would like to thank Russell Rumbaugh
of the Stimson Center, Michael Sulmeyer of the Oce of the Secretary of Defense, Dean Wilkening of Lawrence Livermore
National Laboratory, David Scheidt of Johns Hopkins University Applied Physics Laboratory, Sachin Jain of Aurora Flight
Sciences, Timothy Chung of the Naval Postgraduate School and Andrew Herr of Helicase for their assistance, corrections
and insights. I would also like to thank the numerous colleagues at CNAS and other institutions who provided feedback on
draft versions of this report.
Any errors of analysis, fact or omission are mine alone. CNAS does not take institutional positions.
Robotics on the Battleeld Part II
The Coming Swarm
By Paul Scharre
OCTOBER 2014
VII. Enemy Swarms and Countermeasures 42
VIII. Conclusion: Building the Swarm 44
IX. Recommendations 50
TABLE OF CONTENTS
I. Executive Summary 5
II. Introduction: 10
The Reconnaissance-Strike Swarm
III. Mass 13
IV. Coordination and Intelligence 24
V. Speed 33
VI. Commanding the Swarm 35

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
2
|
About the Author
Paul Scharre is a fellow and director of the 20YY Warfare Initiative at the Center for a New
American Security.

ROBOTICS ON THE BATTLEFIELD PART II:
THE COMING SWARM
By Paul Scharre

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014

|
5
By Paul Scharre
I. EXECUTIVE SUMMARY
e unfolding robotics revolution is transform-
ing a range of industries, from manufacturing to
transportation, warehouse management, household
appliances, toys, elder care and more. Similarly,
it will lead to signicant and perhaps surprising
changes in warfare. Uninhabited vehicles, like the
Predator aircra or the Packbot ground robot,
have already proven invaluable in today’s conicts.
As uninhabited vehicles incorporate increasing
automation and become true robotic systems,
they will have tremendous value in future military
operations. Individually, they will allow military
forces to extend their reach into the battlespace,
operating with greater range and persistence than
would be possible with human-inhabited systems.
With no human on board they can be sent on dan-
gerous or even suicidal missions, allowing more
daring concepts of operation. Individually, robotic
systems can provide warghters signicant advan-
tages in a range of missions. Collectively, swarms
of robotic systems have the potential for even more
dramatic, disruptive change to military operations.
Swarms of robotic systems can bring greater mass,
coordination, intelligence and speed to the battle-
eld, enhancing the ability of warghters to gain a
decisive advantage over their adversaries.
Secretary of Defense Chuck Hagel has called for
a renewed eort to sustain American military
technological dominance, and uninhabited and
autonomous systems are an important component
of such a strategy.
1
Today the U.S. military faces
a pernicious cycle of ever rising platform costs
and shrinking quantities. As a result, the number
of combat ships and aircra in the U.S. inven-
tory has steadily declined, even during periods of
signicant growth in defense spending. Today’s
acute scal pressures only exacerbate these trends,
forcing a crisis not only in military moderniza-
tion and readiness, but also in the ability to eld
sucient quantities to be relevant in future ghts.
As precision-guided munitions proliferate to other
adversaries – both state and non-state actors – the

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
6
|
shrinking numbers of U.S. combat assets becomes
a major strategic liability. Adversaries can con-
centrate their weapons, which are becoming
increasingly accurate and capable at ever-longer
ranges, on the relatively small number of U.S.
ships and bases, overwhelming their defenses. e
current trend of attempting to compensate for
ever-shrinking numbers of capital assets through
increasingly exquisite systems is not sustain-
able. Clinging to greater quantities by eschewing
modernization, however, is not a recipe for success
either. A new paradigm is needed, one that sustains
the qualitative superiority of U.S. forces in aggre-
gate, but that disperses combat power among a
greater number of platforms, increasing resiliency
and diversity and imposing costs on adversaries.
Uninhabited systems can help bring mass back to
the ght by augmenting human-inhabited combat
systems with large numbers of lower cost unin-
habited systems to expand the number of sensors
and shooters in the ght. Because they can take
more risk without a human onboard, uninhabited
systems can balance survivability against cost,
aording the ability to procure larger numbers
of systems. Greater numbers of systems compli-
cates an adversary’s targeting problem and allows
graceful degradation of combat power as assets are
attrited. e disaggregation of combat power into a
larger number of less exquisite systems also allows
the ability to eld a family-of-systems approach,
increasing diversity and reducing technology risk,
driving down cost. Uninhabited systems need not
be exquisite multi-mission systems, but rather can
be purpose-built for specic missions at lower cost.
For example, uninhabited missile barges, under-
sea payload modules, airborne “missile trucks”
and robotic appliqué kits for ground vehicles can
supplement the striking power of existing manned
platforms at relatively low cost. e result can be
greater combat power on the battleeld, at the
same cost. By embracing uninhabited and autono-
mous systems, the United States can disperse its
combat capabilities, increasing resiliency, and
expand its oensive striking capacity, all within
realistic budget constraints.
2
e power of swarming lies in more than just
greater numbers, however. Today’s modern mili-
tary forces ght as a network, with interconnected
human-inhabited platforms passing surveillance
and targeting data across great distances. Future
military forces will ght as a swarm, with greater
coordination, intelligence and speed. Autonomous
and uninhabited systems will be networked and
cooperative with the ability to autonomously coor-
dinate their actions in response to events on the
ground. Swarming, coordinated action can enable
synchronized attack or defense, more ecient allo-
cation of assets over an area, self-healing networks
that respond to enemy actions or widely distrib-
uted assets that cooperate for sensing, deception
and attack. Harnessing the power of swarming
will require new command-and-control models
for human supervision of large swarms. is will
mean moving beyond existing paradigms where
humans directly control a vehicle’s movements to
one where human controllers supervise the mission
at the command level and uninhabited systems
maneuver and perform various tasks on their own.
Increased automation also has the potential to
speed up the pace of warfare by helping to shorten
decision cycles and, in some cases, remove humans
from them entirely. Increased automation can
allow humans to process large amounts of data
quickly, allowing warghters to react to chang-
ing events on the ground faster than the enemy.
In some cases, the fastest reactions might come
from removing humans from some tasks entirely,
as is already done for some defensive actions like
dispensing ares or other countermeasures. While
increased automation may have tactical benets
in allowing faster reaction times to enemy actions,
it could also have strategic consequences if the
speed of action on the battleeld eclipses the speed
of decision-making for policymakers. Increased
|
7
autonomy in the use of force raises the dangerous
specter of “ash wars” initiated by autonomous
systems interacting on the battleeld in ways that
may be unpredictable. While militaries will need
to embrace automation for some purposes, humans
must also be kept in the loop on the most critical
decisions, particularly those that involve the use of
force or movements and actions that could poten-
tially be escalatory in a crisis.
Increasingly sophisticated autonomous systems
will still fall short of human intelligence in many
respects, and uninhabited systems will not be
useful or appropriate for all missions. A human-
machine teaming approach will be needed to nd
the optimal mix of human-inhabited and uninhab-
ited platforms and human and machine cognition
for various tasks. As one example, the Army has
adopted an approach of teaming human-inhabited
Apache helicopters with uninhabited Gray Eagle
aircra to perform armed aerial reconnaissance.
Developing the doctrine, training, concepts of
operation and organization to enable eective
human-machine teaming will be critical to lever-
aging the unique advantages of uninhabited and
autonomous systems in a wide range of mission
areas.
e introduction of greater numbers of uninhab-
ited and autonomous systems on the battleeld will
not lead to bloodless wars of robots ghting robots,
but could make more warfare more deadly and
dangerous for human combatants. Humans will
still ght wars, but new technology will give com-
batants, as it always has, greater stando from the
enemy, survivability or lethality. Exploiting those
advantages will depend principally on the ability to
uncover the most innovative applications of robotic
swarms, which will require not only increased
resources but also an aggressive campaign of
experimentation and technology development.
Many of the underlying technologies behind
increased autonomy are driven by commercial
sector innovation, and as a result will be available
to a wide range of state and non-state actors. In
a world where some of the most-game changing
technologies will be available to everyone, uncov-
ering the best uses of that technology – and doing
so urgently – will be vital to sustaining American
military dominance.
Humans will still ght wars,
but new technology will give
combatants, as it always has,
greater stando from the enemy,
survivability or lethality.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
8
|
KEY RECOMMENDATIONS
THE OFFICE OF THE SECRETARY
OF DEFENSE SHOULD:
• Undertake a study on swarming plat-
forms to examine the potential for
low-cost uninhabited systems to impose
costs on adversaries.
• Fund a multi-year series of experiments
in cooperative multi-vehicle control and
swarming.
• Establish a Defense Robotics Systems
Oce, directly reporting to the Deputy
Secretary of Defense, to coordinate
ongoing eorts on uninhabited systems
across the Department.
THE JOINT STAFF SHOULD:
• Ensure that lessons learned from ex-
periments regarding uninhabited and
autonomous systems are centrally col-
lected and widely shared throughout the
Department.
THE NAVY SHOULD:
• Build an experimental prototype of an
uninhabited missile barge that can dem-
onstrate the ability to remotely control
and launch missiles from a large unin-
habited vessel.
• Build a proof-of-concept demonstra-
tion of an undersea payload module to
exploit U.S. sanctuary undersea.
• Move aggressively to eld autonomous
swarming defensive boats to protect U.S.
ships from enemy fast attack craft. This
should include further experimentation
to rene concepts of operation, a rapid
elding initiative to equip combatants in
high-risk areas like the Straits of Hormuz
and a program of record for outtting all
Navy surface combatants with optional-
ly-manned small boats that can operate
as a defensive swarm.

|
9
THE AIR FORCE SHOULD:
• Investigate the potential for low-cost
swarming uninhabited air vehicles, in-
cluding expendable or non-recoverable
systems such as missiles or decoys, to
conduct a variety of missions including
suppression/destruction of enemy air
defenses, reconnaissance, battle damage
assessment and electronic warfare.
• Conduct an analysis of alternatives of
lower-cost uninhabited aircraft to sup-
plement existing manned aircraft with
additional sensors and missiles, such as
an uninhabited “missile truck.”
• Conduct a series of experiments in
human control over large numbers of
swarming air vehicles.
THE ARMY AND MARINE CORPS
SHOULD:
• Develop a concept of operations for
using appliqué kits for ground convoy
operations and an associated program of
record.
• Conduct a series of modern day “Louisi-
ana Maneuver” experiments on “robotic
wingman” ground robots for long-range
scouting and maneuver operations,
in order to inform further technology
development and requirements for an
eventual program of record.
• Conduct a series of experiments on
swarming uninhabited air vehicles for
persistent surveillance, close air support,
aerial resupply and communications re-
lay to support ground maneuver forces.
THE MARINE CORPS SHOULD:
• Conduct experiments on amphibious
swarming robots for reconnaissance
and counter-mine operations to clear
beaches ahead of an amphibious assault.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
10
|
II. INTRODUCTION: THE
RECONNAISSANCESTRIKE SWARM
From Fighting as a Network to Fighting
as a Swarm
Advances in information technology achieved
in the twentieth century allow modern military
forces to ght as a network. Sensors can detect
enemy forces and pass targeting data through
communications links to shooters, who engage
enemy targets with precision-guided weapons.
e U.S. military was the rst to harness the
advantages of the information revolution to build
a networked force, but other nations are following
suit. Adversaries are building reconnaissance-
strike networks that can detect U.S. forces at long
range and strike them with precision-guided
weapons. ese developments, oen captured
under the label of anti-access, area denial (A2/
AD) challenges, threaten many traditional U.S.
modes of power projection, such as ships, carriers
and air bases that can be targeted with long-
range weapons.
3
As detailed in CNAS’s recent
report, “Robotics on the Battleeld Part I: Range,
Persistence and Daring,” uninhabited systems
can help U.S. forces to counter this threat because
of their increased range, persistence and ability
to take greater risks, enabling new concepts of
operation.
4
But these developments are merely the precursor to
a larger shi in warfare.
Emerging robotic technologies will allow tomor-
row’s forces to ght as a swarm, with greater mass,
coordination, intelligence and speed than today’s
networked forces. Low-cost uninhabited systems
can be built in large numbers, “ooding the zone”
and overwhelming enemy defenses by their sheer
numbers. Networked, cooperative autonomous
systems will be capable of true swarming – coop-
erative behavior among distributed elements that
gives rise to a coherent, intelligent whole. And
automation will enable greater speed in warfare,
with humans struggling to keep pace with the
faster reaction times of machines. e result will
be a paradigm shi in warfare where mass once
again becomes a decisive factor on the battleeld,
where having the most intelligent algorithms may
be more important than having the best hardware,
and where the quickening pace of battle threatens
to take control increasingly out of the hands of
humans.
Keeping Pace with the Unfolding Robotics
Revolution
ese developments will pose profound opera-
tional and policy challenges. Adapting to these
challenges will require the development of new
capabilities, experimentation with new concepts
and development of new doctrine and organi-
zational structures. Despite the U.S. military’s
dominance today, other nations may be better
prepared to capitalize on these coming changes.
e U.S. military is heavily invested – both
nancially and bureaucratically – in today’s
technologies and methods of ghting. While
uninhabited systems have been embraced for
some missions like reconnaissance and bomb
disposal, across the force they largely remain
relegated to niche roles. Only one out of every
20 Department of Defense (DOD) research,
development and procurement dollars goes to
uninhabited systems.
5
Furthermore, elements of
the U.S. military continue to resist technologies
Emerging robotic technologies
will allow tomorrow’s forces
to ght as a swarm, with
greater mass, coordination,
intelligence and speed than
today’s networked forces.

|
11
that disrupt familiar operational paradigms, such
as automation that would change the paradigm of
control for human pilots over aircra.
6
For many
missions, uninhabited and autonomous systems
are seen as an unproven technology and even
potentially threatening when human jobs may be
eliminated. In the face of this discomfort, a “go
slow” approach might be tempting.
e problem is that the enemy gets a vote.
By 2018, global spending on military robotics
is estimated to reach $7.5 billion per year. At
the same time, global spending on commercial
and industrial robotics is estimated to top $43
billion a year.
7
As a result, many of the under-
lying advances in robotics will come from the
commercial sector and will be widely available.
e U.S. military is used to competing in a world
where some of the most game-changing innova-
tions – such as stealth, GPS and precision-guided
weapons – come from the U.S. defense sector. It is
ill-prepared for a world where such technologies
are widely available to all.
If the U.S. military is to keep pace with the
unfolding robotics revolution, it will need to
adopt an aggressive strategy of targeted research
and development, experimentation and concept
and doctrine development. is will require not
only increased resources, but also better institu-
tional processes. Existing acquisition processes
are too sluggish to keep pace with rapid tech-
nological change and pose a strategic risk to the
United States. If they cannot be reformed, then
DOD leaders will increasingly have to operate
outside the traditional processes in order to rap-
idly adapt to emerging needs, as they repeatedly
did when adapting to urgent needs for Iraq and
Afghanistan.
Most importantly, when new technologies upend
existing operational paradigms, the alternative
Emerging robotic technologies
will allow tomorrow’s forces
to ght as a swarm, with
greater mass, coordination,
intelligence and speed than
today’s networked forces.
What is a Robot?
Robotic systems combine two key attributes: (1)
uninhabited, or unmanned, platforms or vehicles;
and (2) autonomous or semi-autonomous opera-
tions. While a true “robot” incorporates both attri-
butes, they can be separated. Some uninhabited
platforms or vehicles are remote-controlled, and
autonomous features can and often are incorpo-
rated onto human-inhabited platforms.
Removing the human from a vehicle can have
several advantages. Vehicles that are uncon-
strained by human physical limitations can have
increased range, endurance, maneuverability,
persistence, speed or stealth. Without a human
onboard, commanders can also use the vehicle
to undertake more hazardous missions without
risking a human life.
Autonomy is the ability of a machine to perform a
task without human input. Increased automation
or autonomy can have many advantages, includ-
ing increased safety and reliability, improved
reaction time and performance, reduced person-
nel burden with associated cost savings and the
ability to continue operations in communications-
degraded or -denied environments.
Elements of the U.S. military
continue to resist technologies
that disrupt familiar
operational paradigms, such as
automation that would change
the paradigm of control for
human pilots over aircra.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
12
|
In the 1980s, technological devel-
opments in sensors, command-
and-control networks and preci-
sion-guided munitions enabled
the possibility of real-time preci-
sion targeting of ground forces,
with the potential for strategic
eects that were not previously
possible without resort to nuclear
weapons. Soviet military theorists
were the rst to recognize the
game-changing potential of these
technologies and coined the term
“reconnaissance-strike complex”
to describe the synergistic com-
bination of sensors, networks and
precision-guided munitions work-
ing together.
The rst battle networks actually
originated in World War II. During
the Battle of Britain, the United
Kingdom used a network of radars
and spotters, connected with radio
and telephone cables, to direct
British ghters toward incoming
German bombers. Actual engage-
ments were still conducted with
unguided weapons, however.
During the next several decades,
precision-guided munitions
increased in accuracy while sen-
sors and network technology also
improved. By the early 1990s they
had reached a culminating point,
and the overwhelming U.S. victory
in the Persian Gulf War validated
Soviet theories about the value of
information technology-enabled
reconnaissance-strike networks.
8
Today, sophisticated nation-states
operate reconnaissance-strike
battle networks comprised of
sensors, command-and-control net-
works and precision-guided weap-
ons. The combination of these
elements allows forces to ght
as a networked whole capable of
long-range precision strikes. These
technologies are not only prolifer-
ating to other states over time, but
many low-cost versions are within
the reach of non-state actors. The
United States should expect future
adversaries, state and non-state
alike, to be able to operate battle
networks capable of targeting U.S.
forces with great precision.
Uninhabited and autonomous
systems will enable the next evolu-
tion, as forces shift from ghting as
a network to ghting as a swarm,
with large numbers of highly
autonomous uninhabited systems
coordinating their actions on the
battleeld. This will enable greater
mass, coordination, intelligence
and speed than would be possible
with networks of human-inhab-
ited or even remotely controlled
uninhabited systems. Human
judgment will still be essential for
many decisions, but automation
will help humans to process large
amounts of data rapidly, control
large numbers of vehicles simul-
taneously and shorten decision
cycles, accelerating the tempo of
operations.
What is a Reconnaissance-Strike Network?
concepts they enable should be embraced through
experimentation and innovation. e history of
revolutions in warfare has shown they are won
by those who uncover the most eective ways of
using new technologies, not necessarily those who
invent the technology rst or even have the best
technology. is report is an attempt to chart out
what those new uses might be, and how they could
change operations on the battleeld.

