
PUBLIC
Document Version: 1.1 – 2020-02-05
Security Guide for SAP S/4HANA 1709
© 2020 SAP SE or an SAP aliate company. All rights reserved.
THE BEST RUN
Content
1 Introduction................................................................7
2 Before You Start.............................................................8
3 System Hardening with SAP Security Notes........................................9
4 SAP S/4HANA System Landscape Information.....................................11
5 User Administration and Authentication..........................................13
5.1 User Management............................................................13
Non-SAP Fiori Technology....................................................13
SAP Fiori Technology.......................................................15
5.2 User Data Synchronization......................................................16
5.3 Role Administration...........................................................16
5.4 Integration into Single Sign-On Environments........................................ 16
6 Network and Communication Security...........................................18
6.1 Communication Channel Security.................................................18
6.2 Network Security............................................................ 19
6.3 Communication Destinations....................................................19
7 ICF and Session Security.....................................................20
8 File System Access Security...................................................22
9 Virus Scanning.............................................................23
9.1 Virus Scanning in File Uploads...................................................23
9.2 General Recommendations for Virus Scan Proles.....................................24
9.3 Further Protection Against Active Content...........................................26
10 Additional System Hardening Activities..........................................27
11 Data Protection............................................................29
11.1 Read Access Logging..........................................................31
11.2 Deletion of Personal Data...................................................... 32
12 SAP S/4HANA Cross Application Infrastructure....................................33
12.1 Data Security in SAP ILM.......................................................33
Data Security in SAP ILM System Connections.....................................33
Users and Authorizations in SAP ILM............................................34
Security of Stored Data in SAP ILM.............................................35
2
P U B L I C
Security Guide for SAP S/4HANA 1709
Content
Logs in SAP ILM...........................................................36
12.2 Payment Card Security........................................................37
Before You Start...........................................................37
Authorizations ...........................................................38
Data Storage Security...................................................... 39
Setting Up Encryption Software ...............................................40
Making Settings for Payment Card Security .......................................40
Relevant SSF Applications ...................................................42
Generating Keys ..........................................................42
Migration of Payment Card Data Stored in Unencrypted Form ..........................43
Migration of Payment Card Data on SAP Business Partner.............................43
Migration to SSF Application PAYCRV ...........................................44
Migration to Current Key Version .............................................. 44
Deleting a Key Version ......................................................45
Security-Relevant Logging and Tracing...........................................45
Recommended Implementation Steps ..........................................45
13 SAP S/4HANA Business Applications............................................47
13.1 Asset Management...........................................................47
Maintenance Operations.....................................................47
Environment, Health and Safety............................................... 47
13.2 Commerce.................................................................57
Commerce Management.................................................... 57
13.3 Finance...................................................................65
Financial Accounting.......................................................65
Controlling.............................................................. 76
Governance, Risk and Compliance for Finance.....................................76
Treasury and Financial Risk Management.........................................82
Financial Operations.......................................................103
Real Estate Management....................................................116
Receivables Management...................................................119
SAP S/4HANA Financial Closing cockpit.........................................142
Travel Management....................................................... 142
13.4 Human Resources...........................................................146
User Management........................................................146
Authorizations...........................................................148
Security-Relevant Logging and Tracing..........................................152
Core HR and Payroll.......................................................152
Talent Management.......................................................229
Time and Attendance Management............................................320
13.5 Manufacturing.............................................................337
Production Planning.......................................................338
Security Guide for SAP S/4HANA 1709
Content
P U B L I C 3
Manufacturing Execution for Discrete Industries...................................339
Quality Management......................................................342
Maintenance Operations................................................... 348
13.6 R&D / Engineering..........................................................349
Product Safety and Stewardship..............................................349
Enterprise Portfolio and Project Management.....................................367
Integrated Product Development for Discrete Industries.............................398
Product Lifecycle Management .............................................. 403
13.7 Sales....................................................................409
Deletion of Personal Data in Sales.............................................409
Global Trade Management...................................................411
13.8 Service...................................................................414
Warranty Management.....................................................414
13.9 Sourcing and Procurement.....................................................416
Authorizations...........................................................416
Data Storage Security..................................................... 422
Other Security-Relevant Information...........................................425
Deletion of Personal Data...................................................427
Specic Read Access Log Congurations........................................430
Ariba Network Integration...................................................431
Supplier and Category Management........................................... 431
Integration.............................................................438
13.10 Supply Chain..............................................................440
Ecient Logistics and Order Fulllment.........................................440
Extended Warehouse Management............................................445
Deletion of Personal Data...................................................459
Transportation Management................................................ 460
13.11 Cross-Line-of-Business.......................................................478
Commodity Management...................................................479
13.12 Analytics Technology........................................................ 484
Process Performance Monitoring............................................. 485
13.13 Enterprise Technology........................................................487
Central Master Data.......................................................487
Specic Read Access Log Congurations........................................491
Legal Content Management.................................................492
Geographical Enablement Framework..........................................494
Master Data Governance................................................... 496
Agent Framework........................................................ 498
13.14 SAP S/4HANA Industries..................................................... 499
Automotive.............................................................499
Banking................................................................501
4
P U B L I C
Security Guide for SAP S/4HANA 1709
Content
Higher Education and Research...............................................526
Professional Services......................................................535
Commercial Project Inception and Lean Stang .................................. 535
Public Sector............................................................542
Retail.................................................................553
Utilities................................................................569
SAP for Insurance........................................................580
Oil and Gas.............................................................585
Engineering, Construction, and Operations...................................... 592
14 Business Network Integration................................................ 596
14.1 Security Aspects for Connectivity Types...........................................596
14.2 Direct Connectivity: SAP S/4HANA as Client........................................597
14.3 Direct Connectivity: SAP S/4HANA as Server....................................... 599
14.4 Roles and Authorizations (Ariba Network)..........................................599
14.5 Roles and Authorizations (SAP Fieldglass).........................................600
Security Guide for SAP S/4HANA 1709
Content
P U B L I C 5

Document History
Version Date Description
1.0 September 15, 2017 Initial Version
1.1 February 5, 2020 The chapters Data Protection [page
502] (under SAP Business Partner for
Financial Services (FS-BP)) and Agent
Framework [page 498] were added.
6 P U B L I C
Security Guide for SAP S/4HANA 1709
Document History
1 Introduction
Target Audience
● Technology consultants
● Security consultants
● System administrators
This document is not included as part of the Installation Guides, Conguration Guides, Technical Operation
Manuals, or Migration Guides. Such guides are only relevant for a certain phase of the software life cycle,
whereas the Security Guides provide information that is relevant for all life cycle phases.
Why Is Security Necessary?
With the increasing use of distributed systems and the Internet for managing business data, the demands on
security are also on the rise. When using a distributed system, you need to be sure that your data and
processes support your business needs without allowing unauthorized access to critical information. User
errors, negligence, or attempted manipulation of your system should not result in loss of information or
processing time. These demands on security apply likewise to SAP S/4HANA.
To assist you in securing SAP S/4HANA, we provide this Security Guide.
About this Document
The Security Guide provides an overview of the security-relevant information that applies to SAP S/4HANA in
general. In particular it comprises general considerations regarding the system access via SAP Fiori Apps. In
case there are specic aspects for the underlying scenarios or applications these are described in an area-
specic chapter.
Security Guide for SAP S/4HANA 1709
Introduction
P U B L I C 7

2 Before You Start
Fundamental Security Guides
SAP S/4HANA is based on SAP NetWeaver and the SAP HANA Platform. With respect to SAP Fiori apps, SAP
Gateway plays a fundamental role as well. This means that the corresponding Security Guides are also
applicable for SAP S/4HANA.
Whenever other guides are relevant, an appropriate reference is included in the documentation for the
individual solution areas in the specic part of this guide.
Also consider the following fundamental security whitepapers found on https://support.sap.com/en/security-
whitepapers.html
:
● Secure Conguration of SAP NetWeaver Application Server Using ABAP
● SAP Security Recommendations: Securing Remote Function Calls (RFC)
● Protecting SAP Applications Against Common Attacks
Important SAP Notes
SAP Note 1538539 contains information about saving temporary les when using Adobe Acrobat Reader in
SAP applications. SAP Note 138498 contains information on single sign-on solutions. SAP Notes relating to
security for the subcomponents of SAP S/4HANA are referenced in the documentation for the individual
components in this guide. For a list of additional security-relevant SAP Hot News and SAP Notes, see the SAP
Support Portal at http://support.sap.com/securitynotes .
8
P U B L I C
Security Guide for SAP S/4HANA 1709
Before You Start
3 System Hardening with SAP Security
Notes
Backlog of Existing Security Notes
There is also a backlog of security notes that require your attention during early phases of your SAP S/4HANA
system setup. The following is a list of important security notes which include manual conguration steps and
which you need to implement in your SAP S/4HANA system. These implementations/congurations can only
be carried out by you due to your specic landscape and specic application environment.
Note
Some of these SAP Notes may not be applicable in your system landscape.
SAP Note Title
1322944
ABAP: HTTP security session management
1531399
Enabling SSL for Session Protection
1585767
Enabling Virus Scanning in SAP Content Server
1616535
Secure conguration of ICM for the ABAP application server
1693981
Unauthorized modication of displayed content
1853140
Managing SAProuter from external host
1973081
XSRF vulnerability: External start of transactions with OK
Code
2086818
Fixing POODLE SSLv3.0 (CVE-2014-3566) Vulnerability
2107562
Fixing POODLE SSLv3.0 (CVE-2014-3566) Vulnerability in
Money Mobiliser Platform
2142551
Whitelist service for Clickjacking Framing Protection in AS
ABAP
2185122
Switchable authorization checks for RFC in data extraction
within CA-MDG-APP-FIN
2245332
Automatic usage of Whitelist Service for Clickjacking Fram
ing Protection in SAPUI5 Apps
Security Guide for SAP S/4HANA 1709
System Hardening with SAP Security Notes
P U B L I C 9

SAP Note Title
2260344
OS command injection vulnerability in SCTC_* Function
modules
2319172
Whitelist based Clickjacking Framing Protection in SAP GUI
for HTML
2319192
Whitelist based Clickjacking Framing Protection in BSP
2333957
Whitelist based Clickjacking Framing Protection in SAP Fiori
Launchpad for SAP NetWeaver AS for ABAP
2349128
Whitelist based Clickjacking Framing Protection in UI theme
designer on ABAP
2421287
Front-end printing with SAP GUI 750
10 P U B L I C
Security Guide for SAP S/4HANA 1709
System Hardening with SAP Security Notes
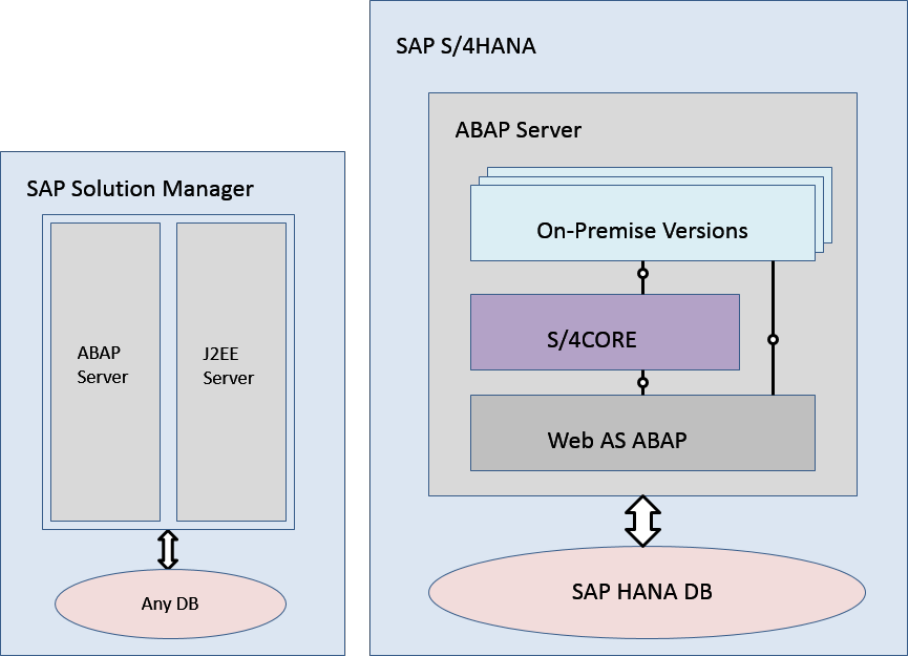
4 SAP S/4HANA System Landscape
Information
There are various ways of deploying SAP S/4HANA in your new or already existing system landscape. This
section describes some examples.
Example: SAP S/4HANA New Installation
A new installation of SAP S/4HANA needs to run on the SAP HANA database. It is recommended to use the
SAP Solution Manager, which can run on any database. This very simple landscape can be enhanced with the
SAP cloud solutions and SAP Business Suite products.
Simple SAP S/4HANA Deployment
Example: SAP S/4HANA in an SAP Business Suite Landscape
It is possible to integrate SAP S/4HANA into an existing SAP Business Suite landscape by replacing the SAP
ERP enhancement package product with SAP S/4HANA. When performing this conversion in your system
Security Guide for SAP S/4HANA 1709
SAP S/4HANA System Landscape Information
P U B L I C 11
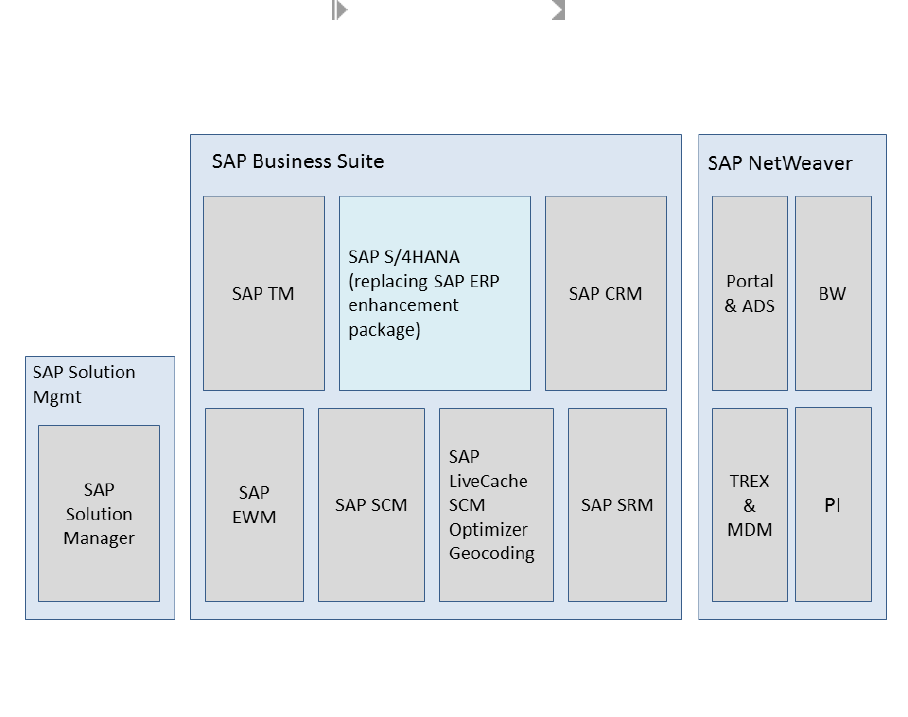
landscape, you need to do some adaptations, for example you need to convert some of your existing business
processes to the simplied SAP S/4HANA processes. Some of the SAP Business Suite processes are no longer
supported, some have been changed, and there are also new processes. How to convert your existing
processes to the SAP S/4HANA processes is described in the Simplication List.
For more information about the Simplication Item Catalog, see the Conversion Guide for SAP S/4HANA 1709
at http://help.sap.com/s4hana_op_1709 Product Documentation .
Example SAP Business Suite landscape with an embedded SAP S/4HANA system
More Information
For more information about SAP Fiori for SAP S/4HANA in a hub deployment, see Landscape Deployment
Recommendations for SAP Fiori Front-End Server.
12
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA System Landscape Information

5 User Administration and Authentication
Overview
SAP S/4HANA generally relies on the user management and authentication mechanisms provided with the
SAP NetWeaver platform, in particular the SAP NetWeaver AS for ABAP Application Server and the SAP HANA
Platform. Therefore, the security recommendations and guidelines for user administration and authentication
as described in the
SAP NetWeaver Application Server for ABAP Security Guide and SAP HANA Platform
also apply to SAP S/4HANA.
In addition to these guidelines, we include information about user administration and authentication that
specically applies to SAP S/4HANA in the following topics:
● User Management
This topic lists the tools to use for user management, the types of users required, and the standard users
that are delivered with SAP S/4HANA.
● User Data Synchronization
SAP S/4HANA can share user data with other components. This topic describes how the user data is
synchronized with these other sources.
● Integration into Single Sign-On Environments
5.1 User Management
5.1.1 Non-SAP Fiori Technology
User management for SAP S/4HANA uses the mechanisms provided with the SAP NetWeaver Application
Server for ABAP, such as tools, user types, and password concept. For an overview of how these mechanisms
apply for SAP S/4HANA, see the sections below. In addition, we provide a list of the standard users required for
operating SAP S/4HANA.
User Administration Tools
This table shows the tools available for user management and administration.
Security Guide for SAP S/4HANA 1709
User Administration and Authentication
P U B L I C 13

Tool Description
User maintenance for ABAP-based systems (transaction
SU01)
For more information about the authorization objects pro
vided by the subcomponents of SAP S/4HANA, see the ap
plication-specic sections.
Role maintenance with the prole generator for ABAP-based
systems (PFCG)
For more information about the roles provided by the sub
components of SAP S/4HANA, see the application-specic
sections. Also, see User and Role Administration of Applica
tion Server ABAP
at help.sap.com Enterprise
Management SAP ERP SAP ERP 6.0 EHP7 SAP ERP
Security Guide
SAP ERP Central Component Security
Guide User Administration and Authentication User
Administration
.
Central User Administration (CUA) for the maintenance of
multiple ABAP-based systems
For central administrative tasks
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively have to change their passwords on a regular
basis, but not those users under which background processing jobs run. The user types that are required for
SAP S/4HANA
● Individual users
○ Dialog users - used for SAP GUI for Windows
○ Internet users - used for Web Applications
● Technical users
● Service users are dialog users who are available for a large set of anonymous users
● Communication users are used for dialog-free communication between systems
● Background users are used for processing in the background
For more information about these user types, see User Types in the SAP NetWeaver Application Server for
ABAP Security Guide .
Standard Users
This section describes the standard users necessary for operating SAP S/4HANA
Note
Ensure you change the passwords and IDs of users that were created automatically during the installation.
14
P U B L I C
Security Guide for SAP S/4HANA 1709
User Administration and Authentication
System User ID Type Password Additional Informa
tion
SAP Web Application
Server
<sapsid>adm SAP system adminis
trator
Mandatory SAP NetWeaver Instal
lation Guide
SAP Web Application
Server
SAP Service <sapsid> SAP system adminis
trator
Mandatory SAP NetWeaver Instal
lation Guide
SAP Web Application
Server
TMSADM SAP system adminis
trator
Mandatory SAP NetWeaver Instal
lation Guide
SAP Web Application
Server
SAP Standard ABAP
Users (SAP*, DDIC,
EARLYWATCH,
SAPCPIC)
See SAP NetWeaver
Security Guide
Optional SAP NetWeaver Secur
ity Guide
Note that EARLY
WATCH and SAPCPIC
may not be needed in
your system land
scape. See note below
this table for details.
SAP ECC SAP Users Dialog users Mandatory The number of users
depends on the area of
operation and the busi
ness data to be proc
essed
Note
In most cases, the user EARLYWATCH is not used anymore. We recommend checking if this is the case in
your landscape. If the user is not needed, it should be deleted to minimize the attack surface. For more
information, see 1749142 .
The user SAPCPIC is sometimes used in legacy RFC scenarios or with EDI. We recommend checking if
SAPCPIC is needed in your landscape. If the user is not needed, it should be deleted to minimize the attack
surface.
5.1.2 SAP Fiori Technology
For details on the user management and authorization concepts used in SAP Fiori apps, see the SAP S/4HANA
UI Technology Guide at the SAP Help Portal under http://help.sap.com/s4hana_op_1709 Product
Documentation
.
Security Guide for SAP S/4HANA 1709
User Administration and Authentication
P U B L I C 15

5.2 User Data Synchronization
By synchronizing user data, you can reduce eort and expense in the user management of your system
landscape. Since SAP S/4HANA is based on SAP NetWeaver, you can use all of the mechanisms for user
synchronization in SAP NetWeaver here.
For more information, see the SAP NetWeaver Security Guide on SAP Help portal at https://help.sap.com/nw75
Security Guide .
5.3 Role Administration
Business roles in SAP S/4HANA represent the central object used to structure users’ access on the frontend
server.
For more information, see the following sections on http://help.sap.com/s4hana_op_1709:
● General information on role maintenance in systems based on SAP NetWeaver Application Server
ABAP:
Enter Conguration of User and Role Administration into the search bar, press Enter and open the search
result with that title.
● Role maintenance for access based on SAP Fiori launchpad:
Enter SAP Fiori Launchpad into the search bar, press Enter , open the search result with that title and then
navigate to:
○ Administration Guide Initial Setup of the Launchpad
○ Security Aspects
● Authorization concepts and role maintenance for custom development:
Enter From the Programmed Authorization Check to a Role into the search bar, press Enter and open the
search result with that title.
● UI content and authorization concept for SAP Fiori apps:
Open the UI Technology Guide under Product Documentation and navigate to App Implementation
User Management and Authorization UI Content and Authorization Concept
5.4 Integration into Single Sign-On Environments
Non-Fiori Technology
SAP S/4HANA supports the single sign-on (SSO) mechanisms provided by SAP NetWeaver Application Server
for ABAP technology. Therefore, the security recommendations and guidelines for user management and
authentication that are described in the SAP NetWeaver Security Guide also apply to SAP S/4HANA.
16
P U B L I C
Security Guide for SAP S/4HANA 1709
User Administration and Authentication

For non-Fiori technology SAP S/4HANA supports the following mechanisms:
● Secure Network Communications (SNC)
SNC is available for user authentication and provides for an SSO environment when using the SAP GUI for
Windows or Remote Function Calls.
● SAP Logon Tickets
SAP S/4HANA supports the use of logon tickets for SSO when using a Web browser as the front-end client.
In this case, users can be issued a logon ticket after they have authenticated themselves with the initial
SAP system. The ticket can then be submitted to other systems (SAP or external systems) as an
authentication token. The user does not need to enter a user ID or password for authentication, but can
access the system directly once it has checked the logon ticket. For more information, see SAP Logon
Tickets in the Security Guide for SAP NetWeaver Application Server at https://help.sap.com/nw75
Security Guide English Security Guides for the AS ABAP SAP NetWeaver Application Server ABAP
Security Guide
.
● Client Certicates
As an alternative to user authentication using a user ID and passwords, users using a Web browser as a
front-end client can also provide X.509 client certicates to use for authentication. In this case, user
authentication is performed on the Web server using the Secure Sockets Layer Protocol (SSL Protocol). No
passwords have to be transferred. User authorizations are valid in accordance with the authorization
concept in the SAP system.
For more information see Client Certicates in the Security Guide for SAP NetWeaver Application Server.
For more information about available authentication mechanisms, see SAP Library for SAP NetWeaver
under User Authentication and Single Sign-On at https://help.sap.com/nw75 Security Guide .
For more information about the available authentication mechanisms, see the User Authentication and Single
Sign-On documentation in the SAP NetWeaver Library.
Fiori Technology
For details on the User Authentication and Single Sign-On concepts used in SAP Fiori apps, see the SAP S/
4HANA UI Technology Guide at the SAP Help Portal under http://help.sap.com/s4hana_op_1709 Product
Documentation
.
Security Guide for SAP S/4HANA 1709
User Administration and Authentication
P U B L I C 17

6 Network and Communication Security
Your network infrastructure is extremely important in protecting your system. Your network needs to support
the communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats. These threats can be based on software aws, at both
the operating system level and application level, or network attacks, such as eavesdropping.
If users cannot log on to your application or database servers at the operating system or database layer, then
there is no way for intruders to compromise the machines and gain access to the backend system database or
les.
Additionally, if users are not able to connect to the server local area network (LAN), they cannot exploit well-
known bugs and security holes in network services on the server machines.
6.1 Communication Channel Security
SAP S/4 HANA uses several protocols for communication to internal and external applications. These can be
SAP systems or third-party systems. The following protocols are supported:
● HTTPS
HTTP connections are protected by the Transport Layer Security (TLS) protocol. This protocol used to be
known as Secure Sockets Layer (SSL).
● RFC
RFC connections can be protected using Secure Network Communications (SNC). For detailed
recommendations on securing RFC connections, see SAP Note 2008727 and the SAP Whitepaper
Securing Remote Function Calls attached to it.
● SOAP
SOAP connections are protected with Web services security.
● IDoc
● REST
Note
We strongly recommend using secure protocols (TLS, SNC) whenever possible.
For more information on securing the protocols above, see the respective chapters in the SAP NetWeaver
Security Guide.
18
P U B L I C
Security Guide for SAP S/4HANA 1709
Network and Communication Security

6.2 Network Security
Network
SAP S/4HANA is based on SAP NetWeaver technology. Therefore, for information about network security, see
the respective sections in the SAP NetWeaver Security Guide at https://help.sap.com/nw75 Security
Guide English . This includes information on using rewall systems for access control and using network
segmentation.
If your system provides Internet services, you should ensure you protect your network infrastructure with a
rewall at least. You can further increase the security of your system (or group of systems) by diving the
system into groups, placing the groups in dierent network segments, and then protecting each segment from
unauthorized access by a rewall.
Bear in mind that unauthorized access is also possible internally if a malicious user has managed to gain
control of one of your systems.
Ports
SAP S/4HANA is executed in SAP NetWeaver and uses the ports of AS ABAP. For more information, see the
corresponding security guides for SAP NetWeaver under the topics for AS ABAP Ports.
6.3 Communication Destinations
The use of communication destination is application-specic. Therefore please check the application-specic
chapters for details.
In this context please note that users and authorizations should be used with specic care, as the use of users
and authorizations in an irresponsible manner can pose security risks. You should therefore follow the security
rules below when communicating between application systems.
General Rules
● Employ the user types ‘system’ and ‘communication’
● Grant a user only the minimum of authorizations
● Tell users to choose a secure password and to not divulge it to anyone else
● Only store user-specic logon data for users of type 'system' and 'communication'
● Wherever possible, use trusted system functions instead of user-specic logon data
Security Guide for SAP S/4HANA 1709
Network and Communication Security
P U B L I C 19
7 ICF and Session Security
Internet Communication Framework (ICF) Services
You should handle Internet Communication Framework (ICF) services in a restrictive manner in order to
minimize the attack surface on the web.
Note
As a general rule you should only activate those ICF services that are needed for the applications running in
your system.
For details on the required services, see the application-specic chapters of this guide. Use transaction SICF to
activate or de-activate ICF services. For more information, see the SAP NetWeaver documentation.
Additional information on the required services can be found in the RFC/ICF Security Guide at http://
help.sap.com/s4hana_op_1709 under SAP NetWeaver for SAP S/4HANA Security Guide RFC/ICF
Security Guides
.
Note
If your rewall(s) use URL ltering, note the URLs used for the services, and adjust your rewall settings
accordingly.
Session Security Protection
Secure Session Management
To increase security and prevent access to the SAP logon ticket and security session cookie(s), we recommend
activating secure session management. We also highly recommend using SSL to protect the network
communications where these security-relevant cookies are transferred.
Session Security Protection on the AS ABAP
For SAP NetWeaver version 7.0 and higher, it is recommended to activate HTTP security session management
using transaction SICF_SESSIONS. In particular it is recommended to activate extra protection of security-
related cookies.
The HttpOnly ag instructs the browser to deny access to the cookie through client side script. As a result,
even if a cross-site scripting (XSS) aw exists, and a user accidentally accesses a link that exploits this aw, the
browser will not reveal the cookie to a third party.
The Secure ag tells the browser to send the cookie only if the request is being sent over a secure channel such
as HTTPS. This helps protect the cookie from being passed over unencrypted requests.
20
P U B L I C
Security Guide for SAP S/4HANA 1709
ICF and Session Security

These additional ags are congured through the following prole parameters:
Prole Parameter Recommended Value Description Comment
icf/
set_HTTPonly_flag_on_cook
ies
0 Add HttpOnly ag Client-dependent
login/ticket_only_by_https 1 Add Secure ag Not client-dependent
For more information, a list of the relevant prole parameters, and detailed instructions, see Activating HTTP
Security Session Management on AS ABAP in the AS ABAP security documentation.
Security Guide for SAP S/4HANA 1709
ICF and Session Security
P U B L I C 21

8 File System Access Security
More Information
For detailed information about data storage security, see the SAP NetWeaver Security Guide.
Using Logical Paths and File Names to Protect Access
Some applications in SAP S/4HANA save data in les in the le system. Therefore, it is important to explicitly
provide access to the corresponding les in the le system without allowing access to other directories or les -
a security issue also known as directory traversal. This is achieved by specifying logical paths and le names in
the system that map to the physical paths and le names. This mapping is validated at runtime. If access is
requested to a directory that does not match a stored mapping, then an error occurs.
In the application-specic part of this guide, there is a list of the logical le names and paths for each
component. It also species for which programs these le names and paths apply.
Activating the Validation of Logical Paths and File Names
You enter the logical paths and le names in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation on path level at
runtime, enter the physical path using the transactions SFILE (client-independent) and SF01 (client-
dependent). To determine which paths are used by your system, you can activate the appropriate settings in
the Security Audit Log. The relevant SAL events are CUQ, CUR, CUS, CUT, and DU5.
For new installations it is recommended to enforce path validation as a default by setting
REJECT_EMPTY_PATH=ON in table FILECMCUST (transaction SM30). For details see SAP Note 2251231 - File
validation enforcement switch for empty physical path
.
For more information, go to http://help.sap.com/s4hana_op_1709, enter one of the following titles into the
search bar, press Enter and open the search result with the relevant title.
● Logical File Names
● Protecting Access to the File System Using Logical Path and File Names
● Security Audit Log
22
P U B L I C
Security Guide for SAP S/4HANA 1709
File System Access Security

9 Virus Scanning
Basic Concepts
You need to install and run a VSI 2.0-compliant virus scanner in your landscape. The SAP S/4HANA code calls
this scanner using a dedicated interface during dierent stages of processing - during upload, download, and
passage through the Gateway, and so on. You can customize the interface with the help of scan proles.
For more information about virus scan proles and customizing, see the SAP NetWeaver documentation at
https://help.sap.com/nw75 Application Help Function-Oriented View Security System Security
Virus Scan Interface .
Additional information is available in SAP Notes 786179 and 1494278 .
9.1 Virus Scanning in File Uploads
Example
The system allows uploading of les. For example, users can add an attachment to business documents. Also,
you can upload template les, such as e-mail HTML templates, which can be used to render data on a UI
Once uploaded into SAP S/4HANA, such documents may be displayed in SAP Fiori apps without further
security-related checks. If a document contains malicious content, unintended actions could be triggered when
the item is downloaded or displayed. This can lead to situations, such as cross-site scripting vulnerabilities.
That is why proper virus scanning at upload time is an essential rst line of defense against (stored) XSS
attacks.
For a technical description of this problem see the SAP NetWeaver Security Guide at https://help.sap.com/
nw75 Security Guide English
It is clear that uploaded les need to be scanned for malware. Also, their type needs to be veried against a
white list of MIME-types. You can meet both these requirements by installing and running a VSI 2.0-compliant
virus scanner in your landscape.
SAP S/4HANA code calls the virus scanner (at upload time) through a dedicated interface, which you can
customize. The pre-delivered scan prole, /SCMS/KPRO_CREATE, needs to be adapted according to your
needs. At runtime the virus scanner rejects all upload documents that are not compliant with the rules
specied in the scan prole.
Note
Changes to the scan prole have a global eect. This means, for example, that all uploads ending up in KPro
face the same virus scan settings at runtime.
Security Guide for SAP S/4HANA 1709
Virus Scanning
P U B L I C 23

9.2 General Recommendations for Virus Scan Proles
Selecting Pre-Delivered Scan Proles
As a rst step, you should enable all the pre-delivered scan proles. You should then consider performance
issues when deciding which ones to disable.
Some scan proles take eect at download time. One benet of scanning at download time is that if a virus
signature is updated since upload, it can be caught at download time. So if a compromised le is uploaded, it is
discovered at download. However, download scanning can impact performance. That is because a le is
uploaded only once, but it may be downloaded many times.
If you want to disable download time scanning, disable the following scan proles:
● /SCET/GUI_DOWNLOAD
● /SIHTTP/HTTP_DOWNLOAD
● /SOAP_CORE/WS_SEND
Customer Proles
You should set up the following customer proles:
Name Description
ZBASIC Basic virus scanning prole
ZEXTENDED Same as above with additional check for active content, and
MIME-type detection
All active proles should refer to ZEXTENDED, except the following,which should refer to ZBASIC.
● /SAPC_RUNTIME/APC_WS_MESSAGE_GET
● /SAPC_RUNTIME/APC_WS_MESSAGE_SET
● /SCET/GUI_UPLOAD
● /SIHTTP/HTTP_UPLOAD
● /SMIM_API/PUT
● /SOAP_CORE/WS_RECEIVE
● /UI5/UI5_INFRA_APP/REP_DT_PUT
For ZEXTENDED, the following settings are recommended:
● CUST_ACTIVE_CONTENT = 1
● CUST_CHECK_MIME_TYPE = 1
● CUST_MIME_TYPES_ARE_BLACKLIST = 0
This setting indicates 'whitelisting' - which indicates entities that are OK.
These settings tell the virus scanner to scan for active content and check MIME types according to the
specied whitelist of le types.
24
P U B L I C
Security Guide for SAP S/4HANA 1709
Virus Scanning

Whitelist
Use the 'whitelisting' le type wherever possible.
Consider the following: the whitelist scanner should be as restrictive as possible. As a compromise, the list
should also contain the complete set of le types required in all active customer scenarios. If you need to
extend the whitelist, you should ensure that the list only contains MIME types from the IANA List .
Template List of File Types
Note
Your whitelist should be as restrictive as possible. For example, you should delete non-needed types from
the template list. A nal whitelist is always a compromise between security and functionality.
Use the template list of le types for consideration.
● application/arj
● application/msword
● application/pdf
● application/postscript
● application/vnd.ms-excel
● application/vnd.ms-powerpoint
● application/vnd.openxmlformats-ocedocument.spreadsheetml.sheet
● application/vnd.openxmlformats-ocedocument.presentationml.presentation
● application/vnd.openxmlformats-ocedocument.wordprocessingml.document
● application/x-compressed
● application/x-dvi
● application/x-gzip
● application/x-zip-compressed
● application/xml
● application/zip
● image/bmp
● image/jpeg
● image/png
● image/vnd.dwg
● image/x-dwg
● text/plain
● text/richtext
● text/xml
Security Guide for SAP S/4HANA 1709
Virus Scanning
P U B L I C 25

9.3 Further Protection Against Active Content
Lines of Defense
There are at least two lines of defense against active content. The rst is performing virus scanning in order to
avoid uploading malicious content in the rst place.
The second line of defense is SAP WebDispatcher. An alternative is the Internet Communication Manager
(ICM). These protect against malicious active content being executed at the front end. This uses additional
HTTP-response headers to instruct browsers to behave in a specic way. SAP WebDispatcher and ICM both
oer the possibility to modify HTTP-response headers.
For more information, see Deleting, Adding, and Enhancing HTTP Header Fields in the SAP NetWeaver
documentation at https://help.sap.com/nw75 Internet Communication Manager (ICM) - SAP NetWeaver
Administration of the ICM - SAP NetWeaver Modication of HTTP Requests Deleting, Adding, and
Enhancing HTTP Header Fields .
SAP recommends adding the following headers:
● SetResponseHeader X-Content-Type-Options "nosni"
This tells the browser not to try reading the attached le with the assumed MIME type.
● SetResponseHeader X-XSS-Protection "1; mode=block"
This prevents cross-site scripting.
Example: Example
Consider the following example of script code. It shows how to improve the security level. You need to adapt it
to your own use case.
If %{RESPONSE_HEADER:Content-Disposition} regimatch ^inline [AND]
If %{RESPONSE_HEADER:Content-Type} regimatch html|xml|xsl
Begin
SetResponseHeader Content-Security-Policy "script-src 'none'; sandbox"
SetResponseHeader X-Content-Security-Policy "script-src 'none'; sandbox"
End
If such a Content-Security-Policy header is added to HTTP responses containing previously uploaded les
(when displayed inline and having content type containing html, xml or xsl), the execution of Javascript will be
prevented at the frontend by all up-to-date browser versions.
26
P U B L I C
Security Guide for SAP S/4HANA 1709
Virus Scanning

10 Additional System Hardening Activities
Click-Jacking Protection
Click-jacking is an attack type where an attacker tries to hijack the clicks of an authenticated user in order to
trigger malicious actions. This attack is based on framing the attacked page into an attacker-controlled
enclosing page.
SAP S/4HANA uses a SAP NetWeaver protection to prevent click-jacking attacks. This is a whitelist-based
solution that controls which pages are allowed to render your application within a frame. To enable the
protection, you need to access and edit the whitelist.
A typical setup will contain host/port of the system (as seen from a browser) and host/port of any trusted
system that hosts applications which are going to frame applications from the current system.
For more information, go to http://help.sap.com/s4hana_op_1709, enter Using a Whitelist for Clickjacking
Framing Protection into the search bar, press Enter and open the search result with that title.
SAP GUI for HTML transactions, Web Dynpro applications, and non-SAPUI5-based applications already use
this exible protection mechanism. SAP Fiori launchpad currently uses a slightly dierent, high security
solution.
Unied Connectivity
If your SAP S/4HANA system can be accessed remotely using Remote Function Calls (RFCs), you can
signicantly increase protection by using the Unied Connectivity (UCON) administration framework.
Generally, external access to the function modules using RFCs is controlled by special authorization checks
and the corresponding roles with purpose-specic assignments to users. UCON also provides a simple but
comprehensive way of controlling which Remote Function Modules (RFM) can be called by other systems: an
RFM can only be called externally if it is assigned to a Communication Assembly (CA).
External access is blocked for all RFMs not assigned to a CA. In this way, it is possible to control and restrict
external access to RFMs independently from the user context.
For details, go to http://help.sap.com/s4hana_op_1709, enter Unied Connectivity into the search bar, press
Enter and open the search result with that title.
Switchable Authorizations Check Framework (SACF)
The Switchable Authorizations Check Framework (SACF) provides additional authorization checks for specic
scenarios. These checks do not change the behavior of the application until you activate the respective
scenario. A scenario denition comprises certain authorization objects and rules telling the system how to
check them. An active scenario is a development object, which can be transferred through your landscape.
Security Guide for SAP S/4HANA 1709
Additional System Hardening Activities
P U B L I C 27
By default, most additional scenario-based authorizations checks are initially set to inactive in SAP S/4HANA
(for compatibility reasons).
For more information, see the chapter Activating Switchable Authorization Checks in the SAP Whitepaper
Securing Remote Function Calls which is attached to SAP Note 2008727 .
Note
From a security perspective, SAP strongly recommends to activate all scenario-checks in SAP S/4HANA in
order to maximize the resilience of systems.
Use the transaction SACF for the customizing and transaction SACF_COMPARE for comparison.
Please also read the important information contained in SAP Note 1922808
For more information, go to http://help.sap.com/s4hana_op_1709, enter Customizing Scenario-Based
Authorizations into the search bar, press Enter and open the search result with that title.
Securing CALL TRANSACTION Statements
When a user manually launches an SAP transaction, the ABAP Kernel automatically checks the user’s
corresponding authorization (Authorization Object S_TCODE).
The system behaves dierently if an SAP transaction is called by a program (ABAP statement CALL
TRANSACTION). In this case, the authorization check (S_TCODE-) depends on the system conguration. This
can be controlled using transaction SE97 and prole parameter auth/check/calltransaction.
Two cases exist:
● New installations
We recommend setting the prole parameter auth/check/calltransaction=3. This switches on the
authorization check for CALL TRANSACTION statements – as long as you have not explicitly switched it o
using transaction SE97. This improves the security level because all roles need to contain appropriate
authorizations.
● Installations migrated from an SAP ERP enhancement package to SAP S/4HANA
Roles formerly used in SAP ERP must be examined thoroughly and adopted with care into the new SAP S/
4HANA environment. Only for the sake of a smooth transition you can avoid this temporarily by setting
auth/check/calltransaction=2. This keeps the check behavior as it was before. However, as a
permanent setting this is not recommended, as in the end you should adopt your roles to the new
environment actively and with care.
For details, see the system documentation of transaction SE97.
28
P U B L I C
Security Guide for SAP S/4HANA 1709
Additional System Hardening Activities
11 Data Protection
Use
Data protection is associated with numerous legal requirements and privacy concerns. In addition to
compliance with general data protection acts, it is necessary to consider compliance with industry-specic
legislation in dierent countries. This section describes the specic features and functions that SAP provides
to support compliance with the relevant legal requirements and data privacy.
This section and any other sections in this Security Guide do not give any advice on whether these features and
functions are the best method to support company, industry, regional or country-specic requirements.
Furthermore, this guide does not give any advice or recommendations with regard to additional features that
would be required in a particular environment; decisions related to data protection must be made on a case-by-
case basis and under consideration of the given system landscape and the applicable legal requirements.
Note
In the majority of cases, compliance with data privacy laws is not a product feature.
SAP software supports data protection by providing security features and specic data-protection-relevant
functions such as functions for the simplied blocking and deletion of personal data.
SAP does not provide legal advice in any form. The denitions and other terms used in this guide are not
taken from any given legal source.
Glossary
Term Denition
Personal data Information about an identied or identiable natural per
son.
Business purpose A legal, contractual, or in other form justied reason for the
processing of personal data. The assumption is that any
purpose has an end that is usually already dened when the
purpose starts.
Blocking A method of restricting access to data for which the primary
business purpose has ended.
Deletion Deletion of personal data so that the data is no longer usa
ble.
Retention period The time period during which data must be available.
Security Guide for SAP S/4HANA 1709
Data Protection
P U B L I C 29
Term Denition
End of purpose (EoP) A method of identifying the point in time for a data set when
the processing of personal data is no longer required for the
primary business purpose. After the EoP has been reached,
the data is blocked and can only be accessed by users with
special authorization.
Some basic requirements that support data protection are often referred to as technical and organizational
measures (TOM). The following topics are related to data protection and require appropriate TOMs:
Access control: Authentication features as described in section User Administration and Authentication [page
13].
Authorizations: Authorization concept as described in section User Management [page 13].
Read access logging: as described in section Read Access Logging [page 31].
Transmission control / Communication security: as described in section Network and Communication
Security [page 18].
Input control / Change logging
Availability control as described in:
● Section Data Storage Security [page 22]
● SAP Business Continuity documentation in the SAP NetWeaver Application Help under http://
help.sap.com/s4hana_op_1709
SAP NetWeaver for SAP S/4HANA Function-Oriented View Solution
Life Cycle Management SAP Business Continuity
Separation by purpose: Is subject to the organizational model implemented and must be applied as part of the
authorization concept.
Caution
The extent to which data protection is ensured depends on secure system operation. Network security,
security note implementation, adequate logging of system changes, and appropriate usage of the system
are the basic technical requirements for compliance with data privacy legislation and other legislation.
Conguration of Data Protection Functions
Certain central functions that support data protection compliance are grouped in Customizing for Cross-
Application Components under Data Protection.
Additional industry-specic, scenario-specic or application-specic conguration might be required.
For information about the application-specic conguration, see the application-specic Customizing.
More Information
You can nd detailed information on data protection in the SAP Help Portal athttp://help.sap.com/
s4hana_op_1709 Additional Information Product Assistance Cross Components Data Protection
30
P U B L I C
Security Guide for SAP S/4HANA 1709
Data Protection