|
13
III. MASS
e United States outproduced its enemies in
World War II. By 1944, the United States and its
Allies were producing over 51,000 tanks a year to
Germany’s 17,800 and over 167,000 planes a year
to the combined Axis total of just under 68,000.
9
Even though many of Germany’s tanks and aircra
were of superior quality to those of the Allies, they
were unable to compensate for the unstoppable
onslaught of Allied iron.
10
Paul Kennedy writes in
e Rise and Fall of Great Powers:
… by 1943-1944 the United States alone was
producing one ship a day and one aircra every
ve minutes! … No matter how cleverly the
Wehrmacht mounted its tactical counterattacks
on both the western and eastern fronts until
almost the last months of the war, it was to be
ultimately overwhelmed by the sheer mass of
Allied repower.
11
e Cold War saw a shi in strategy, with the
United States instead initially relying on nuclear
weapons to counter the growing Soviet conven-
tional arsenal in Europe. By the 1970s, the Soviets
had achieved a three-to-one overmatch against
NATO in conventional forces and a rough parity in
strategic nuclear forces. In response to this chal-
lenge, the U.S. military adopted an “oset strategy”
to counter Soviet numerical advantages with quali-
tatively superior U.S. weapons. e result of this
approach was the invention of stealth technology,
advanced sensors, command and control networks,
and precision-guided weapons.
12
e full eect of these weapons was seen in 1991,
when the United States took on Saddam Hussein’s
Soviet-equipped army. Casualty ratios in the Gulf
War ran an extremely lopsided 30-to-1.
13
Iraqi
forces were so helpless against American precision
airpower that the White House eventually termi-
nated the war earlier than planned because media
images of the so-called “highway of death” made
American forces seem as if they were “cruelly and
unusually punishing our already whipped foes,”
in the words of Gulf War air commander General
Chuck Horner.
14
Precision-guided weapons,
coupled with sensors to nd targets and networks
to connect sensors and shooters, allowed the
information-enabled U.S. military to crush Iraqi
forces ghting with unguided munitions.
e proliferation of precision-guided weapons to
other adversaries is shiing the scales, however,
bringing mass once again back into the equa-
tion. e United States military can expect to face
threats from adversary precision-guided munitions
in future ghts.
15
At the same time, ever rising plat-
form costs are pushing U.S. quantities lower and
lower, presenting adversaries with fewer targets on
which to concentrate their missiles. U.S. platforms
may be qualitatively superior, but they are not
invulnerable. Salvos of enemy missiles threaten to
overwhelm the defenses of U.S. ships and air bases.
Even if missile defenses can, in principle, inter-
cept incoming missiles, the cost-exchange ratio of
attacking missiles to defending interceptors favors
the attacker, meaning U.S. adversaries need only
purchase more missiles to saturate U.S. defenses.
Uninhabited systems oer an alternative model,
with the potential to disaggregate expensive multi-
mission systems into a larger number of smaller,
lower cost distributed platforms. Because they can
take greater risk and therefore be made low-cost
and attritable – or willing to accept some attri-
tion – uninhabited systems can be built in large
Quantity has a quality all
of its own.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
14
|
numbers. Combined with mission-level autonomy
and multi-vehicle control, large numbers of low-
cost attritable robotics can be controlled en masse
by a relatively small number of human controllers.
Large numbers of uninhabited vehicles have sev-
eral potential advantages:
• Combat power can be dispersed, giving the
enemy more targets, forcing the adversary to
expend more munitions.
• Platform survivability is replaced with a concept
of swarm resiliency. Individual platforms need
not be survivable if there are sucient numbers
of them such that the whole is resilient against
attack.
• Mass allows the graceful degradation of combat
power as individual platforms are attrited, as
opposed to a sharp loss in combat power if a
single, more exquisite platform is lost.
• Oensive salvos can saturate enemy defenses.
Most defenses can only handle so many threats
at one time. Missile batteries can be exhausted.
Guns can only shoot in one direction at a time.
Even low cost-per-shot continuous or near-con-
tinuous re weapons like high energy lasers can
only engage one target at a time and generally
require several seconds of engagement to defeat
a target. Salvos of guided munitions or uninhab-
ited vehicles can overwhelm enemy defenses such
that “leakers” get through, taking out the target.
Some examples of ways in which these advantages
could translate to new, innovative approaches for
using uninhabited systems are below.
ATTRITABLE UNINHABITED COMBAT AIRCRAFT
In 2008, a now-infamous study by RAND Project
Air Force examined a potential future air-to-
air exchange between the U.S. and China over
Taiwan.
16
Because U.S. ghters had to y from pro-
tected air bases located in Guam, U.S. numbers in
the ght were signicantly reduced. Even with the
entire U.S. F-22 inventory located at Guam, range
and endurance constraints meant that only six
F-22s could be maintained over Taiwan continu-
ously. By contrast, because of both greater numbers
Artist depiction of Chinese DF-21D anti-ship missile widely circulated on Chinese defense-related web forums.

|
15
of ghters and larger, closer air bases, China was
able to surge seventy-two aircra to the ght.
e analysis assumed that every single air-to-air
missile that came o of a U.S. F-22 hit a Chinese
ghter (probability of kill = 1.0) and that zero
Chinese missiles hit any U.S. F-22s. Even still,
China won the air-to-air engagement because U.S.
ghters ran out of missiles. (F-22s can carry eight
air-to-air missiles each.) Once the F-22s had run
out of missiles, or “gone winchester,” the remaining
Chinese ghters were free to attack vulnerable U.S.
tankers and surveillance aircra.
17
An uninhabited “missile truck” that brought addi-
tional air-to-air missiles to the ght to supplement
human-inhabited F-22s could tip the scales back in
the United States’ favor. Such an aircra need not
have the full performance characteristics of a 5
th
or
6
th
generation ghter aircra. It would only need to
have sucient stealth to get close enough to launch
its missiles against Chinese ghters. If it then
perished in the engagement, that would be accept-
able provided it took a sucient number of enemy
ghters with it. It would still have accomplished
the mission. e uninhabited aircra would not
need advanced autonomy, merely enough to y
in a straight line under a human’s control and
suciently robust communications links for the
human-inhabited F-22s to pass targeting data. All
targeting and ring decisions would be made by
the F-22 pilots. If such an aircra could be built at
relatively low cost, this uninhabited “loyal wing-
man” could be a tremendous force multiplier for
U.S. human-inhabited ghters.
Such a concept is not far from the original vision for
the joint unmanned combat air system (J-UCAS), a
relatively low-cost “aircra in a box.”
18
e Air Force
should begin an analysis of alternatives to deter-
mine whether such an uninhabited aircra could be
built that would have sucient stealth and payload
capacity to augment the missile capacity of existing
manned aircra at relatively low cost.
SMALL UNINHABITED AIR VEHICLES AND
AIRMOBILE ROBOTS
e miniature air-launched decoy (MALD) and
miniature air-launched decoy – jammer (MALD-J)
– loitering air vehicles that are not quite muni-
tions and are not aircra – hint to the potential
of small, loitering uninhabited air vehicles and
air-mobile robots. e MALD functions as an
aerial decoy to deceive enemy radars, while the
MALD-J jams enemy radars.
25
Similar future unin-
habited air vehicles, launched from aircra, ships
or submarines, could saturate enemy territory with
overwhelming numbers of low-cost, expendable
systems.
26
Like D-Day’s “little groups of paratroop-
ers” dropped behind enemy lines, they could sow
confusion and wreak havoc on an enemy.
Loitering electronic attack weapons could cre-
ate an electronic storm of jamming, decoys and
high-powered microwaves. Small air vehicles could
autonomously y down roads searching for mobile
missiles and, once found, relay their coordinates
back to human controllers for attack.
Large numbers of cheap, expendable systems
could be used to deny an enemy use of an air-
eld, “mining” the airspace above it by swarming
overhead like locusts, risking collisions if enemy
aircra tried to takeo or land. Air mobile systems
could conserve power by landing near an aireld
and attacking only periodically, either based on
acoustic signatures of landing aircra or randomly
timed sorties, disrupting air trac for days.
Such aircra would be small and would require a
means of getting to the ght. is could include
submarines parked o an enemy’s coast, uninhab-
ited missile boats that race to the enemy’s coastline
before launching their payloads into the air, large
bomber or cargo aircra or even uninhabited
undersea pods like DARPA’s Hydra program.
27
e Air Force has recently initiated development of
a new “ight plan” for small uninhabited air vehi-
cles. As it begins to scope out the potential for such
Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
16
|
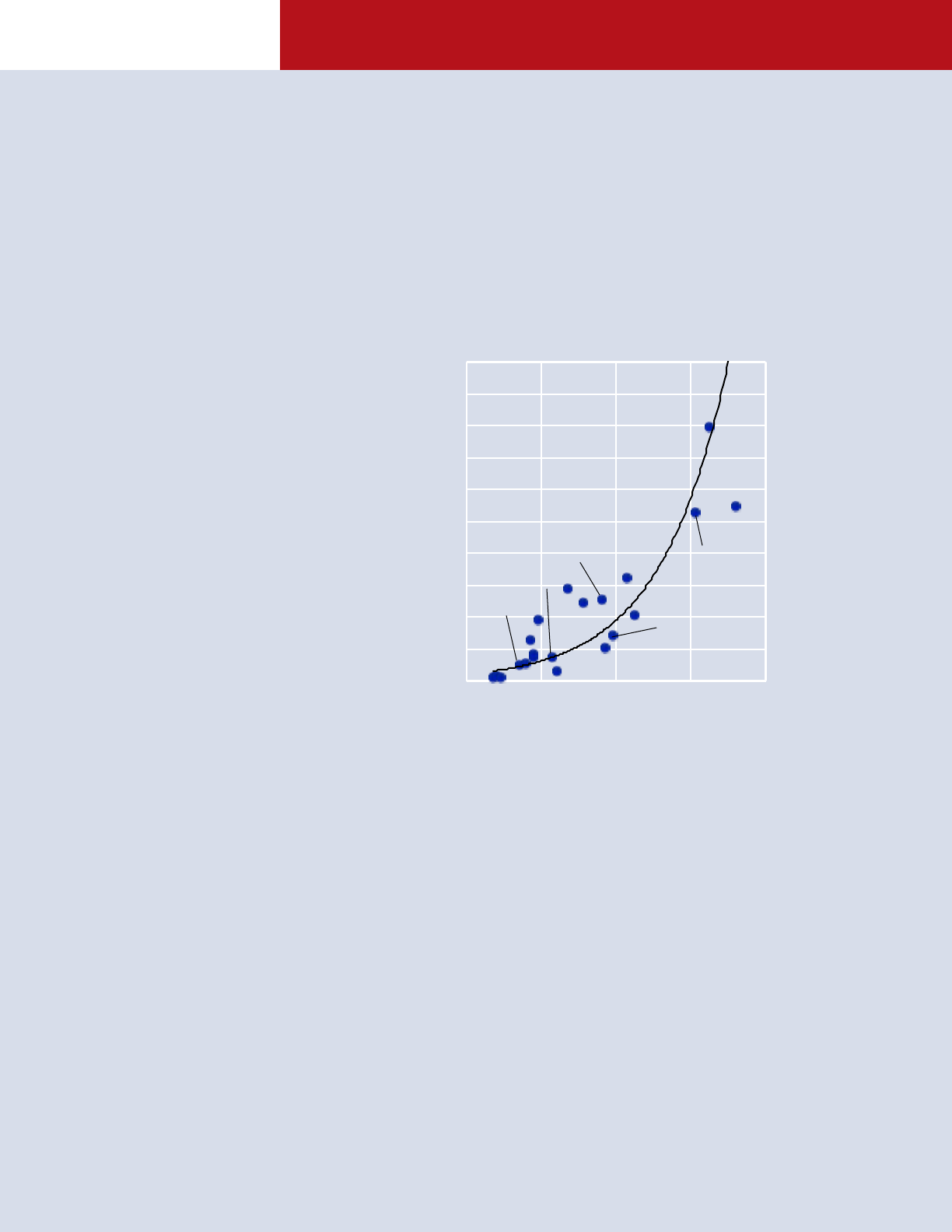
RISING COSTS: AUGUSTINE’S
LAW
In 1984, Norm Augustine observed
as one of “Augustine’s Laws” that the
cost of military aircraft was growing
exponentially, while the defense
budget was only growing linearly.
He humorously noted:
In the year 2054, the entire de-
fense budget will purchase just
one tactical aircraft. This aircraft
will have to be shared by the Air
Force and Navy 3½ days each per
week except for leap year, when
it will be made available to the
Marines for the extra day.
19
Of course, such a trend becomes a
problem long before the Depart-
ment of Defense gets down to only
one aircraft. That time is now.
RISING COSTS, SHRINKING
QUANTITIES
Rising costs have pushed down
procurement quantities for not only
aircraft but also ships. Furthermore,
shrinking procurement quantities
have the pernicious cyclical eect of
further driving up per-unit procure-
ment costs, as developmental costs
are spread over fewer and fewer
units. This can lead to more cuts in
production numbers.
From 2001 to 2008, the base
(non-war) budgets of the Navy
and Air Force grew 22% and 27%,
respectively, adjusted for ination.
20
Meanwhile, the number of combat
ships and aircraft in the U.S. inven-
tory declined by 10% for ships and
nearly 20% for aircraft over the
same period.
21
A number of fac-
tors contributed to this decrease in
numbers despite an overall budget
rise, and this was in part due to a
deliberate choice by the Navy and
Air Force to emphasize quality over
quantity.
22
But better quality can
only compensate so much.
THE QUALITY OF QUANTITY
AUGUSTINE’S LAW: RISING AIRCRAFT COSTS
OVER TIME
Sources: Marcelle Knaack, Encyclopedia of USAF Aircraft & Missile
Systems; Congressional Budget Oce, Total Quantities and Costs of
Major Weapon Systems Procured, 1974-1993; and DOD: F/A-18E/F SAR
(2012), Air Force FY 2011 Budget Estimate and F-35 SAR (2013).
Per Unit Costs of U.S. Combat Aircraft
(2014 USD in millions)
Year
F-100
F-4
F-15
F-16
F/A-18E/F
$-
$20
$40
$60
$80
$100
$120
$140
$160
$180
$200
1940 1960 1980 2000 2020
F35
F-22

|
17
DECLINING AIR COMBAT POWER FROM 20012014
Source: International Institute for Strategic Studies. Includes aircraft in store. Budget data from U.S. Department of Defense.
$-
$20,000
$40,000
$60,000
$80,000
$100,000
$120,000
$140,000
$160,000
$180,000
0
500
1,000
1,500
2,000
2,500
3,000
3,500
4,000
4,500
5,000
2001
2002
2003
2004
2005
2006
2007
2008
2009
2010
2011
2012
2013
2014
Air Force Base (Non-War) Budget
(2014 USD in millions)
Bombers
Fighters
Air Force base (non-
war) budget
Number of Combat Aircraft
DECLINING NAVAL COMBAT POWER FROM 20012014
Source: International Institute for Strategic Studies. Includes ships in reserve. Budget data from U.S. Department of Defense.
Number of Combat Ships
Navy Base (Non-War) Budget
(2014 USD in millions)
$-
$20,000
$40,000
$60,000
$80,000
$100,000
$120,000
$140,000
$160,000
$180,000
0
50
100
150
200
250
2001
2002
2003
2004
2005
2006
2007
2008
2009
2010
2011
2012
2013
2014
Carriers
Cruisers
Destroyers
Frigates
Submarines
Amphibious Ships
Navy base (non-war) budget
Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
18
|
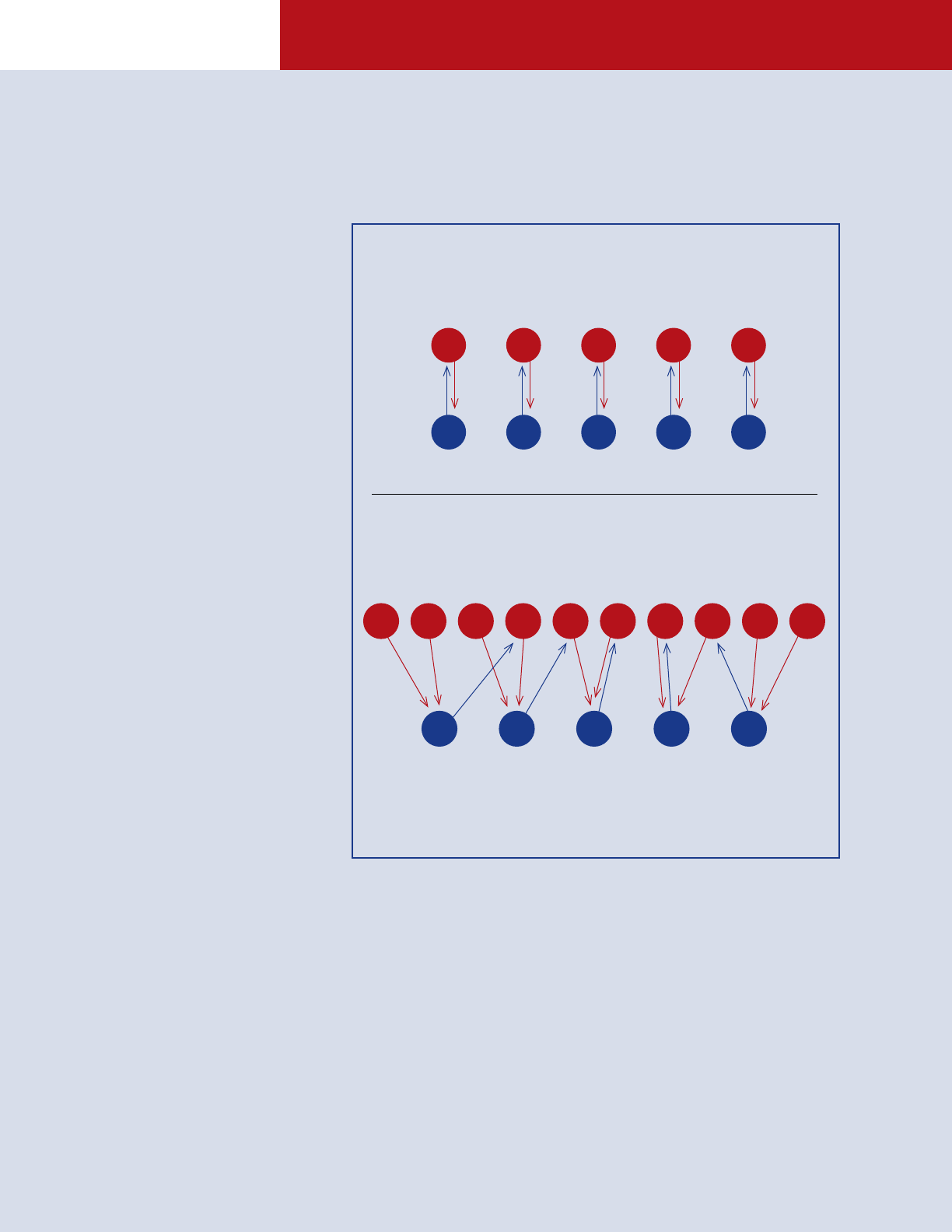
NUMBERS MATTER:
LANCHESTER’S LAW
A standard rule-of-thumb for the
advantage of quantity vs. qual-
ity in military engagements is
Lanchester’s Square Law. Lanches-
ter’s Square Law states that,
all things being equal, having
twice as many units in the fight
actually translates to a fourfold
increase in combat power for
units with aimed-fire weapons.
This is because the numerically
superior force can double up on
attacking enemy units, while the
numerically inferior force can only
attack half of the opposing force
at one time. This is in contrast
to hand-to-hand combat, where
combatants can only attack one
person at a time, and a twofold
increase in numbers translates to
only a twofold increase in combat
effectiveness.
A numerically inferior force can
compensate with greater qualitative
superiority, but a force that is out-
numbered by its opponent 2-to-1
must therefore be four times better
in quality in order to simply match
its opponent. There is, in essence, a
limit to how much qualitative supe-
riority can compensate for smaller
numbers.
23
As one example, a 2009 RAND study
of a hypothetical U.S.-China air war
over Taiwan highlighted the value
of numbers and the limits of qualita-
tive superiority alone. Analysts con-
ducted a detailed model of aircraft
engagements, accounting for quali-
tative and quantitative advantages.
Even though U.S. ghters were as-
sessed to be far more capable than
Chinese ghters – 27 times better in
the case of the U.S. F-22 – China was
able to launch nearly 800 sorties in
the rst day of ghting and won the
battle.
24
LANCHESTER’S SQUARE LAW
5 vs. 5
5 vs. 10
Relative combat power is proportional to the square of
the relative sizes of opposing forces. A two-fold numerical
advantage leads to a four-fold increase in combat power.

|
19
systems, it should be careful to include loitering air
vehicles like MALDs, not just recoverable aircra.
e Air Force should also be sure to examine the
full range of possible missions including strike and
electronic attack, not merely tactical surveillance,
as small uninhabited aircra are used for today.
SQUADORGANIC CLOSE AIR SUPPORT
One particularly notable use for small uninhabited
air vehicles is the ability to put organic close air
support directly in the hands of ground troops. e
Switchblade is a back-packable, loitering precision-
strike weapon. Weighing only 5.5 pounds, it can be
issued directly to ground troops to carry on patrol.
If engaged, they can launch the Switchblade, use its
onboard sensors to nd enemies, and then destroy
them with its low collateral damage warhead.
28
A small, loitering precision-strike air vehicle like
the Switchblade is a “reght ending weapon” that
places close air support directly in the hands of
ground troops and makes it instantly available.
29
Because of its low cost and high value, it can be
purchased in large numbers and issued to ground
troops to provide squad-organic close air support.
Switchblade has been deployed to Afghanistan and
the Army and Marine Corps are procuring addi-
tional systems.
30
GROUND VEHICLES ROBOTIC APPLIQUÉ KITS
e Army has thousands of fully functional
ground vehicles such as HMMWVs and M113
armored personnel carriers that will not be used in
future conicts because they lack sucient armor
to protect human occupants. At very low cost,
however, on the order of tens of thousands of dol-
lars apiece, these vehicles could be converted into
robotic systems. With no human on board, their
lack of heavy armor would not be a problem.
is could be done at low cost using robotic appli-
qué kits – sensors and command systems that are
applied to existing vehicles to convert them for
remote or autonomous operation. Robotic appliqué
kits have already been used to convert construction
vehicles into remotely operated Bobcats and bull-
dozers to counter improvised explosive devices.
31
Applied to existing vehicles, robotic appliqué kits
could give the Army a massive robot ground force
at extremely low cost. e sheer mass of such a
force, and the ability to apply it in sacricial or
suicidal missions, could change how the Army
approaches maneuver warfare.
Uninhabited ground vehicles could be the van-
guard of an advance, allowing robots to be the
“contact” part of a “movement to contact.” Robotic
vehicles could be used to ush out the enemy, ank
or surround them or launch feinting maneuvers.
Uninhabited vehicles could be air-dropped behind
enemy lines on suicide missions. Scouting for tar-
gets, they could be used by human controllers for
direct engagements or could send back coordinates
for indirect re or aerial attacks.
e Army is investigating appliqué kits for cargo
resupply, which will have signicant cost saving
advantages, but not yet for maneuver warfare.
e Army should begin a series of experiments
with uninhabited ground vehicles, akin to the
1940 Louisiana Maneuvers that accompanied the
adoption of the tank, to better understand the
role uninhabited vehicles could play in maneuver
operations.
UNINHABITED ARSENAL SHIPS TO EXPAND
MAGAZINE CAPACITY
A U.S. Aegis ballistic missile defense destroyer
is an amazing piece of machinery. A exible and
mobile oensive and defensive weapons platform, it
can engage and destroy enemy short- and interme-
diate-range ballistic missiles and can strike targets
deep on land with Tomahawk cruise missiles. e
Aegis destroyer’s sole shortcoming is its limited
magazine capacity. A Flight II Arleigh Burke-class
destroyer has 96 vertical launching system (VLS)
cells, a modular system that can be used to carry

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
20
|
a mix of oensive and defensive missiles.
32
VLS
space is limited, and once its missiles are exhausted
the Aegis’s oensive and defensive capabilities are
signicantly reduced.
Uninhabited arsenal ships could be used to
expand destroyer magazine capacity, dramatically
enhancing the oensive and defensive capacity of
existing destroyers. ese could take the form of
uninhabited surface barges or undersea pods. e
commercial shipping industry is already explor-
ing the possibility of uninhabited ships at sea to
reduce costs.
33
By leveraging this technology, the
Navy could eld additional missile capacity at rel-
atively low cost. Uninhabited arsenal ships could
be built much cheaper than additional destroyers
because they would not be warships. ey would
not have radars, guns and other combat capabili-
ties. ey would simply need large numbers of
VLS cells and reliable communications link to
human-inhabited ships, both for targeting and
safety purposes. Any additional survivability
features would need to be balanced against cost,
because such vessels could be attritable in a ght.
In fact, all things being equal, a large number of
lower-cost missile barges would be preferable to a
single high-cost one, since having to target more
barges would be cost-imposing to an adversary.
Undersea payload modules stocked with missiles
would be even better, since they could be parked
very close to an enemy’s coastline and would be
extremely dicult to detect. On warning, they
could launch missiles or even uninhabited aircra
into the ght.
e Navy has already tested the basic concept
of uninhabited missile boats, demonstrating the
ability of a small uninhabited surface vessel to
launch missiles to intercept enemy swarming small
boats in 2012.
34
A missile barge loaded with VLS
cells would be a scaled up version of the same
concept. e missile barge is very similar to the
concept of a minimally-manned low-cost “arse-
nal ship,” which was oated in the mid-1990s.
35
e Navy should begin experiments to scale up
already-demonstrated uninhabited missile boats to
larger, VLS-capable surface and subsurface ves-
sels and begin a study of possible designs. As the
commercial shipping industry begins to explore
uninhabited barges, the Navy may be able to lever-
age commercial-o-the-shelf technologies to lower
cost.
“BILLIONS OF DRONES”
Ultra-cheap 3D-printed mini-drones could allow
the United States to eld billions – yes, billions – of
tiny, insect-like drones. Researchers at Harvard
have developed a technique for 3D-printing
drones cheaply and eectively, without errors, by
the sheet. e “Mobee” drone is manufactured
by a 3D printer in a two-dimensional sheet, and
then pops out of the sheet and folds into a tiny,
bug-sized drone.
36
e Mobee is tiny and lacks a
power source or sophisticated programming, but
computer processing power is becoming smaller
and faster at an exponential rate. Just as swarms
of insects, which individually are not particularly
intelligent, can nevertheless collectively perform
complicated tasks, a cloud of tiny drones could
similarly be used in novel and inventive ways.
“Smart clouds” of 3D printed drones could ood a
building, locating and identifying enemy combat-
ants and civilians, or could even be airdropped
over a wide area to nd enemy personnel and
materiel. If a useful tiny drone could be manufac-
tured using 3D printing techniques for less than a
dollar apiece, procuring a billion is not out of the
Department of Defense’s reach.
Cost-Exchange Ratio
e concept of deploying large number of unin-
habited systems on the battlespace hinges squarely
on the issue of cost. If such systems cannot be
made cheaply, they cannot be made in large
numbers. But “cheap” is a relative term, as is
“expendable.” How cheap do systems need to be in
order to be useful?

|
21
e key metric is not the cost of uninhabited
platforms themselves, but rather the cost-exchange
ratio between adversaries. is ratio is tradition-
ally used in the context of ballistic missile defense,
measuring the aggressor’s marginal cost of over-
whelming enemy defenses as compared to the
defender’s marginal cost of countering the attack.
In general, the cost-exchange ratio can be thought
of as the ratio of the cost of an approach compared
to the cost of its countermeasure. e U.S. military
should consider its investments within the context
of cost-exchange ratios and seek favorable or at
least minimally disadvantageous cost-exchange
ratios. In some cases, an innovation that oper-
ates at an unfavorable cost-exchange ratio but
is less unfavorable than before may still be an
improvement.
Non-material costs and relative cost to an adver-
sary should also be considered. An innovation that
can be countered cheaply may still be advanta-
geous if it forces the enemy to expose himself in a
dangerous way or consumes other scarce resources
for the enemy, such as time or personnel. Similarly,
costs should be considered within the context of
an adversary’s resources. An even cost-exchange or
even a slightly unfavorable one may be a perfectly
acceptable approach if one has deeper pockets than
one’s enemy and is willing to outspend them.
A New Paradigm for Assessing Qualitative
Advantage
e point of building large numbers of lower cost
systems is not to eld forces on the battleeld that
are qualitatively inferior to the enemy. Rather, it
is to change the notion of qualitative superiority
from an attribute of the platform to an attribute
of the swarm. e swarm, as a whole, should be
more capable than an adversary’s military forces.
at is, aer all, the purpose of combat: to defeat
the enemy. What uninhabited systems enable is
a disaggregation of that combat capability into
larger numbers of less exquisite systems which,
individually, may be less capable but in aggregate
are superior to the enemy’s forces.
Disaggregating combat power will not be possible
in all cases, and large (and expensive) vehicles
will still be needed for many purposes. Expensive,
exquisite systems will inevitably be purchased in
small numbers, however, and so where possible
they should be supplemented by larger numbers
of lower-cost systems in a high-low mix. Neither
a cheap-and-numerous nor an expensive-and-few
approach will work in every instance, and U.S.
forces will need to eld a mix of high and low-cost
assets to bring the right capabilities to bear – and
in the right numbers – in future conicts.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
22
|
The chief value of mass is that it can
be used to impose costs on adversar-
ies because it forces one’s adversary
to counter large numbers of sys-
tems. The value of mass in a cost-
imposing strategy can be illustrated
with a simple vignette:
Two adversaries, Red and Blue, are
engaged in a technological com-
petition of innovation and counter-
measures. In an unguided muni-
tions regime, both seek to maximize
the rate of re of their weapons and
the density of the barrage landing
on enemy positions. Because the
unguided munitions are inaccurate,
large numbers are needed to maxi-
mize the odds of a successful hit
on an enemy target. Blue develops
guided munitions rst, however,
and has a game-changing advan-
tage.
With guided munitions, Blue is able
to trade large numbers of unguided
weapons for smaller numbers of
higher-cost guided munitions.
This tradeo is a winning strategy
because the guided munitions
have a high probability of kill (Pk),
meaning they have a high probabil-
ity of hitting and destroying their
target. Rather than pour thousands
of unguided munitions at Red, Blue
can invest scarce defense dollars in
a mere handful of guided munitions
that home in on Red and strike their
target. Red is powerless against this
approach.
This works great for Blue until Red
develops guided munitions as well.
Now Red can counter both Blue’s
munitions and, more importantly,
Blue’s power projection platforms
that launch the munitions with
Red’s own guided munitions. This is
a winning strategy for Red because
– in this vignette – there is a funda-
mental asymmetry between Red’s
and Blue’s strategic approaches.
Blue is a naval power attempting
to project power around the globe
far from its home, while Red is a
land power with a large land mass
within which Red can hide mobile
missile launchers and build scores
of dispersed airelds. Blue has many
targets to engage and Red has few.
Blue now has two approaches to
counter this new challenge from
Red. Blue can continue to invest
in fewer numbers of ever-higher
quality assets or buy larger num-
bers of lower-cost and therefore
lower-quality assets. Blue has a xed
amount of money, so every dollar
spent on one type of platform or
munition is a dollar robbed from
another. Let’s consider the value of
each approach:
Higher-quality: Let’s assume
that for its money Blue can buy 1
high-cost, high-quality asset for
every given Red target , with a
Pk of 0.9.
37
That is, this asset has a
90% probability of achieving a kill
against a Red target.
High-quantity: Alternatively,
for the same amount of money
Blue can invest in 20 lower-cost
and lower-quality assets, each
with a Pk of 0.11. Each individual
weapon has only an 11% chance
of killing a Red target, but the
aggregate odds of one of them
killing a target if twenty are red
is 90%.
38
From Blue’s perspective, both strate-
gies are equal. They cost the same
and achieve the same eect. In one,
all of Blue’s investment dollars go
to a single high-quality asset. In the
other, Blue resources are spread
over a larger number of lower-cost
assets which, in aggregate, achieve
the same capability. Both are viable
strategies for Blue, but how do they
look from Red’s perspective?
For Red, countering Blue’s high-
quantity approach is much more
dicult if Red’s preferred method of
countermeasure is hit-to-kill inter-
ception. If Blue adopts a high-quali-
ty approach, Red’s only challenge is
to nd a way to hit Blue’s single as-
set. If Blue adopts a higher-quantity
approach, on the other hand, then
Red needs to hit and kill all of Blue’s
assets, even though most of them
will not actually succeed in killing
the Red target.
39
From Red’s per-
spective, this is a nightmare. Even
though most of Blue’s assets are
not a threat, Red can’t know which
will miss and which will hit, making
the problem of intercepting Blue’s
assets twenty times harder.
40
Blue’s
choice to disperse combat power
among a large number of assets is
very cost-imposing to Red, since
all of Blue’s assets eectively act as
decoys for the few that get through.
What if Red tried a dierent ap-
proach?
THE COSTIMPOSING VALUE OF MASS

|
23
The challenges involved in getting
a kinetic hit-to-kill on all of Blue’s
assets might drive Red to focus
instead on reducing the Pk of all
of Blue’s assets across the board
through the use of decoys or some
kind of wide-area spoong attack.
What is the eect of such an ap-
proach on Blue?
Let’s assume that Red adopts a
countermeasure that reduces the
eectiveness of Blue’s assets by
50%.
For the high-quantity approach,
Blue’s Pk drops from 0.11 to 0.055
for each asset.
1
In order to get
back up to a 90% probability of a
hit, Blue must launch 41 assets at
Red instead of twenty, or just over
double what was required before
Red degraded Blue’s munitions’
eectiveness.
For the high-quality approach,
Blue’s Pk drops from 0.9 to 0.45
for each asset. In order to get the
total probability of a hit back up
to 90%, Blue must now eld 4
assets instead of one, an increase
of fourfold over its original ap-
proach.
41
Again, numbers matter. Red’s
countermeasure that reduces the
Pk of any given Blue asset by 50% is
much more cost-imposing to Blue
when Blue relies on high-quality
assets. This makes sense, because
when Blue was using a low-cost,
high-quantity approach, Blue wasn’t
1. See Appendix for a table of Pk values.
relying heavily on the quality of its
assets individually for securing a kill
anyway. Blue’s approach favored
mass and Blue can counter degrad-
ed quality by simply throwing more
mass at the problem.
Are larger numbers of low-cost
assets always the answer? Of
course not. The merits of any given
approach in a specic exchange
depend heavily on the particular
assets at play, their cost, actual Pk,
the cost of countermeasures and
counter-countermeasures and the
cost of any platforms to get them
into the ght. The example of trad-
ing twenty lower-cost assets with
a Pk of 0.11 for one high-cost asset
with a Pk of 0.9 is notional and used
only to illustrate the value of mass.
It is not necessarily indicative of any
specic cost-quantity-Pk tradeo.
All things being equal, however, dis-
persing one’s combat power impos-
es signicant costs on the enemy by
forcing the enemy to counter many
threats, even if individually each of
those threats is less capable.
Even if the cost-quantity-Pk tradeo
for a particular asset favors mass,
the ability to get additional mass to
the ght is essential to the success
of this strategy. If Blue relies on $1
billion power-projection platforms
that can carry only four missiles
each, then Blue ought to go with
higher-quality munitions. If Blue can
eld large numbers of low-cost ar-
senal ships and missile trucks to get
more assets into the ght … Well,
then it is another matter entirely.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
24
|
IV. COORDINATION
AND INTELLIGENCE
A large number of uncoordinated uninhabited
systems is not a “swarm;” it is a deluge. A swarm
consists of disparate elements that coordinate and
adapt their movements in order to give rise to an
emergent, coherent whole. A wolf pack is some-
thing quite dierent from a group of wolves.
42
Ant
colonies can build structures and wage wars, but
a large number of uncoordinated ants can accom-
plish neither. Harnessing the full potential of the
robotics revolution will require building robotic
systems that are able to coordinate their behaviors,
both with each other and with human controllers,
in order to give rise to coordinated re and maneu-
ver on the battleeld.
Swarms in Nature
Swarms in nature are wholly emergent entities that
arise from simple rules. Bees, ants, and termites
are not individually intelligent, yet their colonies
can exhibit extraordinarily complex behavior.
Collectively, they are able to eciently and eec-
tively search for food and determine the optimal
routes for bringing it back to their nests. Bees can
“vote” on new nesting sites, collectively decid-
ing the optimal locations. Ants can kill and move
very large prey by cooperating together. Termites
can build massive structures, and ants can build
bridges or oat-like structures over water using
their own bodies.
COLLECTIVE INTELLIGENCE IS AN EMERGENT
PHENOMENON
ese collective behaviors emerge because of
simple rules at the individual level that lead to
complex aggregate behavior. A colony of ants will,
over time, converge on an optimal route back from
a food source because each individual ant leaves
a trail of pheromones behind it as it heads back
to the nest. More ants will arrive back at the nest
sooner via the faster route, leading to a stronger
pheromone trail, which will then cause more ants
to use that trail. No individual ant “knows” which
trail is fastest, but collectively the colony nonethe-
less converges on the optimal route.
SWARMS USE IMPLICIT AND EXPLICIT
COMMUNICATION
Animals communicate through a variety of
methods, both explicit and implicit. Bees com-
municate the degree of interest over their
potential food site through a “waggle” dance,
while wolves use body language and barks to
communicate within the pack.
Implicit communication also plays a signicant
role. Flocks of birds, schools of sh and herds of
animals do not stay together because of explicit
communication signals between individual ani-
mals, but because each animal keys its movements
o of those around it. Once on the attack, a wolf
pack operates as a synchronized whole because
individual members adapt their behavior based
on that of other wolves.
43
is is not dissimilar
from military small unit tactics, where “battle
drills” allow a well-trained re team to execute
coordinated maneuvers with little or no explicit
communication among them, once the decision
has been made to execute a particular drill.
A novel and signicant method of communica-
tion between animals is stigmergy, where animals
e battleeld is a scene
of constant chaos. e winner
will be the one who controls
that chaos, both his own
and the enemy’s.
N B

|
25
alter their environment and, in so doing, leave
signals for other members of the swarm. An ant’s
pheromone trail is an example of stigmergy, as are
the implicit signals termites leave each other in the
environment as they construct nests.
44
SWARMS COMMUNICATIONS CAN BE EXPLOITED
BY OTHER ANIMALS
ere are many examples in nature of animals
exploiting swarm communication signals to
deceive members of a swarm, either to hide within
the swarm or to hijack it for their own purposes.
Several animals exploit swarm communication
signals to hide within a swarm, freeloading on
the benets of security that the swarm brings. e
silvershmalayatelura ponerphila lives among nor-
mally aggressive army ants by rubbing itself on ant
larvae and pupae, absorbing their scent. e West
African Rubber Frog, on the other hand, directly
secretes a pheromone that prevents the normally
aggressive stinging ant paltothyreus tarsatus from
attacking it. e frog then lives inside the colony
during the dry season, reaping the benets of the
nest’s humidity and protection from prey.
45
“Slave-making” ants, by contrast, invert this trick
by fooling other ants into working for their colony.
Slave-making ants raid other rival ant colonies and
steal their larvae, taking them back to the slave-
making ants’ nest and raising them to take care
of the slave-making ants’ workers. Raised their
entire lives in a rival colony, the captured ants are
unaware that they have been hijacked by a rival
species.
46
e slave-making ant polyergus breviceps takes this
method a step further and, in addition to raiding
larvae, can hijack an entire colony. A polyergus
queen can inltrate a rival colony, kill the queen,
and assume control of the colony as its new queen.
Her ospring are then raised by the hijacked
colony and its workers.
47
us, a polyergus queen is
able to take control of the entire swarm and use it
for her purposes by lling one key role.
ese examples of animals exploiting commu-
nication signals among members of a swarm are
analogous to spoong and cyber attacks in the
military domain. Swarm security – ensuring that
other members of a swarm can be “trusted,” in
particular any element that serves as a leader – will
be especially important for military swarms.
Robot Swarms Dier from Animal Swarms
in Important Ways
Like ants, termites and bees, simple rules govern-
ing the behavior of robots can lead to aggregate
swarming behavior for cooperative scouting, forag-
ing, ocking, construction and other tasks. Robot
Ants work together to build a bridge with their bodies.
(SHUTTERSTOCK)