11.1 Read Access Logging
Use
Read access to personal data is partially based on legislation, and it is subject to logging functionality. The
Read Access Logging (RAL) component can be used to monitor and log read access to data and provide
information such as which business users accessed personal data (for example, elds related to bank account
data), and when they did so.
In RAL, you can congure which read-access information to log and under which conditions.
SAP delivers sample congurations for applications.
You can display the congurations in the system by performing the following steps:
1. In transaction SRALMANAGER, on the Administration tab page, choose Conguration.
2. Choose the desired channel, for example, WebDynpro.
3. Choose Search. The system displays the available congurations for the selected channel.
4. Choose Display Conguration for detailed information on the conguration. For specic channels, related
recordings are also be displayed.
Note
For a list of the delivered log domains, see the product assistance at SAP Help Portal under http://
help.sap.com/s4hana_op_1709
Product Assistance Cross Components Data Protection .
Prerequisites
Before you can use the delivered RAL congurations, the following prerequisites are met:
● You are using:
○ SAP NetWeaver 7.1:SP0
○ AS ABAP 7.51
○ Kernel 7.49
○ SAP_UI 7.51 (UI5 1.40)
● The RAL congurations have been activated.
● You have enabled RAL in each system client.
More information
For more information, see the following sections on http://help.sap.com/s4hana_op_1709:
● Enter System Security for SAP NetWeaver AS for ABAP Only into the search bar, press Enter and open the
search result with that title. Navigate to the section Read Access Logging.
Security Guide for SAP S/4HANA 1709
Data Protection
P U B L I C 31

● Enter Services for Application Developers into the search bar, press Enter and open the search result with
that title. Navigate to the section Change Documents.
● Enter Read Access Logging (RAL) and OData into the search bar, press Enter and open the search result
with that title.
For up-to-date information on the delivered RAL congurations, see SAPNote 2347271 .
For information on delivered log conditions, see the application-specic chapters of the Security Guide.
11.2 Deletion of Personal Data
Personal data in a system can be blocked as soon as the business activities for which this data is needed are
completed and the residence time for the data has elapsed. After this time, only users who are assigned
additional authorizations can access the data.
When the retention period has expired, personal data can be destroyed completely so that it can no longer be
retrieved. Residence and retention periods are dened in the customer system.
For this purpose, SAP uses SAP Information Lifecycle Management (ILM) to help you set up a compliant
information lifecycle management process in an ecient and exible manner.
More Information
For more information, see the application-specic sections in this security guide as well as at http://
help.sap.com/s4hana_op_1709 under Product Assistance Cross Components Data Protection .
32
P U B L I C
Security Guide for SAP S/4HANA 1709
Data Protection
12 SAP S/4HANA Cross Application
Infrastructure
12.1 Data Security in SAP ILM
SAP ILM oers options for protecting data security from the archiving of data up to its storage and destruction.
All system connections and ILM functions have authorization protection.
Related Information
Data Security in SAP ILM System Connections [page 33]
Users and Authorizations in SAP ILM [page 34]
Security of Stored Data in SAP ILM [page 35]
Logs in SAP ILM [page 36]
12.1.1 Data Security in SAP ILM System Connections
System Landscape Components
The SAP ILM system landscape includes the following main components:
● Application system (AS ABAP)
● WebDAV server on which ILM stores are set up
● System on which the service for the control of ILM stores runs
Since two dierent services are available for controlling ILM stores, two system landscape variants are
possible.
○ The Storage and Retention Service (SRS) runs either in the application system (AS ABAP) or on a
separate AS ABAP.
For more information, see Conguring Storage and Retention Service for ILM Stores under SAP
Information Lifecycle Management.
○ XML Data Archiving Service (XML DAS) runs on an AS ABAP.
For more information, see Conguring XML Data Archiving Service for ILM Stores under SAP
Information Lifecycle Management.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
P U B L I C 33
Data Security for System Connections
Communication between systems takes places with HTTP connections.
HTTP Connection between Application System and ILM Store Service
If the service (SRS or XML DAS) runs on a separate system, you need an HTTP connection from the application
system to that system. You use an HTTP or HTTPS protocol. The conguration of the HTTP connection is
described in the documentation for the relevant service.
If you use the local SRS service of the application system to control ILM stores, you do not need a connection.
HTTP Connection between ILM Store and ILM Store Service
The ILM Stores that are set up on a WebDAV server need to be connected to a service with an HTTP
connection. A WebDAV protocol, which is an enhancement of the HTTP protocol, is used. The conguration of
the HTTP connection is explained in the documentation for the relevant service.
User Authentication for System Connections
The application system can access the service with an HTTP connection only if the connection is made by a
user who has the corresponding authorizations. This user must be created in the system on which the service
run and entered in the data for the HTTP connection.
In the case of a connection from the service to the WebDAV server, user authentication is performed according
to the options oered by the WebDAV server. SAP supports basic authentication with a user of the WebDAV
server (with password) as well as with SSL.
12.1.2 Users and Authorizations in SAP ILM
User
To make SAP ILM available, you need users for the communication between the participating systems (using
HTTP connections).
For more information, see Data Security in SAP ILM System Connections under SAP Information Lifecycle
Management.
Authorizations
SAP delivers roles with the relevant authorizations for access to the functions of SAP ILM.
For more information, see the following topics under SAP Information Lifecycle Management:
Assigning Authorizations for Retention Management Cockpit
Assigning Authorizations for Retention Warehouse Cockpit
Transactions and Authorizations in SAP NetWeaver ILM
34
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure

12.1.3 Security of Stored Data in SAP ILM
Security of Archived Data in the File System
When storing archived data in the le system, you have read and write access to the le system with the
technical system user of the SAP system. The system temporarily moves the archive les to the le system and
then deletes them after forwarding them to the ILM store. The archive les in the le system and the ILM store
are stored not in plain text but in binary text in an SAP-specic, compressed format.
A logical path denes the storage location of the archived data in the le system. You need to specify this path
in Customizing for the archiving object.
For more information, see:
Data Archiving in the SAP NetWeaver Library
Security Guide for ADK-Based Data Archiving in the Security Guide of the SAP NetWeaver Library
Security of Data in the ILM Store
To guarantee the non-changeability of data and the protection from early deletion, the resources (archive les)
and their higher level collections (hierarchy nodes of the store) are stored on an ILM-certied WebDAV server.
Metadata Security in the Store Hierarchy
To manage the store hierarchies, the service that you use to manage ILM stores saves the metadata to the
system database. Depending on which service you use, the storage location of the metadata is:
ILM Store Service Metadata Storage Location
Storage and Retention Service (SRS) Database of the AS ABAP on which the SRS runs
XML Data Archiving Service (XML DAS) Database of the AS ABAP on which XML DAS runs
XML DAS uses the database pool alias SAP/BC_XMLA.
You can guarantee the security of the metadata with the standard functions of the database you are using.
For more information, see: Database Access Protection, Security Aspects for Database Connections in the SAP
NetWeaver Library.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
P U B L I C 35

Backup of Complete Data in the Retention Warehouse System
To ensure that the dataset you are managing in Retention Warehouse is still complete after the transfer from
the legacy system, use the checksums function before and after the transfer and the ILM-compliant conversion
of the data (archive les).
12.1.4 Logs in SAP ILM
In SAP ILM, logging depends on the service you use to control the stores.
Service Used Type of Log File Server Description
Storage and Retention
Service (SRS)
Log File for SRS AS ABAP on which SRS
runs (application system
or separate system)
Can be called in application log
Log object: ILM
Subobject: ILM_SRS
XML Data Archiving
Service (XML DAS)
Log File for XML
DAS
AS Java on which XML
DAS runs
Can be called in LogViewer
File: applications.log
Category: /Applications/Common/
Archiving/XML_DAS
Trace File for XML
DAS
AS Java on which XML
DAS runs
Can be called in LogViewer
File: defaultTrace.trc
Location: com.sap.archtech.daservice
Service-Independent Log File of Connec
tor
Application system (AS
ABAP)
Can be called in the job log for AS ABAP
System Log (sy
slog)
Application system (AS
ABAP)
Entry in the system log (operation trace) with
message ID DA1 and problem class S for each
deletion of a resource or collection in the ILM
store
36 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
Service Used Type of Log File Server Description
Log Files for ILM
Functions
Application system (AS
ABAP)
Can be called in application log
Log object: ILM
Subobjects:
● ILM_ALINK_REFERENCES (ArchiveLink
references)
● ILM_CHANGE_RETENTION (Change of
retention period)
● ILM_CHECKSUM (Checksum generation)
● ILM_DESTRUCTION (Data destruction)
● ILM_LEGAL_CASE (Set legal holds)
● ILM_LH_PROPAGATION (Using holds on
data)
● ILM_SWISS_KNIFE (Enhancing CDE
contents in RW)
● ILM_TRANS_ADMIN (Transfer of archive
administration data from the legacy sys
tem to RW)
● ILM_UOM (Comparing units of measure
in RW)
● IRM_RT (Rule determination)
● GENERATE (Generating BW objects)
● TRANSFER (Transferring table structures
from RW to BW)
● TRANSFER_VIEW (Transferring data
views from RW to BW)
● DELETE (Deleting BW objects and data)
● WP_CREATE (Creating audit packages in
RW)
12.2 Payment Card Security
12.2.1 Before You Start
Since the measures described in this guideline for security in the use and administration of payment cards
apply in various applications, see the security guides for those particular applications.
The most important SAP Notes that apply to secure handling of payment card data are shown in the table
below.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
P U B L I C 37
SAP Note Title Comment
1032588
Secure handling of credit card data in
S/4HANA
1151936
Key replacement for encryption of pay
ment card data
662340
SSF Encryption using SAPCryptolib
1394093
Security collective note Summarizes information about various
security-relevant problems
12.2.2 Authorizations
The functions for secure handling of payment cards use the authorization concept provided by SAP
NetWeaver. Therefore, the recommendations and guidelines for authorizations as described in the SAP
NetWeaver AS ABAP security guide also apply to the secure handling of payment cards.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
the role maintenance for ABAP technology, use the prole generator (transaction PFCG).
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used as part of secure handling of
payment cards.
Authorization Object Field Value Description
B_CCSEC ACTVT 03 Display of unmasked pay
ment card numbers
B_CCSEC ACTVT 06 Deletion of data records no
longer needed and log en
tries for displaying payment
card data
B_CCSEC ACTVT 71 Display of log entries for dis
playing payment card data
SSFVADM ACTVT
SSFVAPPLIC
01
PAYCRV
Generating a key version
38 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
Authorization Object Field Value Description
ACTVT
SSFVAPPLIC
06
PAYCRV
Deleting a key version
ACTVT
SSFVAPPLIC
42
PAYCRV
Execution of migration pro
grams for SSF application
PAYCRV
12.2.3 Data Storage Security
Use
Since payment card data is needed by many dierent applications for operational processes, the data is stored
on the database. If you choose the security level Masked Display, and Encrypted When Saved, the system stores
payment card numbers in encrypted form on the database in the following database tables:
Database Table Use Comment
PCA_SECURITY_RAW Payment Cards and SAP Business Part
ner
In S/4HANA systems, you must exe
cute a migration program.
CCARDEC Payment Cards in FI, SD and Customer
Master
CCSEC_ ENC Other payment card processes The table is used if the indicator for pe
riodic key replacement is not set in
Customizing.
CCSEC_ENCV Other payment card processes The table is used if the indicator for pe
riodic key replacement is set in Cus
tomizing.
The application database tables refer to these encrypted storage tables.
You can archive and delete the data using the following archiving objects or deletion programs:
Database Table Deletion/Archiving Comment
PCA_SECURITY_RAW Archiving using archiving object
CA_PCA_SEC
CCARDEC Deletion using program CCARDEC_DE
LETE
If the data is used in an unarchived FI
document, customer master record, or
order, the data is not deleted.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
P U B L I C 39

Database Table Deletion/Archiving Comment
CCSEC_ ENC Archiving using archiving object
CA_PCA_ SEC
CCSEC_ENCV Deletion using program RCCSECV_
DATA _ DEL
The data cannot be deleted unless the
last use was more than 500 days in the
past.
12.2.4 Setting Up Encryption Software
To be able to encrypt payment card data in the system, you must install the function package SAPCRYPTOLIB.
The function package SAPCRYPTOLIB contains the functions necessary for encryption. To execute the
encryption software, you have to make general settings in Customizing for SAP NetWeaver. Choose
Application Server System Administration Maintain the Public Key Information for the System .
For more information, see SAP Note 662340.
12.2.5 Making Settings for Payment Card Security
You make settings for payment card security in Customizing for Cross-Application Components under
Payment Cards Basic Settings Make Security Settings for Payment Cards .
The following explanations refer to the settings there.
Security Level
You can select from the following options:
● No Additional Security Measures
● Masked Display, Not Encrypted When Saved
● Masked Display and Encrypted When Saved
Masked display means that when you display or change objects that contain a payment card number, the
system hides part of the number.
Example
For payment card number 1111222233334444, the system displays a value of 1111********4444.
You can specify the number of visible characters at the beginning and end of the payment card number. The
security standards of the payment card industry demand that a maximum of six characters are visible at the
beginning, and four at the end.
40
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure

This masked display is applied for all types of payment cards. If you also select encrypted saving, then the
system applies this only to those payment card types that you specied explicitly in Customizing (see the
section "Relevant Payment Card Types").
We recommend that you use the security level Masked Display, and Encrypted When Saved. You should specify
the smallest number of visible characters possible that allows the payment cards to be identied (for example,
using the last four characters).
Unmasked Display
If card numbers are displayed in masked format, it is still sometimes necessary to display the number
unmasked. In various transactions, we therefore provide a function for unmasked display of payment card
numbers. You can make two specications for this function in Customizing:
● Access log
● Additional authorization check
You can have the system record each display of an unmasked payment card in an access log. This enables you
to monitor which users have displayed which payment card numbers and when.
You can use an additional authorization check for authorization object B_CCSEC to restrict the use of the
display of unmasked card numbers.
We recommend that you activate this additional authorization check and assign the appropriate authorization
only to those user groups that need to access unmasked card numbers as part of their daily work. You should
also activate the access log.
Analyzing Access Logs
You can run reports on accessing of payment card data. For more information, see Security-Relevant Logs and
Tracing [page 45].
Key Replacement
By setting the Key Replacement Active indicator, you specify that the system supports periodic replacement of
the keys (PSEs) used for encryption.
Caution
This indicator is visible only if you installed S/4HANA 6.0 with Enhancement Package 4 and activated the
business function Periodic Key Replacement for Payment Card Encryption (PCA_XKEYV).
We recommend that you set this indicator.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
P U B L I C 41

Relevant Payment Card Types
You can choose the card types (such as, AMEX, Mastercard, VISA) for which you want to activate encryption.
The collumn for this is not visible in the settings for the payment card unless you have already made settings
for payment card encryption in the business partner. This means that you have to have already executed the
migration program or to have set up encrypted saving of further data records. You can make these settings in
Customizing for Cross-Application Components under Payment Cards Basic Settings Maintain Payment
Card Type .
12.2.6 Relevant SSF Applications
For encryption and decryption using the SSF Framework, the applications communicate using an SSF
application. The keys (PSEs) used for encryption and decryption are generated for each SSF application.
If you have not activated key replacement, then, for technical reasons, various SSF applications exist for the
various storage les of encrypted payment card data. If you set the Key Replacement Active indicator, then only
the SSF application PAYCRV is used after that point.
Application
SSF Application, If Key Replacement
Inactive
SSF Application, If Key Replacement
Active
Payment Cards and SAP Business Part
ner
PAYCRD (in S/4HANA systems) PAYCRV
Payment Cards in FI, SD and Customer
Master
CCARD PAYCRV
Other payment card processes PAYCRD PAYCRV
The SSF application PAYCRV supports management of multiple key versions. This is not the case with the SSF
applications PAYCRD and CCARD. Therefore, using the SSF application PAYCRV is mandatory for the process
of periodic key replacement.
12.2.7 Generating Keys
The generation of the keys (PSEs) used for encryption and decryption diers depending on the SSF
application:
● SSF Application *PAYCRV
To generate a key version, on the SAP Easy Access screen, choose Cross-Application Components
Security of Payment Card Data Encryption of Payment Cards Administration of Key Versions for
PAYCRV . The system automatically generates the PSEs and distributes them to the application servers.
You can display them in the transaction STRUST (Trust Manager).
42
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure

The transaction for administration of key versions, in addition to the overview of already generated key
versions, also provides information on how many data records are encrypted and stored on the database
for a version. There you can create new key versions and delete key versions that are no longer used.
● SSF Applications CCARDEC and PAYCRD
In transaction SSFA, create a new entry for an SSF application. Create the PSE in transaction STRUST, and
make sure that you use the algorithm RSA.
12.2.8 Migration of Payment Card Data Stored in
Unencrypted Form
You can use several migration programs to migrate payment card data stored in unencrypted form to
encrypted payment card data. These programs comply with the naming convention RCCSEC_MIGRATION_*.
For information on which program you can use for your system, see the documentation of the individual
programs.
You execute the program to store all payment card data in your system in encrypted form. For operative
processes, you do not have to execute the migration programs. In addition, you can perform the conversion in
several individual steps, whereby you convert only part of the data in each step.
Note that there are special issues related to the SAP Business Partner. For more information, see this section
[page 43].
12.2.9 Migration of Payment Card Data on SAP Business
Partner
The following section is relevant for you only if you use the SAP business partner.
For the SAP business partner in S/4HANA systems to support encrypted storage of payment card data, a one-
time data migration is required.
Before this migration, the system manages the payment card data in the database tables listed below (among
others). In both tables, the payment card number is in plain text.
Database Table Use
CCARD Data of payment card
BUT0CC Relationship between SAP business partner and payment
card using CCINS and CCNUM
You migrate the data of database table CCARD completely to the database tables PCA_SECURITY_*. On the
SAP Easy Access screen, choose Cross-Application Components Security of Payment Card Data
Encryption of Payment Cards Migration of Credit Cards . The encrypted value of the credit card number is
stored during this process in the table PCA_SECURITY_RAW. The relationship to the credit card is reected in
table CCARD by the eld CARD_GUID, and the elds CCNUM and CCINS are initialized. The system considers
only those entries in table CCARD that are still used in table BUT0CC.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
P U B L I C 43
Database Tables
Database Table Use
PCA_SECURITY_* Data of payment card
BUT0CC Relationship between SAP business partner and payment
cards using CARD_GUID
When migrating using the above program, you cannot spread the conversion over time. That means you have
to completely convert the data in one run. The actual encryption can either take place directly during the
migration, or you can encrypt the data later using program PCA_MASS_CRYPTING.
You are required to run the migration program even if you have not yet stored any payment card data in the
business partner data (for instance, at the time of installation), but you want to store encrypted data in the
future.
You cannot work with the system during the migration or after a partially successful migration, since it is not
possible to predict how the executing programs will react. However, severe inconsistencies are to be expected.
To execute the migration program, you need an access code that SAP provides upon request. To request this
code, enter a customer message under component AD-MD-BP. Refer to this security guide or to SAP Note
1032588.
For security reasons, the system stores a backup copy of the table entries in table CCARD_COPY. After you
have ensured that the system works correctly after the migration, you can delete the backup copy using
program RCC_MIGRATION_DEL_COPY.
If you are using Contract Accounts Receivable and Payable (FI-CA), and are using the business partner shadow
table there to improve the performance of mass runs, also see the explanations in the Security Guide for
Contract Accounts Receivable and Payable in the section Payment Card Industry Data Security Standard [page
62].
12.2.10 Migration to SSF Application PAYCRV
If you already encrypted credit card data in the system (using the SSF applications PAYCRD or CCARD), you
can migrate this data to the SSF application PAYCRV. As a result, the system then also replaces the keys for this
data on a periodic basis.
Start the migration on the SAP Easy Access screen under Cross-Application Components Security of
Payment Card Data Encryption of Payment Cards Migration to SSF Application PAYCRV . You can migrate
each of the aected database tables individually and you can enter a maximum runtime. This means that in
this case you can spread the conversion out over time.
12.2.11 Migration to Current Key Version
Once you have generated a new key version, you can migrate the data, which was encrypted and stored under
an older key version, to the current key version. During this process, the system decrypts the data record with
44
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure

the older key version, encrypts the data with the current key version, and updates the database tables. After
the migration is complete, the system does not contain any more data records that still use the older key
version. At that point in time, you can specify that the older key version is deletable.
To run the migration, on the SAP Easy Access screen, choose Cross-Application Components Security of
Payment Card Data Encryption of Payment Cards Execute Conversion . You can dene parallel processing
for the migration using the subarea. The entire dataset is divided into subareas represented by the numbers
000 to 999. The subareas contain a roughly equal number of encrypted records. You can start the migration
program with intervals determined by the subarea, so that up to 1000 parallel jobs are possible. In addition, you
can enter a maximum runtime. This means that you can make the conversion in stages.
12.2.12 Deleting a Key Version
Once the data of an old key version has been migrated completely to the current key version, the old key
version receives the status deletable. To ensure the utmost security, the earliest the key version can actually be
deleted is after an additional waiting period of 90 days after the successful migration.
12.2.13 Security-Relevant Logging and Tracing
Use
You can have the system log users' access to unmasked payment card data. In Customizing, choose the setting
Access Log: Logs for Unmasked Display (see Making Settings for Payment Card Security [page 40]).
The system updates the log on database table CCSEC_LOG. You can carry out an analysis via the SAP Easy
Access screen, under Cross-Application Components Security of Payment Card Data Encryption of
Payment Cards
Evaluate Payment Card Log . To analyze the access log, you need authorization for activity
71 of authorization object B_CCSEC.
You can delete log records if they are at least one year old. To delete the records, on the SAP Easy Access
screen choose Cross-Application Components Security of Payment Card Data Encryption of Payment
Cards
Delete Payment Card Log . To be able to run the deletion report, you need authorization for object
B_CCSEC with activity 06.
12.2.14 Recommended Implementation Steps
The following recommended implementation steps dier according to which of the following situations apply to
you:
● You did not yet set a security level.
● You are already using the security level for saving payment card numbers in encrypted form, and you now
want to implement the process for periodic key replacement.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure
P U B L I C 45

Variant 1: Security Level Not Yet Set
If you have not yet set a security level in Customizing, follow these steps to implement the process for
encrypted storage and periodic key replacement for payment card numbers.
1. Create a key version. To do so, on the SAP Easy Access screen, choose Cross-Application Components
Security of Payment Card Data Encryption of Payment Cards Administration of Key Versions for
PAYCRV
. (See Generating Keys [page 42])
2. Make settings for payment card security (see Making Settings for Payment Card Security [page 40]).
1. Set the security level Masked Display, and Encrypted When Saved.
2. Activate the access log.
3. Activate the additional authorization checks for unmasked display and set up the user authorizations
accordingly.
4. Set the number of visible characters at the beginning and end of the payment card number.
5. Activate the key replacement.
3. Specify the payment card types that you want to save in encrypted form. (See Making Settings for
Payment Card Security [page 40])
4. Migrate the payment card data that was stored in unencrypted form. (See Migration of Payment Card Data
Stored in Unencrypted Form)
5. If you use SAP Business Partner, migrate your payment card data on SAP Business Partner. (See Migration
of Payment Card Data on SAP Business Partner [page 43])
Variant 2: Security Level "Masked Display, and Encrypted When Saved"
Already Used
If you already set the security level Masked Display, and Encrypted When Saved in Customizing, and you already
migrated the legacy data when implementing the security level, then perform the following steps to implement
the process of periodic key replacement.
1. Create a key version. To do so, on the SAP Easy Access screen, choose Cross-Application Components
Security of Payment Card Data Encryption of Payment Cards Administration of Key Versions for
PAYCRV .
2. Activate the key replacement. (See Making Settings for Payment Card Security [page 40])
3. Migrate the stored encrypted data to the SSF application PAYCRV (see Migration to SSF Application
PAYCRV [page 44]).
46
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Cross Application Infrastructure

13 SAP S/4HANA Business Applications
13.1 Asset Management
13.1.1 Maintenance Operations
13.1.1.1 Authorizations in Plant Maintenance
Standard Roles
SAP delivers business role templates which follow the naming convention SAP_BR_*. The delivered business
role templates are designed to cover typical activities of business users with a certain job prole.
Example
The delivered business role template SAP_BR_MAINTENANCE_TECHNICIAN is designed for maintenance
technicians. The role contains business catalogs which cover all the functions that a maintenance technician
requires to carry out their work eectively and safely.
Another example business role template SAP_BR_MAINTENANCE_PLANNER is designed for maintenance
planners. The role contains business catalogs which cover a broad range of functions necessary for planning
and executing maintenance activities.
Each business catalog contains one or more applications and is designed to support segregation of duty.
Note
For more information about how to create roles, see Role Administration [page 16].
13.1.2 Environment, Health and Safety
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 47
13.1.2.1 User Administration and Authentication
Environment, Health, and Safety (EHS) uses the authorization concept provided by the SAP NetWeaver AS for
ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver
AS Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
For more generic information see User Administration and Authentication [page 13] in the Introduction section.
13.1.2.1.1 User Management
The table below shows the standard users that are necessary for operating Environment, Health, and Safety
(EHS). For more generic information see User Management [page 13] in the Introduction section.
User ID Type Password Description
Business processing user Dialog user To be entered Business user of EHS
E-mail inbound processing
user
Communication user Not needed User to process the incoming
e-mails of EHS
Workow engine batch user Background user Not needed User for the background
processing of workows in
EHS
You need to create the users after the installation. Users are not automatically created during installation. In
consequence there is no requirement to change their user IDs and passwords after the installation.
Note
Several business processes within EHS use SAP Business Workow and e-mail inbound and outbound
processing. It is not recommended that you grant the corresponding system users (such as WF_BATCH for
Workow System or SAPCONNECT for e-mail inbound processing) all authorizations of the system
(SAP_ALL).
13.1.2.1.2 Communication Destinations
The table below shows an overview of the communication destinations used by Environment, Health, and
Safety (EHS). For more generic information, see the corresponding chapter in the Introduction section.
48
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Destination Delivered Type Description
<MOC system> No RFC (3, H) Connection to the SAP Management of Change system
(ABAP/3- and HTTP/H-Connection)
<OH system> No RFC Connection to the Occupational Health application of
SAP EHS Management as part of the SAP ERP system
<EWM system> No RFC Connection to the Extended Warehouse Management
system
Note
EHS does not provide any authorizations for:
● SAP Management of Change
● Occupational Health of SAP EHS Management as part of SAP ERP
For detailed information about communication destinations, see Customizing for Environment, Health, and
Safety under Foundation for EHS Integration Specify Destinations for Integration .
13.1.2.2 ICF Security in Environment, Health, and Safety
To use an app in Environment, Health, and Safety, you have to activate the internet communication framework
(ICF) service that is needed for this app.
For general information, see ICF Security [page 20] in the Introduction section.
Incident Management
To use Incident Management apps, proceed as follows:
● In your front-end system, open transaction SICF. Under /default_host/sap/bc/ui5_ui5/sap/,
activate the following UI5 services:
○ repincidents1 (Report Incident)
○ injillanalyss1 (Injuries and Illnesses - Detailed Analysis)
○ incdntanalyss1 (Incidents - Detailed Analysis)
● In your back-end system, open transaction SICF. Under /default_host/sap/bc/webdynpro/sap/,
activate all Web Dynpro services that start with ehhss and ehfnd.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 49
Health and Safety Management
To use Health and Safety Management apps, proceed as follows:
● In your front-end system, open transaction SICF. Under /default_host/sap/bc/ui5_ui5/sap/,
activate the following UI5 services:
○ /sap/bc/ui5_ui5/sap/sbrt_appss1 (Approved Chemicals, Risk Overview)
○ /sap/bc/ui5_ui5/sap/ehschm_reps1 (Chemical Risk Report)
○ /sap/bc/ui5_ui5/sap/ehschm_achs1 (Monitor Approved Chemicals)
○ /sap/bc/ui5_ui5/sap/ehscha_mycs1 (My Chemical Approvals)
○ /sap/bc/ui5_ui5/sap/ehsrisk_lsts1 (Monitor Risks)
○ /sap/bc/ui5_ui5/sap/ehsras_lsts1 (My Risk Assessment Projects)
● In your back-end system, open transaction SICF. Under /default_host/sap/bc/webdynpro/sap/,
activate all Web Dynpro services that start with ehhss and ehfnd.
Environment Management
To use Environment Management apps, proceed as follows:
● In your back-end system, open transaction SICF. Under /default_host/sap/bc/webdynpro/sap/,
activate all Web Dynpro services that start with ehenv and ehfnd.
13.1.2.3 Data Storage Security
Using Logical Path and File Names to Protect Access to the File System
In Environment, Health, and Safety (EHS), the XML export for Incident Management saves data in les in the le
system. Therefore, it is important to explicitly provide access to the corresponding les in the le system
without allowing access to other directories or les (also known as directory traversal). This is achieved by
specifying logical paths and le names in the system that map to the physical paths and le names. This
mapping is validated at runtime and if access is requested to a directory that does not match a stored
mapping, then an error occurs.
The following lists show the logical le names and paths used by EHS and for which programs these le names
and paths apply:
Logical File Names Used
The following logical le name has been created in order to enable the validation of physical le names:
● EHHSS_INCIDENTS_XML
50
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
○ Program R_EHHSS_ALL_INC_TO_XML is using this logical le name and parameters used in this
context.
Logical Path Names Used
The logical le names listed above all use the logical le path EHHSS_BO_XML_EXPORT_PATH.
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out which
paths are being used by your system, you can activate the corresponding settings in the Security Audit Log.
For more information on data storage security, see the respective chapter in the SAP NetWeaver Security
Guide.
13.1.2.4 Data Protection
Data protection is very important in the following examples:
● In the incident management process, you have critical person-related information regarding absences or
injuries.
● In the health and safety management process, personal data about the risk assessment lead and the other
persons involved in a risk assessment are displayed.
● In the environment management process, data about persons assigned to, compliance scenarios, and
persons involved in tasks of category Action, is displayed.
Environment, Health, and Safety (EHS) assumes that agreements for storage of personal data are covered in
individual work contracts. This also applies to notications on initial data storage.
For more generic information, see Data Protection [page 29] in the Introduction section.
13.1.2.4.1 Deletion of Personal Data
Use
The Environment, Health, and Safety (EHS) component might process data (personal data) that is subject to
the data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management
(ILM) to control the blocking and deletion of personal data in EHS.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 51

For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal at http://
help.sap.com/s4hana_op_1709 under Product Assistance Cross Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
The following tables list the relevant application objects and the available deletion functionality for Incident
Management, Health and Safety Management, and Environment Management.
Application Objects and Available Deletion Functionality in Incident Management
Application Objects Provided Deletion Functionality
Incidents Archiving object EHHSS_INC
Incident Summary Reports Archiving object EHHSS_ISR
For more information about application objects and deletion functionality, see the product assistance for SAP
S/4HANA
on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 under Product Assistance
Enterprise Business Applications Asset Management Environment, Health, and Safety Incident
Management (EHS-SUS-IM) Data Archiving in Incident Management .
Application Objects and Available Deletion Functionality in Health and Safety Management
Application Objects Provided Deletion Functionality
Risk Revisions Archiving object EHHSS_RSV
Risks Archiving object EHHSS_RSK
Risk Assessments Archiving object EHHSS_RAS
Safety Instructions Archiving object EHHSS_SI
Control Evaluations Archiving object EHHSS_CEVL
Control Inspections Archiving object EHHSS_CINS
Control Replacements Archiving object EHHSS_CRPL
Sampling Campaigns Archiving object EHHSS_SPLC
Samplings Archiving object EHFND_SPLG
Chemical Approvals Archiving object EHFND_CHA
Assignment of Person to Locations Archiving object EHFND_LOCP
Assignment of Person to Jobs Archiving object EHFND_JOBP
52 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Objects Provided Deletion Functionality
Sampled Person Data destruction object EHFND_SPLNG_SAMPLED_PERSON
For more information about application objects and deletion functionality, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 under Product Assistance
Enterprise Business Applications Asset Management Environment, Health, and Safety Health and Safety
Management (EHS-SUS-HS)
Technical Solution Information . You can nd the information under the
following nodes:
● Data Archiving in Health and Safety Management
● Data Destruction in Health an Safety Management
Application Objects and Available Deletion Functionality in Environmental Management
Application Objects Provided Deletion Functionality
Compliance Scenario Actions Archiving object EHENV_SAC
For more information about application objects and deletion functionality, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 under Product Assistance
Enterprise Business Applications Asset Management Environment, Health, and Safety Environment
Management (EHS-SUS-EM)
Data Archiving in Environment Management .
Relevant Applications and Available End of Purpose Checks
In addition to destroying data used for incident management, health and safety management, or environment
management processes, EHS provides end of purpose checks (EoP) for central business partners. These
checks determine whether dependent data for a certain central business partner is still relevant for business
activities in EHS.
The following table lists the registered applications and the function module used for the end of purpose
checks in EHS.
Application End of Purpose Check Further Information
Incident Management (EHS_INC)
EHHSS_INC_EOP_CHECK_BP
The check determines whether the
business partner is used in:
● Incidents
● Tasks in incidents
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 53

Application End of Purpose Check Further Information
Health and Safety (EHS_HS)
EHHSS_HS_EOP_CHECK_BP
The check determines whether the
business partner is used in:
● Risk assessment projects
● Tasks in risk assessment projects
● Risks
● Control inspections
● Control evaluations
● Control replacements
Health and Safety (EHS_HS_EXPOSURE)
EHHSS_EXP_EOP_CHECK_BP
The check determines whether the
business partner is assigned to:
● Job positions
● Location positions
● Samplings as sampled person
Environment Management (EHS_ENV)
EHENV_EOP_CHECK_BP
The check determines whether the
business partner is used in tasks of cat
egory Action.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
under
Cross-Application Components Data Protection Blocking and Unblocking of Data Business
Partner .
13.1.2.4.2 Read Access Logging of Personal Data in Incident
Management
Use
In Read Access Logging (RAL), you can congure which read-access information to log and under which
conditions.
SAP delivers sample congurations for applications.
Incident Management logs data of illnesses or injuries that are maintained in the Edit Incident screen (web
dynpro application EHHSS_INC_REC_OIF_V3). Since this information is potentially sensitive and access to this
information is in some cases legally regulated, you can use RAL to log the date when the data was accessed
and by whom.
54
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

In the following congurations, the following elds are logged:
Conguration Fields Logged Business Context
Involved Person - Basic Information <concatenate name>
● Injured Person Name
● Phone Number
● Email
Role(s)
Incident Type
Privacy Case
Injured on Site
Injured on Duty
Additional Criteria
Fatality
Location of Death
Cause of Death
Statement of Involved Person
Logs basic information of the person
who is involved in the incident.
Involved Person - Injury-Illness Informa
tion
<concatenate name>
● Injured Person Name
● Phone Number
● Email
Classication
Injury/Illness Type
Injury/Illness Description
Body Part
Body Part Description
Body Side
Logs information on the injuries or the
illness of the person who is involved in
the incident.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 55

Conguration Fields Logged Business Context
Involved Person - Treatment Informa
tion
<concatenate name>
● Injured Person Name
● Phone Number
● Email
First Physician
Further Treatment Provider
Treatment Beyond First Aid
Emergency Room
Inpatient Overnight
Unconsciousness
Immediate Resuscitation
Comment
To First Aid
To Further Treatment
Logs information on the treatment of
the person who is involved in the inci
dent.
Involved Person - Reports and Docu
ments
<concatenate name>
● Injured Person Name
● Phone Number
● Email
File Name (of report forms)
File Name (of documents)
Logs the les of reports and documents
that are assigned to the involved per
son.
Incident - Reports and Documents File Name (of report forms)
Reference (Report forms of person ref
erences)
File Name (of documents)
Reference (documents of person refer
ences)
Logs the les of reports and documents
that are assigned to the incident.
Further Information
You can nd the congurations as described in the Read Access Logging [page 31] chapter.
56
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.1.2.5 Virus Scanning
The interactive forms of Environment, Health, and Safety (EHS) can contain Java Script. Therefore, Java Script
must be enabled in Adobe Acrobat Reader. In addition, e-mails with PDF attachments that contain Java Script
must not be ltered out in the e-mail inbound and outbound process.
For more generic information see Virus Scanning [page 23] in the Introduction section.
13.1.2.6 Other Security-Relevant Information
The following information is relevant for the security of Environment, Health, and Safety (EHS).
13.1.2.6.1 Dispensable Functions with Impacts on Security
Environment, Health, and Safety (EHS) can be integrated with HR Time Management in Customizing. If the
personnel time management (PT) integration is activated, time data (including absences) from HR is displayed
in the incident. An additional option is available to trigger the creation HR Absences from the incident. For all
actions, HR authorizations are checked.
13.1.2.6.2 Security Settings for the Report Incident App
You use the SAP Cloud Platform, mobile service for SAP Fiori to implement the app Report Incident. For more
information on the security settings of the SAP Cloud Platform, mobile service for SAP Fiori, see the SAP Help
Portal at https://help.sap.com . There, search for SAP Cloud Platform, mobile service for SAP
Fiori User Guide.
13.2 Commerce
13.2.1 Commerce Management
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 57

13.2.1.1 Convergent Invoicing, Receivables Mngmt and
Payment Handling
The following section provides an overview of the security-relevant information that applies to Convergent
Invoicing and Receivable Management and Payment Handling as part of Contract Accounts Receivable and
Payable (FI-CA).
13.2.1.1.1 Data Storage Security
Contract Accounts Receivable and Payable (FI-CA) saves data in les in the le system. Therefore, it is
important to explicitly provide access to the corresponding les in the le system without allowing access to
other directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
The following list shows the logical le names and paths used by Contract Accounts Receivable and Payable
(FI-CA) and for which programs these le names and paths apply:
Logical File Names Used in FI-CA and Logical Path Names
The following logical le names have been created in order to enable the validation of physical le names:
Program Logical File Name Used by the Pro
gram
Logical Path Name Used by the Pro
gram
RFKIBI_FILE00 FICA_DATA_TRANSFER_DIR FICA_DATA_TRANSFER_DIR
RFKIBI_FILEP01
RFKKBI_FILEEDIT
RFKKBIBG
RFKKZEDG
RFKKRLDG
RFKKCMDG
RFKKCRDG
RFKKAVDG
RFKKBIB0
58 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