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
26
|
swarms can dier from those found in nature in
several interesting and signicant ways. Robot
swarms can leverage a mix of direct and implicit
communication methods, including sending
complex signals over long distances. Robot swarms
may consist of heterogeneous agents – a mix of
robots of dierent types or robots working together
to perform a task. For example, the “swarmanoid”
is a heterogeneous swarm of “eye-bots, hand-bots,
and foot-bots” that collectively work together to
solve problems.
48
Swarm security is an even larger concern for robot
swarms than for animals. Robot swarms have the
potential to fall victim not only to spoong attacks
like those of the West African Rubber Frog, but
also direct cyber attacks that usurp control of an
uninhabited system.
49
In December 2012, a hacker
demonstrated the ability to take control of a widely
used commercially-available drone by hacking
its unencrypted wi-.
50
“Swarm intelligence” can
help individual members be resilient against some
forms of cyber attacks. “Voting” mechanisms can
allow members to communicate to one when it has
fallen victim to a spoong attack. For example,
swarm elements could share position information,
allowing some measure of resiliency against GPS
spoong.
51
At the same time, whole swarms could
potentially fall victim to hijacking if an enemy
is able to spoof the entire swarm as a whole or
assume the role of a central node. Cyber vulner-
abilities are not unique to uninhabited systems, but
the lack of a human on board does introduce addi-
tional vulnerabilities. Human-inhabited systems
can, in principle, be equipped with physical over-
rides to be used in the event of a cyber attack, and
human “common sense” may aord a measure of
resiliency against some forms of spoong attacks.
e most important dierence between animal and
robot swarms is that robot swarms are designed
while swarm behavior in nature is evolved. Swarms
in nature have no central controller or “common
operating picture.” Robot swarms, on the other
hand, ultimately operate at the direction of a
human being to perform a specic task.
52
More research is needed to leverage the potential
for emergent swarm phenomena. Researchers have
only just begun to understand how simple rules
give rise to complex behavior. Simple robot swarms
have been demonstrated in laboratory settings,
but scientists do not yet have a universal model for
understanding what emergent behaviors will arise
from simple rules.
53
While swarms in nature rely on emergent behav-
ior for complex tasks, such as those performed by
insects, this may not be necessary for robot swarms
or even desirable if it makes swarm behavior less
predictable as a result. Instead, robot swarms could
leverage cooperative behavior for relatively simple
advantages, some of which are explained below.
Concepts for Military Swarming are Largely
Unexplored
Military applications for swarming are intriguing
but largely unexplored. Examples of ghters employ-
ing swarming tactics date back to Genghis Khan,
but have oen played a less-than-central role in
military conict. In their ground-breaking mono-
graph Swarming and the Future of Conict, John
Arquilla and David Ronfeldt articulate an evolution
of four doctrinal forms of conict across history:
• Melee – Chaotic combat among groups with
individuals ghting non-cohesively
• Massing – Large formations of individuals ght-
ing together in ranks and les, such as the Greek
phalanx
• Maneuver – Multiple formations ghting
together, like the Blitzkrieg, coordinating re
and movement across distances to achieve a
coherent aim across the battleeld
• Swarming – Large numbers of dispersed indi-
viduals or small groups coordinating together
and ghting as a coherent whole

|
27
MELEE
MELEE VS. MASS
MASS
In melee ghting, combatants ght as individuals, uncoordinated. Massed formations have the advantage of synchro-
nizing the actions of combatants, allowing them to support one another in combat. Massing requires greater organi-
zation, however, as well as the ability for individuals to communicate to one another in order to act as a whole.
MANEUVER
MASS
MASS VS. MANEUVER
Maneuver warfare combines the advantages of mass with increased mobility. In maneuver warfare, mutually sup-
porting separate massed formations move as independent elements to outank the enemy and force the enemy
into a disadvantageous ghting position. Maneuver warfare requires greater mobility than massing as well as the
ability to communicate eectively between separated ghting elements.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
28
|
MANEUVER VS. SWARM
SWARM
MANEUVER
Swarm warfare combines the highly decentralized nature of melee combat with the mobility of maneuver and a
high degree of organization and cohesion, allowing a large number of individual elements to ght collectively.
Swarming has much higher organization and communication requirements than maneuver warfare, since the
number of simultaneously maneuvering and ghting individual elements is signicantly larger.
ese types of warfare require increasingly sophis-
ticated levels of command-and-control structures
and social and information organization. Examples
of all four forms, including swarming, can found
dating to antiquity, but widespread use of higher
forms of warfare did not occur until social and
information innovations, such as written orders,
signal ags or radio communication, enabled
coherent massing and maneuver.
54
While low-cost uninhabited systems allow a
military to eld large numbers of forces, informa-
tion technology allows them to ght as something
|
29
more than an uncoordinated deluge. Instead,
networking and automation let systems cooperate
to ght together as a coherent entity, even while
dispersed at great distance. Swarming as a doctri-
nal concept has the advantage over maneuver in
that it distributes one’s forces across the battleeld,
while still harnessing them to ght as a coherent
whole. While this places greater pressures on one’s
forces for communication and coordination, it also
presents the enemy with a much more formidable
challenge. Rather than ghting against a forma-
tion, the enemy faces an insuppressible collection
of targets that are, seemingly, everywhere and
nowhere at once.
Intelligent Swarms Have Several Advantages
on the Battleeld
Arquilla and Ronfeldt recommend a tactic of
swarming as “sustainable pulsing” where forces
mass res, then disperse and come together again
to attack.
55
Sean Edwards, in a comprehensive
review of swarming tactics, denes swarming as
“when several units conduct a convergent attack on
a target from multiple axes.”
56
ese are tactical denitions, however, relating to
but one possible advantage stemming from large
numbers of networked, autonomous elements on
the battleeld coordinating to achieve a coherent
whole. For our purposes, we will dene an intel-
ligent robotic swarm more broadly as a network
of uninhabited vehicles that autonomously coor-
dinate their actions to accomplish a task under
some degree of mission-level human direction. e
ability to make networked, autonomous systems
cooperate has many advantages, including but
not limited to coordinated re and maneuver. Just
a few of these potential advantages are explored
below.
DYNAMIC SELFHEALING NETWORKS
Autonomous uninhabited vehicles can coordi-
nate their actions to form self-healing, responsive
networks for reconnaissance, communications
relay and other activities. DARPA’s Heterogeneous
Airborne Reconnaissance Team (HART) suc-
cessfully demonstrated the ability of a network
of cooperating uninhabited aircra to cover an
area for reconnaissance purposes, autonomously
re-tasking assets to cover areas of interest based
on warghter input.
57
Similar self-coordinating
networks could be used for ground and maritime
reconnaissance. Uninhabited undersea vehicles,
working together in concert with undersea pods,
could form a reconnaissance network to coopera-
tively identify and track submarines.
58
Uninhabited
vehicles could autonomously de-mine coastal
areas and beaches and, using simple “anti-social”
communication means to avoid other uninhabited
vehicles, could ensure adequate coverage over a
given area. Intelligent mineelds, conversely, could
shi to re-cover areas that have been de-mined,
presenting enemies with an adaptive threat.
Intelligent networks of uninhabited vehicles with
communications relay payloads could adapt to
network disruptions and shi to cover moving
forces or areas of high bandwidth. When con-
fronted with jamming, networks could shi and
adjust their topology to optimal advantage to avoid
interference.
59
Networks of loitering uninhabited
aircra could provide ground forces not only with
reconnaissance and communications, but also
Swarming as a doctrinal
concept has the advantage
over maneuver in that it
distributes one’s forces across
the battleeld, while still
harnessing them to ght as a
coherent whole.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
30
|
air-mobile resupply, jamming and close air support
all responsive to the needs of warghters on the
ground.
COORDINATED ATTACK AND DEFENSE
Just like wolves in a pack present their enemy with
an ever-shiing blur of threats from all directions,
uninhabited vehicles that can coordinate maneuver
and attack could be signicantly more eective
than uncoordinated systems operating en masse.
Waves of kinetic attack weapons could synchro-
nize their strikes to occur simultaneously or from
multiple directions to saturate and overwhelm
defenses. Decoys, jamming and electronic attack
weapons could autonomously coordinate their
eorts and time them to be optimally advanta-
geous to support kinetic strikes.
For defensive purposes, clouds of uninhabited
vehicles could protect ships or ground troops from
attack, autonomously shiing to interdict potential
threats. e Navy recently demonstrated the ability
of a swarm of autonomous uninhabited surface
vessels to intercept and surround an unknown and
potentially hostile vessel.
60
Swarms of uninhabited
surface, air and undersea vehicles could provide
early detection and interdiction of threats to U.S.
ships, including from enemy swarming small
boats, and the Navy should rapidly move to inte-
grate this capability into a full program of record.
Coordinating attack or defense could allow more
intelligent target selection, leading to more tar-
gets being eectively engaged. One way this could
occur is if munitions had onboard sensors to
conduct battle damage assessment before attack.
In such a case, they could conrm whether a given
target had already been destroyed by any previous
munitions and, if so, could proceed on to second-
ary targets. Communication between munitions
would thus occur indirectly through a form of
stigmergy. is could expand the total number of
targets that a sortie could successfully take out.
For example, if a missile with a Pk = 0.5 were
launched against a target, four missiles would be
needed to get a 90% assured probability of kill. If,
on the other hand, each missile independently had
the ability to look rst before deciding whether to
strike or move on to secondary targets, then four
missiles would still need to be launched, but 50%
of the time the rst missile would strike the target
successfully and the remainder would move on to
secondary targets. 25% of the time, the rst mis-
sile would successfully strike the primary target,
the second missile would successfully strike the
secondary target, and the remaining two missiles
would move onto tertiary targets.
61
Sometimes the
swarm would take out three or even four targets.
Sometimes all of the missiles would be unsuc-
cessful. On average, though, the swarm would
successfully take out two targets rather than just
one. us, in this example, the ability for the mis-
siles to operate cooperatively through stigmergy
would double striking capacity.
e reverse is also true. If a swarm of munitions
were sent aer a group of targets and each muni-
tion had a very high probability of kill such that
only one was needed per target, the munitions
could directly communicate in ight to deconict
their targets in order to ensure that multiple muni-
tions were not wasted on the same target.
DISAGGREGATED FUNCTIONALITY FOR LOWER
COST, MORE DIVERSE SOLUTIONS
A cooperative swarm of uninhabited systems can
distribute its functions across a mix of platforms,
allowing more numerous lower-cost systems.
Rather than a single exquisite multi-mission
platform, a swarm can employ a suite of many
low-cost single-mission platforms that are able to
work cooperatively to accomplish the same mis-
sion. In addition to complicating the enemy’s
targeting problem, employing a diverse mix of
heterogeneous assets has the advantage of forc-
ing the adversary to respond to multiple dierent
kinds of threats. Such an approach can also lower

|
31
costs by using a “high-low mix” of assets, with a
small number of more expensive assets working in
concert with a large number of lower-cost assets to
solve a problem.
For example, a reconnaissance network might
employ a high-low mix of a few expensive, high-
quality sensors combined with large numbers of
lower-quality sensors. e lower-cost sensors could
be distributed over a wide area to nd targets and
then, upon discovering them, cue a platform with a
more expensive sensor to come conrm the target’s
identity. is could enable wider and more ecient
coverage at lower cost.
Similar approaches could be used for inertial
navigation systems and communications relay.
Inertial navigation systems are used for GPS-
independent navigation, an essential capability in
anti-access environments. e estimated posi-
tion of an inertial navigation unit “dris” over
time, however, leading to position inaccuracy that
grows with time. More expensive, higher-quality
systems can compensate for this problem, as can
regular precise position updates from an outside
source, such as an element outside a GPS-denied
area. A high-low mix of inertial navigation sys-
tems among a network of uninhabited vehicles
can allow one to act as a “navigator” for others,
with other platforms requiring only a capable-
enough system to get them through until the next
position update. Similarly, higher-cost long-range
protected communications systems can be located
on a “communicator” within the swarm, with
other systems passing their communications
through this node.
e capabilities of a single exquisite multi-mission
system can be entirely disaggregated among a
swarm of low-cost vehicles performing the same
functions, but merely as a distributed swarm.
is could include surveillance and reconnais-
sance, electronic attack, decoys and deception,
battle damage assessment and strike. By leveraging
A swarm of uninhabited surface vessels patrols in formation in a demonstration on the James River.
U.S. NAVY

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
32
|
existing platforms with modular payloads, such
a swarm could be built and elded at relatively
low cost. Each individual system need not be and
should not be a new, exquisite system in its own
right. Instead, each element of the swarm should
leverage modular design and existing platforms
as much as possible, striving for a simple, low-cost
solution to solve one problem. By being simpler,
they can be built on shorter timelines with lower
technology risk and fewer requirements creep, get-
ting at the underlying conditions behind platform
cost growth.
62
An example of such an approach can be found in
the MALD and MALD-J air-launched decoy and
jammer. While these platforms do not compete
with the functionality of a multi-mission aircra,
they are able to perform their tailored missions –
deception and jamming – at low cost. e same
concept can be leveraged for an expanded array of
missions, and indeed has already been proposed. A
proposed MALD-V variant would use a modular
design to incorporate a variety of single-mission
payloads, from target acquisition to battle damage
assessment to strike.
63
Disaggregating functionality from an exquisite
multi-mission system to a family of heteroge-
neous simpler, special-purpose systems also has
other benets. In addition to forcing the adversary
to respond to a range of threats, it can enhance
resiliency against enemy innovations and coun-
termeasures. If a weakness is shown in any one
system, only that discrete element needs to be
replaced or modied, rather than attempting
modications to a large multi-mission system.
Monocultures have inherent risk. Malfunctions,
like the oxygen system problems that grounded
the F-22 eet, or enemy countermeasures or cyber
attacks can have catastrophic consequences in
a monoculture.
64
at vulnerability may in fact
incentivize adversaries to concentrate their eorts
on attacking that single system.
65
DISTRIBUTED SENSING AND ATTACK
e ability to distribute sensors over a wide area
has tremendous advantages for both active and
passive sensing and precision geolocation. Multiple
cooperative vehicles can accomplish passive preci-
sion geolocation by triangulating targets. For
example, multiple widely distributed sensors can
locate emitters by comparing the dierences in
time of arrival and frequency due to Doppler shi
from relative movement.
66
For active detection,
distributed sensors can function like a multi-static
radar, with one sensor emitting a radar pulse and
multiple sensors detecting the reection, allowing
stealthier and higher-quality radar detection.
e same physical principles can also be used for
distributed attack. An array of electromagnetic emit-
ters can deliver focused electronic attack over long
distances. is approach depends on precise syn-
chronization of the relative location and timing of the
emitters, such that the electromagnetic waves arriving
at the target overlap in time and space. If achievable,
however, a distributed approach can deliver more pre-
cise electronic attack at lower power and with fewer
interference problems than blanketing a wide area.
67
DECEPTION
Swarms of vehicles could be used to deceive an
enemy into thinking a larger vehicle or even an
entire formation is moving through an area.
is could be done through a variety of means,
including generating false acoustic, visual or elec-
tromagnetic signatures. Cooperative decoys could
even be used to generate precisely-timed false radar
returns that create the illusion of a radar track
moving through integrated air defenses.
68
SWARM INTELLIGENCE
Distributed voting by numerous systems could
also be used to solve problems. Swarm intelligence
could be used to improve target identication, with
multiple sensors providing estimates of a target’s
probable ID and weighing their “votes” based on
their estimated condence.

|
33
V. SPEED
Machines cannot yet match human intelligence
in solving ambiguous or novel problems, but they
excel at speed. Automation, particularly among
networked autonomous systems, enables a much
faster pace of military operations. Automation
can be used to assist in processing large amounts
of information quickly, compressing the decision
cycle for human operators. is can result in faster
operations, helping commanders to understand
the battlespace, then adapt and react before their
adversaries. In addition, swarming can delegate
control to autonomous elements reacting immedi-
ately to events on the battleeld, allowing tactical
decision-making closer to the edge of battle.
69
Finally, removing humans entirely from the sense-
decide-act loop can result in faster reactions that
may be impossible for humans to match.
The Ever-Shifting Swarm
e result could be an accelerated pace and speed
of operations that would be impossible for adver-
saries to match unaided by automation. e sheer
volume of information in the future battlespace
may be impossible for commanders to understand
without automated information processing tools.
Moreover, swarming can present enemies with an
ever-shiing, constantly-adapting challenge. Just
as an adversary is beginning to understand the
threat environment, it changes once again.
70
In his
explanation of the importance of “getting inside”
an adversary’s observe-orient-decide-act loop, John
Boyd denes the objective of an accelerated action-
reaction cycle:
Goal: Collapse adversary’s system into confu-
sion and disorder by causing him to over and
under react to activity that appears simultane-
ously menacing as well as ambiguous, chaotic or
misleading.
71
Automated decision-making may not always be as
good as human decision-making, but it need not be
if it is faster, and if that speed leads to a sucient
advantage on the battleeld.
“Flash Wars” and Fragile Stability
An accelerated tempo of operations has the poten-
tial for signicant military advantages, but also
raises serious concerns. Just as the introduction
of automated trading algorithms has led to “ash
crashes,” automation in military crises could
introduce instabilities. e lure of quicker reac-
tion times or merely the fear that other nations
might develop automated weapons systems could
spark an automation arms race. is potential
“gunslinger” quality of automation is exceptionally
dangerous and destabilizing, particularly in cyber-
space where operations move at “net speed.”
ere is a tension between the speed of operations
and the speed of decisions. Automation that might
make sense tactically would be disastrous strategi-
cally if it led to “ash wars.” While militaries will
need to embrace automation for some purposes,
humans must also be kept in the loop on the most
critical decisions, particularly those that involve
the use of force or movements and actions that
could potentially be escalatory in a crisis.
During the Cold War, defense planners faced a
similar problem of “fragile stability,” whereby
vulnerable nuclear arsenals incentivized an enemy
to strike rst. In response, strategists developed
a doctrine of an assured second-strike capac-
ity in order to reduce incentives for a rst strike.
Similarly, strategists today must focus on resiliency
in order to be able to absorb a sudden destabilizing
attack and buy time for decision-makers to under-
stand a crisis before deciding how to respond.
While automation will be essential for some
Speed is the essence of war.
,

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
34
|
purposes, it should not take the place of humans
for decisions about when and how to use force.
Humans in the Loop
e potential for autonomous systems to increase
the speed of operations raises challenges for both
policy and strategy. When humans are the weak
link in an accelerated decision cycle, there are
very real operational incentives to delegate actions
directly to machines. Delegation of certain deci-
sions, however, particularly regarding the use of
force, raises challenging issues.
Two particularly notable policy concerns are
the role of autonomy in decisions regarding the
use of force and the role of human cognitive
enhancement technologies to assist humans in
keeping pace with an accelerating battleeld. e
Department of Defense has a policy on the role
of autonomy in the use of force, DOD Directive
3000.09, “Autonomy in Weapon Systems,” signed
in 2012.
72
State parties to the United Nations
Convention on Certain Conventional Weapons,
which has dealt with “special” weapons in the past
like blinding lasers, took up the issue of increased
autonomy in future weapons for discussion in the
spring of 2014. Discussions on this important topic
should continue, and the United States should con-
tinue to lead in this area.
e need to keep pace with an accelerated tempo
of war also raises dicult issues regarding human
cognitive performance enhancement. Human
performance modication technologies, includ-
ing pharmaceuticals such as Ritalin, Adderall
and other “study drugs,” or other modication
techniques, such as transcranial direct current
stimulation (tDCS), could allow humans to pay
attention, process information and react faster
than would otherwise be possible without these
aids. ese technologies raise dicult legal, policy,
ethical and social issues that must be addressed.
DOD has a responsibility to take care of its service-
members, both by ensuring that they are treated in
an ethical and responsible manner, and also by giv-
ing them access to the best life-saving capabilities.
DOD currently lacks a Department-wide policy on
human cognitive performance enhancement, how-
ever. DOD should take steps to address the policy
issues associated with these technologies in order
to guide research in this sensitive area.

|
35
VI. COMMANDING THE SWARM
Swarming models directly imported from nature
are not likely to be ideal for military settings,
since animal swarms lack a central commander.
At the same time, human controllers will not
want to be in a position to micromanage each
element of a swarm, nor will they have the band-
width to do so even if they desired. Human
commanders will need to control swarms at the
mission level, giving overarching guidance, but
delegating a wide range of tasks to autonomous
systems. In the near term, this will entail a shi to
mission-level autonomy and multi-vehicle con-
trol. In the long term, new command-and-control
models are needed to allow humans to employ
large swarms eectively.
Simple Multi-Vehicle Control is Possible with
Even Limited Autonomy
e U.S. military has demonstrated and used
multi-vehicle control, where one human controls
two or more uninhabited vehicles at the same time,
in experiments and limited operational settings.
e Air Force has experimented with rudimentary
control of multiple uninhabited aircra while in
transit, including in limited real-world operations,
although it is not routinely used.
74
e biggest challenge in adopting multi-vehicle
control is not technical, but rather understand-
ing the cognitive demands placed on the human
operator and how many vehicles can be eec-
tively controlled. ere is no easy answer, and
how many vehicles a single person can manage
depends on the task at hand, the human-machine
interfaces and the level of vehicle autonomy.
Early Air Force concepts for multi-vehicle control
suggested that a pilot could control up to four
vehicles at a time.
75
is is possible for simple
missions, like stationary surveillance, jamming or
point-to-point transit, even with relatively limited
autonomy. In fact, with greater autonomy, human
operators might be able to control far more than
four aircra at a time, so long as the demands
on the human operator per aircra are relatively
minimal.
If human operators are required to respond to
unanticipated events and make decisions, however,
then there are limits to how many vehicles a person
can eectively control. Switching between tasks
introduces ineciencies, as operators reorient their
situational awareness to each new task. e more
situation-specic the cognitive tasks are, and the
more they dier from each other, the greater the
time lag will be. Multiple overlapping events can
lead to wait times between the emergence of a need
for an operator and his or her ability to respond.
Whether or not these wait times are acceptable will
depend on the mission. For emergencies, human
attention may be needed urgently, but in other
situations a vehicle may be able to loiter until the
operator is able to attend to it. In addition, some
tasks may require an operator to focus his or her
attention solely on a single vehicle for some period
of time, such as following an emerging target
or taking control of a vehicle in an emergency,
while others will more readily lend themselves to
multi-tasking.
76
Many of these issues can be addressed through
better technology, concepts of operation or train-
ing. Multi-vehicle control architectures should be
networked, so that primary operators can pass o
control of vehicles to other operators in the event
that they need to focus their attention on one
vehicle. From a concept of operations perspective,
No plan survives rst contact
with the enemy.
()

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
36
|
there should be a sucient number of operators in
aggregate to allow for slack in the system to adapt
to unanticipated events, so that all operators are
not maxed to their cognitive load in steady-state
operations. In addition, human-machine interfaces
should be designed to assist operators in priori-
tizing multiple competing tasks. For example,
blinking lights might be used to draw attention
to an urgent task, while non-urgent tasks could
be placed in a queue so as not to distract opera-
tors from the task they are presently performing.
Improved automation can also help to reduce the
human task loading. Finally, training, experience
and even psychological orientation may play a
signicant role in operators’ ability to handle mul-
tiple, competing cognitive tasks.
Cooperative Multi-Vehicle Control Enables
More Complex Tasks
Cooperative multi-vehicle control takes this
concept to the next level, with a person tasking a
group of vehicles that then coordinate amongst
themselves to accomplish the task as a swarm.
For example, a human might task a swarm of
missiles with a set of targets, but let the missiles
coordinate among themselves to determine which
missile will hit which target. Or a human might
task a group of vehicles to maintain coverage over
an area, whether for surveillance, communica-
tions relay, electronic warfare or establishing
a defensive perimeter, and the vehicles might
coordinate to determine how best to cover the
area. ese vehicles could exist across multiple
An autonomous rigid hull inatable boat (RIB) participates in a demonstration on the James River as part of a swarm of thirteen uninhabited
autonomous boats.
U.S. NAVY

|
37
domains, such as air, sea surface and undersea
vehicles operating collectively with one person
controlling the group.
Concepts for cooperative multi-vehicle control
have been demonstrated in simulations and some
real-world experiments, and many applications
are technically feasible today.
77
In the summer
of 2014, the U.S. Navy demonstrated the ability
for one operator to control a swarm of thirteen
autonomous uninhabited small boats escorting
a high-value ship through a mock strait transit.
When a potentially hostile vessel was spotted, the
operator tasked the swarm to interdict and sur-
round the vessel, which it executed autonomously.
According to naval researchers in charge of the
experiment, such a concept could be scaled up to
one person controlling twenty or thirty boats at
a time.
78
e associated manpower savings and
reduction in risk to personnel are tremendous. An
interdiction operation that normally would have
included forty to y sailors closing with poten-
tially hostile actors can be executed by a single
sailor safely removed from harm’s way. Similar
concepts could be used in other domains and for
other missions, such as a swarm of air and ground
vehicles searching over a wide area to nd and
positively identify targets. While the Navy is mov-
ing out in this area for swarming boats, cultural
resistance to multi-aircra control in the Air Force
has hindered progress for air vehicles.
Multi-Vehicle Control Faces Cultural Barriers
to Adoption
Early Air Force experiments with multi-aircra
control led to dissatisfaction with human machine
interfaces and human task loading, including the
inability of pilots to hand over control of their
aircra to other pilots if they needed to focus atten-
tion on a single airplane.
79
Rather than improve
the technology to allow for networked control and
better interfaces, however, multi-aircra control
was deemed an “unfunded requirement.”
In 2010, then-Defense Secretary Robert Gates
directed the Air Force to develop improved multi-
aircra control interfaces to overcome concerns
about the technology as it existed at the time. His
direction included nearly $50 million in funding.
80
e Air Force never developed the technology,
however, instead arguing that the multi-aircra
control concept needed to be developed further
rst.
e Air Force is no further along in develop-
ing multi-aircra control today. e Air Force’s
recently released Remotely Piloted Aircra Vector
discusses multi-aircra control, but it is not funded
in the DOD budget.
81
Privately, Air Force ocials
claim that multi-aircra control is a “decade aer
next” technology. e reality is that the technology
exists today and has been demonstrated in its basic
form by many companies. What will take a decade
or longer on the current trajectory is cultural
acceptance of a model where pilots are not in direct
physical control of only one aircra at a time.
82
e belief that a human must control only one
aircra at a time comes from applying an exist-
ing paradigm – human-piloted aircra – to a new
technology. Viewing uninhabited air vehicles
through this lens is a choice, however. Military
forces already routinely employ uninhabited air
vehicles that are not directly controlled by human
operators. ey just aren’t called “unmanned
aircra.” ey are called missiles or decoys. Some,
like cruise missiles, y pre-programmed routes.
Others, like homing missiles, are highly autono-
mous and maneuver to targets on their own. And
many can receive new targeting data in ight and
respond to human taskings.
83
As uninhabited
vehicle technology matures, the lines between
uninhabited aircra, missiles and decoys will
continue to blur. If the U.S. military is to fully
capitalize on the potential of uninhabited systems,
it will need to be willing to change the operational
paradigm and embrace new concepts of operation.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
38
|
Large Swarms Require New Command-and-
Control Paradigms
Scaling multi-vehicle control up to large swarms
will require even more fundamental shis in
the command-and-control paradigm. e Naval
Postgraduate School is working on a 50-on-50
swarm vs. swarm aerial dogght, and researchers
at Harvard have built a swarm of over a thou-
sand simple robots working together to create
simple formations.
84
As the number of elements
in a swarm increases, human control must shi
increasingly to the swarm as a whole, rather than
micromanaging individual elements.
How to exercise eective command-and-control
over a swarm is an area of nascent research.
Possible command and control models, ordered
from more centralized to increasingly decentral-
ized control, include:
85
• Centralized control, where swarm elements feed
information back to a central planner that then
tasks each element individually.
• Hierarchical control, where individual swarm
elements are controlled by “squad” level agents,
which are in turn controlled by higher-level con-
trollers, and so on.
• Coordination by consensus, where swarm ele-
ments communicate to one another and converge
on a solution through voting or auction-based
methods.
• Emergent coordination, where coordination
arises naturally by individual swarm elements
reacting to others, like in animal swarms.
Each of these models has dierent advantages,
and may be preferred depending on the situation.
While completely decentralized swarms are able to
nd optimal solutions to complex problems, like
how ant colonies converge on the shortest route
for carrying food back to the base, converging on
the optimal solution may take multiple iterations,
and therefore time.
86
Centralized or hierarchical
planning may allow swarms to converge on opti-
mal, or at least “good enough,” solutions more
quickly, but requires higher bandwidth to transmit
data to a central source that then sends instruc-
tions back out to the swarm. Action by consensus,
through voting or auction mechanisms, could
be used when low bandwidth communications
exist between swarm elements.
87
When no direct
communication is possible, swarm elements could
still rely on indirect communication to arrive at
emergent coordination, however. is could occur
by co-observation, like how animals ock or herd,
or stigmergic communication by altering the
environment.
DECENTRALIZED SWARMS ARE INHERENTLY
ROBUST AND ADAPTIVE
Centralized control is not always optimal even if
robust communications exist, since detailed plans
can prove brittle amid fast-paced changes to a
battleeld environment. Decentralized control,
either through localized “squad commanders,”
voting-based consensus mechanisms or emer-
gent coordination has the advantage of pushing
decision-making closer to the battleeld’s edge.
is can both accelerate the speed of immedi-
ate reaction and make a swarm more robust to
communications disruptions. Swarms of indi-
vidual elements reacting to their surroundings in
accordance with higher-level commander’s intent
represent the ultimate in decentralized execution.
With no central controller to rely upon, the swarm
cannot be crippled or hijacked in toto, although
elements of it could be. What a decentralized
swarm might sacrice in terms of optimality, it
could buy back in faster speed of reaction. And
swarms that communicate indirectly through stig-
mergy or co-observation, like ocks or herds, are
immune to direct communication jamming.
88
Hordes of simple, autonomous agents operating
cooperatively under a centralized commander’s
intent but decentralized execution can be devil-
ishly hard to defeat. e scattered airdrop of

|
39
SWARM COMMANDANDCONTROL MODELS
Centralized Coordination
Swarm elements communicate with a centralized
planner which coordinates all tasks.
Hierarchical Coordination
Swarm elements are controlled by “squad” level
agents, who are in turn controlled by higher-level
controllers.
Coordination by Consensus
All swarm elements communicate to one another
and use “voting” or auction-based methods to con-
verge on a solution.
Emergent Coordination
Coordination arises naturally by individual swarm
elements reacting to one another, like in animal
swarms.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
40
|
paratroopers over Normandy during the D-Day
invasion wrecked detailed Allied plans, but had
the unintended eect of making it nearly impos-
sible for Germans to counter the “little groups of
paratroopers” dispersed around, behind and inside
their formations. Simple guidance like “run to the
sounds of gunre and shoot anyone not dressed
like you” can be eective methods of conveying
commander’s intent, while leaving the door open
to adaptive solutions based on situations on the
ground. e downside to an entirely decentralized
swarm is that it could be more dicult to control,
since specic actions would not necessarily be
predictable in advance.
COMMANDANDCONTROL MODELS MUST
BALANCE COMPETING OBJECTIVES
Choices about command-and-control models for
swarms may therefore depend upon the balance
of competing desired attributes, such as speed of
reaction, optimality, predictability, robustness to
disruption and communications vulnerability.
e optimal command-and-control model for any
given situation will depend on a variety of factors,
including:
• Level of intelligence of swarm elements relative
to complexity of the tasks being performed;
• Amount of information known about the task
and environment before the mission begins;
• Degree to which the environment changes
during the mission, or even the mission itself
changes;
• Speed of reaction required to adapt to changing
events or threats;
• Extent to which cooperation among swarm ele-
ments is required in order to accomplish the task;
• Connectivity, both among swarm elements and
between the swarm and human controllers, in
terms of bandwidth, latency and reliability; and
• Risk, in terms of both probability and conse-
quences, of suboptimal solutions or outright failure.
e best swarm would be able to adapt its
command-and-control paradigm to chang-
ing circumstances on the ground, such as using
bandwidth when it is available but adapting to
decentralized decision-making when it is not. In
addition, the command-and-control model could
change during dierent phases of an operation,
and dierent models could be used for certain
types of decisions.
HUMAN CONTROL CAN TAKE MANY FORMS
Human control over a swarm can take many
forms. Human commanders might develop a
detailed plan and then put a swarm into action,
allowing it to adapt to changing circumstances
on the ground. Alternatively, human command-
ers might establish only higher-level tasks, such
as “nd enemy targets,” and allow the swarm to
determine the optimal solution through central-
ized or decentralized coordination. Or human
controllers might simply change swarm goals or
agent preferences to induce certain behaviors. If
the cognitive load of controlling a swarm exceeds
that of one person, human tasks could be split up
by breaking a swarm into smaller elements or by
dividing tasks based on function. For example,
one human controller could monitor the health of
vehicles, with another setting high-level goals and
yet another approving specic high-risk actions,
like use of force.
Ultimately, a mix of control mechanisms may be
desirable, with dierent models used for dier-
ent tasks or situations. For example, researchers
exploring the use of intelligent agents for real-time
strategy games developed a hierarchical model of
multiple centralized control agents. Squad-based
agents controlled tactics and coordination between
individual elements. Operational-level agents
controlled the maneuver and tasking of multiple
squads. And strategy-level agents controlled over-
arching game planning, such as when to attack.
89
In principle, cooperation at each of these levels
could be performed via dierent models in terms
|
41
of centralized vs. decentralized decision-making or
human vs. machine control. For example, tacti-
cal coordination could be performed through
emergent coordination; centralized agents could
perform operational-level coordination; and
human controllers could make higher-level strate-
gic decisions.
In order to optimize their use of swarms, human
controllers will need training to understand the
behavior and limits of swarm automation in real-
world environments, particularly if the swarm
exhibits emergent behaviors. Human controllers
will need to know when to intervene to correct
autonomous systems, and when such intervention
will introduce suboptimal outcomes.
90
Basic research on robotic swarms is underway
in academia, government and industry. In addi-
tion to better understanding swarming behavior
itself, more research is needed on human-machine
integration with swarms. How does one convey to
human operators the state of a swarm simply and
without cognitive overload? What information is
critical for human operators and what is irrelevant?
What are the controls or orders humans might
give to a swarm? For example, a human controller
might direct a swarm to disperse, coalesce, encir-
cle, attack, evade, etc.
91
Or a human might control
a swarm simply by using simulated “pheromones”
on the battleeld, for example by making targets
attractive and threats repellent.
92
To harness the
power of swarms, militaries will not only need to
experiment and develop new technology, but also
ultimately modify training, doctrine and organi-
zational structures to adapt to a new technological
paradigm.
To harness the power of
swarms, militaries will not
only need to experiment
and develop new technology,
but also ultimately modify
training, doctrine and
organizational structures to
adapt to a new technological
paradigm.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
42
|
VII. ENEMY SWARMS
AND COUNTERMEASURES
Many of the game-changing innovations that
enable swarming – low-cost uninhabited systems,
autonomy and networking – are driven by com-
mercial sector, not military, innovation. ey will
be widely available to a range of actors, and many
states and non-state groups may be more eager
to embrace them than the U.S. military, which is
invested heavily in current operational paradigms.
Strategists should not be deceived by the apparent
lack of sophistication of the cheap drones cur-
rently in the hands of non-state groups like Hamas,
Hezbollah or the Islamic State of Iraq and Syria.
Fully autonomous GPS-programmable drones can
be purchased online today for only a few hundred
dollars. Large numbers of them could be used to
eld an autonomous, jam-proof swarm carrying
explosives or even crude chemical or biological
agents. Just as cheap improvised explosive devices
wreaked havoc on U.S. forces operating in Iraq and
Afghanistan, low-cost drones could similarly be
extremely disruptive and cost-imposing. U.S. forces
must begin to think now about how to counter
these threats and in cost-eective ways.
Reversing the Cost Equation
It is not enough merely to nd a way to destroy an
enemy’s drone; it must be done in a cost-eective
manner. If taking out a $1,000 enemy drone
requires a $1 million missile, then every drone shot
down is a win for the enemy, because it imposes
tremendous costs on the defender.
LOW COSTPERSHOT WEAPONS
Developing low cost-per-shot weapons will be criti-
cal to countering enemy swarms. ese consist of
exotic technologies like lasers and electromagnetic
rail guns as well as more traditional technolo-
gies like machine guns. e Navy is currently
developing laser weapons and rail guns , and will
test a laser weapon at sea in 2014 and a rail gun at
sea in 2016.
93
Lasers and rail guns are appealing
counter-swarm weapons because they are electri-
cally powered and therefore have relatively low
costs for each shot – signicantly lower than a
missile – assuming the power sources are avail-
able. e Navy has already demonstrated the
ability of a laser to shoot down an enemy drone,
although defeating an entire swarm of drones is
a more signicant challenge. Machine guns, like
the sea-based Phalanx and land-based counter-
rocket, artillery and mortar (C-RAM) system are
also eective at defeating incoming projectiles
or drones at low cost. High-energy lasers, if they
could be operationalized successfully, would have
even longer range.
COUNTERSWARM
One method of taking out a swarm could be
with another swarm. As long as the counter-
swarm was cheaper and/or more eective than
the enemy swarm, it could be a relatively low-cost
way to defend against enemy swarm attacks. e
Naval Postgraduate School is currently research-
ing swarm-on-swarm warfare tactics, with the
intent of testing a 50-on-50 aerial swarm ght.
94
Basic research in swarming tactics will be critical,
as winning in swarm combat may depend upon
having the best algorithms to enable better coor-
dination and faster reaction times, rather than
simply the best platforms.
ELECTRONIC ATTACKS
Electronic warfare countermeasures, such as spoof-
ing, jamming, cyber-weapons and high-powered
microwaves are particularly attractive for counter-
ing swarms since they can, in theory, be applied
over a wide area without requiring one to target
individual swarm elements. If a swarm relies on
communications for its coordination, then jam-
ming or cyber attacks could be quite eective
if they disrupted communications and forced
swarm elements to ght individually, devolving
a swarm ght into a melee. Spoong attacks that