RFKKZE00
RFKKRL00
RFKKCM00
RFKKCR00
RFKKAV00
RFKKKA00
RFKKBIT0
RFKKPCSF FI-CA-CARD-DATA-S FI-CA-CARD-DATA-S
RFKKPCDS
RFKKCVSPAY FI-CA-CVS FI-CA-CVS
RFKK_CVSPAY_CONFIRM
RFKKCVSCONFIRMDB
RFKK_CVSPAY_CONFIRM_TEST
RFKK_DOC_EXTR_EXP FI-CA-DOC-EXTRACT-DIR FI-CA-DOC-EXTRACT-DIR
RFKK_DOC_EXTR_AEXP
RFKK_DOC_EXTR_IMP
RFKK_DOC_EXTR_EXTR
RFKK_DOC_EXTR
RFKK_DOC_EXTR_DEL
Class CL_FKK_TEXT_FILE
RFKKBIXBITUPLOAD FI-CA-BI-SAMPLE
FI-CA-BI-SAMPLE-DIR
FI-CA-BI-SAMPLE-DIR
RFKKCOL2 FI-CA-COL-SUB FI-CA-COL-SUB
RFKKCOLL
Transaction FP03DM (Mass Activity)
Transaction FPCI (Mass Activity)
FI-CA-COL-INFO FI-CA-COL-INFO
RFKKCOPM FI-CA-COL-READ FI-CA-COL-READ
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 59
READFILE
RFKKCOPG FI-CA-COL-TEST FI-CA-COL-TEST
RFKKRDI_REPORT FI-CA-RDI FI-CA-RDI
RFKKRDI_REPORT_DIS
SAPFKPY3 FI-CA-DTA-NAME FI-CA-DTA-NAME
RFKKCHK01 FI-CA-CHECKS-EXTRACT FI-CA-CHECKS-EXTRACT
Class CL_FKK_INFCO_SEND
FI-CA-INFCO FI-CA-INFCO
RFKKBE_SAL1
RFKKBE_SAL2
FICA_BE_SAL FICA_BE_SAL
FICA_BE_SAL_XML FICA_BE_SAL_XML
RFKK1099 FI-CA-1099 FI-CA-1099
RFKKOP03 FICA_OPEN_ITEMS FICA_OPEN_ITEMS
RFKKOP04
RFKKOP07
RFKKES_SAL1 FICA_TAX_REP_GEN FICA_TAX_REP_GEN
RFKKES_SAL2
RFKKRDI_REPORT FI-CA-RDI FI-CA-RDI
RFKKRDI_REPORT_DIS
Transaction EMIGALL
ISMW_FILE ISMW_ROOT
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out
which paths are being used by your system, you can activate the corresponding settings in the Security Audit
Log.
For more information about data storage security, see the chapter in the SAP NetWeaver Security Guide.
60
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.2.1.1.2 Data Protection
Contract Accounts Receivable and Payable (FI-CA) processes personal data of business partners that might be
subject to data protection legislation applicable in some countries.
Contract Accounts Receivable and Payable (FI-CA) uses SAP ILM to support the deletion of this personal data.
SAP delivers an end of purpose check for Contract Accounts Receivable and Payable (FI-CA). You register the
end of purpose check (EoP) in the Customizing settings for the blocking and deletion of the SAP Business
Partner.
Display of Blocked Data
Only if a user has special authorization, is it possible to display blocked business partner master data. However,
it is still not possible to create, change, copy, or perform follow-up activities on this blocked business partner
data.
However, FI-CA-specic data relating to a blocked business partner (as for example the contract account)
users can display without having special authorization.
For more information on the blocking and deletion of personal data, on the end of purpose check and on
displaying blocked data in Contract Accounts Receivable and Payable, see the Product Assistance of Contract
Accounts Receivable and Payable under Basic Functions SAP Business Partner Blocking and Deleting
Personal Data .
Process Flow
Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM. You choose whether data deletion is required for data stored in archive les or data stored
in the database, also depending on the type of deletion functionality available. You do the following:
1. Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA).
2. Run transaction FPDPR_BP_INIT once for existing business partners for which you want to execute the
end of purpose checks. New business partners you create are automatically included in the end of purpose
checks.
3. Run transaction FPDPR1 to prepare the end of purpose check of the central business partner.
The function module MKK_BUPA_EOP_CHECK saved for Contract Accounts Receivable and Payable (FI-CA)
in table BUTEOPFM provides the EoP check result obtained by transaction FPDPR1 to transaction
BUPA_PRE_EOP.
4. Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner.
Business users can request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
If you have the needed authorizations, you can unblock data by running the transaction BUPA_PRE_EOP.
You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of Contract Accounts
Receivable and Payable (FI-CA).
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 61

Dene the settings for authorization management under Authorization Management. For more information, see
the Customizing documentation.
Dene the settings for blocking under Blocking and Unblocking Business Partner . For more information, see
the Customizing documentation.
You congure the settings specic for Contract Accounts Receivable and Payable in the Customizing for
Contract Accounts Receivable and Payable under Technical Settings Data Protection and Data Deletion.
For more information, see the Customizing documentation.
13.2.1.1.3 Payment Card Security According to PCI-DSS
Note
The Payment Card Industry Data Security Standard (PCI-DSS) was jointly developed by major credit
card companies in order to create a set of common industry security requirements for the protection of
cardholder data. Compliance with this standard is relevant for companies processing credit card data. For
more information, see http://www.pcisecuritystandards.org .
The following sections of the security guide support you in implementing payment card security aspects
and outline steps that need to be considered to be compliant with the PCI-DSS.
Please note that the PCI-DSS covers more than the steps and considerations given here. Complying with
the PCI-DSS lies completely within the customer’s responsibility, and we cannot guarantee the customer’s
compliance with the PCI-DSS.
For current information about PCI-DSS in general, see SAP Note 1609917 .
Contract Accounts Receivable and Payable (FI-CA) processes all payment transactions with your business
partners. For this purpose, Contract Accounts Receivable and Payable also processes credit card data. For
processing credit card transactions, Contract Accounts Receivable and Payable follows the rules laid down by
the Payment Card Industry Data Security Standard.
Credit card data arrives in Contract Accounts Receivable in the following ways:
● You receive documents, which already contain credit card data in their supplements, by means of the IDoc
interface or by means of BAPIs.
● You receive payments that already contain credit card data with the payment lot transfer program
(RFKKZE00).
● External payment collectors and external cash desk services transfer credit card data using enterprise
services with the payment to Contract Accounts Receivable and Payable.
● Financial Customer Care transfers credit card data for documents from SAP Customer Relationship
Management using RFC.
● Customers or your employees add credit card data as follows:
○ Employees enter credit card data in the master records of business partners and prepaid accounts.
○ Employees enter payment card data in the Maintain Bank Data (FPP4) transaction.
○ Employees enter credit card data for payments in the cash desk, in the cash journal, in payment
specications and in promises to pay.
○ Customers enter credit card data online in SAP Biller Direct. SAP Biller Direct transfers the data to
Contract Accounts Receivable and Payable.
62
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

● You adopt billable items with payment information using the generated RFC interfaces /1FE/<billable item
class>_BIT_CREATE_API.
● You create EDRs of the type AMOUNT using function module FKKBI_EDR_AMOUNT_CREATE.
The program for payment (such as the payment run or the cash desk) generates payment documents with
supplements containing the credit card data. Contract Accounts Receivable and Payable transfers this credit
card data to the payment card company or the clearing house using transaction FPPCDS (creation of le) or
FPCS (online transfer).
Contract Accounts Receivable and Payable stores the data as follows:
Object Table(s)
Business Partner Master Record
BUT0CC
CCARD
Payments in Payment Lot or Credit Card Lot
DFKKZP
Document
DFKKOPC
DFKKOPKC
DFKK_PCARD
Payment Data for a Payment Run
DPAYH
Payment Data for a Payment Using SAP Biller Direct or Fi
nancial Customer Care
DFKKOPC
Payment Specications
DFKKIP_GRP
Promises to pay
DFKKPPD_PAY
Master Record of Prepaid Account
FKKPREPACC
Billable Items Generated tables:
● /1FE/0<billable item class>0PY
● /1FE/0<billable item class>1PY
You must restrict the display of the necessary objects by assigning authorizations, while at the same time
ensuring that this authorization protection cannot be circumvented by database programs or customer-
specic ABAP reports.
You can also make additional security settings for payment card data. For more information, see SAP Note
1032588 and the SAP S/4HANA Security Guide, section “Payment Card Security”.
Archiving
Only masked credit card information can be archived. Clear text credit card information should not be archived.
Archiving encrypted credit card information is problematic because archived data should not be changed.
Encrypted credit card information has to be re-encrypted with a dierent key, for example, with key rotation, as
required by PCI-DSS. This change of data is not possible in an archive.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 63
In technologies that are agnostic to the semantics of the data, such as Process Integration (PI), ABAP Web
Services, or Forward Error Handling (FEH), archiving has to be disabled. IDocs that contain credit card
information should not be archived.
Interfaces (IDoc/Services)
Caution
According to PCI-DSS, IDoc segments are not allowed to store payment card numbers in clear text.
However, during processing of an IDoc in the IDoc Framework, all values are stored temporarily, including
the clear text credit card number. For more information about how to process own IDocs containing credit
card information, see the SAP NetWeaver
SAP NetWeaver Security Guide under Security Guides for
Connectivity and Interoperability Technologies
Security Guide ALE (ALE Applications) in SAP NetWeaver
Release 7.30 .
If you exchange data between systems using IDoc messages, and this data contains unencrypted credit
card information, you have to implement access restrictions and a deletion concept at the level of the le
system.
Contract Accounts Receivable and Payable processes payment card data in the following interfaces:
Type of Interface Technical Name Description
BAPI
BAPI_CTRACPREPAIDACCOUNT_CREA
BAPI - FI-CA Prepaid Account:Create
BAPI
BAPI_CTRACPREPAIDACCOUNT_CHNG
BAPI - FI-CA Prepaid Account:Change
BAPI
BAPI_CTRACPREPAIDACCOUNT_GETD
BAPI - FI-CA Prepaid Account:Read
detailed data
BAPI
BAPI_CTRACDOCUMENT_CREATE
BAPI:BAPI: FI-CA Post Document
RFC
FKK_PREP_PCARD_STORE
Prepaid:Store Payment Data in
DFKK_PCARD
RFC Event 1421 (function module
FKK_SAMPLE_1421)
Parallel BillingCall Settlement
RFC
FKK_BUPA_MAINTAIN_SINGLE
Maintain Business Partner
RFC /1FE/<billable item
class>
_BIT_CREATE_API
Generated RFC interfaces for transfer
ring billable items with payment infor
mation
Enterprise Service
CashPointPaymentCreateNotifica
tion_In
External Cash Point Payment
Web Service
ECC_CASHPOINTPAYMENTCRTNO
External Cash Point Payment
File Report RFKKPCDS Payment cards:Settlement
64 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

ALE/IDoc
ALE_CTRACDOCUMENT_CREATE
BAPI ->
IDoc:ALE_CTRACDOCUMENT_CREATE(
FI-CA Post document)
RFC Debugging
Caution
Disable RFC debugging when you process credit card information in a productive system. Do not activate
the Set RFC Trace option in your productive system. If this option is active, the system saves all input data
of an RFC call in clear text to a le. If credit card numbers (PAN) are included in calls to some function
module, then this data would be stored to this le. Since these numbers have to be stored encrypted
according to the PCI-DSS standard, activating this option would result in no longer being PCI compliant.
Forward Error Handling (FEH)
Caution
Disable Forward Error Handling for all services that contain credit card numbers in SAP Customizing.
Card Verication Values (CVV)
Caution
Do not process asynchronous services that contain a card verication code (CAV2, CID, CVC2, CVV2) or
their values.
Note that in SAP services, these values correspond to the GDT .PaymentCardVerificationValueText
The reason is that the payload of asynchronous services is persisted in the database until the service is
processed and persisting card verication values is not allowed according to PCI-DSS.
Synchronous services can be processed because their payload is not persisted.
13.3 Finance
13.3.1 Financial Accounting
Network and Communication Security
Communication with external systems takes place using the standard channels provided by SAP basis
technology:
● Application Link Enabling(ALE)/IDoc
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 65

● Standard interfaces to BI, CRM, and SRM systems
● Batch-Input
Ensure that no unauthorized access can take place at the time of data transfer using encryption and with
the help of your network.
● Remote Function Call(RFC) / Business Application Programming Interface (BAPI)
● File Interface
Ensure that no unauthorized access can take place at the time of data transfer using encryption and with
the help of your network.
● SAP Process Integration (PI)
● E-mail, fax
Example
○ Financial Accounting has interfaces to Taxware and Vertex software used for performing tax
calculations.
○ Electronic advance return for tax on sales/purchases:
○ There is an interface for the electronic advance return for tax on sales and purchases using
Elster. Communication takes place by means of XI.
○ You can digitally sign the electronic advance return for tax on sales/purchases.
○ Payments and payment advice notes are dispatched using IDoc, and dunning notices are sent by e-
mail or fax.
Communication Destinations
All the technical users generally available can be used.
Data Storage Security
Many of the Financial Accounting transactions access sensitive data. Access to this kind of data, such as
nancial statements, is protected by standard authorization objects.
13.3.1.1 Deletion of Personal Data in Financial Accounting
Use
The Financial Accounting (FI) component might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA
on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
66
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Relevant Application Objects and Available Deletion Functionality
Application Object Provided Deletion Functionality
FI documents
ILM object FI_DOCUMNT (SAP note 2011278 )
Bank statement ILM object FI_ELBANK
Check management ILM object FI_SCHECK
Interest data
● Deletion report RFINTITDEL_DES
● ILM object FI_INTEREST_DESTRUCTION (SAP note
1926249 )
Payment data Deletion report SAPF110R
Payment order Deletion report RFPYORDD
Dunning data
● Deletion report SAPF150R_DES
● ILM object FI_DUNNING_DESTRUCTION (SAP note
1932584 )
Cash Journal data
ILM object FI_TCJ_DOC (SAP note 1949312 )
Payment requests
ILM object FI_PAYRQ (SAP note 2005535 )
Payment advice data Deletion report RFAVIS20
Error correction system (ECS)
ILM object GLE_ECS (SAP note 1900413 )
Down payment chain
ILM object /SAPPCE/DP (SAP note 1876387 )
Accounting interface posting data ILM object MM_ACCTIT
Asset Accounting
ILM object AM_ASSET (SAP note 1860049 )
Available Check
Implemented Solution: End of Purpose Check
For more information, see SAP note 2018575 .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 67
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in
Customizing for Cross-Application Components under Data Protection.
13.3.1.2 General Ledger Accounting (FI-GL)
13.3.1.2.1 Data Storage Security
Logical Path and File Names
The FI-GL component saves data in les in the le system. Therefore, it is important to explicitly provide access
to the corresponding les in the le system without allowing access to other directories or les (also known as
directory traversal). This is achieved by specifying logical paths and le names in the system that map to the
physical paths and le names. This mapping is validated at runtime and if access is requested to a directory
that does not match a stored mapping, then an error occurs.
The following lists show the logical le names and paths used by the FI-GL component. They also show the
programs for which these le names and paths apply.
Logical File Names and Paths for FI-GL and FI-SL
Logical File Names
The following logical le names have been created to enable the validation of physical le names:
● FI_COPY_COMPANY_CODE_DATA_FOR_GENERAL_LEDGER_0X
○ Programs using this logical le name:
○ RFBISA00
○ RFBISA01
○ RFBISA51
○ Parameter used in this context:
○ <PARAM_1> Program Name
● FI_INFOSYS_TRANSPORT
○ Programs using this logical le name:
○ RGRJTE00
○ RGRLTE00
○ RGRMTE00
○ RGRRTE00
○ RGRSTE00
68
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

○ RGRVTE00
○ RGRXTE00
○ RGSSTE00
○ RGSVTE00
○ RGRJTI00
○ RGRMTI00
○ RGSSTI00
○ RGSVTI00
○ Parameter used in this context:
○ <PARAM_1> Program name
● FI_VALUATION
○ Programs using this logical le name:
○ FAGL_FCV
○ FAGL_FC_VALUATION
○ SAPF100
○ Parameters used in this context:
○ <PARAM_1> Program name
○ <PARAM_2> Key date (from the selection screen)
○ <PARAM_3> Valuation area (from the selection screen) for FAGL_FCV and FAGL_FC_VALUATION
valuation method (from the selection screen) for SAPF100
Logical Path Names
The logical le names listed above all use the logical le path FI_ROOT.
Logical File Names and Paths for FI-GL-IS (Information System)
Logical File Names
The following logical le names have been created to enable the validation of physical le names:
● FI_EXTERNAL
Programs using this logical le name and parameters used in this context:
Program <PARAM_1> <PARAM_2> <PARAM_3>
RFAWVZ58 Program name (SY-REPID) String 'AWV' Parameter 'Key Date'
RFAWVZ5A Program name (SY-REPID) String 'AWV' Parameter 'Key Date'
RFAWVZ5P Program name (SY-REPID) String 'AWV'
RFAWVZ5A_NACC Program name (SY-REPID) String 'AWV' Parameter 'Key Date'
RFAWVZ5P_NACC Program name (SY-REPID) String 'AWV'
RFBIDET0 Program name (SY-REPID) Parameter 'Client'
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 69

RFBIKRT0 Program name (SY-REPID) Parameter 'Client'
RFFR0E84 Program name (SY-REPID) Parameter 'Customers/
vendors'
Parameter 'Key Date'
RFFRDDE0 Program name (SY-REPID) Parameter 'Company Code' Parameter 'Type'
RFFRLIST Program name (SY-REPID)
RFFRMOD1 Program name (SY-REPID)
RFIDPTFO Program name (SY-REPID) Concatenated parameters
<Company
Code>_<Year>_<Period>
String 'READ' or 'WRITE'
RFLBOX00 Program name (SY-REPID) Parameter 'Procedure' Parameter 'Input Record
Format'
RFLBOX80 Program name (SY-REPID) Parameter 'Procedure' Parameter 'Input Record
Format'
RFLBOXIN Program name (SY-REPID) String 'LOCKBOX' String 'BAI'
RFSBLIW0 Program name (SY-REPID)
● FI_POSTING
Programs using this logical le name and parameters used in this context:
Program <PARAM_1> <PARAM_2> <PARAM_3>
RFBIBLT0 Program name (SY-REPID)
RFEBCK00 Program name (SY-REPID) Parameter 'Document Type' Parameter 'Session name'
RFEBCKT0 Program name (SY-REPID)
SAPF100A Program name (SY-REPID) Parameter 'Key Date'
● FI_TAX
Programs using this logical le name and parameters used in this context:
Program <PARAM_1> <PARAM_2> <PARAM_3>
RFASLD02 Program name (SY-REPID) Parameter year for 'Report
ing Quarter'
Parameter 'Reporting Quar
ter'
RFASLD11 Program name (SY-REPID) Parameter year for 'Report
ing Quarter'
Parameter 'Reporting Quar
ter'
70 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

RFASLD11B Program name (SY-REPID) Parameter year for 'Report
ing Quarter'
Parameter 'Reporting Quar
ter'
RFUMPT00 Program name (SY-REPID) Parameter 'Company Code'
RFUSVB10 Program name (SY-REPID) Parameter 'Posting Date'
(lower value)
Parameter 'Posting Date'
(higher value)
RFKQSU30 Program name (SY-REPID)
RFUMPT00 Program name (SY-REPID)
RFUSVS12 Program name (SY-REPID) Parameter 'Entity Responsi
ble'
See note 1
RFUSVS14 Program name (SY-REPID) Concatenated parameters
<Company Code>_<Year>
See note 1
RFUVPT00 Program name (SY-REPID) Parameter 'Company Code' See note 2
Notes:
○ Note 1
If the le specied in the parameter “File for Leasing” is accessed, PARAM_3 contains the value READ;
consequently, the le content is read only and added to the output le.
If the le specied in the parameter “UNIX File for Output” is accessed, PARAM_3 contains the value
“WRITE”.
○ Note 2
If the le listed in the parameter “File Name - Application Server” on the “Periodic File O” tab page is
accessed, PARAM_3 contains the string PERIOD_WRITE.
If the le listed in the parameter “ECSL File Name (AS)” on the “Periodic File O” tab page is accessed,
PARAM_3 contains the string PERIOD_READ.
If the le listed in the parameter “XML File App. OP” on the “Annual File O/P” tab page is accessed,
PARAM_3 contains the string YEAR_READ.
If the le listed in the parameter “File Name - Application Server” on the “Annual File O/P” tab page is
accessed, PARAM_3 contains the string YEAR_WRITE.
● FI_RFASLD12_FILE
Programs using this logical le name and parameters used in this context:
Program <PARAM_1>
RFASLD02 Program name (SY-CPROG)
Logical Path Names
The logical le names listed above use the following logical le paths:
Logical File Name Logical File Path
FI_EXTERNAL FI_ROOT
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 71

FI_POSTING
FI_TAX
FI_RFASLD12_FILE FI_ERVJAB_FILE_PATH
13.3.1.3 Bank Accounting (FI-BL)
Important SAP Notes
For a list of additional security-relevant SAP HotNews and SAP Notes, see the SAP Support Portal at http://
support.sap.com/securitynotes .
13.3.1.4 Asset Accounting (FI-AA)
Important SAP Notes
For a list of additional security-relevant SAP HotNews and SAP Notes, see the SAP Support Portal at http://
support.sap.com/securitynotes.
Standard Roles
Role Description
SAP_BR_AA_ACCOUNTANT Asset Accountant
SAP_AUDITOR_BA_FI_AA AIS Fixed Assets
SAP_AUDITOR_BA_FI_AA_A AIS - Fixed Assets (Authorizations)
Standard Authorization Objects
For the list of standard authorization objects available for Asset Accounting, see transaction SU21, Object Class
Asset Accounting (AM).
72
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Network and Communication Security
Asset Accounting provides BAPIs for communicating with third-party systems.
Communication Destinations
For workow tasks, you sometimes need either the WF-BATCH user or a user that you can use for background
steps of this kind. To execute the decision steps required before reaching these background steps, you need a
user that is explicitly assigned.
13.3.1.5 Special Purpose Ledger (FI-SL)
Data Storage Security
Protect access to the le system with logical paths and le names
The Special Purpose Ledger saves data in les in the le system. Therefore, it is important to allow access
explicitly to certain les in the le system without allowing access to other les (also called le traversals). You
achieve this by entering logical paths and le names in the system, which are assigned to the physical paths
and le names. This assignment is validated at runtime. If access to a le is requested that does not match any
stored assignment, then an error occurs.
Access to the le system is protected for the following programs by the logical le name listed.
Program
Logical File Name Used by
the Program Parameter Used in Context
Logical Path Name Used by
the Program
RGRJTE00 FI_INFOSYS_TRANSPORT <PARAM_1> Program Name FI_ROOT
RGRLTE00
RGRMTE00
RGRRTE00
RGRSTE00
RGRVTE00
RGRXTE00
RGSSTE00
RGSVTE00
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 73

Program
Logical File Name Used by
the Program Parameter Used in Context
Logical Path Name Used by
the Program
RGRJTI00
RGRMTI00
RGSSTI00
RGSVTI00
SAPMGLRV FI_ROLLUP <PARAM_1> Program Name
(SY-CPROG)
FI_ROOT
SAPFGRWE FI_REPORT_WRITER <PARAM_1> Program Name
(SY-CPROG – generated pro
gram name)
FI_ROOT
Activating the Validation of Logical Paths and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default.To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-dependent). To determine
which paths are used by your system, you can activate the appropriate settings in the Security Audit Log.
13.3.1.6 Corporate Close - Consolidation Foundation
13.3.1.6.1 Deletion of Personal Data
Use
The Real-Time Consolidation (FIN-RTC) component in SAP S/4HANA might process data (personal data)
that is subject to the data protection laws applicable in specic countries.
74
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Consolidation Methods
● Transaction codes RTCTM and RTCRM
● Fiori App Dene Validation Methods
RTC_DPP_METHOD
Consolidation Models (transaction code RTCMD) RTC_DPP_MODEL
Validation Rules (Fiori app Dene Validation Rules) RTC_DPP_VALIDATION_RULE
Data Release Lock (Fiori app Consolidation Data Release
Monitor)
RTC_DPP_DATA_RELEASE_LOCK
Data Release Requests
● Fiori app Consolidation Data Release Cockpit
● Fiori app Consolidation Data Release Monitor
RTC_DPP_DATA_RELEASE_REQUEST
Rule Result Comments (Fiori app Consolidation Data Release
Cockpit)
RTC_DPP_RULE_RESULT_COMMENTS
Task Logs (all programs that run currency translation and
post journal entries, for example, transaction code RTCCT
and Fiori app Consolidation Data Release Cockpit)
RTC_DPP_TASK_LOG
Note
For the deletion programs mentioned in the table above, you can also Display Records.
Run Deletion Programs
SAP recommends scheduling regular jobs to run the deletion programs using the Dene Background Job
(SM36) transaction.
13.3.1.7 Central Finance (FI-CF)
The following functions are available for Central Finance:
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 75
Schedule Clean-Up Report in Source System
Data relating to FI/CO documents is temporarily stored in log tables in the source system before it can be
transferred to Central Finance. To delete the temporary information from these tables, a clean-up program
(RFIN_CFIN_CLEANUP) is run and must be scheduled regularly (for example, once a month). In the
conguration of this program, you can dene for how many periods a temporarily stored data record is kept
before being deleted by the clean-up program (for example, so that an incorrect posting can be corrected).
Read Access Log for the Application Log
The application log for the Central Finance initial load may contain sensitive, personal data. Therefore, we
provide a read access log for this application log (CFIN_INITIAL_LOAD) for the channel DYNP.
13.3.1.8 Joint Venture Accounting
13.3.2 Controlling
13.3.2.1 Network and Communication Security
Controlling is integrated with Microsoft Oce.For information on security aspects with Microsoft Oce
applications, refer to the documentation of those products.
Communication in Manager Self-Service (MSS) and in the Web Application for the Business Unit Analyst (BUA)
is based on Remote Function Calls (RFCs).
13.3.2.1.1 Communication Destinations
Technical users are required for communication over ALE, for batch reporting, and for third-party providers
that access Controlling data.
13.3.3 Governance, Risk and Compliance for Finance
76
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.3.3.1 International Trade
The following security information applies to SAP S/4HANA for international trade only.
13.3.3.2 Deletion of Personal Data in International Trade
International Trade might process data (personal data) that is subject to the data protection laws applicable in
specic countries.
Note
SAP S/4HANA for international trade does not use SAP Information Lifecycle Management (ILM)
to control the blocking and deletion of personal data. SAP S/4HANA for international trade uses SAP
Business Partner (BP) instead to control the blocking and deletion of personal data.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for dening the settings for blocking. Choose Customizing, then Cross-Application Components under Data
Protection.
13.3.3.2.1 Intrastat-Declarations
Personal data of the contact person of the provider of information, for example rst name, last name and e-
mail address, is written into Intrastat declaration les to be compliant with the le formats dened by
authorities. These le formats are country-specic and can be changed by authorities at any time.
Intrastat declaration les are saved outside the SAP S/4HANA system. Therefore, the management of those
les and the deletion of personal data in those les must be done outside the SAP S/4HANA system.
13.3.3.3 Authorizations in International Trade
International trade uses the authorization concept provided by the SAP NetWeaver for Application Server
ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver
for Application Server ABAP also apply.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 77
13.3.3.3.1 Business Catalogs in International Trade
Business catalogs are the central object for UI and authorization assignment to business users and for
structuring and organizing the menu and authorization maintenance. If a user is assigned to a business
catalog, he gains access to all apps included in the catalog and therefore requires the corresponding
authorizations.
In On-Premise, business catalogs are dened by customers by composing the relevant apps based on their
specic requirements. Authorizations are determined via the Fiori-PFCG integration when entering the catalog
in the PFCG role menu. SAP delivers business catalogs as templates that customers may copy to create their
own content. To give users access to the apps, must assign them to the Business catalogs.
Business Catalogs
Business Catalog: SAP_SLL_BC_CLS_LEGCTRL
International Trade Classication - Legal Control
Apps
● Manage Control Classes
● Manage Control Groupings
● Classify Products - Legal Control
● Reclassify Products - Legal Control
Business Catalog: SAP_SLL_BC_CLS_CMMDTYCODE
International Trade Classication - Commodity Codes
Apps
● Manage Commodity Codes
● Classify Products – Commodity Codes
● Reclassify Products – Commodity Codes
Business Catalog: SAP_SLL_BC_CLS_ISSRVCCODE
International Trade Classication - Intrastat Service Codes
Apps
● Manage Intrastat Service Codes
● Classify Products – Intrastat Service Codes
● Reclassify Products – Intrastat Service Codes
Business Catalog: SAP_SLL_BC_INTRASTAT_DECLN
Intrastat - Declaration Management
Apps
● Manage Intrastat Service Codes
● Classify Products – Intrastat Service Codes
● Reclassify Products – Intrastat Service Codes
Business Catalog: SAP_SLL_BC_INTRASTAT_SEL
Intrastat - Selection Report Execution
78
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Apps
● Select Dispatches and Customer Returns
● Select Receipts and Returns to Supplier
Business Catalog: SAP_SLL_BC_LICENSE_MANAGE
International Trade Compliance - License Management
Apps
● Manage Licenses
Business Catalog: SAP_SLL_BC_CMPLCDOC_MANAGE
International Trade Compliance - Document Management
Apps
● Resolve Blocked Documents - Trade Compliance
● Manage Documents - Trade Compliance
13.3.3.3.1.1 Display Business Catalog in International Trade
You can manage authorization elds in PFCG role by using transaction PFCG. The authorization eld is used in
Business Partner display catalog.
Business Catalog: SAP_CMD_BC_BP_DISP
Master Data - Business Partner Display
Authorization Object Description Authorization Field
B_BUPA_GRP Authorization Group for Business Part
ners
BEGRU
B_BUPA_RLT Business Partner Role RLTYP
Business Partner Display Catalog Used by Intrastat Apps (POI)
If you assign business catalog SAP_SLL_BC_INTRASTAT_DECLN in a backend role, you also assign business
catalog SAP_CMD_BC_BP_DISP in a backend role. Specify business partner role type B_BUPA_RLT with
ACTVT = 03 & RLTYP = 'SLLSTL'. 'SLLSTL' is the contact person created as provider of information.
Business Partner Display Catalog Used by Legal Control Apps
If you assign business catalog SAP_SLL_BC_LICENSE_MANAGE in backend role, you also assign business
catalog SAP_CMD_BC_BP_DISP in a backend role.
.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 79
13.3.3.3.1.2 Manage Authorization for Generic Service in
Business Catalog in International Trade
You can use the generic object services in the business catalog, to restrict application specic authorization
elds by following the documentation of the following topics:
● Generic Object Services (GOS) attachment service [page 80]
● Generic Service - Application Job SU22 Authorization Default [page 80]
13.3.3.3.1.2.1 Generic Object Services (GOS) attachment
service
Integration with attachment service for license master
Manual action required
1. Assign Fiori catalog SAP_SLL_BC_LICENSE_MANAGE to PFCG role in backend.
2. Input value for authorization object S_GOS_ATT manually.
● BOROBJTYPE = ITRLICMSTR
● ACTIVITY = 02 and 06
13.3.3.3.1.2.2 Generic Service - Application Job SU22
Authorization Default
Integration with application job for Intrastat selection reports
Manual action required
1. Assign Fiori catalog to PFCG role.
2. Assign authorization default for selection reports.
● Transaction VE01 - Select SD Dispatches and Returns
● Transaction MEIS - Select MM Receipts and Returns
13.3.3.3.2 Standard Authorization Objects in International
Trade
The following table shows the default authorization objects that you need for international trade.
80
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Description
ITM_BUKRS Authorization for Company Code
ITM_LGREG Authorization for Legal Regulation
ITM_LMGM Authorization for Legal Regulation / License Type
/ECRS/RPHD Intrastat Declaration
/ECRS/POIA Provider of Information
/ECRS/SP Selection Program for Intrastat Reporting
ITM_CLS_NC Trade Classication: Auth. for Numbering Scheme Content
ITM_CLS_LR Trade Classication: Authorization for Legal Regulation
ITM_CLS_NS Trade Classication: Authorization for Numbering Scheme
For International Trade apps, you nd the following authorization objects in the tables listed below:
Authorization Object App Name
ITM_CLS_NC Classify Products - Commodity Codes
Reclassify Products - Commodity Codes
Classify Products - Intrastat Service Codes
Reclassify Products - Intrastat Service Codes
Authorization Object App Name
ITM_CLS_LR Classify Products - Legal Control
ITM_CLS_NS Reclassify Products - Legal Control
Authorization Object App Name
ITM_CLS_NC Manage Control Classes
Authorization Object App Name
ITM_CLS_LR Manage Control Groupings
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 81

Authorization Object App Name
ITM_BUKRS Manage Licenses
ITM_LMGM
ITM_LGREG
ITM_CLS_NS
ITM_CLS_NC
S_GOS_ATT
Authorization Object App Name
ITM_BUKRS Resolve Blocked Documents - Trade Compliance
ITM_LGREG
ITM_CLS_NS
ITM_CLS_NC
Authorization Object App Name
ITM_BUKRS Manage Documents - Trade Compliance
ITM_LGREG
ITM_CLS_NS
ITM_CLS_NC
Authorization Object Transaction Name
/ECRS/SP MEIS: Select Receipts, Returns to Supplier
VE01: Select Dispatches, Customer Returns
13.3.4 Treasury and Financial Risk Management
82
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.3.4.1 SAP Bank Communication Management (incl. SAP
Integration Package for SWIFT)
About this Document
The Security Guide provides an overview of the specic security-relevant information that applies to the SAP
Bank Communication Management including the SAP Integration Package for SWIFT .
13.3.4.1.1 Technical System Landscape
Use
SAP Bank Communication Management is responsible for the creation and approval of batches, the payment
status monitor and bank statement monitor. Use of the SAP Integration package for SWIFT is optional ; it
provides a le interface to the Swift Alliance Access/Alliance Gateway (SWIFT is not SAP software and not part
of SAP Bank Communication Management ).
The gure below shows an overview of the technical system landscape for SAP Bank Communication
Management .
For more information about recommended security zone settings, see SAP NetWeaver Security Guide
(Complete).
13.3.4.1.2 User Management
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively have to change their passwords on a regular
basis, but not those users under which background processing jobs run.
The user types that are required for the SAP Bank Communication Management include:
● Individual users
Dialog users are used for SAP GUI for Windows connections.
● Technical users
Communication users are used for XI communication.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 83

Standard Users
The table below shows the standard users that are necessary for operating the SAP Bank Communication
Management .
System User ID Type Password Description
SAP Bank Communi
cation Management
For example:
BRMXIUSER
Communication user You specify the initial
password during the
installation.
The user ID and pass
word are stored in the
XI channel for the con
nection.
XI Integration Server For example:
SWIFTADMIN
Default user You specify the initial
password during the
installation.
Member of user group
SWIFT_ADMINISTRA
TOR as described in
the SAP Integration
Package for SWIFT
Conguration Guide .
You need to create these users before XI conguration.
Assign role SAP_XI_IS_SERV_USER to user BRMXIUSER and role SWIFT_ADMINSTRATOR to user
SWIFTADMIN.
Creation of role SWIFT_ADMINSTRATOR is described in the SAPIntegration Package for SWIFT Conguration
Guide .
13.3.4.1.3 Authorizations
Standard Roles
The table below shows the standard roles that are used by the SAP Bank Communication Management.
Role Description
SAP_XI_IS_SERV_USER Exchange Infrastructure: Integration Server Service User
SWIFT_ADMINSTRATOR Operating SWIFT interface. See Integration Package for
SWIFT Conguration Guide
SAP_BPR_CASH_MANAGER Cash Manager
84 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by SAP Bank Communication
Management.
Authorization Object Description
F_FEBB_BUK Company Code Bank Statement
F_REGU_BUK Automatic Payment: Activity Authorization for Company Co
des
13.3.4.1.4 Communication Destinations
The table below shows an overview of the communication destinations used by SAP Bank Communication
Management .
Destination Delivered Type User, Authorizations
INTEGRATION_SERVER No RFC XIAPPLUSER
Role
SAP_XI_APPL_SERV_USER
LCRSAPRFC No RFC
SAPSLDAPI No RFC
These destinations are not application-specic but they are required for the operation of the Exchange
Infrastructure.
13.3.4.1.5 Data Storage Security
Master and transaction data of SAP Bank Communication Management is saved in the database of the SAP
system in which SAP Bank Communication Management is installed.
Access to this data is restricted through the authorizations for authorization object F_STAT_MON. You can add
this authorization object to the role or user that is used by you for payment medium creation.
Payment order related transaction data is distributed to connected systems using XI, especially if the optional
Integration Package for SWIFT is used.
Access to data on natural persons in particular is subject to data protection requirements and must be
restricted by assigning authorizations.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 85
Using Logical Path and Filenames to Protect Access to the File System
SAP Bank Communication Management saves data in les in the le system. Therefore, it is important to
explicitly provide access to the corresponding les in the le system without allowing access to other
directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
The following lists show the logical le names and paths used by SAP Bank Communication Management and
for which programs these le names and paths apply:
Logical File Names Used in SAP Bank Communication Management
The following logical le names have been created in order to enable the validation of physical le names:
● FI_RFEBKAT0_FILE
○ Program using this logical le name and parameters used in this context:
○ RFEBKAT0
● FI_RFEBKATX_FILE
○ Program using this logical le name and parameters used in this context:
○ RFEBKATX
● FI_RFEBKAT1_FILE
○ Program using this logical le name and parameters used in this context:
○ RFEBKAT1
● FI_RFEBEST0_FILE
○ Program using this logical le name and parameters used in this context:
○ RFEBEST0
● FI_RFEBLBT1_FILE
○ Program using this logical le name and parameters used in this context:
○ RFEBLBT1
● FI_RFEBLBT2_FILE
○ Program using this logical le name and parameters used in this context:
○ RFEBLBT2
Parameters used in this context: <PARAM_1> Program name
Logical Path Name Used in SAP Bank Communication Management
The logical le names listed above all use the logical le path FI_FTE_TEST_FILES .
13.3.4.2 SAP In-House Cash (FIN-FSCM-IHC)
In the following sections you can nd information about the specic security functions for the SAP In-House
Cash (FIN-FSCM-IHC) component.
In addition, you can access further information at the following places:
For information about the specic security functions for the component Bank Customer Accounts (IS-B‑BCA),
see Bank Customer Accounts (BCA) [page 503] in the Banking section.
86
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Reason: SAP In-House Cash (FIN-FSCM-IHC) uses Bank Customer Accounts as the basis for various functions.
For information about the specic security functions for the component Bank Accounting (FI-BL), see the
under Bank Accounting (FI-BL) [page 72] in the Banking section.
Reason: SAP In-House Cash (FIN-FSCM-IHC) uses various functions of Bank Accounting , such as the creation
of data media for central payments.
13.3.4.2.1 Security Aspects of Data, Data Flow and Processes
The following sections show an overview of the data ow in the processes of SAPIn-House Cash .
Note
The appropriate Security Guides apply for all of the external systems that you require when using the SAP
In-House Cash component. Include these Security Guides in your cross-application security concept.
13.3.4.2.1.1 Internal Payments
The gure below shows an overview of internal payments between two subsidiary companies and the transfer
of the balances to the general ledger.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 87
The table below shows the security aspect to be considered for the process step and what mechanism applies.
Step Description Security Measure
1 Payment order
(IDoc/ALE)
User type: dialog user or technical user
2a Bank statement
(IDoc/ALE)
User type: dialog user or technical user
88 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
2b Bank statement
(IDoc/ALE)
User type: dialog user or technical user
3 General ledger transfer; only relevant if
SAP In-House Cash and the head oce
are running in two dierent systems
(IDoc/ALE)
User type: dialog user or technical user
13.3.4.2.1.2 Head Oce Payments
The following gure shows an overview of the data ow if the head oce takes over the payments for the
payables of a single subsidiary company.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 89
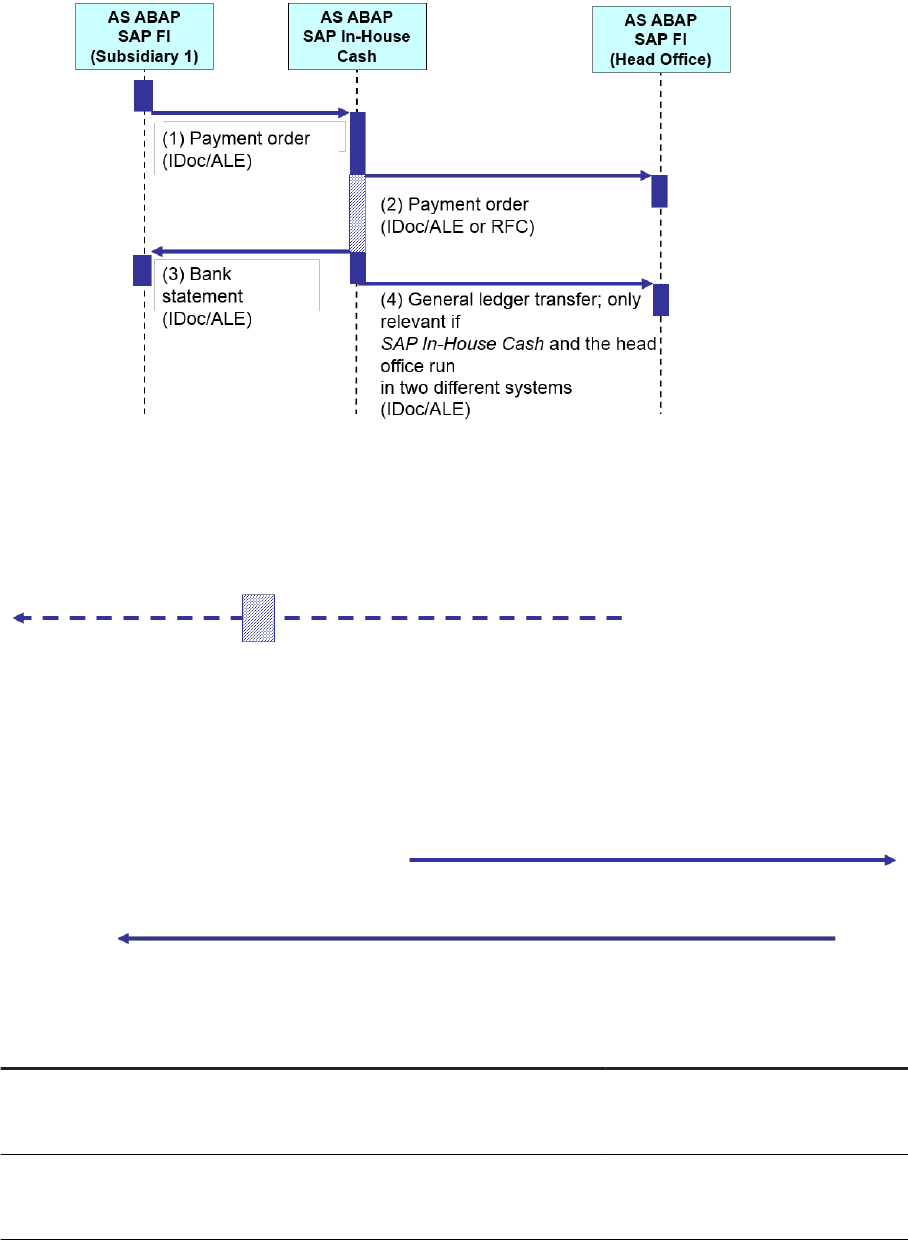
The table below shows the security aspect to be considered for the process step and what mechanism applies.
Step Description Security Measure
1 Payment order
(IDoc/ ALE )
User type: dialog user or technical user
2 Payment order
(IDoc/ ALE or RFC)
User type: dialog user or technical user
90 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Step Description Security Measure
3 Bank statement
(IDoc/ ALE )
User type: dialog user or technical user
4 General ledger transfer; only relevant if
SAP In-House Cash and the head oce
are running in two dierent systems
(IDoc/ ALE )
User type: dialog user or technical user
Note
The type of communication for the second step depends on your settings. If you have activated the In-
House Cash (Enterprise) (IHC_EP) application, then communication is by RFC. Otherwise it is by IDoc/
ALE . You can nd these settings in Customizing of SAP In-House Cash under Basic Settings → Business
Transaction Events/Event Control → Activate SAP Components .
13.3.4.2.1.3 Central Incoming Payments
The gure below shows an overview of an incoming payment that is intended for a subsidiary company of the
head oce.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 91