|
43
trick a swarm with false data or cyber attacks
that potentially even take control of a swarm are
also appealing ways to counter large numbers of
systems.
Uninhabited systems are not uniquely susceptible
to electronic warfare, cyber attacks and spoof-
ing, but the consequences of some types of attacks
could be greater in some cases.
95
Because machine
cognition lacks the “common sense” capabilities
of a human, there is a higher risk that the system
might fail badly if manipulated with false data.
Whereas humans can adjust and adapt to new and
unanticipated situations, machines can be “brittle”
if presented with situations for which they were not
programmed, leading to unpredictable outcomes.
Counter-countermeasures
e dicultly in tricking a person with false data
points to one possible safeguard against spoong
or cyber attacks.
96
Maintaining a human “in the
loop” – not for every swarm action but for particu-
larly high-risk ones, such as target authorization
– is one potential fail-safe. By building in “human
rebreaks” within a swarm’s decision-cycle,
militaries can ensure that even if an adversary
were to be able to insert false data, there would be
limits to what the swarm could do without human
approval.
97
While humans are not incapable of
mistakes, a human rewall would ensure that there
was at least a common sense check before authoriz-
ing high-risk swarm actions.
98
At the very least, a
human rewall would ensure that in order for an
adversary to take control of a swarm, the enemy
would have to actually exercise some direct human
control and replicate the human control interfaces,
not merely insert malicious code.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
44
|
VIII. CONCLUSION: BUILDING
THE SWARM
A New Paradigm for Technological
Superiority
We need not wait until 2054 when the Department
of Defense will only have sucient dollars to fund
one aircra, split between the Air Force, Navy
and Marine Corps, for Augustine’s Law of rising
costs to take its toll. e crisis in rising costs and
shrinking quantities that Norm Augustine warned
about is here today. Quantities for next-generation
systems are so low that even dramatic qualitative
advantages over adversaries, on the order of 27-to-
1, are not sucient to overcome the challenges
inherent in projecting power at long range and
with limited numbers of assets. e solution is not
to stop modernizing, however, or to retain legacy
force structure at the expense of higher-quality sys-
tems. Instead, we need a new paradigm that allows
the United States to eld high quality systems and
in large quantities. And this strategy must work
in the midst of a constrained scal environment.
Accommodating rising costs through massive
growth in the defense budget in perpetuity is nei-
ther feasible nor responsible.
Distributing functionality from single, exquisite
multi-mission systems to large numbers of lower
cost, less complex systems is one approach to help
address this problem. Because uninhabited sys-
tems have no person on board, survivability can
be balanced against cost, replacing the concept of
platform survivability with swarm resiliency. Large
numbers of systems can be built to be attritable.
If some are destroyed, the remainder can carry
on the mission, allowing graceful degradation of
combat capability rather than risk the catastrophic
loss of a single expensive platform. A large number
of diverse assets also imposes costs on adversaries,
dramatically expanding the number and diversity
of the targets they must strike, and enhances resil-
iency by avoiding monocultures.
Perhaps most importantly, because they would be
less complex than exquisite multi-mission sys-
tems, adopting a distributed approach could begin
to reign in rising costs. Increasing complexity of
systems and, in particular, shiing requirements is
a major factor behind ever-rising platform costs.
99
is need not be the case, however. Many com-
mercial technologies, including computers and
automobiles, are as complex as modern weapon
systems in terms of numbers of parts and lines of
code, and yet do not face the same challenge of
exponentially rising costs.
100
Economies of scale
are a factor – another advantage of adopting a
cheap-and-many approach – but development
timelines are also a major contributor to the
problem. DOD frequently develops major weapon
systems on twenty or thirty year timelines, which
creates perverse incentives to generate unrealistic
requirements based on unproven technology. Long
development timelines also virtually guarantee
that requirements will change over time as adver-
sary capabilities evolve, which further increases
costs. In the worst cases, even with shiing
requirements, platforms are unable to keep pace
with adversary or commercial sector innovation
and risk being obsolete before they are even elded.
A smarter approach would be to break down
exquisite systems into smaller components. One
typical way in which this is done is to disaggre-
gate modernization across time, building modular
platforms with incremental improvements in each
procurement “block” over time.
101
With only mar-
ginal changes between each “block,” this approach
reduces technology risk and, as a consequence,
cost. Another approach would be to disaggregate
a system spatially into many components, adopt-
ing a family-of-systems approach. is would
consist of a number of single-mission systems
working together to accomplish a task, rather than
a single exquisite multi-mission system. Because
single-mission systems would be less complex than
multi-mission systems, they could be produced

|
45
with lower technology risk and at lower cost. In
addition, provided that network architectures are
designed with sucient interoperability up front,
such an approach is inherently modular. Concerns
about size, weight and power that traditionally
bedevil modular design approaches no longer
matter when combat functions are disaggregated
spatially among many platforms. Provided they
can plug into the network, new systems are inher-
ently “plug and play.”
Disaggregating complex multi-mission systems
into a family of lower-cost single-mission sys-
tems has not been particularly appealing to date
since, without automation, human operators were
ultimately needed to control them, either physi-
cally onboard the platform or remotely. People
cost money, and rising personnel costs have placed
steady downward pressure on end-strength for all
of the military Services. In a world where Services
envision having fewer aircra, ships and ground
vehicles because they have fewer people to control
them, highly capable multi-mission systems make
sense.
Autonomous uninhabited systems oer the poten-
tial for a dierent approach. ey can be used
to augment existing human-inhabited systems,
putting additional sensors and missiles into the
ght at relatively low cost. e onboard automation
need not be intelligent enough to replace human
operators entirely, but need merely be sucient
to reduce the cognitive load for a human supervi-
sor such that he or she can control many vehicles
at one time. is breaks the current relationship
between people and platforms, and allows a force
small in personnel to eld and control a very large
force in platforms. Some human-inhabited plat-
forms may be needed forward in the battlespace for
various functions, including to “quarterback” the
ght. ere also may be little benet to removing
humans from very large and expensive systems like
ships or bombers. But augmenting these human-
inhabited assets with larger numbers of lower cost
uninhabited systems may dramatically increase
the ability of those humans to accomplish their
mission.
Human-Machine Teaming
e Army’s manned-unmanned teaming concept
for its aviation assets is an instructive example
of this approach. e Army’s recent decision to
retire its aging Kiowa armed reconnaissance
helicopter without a replacement allowed the
Army to adopt an alternative approach: teaming
the human-inhabited AH-64 Apache helicopters
with its uninhabited MQ-1C Gray Eagle aircra.
e uninhabited Gray Eagles do not on their own
replace every task the Kiowa once performed,
but in aggregate the Gray Eagles and Apaches
do. Not only is this approach less expensive, it
also enables new concepts of operation, since
Gray Eagles can be sent forward to undertake
more dangerous missions without risking human
lives. Gray Eagles also incorporate a high degree
of automation, which reduces the human task
loading for simple missions. As a result, the Gray
Eagle can even be controlled directly from the
Apache’s cockpit.
In this model, human-inhabited and uninhab-
ited systems are both leveraged for their relative
strengths, as are human and machine cognition
and automation. is is not to say that unin-
habited and autonomous systems are without
signicant limitations. An uninhabited vehicle is
a poor choice for demonstrating political will to
an adversary, when one wishes to show the resolve
to suer and die for a piece of terrain. Removing
a person from a vehicle also means removing the
most advanced information processing system
on the planet – the human brain – and placing it
at another location. Cognition for uninhabited
systems depends instead on some combination of
onboard autonomy and a communications link to
ooard human controllers, both of which have
limitations. Communications can be disrupted
and degraded, and even under the best conditions

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
46
|
bandwidth today is insucient to convey all of
the sensory information a person can take in
when physically present. Machine intelligence has
limitations as well. While machines exceed human
cognitive capacities in some areas, particularly
speed, they lack robust general intelligence that is
exible across a range of situations. Some deci-
sions, particularly those requiring judgment or
creativity, will be inappropriate for autonomous
systems. ose who can eld a mix of human and
machine abilities, maximizing the advantages of
both, will be best suited to capitalize on the poten-
tial of the robotics revolution.
As uninhabited systems become increasingly
autonomous, this balance of tasks will shi over
time. In some cases, trusting automation will
be dicult. Humans may be unwilling to cede
control for some tasks over to machines. Debates
over autonomous cars are an instructive example.
Human beings are horrible drivers, killing more
than thirty thousand people a year in the United
States alone, or roughly the equivalent of a 9/11
attack every month. Self-driving cars, on the other
hand, have already driven nearly three quarters of
a million miles, including in crowded city streets,
without a single accident.
102
Autonomous cars have
the potential to save literally tens of thousands of
lives every year, yet rather than rushing to put self-
driving cars on the streets as quickly as possible,
adoption is moving forward cautiously.
103
At the
state of the technology today, even if autonomous
cars are far better than human drivers overall,
there would inevitably be situations where the
autonomy fails and humans, who are better at
adapting to novel and ambiguous circumstances,
would have done better in that instance.
104
Even
if, in aggregate, thousands of lives could be saved
with more autonomy, humans tend to focus on
the few instances where the autonomy could fail
and humans would have performed better. Ceding
human control to automation requires trust, which
is not easily given.
Increased autonomy can run into similar obstacles
in military contexts, especially when cultural
issues related to identity compound the issue.
While Army uninhabited aircra incorporate a
high degree of automation, equivalent Air Force
aircra do not, even though they are built by the
same contractor. In fact, Air Force MQ-9 Reapers
do not include automated takeo and landing
functionality, even though the vast majority of
MQ-9 accidents occur on takeo and landing.
105
Automating takeo and landing would require
ceding control, however, changing the relation-
ship of the human controller to the aircra. For
Army soldiers, who see uninhabited aircra as just
another piece of equipment, ceding control is not
problematic. In the Air Force, however, piloting is
central to the collective sense of identity. Tellingly,
the Air Force insists upon identifying uninhabited
aircra as “remotely piloted,” even applying this
term to future aircra which, in principle, ought
to have a high degree of automation.
106
Conversely,
not only does the Army refer to its uninhabited
aircra as “unmanned aircra systems,” the
people controlling them are called “operators,”
not pilots.
107
Terminology aside, the paradigm
that equates “piloting” to direct physical control of
the aircra, rather than human supervision and
mission command, leads to resistance to automa-
tion that could prevent accidents and increase
eciencies.
Culture matters, both to individuals and orga-
nizations. It cannot be blithely swept aside, but
nor can it be accepted when it hinders necessary
change. When existing cultural paradigms prevent
the adoption of new approaches that could have
game-changing results on the battleeld, change is
required. Cultures must adapt. e Army cavalry
is a ne example in this regard. While tanks and
motorized ghting vehicles have long replaced
horses in modern combat, the cavalry ethos lives
on in Army “cavalry” units today. Cavalry sol-
diers honor their heritage with Stetsons and tall

|
47
boots for dress uniforms. New cavalry soldiers
must “earn their spurs.” But the denition of
what it means to be a cavalry soldier has evolved.
Similarly, the denition of what it means to be a
“pilot” will change over time. e signicance of
physically controlling an aircra by stick and rud-
der will fade, to be replaced with greater emphasis
on areas where human cognition is still needed,
such as mission-level command and decisions over
the use of force.
While pilots may be the rst to grapple with this
paradigm shi, autonomous systems will raise the
same issues across many military positions, from
truck drivers to tank commanders. As uninhabited
and autonomous systems are increasingly intro-
duced into the force, the skills that we require of
military personnel may change. Physical prowess
for some tasks, like piloting an aircra, driving a
vehicle or ring a rie will be less important in a
world where aircra y themselves, vehicles drive
on their own and smart ries correct for wind,
humidity, elevation and the shooter’s movements
all on their own. e cognitive skills that are most
in demand for humans will change as well, per-
haps in surprising ways. As machine intelligence
becomes increasingly capable, the tasks that are
required of humans will change, to include not
only the tasks that machines do poorly, but also
the supervision of complex autonomous systems in
combat.
108
is places new burdens on the selec-
tion, training and education of military personnel.
The Rapid Pace of Technological
Advancement
DOD will need to move swily to harness the
advantages of swarming if it is to retain its current
fragile lead in military robotics.
109
e technology
that enables swarming is generally not new plat-
forms, vehicles or munitions, but rather improved
autonomy for existing hardware. For some appli-
cations, such as swarming boats, the degree of
autonomy required to enable swarming exists
today. For others, improved autonomy is needed,
and the gulf between what is possible today and
what is needed for some applications can be quite
large. However, the underlying technologies that
enable more advanced autonomy, such as improved
computer processing power, are advancing at an
exponential rate. As a result, many information-
based technologies that may have seemed like
science ction only a few years ago, like “smart”
glasses and watches, self-driving cars or bionic
exoskeletons, exist today.
110
e rate of their dif-
fusion into our highways, homes and businesses
is a product of price, business models, market
availability and legal and policy issues, but the
capabilities exist today.
Likewise, the ability to eld fully autonomous,
cooperative vehicles and munitions may be real-
ized sooner than anticipated. Many swarming
applications have already been demonstrated in
simple form. Beyond the military domain, there
are strong commercial incentives for invest-
ments in cooperative robotic systems, given their
potential to develop solutions for area coverage,
self-healing networks, optimal transport and other
tasks. DOD may have to import into the defense
sector swarm algorithms rst developed for non-
defense applications, reversing the traditional
paradigm of DOD exporting advanced technology
into the commercial space.
111
Whether the U.S. military successfully capitalizes
on swarming’s potential will depend upon bureau-
cracy and culture. To tap into commercial sector
innovation in robotics, DOD will need to lower the
barriers to entry that currently exist for non-tradi-
tional defense companies and make itself a more
attractive customer, or risk freezing itself out of an
important market. DOD’s sluggish requirements
and acquisition process is also a strategic risk.
If DOD continues to develop “next-generation”
weapon systems on thirty-year timelines, it will be
hard-pressed to maintain the most cutting-edge
computer hardware and soware.
112
Shorter acqui-
sition timelines and more modular system designs

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
48
|
are needed. e cultural lens through which tech-
nology is viewed also matters. When acquisition
challenges are combined with a desire to “go slow”
in areas where automation raises uncomfortable
cultural issues, the U.S. military may nd itself at
risk of falling behind.
The Human Element
Cultural resistance to robotic systems oen stems
from a perception that they are replacing humans,
and terminology that refers to robotic systems as
“unmanned” can feed this perception. e reality,
however, is a future of human-machine teaming.
Many of the tasks humans perform in warfare will
change, but humans will remain central to war,
for good or ill. e introduction of increasingly
capable uninhabited and autonomous systems on
the battleeld will not lead to bloodless wars of
robots ghting robots, with humans sitting safely
on the sidelines. Death and violence will remain
an inescapable component of war, if for no other
reason than that it will require real human costs
for wars to come to an end. Nor will humans be
removed from the battleeld entirely, telecom-
muting to combat from thousands of miles away.
Remote operations will have a role, as they already
do in uninhabited aircra operations today, but
humans will be needed forward in the battlespace,
particularly for command-and-control when long-
range communications are degraded.
Even as uninhabited and autonomous systems
play an increasing role on the battleeld, it is still
humans who will ght wars, only with dierent
weapons. Combatants are people, not machines.
Technology will aid humans in ghting, as it has
since the invention of the sling, the spear and
the bow and arrow. Better technology can give
combatants an edge in terms of stando, surviv-
ability or lethality, advantages that combatants
have sought since the rst time a human picked
up a club to extend his reach against an enemy.
But technology alone is nothing without insight
into the new uses it unlocks. e tank, radio and
airplane were critical components of the blitz-
krieg, but the blitzkrieg also required doctrine,
organization, concepts of operation, experimenta-
tion and training to be developed successfully. It
was people who developed those concepts, who
draed requirements for the technology, who
restructured organizations and rewrote doctrine
and who ultimately fought. In the future, it will
be no dierent.
War will remain a clash of wills. To the extent that
uninhabited systems allow an actor to reduce the
costs of war, they can be a major advantage. ose
who master a new technology and its associated
concepts of operation rst can gain game-changing
advantages on the battleeld, allowing decisive
victory over those who lag behind. But techno-
logical innovation in war can be a double-edged
sword. If this advantage erodes a nation’s willing-
ness to face squarely face the burden of war, it can
be a detriment. e illusion that such advantages
can lead to quick, easy wars can be seductive,
however, and those who succumb to it may nd
their illusions shattered by the unpleasant and
bloody realities of war.
113
Uninhabited systems
can lead to greater stando from the enemy, but
the millennia-long evolution of weapons and
countermeasures suggests that such weapons will
proliferate: no innovation leaves its user invulner-
able for very long. Similarly, automation has the
potential to accelerate the pace of warfare, but not
necessarily in ways that are conducive to the cause
of peace. An accelerated tempo of operations may
lead to combat that is more chaotic, but not more
It is still humans who will
ght wars, only with dierent
weapons.

|
49
controllable. Wars that start quickly may not end
quickly.
Uninhabited and autonomous systems raise chal-
lenging operational, strategic and policy issues, the
full scope of which cannot yet be seen. e nations
and militaries that see furthest into the future to
anticipate these challenges and prepare for them
now will be best poised to succeed in the warght-
ing regime to come.
Conclusion
e past decade of conict has seen the intro-
duction of uninhabited systems in warfare in
important ways, saving lives and money, but their
use has to-date been conned largely to niche
roles. is is merely the precursor to a larger shi
in warfare where large numbers of autonomous
uninhabited systems play signicant roles on the
battleeld.
Autonomous and uninhabited systems have
the potential to give tremendous advantages to
actors who gure out how best to employ them.
As detailed in “Robotics on the Battleeld Part
I: Range, Persistence and Daring,” uninhabited
systems can operate with longer endurance and
therefore greater range and persistence. is is
particularly important in countering anti-access
threats where long-range missiles threaten U.S.
ships and bases. Uninhabited systems can also
enable more daring concepts of operation, allowing
commanders to take risks with uninhabited assets
that they would not with human-inhabited ones.
Large numbers of uninhabited systems can
bring greater mass onto the battleeld, and with
it greater resiliency and diversity. Cooperative,
autonomous systems can operate as self-healing
networks and self-coordinate to adapt to events as
they unfold. And automation can accelerate the
pace of battle, compressing decision cycles and
constantly altering the adversary’s threat picture
before he can respond.
For actors who are able to harness the advantages
of uninhabited and autonomous systems, their
forces will be able to operate with greater:
• Range and persistence
• Daring
• Mass
• Coordination and intelligence
• Speed
In aggregate, these advantages will lead to the evo-
lution from today’s reconnaissance-strike networks
to tomorrow’s reconnaissance-strike swarm.
Perhaps most signicantly, the underlying technol-
ogy that will enable these innovations does not
stem from secret U.S. defense labs, but in many
cases will be widely available. Moreover, much
of the technology that will enable autonomous
operations and swarming is better algorithms and
soware, not necessarily new platforms. ere is
an urgent need to innovate faster than adversaries,
and to discover the best ways of employing swarms
rst. To do so, the United States must invest in a
robust plan of experimentation, prototyping, and
iterative concept and technology development.
Where these technologies raise challenging policy
concerns, such as increased automation in the use
of force or human cognitive performance enhance-
ment to keep pace with faster machines, the United
States should grapple forthrightly with the issues
and cra sensible policy guidelines to guide tech-
nological development.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
50
|
IX. RECOMMENDATIONS
Elements of the Department of Defense are
conducting experiments on swarms and other
applications of uninhabited and autonomous
systems, but DOD currently lacks a comprehensive
plan to take full advantage of their potential.
Developing the technology alone is not sucient,
as the truly game-changing innovations come from
the ways in which a new technology is ultimately
used. e best path forward for developing these
applications is an iterative process of experimenta-
tion with new technologies and concepts, which
then informs further technology development.
Simulations can be useful, but concepts of opera-
tion ultimately must be tested in the eld. Actual
experimentation with real users also can solicit
new ideas, as well as feedback on what avenues
for research are promising, or where a concept or
technology does not work well.
e chief stumbling block in DOD is the “val-
ley of death” between cutting edge research and
development and formal programs of record.
rough organizations like the Defense Advanced
Research Projects Agency (DARPA), Oce of
Naval Research (ONR) and other labs, DOD does
an excellent job of undertaking high-risk / high-
reward proof of concept research. Transitioning
new, promising concepts to actual funded
DOD programs, however, is uneven at best.
Experimentation and technology development can
help bridge the gap by clarifying what is possible,
what is promising and what is not.
To sustain the U.S. military’s current, but fragile,
lead in robotics:
The Oce of the Secretary of Defense
should:
• Undertake a study on total lifecycle costs for
uninhabited systems, including the potential for
automation to reduce costs by reducing the need
to train operators to physically control vehicles.
e study should focus particular attention on
aircra, where pilot training costs run high.
• Undertake a study on swarming platforms to
examine the potential for low-cost uninhabited
systems to impose costs on adversaries. e study
should include an evaluation of platform surviv-
ability, total cost, amount of vehicles elded per
dollar and costs to adversaries to respond.
• Investigate the potential for uninhabited systems
to increase resiliency and reduce costs by disag-
gregating complex systems into a larger number
of smaller, simpler systems.
• Ensure future military systems are built with
modular designs and open architectures to allow
upgrades and plug-and-play interoperability into
a family of systems.
• Fund a multi-year series of experiments in coop-
erative multi-vehicle control and swarming.
• Establish a Defense Robotics Systems Oce,
directly reporting to the Deputy Secretary of
Defense, to coordinate ongoing eorts on unin-
habited systems across the Department.
114
• Undertake a comprehensive policy review of
human cognitive performance enhancement
technologies.
• Continue to lead in international discussions on
autonomy in weapon systems.
The Joint Sta should:
• Ensure requirements for all new programs are
written so as not to exclude uninhabited or
autonomous solutions or partial solutions as part
of a family of systems.
• Include cost – and not only platform costs but
also total lifecycle costs – as a factor in balancing
new program requirements.
• Ensure that lessons learned from experiments
regarding uninhabited and autonomous sys-
tems are centrally collected and widely shared
throughout the Department.

|
51
The Navy should:
• Build an experimental prototype of an unin-
habited missile barge that can demonstrate the
ability to remotely control and launch missiles
from a large uninhabited vessel.
• Build a proof-of-concept demonstration of an
undersea payload module to exploit U.S. sanctu-
ary undersea.
• Move aggressively to eld autonomous swarming
defensive boats to protect U.S. ships from enemy
fast attack cra. is should include further
experimentation to rene concepts of operation,
a rapid elding initiative to equip combatants in
high-risk areas like the Straits of Hormuz and a
program of record for outtting all Navy surface
combatants with optionally-manned small boats
that can operate as a defensive swarm.
• Conduct a series of further experiments in multi-
domain swarms of air, surface and subsurface
vehicles for a variety of missions.
• Sustain development of low cost-per-shot coun-
ter-swarm weapons such as high-energy lasers
and electromagnetic rail guns.
The Air Force should:
• Investigate the potential for low-cost swarming
uninhabited air vehicles, including expendable
or non-recoverable systems such as missiles
or decoys, to conduct a variety of missions
including suppression/destruction of enemy air
defenses, reconnaissance, battle damage assess-
ment and electronic warfare.
• Conduct an analysis of alternatives of lower-
cost uninhabited aircra to supplement existing
manned aircra with additional sensors and
missiles, such as an uninhabited “missile truck.”
• Fund development of improved multi-aircra
control interfaces for existing uninhabited
aircra.
• Conduct a series of experiments in human con-
trol over large numbers of swarming air vehicles.
The Army and Marine Corps should:
• Develop a concept of operations for using appli-
qué kits for ground convoy operations and an
associated program of record.
• Conduct a series of modern day “Louisiana
Maneuver” experiments on “robotic wingman”
ground robots for long-range scouting and
maneuver operations, in order to inform further
technology development and requirements for an
eventual program of record.
• Conduct a series of experiments on swarm-
ing uninhabited air vehicles for persistent
surveillance, close air support, aerial resupply
and communications relay to support ground
maneuver forces.
• Include ground robotics as part of the set of pos-
sible solutions as part of a family of systems for
all future programs, such as a light airborne tank
or new ground combat vehicle.
The Marine Corps should:
• Conduct experiments on amphibious swarm-
ing robots for reconnaissance and counter-mine
operations to clear beaches ahead of an amphibi-
ous assault.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
52
|

|
53
ENDNOTES
1. Chuck Hagel, “Defense Innovation Days Opening Keynote,” (Southeastern
New England Defense Industry Alliance, Newport, September 3, 2014),
http://www.defense.gov/Speeches/Speech.aspx?SpeechID=1877. Deputy
Secretary of Defense Bob Work has also expounded on this issue: Bob Work,
“National Defense University Convocation,” (National Defense University,
Washington, August 5, 2014), http://www.defense.gov/speeches/speech.
aspx?speechid=1873.
2. T.X. Hammes has made a similar, and compelling, argument: T.X. Hammes,
“The Future of Warfare: Small, Many, Smart vs. Few and Exquisite?”
Warontherocks.com, July 16, 2014, http://warontherocks.com/2014/07/
the-future-of-warfare-small-many-smart-vs-few-exquisite/#_).
3. Department of Defense, “Air-Sea Battle: Service Collaboration to Address
Anti-Access and Area Denial Challenges,” (Air-Sea Battle Oce, May 2013).
4. Paul Scharre, “Robotics on the Battleeld – Part One: Range,
Persistence and Daring,” (Center for a New American Security, May
2013), http://www.cnas.org/sites/default/les/publications-pdf/CNAS_
RoboticsOnTheBattleeld_Scharre.pdf.
5. David Klein, “US Department of Defense 2015 Budget Analysis,” Auvsi.org,
May 2, 2014, http://www.auvsi.org/Mississippi/blogs/david-klein/2014/05/02/
us-department-of-defense-2015-budget-analysis.
6. Paul Scharre, “How to Lose the Robotics Revolution,” Warontherocks.com,
July 29, 2014, http://warontherocks.com/2014/07/how-to-lose-the-robotics-
revolution.
7. Michael C. Horowitz, “The Looming Robotics Gap,” ForeignPolicy.
com, May 5, 2014, http://www.foreignpolicy.com/articles/2014/05/05/
the_looming_robotics_gap_us_military_technology_dominance.
8. Robert O. Work and Shawn Brimley, “20YY: Preparing for War in the Robotic
Age” (Center for a New American Security, January 2014), 10-19, http://www.
cnas.org/20YY-Preparing-War-in-Robotic-Age; Barry Watts, “The Evolution
of Precision Strike” (Center for Strategic and Budgetary Assessments, August
2013), http://www.csbaonline.org/publications/2013/08/the-evolution-of-
precision-strike/; Barry Watts, “Six Decades of Guided Munitions and Battle
Networks: Progress and Prospects” (Center for Strategic and Budgetary
Assessments, March 2007), http://www.csbaonline.org/publications/2007/03/
six-decades-of-guided-munitions-and-battle-networks-progress-and-
prospects/; and Wayne P. Hughes Jr., Fleet Tactics and Coastal Combat
(Annapolis, MD: Naval Institute Press, 2000), 285.
9. Paul Kennedy, The Rise and Fall of Great Powers (New York: Random House,
1987), 353-354.
10. The standard metric for weighing the value of quantitative advantages of
aimed-re weapons is Lanchester’s Square Law, which states that the military
advantage of increased numbers increases with the square of the combat
ratio. So, for example, a two-fold superiority in numbers actually translates
to a four-fold military advantage. This is because aimed-re weapons can
focus their attacks, bringing all repower to bear at the same time. This is in
contrast with the linear-scaling advantage in additional numbers in an era
of hand-to-hand combat, where phalanxes of ghters could only engage one
person at a time. Under Lanchester’s Square Law, German tanks would have
had to have been nine times better than Allied tanks to compensate for their
three-fold numerical disadvantage.
11. Kennedy, The Rise and Fall of Great Powers, 356.
12. William J. Perry, “Technology and National Security: Risks and
Responsibilities,” April 7-8, 2003, http://stanford.edu/dept/france-stanford/
Conferences/Risk/Perry.pdf.
13. The United States suered 148 battle deaths during the war with 210
coalition partners killed. See Patrick Cooper, “Coalition deaths fewer than
in 1991,” CNN.com, June 25, 2003, http://www.cnn.com/2003/WORLD/
meast/04/17/sprj.irq.casualties/. Estimates of Iraqi military casualties vary
wildly, from roughly 1,000 to over 100,000. For a brief overview of the range
of estimates and associated debate, see Jack Kelly, “Estimates of deaths in rst
war still in dispute,” Post-Gazette, February 16, 2003, http://old.post-gazette.
com/nation/20030216casualty0216p5.asp. For the purposes of calculating
casualty ratios, we estimate 12,000 Iraqi military killed based on the Gulf War
Air Power Survey, yielding a ratio of approximately 33:1. Thomas A. Keaney
and Eliot A. Cohen, “Gulf War Air Power Survey Summary Report,” Washington,
DC 1993, 249, http://www.afhso.af.mil/shared/media/document/AFD-100927-
061.pdf.
14. Tom Clancy and Chuck Horner, Every Man a Tiger (New York: Berkley Books,
1999), 499-500.
15. Department of Defense, “Air-Sea Battle: Service Collaboration to Address
Anti-Access and Area Denial Challenges.”
16. John Stillion and Scott Perdue, Air Combat Past, Present, and Future,
RAND Corporation, August 2008, http://www.docstoc.com/docs/42891479/
Air-Combat-Past-Present-and-Future. The study generated a signicant deal
of controversy, not necessarily for the numerical analysis outlined here but
because of derogatory statements in the brief about the performance of the
F-35 Joint Strike Fighter. Adding additional color, the study became associated
with the phrase that U.S. forces were “clubbed like baby seals.” Eventually,
RAND had to issue a clarication. Graham Warwick, “UPDATED: F-35 Criticisms
– RAND claries,” Aviation Week, September 25, 2008.
17. This scenario obviously includes a number of assumptions, some of which
are questionable and some of which are clearly unrealistic, but used to
simplify the analysis. It assumes that Chinese ghters do not turn and run,
even after suering heavy losses. It ignores any possible dogghting kills by
F-22s using guns against Chinese ghters (the F-22 has superior stealth and
maneuverability). And it assumes that U.S. tankers and surveillance aircraft
do not begin to ee immediately when Chinese ghters are seen. The analysis
also assumes, however, that U.S. missiles have a probability of kill (Pk) of 1.0
and Chinese missiles have a Pk of 0. More reasonable Pk assumptions would
tilt the simulated ght further in China’s favor.
18. DARPA, “Joint Unmanned Combat Air Systems,” http://archive.darpa.
mil/j-ucas/index.htm.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
54
|
19. Norman R. Augustine, Augustine’s Laws (American Institute of Aeronautics,
1984).
20. U.S. Department of Defense, National Defense Budget Estimates for FY
2015, Table 2-1, http://comptroller.defense.gov/budgetmaterials.aspx.
21. International Institute for Strategic Studies, The Military Balance (2001)
and International Institute for Strategic Studies, The Military Balance (2008).
22. In the latter half of the twentieth century, shipbuilding costs rose on an
average annual basis by 7.4% for nuclear aircraft carriers, 9.8% for attack
submarines, 10.7% for surface combatants, and 10.8% for amphibious ships.
Mark V. Arena et al, Why Has the Cost of Navy Ships Risen? (Washington: The
RAND Corporation), 2006. For more insight on the sources behind cost growth
for aircraft, see Mark V. Arena et al, Why Has the Cost of Fixed-Wing Aircraft
Risen? (Washington: The RAND Corporation), 2008.
23. Lanchester’s Law is a very rough rule of thumb given for illustrative
purposes. In a precision-guided weapons exchange, models focusing on the
probability of kill are more accurate. Nevertheless, the overall point about
a limit on how much better quality can compensate for reduced quantity
remains valid.
24. David A. Shlapak et al., A Question of Balance (Washington: The RAND
Corporation), 2009, 65-67, t http://www.rand.org/pubs/monographs/MG888.html.
25. “Miniature Air Launched Decoy (MALD),” Raytheon.com, http://www.
raytheon.com/capabilities/products/mald/.
26. The MALD is air-deployable from a C-130 cargo plane. See “Miniature Air
Launched Decoy (MALD),” youtube.com, September 21, 2012, http://www.
youtube.com/watch?v=OmG5Q4i5R3s.
27. DARPA, “Network of unmanned undersea platforms would assist
manned vessels,” August 22, 2013, http://www.darpa.mil/NewsEvents/
Releases/2013/08/22a.aspx.
28. AeroVironment, “Switchblade,” https://www.avinc.com/uas/adc/
switchblade/.
29. Andrew Tarantola, “America’s kamikaze drone makes the skies
way less friendly,” Gizmodo, September 5, 2013, http://gizmodo.com/
americas-kamikaze-drone-makes-the-skies-way-less-frien-1227821895.
30. “US military bringing a switchblade to a gun ght,” Defense
Industry Daily, August 29, 2013, http://www.defenseindustrydaily.com/
us-army-brings-a-switchblade-to-a-gun-ght-07071/.
31. For example, see QinetiQ, “Robotic appliqué kit,” https://www.qinetiq-na.
com/products/unmanned-systems/robotic-controller-kit/.
32. FAS Military Analysis Network, “DDG-51 Arleigh Burke – class,” fas.org,
http://fas.org/man/DOD-101/sys/ship/ddg-51.htm.
33. Adam Leach, “Are Unmanned Cargo Ships on the Horizon?” Ship-
tTechnology.com, May 13, 2014, http://www.ship-technology.com/features/
featureare-unmanned-cargo-ships-on-the-horizon-4262804/.
34. Tamir Eshel, “US Navy Tests Rafael Spike Missiles on Unmanned
Vessels,” Defense-Update.com, October 31, 2012, http://defense-update.
com/20121031_us-navy-tests-rafael-spike-missiles-on-unmanned-vessels.
html.
35. “Missile barge program could swamp carriers,” Baltimore Sun,
3 September 1995, http://articles.baltimoresun.com/1995-09-03/
news/1995246035_1_cruise-missiles-carrier-warships. “Revisiting the arsenal
ship,” New Wars, October 6, 2007, http://newwars.blogspot.com/2007/10/
revisiting-arsenal-ship.html.
36. “Printing drones by the sheet (or how we get to tens of billions of drones
by 2020),” Global Guerrillas, February 16, 2012, http://globalguerrillas.
typepad.com/globalguerrillas/2012/02/printing-drones-by-the-sheet.html.
37. For reference, historical Pk values for various air-to-air missiles: AIM-7
(estimated pre-Vietnam) = 0.7; AIM-7 (actual in Vietnam) = 0.08; AIM-9
(estimated pre-Vietnam) = ~0.65; AIM-9 (actual in Vietnam) = 0.15; AIM-9L
(actual in Falklands) = 0.73 (19 kills for 26 missiles red); AIM-9M (actual in
Desert Storm) = 0.23 (11 kills for 48 missiles red); AIM-120 (actual to-date) =
~0.59 (10 kills for 17 missiles red in combat). Source: John Stillion and Scott
Perdue, Air Combat Past, Present, and Future, slides 19-28.
38. Total probability of a hit for a salvo is given by the following formula:
Probability of hit = 1 – (1 – Pk)^N where Pk is the probability of kill for a
single munition and N is the number of munitions red in a salvo.
39. Of course, reducing the number of Blue’s assets has some value for Red,
even if Red does not eliminate all of them. Partially reducing Blue’s salvo
reduces the likelihood of Red’s target being taken out, even if it does not
eliminate it entirely.
40. This is not the case for unguided munitions, for example in the case of
Hamas’ rocket attacks against Israel. Because Hamas uses unguided rockets,
Israel can calculate the rockets’ trajectory and determine which are likely
to strike populated areas, and therefore only target those that are threats.
Guided munitions that home in on targets move, however, considerably
complicating the problem of distinguishing which will miss.
41. This does not at all consider the critical question of “shot doctrine,” or how
many munitions Blue should shoot before stopping to assess whether the
target has been taken out and whether or not to shoot more munitions. In
an ideal scenario, one would have both the time and the means to “shoot-
look-shoot,” that is, re one munition, observe whether it has taken out the
target, and only re a second munition if it has not. This would maximize the
eectiveness of each munition and ensure that none were wasted against
already destroyed targets. In practice, time is a factor, as is the practical
matter of actually conducting a real-time battle damage assessment. In some
situations it is more advantageous to shoot two munitions, then observe, then
shoot again if necessary (shoot-shoot-look-shoot). Other combinations are
also possible. Suce to say, shot doctrine plays a signicant role.
42. Some researchers distinguish between “swarming” and “teaming,” only
using the term swarming to refer to cooperative behavior with large numbers
of agents and where the agents themselves are not particularly intelligent.
In this report, we use the term “swarming” to cover cooperative behavior
regardless of the number of agents or their degree of individual intelligence.