The table below shows the security aspect to be considered for the process step and what mechanism applies.
Step Description Security Measure
1 Incoming payment via bank statement
(RFC)
Access authorization via RFC user
2 Bank statement
(IDoc/ALE)
User type: dialog user or technical user
92 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
3 General ledger transfer; only relevant if
SAP In-House Cash and the head oce
are running in two dierent systems
(IDoc/ALE)
User type: dialog user or technical user
13.3.4.2.1.4 Local Payments
The gure below shows an overview of the data ow if a subsidiary company uses the house bank of a dierent
subsidiary company for its payment that is located in the country of the payment recipient. This avoids having
to make a foreign payment. The process ow is similar to Head Oce Payments [page 89] .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 93
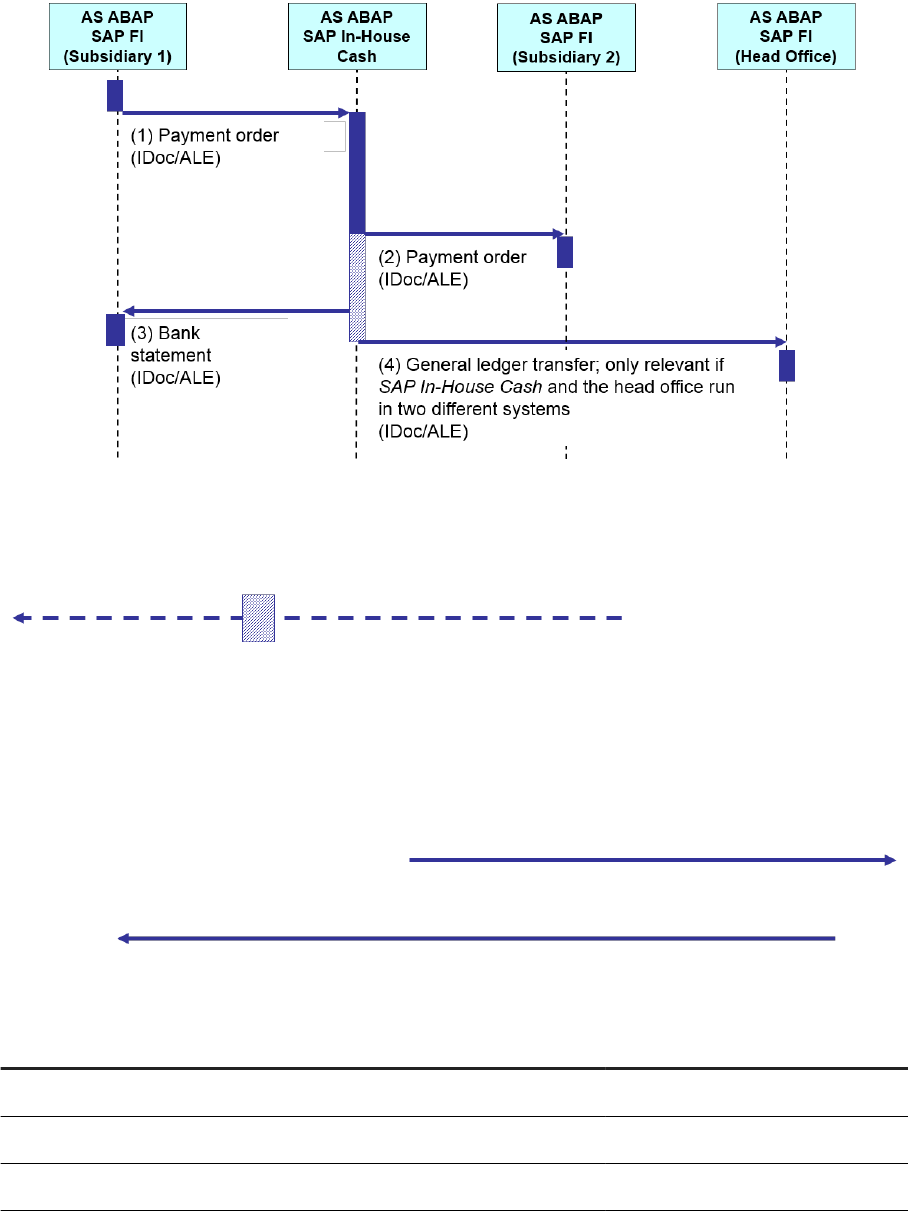
The table below shows the security aspect to be considered for the process step and what mechanism applies.
Step Description Security Measure
1 Payment order(IDoc/ALE) User type: dialog user or technical user
2 Payment order(IDoc/ALE) User type: dialog user or technical user
3 Bank statement(IDoc/ALE) User type: dialog user or technical user
94 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
4 General ledger transfer; only relevant if
SAPIn‑House Cash and the head oce
are running in two dierent sys
tems(IDoc/ALE)
User type: dialog user or technical user
13.3.4.2.2 Authorizations
Standard Roles
The table below shows the standard roles that are used by the SAP In-House Cash component. They contain
the maximum values of the authorizations.
Roles Description Comments
SAP_CFM_IHC_SUPERVISOR In-House Cash Supervisor Relevant for CFM 2.0
SAP_FSCM_IHC_SUPERVISOR FSCM In-House Cash Supervisor EA-Finserv 200 onwards
Authorization Objects
The table below shows the security-relevant authorization objects that are used by the SAP In-House Cash
component.
Authorization Objects Description
IHC_ACTION Authorizations for IHC activities
IHC_ROUTE Authorizations in route denition
IHC_CMSTAT Cash Management status of In-House Cash
F_PAYRQ Authorization object for payment requests
See also the Customizing activities in the SAP Customizing Implementation Guide (IMG). To do this, choose
SAP Reference IMG Financial Supply Chain Management In-House Cash Authorization Management. .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 95
13.3.4.3 Cash and Liquidity Management
Network and Communication Security
Communication with external systems is possible using standard interfaces via BAPI, IDoc, and XI.
Communication Destinations
In certain cases, a technical user may be required for the use of BAPIs.
Internet Communication Framework Security (ICF)
You should only activate those services that are needed for the applications running in your system. For more
information, see Internet Communication Framework Security (ICF) [page 96].
Data Storage Security
You can use logical path and le names to protect access to the le system. For more information, see Data
Storage Security [page 97].
13.3.4.3.1 Internet Communication Framework Security (ICF)
You should only activate those services that are needed for the applications running in your system. For Cash
and Liquidity Management, the following services are needed:
● Web Dynpro services
○ WDA_FCLM_BAM_ACC_MASTER
○ WDA_FCLM_BAM_ACC_REVIEW
○ WDA_FCLM_BAM_ADAPT_SIGN
○ WDA_FCLM_BAM_BANK_DATA
○ WDA_FCLM_BAM_CHGREQ
○ WDA_FCLM_BAM_HIERARCHY
○ WDA_FCLM_BAM_HIER_BP
○ WDA_FCLM_BAM_HIER_MAINTAIN
○ WDA_FCLM_BAM_MASS_CHANGE
○ WDA_FCLM_BAM_REVIEW_REPORT
○ WDA_FCLM_BAM_REQOVERVIEW
96
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
○ WDA_FCLM_REPORT
○ WDA_FCLM_UPLOAD_DOWNLOAD
○ WDA_FCLM_BAM_SENTITEMS
○ WD_FCLM_FPM_OVP_CFA
○ WD_FCLM_FPM_OVP_FD
○ WD_FCLM_FPM_OVP_FO
● Workow services
○ ibo_wda_inbox
○ swf_formabsenc
○ swf_workplace
○ UCT_DISPLAY_DOCUMENT
○ UCT_DISPLAY_INBOX
○ UCT_DISPLAY_SIGNOFF
○ UCT_DISPLAY_CHANGE
○ USMD_CREQUEST_PROTOCOL2
○ USMD_SSW_RULE
○ USMD_WF_NAVIGATION
● POWL services
○ POWL
○ POWL_COLLECTOR
○ powl_composite
○ POWL_EASY
○ POWL_ERRORPAGE
○ POWL_MASTER_QUERY
○ POWL_PERS_COMP
Use the transaction SICF to activate these services. If your rewalls use URL ltering, also note the URLs used
for the services and adjust your rewall settings accordingly. For more information about ICF security, see the
respective chapter in the SAP NetWeaver Security Guide.
13.3.4.3.2 Data Storage Security
Using Logical Paths and File Names to Protect Access to the File System
Cash and Liquidity Management saves data in les in the le system. Therefore, it is important to explicitly
provide access to the corresponding les in the le system without allowing access to other directories or les
(also known as directory traversal). This is achieved by specifying logical paths and le names in the system
that map to the physical paths and le names. This mapping is validated at runtime and if access is requested
to a directory that does not match a stored mapping, then an error occurs.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 97
The following list shows the logical paths and le names that are used in Cash and Liquidity Management and
the programs for which these le names and paths apply. The logical paths and le names have been created
to activate the validation of physical le names:
Logical le names used in Cash and Liquidity Management:
● FCLM_CM_MEMO_RECORD_EXPORT
○ Name of the program that uses this logical le name:
RFTS6510_CREATE_STRUCTURE (transaction RFTS6510CS)
○ Parameters used in this context:
No parameters
○ Logical path name:
FCLM_CM_MEMO_RECORD_EXPORT
● FCLM_CM_MEMO_RECORD_IMPORT
○ Name of the program that uses this logical le name:
RFTS6510 (transaction RFTS6510)
○ Parameters used in this context:
No parameters
○ Logical path name:
FCLM_CM_MEMO_RECORD_IMPORT
Activating the Validation of Logical Paths and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-dependent). To determine
which paths are used by your system, you can activate the appropriate settings in the Security Audit Log.
13.3.4.3.3 Data Protection
13.3.4.3.3.1 Deletion of Personal Data
Use
Cash and Liquidity Management might process data (personal data) that is subject to the data protection laws
applicable in specic countries.
You can use SAP Information Lifecycle Management (ILM) to control the blocking and deletion of personal data.
With Cash and Liquidity Management, SAP provides where-used checks (WUC) for you to identify data that are
no longer in use.
For information about the Customizing of blocking and deletion, see Conguration: Simplied Blocking and
Deletion.
98
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available Deletion Functionality
Cash and Liquidity Management itself does not directly use SAP ILM. But the integrated source applications,
which have to comply with retention periods, use SAP ILM to support the deletion of personal data.
Cash and Liquidity Management, however, provides the program Aggregate Flows, which helps to reduce the
data volume in database table FQM_FLOW for One Exposure from Operations.
Application Detailed Description Provided Deletion Functionality
One Exposure from Operations You use this transaction to delete ows
with certainty level ACTUAL in One Ex
posure and substitute them with aggre
gation ows. They then no longer con
tain any person-related information.
For more information, see the corre
sponding program documentation.
FQM_AGGREGATE_FLOWS
Where-Used Check (WUC)
A where-used check is a simple check to ensure data integrity in case of potential blocking. The checks in Cash
and Liquidity Management check whether any dependent data for a certain business partner exists in the
related tables.
If dependent data exists, that is, if the data is still required for business activities, the system does not block a
certain BP. If you still want to block the data, the dependent data must be deleted by using the existing
archiving and deletion tools or by using any other customer-specic solution.
Relevant Application Objects and Available EoP/WUC functionality
For the following application object, a where-used check (WUC) supporting the blocking of business partner
master data is available:
Application Related Table Implemented Solution (EoP or WUC)
One Exposure from Operations
FQM_FLOW
WUC with function module
FQM_BUPA_WUC_CHECK
Bank Relationship Management
FCLM_BAM_AMD
FCLM_BAM_BNKABP2
WUC with function module
FIN_FSCM_CLM_BAM
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 99

Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business data in Customizing for Cross-
Application Components under Data Protection.
● Dene the settings for authorization management under Cross-Application Components Data
Protection Authorization Management .
● Check the following settings for blocking in Customizing for Cross-Application Components under Data
Protection Blocking and Unblocking of Data Business Partner .
○ Under Register Application Names for EoP Check (view V_BUTEOPAPP) you nd One Exposure from
Operations (FQM).
○ Under Dene Application Function Modules Registered for EoP Check (view V_BUTEOPFM) you nd a list
of application function modules. Each application that consumes business partners registered their
function module in this view. These function modules are called by the blocking/unblocking report
when performing the end-of-purpose checks.
○ FQM: Function module FQM_BUPA_WUC_CHECK
○ Bank Account Management: Function module FIN_FSCM_CLM_BAM
For more information about conguration, see the Customizing documentation.
13.3.4.4 SAP Treasury and Risk Management
13.3.4.4.1 Data Storage Security
Using Logical Paths and File Names to Protect Access to the File System
SAP Treasury and Risk Management (FIN-FSCM-TRM) saves data in les in the le system. Therefore, it is
important to explicitly provide access to the corresponding les in the le system without allowing access to
other directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
The following list shows the logical paths and le names that are used in SAP Treasury and Risk Management
(FIN-FSCM-TRM) and the programs for which these le names and paths apply. The logical paths and le
names have been created to activate the validation of physical le names:
Logical le names used in SAP Treasury and Risk Management
● FTRM_FTR_DEALDATA_AMORTIZATION_SCHEDULES_IMPORT
○ Program that uses this logical le name:
○ RFTR_INTF_MAINFLOWS_UPLOAD
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_FTR_DEALDATA_IMPORT.
100
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
● FTRM_TCR_MARKETDATA_DF_IMPORT
○ Program that uses this logical le name:
○ RFTBDF06 [function Datafeed: Import External Market Data in Datafeed Notation (transaction
TBD5 )]
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_DF_IMPORT.
● FTRM_TCR_MARKETDATA_DF_SECURITIES_IDS_IMPORT_FOR_CUSTOMIZING
○ Program that uses this logical le name:
○ RFTBDF05 [function Datafeed: Import Security ID Numbers (transaction TBD2 )]
No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_DF_IMPORT.
● FTRM_TCR_MARKETDATA_FF_REQUEST_LIST_EXPORT
○ Program that uses this logical le name:
○ RFTBFF01 [function Market Data File Interface: Generate Rates and Prices Request List
(transaction TBDN )]
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_FF_EXPORT.
● FTRM_TCR_MARKETDATA_FF_IMPORT
○ Program that uses this logical le name:
○ RFTBFF01 [function Market Data File Interface: Import Rates and Prices (transaction TBDM )]
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_FF_IMPORT.
● FTRM_TCR_MARKETDATA_FF_ERRORLOG_EXPORT
○ Program that uses this logical le name:
○ RFTBFF01 [function Market Data File Interface: Import Rates and Prices (transaction TBDM )]
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_FF_EXPORT.
● FTRM_TCR_MARKETDATA_FF_SECURITIES_YEAR_END_PRICES_IMPORT
○ Program that uses this logical le name:
○ RFDWZFF0
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_FF_IMPORT.
● FTRM_TCR_MARKETDATA_FF_STATISTICS_IMPORT
○ Program that uses this logical le name:
○ RFTBFF20 [function Market Data File Interface: Import Statistics Data (transaction TVMD )]
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_FF_IMPORT.
● FTRM_TCR_TEMP_TCURC_EXPORT (Treasury: Sequential Output File for TCURC)
○ Program that uses this logical le name:
○ RZKLAODC
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TCR_TEMP_EXPORT.
● FTRM_TCR_TEMP_TCURT_EXPORT (Treasury: Sequential Output File for TCURT)
○ Program that uses this logical le name:
○ RZKLAODT
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 101
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_TCR_TEMP_EXPORT.
● FTRM_FTR_RED_SCHEDULE (Treasury: Redemption Schedule Parser)
○ Program that uses this logical le name:
○ FTBAS_SCHEDULE_BATCH_LOAD
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_FTR_RED_SCHEDULE.
● FTRM_AN_LIMIT
○ Program that uses this logical le name:
○ RFTBLBI1 (Batch Input Report for Creating Limits )
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_AN_LIMIT.
● FTRM_AN_INT_LIMIT
○ Program that uses this logical le name:
○ RFTBLBI1 ( Batch Input Report for Creating Limits)
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_AN_INT_LIMIT.
● FTRM_TCR_MARKETDATA_FF_DERIVATIVE_PRICES_ERRORLOG_EXPORT
○ Program that uses this logical le name:
○ RFTBFF30 (Import DTB Derivative Prices: transaction TVDT )
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_FF_EXPORT.
● FTRM_TCR_MARKETDATA_FF_DERIVATIVE_PRICES_IMPORT
○ Program that uses this logical le name:
○ RFTBFF30 (Import DTB Derivative Prices: transaction TVDT )
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_TCR_MARKETDATA_FF_IMPORT.
● FTRM_AN_BATCH_INPUT_DER
○ Programs using this logical le name:
○ RJBDBTC3 (Batch Input for Derivatives )
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_AN_BATCH_INPUT_DER.
● FTRM_AN_BATCH_INPUT_MM
○ Programs using this logical le name:
○ RJBDBTC2 (Batch Input for Derivatives)
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_AN_BATCH_INPUT_MM.
● FTRM_AN_BATCH_INPUT_FX
○ Programs using this logical le name:
○ RJBDBTC1 (Batch Input for FX Transactions )
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_AN_BATCH_INPUT_FX.
● FTRM_AN_BATCH_INPUT_ERR_FILE
○ Programs using this logical le name:
○ Include MJBEHF01
102
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
○ No parameters are used in this context.
○ The logical le name uses the logical le path FTRM_AN_BATCH_INPUT_ERR_FILE.
● FTRM_TARO_SEND
○ Programs using this logical le name:
○ R_TLR_TARO_SEND
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TARO_SEND (this is where the send program puts
the les to be sent to the repository)
● FTRM_TARO_IMPORT
○ Programs using this logical le name:
○ R_TLR_TARO_IMPORT and R_TLR_TARO_IMPORT_REPORTS
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TARO_IMPORT (this is where the system expects
les sent by the repository)
● FTRM_TARO_ARCHIVE
○ Programs using this logical le name:
○ R_TLR_TARO_IMPORT and R_TLR_TARO_IMPORT_REPORTS
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TARO_ARCHIVE (this is where imported les are
stored if they were successfully imported)
● FTRM_TARO_ERROR
○ Programs using this logical le name:
○ R_TLR_TARO_IMPORT and R_TLR_TARO_IMPORT_REPORTS
○ No parameters are used in this context:
○ The logical le name uses the logical le path FTRM_TARO_ERROR (this is where imported les are
stored if they were NOT successfully imported but caused an error)
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out which
paths are being used by your system, you can activate the corresponding settings in the Security Audit Log. For
more information, see about data storage security, see the respective chapter in the SAP NetWeaver Security
Guide.
13.3.5 Financial Operations
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 103

13.3.5.1 Contract Accounting
13.3.5.1.1 Data Storage Security
Contract Accounts Receivable and Payable (FI-CA) saves data in les in the le system. Therefore, it is
important to explicitly provide access to the corresponding les in the le system without allowing access to
other directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
The following list shows the logical le names and paths used by Contract Accounts Receivable and Payable
(FI-CA) and for which programs these le names and paths apply:
Logical File Names Used in FI-CA and Logical Path Names
The following logical le names have been created in order to enable the validation of physical le names:
Program Logical File Name Used by the Pro
gram
Logical Path Name Used by the Pro
gram
RFKIBI_FILE00 FICA_DATA_TRANSFER_DIR FICA_DATA_TRANSFER_DIR
RFKIBI_FILEP01
RFKKBI_FILEEDIT
RFKKBIBG
RFKKZEDG
RFKKRLDG
RFKKCMDG
RFKKCRDG
RFKKAVDG
RFKKBIB0
RFKKZE00
RFKKRL00
RFKKCM00
RFKKCR00
104 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

RFKKAV00
RFKKKA00
RFKKBIT0
RFKKPCSF FI-CA-CARD-DATA-S FI-CA-CARD-DATA-S
RFKKPCDS
RFKKCVSPAY FI-CA-CVS FI-CA-CVS
RFKK_CVSPAY_CONFIRM
RFKKCVSCONFIRMDB
RFKK_CVSPAY_CONFIRM_TEST
RFKK_DOC_EXTR_EXP FI-CA-DOC-EXTRACT-DIR FI-CA-DOC-EXTRACT-DIR
RFKK_DOC_EXTR_AEXP
RFKK_DOC_EXTR_IMP
RFKK_DOC_EXTR_EXTR
RFKK_DOC_EXTR
RFKK_DOC_EXTR_DEL
Class CL_FKK_TEXT_FILE
RFKKBIXBITUPLOAD FI-CA-BI-SAMPLE
FI-CA-BI-SAMPLE-DIR
FI-CA-BI-SAMPLE-DIR
RFKKCOL2 FI-CA-COL-SUB FI-CA-COL-SUB
RFKKCOLL
Transaction FP03DM (Mass Activity)
Transaction FPCI (Mass Activity)
FI-CA-COL-INFO FI-CA-COL-INFO
RFKKCOPM FI-CA-COL-READ FI-CA-COL-READ
READFILE
RFKKCOPG FI-CA-COL-TEST FI-CA-COL-TEST
RFKKRDI_REPORT FI-CA-RDI FI-CA-RDI
RFKKRDI_REPORT_DIS
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 105

SAPFKPY3 FI-CA-DTA-NAME FI-CA-DTA-NAME
RFKKCHK01 FI-CA-CHECKS-EXTRACT FI-CA-CHECKS-EXTRACT
Class CL_FKK_INFCO_SEND
FI-CA-INFCO FI-CA-INFCO
RFKKBE_SAL1
RFKKBE_SAL2
FICA_BE_SAL FICA_BE_SAL
FICA_BE_SAL_XML FICA_BE_SAL_XML
RFKK1099 FI-CA-1099 FI-CA-1099
RFKKOP03 FICA_OPEN_ITEMS FICA_OPEN_ITEMS
RFKKOP04
RFKKOP07
RFKKES_SAL1 FICA_TAX_REP_GEN FICA_TAX_REP_GEN
RFKKES_SAL2
RFKKRDI_REPORT FI-CA-RDI FI-CA-RDI
RFKKRDI_REPORT_DIS
Transaction EMIGALL
ISMW_FILE ISMW_ROOT
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out
which paths are being used by your system, you can activate the corresponding settings in the Security Audit
Log.
For more information about data storage security, see the chapter in the SAP NetWeaver Security Guide.
13.3.5.1.2 Data Protection
Contract Accounts Receivable and Payable (FI-CA) processes personal data of business partners that might be
subject to data protection legislation applicable in some countries.
Contract Accounts Receivable and Payable (FI-CA) uses SAP ILM to support the deletion of this personal data.
SAP delivers an end of purpose check for Contract Accounts Receivable and Payable (FI-CA). You register the
end of purpose check (EoP) in the Customizing settings for the blocking and deletion of the SAP Business
Partner.
106
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Display of Blocked Data
Only if a user has special authorization, is it possible to display blocked business partner master data. However,
it is still not possible to create, change, copy, or perform follow-up activities on this blocked business partner
data.
However, FI-CA-specic data relating to a blocked business partner (as for example the contract account)
users can display without having special authorization.
For more information on the blocking and deletion of personal data, on the end of purpose check and on
displaying blocked data in Contract Accounts Receivable and Payable, see the Product Assistance of Contract
Accounts Receivable and Payable under Basic Functions SAP Business Partner Blocking and Deleting
Personal Data .
Process Flow
Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM. You choose whether data deletion is required for data stored in archive les or data stored
in the database, also depending on the type of deletion functionality available. You do the following:
1. Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA).
2. Run transaction FPDPR_BP_INIT once for existing business partners for which you want to execute the
end of purpose checks. New business partners you create are automatically included in the end of purpose
checks.
3. Run transaction FPDPR1 to prepare the end of purpose check of the central business partner.
The function module MKK_BUPA_EOP_CHECK saved for Contract Accounts Receivable and Payable (FI-CA)
in table BUTEOPFM provides the EoP check result obtained by transaction FPDPR1 to transaction
BUPA_PRE_EOP.
4. Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner.
Business users can request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
If you have the needed authorizations, you can unblock data by running the transaction BUPA_PRE_EOP.
You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of Contract Accounts
Receivable and Payable (FI-CA).
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
Dene the settings for authorization management under Authorization Management. For more information, see
the Customizing documentation.
Dene the settings for blocking under Blocking and Unblocking Business Partner . For more information, see
the Customizing documentation.
You congure the settings specic for Contract Accounts Receivable and Payable in the Customizing for
Contract Accounts Receivable and Payable under
Technical Settings Data Protection and Data Deletion.
For more information, see the Customizing documentation.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 107

13.3.5.1.2.1 Payment Card Security According to PCI-DSS
Note
The Payment Card Industry Data Security Standard (PCI-DSS) was jointly developed by major credit
card companies in order to create a set of common industry security requirements for the protection of
cardholder data. Compliance with this standard is relevant for companies processing credit card data. For
more information, see http://www.pcisecuritystandards.org .
The following sections of the security guide support you in implementing payment card security aspects
and outline steps that need to be considered to be compliant with the PCI-DSS.
Please note that the PCI-DSS covers more than the steps and considerations given here. Complying with
the PCI-DSS lies completely within the customer’s responsibility, and we cannot guarantee the customer’s
compliance with the PCI-DSS.
For current information about PCI-DSS in general, see SAP Note 1609917 .
Contract Accounts Receivable and Payable (FI-CA) processes all payment transactions with your business
partners. For this purpose, Contract Accounts Receivable and Payable also processes credit card data. For
processing credit card transactions, Contract Accounts Receivable and Payable follows the rules laid down by
the Payment Card Industry Data Security Standard.
Credit card data arrives in Contract Accounts Receivable in the following ways:
● You receive documents, which already contain credit card data in their supplements, by means of the IDoc
interface or by means of BAPIs.
● You receive payments that already contain credit card data with the payment lot transfer program
(RFKKZE00).
● External payment collectors and external cash desk services transfer credit card data using enterprise
services with the payment to Contract Accounts Receivable and Payable.
● Financial Customer Care transfers credit card data for documents from SAP Customer Relationship
Management using RFC.
● Customers or your employees add credit card data as follows:
○ Employees enter credit card data in the master records of business partners and prepaid accounts.
○ Employees enter payment card data in the Maintain Bank Data (FPP4) transaction.
○ Employees enter credit card data for payments in the cash desk, in the cash journal, in payment
specications and in promises to pay.
○ Customers enter credit card data online in SAP Biller Direct. SAP Biller Direct transfers the data to
Contract Accounts Receivable and Payable.
● You adopt billable items with payment information using the generated RFC interfaces /1FE/<billable item
class>_BIT_CREATE_API.
● You create EDRs of the type AMOUNT using function module FKKBI_EDR_AMOUNT_CREATE.
The program for payment (such as the payment run or the cash desk) generates payment documents with
supplements containing the credit card data. Contract Accounts Receivable and Payable transfers this credit
card data to the payment card company or the clearing house using transaction FPPCDS (creation of le) or
FPCS (online transfer).
108
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Contract Accounts Receivable and Payable stores the data as follows:
Object Table(s)
Business Partner Master Record
BUT0CC
CCARD
Payments in Payment Lot or Credit Card Lot
DFKKZP
Document
DFKKOPC
DFKKOPKC
DFKK_PCARD
Payment Data for a Payment Run
DPAYH
Payment Data for a Payment Using SAP Biller Direct or Fi
nancial Customer Care
DFKKOPC
Payment Specications
DFKKIP_GRP
Promises to pay
DFKKPPD_PAY
Master Record of Prepaid Account
FKKPREPACC
Billable Items Generated tables:
● /1FE/0<billable item class>0PY
● /1FE/0<billable item class>1PY
You must restrict the display of the necessary objects by assigning authorizations, while at the same time
ensuring that this authorization protection cannot be circumvented by database programs or customer-
specic ABAP reports.
You can also make additional security settings for payment card data. For more information, see SAP Note
1032588 and the SAP S/4HANA Security Guide, section “Payment Card Security”.
Archiving
Only masked credit card information can be archived. Clear text credit card information should not be archived.
Archiving encrypted credit card information is problematic because archived data should not be changed.
Encrypted credit card information has to be re-encrypted with a dierent key, for example, with key rotation, as
required by PCI-DSS. This change of data is not possible in an archive.
In technologies that are agnostic to the semantics of the data, such as Process Integration (PI), ABAP Web
Services, or Forward Error Handling (FEH), archiving has to be disabled. IDocs that contain credit card
information should not be archived.
Interfaces (IDoc/Services)
Caution
According to PCI-DSS, IDoc segments are not allowed to store payment card numbers in clear text.
However, during processing of an IDoc in the IDoc Framework, all values are stored temporarily, including
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 109
the clear text credit card number. For more information about how to process own IDocs containing credit
card information, see the SAP NetWeaver SAP NetWeaver Security Guide under Security Guides for
Connectivity and Interoperability Technologies Security Guide ALE (ALE Applications) in SAP NetWeaver
Release 7.30
.
If you exchange data between systems using IDoc messages, and this data contains unencrypted credit
card information, you have to implement access restrictions and a deletion concept at the level of the le
system.
Contract Accounts Receivable and Payable processes payment card data in the following interfaces:
Type of Interface Technical Name Description
BAPI
BAPI_CTRACPREPAIDACCOUNT_CREA
BAPI - FI-CA Prepaid Account:Create
BAPI
BAPI_CTRACPREPAIDACCOUNT_CHNG
BAPI - FI-CA Prepaid Account:Change
BAPI
BAPI_CTRACPREPAIDACCOUNT_GETD
BAPI - FI-CA Prepaid Account:Read
detailed data
BAPI
BAPI_CTRACDOCUMENT_CREATE
BAPI:BAPI: FI-CA Post Document
RFC
FKK_PREP_PCARD_STORE
Prepaid:Store Payment Data in
DFKK_PCARD
RFC Event 1421 (function module
FKK_SAMPLE_1421)
Parallel BillingCall Settlement
RFC
FKK_BUPA_MAINTAIN_SINGLE
Maintain Business Partner
RFC /1FE/<billable item
class>
_BIT_CREATE_API
Generated RFC interfaces for transfer
ring billable items with payment infor
mation
Enterprise Service
CashPointPaymentCreateNotifica
tion_In
External Cash Point Payment
Web Service
ECC_CASHPOINTPAYMENTCRTNO
External Cash Point Payment
File Report RFKKPCDS Payment cards:Settlement
ALE/IDoc
ALE_CTRACDOCUMENT_CREATE
BAPI ->
IDoc:ALE_CTRACDOCUMENT_CREATE(
FI-CA Post document)
RFC Debugging
Caution
Disable RFC debugging when you process credit card information in a productive system. Do not activate
the Set RFC Trace option in your productive system. If this option is active, the system saves all input data
of an RFC call in clear text to a le. If credit card numbers (PAN) are included in calls to some function
110
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

module, then this data would be stored to this le. Since these numbers have to be stored encrypted
according to the PCI-DSS standard, activating this option would result in no longer being PCI compliant.
Forward Error Handling (FEH)
Caution
Disable Forward Error Handling for all services that contain credit card numbers in SAP Customizing.
Card Verication Values (CVV)
Caution
Do not process asynchronous services that contain a card verication code (CAV2, CID, CVC2, CVV2) or
their values.
Note that in SAP services, these values correspond to the GDT .PaymentCardVerificationValueText
The reason is that the payload of asynchronous services is persisted in the database until the service is
processed and persisting card verication values is not allowed according to PCI-DSS.
Synchronous services can be processed because their payload is not persisted.
13.3.5.2 Settlement Management
13.3.5.2.1 Deletion of Personal Data
The Settlement Management (LO-AB) application might process data (personal data) that is subject to the
data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM)
to control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 111

Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
Customer Settlement List See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
under Product Assistance
Enterprise Business Applications
Finance Financial Operations
Settlement Management Document
Categories in Settlement Management
Customer Settlement List .
ILM object AB_DOCUMENT assigned to
archiving object
WBU.
For more information see the product
assistance for SAP S/4HANA on the
SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications
Finance
Financial Operations Settlement
Management
Functions for Document
Processing Archiving of Settlement
Management Documents
Customer
Settlement Lists (LO-AB) .
Report:
WLF_UPDATE_AB_EOP_FROM_ARCHIVE
.
Customer Settlement See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications Finance
Financial Operations Settlement
Management Document Categories in
Settlement Management
Customer
Settlement .
ILM object AB_DOCUMENT assigned to
archiving object
WCI.
For more information see the product
assistance for SAP S/4HANA on the
SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications
Finance
Financial Operations Settlement
Management
Functions for Document
Processing Archiving of Settlement
Management Documents
Customer
Settlements (LO-AB) .
Report:
WLF_UPDATE_AB_EOP_FROM_ARCHIVE
.
112
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Application Object Detailed Description Provided Deletion Functionality
Supplier Billing Document See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications Finance
Financial Operations Settlement
Management Document Categories in
Settlement Management
Supplier
Billing Document .
ILM object AB_DOCUMENT assigned to
archiving object
WLF.
For more information see the product
assistance for SAP S/4HANA on the
SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications
Finance
Financial Operations Settlement
Management
Functions for Document
Processing Archiving of Settlement
Management Documents
Supplier
Billing Documents (LO-AB) .
Report:
WLF_UPDATE_AB_EOP_FROM_ARCHIVE
.
Settlement Document List See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications Finance
Financial Operations Settlement
Management Document Categories in
Settlement Management
Settlement
Document List .
ILM object AB_DOCUMENT assigned to
archiving object
WRECH.
For more information see the product
assistance for SAP S/4HANA on the
SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications
Finance
Financial Operations Settlement
Management
Functions for Document
Processing Archiving of Settlement
Management Documents
Settlement
Document Lists (LO-AB) .
Report:
WLF_UPDATE_AB_EOP_FROM_ARCHIVE
.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 113
Application Object Detailed Description Provided Deletion Functionality
Supplier Settlement List See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications Finance
Financial Operations Settlement
Management Document Categories in
Settlement Management
Supplier
Settlement List .
ILM object AB_DOCUMENT assigned to
archiving object
WREG.
For more information see the product
assistance for SAP S/4HANA on the
SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications
Finance
Financial Operations Settlement
Management
Functions for Document
Processing Archiving of Settlement
Management Documents
Supplier
Settlement Lists (LO-AB) .
Report:
WLF_UPDATE_AB_EOP_FROM_ARCHIVE
.
Expense Settlement See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications Finance
Financial Operations Settlement
Management Document Categories in
Settlement Management
Expense
Settlement .
ILM object AB_DOCUMENT assigned to
archiving object
WSI.
For more information see the product
assistance for SAP S/4HANA on the
SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications
Finance
Financial Operations Settlement
Management
Functions for Document
Processing Archiving of Settlement
Management Documents
Expense
Settlements (LO-AB) .
Report:
WLF_UPDATE_AB_EOP_FROM_ARCHIVE
.
114
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Object Detailed Description Provided Deletion Functionality
Settlement Document See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications Finance
Financial Operations Settlement
Management Document Categories in
Settlement Management
Settlement
Document .
ILM object AB_DOCUMENT assigned to
archiving object
WZR.
For more information see the product
assistance for SAP S/4HANA on the
SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications
Finance
Financial Operations Settlement
Management
Functions for Document
Processing Archiving of Settlement
Management Documents
Settlement
Documents (LO-AB) .
Report:
WLF_UPDATE_AB_EOP_FROM_ARCHIVE
.
Condition Contract See the product assistance for SAP S/
4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709
Product Assistance Enterprise
Business Applications Finance
Financial Operations Settlement
Management Condition Contract
Management
Condition Contract .
ILM object WCB_COCO assigned to ar
chiving object
WCB_COCO.
Report:
WCB_UPDATE_EOP_FROM_ARCHIVE.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 115

Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Settlement Management (LO-AB) End of purpose (EoP) check SAP delivers an end of purpose check
for Settlement Management (LO-AB).
All applications register either an end of
purpose (EoP) check in the Customiz
ing settings for the blocking and dele
tion of business partner data or a
where-used check (WUC). For informa
tion about the Customizing of blocking
and deletion for LO-AB, see Congura
tion: Simplied Blocking and Deletion.
Conguration: Simplied Blocking and Deletion
You congure the settings the related to the blocking and deletion of customer and supplier master data in
Customizing for Logistics - General under Business Partner Deletion of Customer and Supplier Master
Data.
.
13.3.6 Real Estate Management
13.3.6.1 Real Estate Management
Authorizations
Standard Roles of Real Estate Management
Role Description
SAP_RE_APPL
Real Estate Management (including administration and Cus
tomizing)
SAP_EP_RW_REFX_I
AC - Flexible Real Estate Management
SAP_EP_RW_REFX_II
AC - Flexible Real Estate Management - support processes
116 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Network and Communication Security
External heating expenses settlement is available In Real Estate Management. To make this settlement
possible, the necessary les must be generated in the SAP system in an internal SAP format. You then need to
send the data medium to the settlement company.
Trace and Log Files
The change documents provide information on changes to the authorization group and to the person
responsible for the object.
Data Storage Security
Using Logical Paths and File Names to Protect Access to the File System
Flexible Real Estate Management (RE-FX) saves data in les in the le system. Therefore, it is important to
explicitly provide access to the corresponding les in the le system without allowing access to other
directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
The following lists show the logical le names an paths that are used by Flexible Real Estate Management (RE-
FX), and for which programs these le names and paths apply:
Logical File Names Used in Flexible Real Estate Management (RE-FX)
The logical le name REFX_CREATE_TAPE makes it possible to validate physical le names in Flexible Real
Estate Management (RE-FX). The following programs use this logical le name:
● RFRESCMLTAPE
● RFRESCMLTAPECO
● RFRESCSETTLE
● RFRESCSETTLESC
● RFRESCCONTINUE
● RFRESCBOOKING
● RFRESCSETTLCO
● RFRESCCONTINUECO
● RFRESCPOSTCO
Logical Path Names Used in Flexible Real Estate Management (RE-FX)
The logical le names of Flexible Real Estate Management (RE-FX) listed above all use the logical le path
REFX_ROOT.
Activating the Validation of Logical Path and File Names
The logical paths and le names are entered in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 117
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out which
paths are being used by your system, you can activate the corresponding settings in the Security Audit Log.
13.3.6.2 Deletion of Personal Data in RE-FX
Use
The Flexible Real Estate Management (RE-FX) component might process data (personal data) that is
subject to the data protection laws applicable in specic countries. You can use SAP Information Lifecycle
Management (ILM) to control the blocking and deletion of personal data. For more information, see the
product assistance for SAP S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709
Product Assistance Cross Components Data Protection .
Relevant Archiving Objects
Archiving Object Technical Name
Architectural Object REFX_AO
Adjustment Measure REFX_AT
Business Entity REFX_BE
Buildings REFX_BU
Comparative Group of Apartments REFX_CG
Real Estate Contract REFX_CN
Cash Flow of Contracts REFX_CNCF
Joint Liability REFX_JL
Land Register REFX_LR
RE: Move Planning REFX_MP
Notice of Assessment REFX_NA
Contract Oer REFX_OF
Oered Object REFX_OO
Option Rate Determination per Object/Subobject REFX_OR
118 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Archiving Object Technical Name
Other Public Register REFX_PE
Participation Group REFX_PG
Parcel of Land REFX_PL
Property REFX_PR
RE Document REFX_RADOC
Parcel Update REFX_RC
Rental Object REFX_RO
Cash Flow of Rental Objects REFX_ROCF
RE Search Request REFX_RR
Reservation REFX_RS
Recurring Reservation REFX_RSREC
Service Charge Settlement REFX_SCSE
Settlement Unit REFX_SU
Correction Object REFX_TC
Available Check
Implemented Solution: End of Purpose (EoP) check
For more information, see SAP Note 2134204 .
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in
Customizing for Cross-Application Components under Data Protection.
13.3.7 Receivables Management
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 119
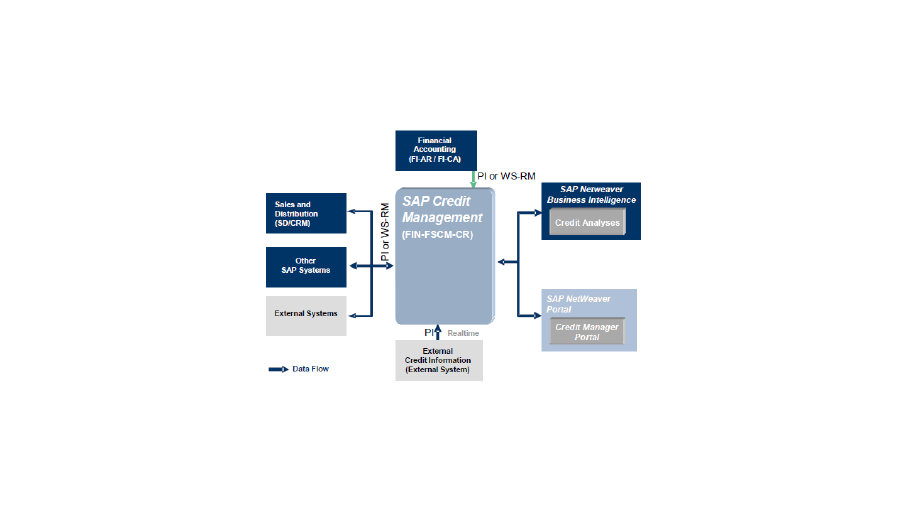
13.3.7.1 SAP Credit Management
13.3.7.1.1 Technical System Landscape
Use
This gure shows an overview of the technical system landscape for SAP Credit Management.
Technical System Landscape
To exchange messages with external information providers, you have to use the Integration Server. For
accounting systems as well as Sales and Distribution (SD) systems, you can congure the communication
either via the Integration Server or via a point to point connection using Web Services Reliable Messaging
(WSRM). The SAP Business Information Warehouse is connected via Remote Function Call (RFC).
For more information about recommended security zone settings, see SAP NetWeaver Security Guide
(Complete).
For SAP Credit Management the business package for the Credit Manager provides you with portal content so
that you can use the functions from SAP Credit Management in the portal. Security-relevant information about
the use of the portal content is available in the SAP NetWeaver Security Guide for the usage types Enterprise
Portal Core (EPC) and SAP Enterprise Portal (EP) in the portal security guide.
13.3.7.1.2 Security Aspects of Data, Data Flow, and Processes
This gure shows an example of a data ow for the SAP Credit Management application.
120
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
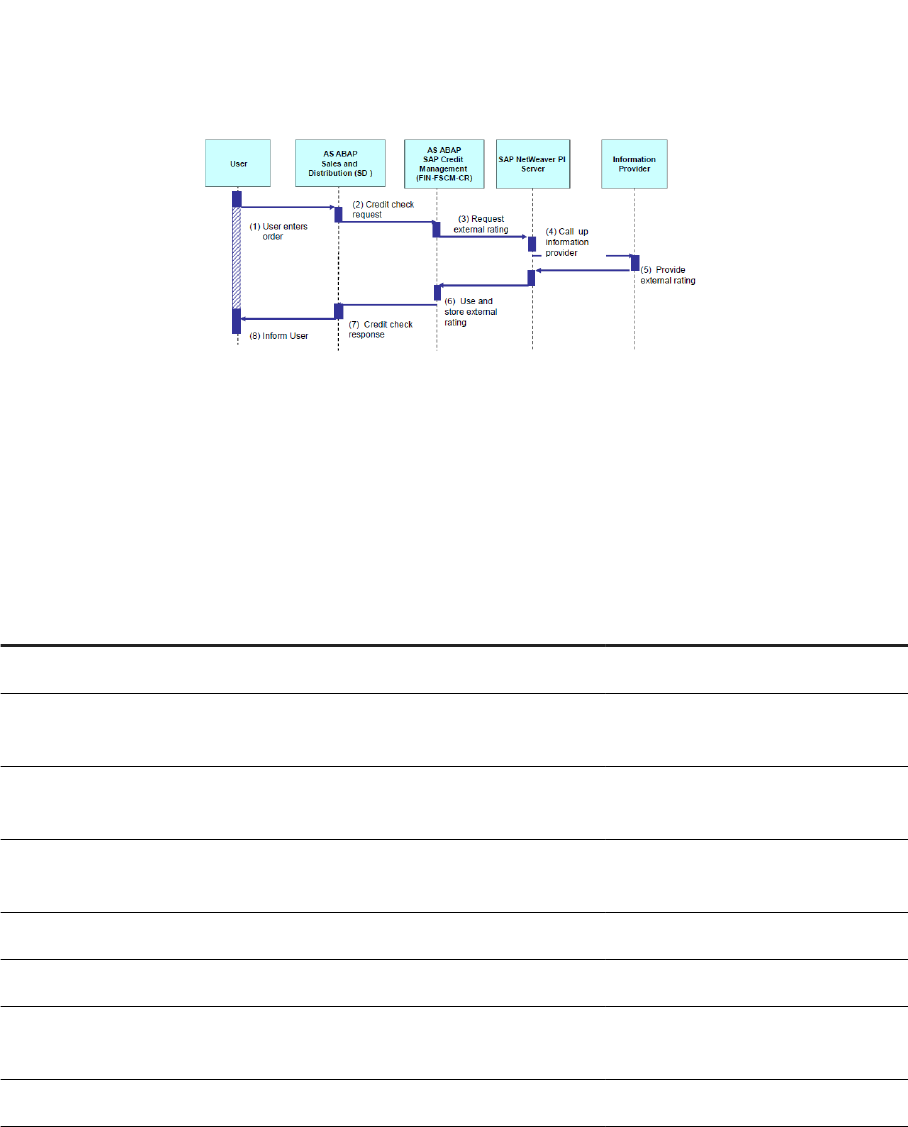
This table shows the security aspect to be considered for the process step and what mechanism applies.
Step Description Security Measure
1 User enters order User types: dialog or internet user
2 Credit check request Communication protocol HTTPS or
HTTP
3 Request external rating Communication protocol HTTPS or
HTTP
4 Call up information provider Communication protocol HTTPS or
HTTP
5 Provide external rating Not applicable
6 Use and store external rating Not applicable
7 Credit check response Communication protocol HTTPS or
HTTP
8 Inform user Not applicable
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 121

13.3.7.1.3 User Management
Standard Users
This table shows the standard users that are necessary for operating SAP Credit Management.
System User ID Type Password Description
SAP Credit
Management, client
systems
For example,
CREDITXIUSER
Communication user You specify the initial
password during the
installation.
The user ID and pass
word are stored in the
XI channel for the con
nection.
This is required for
communication be
tween SAP Credit
Management and cli
ent systems using the
XI channel.
You need to create this user before XI conguration. Assign both roles SAP_FIN_FSCM_CR_USER and
SAP_XI_IS_SERV_USER to the user. The user and password are added to the XI channel logon data that you
create when you congure your exchange server.
13.3.7.1.4 Authorizations
Dening Authorizations
You can control the right of access to SAP Credit Management data by assigning authorizations – separately by
credit segment and activity - to the authorization object F_UKM_SGMT. The elds of this authorization object
are:
You can restrict the access to credit segment-independent master data of SAP Credit Management (for
example, the score) by using the authorization object for business partner roles (B_BUPA_RLT) with the role
Business Partner Credit Management (
UKM000).
You can restrict the access to logs (application logs) of SAP Credit Management using the authorization object
S_APPL_LOG.
For SAP Credit Management, the following forms are relevant for object name and subobject:
Object Name Subobject Meaning
FIN-FSCM-CR BW-SCORING
Transfer of score from BW
FIN-FSCM-CR COMMITMENT
Credit exposure update
FIN-FSCM-CR CREDITCHECK
Credit check
122 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Object Name Subobject Meaning
FIN-FSCM-CR MONITOR
Update entries for external credit Infor
mation
FIN-FSCM-CR SEARCH_ID
Search ID at credit information provider
FIN-FSCM-CR REPLICATE
Replicate FI-CA score
FIN-FSCM-CR EVENTING
Log of events occurred
FIN-FSCM-CR-MASS ERROR
ERROR_BIG
ERROR_PROG
ERROR_UPD
INFO
STATISTICS
SUCCESS
WARNING
Logs of mass changes, can be dieren-
tiated by the severity of the error
13.3.7.1.5 Communication Destinations
Use
This table shows an overview of the communication destinations (RFC) used by SAP Credit Management.
Connection Destinations when Using the Integration Server
Destination Delivered User, Authorizations
INTEGRATION_SERVER
No
XIAPPLUSER
Role
SAP_XI_APPL_SERV_USER
LCRSAPRFC
No
SAPSLDAPI
No
These destinations are not application-specic but they are required for the operation of SAP Process
Integration.
For point to point connections via Web Services Reliable Messaging (WSRM), you use the SOA Manager in both
systems to create the logical port and the endpoint.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 123
13.3.7.1.6 Data Storage Security
Use
Master and transaction data of SAP Credit Management are saved in the database of the SAP system in which
SAP Credit Management is installed. They are not distributed to connected systems via XI, however they can be
optionally extracted to SAP Business Information Warehouse.
Access to this data is restricted through the authorizations for authorization object F_UKM_SGMT.
Authorizations for this authorization object are provided for role SAP_FIN_FSCM_CR_USER in the standard
delivery; you can copy the role and adapt it as required. For more information about authorization object
F_UKM_SGMT, see the conguration guide of SAP Credit Management.
Access to data on natural persons in particular is subject to data protection requirements and must be
restricted by assigning authorizations.
13.3.7.1.7 Security-Relevant Logging and Tracing
Use
All changes to the master data of SAP Credit Management are recorded as change documents in the business
partner record. Changes automatically executed by the system as a follow-on process to an event appear under
the name of the communication user if the event was triggered by an XI message.
Example
A credit check is initiated by SD; the system detects that the validity date of the credit limit has expired and
determines a new credit limit on the basis of the Customizing settings.
13.3.7.2 SAP Dispute Management
13.3.7.2.1 Technical System Landscape
Use
You can use SAP Dispute Management in a one-system scenario or in a multiple-system scenario. If you use
SAP Dispute Management in a one-system scenario, this means that you use SAP Dispute Management in the
same system as Accounts Receivable. In a multiple-system scenario, you run SAP Dispute Management in a
separate system. This communicates with the Accounts Receivable system connected by means of
synchronous and asynchronous BAPI calls and dialog calls.
124
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
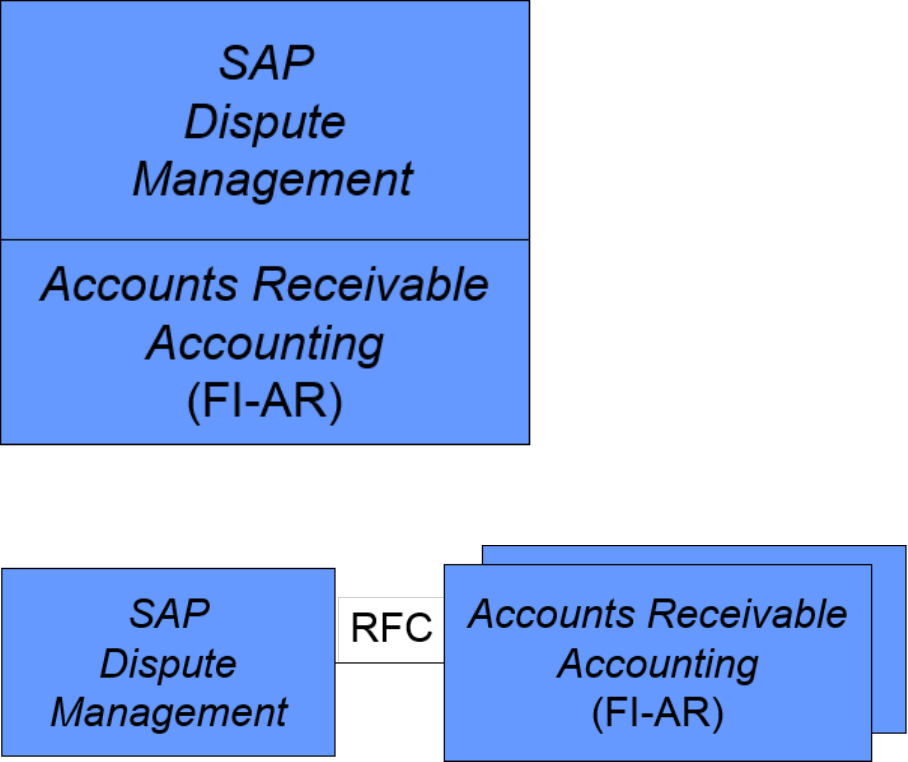
The gure below shows an overview of the technical system landscape for SAP Dispute Management in a one-
system scenario.
The gure below shows an overview of the technical system landscape for SAP Dispute Management in a
multiple-system scenario.
For SAP Dispute Management, with Business Package for Dispute Manager you can also use portal content to
use the functions of SAP Dispute Management in the portal. For security-relevant information about using the
portal content, see the SAP NetWeaver Security Guide for the usage types Enterprise Portal Core (EPC) and
Enterprise Portal (EP) in the Portal security guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 125
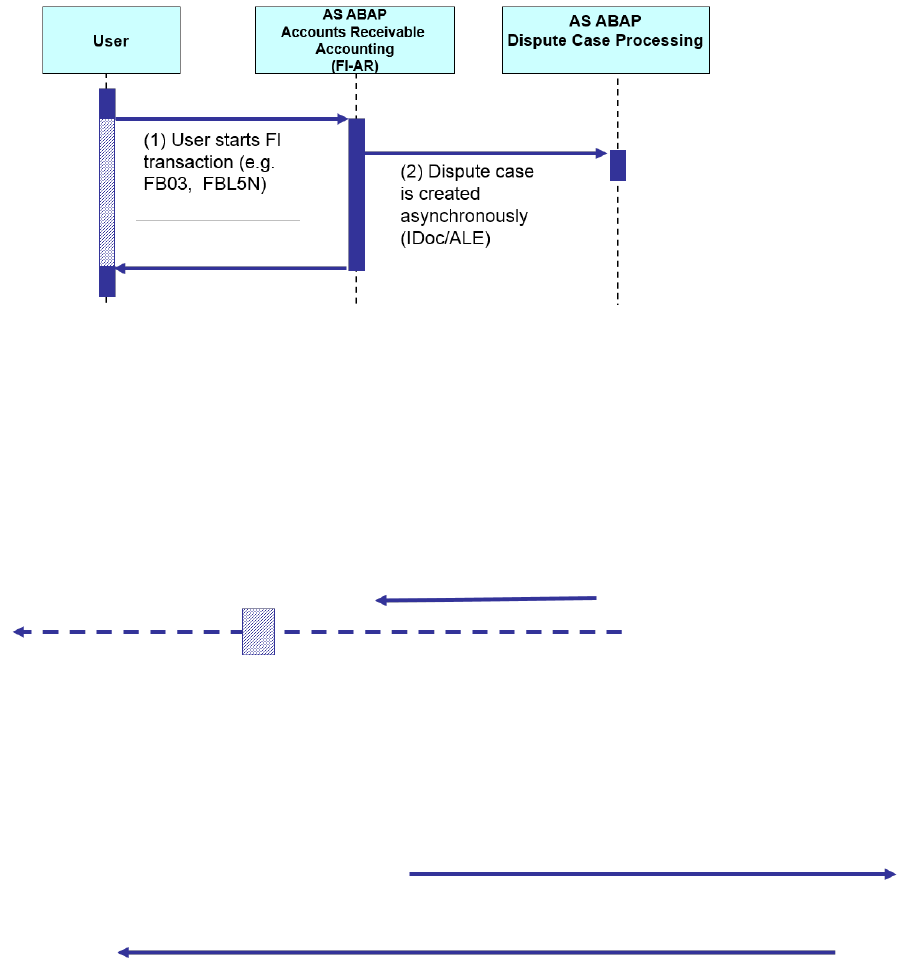
13.3.7.2.2 Security Aspects of Data, Data Flow, and Processes
The gure below shows an example of the data ow that occurs when you create a dispute case in a multiple-
system scenario:
The table below shows the security aspect to be considered for the process step and what mechanism applies.
126
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
1 User starts FI transaction (for example,
FB03 for document display or FBL5N
for line item list)
User type: Dialog user
2 Dispute case is created asynchronously
(IDoc/ALE)
User type: Technical user or, when the
Trusted/Trusting connection is used, di
alog user (see also User Administration
[page 127])
As already mentioned under Technical System Landscape [page 124], SAP Dispute Management uses BAPI
calls (IDocs) asynchronously for the data ow between the Accounts Receivable system and the Dispute Case
Processing system. The following IDocs are aected:
● Sending system: Accounts Receivable Accounting, receiving system: Dispute Case Processing
○ AttributesChange
○ Create
○ Process
● Sending system: Dispute Case Processing, receiving system: Accounts Receivable Accounting
○ AttributeSynchronize
○ StatusChanged
○ WriteO
If you are using SAP Dispute Management in a one-system scenario, synchronous BAPI calls are used instead.
13.3.7.2.3 User Management
User Administration Tools
The table below shows the user management tools for SAP DisputeManagement .
User Management Tools
Tool Detailed Description Prerequisites
User and role maintenance with
SAPNetWeaver AS ABAP (transactions
SU01 and PFCG )
For more information, see User and
Role Administration of Application
Server ABAP in the SAP NetWeaver
documentation.
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that users who perform their tasks interactively have to change their passwords on a regular basis,
but not those users who perform their tasks using background processing.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 127
The user types that are required for SAP Dispute Management include:
● Individual users:
○ For each individual user in your system, you need dialog users for the following purposes:
○ To use the system via SAP GUI for Windows
○ If you use SAPDisputeManagement in a multiple system scenario and the RFC destinations used
use a Trusted/Trusting system relationship, calls to the other system are performed using the
current user from the calling system. Therefore, for each user a valid user must also exist in the
target system.
● Technical users:
○ Background users can be used for processing in the background.
○ If you use SAPDisputeManagement in a multiple system scenario and the RFC destinations concerned
are congured such that they do not use a Trusted/Trusting system relationship, you need the
following technical users for the RFC destinations:
○ Communication users are used for synchronous and asynchronous BAPI calls (IDocs).
○ Dialog users are used for dialog calls that take place remotely in the other system.
For more information about these user types, see under User Types in the Security Guide for SAP NetWeaver
AS ABAP .
Standard Users
If you use SAP Dispute Management in a multiple system scenario and there is no Trusted/Trusting system
relationship between the systems involved, you have to congure corresponding users for the RFC
communication between the systems involved.
Note that in SAP Dispute Management , asynchronous BAPI calls, synchronous BAPI calls, and dialog calls take
place between the systems involved. There are calls from the Dispute Case Processing system to the system
for Accounts Receivable Accounting and vice versa.
The table below shows the users required if you use SAP Dispute Management in a multiple system scenario
and there is no Trusted/Trusting system relationship between the systems involved.
Standard Users
System User ID Type Password Description
System for Dispute
Case Processing
Example: ALERE
MOTE1_COM
Communication users The user ID and pass
word are stored in the
RFC destination for the
connection.
These users are used
when synchronous or
asynchronous BAPI
methods are called
from the Accounts Re
ceivable system in the
Dispute Case Process
ing system.
128 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

System User ID Type Password Description
System for Dispute
Case Processing
Example: ALERE
MOTE1_DIA
Dialog users The user ID and pass
word are stored in the
RFC destination for the
connection.
This user is used for di
alog calls from the Ac
counts Receivable Ac
counting system in the
Dispute Case Process
ing system.
Accounts Receivable
Accounting system
Example: ALERE
MOTE2_COM
Communication users The user ID and pass
word are stored in the
RFC destination for the
connection.
These users are used
when synchronous or
asynchronous BAPI
methods are called
from the Dispute Case
Processing system in
the Accounts Receiva
ble system.
Accounts Receivable
Accounting system
Example:ALERE
MOTE2_DIA
Dialog users The user ID and pass
word are stored in the
RFC destination for the
connection.
This user is used for di
alog calls from the Dis
pute Case Processing
system in the Ac
counts Receivable Ac
counting system.
Create the users and enter them in the corresponding RFC destinations. You can assign user IDs as required.
The user IDs above are merely examples.
13.3.7.2.4 Communication Destinations
Use
The following table shows an overview of the communication destinations (RFC) that you need for SAP Dispute
Management if you use it in a multiple-system scenario. You can use these communication destinations to
establish communication between the Financial Accounting system and the Dispute Case Processing system.
You can assign names for your RFC destinations as required. The names of the RFC destinations that are
specied in the table are merely examples. The destinations are not delivered in the standard system; you need
to create them yourself.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 129

Destination Description User, Authorizations
Example: DM2FIN_DIAG This destination is used for dialog calls
that take place from the Dispute Case
Processing system to the Accounts Re
ceivable system by means of RFC.
RFC user (dialog) in Accounts Receiv
able
Role:
SAP_FIN_FSCM_DM_AR_RFC_DIALOG
Contains the authorizations required by
a user to call SAP Dispute Management
dialog methods using RFC from the Dis
pute Case Processing system in the Ac
counts Receivable system.
Examples of such methods are includ
ing open items in a dispute case and
navigating from a dispute case to a
linked line item.
Example: DM2FIN_COMM This destination is used for synchro
nous and asynchronous (IDocs) BAPI
calls that take place from the Dispute
Case Processing system to the Ac
counts Receivable system.
RFC user (communication) in Ac
counts Receivable
Role:
SAP_FIN_FSCM_DM_AR_RFC_COMM
Contains the authorizations required by
a user to call synchronous and asyn
chronous SAP Dispute Management
BAPI methods from the Dispute Case
Processing system in the Accounts Re
ceivable system.
Examples of such methods are the au
tomatic write o of dispute cases and
automatic notication of Accounts Re
ceivable when conrming and voiding
cases.
Example: FIN2DM_DIAG This destination is used for dialog calls
that take place from the Accounts Re
ceivable system to the Dispute Case
Processing system by means of RFC.
RFC user (dialog) in Dispute Case
Processing
Role: SAP_FIN_FSCM_DM_RFC_DIALOG
Contains the authorizations for a user
with which the DISPLAY method is
called in the Dispute Case Processing
system from the Accounts Receivable
system by RFC. The role contains the
authorizations necessary for displaying
the dispute case.
130 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Destination Description User, Authorizations
Example: FIN2COL_COMM This destination is used for synchro
nous and asynchronous (IDocs) BAPI
calls that take place from the Accounts
Receivable system to the Dispute Case
Processing system.
RFC user (communication) in Dispute
Case Processing
Role: SAP_FIN_FSCM_DM_RFC_COMM
Contains the authorizations required by
a user to call synchronous and asyn
chronous BAPI methods from the Ac
counts Receivable system in the Dis
pute Case Processing system.
Examples of such methods are creating
dispute cases from Accounts Receiva
ble and automatically changing dispute
cases using clearing transactions in Ac
counts Receivable.
Set up RFC destinations for the ALE scenario
When you set up the RFC destinations for the ALE scenario, check whether the option of trusted/trusting
system relationship is relevant for you. Using an RFC trusted/trusting system relationship between two SAP
systems means that in the case of an RFC (Remote Function Call) from the trusted to the trusting system, no
password is sent for the logon to the trusting system. You can congure the RFC destinations in such a way that
the call in the target system occurs with the current user from the calling system without a password being
specied or entered on the logon screen. This has the following advantages, for example:
● When changes to objects or data are logged in the called system, this logging takes place with the current
user from the calling system. This makes it easier to track changes that occurred through RFC.
● You can assign individual authorizations to the users in the called system. As such you can dierentiate
which actions or functions are accessible to the user in the called system irrespective of the user.
With this procedure, you must create the users that are to be allowed to execute using RFC functions in the
called system as well. Note that in the ALE scenario of SAP Dispute Management, RFC calls take place from the
Accounts Receivable system to the Dispute Case Processing system and vice versa. A trust relationship
between SAP systems is not mutual. This means that you can choose whether one system is to be designated
as trusted for the other system and vice versa, or whether you want to dene the trust relationship only in one
direction.
In Customizing of ALE (Application Link Enabling), you can also dene dierent RFC destinations for dialog
calls, for BAPI calls, and for sending IDocs. As such you can also dene an RFC destination for the dialog calls
that use the trusted/trusting system relationship and use the current user from the calling system for the RFC
calls in the target system, whilst you dene an RFC destination for BAPI calls and for the sending of IDocs that
does not use the trusted/trusting system relationship and in which you enter a communication user.
Note
Note the following if your Accounts Receivable system is known as a trusted system by the Dispute Case
Processing system and you want to congure the RFC destination used for sending IDocs so that it uses the
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 131

trusted/trusting system relationship and the RFC calls in the target system with the current user from the
calling system:
IDocs are sent to the Dispute Case Processing system from the Accounts Receivable system when items
are cleared in the Accounts Receivable system, the clearing of items is reset, or partial payments are
executed on items for which a promise to pay exists for the corresponding invoice. If the corresponding RFC
destination uses the trusted/trusting system relationship, and carries out the call in the target system with
the current user from the calling system, this means that the user triggering the clearing, reset of clearing,
or partial payment must also be dened in the Dispute Case Processing system. You must therefore create
all users who carry out clearing, resets of clearing, or partial payments in the Accounts Receivable system,
and therefore aect dispute cases, in the Dispute Case Processing system.
13.3.7.2.5 Data Storage Security
Use
Master data, transaction data, and Customizing data of SAP Dispute Management are stored in the database of
the SAP system.
Access to the database is restricted by the authorization objects of SAP Dispute Management.
13.3.7.3 SAP Collections Management
13.3.7.3.1 Technical System Landscape
Use
You can use SAP Collections Management in a one-system scenario or in a multiple-system scenario. If you
use SAP Collections Management in a one-system scenario, this means that you use Collections Management
in the same system as Accounts Receivable. In a multiple-system scenario, you run Collections Management in
a separate system. This communicates with the Accounts Receivable system connected by means of
synchronous and asynchronous RFC calls and dialog calls.
132
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
The gure below shows the technical system landscape in a one-system scenario:
The following gure shows the technical system landscape in a multiple-system scenario:
If you connect several FI systems in a multiple-system scenario but have not installed a central system for
processing customer master data, then you can resolve conicts when assigning numbers with the connection
of Unied Key Mapping Service to SAP Process Integration (UKMS connection to SAP Process Integration).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 133
The gure below shows the technical system landscape in a multiple-system scenario with several FI
systems:
For additional information, go to http://help.sap.com/s4hana_op_1709, enter Connecting to SAP Process
Integration into the search bar, press Enter , and open the search result with that title.
13.3.7.3.2 Security Aspects of Data, Data Flow, and Processes
The following sections show an overview of the data ow in a multiple-system scenario.
13.3.7.3.2.1 Transfer of Transaction Data
The gure below shows the transfer of transaction data, meaning FI items, from the Accounts Receivable (FI-
AR) system to the Collections Management system. This is data that the system needs for creating the
worklists.
134
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
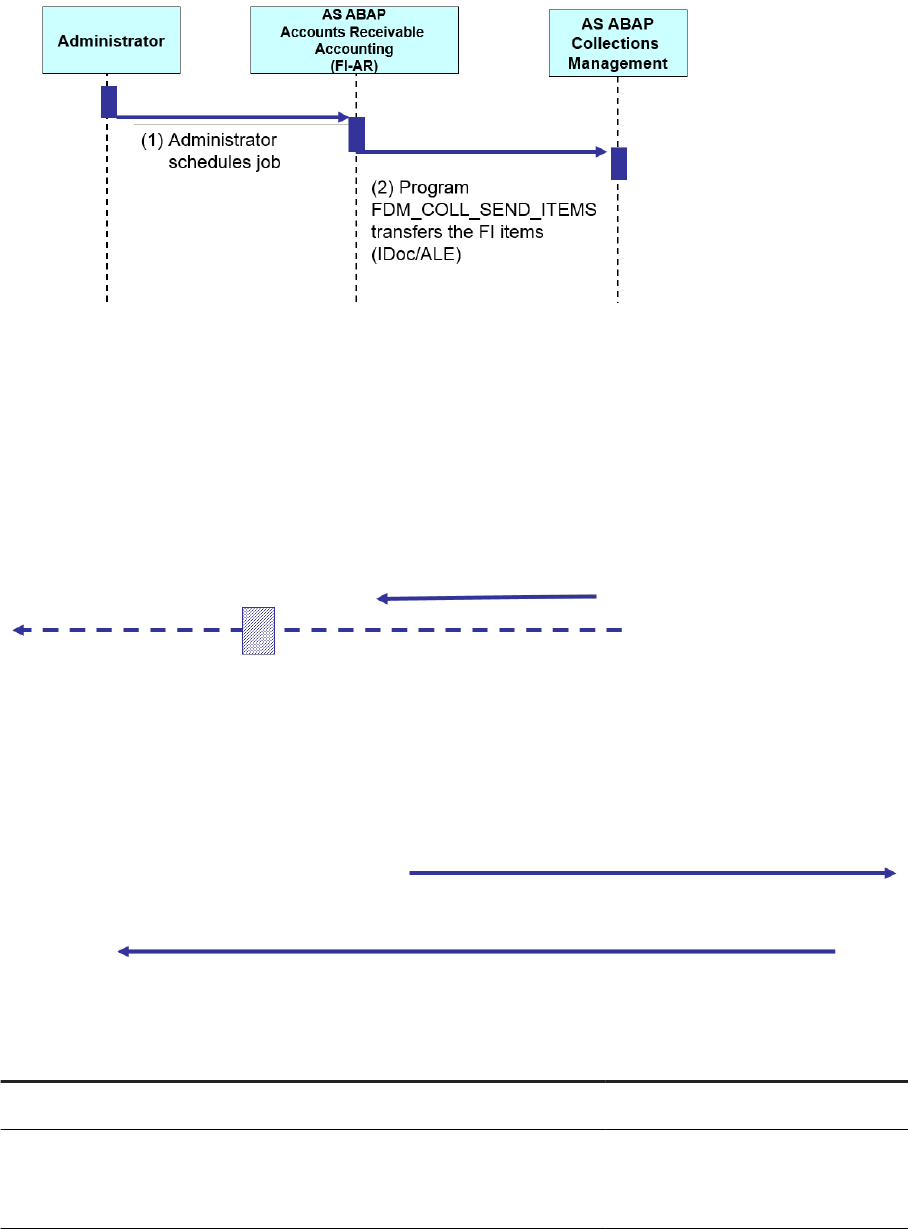
The table below shows the security aspect to be considered for the process step and what mechanism applies.
Step Description Security Measure
1 The administrator schedules the job. User type: Dialog user
2 Program FDM_COLL_SEND_ITEMS
transfers the FI items (IDoc/ALE)
User type: Technical user or, when the
Trusted/Trusting connection is used, di
alog user (see also )
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 135
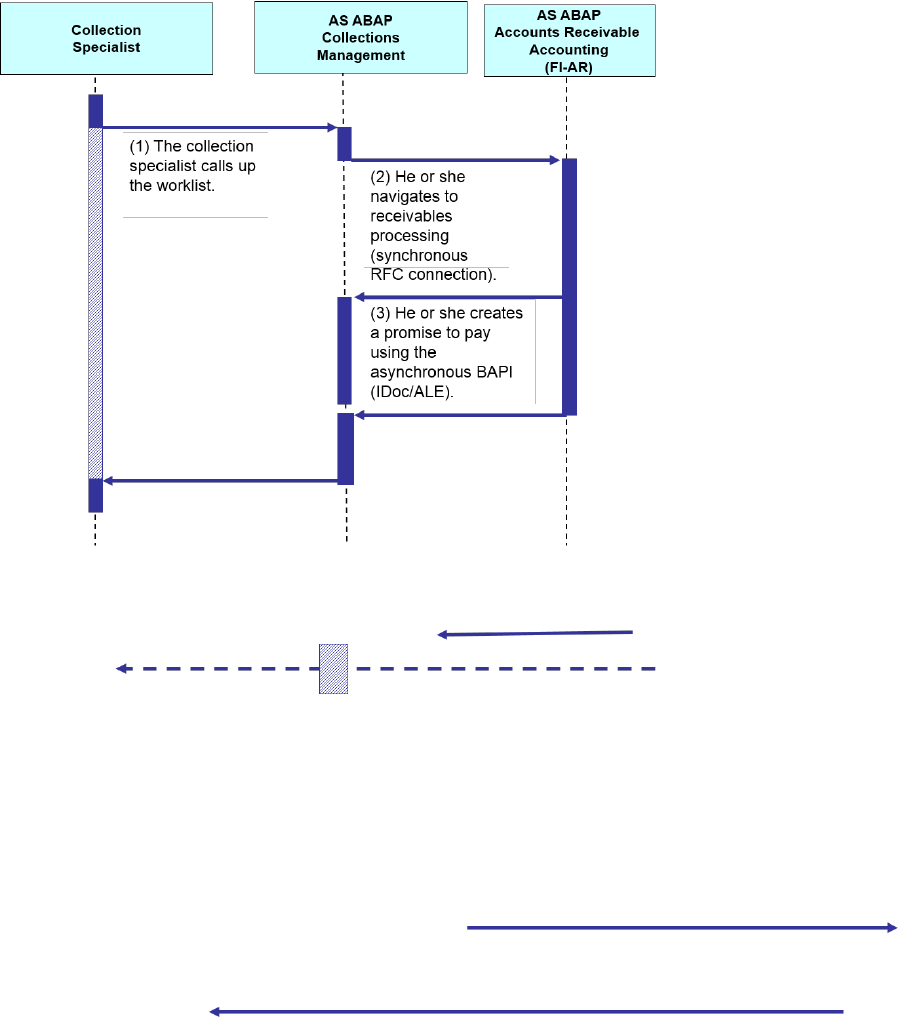
13.3.7.3.2.2 Processing of Items in the Worklist
The gure below shows how a collection specialist processes an item in his worklist, so creating a promise to
pay.
The table below shows the security aspect to be considered for the process step and what mechanism applies.
136
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
1 The collection specialist call up the
worklist (transaction UDM_SPECIAL
IST)
User type: Dialog user
2 He then navigates to receivables proc
essing (synchronous RFC connection)
User type: Dialog user
3 He creates a promise to pay with asyn
chronous BAPI (IDoc/ALE)
User type: Technical user or, when the
Trusted/Trusting connection is used, di
alog user
13.3.7.3.3 User Management
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that users who perform their tasks interactively have to change their passwords on a regular basis,
but not those users who perform their tasks using background processing.
The user types that are required for SAP Collections Management include:
● Individual users:
○ For each individual user in your system, you need dialog users for the following purposes:
○ To use the system via SAP GUI for Windows
○ If you use SAP Collections Management in a multiple system scenario and the RFC destinations
used use a Trusted/Trusting system relationship, calls to the other system are performed using
the current user from the calling system. Therefore, for each user a valid user must also exist in the
target system.
● Technical users:
○ Background users can be used for processing in the background.
○ If you use SAP Collections Management in a multiple system scenario and the RFC destinations
concerned are congured such that they do not use a Trusted/Trusting system relationship, you need
the following technical users for the RFC destinations:
○ Communication users are used for synchronous and asynchronous BAPI calls (IDocs).
○ Dialog users are used for dialog calls that take place remotely in the other system.
Standard Users
If you use SAP Collections Management in a multiple system scenario and there is no Trusted/Trusting system
relationship between the systems involved, you have to congure corresponding users for the ALE/RFC
communication between the systems involved.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 137

Note that in SAP Collections Management, asynchronous BAPI calls (IDocs), synchronous BAPI calls, and
dialog calls take place between the systems involved. There are calls from the Collections Management system
to the system for Accounts Receivable Accounting and vice versa.
The following table shows the standard users required if you use SAP Collections Management in a multiple
system scenario and there is no Trusted/Trusting system relationship between the systems involved.
System User ID Type Password Description
Collections Manage
ment system
Example: ALE-DIAG1 Dialog users The user ID and pass
word are stored in the
RFC destination for the
connection.
This user is used for di
alog calls from the Ac
counts Receivable Ac
counting system in the
Collections Manage
ment system.
Collections Manage
ment system
Example: ALE-COMM1 Communication users The user ID and pass
word are stored in the
RFC destination for the
connection.
This user is used for
synchronous BAPI
calls or asynchronous
BAPI calls (IDocs) from
the Accounts Receiva
ble Accounting system
in the Collections Man
agement system.
Accounts Receivable
Accounting system
Example: ALE-DIAG2 Dialog users The user ID and pass
word are stored in the
RFC destination for the
connection.
This user is used for di
alog calls from the Col
lections Management
system in the Ac
counts Receivable Ac
counting system.
Accounts Receivable
Accounting system
Example: ALE-COMM2 Communication users The user ID and pass
word are stored in the
RFC destination for the
connection.
This user is used for
synchronous BAPI
calls or asynchronous
BAPI calls (IDocs) from
the Collections Man
agement system in the
Accounts Receivable
Accounting system.
Create the users required and enter them in the corresponding RFC destinations. You can assign user IDs as
required. The user IDs above are merely examples.
138
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.3.7.3.4 Communication Destinations
Use
The following table shows an overview of the communication destinations that you need for SAP Collections
Management if you use it in a multiple-system scenario. You can use these communication destinations to
establish communication between the Financial Accounting system and the system that contains SAP
Collections Management.
You can assign names for your RFC destinations as required. The names of the RFC destinations that are
specied in the table are merely examples. The destinations are not delivered in the standard system; you need
to create them yourself.
Destination Description User, Authorizations
Example: COL2FIN_DIAG This destination is used for dialog calls
that take place from the Collections
Management system to the Accounts
Receivable system by means of RFC.
RFC user (dialog) in Receivables Proc
essing
Role:
SAP_FIN_FSCM_COL_AR_RFC_DIALOG
Contains the authorizations for a user
with which the navigate to receivables
processing from the worklist by means
of RFC. The authorizations permit the
following activities:
Display of invoice data
Display of payment data
Display of invoice history
Creation, change, or display of a con
tact person
Example: COL2FIN_COMM This destination is used for synchro
nous and asynchronous (IDocs) BAPI
calls that take place from the Collec
tions Management system to the Ac
counts Receivable system.
RFC user (communication) in Ac
counts Receivable
Role:
SAP_FIN_FSCM_COL_AR_RFC_COMM
Contains authorizations for a user with
which synchronous and asynchronous
BAPI methods are called from the SAP
Collections Management system in the
Accounts Receivable system.
An example of such a method is the au
tomatic notication to Accounts Re
ceivable when promises to pay are con
rmed and voided.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 139

Destination Description User, Authorizations
Example: FIN2COL_DIAG This destination is used for dialog calls
that take place from the Accounts Re
ceivable system to the Collections Man
agement system by means of RFC.
RFC user (dialog) for collections man
agement functions
Role:
SAP_FIN_FSCM_COL_RFC_DIALOG
Contains authorizations for a user with
which dialog methods are called in the
SAP Collections Management system
from the Financial Accounting system
by means of RFC.
For example, navigation from receiva
bles processing to the detail display of
the promise to pay or dispute case.
Example: FIN2COL_COMM This destination is used for synchro
nous and asynchronous (IDocs) BAPI
calls that take place from the Accounts
Receivable system to the Collections
Management system.
RFC user (communication) for collec
tions management
Role: SAP_FIN_FSCM_COL_RFC_COMM
Contains authorizations for a user with
which synchronous and asynchronous
methods are called in the SAP Collec
tions Management system from the Fi
nancial Accounting system.
For example:
Posting of IDocs with data from Finan
cial Accounting
Creation of dispute cases, promises to
pay, customer contacts, and resubmis
sions
Reading of attributes of dispute cases,
promises to pay, customer contacts,
and resubmissions for display in receiv
ables processing
Possible additional necessary destinations
If you connect several FI systems in a multiple-system scenario and use the connection of Unied Key Mapping
Service to SAP Process Integration (UKMS connection to SAP Process Integration) to resolve conicts when
assigning numbers, you also need to set up the following destinations:
● Calls from the of accounts receivable system to the system of SAP Process Integration (PI system)
● Calls from the Collections Management system to the PI system
140
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