|
55
Rather, the term swarm is used to refer to cooperative behavior of a number
of individual agents where their cooperation leads to a whole greater than the
sum of its individual parts.
43. For a vivid illustration, see this video of a pack of wolves ghting a grizzly
bear over a kill, “Wild Kingdom – Wolves vs. Grizzly,” https://www.youtube.
com/watch?v=jY7Xmt4HzV0.
44. For an excellent overview of animal swarming, see Eric Bonabeau, Guy
Theraulaz, Marco Dorigo, Swarm Intelligence: From Natural to Articial
Systems (New York: Oxford University Press, 1999).
45. Matt Soniak, “3 sneaky chemical tricks used by animals,”
Mental_Floss, March 3, 2014, http://mentaloss.com/
article/55203/3-sneaky-chemical-tricks-used-animals.
46. Rumsaïs Blatrix, Claire Sermage, “Role of Early Experience in Ant
Enslavement: a Comparative Analysis of a Host and a Non-Host Species,”
FrontiersinZoology.com, August 2, 2005, http://www.frontiersinzoology.com/
content/2/1/13.
47. Howard Topo, Ellen Zimmerli, “Colony Takeover by a Socially Parasitic
Ant, Polyergus Breviceps: the Role of Chemicals Obtained During Host-Queen
Killing,” The British Journal of Animal Behaviour, 46 no. 3 (September 1993),
479-486.
48. “Swarmanoid: towards humanoid robotic swarms,” http://www.
swarmanoid.org/.
49. The natural world does have examples of direct cognitive hijacking, akin
to cyber attacks. The protozoan parasite toxoplasma gondii, or “toxo”, alters
the behavior of mice it infects by making them less afraid of cats. Once the
mice are eaten, toxo reproduces in the cat’s intestines and infects other mice
through cat feces. The “zombie ant” fungus ophiocordyceps unilateralis is
even more inventive. It infects ants’ brains and directs them to very specic
spots in the rain forest that are the optimal humidity and temperature for
fungal growth. The infected ants then climbs to the underside of a leaf of a
particular height o the ground on the northern side of the plant and bites
down. The ant’s jaws lock in place in a “death grip” and the ant dies. Then the
fungus grows stalks from the ant’s body, which it uses to rain down spores on
other ants passing by. Matt Simon, “Absurd Creature of the Week: The Zombie
Ant and the Fungus That Controls Its Mind,” wired.com, September 13, 2013,
http://www.wired.com/2013/09/absurd-creature-of-the-week-zombie-ant-
fungus/. For a delightful overview of some of the more colorful examples in
nature, see Ed Young, “Suicidal crickets, zombie roaches, and other parasite
tales,” TED, March 2014, http://www.ted.com/talks/ed_yong_suicidal_
wasps_zombie_roaches_and_other_tales_of_parasites#.
50. Hack a drone yourself using SkyJack freeware: Samy Kamkar, “Skyjack,”
samy.pl, December 2, 2013, http://samy.pl/skyjack/.
51. Sharing position data from inertial navigation systems among vehicles can
also modestly mitigate the problem of inertial navigation “drift” in accuracy
over time, although it does not solve the problem.
52. This need not be real-time supervision, of course.
53. For example, see “Self-Organizing Systems Research Group,” Harvard
University, http://www.eecs.harvard.edu/ssr/.
54. John Arquilla and David Ronfeldt, Swarming and the Future of Conict
(Santa Monica: The RAND Corporation, 2005), vii, http://www.rand.org/
content/dam/rand/pubs/documented_briengs/2005/RAND_DB311.pdf.
Some modern-day examples of swarming with human agents can be found
in the tactics of protestors and rioters, particularly when empowered with
information technology that allows them to rapidly communicate and
synchronize their actions. Bill Wasik, “#Riot: Self-Organized, Hyper-Networked
Revolts – Coming to a City Near You,” wired.com, December 16, 2011, http://
www.wired.com/2011/12/_riots/all/.
55. Arquilla and Ronfeldt, ibid, page vii.
56. Sean Edwards, Swarming and the Future of Warfare (Santa Monica: The
RAND Corporation, 2005), xvii, http://www.rand.org/content/dam/rand/pubs/
rgs_dissertations/2005/RAND_RGSD189.pdf.
57. “HART on-demand intelligence systems proves value to warghters ahead
of theater deployment,” Space War, May 20, 2011, http://www.spacewar.
com/reports/HART_On_Demand_Intelligence_System_Proves_Value_To_
Warghters_Ahead_of_Theater_Deployment_999.html.
58. Scott Littleeld, “Hydra,” darpa.mil, http://www.darpa.mil/Our_Work/
TTO/Programs/Hydra.aspx; and Andy Coon, “Upward Falling Payloads (UFP),”
darpa.mil, http://www.darpa.mil/Our_Work/STO/Programs/Upward_
Falling_Payloads_(UFP).aspx.
59. Patrick Tague, “Improving Anti-Jamming Capability and Increasing
Jamming Impact With Mobility Control” (paper presented at the Mobile
Adhoc and Sensor Systems (MASS), 2010 Institute of Electrical and Electronics
Engineers 7th International Conference, San Francisco, California, November
8-12, 2010), 501-506.
60. Oce of Naval Research.
61. This assumes that follow-on secondary and tertiary targets are within the
available range of the munition given its remaining fuel. Targets would have
to be reasonably clustered for this to work.
62. Mark V. Arena et al., Why Has the Cost of Navy Ships Risen?; and Mark V.
Arena et al., Why Has the Cost of Fixed-Wing Aircraft Risen?.
63. “Expendable Wave: Raytheon’s MALD and MALD-J Decoys,”
defenseindustrydaily.com, April 24, 2013, http://www.defenseindustrydaily.
com/raytheons-mald-decoys-gaining-versatility-04844/.
64. Brian Everstine, “Flight Restrictions Lifted for F-22s with Auto
Oxygen System,” defensenews.com, April 4, 2013, http://www.
defensenews.com/article/20130404/DEFREG02/304040017/
Flight-Restrictions-Lifted-F-22s-Auto-Oxygen-System.
65. The debate on monoculture vs. diversity has a long history in the
information technology sector. For a very brief and readable survey of the
arguments, see Bruce Schneier, “Software Monoculture,” Schneier on Security,
December 1, 2010, https://www.schneier.com/blog/archives/2010/12/
software_monocu.html.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
56
|
66. Sherrill Lingle et al., Methodologiees for Analyzing Remotely Piloted
Aircraft in Future Roles and Missions, (Santa Monica: The RAND Corporation,
2012), 18, http://www.rand.org/content/dam/rand/pubs/documented_
briengs/2012/RAND_DB637.pdf.
67. “DARPA-BAA-09-65 – Precision Electronic Warfare (PREW),” FedBizOpps.
gov, August 24, 2009, https://www.fbo.gov/index?s=opportunity&mode=for
m&id=85271e56b3b9aa657b2fd26cbeaa3944&tab=core&_cview=1.
68. Mark J. Mears, “Cooperative Electronic Attack Using Unmanned Air
Vehicles,” Air Force Research Lab, Wright-Patterson Air Force Base, http://
www.dtic.mil/dtic/tr/fulltext/u2/a444985.pdf.
69. For more, see David Scheidt, in Kimon P. Valavanis, George J. Vachtsevanos,
Handbook of Unmanned Aerial Vehicles, (Springer, 2014).
70. For a technical description of this eect, see David Scheidt, ibid.
71. Col Dr. Frans Osinga, “A Discourse on Winning and Losing,” July 13,
2007, http://www.au.af.mil/au/awc/awcgate/boyd/osinga_boydconf07_
copyright2007.pdf.
72. United States Department of Defense, Autonomy in Weapon Systems,
3000.09 (November 21, 2012). In full disclosure, the author was a major
contributor to the development of DOD Directive 3000.09.
73. This oft-repeated aphorism of military operations is actually paraphrased
from Helmuth Von Moltke’s original statement: “No operation extends with
any certainty beyond the rst encounter with the main body of the enemy.”
74. Source: U.S. Air Force.
75. Lt Gen Dave Deptula, “Air Force Unmanned Aerial System (UAS) Flight
Plan 2009-2047,” slide 11, http://www.defense.gov/DODcmsshare/
briengslide/339/090723-D-6570C-001.pdf.
76. Brian Mekdici and M.L. Cummings, “Modeling Multiple Human Operators
in the Supervisory Control of Heterogenous Unmanned Vehicles,” September
2009, http://web.mit.edu/aeroastro/labs/halab/papers/PerMIS09.pdf.
77. For example, see “Aurora’s Autonomy and Flight Control,” aurora.aero,
http://www.aurora.aero/Research/Autonomy.aspx; and “Product and
Services: Cooperative Control/UDMS,” proxytechnologiesinc.com, http://www.
proxytechnologiesinc.com/systems.html.
78. Robert Brizzolara and Matthew Klunder, Oce of Naval Research media
roundtable, September 30, 2014.
79. Keith Button, “The MAC Attack,” DefenseNews.com, October, 1, 2009,
http://www.defensenews.com/article/20091001/C4ISR02/910010314/
The-MAC-attack.
80. This direction was issued as part of the Fiscal Year (FY) 2012 Defense
Budget, with $46 million allocated over the future years’ defense plan from
FY12-FY15.
81. “United States Air Force RPA Vector – Vision and Enable Concepts 2013-
2038,” (United States Air Force, February 17, 2014).
82. For example, current FAA guidelines that pilots may not perform crew
duties for more than one aircraft at a time are often cited as a rationale for
not elding multi-aircraft control technology. FAA guidelines do not apply to
military operations outside of U.S. national airspace, however. United States
Department of Transportation Federal Aviation Administration, Unmanned
Aircraft Systems (UAS) Operational Approval, N 8900.227 (July 30, 2013).
83. For example, see “Tactical Tomahawk Takes Flight,” navy.mil, August 27,
2002, http://www.navy.mil/submit/display.asp?story_id=3311.
84. “Dogghting Drones – Swarms of Unmanned Battle-Bots Take
to the Skies,” airforce-technology.com, July 23, 2012, http://www.
airforce-technology.com/features/featuredogght-drones-unmanned-battle-
bot-swarms/ and Radhika Nagpal, “The Kilobot Project,”eecs.harvard.edu,
http://www.eecs.harvard.edu/ssr/projects/progSA/kilobot.html.
85. For a more detailed examination of a wider array of possible command-
and-control models, see David Scheidt, Kevin Schultz, “On Optimizing
Command and Control Structures,” Proceedings of the 16th International
Command and Control Research and Technology Consortium (The Johns
Hopkins University Applied Physics Laboratory, 2011).
86. This process is called “particle swarm optimization.” Another downside to
this approach is that it only may result in localized optimization.
87. Coordination is still possible is very low bandwidth environments. For
example, DARPA’s Collaborative Operations in Denied Environment (CODE)
project restricts communications between the swarm and the command
element to 50 kilobits per second, or less than a 56k dial-up modem, circa
1997. “Collaborative Operations in Denied Environment (CODE),” fedbizopps.
gov, April 25, 2014, https://www.fbo.gov/index?s=opportunity&mode=form
&id=2f2733be59230cf2ddaa46498fe5765a&tab=core&_cview=1.
88. One could employ other analogous forms of “jamming” to disrupt
their method of implicit communication, however, such as blocking visual
co-observation of swarm elements with obscurants. Dave Scheidt, JHU/APL,
personal correspondence.
89. Firas Safadi, Raphael Fonteneau, Damien Ernst, “Articial Intelligence
Design for Real-time Strategy Games,” Proceedings of NIPS Workshop on
Decision Making with Multiple Imperfect Decision Makers, December 16, 2011.
90. John Hawley et al., The Human Side of Automation: Lessons for Air Defense
Command and Control, Army Research Laboratory, March 2005.
91. Timothy Chung, Naval Postgraduate School, personal correspondence.
92. John A. Sauter et al., “Distributed Pheromone-Based Swarming Control
of Unmanned Air and Ground Vehicles for RSTA,” (paper presented at SPIE
Defense and Security Conference, Orlando, Florida, March 2008).
93. “All Systems Go: Navy’s Laser Weapon Ready for Summer Deployment,”
Navy.mil, April 7, 2014, http://www.navy.mil/submit/display.asp?story_
id=80172; and Allen McDuee, “Navy’s New Railgun Can Hurl a Shell Over
5,000 MPH,” Wired.com, April 9, 2014, http://www.wired.com/2014/04/
electromagnetic-railgun-launcher/.
94. “Dogghting Drones – Swarms of Unmanned Battle-Bots Take to the Skies.”

|
57
95. Additionally, while having a person physically onboard a platform does not
render it immune to cyberattacks, having a person physically present could
at least prevent the adversary from taking control of the system via cyber
attacks, provided there are hardware-level physical overrides. A co-located
human operator could physically unplug, for example, a malfunctioning
missile battery. When systems are controlled remotely, this additional failsafe
does not exist.
96. Humans, of course, are not impervious to deception. Machines actually
might be better at detecting data that is manipulated slightly. A person
might not notice 1% dierence in position data, whereas a machine might
catch such a dierence. Humans, however, have a level of common sense that
can be applied to information that is grossly wrong. If sent the directive to
attack friendly forces, for example, a human would intuitively know that the
order was either garbled or the result of enemy deception. Some degree of
“skepticism” can be programmed into machines – if certain types of failures
or enemy attacks can be anticipated. Human intelligence is far more robust,
however, to unanticipated circumstances.
97. This, of course, depends on an eective communications link.
98. Andrew Herr, “Will Humans Matter in the Wars of 2030?,” forthcoming
publication.
99. Mark V. Arena et al., Why Has the Cost of Navy Ships Risen; and Mark V.
Arena et al., Why Has the Cost of Fixed-Wing Aircraft Risen?.
100. For example, the F-35 Joint Strike Fighter has over 24 million lines of code.
A Mercedes S-class sedan as approximately 100 million lines of code. “A Digital
Jet for the Modern Battlespace,” f35.com, https://www.f35.com/about/life-
cycle/software; and Robert N. Charette, “This Car Runs on Code,” spectrum.
ieee.org, February 1, 2009, http://spectrum.ieee.org/transportation/systems/
this-car-runs-on-code.
101. Admiral Jonathan W. Greenert, “Payloads over Platforms: Charting
a New Course,” usni.org, July 2012, http://www.usni.org/magazines/
proceedings/2012-07/payloads-over-platforms-charting-new-course.
102. Chris Urmson, “The Latest Chapter for the Self-Driving Car: Mastering City
Street Driving,” Google Ocial Blog on BlogSpot.com, April 28, 2014, http://
googleblog.blogspot.com/2014/04/the-latest-chapter-for-self-driving-car.
html.
103. For a good overview of the state of technology today, including current
limitations of autonomous vehicles, and likely future trends see “Self-
driving cars take a small step closer to reality,” TheStar.com, September
15, 2014, http://www.thestar.com.my/Tech/Tech-News/2014/09/15/
Self-driving-cars-take-a-small-step-closer-to-reality/.
104. Patrick Lin, “The Ethics of Autonomous Cars,” TheAtlantic.com,
October 8, 2013, http://www.theatlantic.com/technology/archive/2013/10/
the-ethics-of-autonomous-cars/280360/.
105. Takeo and landing are also the most prevalent conditions for accidents
for human-inhabited aircraft as well. The challenge of manually landing an
aircraft is compounded in an uninhabited aircraft because the pilot does not
get immediate kinesthetic feedback on the aircraft’s movement. Thus, there
is not only a slight time delay in communications between the aircraft and the
controller, but also a time delay in perception by the pilot, who must rely on
visual or other cues to perceive movement of the aircraft.
106. For example, the Air Force’s vision document for uninhabited aircraft out
to 2038 still refers to them as “remotely piloted,” “United States Air Force RPA
Vector – Vision and Enabling Concepts 2013-2038.” For a somewhat humorous
overview of the tortured language used to refer to uninhabited aircraft see
Joe Trevithick, “Learn to Speak Air Force – A Public Service Announcement
Regarding Drones,” Medium.com/War-Is-Boring, May 27, 2014, https://
medium.com/war-is-boring/learn-to-speak-air-force-e6ebc5614b25.
107. Department of the Army, Unmanned Aircraft System Flight Regulations,
Army Regulation 95-23 (July 2, 2010), http://www.apd.army.mil/pdles/
r95_23.pdf.
108. For more on what this shift to supervisory control will mean and the
challenges it will bring, see Hawley, ibid.
109. Michael C. Horowitz, “The Looming Robotics Gap.”
110. Ekso Bionics, “Yes, We Said Bionics,” http://www.eksobionics.com/ekso.
111. Ben Fitzgerald and Kelley Sayler, “Creative Disruption: Technology,
Strategy and the Future of the Global Defense Industry” (Center for a New
American Security, June 2013), http://www.cnas.org/sites/default/les/
publications-pdf/CNAS_FutureDefenseIndustry_FitzGeraldSayler.pdf.
112. General Mike Hostage, commander of the Air Force’s Air Combat
Command, has made this point about the software on the F-22, saying “The
F-22, when it was produced, was ying with computers that were already so
out of date you would not nd them in a kid’s game console in somebody’s
home gaming system. But I was forced to use that because that was the
[specication] that was written by the acquisition process when I was going to
buy the F-22.” “Interview: Gen. Michael Hostage, Commander, US Air Force’s
Air Combat Command,” 3 February 2014, http://mobile.defensenews.com/
article/302030017.
113. For an excellent critique of the belief that technology can make war quick
or easy, see H.R. McMaster, “The Pipe Dream of Easy War,” New York Times,
July 20, 2013, http://www.nytimes.com/2013/07/21/opinion/sunday/the-
pipe-dream-of-easy-war.html?pagewanted=all&_r=0.
114. This echoes a recommendation from Samuel J. Brannen in “Sustaining
the U.S. Lead in Unmanned Systems,” (CSIS International Security Program,
February 2014), 15, http://csis.org/les/publication/140227_Brannen_
UnmannedSystems_Web.pdf.

Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
58
|

Appendix
TOTAL PROBABILITY OF KILL FOR SALVO 60
Robotics on the Battleeld Part II
The Coming Swarm
OCTOBER 2014
60
|
APPENDIX: TOTAL PROBABILITY OF KILL FOR SALVO*
By number of munitions red and probability of kill (Pk) for each munition.
Number of
Munitions per
Salvo
Single
Munition Pk =
0.9
Single
Munition Pk =
0.8
Single
Munition Pk =
0.7
Single
Munition Pk =
0.6
Single
Munition Pk =
0.5
1 0.9 0.8 0.7 0.6 0.5
2 0.99 0.96 0.91 0.84 0.75
3 0.999 0.992 0.973 0.936 0.875
4 0.9999 0.9984 0.9919 0.9744 0.9375
5 0.99999 0.99968 0.99757 0.98976 0.96875
6 1 0.99994 0.99927 0.9959 0.98438
7 1 0.99999 0.99978 0.99836 0.99219
8 1 1 0.99993 0.99934 0.99609
9 1 1 0.99998 0.99974 0.99805
10 1 1 0.99999 0.9999 0.99902
11 1 1 1 0.99996 0.99951
12 1 1 1 0.99998 0.99976
13 1 1 1 0.99999 0.99988
14 1 1 1 1 0.99994
15 1 1 1 1 0.99997
16 1 1 1 1 0.99998
17 1 1 1 1 0.99999
18 1 1 1 1 1
19 1 1 1 1 1
20 1 1 1 1 1
21 1 1 1 1 1
22 1 1 1 1 1
23 1 1 1 1 1
24 1 1 1 1 1
25 1 1 1 1 1
26 1 1 1 1 1
27 1 1 1 1 1
28 1 1 1 1 1
29 1 1 1 1 1
30 1 1 1 1 1
… … … … … …
39 1 1 1 1 1
40 1 1 1 1 1
41 1 1 1 1 1
* Total probability of a kill for a salvo (Pksalvo) is given by the following formula: Pksalvo = 1 – (1 – Pk)^N where Pk is the probability of kill for a single munition
and N is the number of munitions red in a salvo.
|
61
Single
Munition Pk =
0.45
Single
Munition Pk =
0.4
Single
Munition Pk =
0.3
Single
Munition Pk =
0.2
Single
Munition Pk =
0.11
Single
Munition Pk =
0.055
0.45 0.4 0.3 0.2 0.11 0.055
0.6975 0.64 0.51 0.36 0.2079 0.106975
0.83363 0.784 0.657 0.488 0.29503 0.156091
0.90849 0.8704 0.7599 0.5904 0.37258 0.202506
0.94967 0.92224 0.83193 0.67232 0.44159 0.246369
0.97232 0.95334 0.88235 0.73786 0.50302 0.287818
0.98478 0.97201 0.91765 0.79028 0.55769 0.326988
0.99163 0.9832 0.94235 0.83223 0.60634 0.364004
0.99539 0.98992 0.95965 0.86578 0.64964 0.398984
0.99747 0.99395 0.97175 0.89263 0.68818 0.43204
0.99861 0.99637 0.98023 0.9141 0.72248 0.463277
0.99923 0.99782 0.98616 0.93128 0.75301 0.492797
0.99958 0.99869 0.99031 0.94502 0.78018 0.520693
0.99977 0.99922 0.99322 0.95602 0.80436 0.547055
0.99987 0.99953 0.99525 0.96482 0.82588 0.571967
0.99993 0.99972 0.99668 0.97185 0.84503 0.595509
0.99996 0.99983 0.99767 0.97748 0.86208 0.617756
0.99998 0.9999 0.99837 0.98199 0.87725 0.638779
0.99999 0.99994 0.99886 0.98559 0.89075 0.658646
0.99999 0.99996 0.9992 0.98847 0.90277 0.677421
1 0.99998 0.99944 0.99078 0.91347 0.695163
1 0.99999 0.99961 0.99262 0.92298 0.711929
1 0.99999 0.99973 0.9941 0.93146 0.727773
1 1 0.99981 0.99528 0.939 0.742745
1 1 0.99987 0.99622 0.94571 0.756894
1 1 0.99991 0.99698 0.95168 0.770265
1 1 0.99993 0.99758 0.95699 0.7829
1 1 0.99995 0.99807 0.96172 0.794841
1 1 0.99997 0.99845 0.96593 0.806125
1 1 0.99998 0.99876 0.96968 0.816788
… … … … … …
1 1 1 0.99983 0.98938 0.889887
1 1 1 0.99987 0.99055 0.895943
1 1 1 0.99989 0.99159 0.901666




About the Center for a
New American Security
The mission of the Center for a New American
Security (CNAS) is to develop strong, pragmatic
and principled national security and defense
policies. Building on the expertise and
experience of its sta and advisors, CNAS
engages policymakers, experts and the public
with innovative, fact-based research, ideas
and analysis to shape and elevate the national
security debate. A key part of our mission is to
inform and prepare the national security leaders
of today and tomorrow.
CNAS is located in Washington, and was
established in February 2007 by co-founders
Kurt M. Campbell and Michèle A. Flournoy.
CNAS is a 501(c)3 tax-exempt nonprot
organization. Its research is independent and
non-partisan. CNAS does not take institutional
positions on policy issues. Accordingly, all views,
positions, and conclusions expressed in this
publication should be understood to be solely
those of the authors.
© 2014 Center for a New American Security.
All rights reserved.
Center for a New American Security
1152 15th Street, NW
Suite 950
Washington, DC 20005
TEL 202.457.9400
FAX 202.457.9401
EMAIL info@cnas.org
www.cnas.org
Production Notes
Soy ink is a helpful component in paper recycling. It helps in this
process because the soy ink can be removed more easily than
regular ink and can be taken out of paper during the de-inking
process of recycling. This allows the recycled paper to have less
damage to its paper bers and have a brighter appearance.
The waste that is left from the soy ink during the de-inking
process is not hazardous and it can be treated easily through
thedevelopment of modern processes.
Paper recycling is reprocessing waste paper bers back into
ausable paperproduct.

1152 15th Street, NW
Suite 950
Washington, DC 20005
STRONG, PRAGMATIC AND PRINCIPLED
NATIONAL SECURITY AND DEFENSE POLICIES
TEL 202.457.9400
FAX 202.457.9401
EMAIL [email protected]rg
www.cnas.org
Printed on Post-Consumer Recycled paper with Soy Inks