For additional information, see Customizing of SAP Collections Management under Basic Settings for
Collections Management Business Partners Master Data Distribution for Several FI Systems , if you have
activated business function FSCM Functions 2 (FIN_FSCM_CCD_2).
For additional information about the security aspects of the CRM Middleware that you can use as a tool for
master data replication, see the Security Guide for SAP Customer Relationship Management.
Set up RFC destinations for the ALE scenario
When you set up the RFC destinations for the ALE scenario, check whether the option of trusted/trusting
system relationship is relevant for you. Using an RFC trusted/trusting system relationship between two SAP
systems means that in the case of an RFC (Remote Function Call) from the trusted to the trusting system, no
password is sent for the logon to the trusting system. You can congure the RFC destinations in such a way that
the call in the target system occurs with the current user from the calling system without a password being
specied or entered on the logon screen. This has the following advantages, for example:
When changes to objects or data are logged in the called system, this logging takes place with the current user
from the calling system. This makes it easier to track changes that occurred through RFC.
You can assign individual authorizations to the users in the called system. As such you can dierentiate which
actions or functions are accessible to the user in the called system irrespective of the user.
With this procedure, you must create the users that are to be allowed to execute using RFC functions in the
called system as well. Note that in the ALE scenario of SAP Collections Management, RFC calls take place from
the Accounts Receivable system to the Collections Management system and vice versa. A trust relationship
between SAP systems is not mutual. This means that you can choose whether one system is to be designated
as trusted for the other system and vice versa, or whether you want to dene the trust relationship only in one
direction.
In the Customizing of ALE (Application Link Enabling), you can also dene dierent RFC destinations for dialog
calls, for BAPI calls, and for sending IDocs. As such you can also dene an RFC destination for the dialog calls
that use the trusted/trusting system relationship and use the current user from the calling system for the RFC
calls in the target system, whilst you dene an RFC destination for BAPI calls and for the sending of IDocs that
does not use the trusted/trusting system relationship and in which you enter a communication user.
Note
Note the following if your Accounts Receivable system is known as a trusted system by the Collections
Management system and you want to congure the RFC destination used for sending IDocs so that it uses
the trusted/trusting system relationship and carries out the RFC calls in the target system with the current
user from the calling system:
IDocs are sent to the Collections Management system from the Accounts Receivable system when items
are cleared in the Accounts Receivable system, the clearing of items is reset, or partial payments are
executed on items for which a promise to pay exists for the corresponding invoice. If the corresponding RFC
destination uses the trusted/trusting system relationship, and carries out the call in the target system with
the current user from the calling system, this means that the user triggering the clearing, reset of clearing,
or partial payment must also be dened in the Collections Management system. You must therefore create
all users who carry out clearing, resets of clearing, or partial payments in the Accounts Receivable system,
and therefore aect promises to pay, in the Collections Management system.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 141

13.3.8 SAP S/4HANA Financial Closing cockpit
13.3.8.1 Authorizations
The SAP S/4HANA Financial Closing cockpit uses the authorization concept provided by the SAP NetWeaver
AS ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP
NetWeaver AS Security Guide ABAP also apply to the SAP S/4HNA Financial Closing cockpit.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP and the User Management
Engine's user administration console on the AS Java.
For more information about how to create roles, go to the SAP Help Portal and search for User and Role
Administration of Application Server ABAP. There, go to Conguration of User and Role Administration Role
Administration
Authorizations for Business Intelligence (BI) iViews
BI authorizations are maintained separately from the authorizations in the SAP S/4HANA Financial Closing
cockpit. You need the standard BI authorizations for executing queries.
For more information, go to the SAP Help Portal and search for Data Warehouse Management. There, go to
Authorizations Authorizations for Working with Queries .
13.3.9 Travel Management
142
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.3.9.1 Travel Management
Authorizations
Standard Roles in Travel Management (for Web Dynpro ABAP-Based Applications)
Role Description
SAP_FI_TV_WEB_TRAVELER_2
Traveler
The role contains the authorization prole needed to execute
the applications of the Travel and Expenses Employee Self-
Service (ESS) in SAP Enterprise Portal.
SAP_FI_TV_WEB_TRAVELER_EXT_TP
Traveler
Users with this role can execute the work center for travelers
and the corresponding applications in NWBC. NWBC calls a
third-party travel planning solution instead of SAP Travel
Planning.
The role contains the authorization prole needed to execute
the applications of the Travel and Expenses ESS in SAP
Enterprise Portal.
SAP_FI_TV_WEB_ESS_TRAVELER_2
ESS Single Role for Travelers
Users with this role can execute the work center for travelers
and the corresponding applications in NWBC.
This role is integrated into the ESS role for Web Dynpro
ABAP-based applications (SAP_EMPLOYEE_ESS_WDA_1).
SAP_FI_TV_WEB_ASSISTANT_2
Travel Assistant
Users with this role can execute the work center for travel
assistants and the corresponding applications in NWBC.
The role contains the authorization prole needed to execute
the applications of the Travel and Expenses ESS in SAP
Enterprise Portal.
SAP_FI_TV_WEB_ESS_ASSISTANT_2
Travel Assistant
Users with this role can execute the work center for travel
assistants and the corresponding applications in NWBC.
SAP_FI_TV_WEB_APPROVER_2
Approving Manager
Users with this role can execute the work center for approv
ing managers and the corresponding applications in NWBC.
This role is integrated into the MSS role for Web Dynpro
ABAP-based applications (SAP_MANAGER_MSS_NWBC).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 143

Role Description
SAP_FI_TV_WEB_POLICY_ADMIN_2
Travel Policy Administrator
Users with this role can execute frequently used Customiz
ing applications for policy management in NWBC.
SAP_FI_TV_TIC_AGENT
Travel Interaction Center Agent
This role authorizes service agents to run the required trans
actions and Web Dynpro ABAP-based applications in the
Travel Management system from within the Travel Interac
tion Center.
The Travel Interaction Center is a Shared Services Center in
SAP Customer Relationship Management (SAP CRM).
Authorization Proles
The standard system contains the travel prole FI-TV (infotype 0470 of Human Resources Management
(HCM)). Alternatively, you can create the authorization prole by means of organizational assignment using the
HR feature TRVCP.
Authorization Objects
For all general functions, Travel Management uses the authorization object P_TRAVL.
The transfer of results from expense reports to accounting is protected by the authorization object F_TRAVL.
The travel plan status is protected by the authorization object F_TRAVL_S.
Network and Communication Security
In Travel Management, you can set up connections to the following global distribution systems (GDS):
● Amadeus
The partner is responsible for the Gateway.
● Galileo
The partner is responsible for the Gateway.
Alternatively or in addition, you can use SAP Process Integration to set up direct connections to the following
travel service providers:
● Flight reservation systems, for example, low-cost carrier providers
Depending on the partner, communication with the Web services is HTTPS or HTTP based.
● Hotel reservation systems such as HRS
Depending on the partner, communication with the Web services is HTTPS or HTTP based. For the
communication channel, you can make various security settings. For more information, see the
Conguration Guide.
● Rail portals such as Deutsche Bahn (BIBE)
Communication with the Web services is HTTPS based.
144
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Alternatively, instead of using SAP Travel Planning, you can use third-party online booking systems (third-party
travel planning) such as:
● GetThere
Communication with the Web services of GetThere (and of Sabre, if applicable) is HTTPS based.
In SAP Enterprise Portal, you can use Single Sign-On (SSO) to automatically log on the SAP Travel
Management users to a third-party online booking system.
● e-Travel
Communication with the Web services of e-Travel is HTTPS based.
In SAP Enterprise Portal, you can use SSO to automatically log on the SAP Travel Management users to a
third-party online booking system.
For credit card clearing in Travel Management, you can use SAP Process Integration to set up direct connections
to credit card companies. You agree upon the safeguarding of the connection with the respective partner. For
more information, see
SAP Library under Travel Management (FI-TV) Travel Expenses (FI-TV-COS) Credit
Card Clearing .
Data Storage Security
Travel Management transmits credit card information to the named partners. The data in the SAP system
cannot be accessed.
Travel Management supports secure handling of credit card data.
To set up connections to third-party systems, such as reservation systems, you might require company IDs and
user-specic technical passwords, which you can dene in Customizing or in user-specic infotypes. In
Customizing, this data is protected by standard authorization objects for Customizing.
Travel Management imports data from les in the le system. Therefore, it is important to explicitly provide
access to the corresponding les in the le system without allowing access to other directories or les (also
known as directory traversal). You do this by specifying logical paths and le names in the system that are
assigned to the physical paths and le names. The system validates the assignment at runtime and issues an
error message if access to a directory is requested that does not match any assignment dened.
13.3.9.2 Deletion of Personal Data in FI-TV
Use
The Travel Management (FI-TV) component might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components
Data Protection .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 145

Relevant Application Objects and Available Deletion Functionality
For information, see SAP Note 2028594 .
Relevant Application and Available WUC functionality
Application Implemented Solution Further Information
Travel Expenses (FI-TV-COS)
Where-used check (WUC)
SAP Note 2028595
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in
Customizing for Cross-Application Components under Data Protection.
13.4 Human Resources
13.4.1 User Management
Use
User management for Human Resources uses the mechanisms provided by SAP NetWeaver Application Server
(ABAP, Java, or ABAP and Java), for example, tools, user types, and password policies. See the sections below
for an overview of how these mechanisms apply to Human Resources. In addition, there is a list of the standard
users that are necessary for operating Human Resources.
User Administration Tools
The table below shows the tools for user management in Human Resources.
146
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Tool Description
User and role maintenance with SAP NetWeaver AS for
ABAP (transactions SU01 and PFCG)
For more information, look for User Administration and Iden
tity Management in ABAP Systems in the documentation of
SAP NetWeaver at http://help.sap.com/netweaver .
User Management Engine of SAP NetWeaver AS for Java This tool is used for user management of HR portal roles
(business packages).
For more information, look for User Management Engine in
the documentation of SAP NetWeaver at http://
help.sap.com/netweaver
.
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, it may be
necessary that individual users who perform tasks interactively have to change their passwords on a regular
basis, but not users who run background processing jobs.
The specic user types that are required for human resources include:
● Individual users
○ Admisnistrator
○ Personnel Administration
○ Benets Administration
○ Manager
○ Personnel Administration
○ Benets Administration
○ Compensation Administration
○ Training and Event Management
○ Specialists for
○ Personnel Administration
○ Talent Management
○ Benets Administration
○ Compensation Administration
○ Training and Event Management
● Technical users
Technical users are required for the following business processes:
○ WF-BATCH user
If you want to use the workow functions for the dierent Personnel Management functions, you must
create a WF-BATCH system user in the standard system.
○ Distribution of master data through ALE technology. For more information, see the documentation for
the report RHALEINI (HR: ALE Distribution of HR Master Data).
○ Compensation Management (PA-CM): For the integration with the Award function, the technical user
requires authorization for the following functions:
○ Call RFC function module HRCM_RFC_LTI_ACCRUALDATA_GET (Determine awards data for
accumulating accruals)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 147

○ Read the Award infotype (0382), authorization object P_ORGIN
○ Budget Management (PA-PM)
○ You use background processing to create commitments in accounting with a RFC connection.
Depending on the process and the system landscape used, it may be necessary to set up a user for
the background processing. You can use your own user (an additional logon is required) or set up a
special commitment engine user.
For more information about these user types, see the Security Guide for SAP NetWeaver Application Server
ABAP under http://help.sap.com/netweaver .
13.4.2 Authorizations
The authorizations topic plays a fundamental role in the area of Human Resources since access to personnel
data must be carefully protected. In SAP Human Resources, there is a two-part concept for setting up
authorizations. You should familiarize yourself with this concept if you use Human Resources components.
Human Resources uses the authorization concept provided by SAP NetWeaver Application Server. Therefore,
the security recommendations and guidelines for authorizations detailed in the Security Guide for SAP
NetWeaver AS ABAP and in the Security Guide for SAP NetWeaver AS Java also apply to Human Resources.
Note
Furthermore, Human Resources has specic structural authorizations for which the organizational
assignment is checked to see whether a user may perform an activity.
For detailed information about authorizations in Human Resources, go to http://help.sap.com/
s4hana_op_1709, enter Authorizations for Human Resources into the search bar, press Enter , and open
the search result with that title.
The SAP NetWeaver Application Server authorization concept is based on assigning authorizations to users
based on roles. For role maintenance, use the prole generator (transaction PFCG) on the SAP NetWeaver AS
ABAP.
Standard Roles
The table below shows the standard roles that are used by the Personnel Management components listed
under “Description”.
Note
The standard roles for Human Resources components that are described in a separate chapter of this
Security Guide are also in the “Authorizations” section. The same applies to the self-service components
Employee Self-Service [page 202] and Manager Self-Service [page 217] that are also described under
Cross-Application Components Self-Services in this Security Guide.
148
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Standard Roles
Role Description
SAP_HR_BN* Roles for the PA-BN (Benets) component
SAP_HR_CM* Roles for the PA-CM (Compensation Management) compo
nent
SAP_HR_CP* Roles for the PA-CM-CP (Personnel Cost Planning) compo
nent
SAP_HR_OS* Roles for the PA-OS (Organizational Structure) component
SAP_HR_PA_xx_* Roles for the international versions and country versions of
the PA-PA (Personnel Administration) component
SAP_HR_PA_PF_xx_* Roles for the PA-PF (Pension Schemes) component
SAP_HR_PD* Roles for the PA-PD (Personnel Development) component
SAP_HR_RC* Roles for the PA-RC (Recruitment) component
SAP_HR_REPORTING
Role for the Human Resources Analyst
Note
This role is obsolete. We recommend that you no longer
use this role.
SAP_ASR_ADMINISTRATOR
Enhancement of the role SAP_HR_PA_xx_* for the HR ad
ministrators that use the functions of the component PA-AS
(
HR Administrative Services)
For the roles marked with an asterisk (*), several roles exist for each of the components. For roles with xx,
where xx represents the SAP country key, various roles exist for each of the country versions.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by Human Resources.
Note
For more information about the authorization objects for Human Resources, see http://help.sap.com/
s4hana_op_1709 under Product Assistance Enterprise Business Applications Human Resources HR
Tools
Authorizations for Human Resources Technical Aspects Authorization Objects .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 149

Most Important Standard Authorization Objects
Authorization Object Name Description
P_ORGIN
HR master data Used to check the authorization for ac
cessing HR infotypes. The checks take
place when HR infotypes are edited or
read.
P_ORGINCON
HR master data with context This authorization object consists of
the same elds as the authorization ob
ject P_ORGIN, and also includes the
eld
PROFL (structural prole). A check
using this object enables user-specic
contexts to be mapped in HR master
data.
P_ORGXX
HR master data – extended check You can use this object to determine
that other elds are also to be checked.
You can determine whether this check
is to be performed in addition to or as
an alternative to the HR Master Data au
thorization check.
P_P_ORGXXCON
HR master data - extended check with
context
This authorization object consists of
the same elds as the authorization ob
ject P_ORGXX, and also includes the
eld
PROFL (structural prole). A check
using this object enables user-specic
contexts to be mapped in HR master
data
P_TCODE
HR: Transaction Code This authorization object checks some
specic SAP Human Resources trans
actions.
PLOG
Personnel planning Determines for which types of informa
tion processing a user has authoriza
tion.
PLOG_CON
Personnel planning with context This authorization object consists of
the same elds as the object PLOG, and
also includes the eld
PROFL (structural
prole). The check using this object en
ables user-specic contexts to be map
ped.
150 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Name Description
P_ASRCONT
Authorization for process content The Authorization for Process Content
object is used by the authorization
check for HR Administrative Services. It
checks the authorization for access to
various process contents and also runs
through the authorization objects that
you have specied in Customizing in
the table T77S0 (see note below). For
more information, see
http://
help.sap.com/s4hana_op_1709 under
Product Assistance Enterprise
Business Applications
Human
Resources Shared Services HR
Administrative Services (PA-AS)
HCM
Processes and Forms and section Au
thorization Concept of HCM Processes
and Forms.
P_DEL_PERN
Deletion of personnel numbers in live
systems
This authorization object is used in the
report RPUDELPP and facilitates the de
letion of personnel numbers in live sys
tems. It is used by two roles, one for re
questing the deletion and one for per
forming the deletion. These roles need
to be assigned to two dierent users
(double verication principle).
P_EICAU
Authorization for activity in the Em
ployee Interaction Center
This authorization object checks the
authorization for editing EIC activities.
For more information, see http://
help.sap.com/s4hana_op_1709 under
Product Assistance Enterprise
Business Applications Human
Resources
Shared Services
Employee Interaction Center (EIC)
General Settings and section Authori
zation Concept for Employee Interaction
Center (EIC).
Note
In Customizing for certain authorization objects, you can specify whether they are to be checked. The table
T77S0 in the Group for Semantic Short Text for PD Plan AUTSW groups all central switches and settings for
the Human Resources authorization check. Note that changes to the settings severely aect your
authorization concept.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 151

For more information about changing the main authorization switch, see Customizing for Personnel
Administration and choose Tools Authorization Management .
13.4.3 Security-Relevant Logging and Tracing
Change documents are created for the infotypes of SAP Human Resources, on the basis of which you can trace
changes to infotype data. For more information, see http://help.sap.com/s4hana_op_1709 under Product
Assistance Enterprise Business Applications Human Resources HR Tools in the following sections:
● Creating Change Documents for Personnel Administration Infotypes
● Creation of Change Documents for Personnel Planning Infotypes
13.4.4 Core HR and Payroll
13.4.4.1 Core HR
About This Chapter
This section of the Security Guide provides an overview of security-relevant information for Core HR.
Overview of the Main Sections of This Chapter
The following sections contain the security-relevant information that is specic to Personnel Management:
● Important SAP Notes
This section lists the most important SAP Notes for the security of Personnel Management.
● Authorizations
This section provides an overview of the authorization concept used for Personnel Management.
● Communication Channel Security
This section provides an overview of the communication paths used by Personnel Management and
provides information on how you can best protect them.
● Communication Destinations
This section provides an overview of the communication destination for the components of Personnel
Management and the country-specic components of Personnel Administration.
● Data Storage Security
This section provides an overview of the critical data used by Personnel Management, as well as the
security mechanisms used.
● Security for Additional Applications
152
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
This section contains information about temporary sequential (TemSe) data storage, which only
temporarily stores data from country-specic reports from Personnel Administration.
● Other Security-Relevant Information
This section contains information about security-relevant Customizing for infotype records and indicates
the reports that perform database statistics and consistency checks without checking the user's
authorizations.
● Chapter with the security-relevant information for the component HCM Processes and Forms
13.4.4.1.1 Authorizations
Use
The Personnel Management components use the two-part authorization concept from SAP Human Resources.
For more information, see section Authorizations in the SAP S/4HANA Security Guide forHuman Resources
section.
Standard Roles
The table below shows the standard roles that are used by the Personnel Management components.
Role Description
SAP_HR_OS*
Roles for the PA-OS (Organizational Structure) component
SAP_HR_PA_xx_*
Roles for the international versions and country versions of
the component PA-PA (Personnel Administration)
Note
For the roles marked with an asterisk (*), several roles exist for each of the components. For roles with “xx”,
where “xx” represents the SAP country key, various roles exist for each of the country versions.
Standard Authorization Objects
The Personnel Management components use the standard authorization objects from SAP Human Resources.
For more information about the authorization objects for Human Resources, see SAP Library for SAP S/4HANA
on SAP Help Portal at Human Resources HR Tools Authorizations for Human Resources Technical
Aspects Authorization Objects .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 153

13.4.4.1.2 Communication Channel Security
Use
The table below shows the communication channels used by Personnel Management, the protocol used for the
connection, and the type of data transferred.
Communication Path Protocol Used Type of Data Transferred
Data Requiring Particular
Protection
Interface Toolbox (Transac
tion PU12)
ALE Master data, Benets data,
organizational data as de
ned by the user
SAP BW Extractor program Master data, organizational
data, Personnel Development
data
SAP CO
(for distributed systems)
RFC Cost centers, orders, and so
on
Authorizations for CO ob
jects are required here
External les ASCII Personnel Administration
data
Applicable only for country
versions Australia and New
Zealand
MS Word Report interface with SAP
NetWeaver
Oce Integration
Connection of PDF-based
print forms to the archive
HTTP(S) Person-related data (for ex
ample, employee photo)
DIAG and RFC connections can be protected using Secure Network Communications (SNC). The Secure
Sockets Layer protocol (SSL protocol) protects HTTP connections.
Note
If you convert the protocol from HTTP to HTTPS and use PDF-based print forms, see SAP Note 1461447.
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
13.4.4.1.3 Communication Destinations
Use
Specic communication destinations are available for the Personnel Management components and Personnel
Administration country-specic components.
154
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Features
The function group HRPDV_SERVICES contains the following Remote Function Calls (RFCs) for displaying and
updating the position attributes. The communication user requires authorization for the authorization object
S_RFC to execute Remote Function Calls.
Function Group Function Module Description
HRPDV_SERVICES HRPDV_GET_ROOT_OBJECT Gets the root object for the user
HRPDV_ORG_PATHROOTS Root object specication
HRPDV_CREATE_POSITION Creates a new position in the organiza
tional unit
HRPDV_GET_POSITION_ATTR Gets the corresponding position attrib
utes
HRPDV_UPDATE_POSITION_ATTR Updates the corresponding position at
tributes
HRPDV_COPY_POSITION Copies an existing position and the cor
responding attributes several times
HRPDV_DELIMIT_POSITION Delimits an existing position
HRPDV_POSITION_SEARCH Enables a search for positions based on
Object and Data Provider (OADP)
HRPDV_GET_TIME_CONSTRAINTS Gets the time constraints information
of the corresponding position infotypes
and relationships
HRPDV_TRANSFER_EMPLOYEE Enables the conversion of an employee
from one position to another or creates
an additional personnel assignment for
the employee
HRPDV_GET_POSITION_F4_HELPS Returns the input help values for the in
fotype elds Account Assignment and
Employee Subgroup
Benets (PA-BN)
When evaluating retirement benets for employees, service-related data is sent to an external system using
IDocs. The Benets system places the IDocs in a special port. External systems can collect the IDocs from this
port. The external systems evaluate the retirement benets based on the transferred data and then send them
with an inbound IDoc back to the SAP system.
There are no special functions from the Benets system side to protect this data.
Compensation Management (PA-CM)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 155

The self-service scenario Salary Benchmarking (HRCMP0053) exchanges data with external benchmarking
providers. You communicate synchronously and online using HTTPS protocol (HyperText Transfer Protocol
with SSL).
Personnel Administration
● HR Administrative Services
HR Administrative Services can transfer personal data from SAP E-Recruiting and return data to SAP E-
Recruiting . For more information, see the Security Guide for SAP E-Recruiting under Communication
Destinations .
● Pension Fund (PA-PF)
○ You can create les with SAP List Viewer (ALV) and TemSe ( Temporary Sequential Objects ).
○ There is no encryption of data in the standard SAP system.
13.4.4.1.4 Data Storage Security
The infotypes in Personnel Management contain particularly sensitive data. This data is protected by central
authorization objects.
Note
For more information about authorization objects, see section Authorizations in the SAP S/4HANA security
guide for Human Resources.
Examples of infotypes containing particularly sensitive data:
● International infotypes for Personnel Administration (PA-PA)
○ Personal Data (0002)
○ Basic Pay (0008)
○ Bank Details (0009)
○ Family Member/Dependents (0021)
● Personnel Development (PA-PD)
○ Qualications
○ Appraisals
● Personnel Cost Planning and Simulation (PA-CP)
○ Planning of Personnel Costs (0666), contains salary-based information
● Management of Global Employees (PA-GE)
○ Compensation Package Oer (0706)
Other sensitive Personnel Management data
● Budget Management
156
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
The Budget Management component accesses the salary data of employees and displays data from the
Controlling (CO) and Funds Management (FI-FM) components. The standard authorization concept for
Human Resources , Controlling , and Funds Management is used for these processes. The following
authorization objects are also available to protect the data:
○ P_ENCTYPE ( HR: PBC - Financing ): Determines which funds reservation types a user can access and
which activities the user is allowed to perform.
○ P_ENGINE ( HR: Authorization for Automatic Commitment Creation ): Determines which activities a
user is allowed to perform when creating commitments.
● Pension Fund (PA-PF)
Access to salary data, pensions, and benets entitlements is protected by the following authorization
objects:
○ P_ORIGIN ( HR: Master Data )
○ P_CH_CK ( HR-CH: Pension Fund: Account Access )
○ P_NL_PKEV( Bevoegdheidsobject voor PF-gebeurtenissen )
● Personnel Cost Planning (PA-CM-CPand PA-CP)
The old Personnel Cost Planning (PA-CM-CP) and the new Personnel Cost Planning and Simulation (PA-CP)
components both save salary-relevant information to the clusters of the database PCL5. You can control
access rights using the authorization object P_TCODE ( HR: Transaction Code ).
● Employee Interaction Center (PA-EIC)
The EIC Authentication infotype (0816) enables question and response pairs to be saved that an agent of
Employee Interaction Center then uses to identify a calling employee. You can only maintain the infotype
with the Authentication for EIC Employee Self-Service.
● HR Administrative Services (PA-AS)
The personnel le and all process instances are saved with intermediate statuses and history to the Case
Management databases.
13.4.4.1.5 Security for Additional Applications
Personnel Administration country-specic components use several reports that store security-relevant and
sensitive data. This data includes employee data relating to salary, tax, social insurance, pension contributions,
and garnishments.
The data is stored in temporary sequential (TemSe) les and used when printing legal forms, statistics, and
business reports. Access to TemSe is controlled by the authorization object S_TMS_ACT. Data encryption is
not necessary here. For a list of all reports and programs using TemSe, see the Personnel Administration
documentation for your country version.
You can also download data directly from the front-end server (for example, PC/terminal) or application server
without rst storing the data records in the TemSe. To do so, you copy the data to a data carrier that you can
then send to the authorities.
13.4.4.1.6 Other Security-Relevant Information
Use
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 157

Other security-relevant Customizing for infotype records
With the eld Access Auth. (Access Authorization) in table V_T582A (Infotype attributes (Customizing)), you
can control access to an infotype record depending on whether the record belongs to the area of responsibility
of a person responsible on the current date. For more information, see Customizing for Personnel Management
under Personnel Administration Customizing Procedures Infotypes Infotypes . Note in particular the
help for the Access Authorization eld.
Technical utilities without integrated authorization check
The following technical utilities read data without the user’s authorizations being checked. You should therefore
only assign relevant report authorizations to roles containing system administrator functions.
● Reports with the prex RHDBST*: Database statistics
● Reports with the prex RHCHECK*: Consistency checks for Organizational Management and Personnel
Development data.
If required, you can use the following reports (developed for SAP internal use) for testing purposes.However, SAP
does not accept any responsibility for these reports:
● Report RPCHKCONSISTENCY: (Consistency check for HR master data)
● Report RPUSCNTC (Find Inconsistencies in Time Constraints)
13.4.4.1.7 HCM Processes and Forms
About this Document
This chapter provides an overview of the security-relevant information that applies to HCM Processes and
Forms (PA-AS).
Overview of the Main Sections of This Chapter
The HCM Processes and Forms chapter comprises the following sections:
● Before You Start
This section contains references to other Security Guides that build the foundation for the HCM Processes
and Forms chapter and a list of the most important SAP Notes for HCM Processes and Forms regarding
security.
● Authorizations
This section provides an overview of the authorization concept that applies to HCM Processes and Forms.
● Internet Communication Framework Security
This section provides an overview of the Internet Communication Framework (ICF) services that are used
by HCM Processes and Forms.
158
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

● Security for Additional Applications
This section provides information on a Business Add-In (BAdI) that can be used for the attachment
handling of HCM Processes and Forms.
● Other Security-Relevant Information
This section provides information on the possibility of protecting the Customizing views of HR
Administrative Services by a using a grouping option for the authorization check to prevent users without
authorization from maintaining person-related data.
13.4.4.1.7.1 Authorizations
Use
HCM Processes and Forms uses the authorization concept provided by the SAP NetWeaver AS for ABAP.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS
Security Guide ABAP also apply to HCM Processes and Forms.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see section Role Administration in the SAP Library for SAP
S/4HANA Identity Management.
Role and Authorization Concept for HCM Processes and Forms
The authorization concept for HCM Processes and Forms is described under the section Authorization Concept
of HCM Processes and Forms in the SAP Library for SAP S/4HANA HCM Processes and Forms.
Standard Roles
The table below shows the standard roles that are used for HCM Processes and Forms authorizations.
Standard Roles for HCM Processes and Forms
Role Name Description
SAP_ASR_HRADMIN_SR_HCM_CI_3
HR Administrator: NWBC Role This single role contains the authoriza
tions for the HR Administrator role.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 159
Role Name Description
SAP_ASR_EMPLOYEE_SR_HCM_CI_3
ESS Single Role for HCM PF Services This single role contains the authoriza
tions for the Employee role in Employee
Self-Service (WDA).
SAP_ASR_EMPLOYEE
HR Administrative Services : Employee This single role contains the authoriza
tions for the Employee role in the
Business Package for Employee Self-
Service (up to and including 1.4.1).
SAP_ASR_MANAGER
HR Administrative Services : Manager This single role contains the authoriza
tions for the Manager role.
Note
The Employee and Manager roles use HCM Processes and Forms. For security-relevant information
regarding these components, see the sections Employee Self Service and Manager Self Service under Self
Services in the S/4 HANA Security Guide.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by HCM Processes and Forms:
Authorization Object Name Comment
S_RFC
Authorization Check for RFC Access
S_SCMG_CAS
Case Management: Case These authorization objects manage
access to the Process Object of HCM
Processes and Forms.
S_SCMG_FLN
Case Management: Authorization by
Field
S_SRMGS_CT
Records Management: Authorizations
for Document Content
These authorization objects manage
access to the digital Personnel File in
the HR Administrator Role.
S_SRMGS_DC
Records Management: Authorization
for Documents
S_SRMGS_PR
Records Management: Authorizations
for Attributes
S_SRMSY_CL
SAP Records Management : General
Authorization Object
S_TCODE
Transaction Code Check at Transaction
Start
160 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Name Comment
P_ASRCONT
Authorization for Process Content This authorization object manages the
rights to start and execute processes
with HCM Processes and Forms.
13.4.4.1.7.2 Internet Communication Framework Security
Use
You should only activate those services that are needed for the applications running in your system. For HCM
Processes and Forms, the following services are needed which you can nd under the path
default_host/sap/bc/webdynpro/sap/:
● asr_form_display
● asr_keyword_search
● asr_launchpad
● asr_mass_start_process
● asr_OBJECT_SEARCH
● asr_pa_pd_processes_display
● ars_personnel_file
● asr_processes_display
● ASR_PROCESS_EXECUTE_FPM
● asr_process_select
● ars_profiles_show
● asr_srch_pd_process
Activities
Use the transaction SICF to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
More Information
For more information, see Activating and Deactivating ICF Services in the SAP NetWeaver Library
documentation.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 161

13.4.4.1.7.3 Security for Additional Applications
For the uploading of attachments in HCM Processes and Forms you can use Business Add-In (BAdI)
HRASR00ATTACHMENT_HANDLING for dening the le types allowed and the maximum size of attachments. For
more information, see the BAdI documentation in the SAP S/4HANA system.
13.4.4.1.7.4 Other Security-Relevant Information
Authorizations for the Implementation Guide for HR Administrative Services
The views in the Implementation Guide for HR Administrative Services are protected separately by a grouping
for the authorization check to prevent users without authorization maintaining person-related data. Under the
eld name DICBERCLS ( Authorization Group), you can set the following in the authorization object
S_TABU_DIS:
● Switch PASC: Authorization check for all views of HR Administrative Services in which no Customizing
settings were made that aect authorization checks for the users of HR Administrative Services.
● Switch PASA: Additional authorization check for the views that may aect the authorization check for users
of HR Administrative Services.
13.4.4.1.8 Personnel & Organization
About This Chapter
This chapter of the Security Guide provides an overview of the security-relevant information for Personnel &
Organization (PA-PAO).
Role and Authorization Concept for Personnel & Organization
The Personnel & Organization component uses the following authorization concepts:
● SAP NetWeaver authorization concept (based on assigning authorizations to users based on roles)
For this purpose, the roles mentioned in section Standard Roles are available as a template. You can copy
the standard roles to the customer name space and adjust them to suit your requirements. You use the
prole generator (transaction PFCG) to maintain roles.
● Structural Authorizations (HCM-specic authorization concept)
You congure structural authorizations in Customizing for Personnel & Organization by choosing the
following path:
Security Authorizations Structural Authorizations .
For more information about the structural authorization check, see Structural Authorization Check (in SAP
Library for SAP S/4HANA under Human Resources HR Tools Authorizations for Human
Resources
).
Standard Roles
162
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
The following standard single roles are available for the Personnel & Organization component: Single Roles for
Personnel & Organization.
Gateway Information
For information on security information for Gateway, please see:
Security Settings in the SAP Gateway
The SAP Gateway Foundation Security Guide available via http://help.sap.com//nw74 Security Information
Security Guide and search for the document SAP NetWeaver Gateway Foundation Security Guide.
13.4.4.2 Payroll (PY)
About This Chapter
This section of the Security Guide provides an overview of security-relevant information for Payroll (PY).
Overview of the Main Sections of This Chapter
The chapter “Payroll” comprises the following main sections:
● Important SAP Notes
This section lists the most important SAP Notes with regard to the security of Payroll.
● User Management
This section provides an overview of the user types required for Payroll.
● Authorizations
This section provides an overview of the authorization concept used for Payroll.
Note also the section Authorizations for Human Resources overall.
● Communication Channel Security
This section provides an overview of the communication paths used by Payroll.
● Data Storage Security
This section provides an overview of the critical data used by Payroll, as well as the security mechanisms
used.
● Security for Third-Party Applications or Additional Applications
This section contains security information that applies for additional applications that are used together
with Payroll (for example, the Interface Toolbox or B2A: Communication with Authorities).
● Country-Specic Features
This section contains additional security-relevant information for some country versions.
Note
The information in the chapter “Payroll (PY)” applies for all country versions of Payroll. The country-
specic sections only contain additional country-specic information, if any exists.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 163

13.4.4.2.1 Important SAP Notes
The following table lists the most important SAP Notes with regard to the security of Payroll.
Title SAP Note Comment
Analyzing HR authorizations
902000
Contains general information about au
thorizations in the attachments
Q&A: How to customize Payroll Ac
counting postings in Rel.4.x
116523
Explains that the display authorizations
for posting to Accounting are controlled
using the report authorizations (that is,
there are no table authorizations)
13.4.4.2.2 User Management
Denition
User management for Payroll uses the mechanisms provided by the SAP Web Application Server ( ABAP), for
example, tools, user types, and password policies. For an overview of how these mechanisms apply for Payroll ,
see the sections below. In addition, there is a list of the standard users that are necessary for operating Payroll .
User Management Tools
The table below shows the tools to use for user management with Payroll .
User Management Tools
Tool Detailed Description Prerequisites
User and Role Maintenance (transac
tion PFCG)
You can use the Role Maintenance
transaction PFCG to generate proles
for your Payroll users.
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively have to change their passwords on a regular
basis, but not those users under which background processing jobs run.
164
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
The user types required for Payroll include:
● Individual users
○ Administration user
○ Payroll manager
○ Payroll specialist
● Technical users
○ Payroll procedure administrator
○ ALE user for posting payroll results to Accounting
For more information about these user types, see the SAP Web AS ABAP Security Guide under User Types.
13.4.4.2.3 Authorizations
Role Concept and Authorization Concept for Payroll
Payroll uses the authorization concept provided by SAP NetWeaver Application Server for ABAP, which is
based on the assignment of authorizations to users using roles.
The roles named as “standard roles” are available as templates. You can copy the standard roles into the
customer-specic namespace and adjust them to suit your requirements. To maintain roles, you use the Prole
Generator (transaction PFCG).
Standard Roles
The following table shows examples of standard roles that are used by the Payroll component.
Standard Roles
Role Description
SAP_HR_PY_xx_PAYROLL-ADM Payroll administrator <xx>
SAP_HR_PY_xx_PAYROLL-MANAGER Payroll manager <xx>
SAP_HR_PY_xx_PAYROLL-PROC-ADM Payroll procedure administrator <xx>
SAP_HR_PY_xx_PAYROLL-SPEC Payroll specialist <xx>
SAP_HR_PY_xx_* Roles for mapping country-specic tasks within Payroll
SAP_HR_PY_PAYROLL-LOAN-ADM Loan accounting administrator
xx stands for the country key. For the roles marked with an asterisk (*), additional roles exist for each of the
countries.
Standard Authorization Objects
Payroll uses the authorization objects that are usually available for Human Resources. For more information,
see Authorizations .
The following table shows the security-relevant authorization objects that are also used by Payroll .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 165

Standard Authorization Objects
Authorization Objects Name Description Additional Information
P_PBSPWE Process Workbench Engine
(PWE) authorization
Authorizations for the Proc
ess Workbench Engine(PWE)
P_PCLX HR: Cluster Check when accessing HR
les on the PCLx (x = 1, 2, 3,
4) databases
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_PCLX (HR:
Cluster)
P_PCR HR: Personnel control record Authorization check for the
personnel control record
(transaction PA03)
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_PCR (HR:
Personnel Control Record)
P_PE01 HR: Authorization for person
nel calculation schemes
Authorization check for per
sonnel calculation schemes
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_PE01 (HR:
Authorization for Personnel
Calculation Schemas)
P_PE02 HR: Authorization for person
nel calculation rule
Authorization check for per
sonnel calculation rules
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_PE02 (HR:
Authorization for Personnel
Calculation Rule)
166 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Objects Name Description Additional Information
P_PYEVDOC HR: Posting document Protection of actions on pay
roll posting documents
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_PYEVDOC (HR:
Posting Document)
P_PYEVRUN HR: Posting run Control of actions that are
possible for posting runs
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_PYEVRUN (HR:
Posting Run)
P_OCWBENCH HR: Activities in the O-Cycle
Workbench
Used for the authorization
check in the O-Cycle Work
bench.
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_OCWBENCH
(HR: Activities in the O
Cycle Workbench)
S_TMS_ACT Actions on TemSe objects The authorization deter
mines who may execute
which operations on which
TemSe objects
SAP Library for SAP S/
4HANA under
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects S_TMS_ACT
(TemSe: Actions on TemSe
Objects)
For documentation about authorization objects, see SAP Library for SAP S/4HANA and choose Human
Resources HR Tools Authorizations for Human Resources Technical Aspects Authorization Objects .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 167

Authorizations for Posting Data to Accounting
The authorization check for posting data to Accounting is performed using report authorizations. This means
that the dierent level of detail of the data comes from calling dierent reports and can be restricted using
corresponding report authorizations.
When posting data to Accounting, the following authorization checks are made:
● Report RPCIPA00
○ Authorization object S_Program, based on report RPCIPA00
○ Authorization object P_PYEVRUN, based on:
○ Run type PP
○ Run information (simulation, productive)
○ Activity (display)
● Report RPCIPS00
○ Authorization object S_Program, based on report RPCIPS00
○ Authorization object P_PYEVDOC, based on:
○ Company code of document
○ Activity (display of contents of posting document)
● Report RPCIPD00
○ Authorization object S_Program, based on report RPCIPD00
○ Authorization object P_PYEVDOC, based on:
○ Company code of document
○ Activity (display of detailed posting information with data related to personnel number)
For more information, see SAP Note 1235291.
13.4.4.2.4 Communication Channel Security
Use
The table below shows the communication channels used by Payroll , the protocol used for the connection, and
the type of data transferred.
Communication Paths
Communication Paths Protocol Used Type of Data Transferred
Data Requiring Special Pro
tection
Interface Toolbox (Transac
tion PU12)
ALE, local les Determined by the user Salary data, HR master data
Display posting runs (trans
action PCP0)
ALE Data for cost accounting Salary data (accumulated in
part)
Display documents from Ac
counting
ALE Documents from Accounting
168 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Communication Paths Protocol Used Type of Data Transferred
Data Requiring Special Pro
tection
Data medium les (creation
in Accounting)
Local les Files for transfer of bank
transfers to the banks
Salary data
Display original document for
an external wage component
in infotype External Wage
Components (0579)
RFC Documents from Accounting Additional salary data from
external systems
RFC connections can be protected using Secure Network Communications (SNC). For more information, see
the SAP NetWeaver Security Guide under Transport Layer Security.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
In addition, there is also an authorization check for calling the RFC-capable function module itself (CALL
FUNCTION 'AUTHORITY_CHECK_RFC'). For more information, see SAP NetWeaver Library and choose RFC
Programming in ABAP.
For more information about the security of ALE connections, see SAP NetWeaver Security Guide ALE.
13.4.4.2.5 Data Storage Security
Data Storage
The payroll results are saved as compressed to an INDX-like table. In the standard system, access is protected
using the read and write authorizations for the infotypes and the authorizations for the required cluster.
The Payroll data and the posting to Accounting are saved to the databases of SAP NetWeaver Application
Server (AS) ABAP. Payroll uses the standard security concept of SAP NetWeaver AS for ABAP for this.
The payroll results in the table PCL2 are protected using the authorization object P_PCLX.
The posting data is stored in the table PPOIX and other transparent tables. Access to the posting data is
regulated using the report authorizations. For more information, see Authorizations under Payroll.
Caution
Data stored in database tables can be displayed using the transactions SE16 or SE16N even without an
application-specic authorization check. To prevent this, you remove the authorizations for these
transactions in productive systems or adjust them accordingly.
For more information, see SAP NetWeaver Library under Authorization Checks and in SAP NetWeaver
Application Server for ABAP.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 169

Using Logical Paths and File Names to Protect Access to the File System
Payroll saves data in les in the local le system. Therefore, it is important to assign explicit access to the
corresponding les in the le system without access to other directories or les (also called directory
traversal). This is achieved by entering logical paths and le names in the system that are assigned to the
physical paths and le names. This assignment is validated at runtime. If access to a directory is requested that
does not correspond to a stored assignment, an error occurs.
The following lists show the logical le names and paths that are used by Payroll, and the reports for which
these le names and paths are valid:
Logical File Names and Path Names Used in Payroll
The following logical le names and logical le paths were created using transaction FILE to facilitate the
validation of physical le names:
Logical File Name Reports That Use These Logical File
Names
Logical File Path
HR_XX_DIR_RPUFCP01 RPUFCP01 HR_XX_DIR_RPUFCP01
In addition, country-specic logical le names and le paths were created for some country versions. For more
information, see the following sections of the Security Guide:
● Country-Specic Features: Canada
● Country-Specic Features: Germany
● Country-Specic Features: Great Britain
● Country-Specic Features: Non-Prot Organizations
● Country-Specic Features: Singapore
● Country-Specic Features: USA
● Country-Specic Features: Other Countries
Activating Validation of Logical Paths and File Names
These logical paths and le names are specied in the system for the corresponding reports. Due to downward
compatibility reasons, the validation is deactivated by default at runtime. To activate the validation at runtime,
you maintain the physical path using the transactions FILE (client-independent) and SF01 (client-dependent).
To determine which paths are used by your system, you can activate the corresponding settings in the Security
Audit Log.
For more information, see the following:
● Logical File Names
● Protecting Access to the File System
● Security Audit Log
170
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.4.4.2.6 Security for Additional Applications
Display of Documents Using Remote Function Call (RFC)
Posting Data to Accounting
Administrators for Accounting can use the transaction PCP0 ( Display posting runs ) to display posting
documents for Human Resources by choosing Goto Document Overview Goto Accounting
Documents . The administrator requires a user for Human Resources that has the corresponding report
authorizations for posting data to Accounting (see Authorizations under Payroll ). You can also deactivate this
option by removing the corresponding ALE function module.
Conversely, the authorization check for displaying documents from Accounting must be made from the HR
system to Accounting.
External Wage Components
From the External Wage Components infotype (0579), users can display the original document for an external
wage component. The document is displayed using the function module HR_PCIF_SHOW_RECEIPT, which calls
an RFC-capable function module in the external system. This function module then has to perform its own
checks.
The function module BAPI_WAGE_COMP_EXT_GET_LIST is used to display a list of data of the External Wage
Components infotype (0579). This uses the function module HR_CHECK_AUTHORITY_INFTY for the
authorization check.
For the detailed view, the function module BAPI_WAGECOMPEXT_GETDETAIL is used. This uses the function
module HR_READ_INFOTYPE for the authorization check.
For more information, see SAP Note 318789.
Interface Toolbox and Outsourcing
The interface toolbox (transaction PU12) uses the cluster IF. It uses the following authorization objects:
● P_PCLX
● P_PCR
● S_TMS_ACT
● P_PBSPWE
Outsourcing uses ALE and local les with le access using transaction AL11. This is controlled using user exits
in the interface toolbox.
In the standard system, Outsourcing uses the logical system FILEPORT. You can use the transaction WE21 to
dene customer-specic logical systems.
The XML conversion to IDOC is made using the function module OUT_IDOC_XML_TRANSFORM of the function
group HROT and the function group IDOC_XML1 (RSIDOCWF). The function module GUI_DOWNLOAD
(function group SFES) is also called for the conversion.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 171

Communication with Authorities
For more information, see B2A: Communication with Authorities .
TemSe Files
The country versions for Payroll use reports in which sensitive data is displayed. For example, this data can be
from the following sensitive areas:
● Salary
● Tax
● Social insurance
● Pension contributions
● Court orders
This data is saved in temporary sequential (TemSe) les. The TemSe process is used for the following
purposes:
● To create and output statutory forms, statistics, and analyses
● To download data for the front end server or application server directly, without storing the data as TemSe
objects beforehand. The data can then be transferred from the front end server or application server to a
data medium that can be transferred to the authorities.
● For posting data to Accounting
Caution
We recommend you no longer use the TemSe process for posting data to Accounting. If you run
Accounting and Human Resources in separate systems, we recommend instead that you use
Application Link Enabling (ALE). For more information, see SAP Notes 560301, 121614, and 125164.
You can control access to the TemSe objects within the SAP S/4HANA system using the authorization object
S_TMS_ACT ( TemSe: Actions on TemSe Objects) . Data encryption is not necessary here.
You can nd information about the TemSe objects for your country version in the Payroll documentation for
your country version.
13.4.4.2.6.1 B2A: Communication with Authorities
This section of the Security Guide provides an overview of security-relevant information for B2A:
Communication with Authorities. B2A: Communication with Authorities is based on SAP S/4HANA Central
Component and Human Resources. Therefore, the corresponding sections in the Security Guide also apply for
B2A: Communication with Authorities.
B2A: Communication with Authorities is used by the following country versions:
● Switzerland
For more information, see CountrySpecic Features: Switzerland
172
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

● Germany
For more information, see B2A: Communication with Authorities (PY-DE-BA).
● Great Britain
For more information, see CountrySpecic Features: Great Britain
Underlying Security Guides
Security Guide of Scenario, Application, or Component Path
Secure Store and Forward (SSF) SAP NetWeaver Developers' Guide in SAP NetWeaver Library
under Secure Store and Forward Mechanism (SSF)
SAP Business Connector (BC) SAP Business Connector Security Guide
SAP NetWeaver Exchange Infrastructure/Process Integra
tion (XI/PI)
SAP Process Integration (PI) Security Guides
Important SAP Notes
Currently, there are no security-relevant SAP Notes for B2A.
Authorizations
For more information, see Authorizations.
13.4.4.2.6.1.1 Authorizations
Use
B2A: Communication with Authorities uses the authorization concept provided by SAP NetWeaver AS for
ABAP . Therefore, the security recommendations and guidelines for authorizations as described in the SAP
NetWeaver AS Security Guide ABAP also apply to B2A: Communication with Authorities.
Roles and Authorization Concept for B2A: Communication with Authorities
Standard Roles
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 173

Currently, there are no application-specic roles available.
Standard Authorization Objects
The following table shows the authorization objects relevant for security used by B2A: Communication with
Authorities.
Standard Authorization Objects
Authorization Object Field Value Description
P_B2A (HR-B2A: B2A
Manager
)
MOLGA
Country Grouping: Unique
identier for a country, for
example, 01 for Germany
You use this authorization
object to determine the au
thorization check for B2A
Manager. You need to main
tain this authorization object
only if you use B2A Manager.
B2A_WERKS
Authorization Check – Per
sonnel Area
B2A_BTRTL
Authorization Check – Per
sonnel Subarea
SAGRP
Area – identies an applica
tion in Human Resources
DOCTY
Document Type – includes
documents of the same type
within an area within the
framework of the B2A func
tions
B2A_ACTIO
● S – Send Messages
● D – Detail View for Mes
sages
● R – Reorganize Mes
sages
● L – Delete Messages
● Z – Convert Status of
Messages
13.4.4.2.7 Country-Specic Features
The following chapters contain information on country-specic features.
174
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.4.2.7.1 Country-Specic Features: Australia
Sensitive Data
The Human Resources infotypes often contain sensitive data. This data is protected by central authorization
objects. For the country version for Australia (PY-AU, PA-PA-AU), this aects the tax le number (TFN number)
in the infotype TFN Australia (0227), for example.
More Information
Payroll (PY)
13.4.4.2.7.2 Country-Specic Features: Canada
Data Storage Security
For general information about data storage security in Payroll, see Data Storage Security under Payroll.
The following contains specic information about the logical le names and path names for Payroll Canada (PY-
CA).
Logical File Names Used in Payroll Canada
The following logical le names were created to facilitate the validation of physical le names:
Logical File Names and Reports
Logical File Name Reports That Use These Logical File Names
HR_CA_DIR_CRA_XML_FILE_NAME_APPV RPCYERK3_XML
HR_CA_DIR_CRA_XML_FILE_NAME_FEND RPCYERK3_XML
HR_CA_DIR_CRA_XML_SCH_NAME_FEND RPCYERK3_XML
HR_CA_DIR_MRQ_XML_FILE_NAME_APPV RPCYERK3_MRQ_XML
HR_CA_DIR_MRQ_XML_FILE_NAME_FEND RPCYERK3_MRQ_XML
HR_CA_DIR_MRQ_XML_SCH_NAME_APPV RPCYERK3_MRQ_XML
HR_CA_DIR_MRQ_XML_SCH_NAME_FEND RPCYERK3_MRQ_XML
HR_CA_DIR_ROE_FILE_NAME RPCROEK0_DISPLAY_XML
HR_CA_DIR_ROE_FILE_NAME RPCROEK0_XMPORTER
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 175

Logical File Name Reports That Use These Logical File Names
HR_CA_DIR_XML_FILE_NAME_FEND RPCXMLK0_VALIDATE
HR_CA_DIR_XML_SCH_NAME_FEND RPCXMLK0_VALIDATE
Logical Path Names Used in Payroll Canada
The logical le names listed above all use the logical le path HR_CA_FILE_PATH.
Particularly Sensitive Data
The Human Resources infotypes often contain sensitive data. This data is protected by central authorization
objects. For the country version for Canada, this includes the social insurance number (SNI number) in the
infotype Personal Data (0002).
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide.
13.4.4.2.7.3 Country-Specic Features: Switzerland
Authorizations
The country version for Switzerland (PA-PA-CH, PY-CH) uses the standard authorization concept used by SAP
S/4HANA. Therefore, the recommendations and guidelines for authorizations as described for SAP S/4HANA
also apply to the country version for Switzerland.
Standard Authorization Objects
The country version for Switzerland uses the security-relevant authorization objects that are available for
Personnel Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for Switzerland.
176
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Country-Specic Authorization Objects
Authorization Object Field Value Description
P_CH_PK
KONNR (Individual PF Ac
count Number)
AUTGR (HR-CH: Authoriza
tion group for PF accounts)
PKKLV (HR-CH: Pension
fund : Authorization level for
account access)
HR-CH: Pension Fund: Ac
count Access (see
Authorizations for Human
Resources Technical
Aspects
Authorization
Objects P_CH_PK (HR-CH:
Pension Fund: Account
Access)
)
For the documentation for the authorization object P_CH_PK, see SAP Library for SAP S/4HANA and choose
Human Resources HR Tools Authorizations for Human Resources Technical Aspects Authorization
Objects
.
Communication Channel Security
The following table presents the communication paths used by the country version for Switzerland for B2A:
Communication with Authorities, the protocol used by the connection, and the type of data transferred.
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
ELM (Uniform Wage Notica-
tion Procedure)
External communication be
tween PI* and distributor/
authorities: HTTPS
Internal communication be
tween HR backend system
and PI: RFC Adapter
Internal communication be
tween PI and PI: HTTP(S)
Personnel data Personal data
* PI = SAP NetWeaver Exchange Infrastructure/Process Integration (XI/PI)
You can use Secure Network Communications (SNC) to protect RFC connections. The Secure Sockets Layer
protocol (SSL protocol) protects HTTP connections.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
For more information about B2A security, see B2A: Communication with Authorities.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 177

More Information
See S/4 Security Guide for Human Resources and choosePayroll (PY)
13.4.4.2.7.4 Country-Specic Features: Germany
Authorizations
The country version for Germany (Payroll and/or Personnel Administration) uses the standard authorization
concept used by S/4HANA. Therefore, the recommendations and guidelines for authorizations as described for
S/4HANA also apply to the country version for Germany (PY-DE, PA-PA-DE).
Standard Roles
For information about the standard roles used by Payroll, see Authorizations.
The following table shows the standard roles that the country version for Germany also uses.
Standard Roles
Role Description
SAP_AUDITOR_TAX_HR
Role HR-DE Audit § 147 AO (Template) for Personnel Admin
istration Germany (PA-PA-DE)
Standard Authorization Objects
The country version for Germany uses the security-relevant authorization objects that are available for
Personnel Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for Germany.
178
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Country-Specic Authorization Objects
Authorization Object Field Value Description
P_DBAU_SKV
HR: DBAU: Construction In
dustry Germany - Social
Fund Procedure
ACTVT
● Add or Create
● Display
● Delete
This object is only used in
Construction Pay Germany
and then only within the
framework of the report for
the social fund procedure. A
check is made as to which re
ports are to be run by an ad
ministrator using which pa
rameters or worksteps.
For more information, see
SAP Library for S/4HANA un
der P_DBAU_SKV (HR:
DBAU: Construction Pay
Germany – Social Fund
Procedure)
REPID
ABAP Report Name: Con
tains the name of a report in
which the authorization ob
ject is checked, for example,
the evaluation report for the
social fund procedure. The
authorization granted applies
only to this report.
RZNUM
Data Center Number for
Construction Industry Social
Fund
Determines the data center
numbers to which a granted
authorization applies
ZVKAS
Social Fund
Determines the social funds
for which a granted authori
zation applies
P_DE_BW
HR-DE: SAPScript State
ments
BEWID
Statement Identier
Identies exactly one state
ment within Statements
This object determines the
authorization check within
Statements (with SAPScript)
for German Payroll.
For more information, see
SAP Library for S/4HANA un
der P_DE_BW (HR-DE:
Statements SAPScript)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 179

Authorization Object Field Value Description
BSUBJ
Functional Area ID for State
ments
Logical subdivision of state
ments according to individual
topics
Values 01–04
BACT
● E = Creation of State
ments
● A = Asynchronous Ar
chiving
● S = Fast Data Entry/Ad-
hoc Query
● D = Create Data Records
● V = Administrate Ar
chived Statements
● Z = Display Archived
Statements
For the documentation for the authorization objects, see SAP Library for S/4HANA and choose Human
Resources
HR Tools Authorizations for Human Resources Technical Aspects Authorization Objects .
Data Storage Security
For general information about data storage security in Payroll, see Data Storage Security.
The following contains specic information about the logical le names and path names for Payroll Germany
(PY-DE).
Logical File Names Used in Payroll Germany
The following logical le names and logical le paths were created to facilitate the validation of physical le
names:
Logical File Names, Reports, and File Paths
Logical File Name Reports That Use These Logical File
Names
Logical File Path
HR_DE_DIR_B2A_KK_ZERTLIST RPUSVKD0 HR_DE_B2A_KK_ZERTLIST
HR_DE_DIR_B2A_KK_ZERTREQUEST RPUSVKD0 HR_DE_B2A_KK_ZERTREQUEST
HR_DE_DIR_B2A_KK_ZERTRESPONSE RPUSVKD0 HR_DE_B2A_KK_ZERTRESPONSE
180 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Logical File Name Reports That Use These Logical File
Names
Logical File Path
HR_DE_DIR_RBM_IN RPCRBMD0_INBOUND HR_DE_DIR_RBM_IN
HR_DE_DIR_RBM_OUT RPCZFADD_INBOUND HR_DE_DIR_RBM_OUT
HR_DE_DIR_RBM_PRO RPCRBMD0_INBOUND HR_DE_DIR_RBM_PRO
HR_DE_DIR_RPCAODD0 RPCAOPD0
RPCOADD0
HR_DE_TX_DATENUEBERLASSUNG_PFA
D
HR_DE_DIR_RPCEHBD0 RPCEHBD0 HR_DE_DIR_RPCEHBD0
HR_DE_DIR_RPCEHCD1 RPCEHCD1 HR_DE_DIR_RPCEHCD1
HR_DE_DIR_RPCEHFD0 RPCEHFD0 HR_DE_DIR_RPCEHFD0
HR_DE_DIR_RPCSVGD0 RPCSVGD0 HR_DE_DIR_RPCSVGD0
HR_DE_DIR_RPLEHAD3 RPLEHAD3 HR_DE_DIR_RPLEHAD3
HR_DE_DIR_RPSKGOD0 RPSKGOD0 HR_DE_DIR_RPSKGOD0
HR_DE_DIR_RPSPSDD0 RPSPSDD0 HR_DE_DIR_RPSPSDD0
HR_DE_DIR_RPURZBD0 RPURZBD0 HR_DE_DIR_RPURZBD0
HR_DE_DIR_RPUTXCD0 RPUTXCD0 HR_DE_TX_RPUTXED0_PFAD
HR_DE_DIR_RPUTXED0 RPUTXED0 HR_DE_TX_RPUTXED0_PFAD
HR_DE_DIR_RPUVEODD RPUVEODD HR_DE_DIR_RPUVEODD
HR_DE_DIR_RPUWEDDA RPUWEDDA HR_DE_DIR_RPUWEDDA
HR_DE_DIR_RPUZVCD2 RPUZVCD2 HR_DE_PBSZV2006_NOTIFS
HR_DE_DIR_RPUZVTD2 RPUZVTD2 HR_DE_PBSZV2006_NOTIFS
HR_DE_DIR_RPXKHSD0 RPXKHSD0 HR_DE_DIR_RPXKHSD0
HR_DE_DIR_ZFA_INCOMING RPCZFADD_INBOUND HR_DE_DIR_ZFA_INCOMING
HR_DE_DIR_ZFA_OUTGOING RPCZFADD_INBOUND HR_DE_DIR_ZFA_OUTGOING
HR_DE_DIR_ZFA_PROCESSED RPCZFADD_INBOUND HR_DE_DIR_ZFA_PROCESSED
More Information
See Payroll (PY) under S/4HANA Security Guide Human Resources.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 181
13.4.4.2.7.4.1 B2A: Communication with Authorities (PY-DE-
BA)
About This Chapter
This section of the Security Guide provides an overview of security-relevant information for B2A:
Communication with Authorities (PY-DE-BA).
References to Cross Chapters
B2A: Communication with Authorities (PY-DE-BA) is based on SAP S/4HANA, Human Resources, or Personnel
Management. Therefore, the corresponding Security Guides also apply to B2A: Communication with
Authorities (PY-DE-BA). Note in particular the most important sections or specic restrictions that are entered
in the following table.
Underlying Security Guides
Security Guide of Scenario, Application, or Component Path
Secure Store and Forward
(SSF)
SAP NetWeaver Developers' Guide in SAP NetWeaver Library
under Secure Store and Forward Mechanism (SSF)
SAP Business Connector
(BC)
SAP Business Connector Security Guide
SAP NetWeaver Exchange Infrastructure/Process Integra
tion
(XI/PI)
SAP Process Integration (PI) Security Guides
Important SAP Notes
Currently, there are no security-relevant SAP Notes for B2A.
Conguration
For information about the general settings for setting up B2A: Communication with Authorities (PY-DE-BA), see
Customizing for Payroll under Payroll: Germany Communication with Authorities (B2A) .
182
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Data Flow and Process
● • ELSTER: The data is encrypted and signed before being transferred from the HR system to the tax
authorities.
● • ELENA: The data is encrypted and signed before being transferred from the HR system to the pension
insurance.
● • SI (DEUEV, …): The data is encrypted and signed before being transferred from the HR system to the
health insurance fund.
Authorizations
For more information, see Authorizations under B2A: Communication with Authorities.
13.4.4.2.7.4.1.1 Communication Channel Security
Use
The following table shows the communication paths that B2A: Communication with Authorities (PY-DE-BA)
uses, the protocol used for the connection, and the type of data transferred.
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
ELSTER HTTP
Internal: HR system -> Mid
dleware (BC or PI): Commu
nication channel RFC
External: Middleware -> Tax
authorities: Communication
channel HTTP
Personnel data Person-related data
ELENA HTTP/HTTPS/E-mail Personnel Data Person-related data
SI (DEUEV, …) HTTP/E-mail Personnel data Person-related data
ZfA/PRN VPN Personnel data Person-related data
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 183

Communication Destinations
The following table provides an overview of the communication destinations that B2A: Communication with
Authorities (PY-DE-BA) uses.
Destination Provided Type Description
HR_DE_ELSTER No RFC Transfer of data for ELSTER
to middleware (BC, XI)
HR_DE_ELENA No HTTP/HTTPS Transfer of data for ELENA to
pension insurance
HR_DE_GKV No HTTP Transfer of data for GKV to
health insurance
Security-Relevant Logging and Tracing
● ELSTER: Tracing for error analysis using BI/BC is possible.
● ELENA: Tracing for error analysis using BC is possible.
● SI (DEUEV, …): Tracing for error analysis using ICM (transaction: SMICM) is possible.
● ZfA/PRN: Tracing for error analysis using ICM (transaction: SMICM) is possible.
13.4.4.2.7.5 Country-Specic Features: Denmark
Authorizations
The country version for Denmark (PA-PA-DK, PY-DK) uses the standard authorization concept used by SAP S/
4HANA. Therefore, the recommendations and guidelines for authorizations as described for SAP S/4HANA
also apply to the country version for Denmark.
Standard Authorization Objects
The country version for Denmark uses the security-relevant authorization objects that are available for
Personnel Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for Denmark.
184
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Country-Specic Authorization Objects
Authorization Object Field Value Description
P_DK_PBS
PBSFIRMA HR_DK (Company
Used for PBS)
Authorization check for PBS
companies (see P_DK_PBS
(HR-DK: Authorization check
for access to PBS company))
For the documentation for the authorization object P_DK_PBS, see SAP Library for SAP S/4HANA and choose
Human Resources HR Tools Authorizations for Human Resources Technical Aspects Authorization
Objects .
More Information
See Payroll (PY) under SAP S/4HANA Security Guide for Human Resources
13.4.4.2.7.6 Country-Specic Features: Spain
Authorizations
The country version for Spain (PA-PA-ES, PY-ES) uses the standard authorization concept used by SAP S/
4HANA. Therefore, the recommendations and guidelines for authorizations as described for SAP S/4HANA
also apply to the country version for Spain.
Standard Authorization Objects
The country version for Spain uses the security-relevant authorization objects that are available for Personnel
Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for Spain.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 185

Country-Specic Authorization Objects
Authorization Object Field Value Description
P_ES_PA_OK
INFTY (Infotype)
SUBTY (Subtype)
PES_SPRPS (Lock indicator
for HR master record)
PES_FCODE (Function code)
ACTVT (Activity)
Authorization check for the
function codes that are per
mitted for the HR master
data of the country version
for Spain
More Information
See Payroll (PY) under SAP S/4HANA Security Guide for Human Resources.
13.4.4.2.7.7 Country-Specic Features: Great Britain
Communication Channel Security
The following table presents the communication paths used by the country version for Great Britain (PY-GB,
PA-PA-GB) for B2A: Communication with Authorities, the protocol used by the connection, and the type of data
transferred.
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
E-Filing Internal communication be
tween HR backend system
and middleware: HTTP(S)
(SAP Business Connector
(BC): TCP/IP or PI*: Proxy)
External communication be
tween middleware and tax
authorities: HTTP(S)
Personnel Data Personal Data
* PI = SAP NetWeaver Exchange Infrastructure/Process Integration (XI/PI)
HTTP connections are protected using the Secure Sockets Layer (SSL) protocol.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
186
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
For more information about B2A security, see B2A: Communication with Authorities.
Communication Destinations
You can communicate with the GB Inland Revenue Gateway. The communication channel is encrypted with 128
Bit SSL. The employees' tax data is transferred via RFC connections and using the protocol HTTPS.
Data Storage Security
For general information about data storage security in Payroll, see Data Storage Security.
The following contains specic information about the logical le names and path names for Payroll Great Britain
(PY-GB).
Logical File Names Used in Payroll Great Britain
The following logical le names were created to facilitate the validation of physical le names:
Logical File Names and Reports
Logical File Name Reports That Use These Logical File Names
HR_GB_DIR_RPUASHG0 RPUASHG0
HR_GB_DIR_RPUHESG1 RPUHESG1
HR_GB_DIR_RPUTPSG0 RPUTPSG0
HR_GB_DIR_RPUUSSG0 RPUUSSG0
HR_GB_DIR_RPUUSSG1
RPUUSSG1
Logical Path Names Used in Payroll Great Britain
The logical le names listed above all use the logical le path HR_GB_DIR_FILEPATH.
More Information
See Payroll (PY) under SAP S/4HANA Security Guide for Human Resources
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 187

13.4.4.2.7.8 Country-Specic Features: The Netherlands
Authorizations
The country version for The Netherlands (PA-PA-NL, PY-NL) uses the standard authorization concept used by
SAP S/4HANA. Therefore, the recommendations and guidelines for authorizations as described for SAP S/
4HANA also apply to the country version for The Netherlands.
Standard Authorization Objects
The country version for The Netherlands uses the security-relevant authorization objects that are available for
Personnel Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for The Netherlands.
Country-Specic Authorization Objects
Authorization Object Field Value Description
P_NL_AEDM
JUPER (Legal person)
ACTVT (Activity)
HR: Authorization object for
Day-one-announcement
P_NL_LA06
JUPER (Legal person)
ACTVT (Activity)
HR: Authorization object for
wage return 2006
P_NL_PKAB
ACTVT (Activity) Authorization object for PF
Actuarial le
P_NL_PKEV
KASSE (Pension Fund)
EVENT (HR-NL: Event)
PKELV (Authorization level
for reading event)
Authorization object for PF
events
P_NL_PKFKT
PKNL_PKFKT (PK Function) Authorization object for PF
functions
P_NL_PKFXV
KASSE (Pension Fund)
PKNL_FXVIE (Function view
of fund)
Authorization object for PF
function views
P_NL_PKTB
ACTVT (Activity) Authorization object for PF
pay scale calculation
188 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Communication Destinations
You can use the Gemeentelijke Basis Administratie (GBA) interface to upload the inbound data for retirement
pension plan for the country version for The Netherlands.
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources.
13.4.4.2.7.9 Country-Specic Features: Italy
Important SAP Notes
The following table presents the most important SAP Notes regarding security for the country version for Italy
(PA-PA-IT, PY-IT).
Title SAP Note Comment
Change of master data in a productive
payroll
385319
Authorizations
The country version for Italy uses the standard authorization concept used by SAP S/4HANA. Therefore, the
recommendations and guidelines for authorizations as described for SAP S/4HANA also apply to the country
version for Italy.
Standard Authorization Objects
The country version for Italy uses the security-relevant authorization objects that are available for Personnel
Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
Country-Specic Authorization Objects
The following table shows the security-relevant authorization objects that are also used in the country version
for Italy.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 189

Country-Specic Authorization Objects
Authorization Object Field Value Description
P_IT_UERST
P_RESET (Reject posting for
social insurance)
Authorization for termination
of social insurance (report
RPCUEDI0)
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources
13.4.4.2.7.10 Country-Specic Features: Non-Prot
Organizations
Data Storage Security
For general information about data storage security in Payroll, see Data Storage Security.
The following contains specic information about the logical le names and path names for Payroll for Non
Prot Organizations (PY-NGO).
Logical File Names Used in Payroll for Non-Prot Organizations
The following logical le names were created to facilitate the validation of physical le names:
Logical File Names and Reports
Logical File Name Reports That Use These Logical File Names
HR_UNUCMT_LOADER_FILE HUNUCMT_LOADER
Logical Path Names Used in Payroll for Non-Prot Organizations
The logical le names listed above all use the logical le path HR_UN_FILEPATH.
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources
190
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.4.4.2.7.11 Country-Specic Features: Norway
Authorizations
The country version for Norway (PY-NO, PA-PA-NO) uses the standard authorization concept used by SAP S/
4HANA. Therefore, the recommendations and guidelines for authorizations as described for SAP S/4HANA
also apply to the country version for Norway.
Standard Authorization Objects
The country version for Norway uses the security-relevant authorization objects that are available for
Personnel Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for Norway.
Country-Specic Authorization Objects
Authorization Object Field Value Description
P_NO_ALTIN
ACTVT (Activity) Norway: Authorization to
send data to Altinn Portal
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources.
13.4.4.2.7.12 Country-Specic Features: New Zealand
Sensitive Data
The Human Resources infotypes often contain sensitive data. This data is protected by central authorization
objects. For the country version for New Zealand (PY-NZ, PA-PA-NZ), this aects the employee IRD number in
the infotype IRD Nbr New Zealand (0309). You have the following options for accessing the number:
● Directly using the infotype IRD Nbr New Zealand (0309) with the transaction Maintain HR Master Data
(PA30)
● By choosing the IRD Number pushbutton in the infotype Tax New Zealand (0313).
The authorizations required to read or change the IRD number depend on the authorizations in the user prole.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 191

More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources.
13.4.4.2.7.13 Country-Specic Features: Russia
Authorizations
The country version for Russia (PA-PA-RU, PY-RU) uses the standard authorization concept used by SAP S/
4HANA. Therefore, the recommendations and guidelines for authorizations as described for SAP S/4HANA
also apply to the country version for Russia.
Standard Authorization Objects
The country version for Russia uses the security-relevant authorization objects that are available for Personnel
Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for Russia.
Country-Specic Authorization Objects
Authorization Object Field Value Description
P_RU_0294C
AUTHC (Authorization level) HR-RU: Authorization for
checking records of infotype
0294
P_RU_PKMN
HR_RU_EVNT (Count param
eter)
HR_RU_PKID (Package type)
HR_RU_REGN (Registration
number)
HR_RU_USER (Name of pro
cessor who changed the ob
ject)
Authorization for checking
HR_RU_PF DMS – Package
Manager
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources.
192
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.4.4.2.7.14 Country-Specic Features: Saudi Arabia
Authorizations
The country version for Saudi Arabia (PA-PA-SA, PY-SA) uses the standard authorization concept of SAP S/
4HANA. Therefore, the recommendations and guidelines for authorizations as described for SAP S/4HANA
also apply to this country version.
Standard Authorization Group
Authorization group PCSA is provided with this country version.
13.4.4.2.7.15 Country-Specic Features: Singapore
Data Storage Security
For general information about data storage security in Payroll, see Data Storage Security.
The following contains specic information about the logical le names and path names for Payroll Singapore
(PY-SG).
Logical File Names Used in Payroll Singapore
The following logical le names were created to facilitate the validation of physical le names:
Logical File Names and Reports
Logical File Name Reports That Use These Logical File Names
HR_SG_DIR_NRSFILENAME RPCNRSR0_XML_ALV
Logical Path Names Used in Payroll Singapore
The logical le names listed above all use the logical le path HR_SG_DIR_NRS.
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 193

13.4.4.2.7.16 Country-Specic Features: USA
Important SAP Notes
The following table presents the most important SAP Notes regarding security for the country version for USA
(PA-PA-US, PY-US).
Title SAP Note Comment
Tax Reporter Transaction and Spool Se
curity
430595
Authorizations
The country version for USA uses the standard authorization concept used by SAP S/4HANA. Therefore, the
recommendations and guidelines for authorizations as described for SAP S/4HANA also apply to the country
version for USA.
Standard Authorization Objects
The country version for USA uses the security-relevant authorization objects that are available for Personnel
Management and Payroll.
For more information, see the following:
● Authorizations (Personnel Management)
● Authorizations (Payroll)
The following table shows the security-relevant authorization objects that are also used in the country version
for USA.
Country-Specic Authorization Objects
Authorization Object Field Value Description
P_USTR
ACTVT (Activity)
PERSA (Personnel Area)
BTRTL (Personnel Subarea)
Authorizations for Tax Report
Communication Channel Security
The following table shows the communication paths that the country version for USA uses, the protocol used
for the connection, and the type of data transferred.
194
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
BSI Tax Factory for tax calcu
lation
RFC Tax data for the country ver
sion for USA
You can use Secure Network Communications (SNC) to protect RFC connections.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
Communication Destinations
You can exchange data with local servers or terminals for the VET and EEO reports for the country version for
USA. You can use this function to download les from the application server to a presentation server. You then
receive the text les required by the authorities with the output format .txt. This output format complies with
the law.
The data is not encrypted in the standard system. It is your decision as to the level of encryption that you want
to use if you want to send the data to the Federal Commission or Department of Labor.
The following table presents an overview of the communication destinations that the country version for USA
uses.
Communication Destinations
Destination Provided Type Description
BSI For country version for USA RFC with the function mod
ule PAYROLL_TAX_CALC_US
PAYROLL_TAX_CALC_US_50
PAYROLL_TAX_CALC_US_60
PAYROLL_TAX_CALC_US_70
Data Storage Security
For general information about data storage security in Payroll, see Data Storage Security.
The following contains specic information about the logical le names and path names for Payroll USA (PY-
US).
Logical File Names Used in Payroll USA
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 195

The following logical le names were created to facilitate the validation of physical le names:
Logical File Names and Reports
Logical File Name Reports That Use These Logical File Names
HR_US_TR_XML_SCHEMA RPCTRTU1_XML
Logical Path Names Used in Payroll USA
The logical le names listed above all use the logical le path HR_US_TR.
Particularly Sensitive Data
The Human Resources infotypes often contain sensitive data. This data is protected by central authorization
objects. For the country version for USA, this includes the social security number (SSN number) in the infotype
Personal Data (0002).
Other Security-Relevant Information
You can use the interface toolbox (transaction PU12) to update the taxability model. Currently, there are no
special authorizations for this. For more information about the interface toolbox, see section Security for
Additional Applications under Payroll.
You have the following options to prevent unauthorized or unintentional updates of the database PCL4:
● You can use the feature UTXSS to activate and deactivate the authorization checks for the tax report.
● You can use the feature UTXSP to specify codes for spool authorizations depending on the tax company
and the tax class.
For more information, see the documentation of the features in the SAP S/4HANA system.
More Information
See Payroll (PY) in the S/4HANA Security Guide for Human Resources.
13.4.4.2.7.17 Country-Specic Features: Other Countries
Data Storage Security
For general information about data storage security in Payroll, see Data Storage Security.
196
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

The following contains specic information about the logical le names and path names for Payroll for Other
Countries (PY-XX).
Logical File Names Used in Payroll for Other Countries
The following logical le names and logical le paths were created to facilitate the validation of physical le
names:
Logical File Names, Reports/Function Modules, and File Paths
Logical File Name Reports or Function Modules That
Use These Logical File Names
Logical File Path
HR_XX_DIR_B2AFILE
Report H99_B2AFILE
HR_XX_DIR_B2AFILE
HR_XX_DIR_RPUFCP01
Report RPUFCP01
HR_XX_DIR_RPUFCP01
HR_XX_DIR_RH_CALL_ORGDISPLAY
Function module
RH_CALL_ORGDISPLAY
HR_XX_DIR_RH_CALL_ORGDISPLAY
HR_XX_DIR_RHMOVE40
Report RHMOVE40
PD_DATASET
HR_OT_FILEPORT
Report RPUOTFL0
HR_OT_DIR_FILEPORT
More Information
See Payroll (PY) in the SAP S/4HANA Security Guide for Human Resources.
13.4.4.3 Self-Services
13.4.4.3.1 Important SAP Notes
Denition
This chapter of the Security Guide provides you with information about the following self-service components:
● Business Unit Analyst (BUA)
● Project Self-Services (PSS)
● Higher Education and Research (IS-HER-CSS)
● General Parts (PCUI_GP)
If not stated otherwise, the security settings for user management and authorizations apply to all of the afore-
mentioned components.
The following self-service components have their own sections in this chapter:
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 197

● Employee Self-Service
● Manager Self-Service
Note
For these components, all security-relevant information is included in the relevant subsections.
Important SAP Notes
The table below shows important SAP Notes that apply to the security for some Self-Service applications. For
more information about standard roles for assigning authorization in the Self-Service applications, see the
Authorizations section of this Security Guide.
Important SAP Notes
SAP Note Number Title Comment
846439 PSS: Authorizations and roles for Web
Dynpro
This SAP Note contains the authoriza
tion objects and the default values de
ned for the Web Dynpro applications
for Project Self-Services (component
EP-PCT-PLM-PSS).
13.4.4.3.2 User Management
Use
User management for Self-Service applications uses the mechanisms provided with the SAP NetWeaver
Application Server , for example, tools, user types, and password policy . For an overview of how these
mechanisms apply for Self-Service applications, see the sections below.
User Administration Tools
The table below shows the tools to use for user management and user administration with the Self-Service
applications.
User Management Tools
Tool Detailed Description Prerequisites
User and role maintenance in SAP
NetWeaver AS for ABAP (transactions
SU01 and PFCG)
You can use the Role Maintenance
(PFCG) transaction to generate proles
for your self-service users.
198 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

For more information, see the User and Roles section inSAPLibrary for SAP NetWeaver (see also
help.sap.com Documentation SAPNetWeaver ).
User Types
For information about the user types , see the SAP NetWeaver Application Server ABAP Security Guide.
Recommendation
For portal roles, we recommend that you set up the connection between the portal and the connected
systems ( ECC system, J2EE Engine, BW system) such that each individual user has access.
Standard Users
Component Standard Users
Project Self-Service
Business Unit Analyst
No standard users exist in the standard SAP system for
these components.
Higher Education and Research For information about the standard users for this compo
nent, see the Security Guide for this component.
13.4.4.3.3 Authorizations
Use
The Self-Service applications use the authorization concept provided by SAP NetWeaver Application Server .
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver Security
Guide for ABAP also apply to the Self-Service applications.
The SAP NetWeaver Application Server authorization concept is based on assigning authorizations to users
based on roles. For role maintenance, use the Prole Generator (transaction PFCG). For more information, see
Editing Roles and Authorizations for Web Dynpro Services .
Standard Roles
Business Unit Analyst and Project Self-Services
There are no standard roles for these components.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 199

Higher Education and Research
For information about the standard roles for this component, see the Security Guide for this component.
Standard Authorization Objects
The table below shows the general security-relevant authorization objects that are used by the Self-Service
applications.
Standard Authorization Objects for Self-Service Applications:
Authorization Object Field Value Description
S_RFC RFC_NAME Depends on service Saves data when the back-
end system is accessed via
RFC from the Web Dynpro
front end.
Higher Education and Research
For information about the standard authorization objects for this component, see the Security Guide for this
component.
Internal Service Request and Personnel Change Requests
For information about standard authorization objects for the Internal Service Request (ISR) and Personnel
Change Requests , see SAP Note 623650.
13.4.4.3.3.1 Maintain Roles and Authorizations for Web
Dynpro Services
Use
You use this procedure to maintain roles, their associated Web Dynpro services, and authorizations.
Procedure
1. In transaction PFCG, create a role or select an existing default role for the component. Choose Create Role
or copy the existing default role.
2. Assign the services you require to the role.
1. On the Menu tab page, choose Authorization Default .
The Service dialog box appears.
2. Select the External Service checkbox.
3. Select WEBDYNPRO as the external service type.
200
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
4. In the Service eld, select the Web Dynpro service you require.
5. Choose Save.
The authorization objects and default values maintained for the service are then displayed in the menu
tree structure.
In the same manner, select all the Web Dynpro services that you want to use.
3. Assign the required authorizations.
To do this, choose the Authorizations tab page to maintain the authorization objects and values in
accordance with your requirements.
For more detailed information about role maintenance, see Role Administration [page 16].
13.4.4.3.3.2 Authorizations for Controlling Services (BUA)
The table below shows the standard authorization objects that are used by the controlling services in Business
Unit Analyst (BUA).
Note
These authorization objects are also used by the controlling services in Business Package forManager Self-
Service (MSS).
Authorization Object Description
K_CCA General authorization object for Cost Center Accounting.
Is checked in the relevant Monitor iViews, Master Data
iViews, and Express Planning services.
K_ORDER General authorization object for internal orders.
Is checked in the relevant Monitor iViews, Master Data
iViews, and Express Planning services.
K_PCA Area responsible, Prot Center.
Is checked in the relevant Monitor iViews, Master Data
iViews, and Express Planning services.
K_CSKS_PLA Cost element planning.
Is checked in the relevant Express Planning services.
K_FPB_EXP Authorization object for Express Planning.
This authorization object checks the Express Planning
Framework call and the planning round call. The actual plan
data is protected by the authorization objects for the individ
ual Express Planning services.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 201
Note
For more information about the elds for the authorization objects K_CCA, K_ORDER, and K_PCA, see SAP
Note 15211.
13.4.4.3.4 Employee Self-Service
About This Document
This chapter provides an overview of the security-relevant information that applies to Employee Self-Service
(CA-ESS).
The following deployment options are available for Employee Self-Service (ESS):
● Business Package for Employee Self-Service (up to and including 1.50)
This Business Package is a “classic” SAP Business Package that runs in the SAP Enterprise Portal. The
Portal role consists of worksets and iViews based on Web Dynpro ABAP technologies.
● Business Package for Employee Self-Service (WDA)
This Business Package also runs in the SAP Enterprise Portal but it has only one workset with one iView
that launches the role structure with the applications maintained in the back-end system. In this business
package, all applications are based on Web Dynpro ABAP technology.
● Employee Self-Service in SAP Business Client for HTML
The role structure of this deployment option is maintained in the back-end system with the SAP role
maintenance transaction PFCG. All applications available with this role are based on Web Dynpro ABAP
technology.
Note
Some parts of the security information in this chapter only apply to individual ESS deployment options. In
this case, you will nd a comment explaining for which deployment option this information is valid right at
the beginning of each section. If not stated otherwise, the security information in this chapter applies to all
ESS deployment options.
See also:
● For more information about the roles in SAP Enterprise Portal, see SAP Library for SAP S/4HANA on SAP
Help Portal at
Cross-Application Functions in SAP ERP Roles Business Packages (Portal Content) .
● For more information about the roles in SAP Business Client, see SAP Library for SAP S/4HANA on SAP
Help Portal at Cross-Application Functions in SAP ERP Roles Roles in SAP NetWeaver Business
Client
.
● For more information about SAP Business Client, see SAP Library for SAP NetWeaver on SAP Help Portal
at SAP NetWeaver by Key Capability Application Platform by Key Capability ABAP Technology UI
Technology SAP NetWeaver Business Client .
202
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Overview of the Main Sections of This Chapter
This chapter comprises the following sections with security-related topics specic to Employee Self-Service:
● Before You Start
This section comprises references to other Security Guides that are relevant for Employee Self-Service and
a list of the most important notes for Employee Self-Service regarding security.
● User Administration and Authentication
This section provides an overview of the following user administration and authentication aspects for
Employee Self-Service:
○ User Management
This section contains information about the user types that are required by Employee Self-Service and
standard users for Employee Self-Service.
○ Integration into Single Sign-On Environments
This topic describes how the Employee Self-Service supports Single Sign-On mechanisms.
● Authorizations
This section provides an overview of the authorization concept that applies to Employee Self-Service.
● Session Security Protection
This section provides information on activating secure session management.
● Network and Communication Security
This section provides an overview of the communication paths used by Employee Self-Service and the
security mechanisms that apply. It also includes our recommendations for the network topology to restrict
access at the network level:
○ Communication Channel Security
○ Network Security
○ Communication Destinations
● Internet Communication Framework Security
This section provides an overview of the Internet Communication Framework (ICF) services that are used
by Employee Self-Service.
● Security-Relevant Logging and Tracing
This section provides an overview of the logging and tracing mechanisms that apply to Employee Self-
Service.
13.4.4.3.4.1 User Administration and Authentication
User management for Employee Self-Service uses the mechanisms provided with the SAP NetWeaver
Application Server for ABAP:
The security recommendations and guidelines for user administration and authentication as described in the
SAP NetWeaver Application Server for ABAP Security Guide apply for Employee Self-Service (WDA) in SAP
NetWeaver Business Client for HTML apply to the ESS business packages (Business Package for Employee Self-
Service) and Business Package for Employee Self-Service (WDA).
In addition to these guidelines, information about user administration and authentication that specically
applies to Employee Self-Service is included in the following sections:
● User Management
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 203
● Integration into Single Sign-On Environments
13.4.4.3.4.1.1 User Management
Use
User management for Employee Self-Service (WDA) in SAP NetWeaver Business Client for HTML uses the
mechanisms provided with the SAP NetWeaver Application Server for ABAP.
For an overview of how these mechanisms apply to Employee Self-Service, see the sections below.
User Administration Tools
The table below shows the tools to use for user management and user administration with Employee Self-
Service.
User Management Tools
Tool Detailed Description Comment
User maintenance for ABAP-based sys
tems (transaction SU01)
You use the user maintenance transac
tion to generate users in the ABAP-
based systems and to assign authoriza
tion proles.
Used for all ESS deployment options
Role maintenance (transaction PFCG) You use the role maintenance transac
tion to generate authorization proles
for your self-service users.
For more information, see User and
Role Administration of AS ABAP.
Used for all ESS deployment options
Note
For the ESS business packages, you must perform user mapping for the users in the ABAP system and the
Portal. For more information, see Assigning Portal Roles to Users.
Caution
Ensure that you give end users general reading permission for the SAP Enterprise Portal. For more
information, see SAP Note 939412 .
204
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively must change their passwords on a regular
basis, but not those users under which background processing jobs run.
User types that are required for Employee Self-Service include:
● Individual users:
○ Dialog users (Used for SAP GUI for Windows or RFC connections)
○ Internet users (Same policies apply as for dialog users, but used for Internet connections).
● Technical users:
○ Service users .
For more information on these user types, see User Types in the SAP NetWeaver AS ABAP Security Guide.
Note
For the Business Package for Employee Self-Service (up to and including 1.41), we recommend you set up
the connection between the SAP Enterprise Portal and the connected systems (ECC system, J2EE Engine,
BW system) so that each individual user has access. This does not apply to the Business Package for
Employee Self-Service (WDA).
Standard Users
For Employee Self-Service, no standard users are delivered.
13.4.4.3.4.1.2 Integration into Single Sign-On Environments
Use
Employee Self-Service supports the Single Sign-On (SSO) mechanisms provided by SAP NetWeaver.
Therefore, the security recommendations and guidelines for user administration and authentication as
described in the SAP NetWeaver Security Guide also apply to Employee Self-Service.
For more information about the available authentication mechanisms, see User Authentication and Single
Sign-On in the SAP NetWeaver Library.
Conguration of Web Services with Client Certicates
For ESS applications of the Business Package for Employee Self-Service, the use of client certicates should be
congured for authentication when users access the J2EE Engine using an end-to-end connection. To achieve
this, follow the instructions under Conguring the Use of Client Certicates for Authentication.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 205
13.4.4.3.4.2 Authorizations
Use
Employee Self-Service uses the authorization concept provided by the SAP NetWeaver AS for ABAP. Therefore,
the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS Security Guide
ABAP also apply to ESS.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see Role Administration.
Role and Authorization Concept for Employee Self-Service
Employee Self-Service embraces services from a variety of SAP applications and also uses the authorizations
of these individual components. Most of these services belong to HCM components, see Authorizations for
Human Resources.
Standard Roles
The tables below show the standard roles that are used for authorizations by the Business Package for
Employee Self-Service (up to and including 1.50) and by Employee Self-Service (WDA).
Standard Roles for the Business Package for Employee Self-Service
Role Name Description
SAP_ESSUSER_ERP05
Single Role with all Non-Country-Spe
cic Functions
Single role that comprises all non coun
try-specic functions.
SAP_EMPLOYEE_ERP05_xx
ESS ERP05: Country-Specic Func
tions for <Country>
Single role comprising country-specic
functions. A separate role exists for
each country version (xx = country ID).
The corresponding composite role is
SAP_EMPLOYEE_ERP05.
206 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Role Name Description
SAP_ASR_EMPLOYEE
HR Administrative Services: Employee Enhancement of the role
SAP_ESSUSER_ERP05 for the employ
ees that use the functions of the com
ponent PA-AS (HR Administrative Serv
ices) in the
Business Package for
Employee Self-Service (up to and in
cluding 1.4.1).
Caution
For the Business Package for Employee Self-Service, you also need SAP Note 857431 for generating the
authorization proles.
Standard Roles for Employee Self-Service (WDA)
Role Name Description
SAP_EMPLOYEE_XX_ESS_WDA_2
ESS International Single Role Authorizations for all international serv
ices in Employee Self-Service (WDA).
For more information about this and all
other Employee Self-Service (WDA)
roles, see Single Roles for Employee
Self-Service (WDA).
SAP_EMPLOYEE_AU_ESS_WDA_1
ESS Single Role for Australia Authorizations for country-specic
services for Australia in Employee Self-
Service (WDA).
SAP_EMPLOYEE_CA_ESS_WDA_2
ESS Single Role for Canada Authorizations for country-specic
services for Canada in Employee Self-
Service (WDA).
SAP_EMPLOYEE_CH_ESS_WDA_1
ESS Single Role for Switzerland Authorizations for country-specic
services for Switzerland in Employee
Self-Service (WDA).
SAP_EMPLOYEE_CN_ESS_WDA_1
ESS Single Role for China Authorizations for country-specic
services for China in Employee Self-
Service (WDA).
SAP_EMPLOYEE_DE_ESS_WDA_1
ESS Single Role for Germany Authorizations for country-specic
services for Germany in Employee Self-
Service (WDA).
SAP_EMPLOYEE_HK_ESS_WDA_1
ESS Single Role for Hong Kong Authorizations for country-specic
services for Hong Kong in Employee
Self-Service (WDA).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 207

Role Name Description
SAP_EMPLOYEE_IN_ESS_WDA_2
ESS Single Role for India Authorizations for country-specic
services for India in Employee Self-
Service (WDA).
SAP_EMPLOYEE_JP_ESS_WDA_2
ESS Single Role for Japan Authorizations for country-specic
services for Japan in Employee Self-
Service (WDA).
SAP_EMPLOYEE_MY_ESS_WDA_1
ESS Single Role for Malaysia Authorizations for country-specic
services for Malaysia in Employee Self-
Service (WDA).
SAP_EMPLOYEE_PT_ESS_WDA_1
ESS Single Role for Portugal Authorizations for country-specic
services for Portugal in Employee Self-
Service (WDA).
SAP_EMPLOYEE_SG_ESS_WDA_1
ESS Single Role for Singapore Authorizations for country-specic
services for Singapore in Employee
Self-Service (WDA).
SAP_EMPLOYEE_TH_ESS_WDA_1
ESS Single Role for Thailand Authorizations for country-specic
services for Thailand in Employee Self-
Service (WDA).
SAP_EMPLOYEE_US_ESS_WDA_1
ESS Single Role for the United States Authorizations for country-specic
services for the USA in Employee Self-
Service (WDA).
SAP_FI_TV_WEB_ESS_TRAVELER_2
ESS Single Role for the Traveler Authorizations for ESS services for the
traveler role in Employee Self-Service
(WDA).
SAP_ASR_EMPLOYEE_SR_HCM_CI_3
ESS Single Role for HCM P&F Services Authorizations for international ESS
services from the HR Process and
Forms application in Employee Self-
Service (WDA).
SAP_PM_EMPLOYEE_HCM_CI_1
ESS Single Role for HCM PM Services Authorizations for ESS services from
the Performance Management applica
tion in Employee Self-Service (WDA).
SAP_TMC_EMPLOYEE_6
Employee in Talent Management Authorizations for ESS services from
the Talent Management and Talent
Development application in Employee
Self-Service (WDA). For more informa
tion, see Employee in Talent
Management.
208 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Role Name Description
SAP_RCF_ESS_SR_ERC_CI_4
E-Recruiting services for ESS (WDA) Authorizations in SAP E-Recruiting for
employees that use SAP E-Recruiting
services in ESS (WDA).
/SAPSRM/EMPLOYEE_ESS
SAP SRM Employee for ESS Authorizations in SAP SRM for employ
ees that use services from Purchasing
in ESS (WDA).
Note
The composite role SAP_EMPLOYEE_ESS_WDA_2, which contains the single roles listed above (except for
the last two roles), is required for
Employee Self-Service (WDA) in SAP NetWeaver Business Client for HTML.
For more information on all roles for ESS (WDA), see also Roles in Employee Self-Service (WDA).
Standard Authorization Objects
The following table presents the general authorization objects relevant for security that are used by the
Business Package for Employee Self-Service (up to and including 1.50).
Standard Authorization Objects for Self-Service Applications
Authorization Object Field Value Description
S_RFC RFC_NAME
Depends on service Saves data from RFC access
to Web Dynpro front end to
the back-end system.
Apart from these authorization objects, all Employee Self-Service deployment options use the authorization
objects from the following application areas or application components:
● Human Capital Management
See the SAP S/4HANA Security Guide at Human Capital Management Authorizations .
● SAP E-Recruiting
See the SAP S/4HANA Security Guide at Human Capital Management Talent Management SAP E-
Recruiting Authorizations .
● HCM Processes and Forms
See the SAP S/4HANA Security Guide at Human Capital Management Personnel Administration (PA)
HCM Processes and Forms Authorizations .
● Travel Management
See the SAP S/4HANA Security Guide at Accounting Financial Accounting Travel Management (FI-
TV)
.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 209

13.4.4.3.4.3 Session Security Protection
Use
To increase security and prevent access to the SAP logon ticket and security session cookie(s), we recommend
activating secure session management.
We also highly recommend using SSL to protect the network communications where these security-relevant
cookies are transferred.
Session Security Protection on the AS ABAP
The following section is relevant for Employee Self-Service (WDA):
To prevent access in javascript or plug-ins to the SAP logon ticket and security session cookies
(SAP_SESSIONID_<sid>_<client>), activate secure session management. With an existing security
session, users can then start applications that require a user logon without logging on again. When a security
session is ended, the system also ends all applications that are linked to this security session.
Use the transaction SICF_SESSIONS to specify the following parameter values shown in the table below in
your AS ABAP system:
Session Security Protection Prole Parameters
Prole Parameter Recommended Value Comment
icf/
set_HTTPonly_flag_on_cookies
0 Client-Dependent
login/ticket_only_by_https
1 Not Client-Dependent
For more information, a list of the relevant prole parameters, and detailed instructions, see Activating HTTP
Security Session Management on AS ABAP in the AS ABAP security documentation.
13.4.4.3.4.4 Network and Communication Security
Your network infrastructure is extremely important in protecting your system. Your network needs to support
the communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats based on software aws (at both the operating system
level and application level) or network attacks such as eavesdropping. If users cannot log on to your application
or database servers at the operating system or database layer, then there is no way for intruders to
compromise the machines and gain access to the back-end system’s database or les. Additionally, if users are
not able to connect to the server LAN (local area network), they cannot exploit well-known bugs and security
holes in network services on the server machines.
The network topology for Employee Self-Service is based on the topology used by the SAP NetWeaver
platform. Therefore, the security guidelines and recommendations described in the SAP NetWeaver Security
210
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Guide also apply to Employee Self-Service. Details that specically apply to Employee Self-Service are
described in the following sections:
● Communication Channel Security
This topic provides an overview of the communication channels used by Employee Self-Service, the
protocol used for the connection, and the type of data transferred.
● Network Security
This topic describes the recommended network topology for Employee Self-Service. It shows the
appropriate network segments for the various client and server components and where to use rewalls for
access protection. It also includes a list of the ports needed to operate Employee Self-Service.
● Communication Destinations
This topic describes the information needed for the various communication paths, for example, which
users are used for which communications.
For more information, see the following sections in the SAP NetWeaver Security Guide:
● Network and Communication Security
● Security Guides for Connectivity and Interoperability Technologies
13.4.4.3.4.4.1 Communication Channel Security
Use
DIAG and RFC connections can be protected using Secure Network Communications (SNC). HTTP
connections are protected using the Secure Sockets Layer (SSL) protocol.
For more information, see Transport Layer Security in the SAP NetWeaver Security Guide.
Recommendation
We strongly recommend using secure protocols (SSL, SNC) whenever possible.
SSL connections for Adobe Document Services
For ESS applications to perform security-related functions such as digitally signing PDF documents or
launching of PDF forms, you must set up an SSL connection to the Web service. To achieve this, follow the
instructions under Conguration of the Web Service SSL Connection in the Adobe Document Services
Conguration Guide.
13.4.4.3.4.4.2 Network Security
Ports
The Employee Self-Service runs on SAP NetWeaver and uses the port from the AS ABAP (for Employee Self-
Service (WDA)).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 211
For more information, see the topics for AS ABAP Ports in the corresponding SAP NetWeaver Security Guide.
For other components, for example, SAPinst, SAProuter, or the SAP Web Dispatcher, see https://
help.sap.com/viewer/ports.
13.4.4.3.4.4.3 Communication Destinations
Use
The tables below provide an overview of the communication destinations required for the three Employee Self-
Service deployment options.
Employee Self-Service (WDA) in SAP Business Client for HTML
For this deployment option, you have to maintain RFC connections using the transaction SM59, see also the
following table 1.
Table 1: Connection Destinations for Employee Self-Service (WDA) in NWBC for HTML
Destination Delivered Type Recommended User
Authorizations
Description
SAP_ECC_HumanReso
urces
No ABAP connection n/a System alias for the
ECC HCM system
SAP_ECC_HumanReso
urces_HTTP
No HTTP connection n/a System alias for the
ECC HCM system
SAP_SRM
No ABAP connection n/a System alias for the
SRM system for Pur
chasing applications
SAP_SRM_HTTP
No HTTP connection n/a System alias for the
SRM system for Pur
chasing applications
SAP_EREC_TalentMa
nagement
No ABAP connection n/a System alias for the
SAP E-Recruiting sys
tem
SAP_EREC_TalentMa
nagement_HTTP
No HTTP connection n/a System alias for the
SAP E-Recruiting sys
tem
Business Package for Employee Self-Service (WDA)
For the this deployment option, you have to maintain system aliases in the Portal System Landscape
Administration, see also the following table 2.
212
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Table 2: Connection Destinations for the Business Package for Employee Self-Service (WDA)
Destination Delivered Type Recommended User
Authorization
Description
SAP_ECC_HumanReso
urces
Yes Entry in Portal System
Landscape Administra
tion
n/a System alias for the
ECC HCM system
SAP_SRM
Yes Entry in Portal System
Landscape Administra
tion
n/a System alias for the
SRM system for Pur
chasing applications
SAP_EREC_TalentMa
nagement
Yes Entry in Portal System
Landscape Administra
tion
n/a System alias for the
SAP E-Recruiting sys
tem
More Information
For the Business Package for Employee Self-Service (WDA):
● Setting Up the System Landscape
For the Business Package for Employee Self-Service:
● Setting Up the System Landscape
13.4.4.3.4.5 Internet Communication Framework Security
Use
You should only activate those services that are needed for the applications running in your system. For
Employee Self-Service (WDA), the following services are needed which, unless stated otherwise, you can nd in
the path default_host/sap/bc/webdynpro/sap/:
For general ESS applications:
● HRESS_A_MENU
● HRESS_A_PERSINFO
● hress_a_payslip
● HRESS_A_TCS
For applications from HCM Processes and Forms (PA-AS):
● asr_form_display
● ars_personnel_file
● asr_processes_display
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 213
● ASR_PROCESS_EXECUTE_FPM
For applications from Cross-Application Time Sheet (CA-TS) and Personal Time Management (PT):
● hress_a_cats_1
● hress_a_cats_print
● hress_a_corrections
● hress_a_lea_team_calendar
● hress_a_ptarq_leavreq_appl
● HRESS_A_PTARQ_TIMEACC
● HRESS_A_TIME_DATESEL
● hress_a_time_persel
For applications from Benets (PA-BN):
● HRESS_A_BEN_PART_OVERVIEW
● HRESS_A_BENEFITS_ENROLLMENT
● HRESS_A_BEN_PRINT_ENRO_FORM
● HRESS_A_BEN_FSA_CLAIMS
● HRESS_A_BEN_PRINT_ENRO_FORM
● HRESS_A_BEN_PRINT_CONF_FORM
For applications from Performance Management (PA-PD-PM):
● HAP_CONFIGURATION
● HAP_DOCUMENT_LINK
● HAP_MAIN_DOCUMENT
● HAP_QUALIFICATION_PROFILE
● HAP_START_PAGE_POWL_UI_ESS
● HAP_a_ESS_Startpage
For applications from Travel Management (FI-TV):
● FITE_EXPRESS_EXPENSES
● FITE_REQUEST_DELETE
● FITE_EXPENSES_DELETE
● FITP_PLAN_CANCEL
● FITV_UNLOCK_PERSNO
● FITV_TRIP_FORM
● FITV_ROUTING
● FITP_PROFILE
● FITE_REQUEST
● FITP_PLANNING FITE_EXPENSES
● FITV_POWL_TRIPS
And in the path default_host/sap/bc/bsp/sap/:
● fitv_bsp_pfcg
214
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

For applications from Self-Service Procurement (SRM-EBP-SHP) in the path /default_host/sap/bc/
webdynpro/sapsrm/:
● WDA_L_FPM_OIF
● WDA_L_FPM_OVP
● WDA_L_PRINT_PREVIEW
For applications from ERP E-Procurement (MM-PUR-SSP):
● /SRMERP/WDA_I_SC_ESS
● /SRMERP/WDA_I_SC_FS_ESS
● /SRMERP/WDA_I_WSCP
For applications from SAP E-Recruiting (PA-ER):
● All services with the prex hrrcf in the path /default_host/sap/bc/webdynpro/sap/
● All services in the path /default_host/sap/bc/erecruiting/
● All services with the prex hrrcf_wd in the path /default_host/sap/bc/bsp/sap/
Note
You activate the services in Customizing for SAP E-Recruiting under Technical Settings User
Interfaces Candidate Front-End Candidate Specify E-Recruiting Services (Web Dynpro ABAP) .
For country-specic applications:
● HRESS_A_PAYINFO
● HRESS_A_REP_AU_PS
● Hress_a_rep_ca_tfr
● HRESS_A_REP_CH_PKB1
● HRESS_A_REP_CH_PKB4
● HRESS_A_REP_CN_CTXD
● HRESS_A_REP_HK_IR56B
● HRESS_A_REP_HK_IR56F
● HRESS_A_REP_HK_IR56G
● HRESS_A_REP_IN_FORM16
● HRESS_A_REP_JP_YEA_DEP
● HRESS_A_REP_JP_YEA_INS
● HRESS_A_REP_JP_YEA_WTS
● HRESS_A_REP_MY_EA
● HRESS_A_REP_MY_PCB2
● HRESS_A_REP_PT_IID
● HRESS_A_REP_SG_IR21
● HRESS_A_REP_SG_IR8A
● HRESS_A_REP_SG_IR8E
● HRESS_A_REP_SG_IR8S
● HR_EA_A_OVERVIEW_EE
● HR_EA_A_OVERVIEW_CU
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 215

● HR_EA_A_OVERVIEW_AP
● HR_EA_A_OVERVIEW_TO
● HRESS_A_REP_IN_SSITP
● HRESS_A_CLAIM_IN
● HRESS_A_ITDCL_IN
● HRESS_FWS_EMP_CALENDAR
● ASR_PROCESS_EXECUTE_FPM
Activities
Use the transaction SICF to activate these services.
If your rewalls use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
More Information
For more information, see Activating and Deactivating ICF Services in the SAP NetWeaver Library
documentation.
For more information about ICF security, see the RFC/ICF Security Guide.
13.4.4.3.4.6 Leave Request-Specic Virus Scan Prole
(ABAP)
Attackers can abuse a le upload to modify displayed application content or to obtain authentication
information from a legitimate user. Usually, virus scanners are not able to detect les designed for this kind of
attack.
For this reason, the standard SAP Virus Scan Interface includes an enhancement option to protect the user
and/or the SAP system from potential attacks.
For more information about the behavior of the virus scanner when default virus scan proles (VSP) are
activated, see SAP note 1693981 (Unauthorized modication of displayed content).
SAP Leave Request Application (HRESS_A_PTARQ_LEAVREQ_APPL) changes this behavior so that the le types
(EXE, RAR, DLL) are blocked.
When you have created and activated the application-specic virus scan prole (SIHTTP/HTTP_UPLOAD), this
prole produces the following impact: The MIME sning check is activated, and the MIME type APPLICATION/
OCTET-STREAM
will be blocked.
216
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.4.4.3.4.7 Security-Relevant Logging and Tracing
Employee Self-Service relies on the logging and tracing mechanisms from SAP NetWeaver.
For more information, see the following topics:
● For the AS ABAP (relevant for Employee Self-Service (WDA)):
Auditing and Logging
13.4.4.3.5 Manager Self-Service
About This Document
This chapter provides an overview of the security-relevant information that applies to Manager Self-Service
(EP-PCT-MGR).
The following deployment options are available for Manager Self-Service (MSS):
● Business Package for Manager Self-Service
This Business Package is a “classic” SAP Business Package that runs in the SAP Enterprise Portal. The
Portal role consists of worksets and iViews based on Web Dynpro ABAP technologies.
● Manager Self-Service in SAP Business Client
The role structure for this deployment option is maintained in the back-end system with the SAP role
maintenance transaction PFCG. All applications available with this role are based on Web Dynpro ABAP
technology.
Note
Some parts of the security information in this chapter only apply to one of the MSS deployment options. In
this case, you will nd a comment explaining for which deployment option this information is valid right at
the beginning of each section. If not stated otherwise, the security information in this chapter applies to
both MSS deployment options.
See also:
● For more information about the roles in SAP Enterprise Portal, see SAP Library for SAP S/4HANA on SAP
Help Portal at
Cross-Application Functions in SAP ERP Roles Business Packages (Portal Content) .
● For more information about the roles in SAP Business Client, see SAP Library for SAP S/4HANA on SAP
Help Portal Cross-Application Functions in SAP ERP Roles Roles in SAP NetWeaver Business Client .
● For more information about SAP Business Client, see SAP Library for SAP NetWeaver on SAP Help Portal
at
http://help.sap.com/netweaver SAP NetWeaver by Key Capability Application Platform by Key
Capability ABAP Technology UI Technology SAP NetWeaver Business Client .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 217
Overview of the Main Sections of This Chapter
This chapter comprises the following sections with security-related topics specic to Manager Self-Service:
● Before You Start
This section comprises references to other Security Guides that are relevant for Manager Self-Service and
a list of the most important notes for Manager Self-Service regarding security.
● User Administration and Authentication
This section provides an overview of the following user administration and authentication aspects for
Manager Self-Service:
○ User Management
This section contains information about the user types that are required by Manager Self-Service and
standard users for Manager Self-Service.
○ Integration into Single Sign-On Environments
This topic describes how the Employee Self-Service supports Single Sign-On mechanisms.
● Authorizations
This section provides an overview of the authorization concept that applies to Manager Self-Service.
● Session Security Protection
This section provides information about activating secure session management, which prevents JavaScript
or plug-ins from accessing the SAP logon ticket or security session cookie(s).
● Network and Communication Security
This section provides an overview of the communication paths used by Manager Self-Service and the
security mechanisms that apply. It also includes our recommendations for the network topology to restrict
access at the network level:
○ Network Security
○ Communication Destinations
● Internet Communication Framework Security
This section provides an overview of the Internet Communication Framework (ICF) services that are used
by Manager Self-Service.
● Security-Relevant Logging and Tracing
This section provides an overview of the logging and tracing mechanisms that apply to Manager Self-
Service.
13.4.4.3.5.1 User Administration and Authentication
User management for Manager Self-Service uses the mechanisms provided with the SAP NetWeaver
Application Server for ABAP.
The security recommendations and guidelines for user administration and authentication as described in the
SAP NetWeaver Application Server for ABAP apply for Manager Self-Service in SAP NetWeaver Business Client.
In addition to these guidelines, information about user administration and authentication that specically
applies to Manager Self-Service is included in the following sections:
● User Management
● Integration into Single Sign-On Environments
218
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.4.3.5.1.1 User Management
Use
User management for Manager Self-Service uses the mechanisms provided with the SAP NetWeaver
Application Server for ABAP (for example, tools, user types, and password policies).
For an overview of how these mechanisms apply for Manager Self-Service, see the sections below.
User Administration Tools
The table below shows the tools to use for user management and user administration with Manager Self-
Service.
User Management Tools
Tool Detailed Description Comment
User maintenance for ABAP-based sys
tems (transaction SU01)
You use the user maintenance transac
tion to generate users in the ABAP-
based systems.
Used for both MSS deployment options
Role maintenance (transaction PFCG) You use the role maintenance transac
tion to generate proles for your self-
service users.
For more information, see User and
Role Administration of AS ABAP.
Used for both MSS deployment options
Note
For the Business Package for Manager Self-Service, it is necessary to perform user mapping for the users in
the ABAP system and the Portal. For more information, see Assigning Portal Roles to Users.
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively must change their passwords on a regular
basis, but not those users under which background processing jobs run.
The user types that are required for the Manager Self-Service are Individual users:
● Dialog users (Used for SAP GUI for Windows or RFC connections)
● Internet users (Same policies apply as for dialog users, but used for Internet connections).
For more information about these user types, see User Types in the SAP NetWeaver AS for ABAP Security
Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 219

Recommendation
For the Business Package for Manager Self-Service, we recommend you set up the connection between the
SAP Enterprise Portal and the connected systems (ECC system, J2EE Engine, BI system) so that each
individual user has access. This does not apply to Manager Self-Service in SAP NWBC. .
Standard Users
For Manager Self-Service, no standard users are delivered.
13.4.4.3.5.1.2 Integration into Single Sign-On Environments
Use
Manager Self-Service supports the Single Sign-On (SSO) mechanisms provided by SAP NetWeaver. Therefore,
the security recommendations and guidelines for user administration and authentication as described in the
SAP NetWeaver Security Guide also apply to Manager Self-Service.
For more information about the available authentication mechanisms, see User Authentication and Single
Sign-On in the SAP NetWeaver Library and Integration into Single Sign-On Environments [page 16].
Conguration of Web Services with Client Certicates
For MSS applications of the Business Package for Manager Self-Service, the use of client certicates should be
congured for authentication when users access the J2EE Engine using an end-to-end connection. To achieve
this, follow the instructions under Conguring the Use of Client Certicates for Authentication.
13.4.4.3.5.2 Authorizations
Use
Manager Self-Service uses the authorization concept provided by the SAP NetWeaver AS for ABAP. Therefore,
the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS Security Guide
ABAP also apply to Manager Self-Service. The SAP NetWeaver authorization concept is based on assigning
authorizations to users based on roles. For role maintenance, use the prole generator (transaction PFCG) on
the AS ABAP.
Note
For more information about how to create roles, see Role Administration.
220
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Role and Authorization Concept for Manager Self-Service
Manager Self-Service embraces services from a variety of SAP applications and also uses the authorizations of
these individual components. Many services belong to HCM components, see Authorizations for Human
Resources.
Recommendation
For Manager Self-Service, we highly recommend that you use the HCM-specic structural authorization
check in addition to the general SAP authorization check. For more information see SAP Library for SAP S/
4HANA on SAP Help Portal at Human Resources HR Tools Authorizations for Human Resources
Structural Authorization Check .
Standard Roles
The table below shows the standard roles that are used for authorizations by Manager Self-Service.
Standard Roles for Manager Self-Service
Role Description
SAP_ASR_MANAGER
Authorizations for the functions of the PA-AS component
(HR Administrative Services) for line managers in Manager
Self-Service.
SAP_TIME_MGR_XX_ESS_WDA_1
Authorizations for line managers in Manager Self-Service for
services used to approve leave requests and working times
from Employee Self-Service (WDA).
SAP_TMC_MANAGER
Authorizations for managers relating to Talent Management
activities.
For more information, see Manager in Talent Management.
The structural authorization prole TMS_MAN_PROF is also
available as a template for the manager.
For more information, see Customizing for Talent
Management and Talent Development under Basic Settings →
Authorizations in Talent Management → Dene Structural
Authorizations.
SAP_RCF_MANAGER
Authorizations for the Manager role, which enables access
to SAP E-Recruiting from the Portal (Manager Self Service).
SAP_MANAGER_MSS_OTH_NWBC
Authorizations for remote system applications including ap
plications from SAP E-Recruiting.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 221
Role Description
SAP_HR_LSO_HR-MANAGER
Authorizations for the applications of the HR Manager Train
ing role of the SAP Learning Solution component.
SAP_HR_LSO_MANAGER
Authorizations for the applications of the Manager role of
the SAP Learning Solution component.
SAP_FI_TV_WEB_APPROVER
Authorizations for applications of the Travel Approver role of
the SAP Travel Management component.
SAP_HR_CPS_DET_PLAN_L_SR_NWBC
Authorizations for applications of the manager role of the
Personnel Cost Planning component.
SAP_SR_MSS_FIN_5
Authorizations for the Financials applications in Manager
Self-Service.
Caution
For the Business Package for Manager Self-Service, you also need SAP Note 844639 for generating the
authorization proles.
Note
The composite role SAP_MANAGER_MSS_NWBC, which contains the single roles listed above , is required for
Manager Self-Service in SAP NetWeaver Business Client.
Standard Authorization Objects
The following section provides an overview of the security-relevant authorization objects that are used by
Manager Self-Service.
Standard Authorization Objects for the Business Package for Manager Self-Service
Authorization Object Field Value Description
S_RFC RFC_NAME
Depends on service Saves data from RFC access
to Web Dynpro front end to
the back-end system.
Standard Authorization Objects for Controlling Services in MSS (Both Deployment Options)
Authorization Object Description
K_CCA
General authorization object for Cost Center Accounting.
Is checked in the relevant Monitor iViews, Master Data
iViews, and Express Planning services.
222 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Authorization Object Description
K_ORDER
General authorization object for internal orders.
Is checked in the relevant Monitor iViews, Master Data
iViews, and Express Planning services.
K_PCA
Area responsible, Prot Center.
Is checked in the relevant Monitor iViews, Master Data
iViews, and Express Planning services.
K_CSKS_PLA
Cost element planning.
Is checked in the relevant Express Planning services.
K_FPB_EXP
Authorization object for Express Planning.
This authorization object checks the Express Planning
Framework call and the planning round call. The actual plan
data is protected by the authorization objects for the individ
ual Express Planning services.
Note
For more information about the elds for the authorization objects K_CCA, K_ORDER, and K_PCA, see SAP
Note 15211 .
Apart from these authorization objects, both Manager Self-Service deployment options use the authorization
objects from the following application areas or application components:
● Human Capital Management
See the SAP S/4HANA Security Guide at Human Capital Management Authorizations .
● SAP E-Recruiting
See the SAP S/4HANA Security Guide at Human Capital Management Talent Management SAP E-
Recruiting
Authorizations .
● HCM Processes and Forms
See the SAP S/4HANA Security Guide at Human Capital Management Personnel Administration (PA)
HCM Processes and Forms Authorizations .
● Travel Management
See the SAP S/4HANA Security Guide at Accounting Financial Accounting Travel Management (FI-
TV)
.
Authorizations for Business Intelligence (BI) iViews (BP MSS)
For the BI iViews in the Business Package for Manager Self-Service, users need the standard BI authorizations
for executing queries. For more information, see Authorization Check When Executing a Query (in the Data
Warehouse Management section of the documentation for SAP NetWeaver Business Intelligence).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 223
In Human Capital Management, BI queries use a BI variable for personalization. Data is read from the
DataStore object for personalization 0PERS_VAR. If required, you can ll this DataStore Object from structural
authorizations (see Structural Authorizations - Values (0PA_DS02) and Structural Authorizations - Hierarchy
(0PA_DS03)).
More Information
For more information, see the SAP Help Portal BI Content documentation for Human Resources at http://
help.sap.com
SAP NetWeaver SAP NetWeaver by Key Capability Information Integration by Key
Capability BI Content BI Content 705 Human Resources Organizational Management ODS Objects .
13.4.4.3.5.3 Session Security Protection
Use
To increase security and prevent access to the SAP logon ticket and security session cookie(s), we recommend
activating secure session management.
We also highly recommend using SSL to protect the network communications where these security-relevant
cookies are transferred.
Session Security Protection on the AS ABAP
The following section is relevant for Manager Self-Service in SAP NetWeaver Business Client:
To prevent access in javascript or plug-ins to the SAP logon ticket and security session cookies
(SAP_SESSIONID_<sid>_<client>), activate secure session management. With an existing security
session, users can then start applications that require a user logon without logging on again. When a security
session is ended, the system also ends all applications that are linked to this security session.
Use the transaction SICF_SESSIONS to specify the following parameter values shown in the table below in
your AS ABAP system:
Session Security Protection Prole Parameters
Prole Parameter Recommended Value Comment
icf/
set_HTTPonly_flag_on_cookies
0 Client-Dependent
login/ticket_only_by_https
1 Not Client-Dependent
For more information, including a list of the relevant prole parameters and detailed instructions, see Activating
HTTP Security Session Management on AS ABAP in the AS ABAP security documentation.
224
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.4.3.5.4 Network and Communication Security
Your network infrastructure is extremely important in protecting your system. Your network needs to support
the communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats based on software aws (at both the operating system
level and application level) or network attacks such as eavesdropping. If users cannot log on to your application
or database servers at the operating system or database layer, then there is no way for intruders to
compromise the machines and gain access to the back-end system’s database or les. Additionally, if users are
not able to connect to the server LAN (local area network), they cannot exploit well-known bugs and security
holes in network services on the server machines.
The network topology for Manager Self-Service is based on the topology used by the SAP NetWeaver platform.
Therefore, the security guidelines and recommendations described in the SAP NetWeaver Security Guide also
apply to Manager Self-Service. Details that specically apply to Manager Self-Service are described in the
following topics:
● Network Security
This topic describes the recommended network topology for Manager Self-Service. It shows the
appropriate network segments for the various client and server components and where to use re walls for
access protection. It also includes a list of the ports needed to operate Manager Self-Service.
● Communication Destinations
This topic describes the information needed for the various communication paths, for example, which
users are used for which communications.
For more information, see the following sections in the SAP NetWeaver Security Guide:
● Network and Communication Security
● Security Guides for Connectivity and Interoperability Technologies
13.4.4.3.5.4.1 Network Security
Ports
Manager Self-Service runs on SAP NetWeaver and uses the ports from the AS ABAP (for Manager Self-Service
in SAP NWBC).
For more information, see the topic for AS ABAP Ports in the corresponding SAP NetWeaver Security Guides.
For other components, for example, SAPinst, SAProuter, or the SAP Web Dispatcher, see https://
help.sap.com/viewer/ports.
13.4.4.3.5.4.2 Communication Destinations
The tables below provide an overview of the communication destinations required for the MSS deployment
options.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 225
Manager Self-Service in SAP Business Client
For this deployment option, you have to maintain RFC connections using the transaction SM59, see also the
following table 1.
Table 1: Connection Destinations for Manager Self-Service in SAP Business Client
Destination Delivered Type Recommended User
Authorizations
Description
SAP_ECC_HumanReso
urces
No ABAP connection n/a System alias for the
ECC HCM system
SAP_ECC_HumanReso
urces_HTTP
No HTTP connection n/a System alias for the
ECC HCM system
SAP_ECC_FINANCIAL
S
No ABAP connection n/a System alias for the
ECC FI system for Fi
nancials applications
SAP_ECC_FINANCIAL
S_HTTP
No HTTP connection n/a System alias for the
ECC FI system for Fi
nancials applications
SAP_EREC_TalentMa
nagement
No ABAP connection n/a System alias for the
SAP E-Recruiting sys
tem
SAP_EREC_TalentMa
nagement_HTTP
No HTTP connection n/a System alias for the
SAP E-Recruiting sys
tem
13.4.4.3.5.5 Internet Communication Framework Security
Use
You should only activate the services needed for the applications running in your system. For Manager Self-
Service in SAP Business Client, the following services are needed which you can nd under the path
default_host/sap/bc/webdynpro/sap/:
For applications from the Suite Inbox (CA-EPT-IBO):
● IBO_WDA_INBOX
For applications from HCM Processes and Forms (PA-AS):
● asr_form_display
● asr_mass_start_process
● asr_pa_pd_processes_display
226
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
● asr_processes_display
● ASR_PROCESS_EXECUTE_FPM
● asr_process_select
● asr_srch_pd_process
For applications from Cross-Application Time Sheet (CA-TS) and Personal Time Management (PT):
● HRMSS_A_CATS_APPROVAL
● HRESS_A_PTARQ_LEAVREQ_APPL
● HRESS_A_LEA_TEAM_CALENDAR
For applications from Talent Management and Talent Development (PA-TM):
● HRTMC_EMPLOYEE_PROFILE
● HRTMC_LONG_PROFILE
● hrtmc_side_by_side
● HRTMC_TA_ASSESSMENT
● HRTMC_TA_DASHBOARD
● HRTMC_TA_DEV_PLAN
● hrtmc_teamviewer
For applications from Performance Management (PA-PD-PM):
● HAP_MAIN_DOCUMENT
● HAP_START_PAGE_POWL_UI_MSS
● HAP_A_PMP_PIE_CHART
● HAP_A_PMP_GOALS
● HAP_A_PMP_OVERVIEW
● HAP_A_PMP_MAIN
For applications from Enterprise Compensation Management (PA-ECM):
● HCM_ECM_PLANNING_OVERVIEW_OIF
● HCM_ECM_PLANNING_UI_GAF
● HCM_ECM_PROFILE_OIF
● HCM_ECM_SIDEBYSIDE_OIF
● HCM_ECM_TEAMVIEWER_OIF
For applications from Personnel Cost Planning (PA-CP):
● WDA_HCP_DET_PLAN
For applications from SAP Learning Solution (PE-LSO):
● LSO_MANAGE_PARTICIPANTS
● LSO_MANAGE_MANDATORY_ASSIGN
For applications from SAP E-Recruiting (PA-ER):
● default_host/sap/bc/erecruiting/dataoverview
● hrrcf_a_dataoverview
● hrrcf_a_requi_monitor
● hrrcf_a_req_assess
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 227

● hrrcf_a_tp_assess
● hrrcf_a_qa_mss
● hrrcf_a_substitution_manager
● hrrcf_a_substitution_admin
Note
You activate the services in Customizing for SAP E-Recruiting at Technical Settings User Interfaces
Manager Involvement Specify E-Recruiting Services for MSS .
For applications from Travel Management (FI-TV):
● FITV_POWL_APPROVER
● FITV_TRIP_FORM
● FITV_POWL_PERSONALIZATION
For applications from the Financials (FI) application area:
● QISR_UI_STATUSOVERVIEW
● QISR_UI_STATUSOVERVIEW
● QISR_UI_STATUSOVERVIEW
● FPB_EXP_OVERVIEW
● FCOM_PBC_MONITOR
● FCOM_PBC_MONITOR
● FPB_VARIANCE_MONITOR_OVERVIEW
● FCOM_EQM_MONITOR
● FPB_LINEITEM_MONITOR_OVERVIEW
● FPB_VARIANCE_MONITOR_OVERVIEW
● FPB_LINEITEM_MONITOR_OVERVIEW
● FCOM_EQM_MONITOR
● FCOM_PBC_MONITOR
● FCOM_PBC_MONITOR
● FPB_LINEITEM_MONITOR_OVERVIEW
● FPB_VARIANCE_MONITOR_OVERVIEW
Activities
Use the transaction SICF to activate these services.
If your rewalls use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
228
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
More Information
For more information, see Activating and Deactivating ICF Services in the SAP NetWeaver Library
documentation.
For more information about ICF security, see the RFC/ICF Security Guide .
13.4.4.3.5.6 Security-Relevant Logging and Tracing
Manager Self-Service relies on the logging and tracing mechanisms from SAP NetWeaver.
For more information, see the following topics:
● For the AS ABAP (relevant for Manager Self-Service in SAP NetWeaver Business Client):
○ Auditing and Logging
○ Tracing and Logging (for NWBC)
13.4.5 Talent Management
13.4.5.1 SAP E-Recruiting
13.4.5.1.1 Security Aspects of Data Flow and Processes
The following section provides an overview of the data ows in the security-relevant scenarios for SAP E-
Recruiting.
13.4.5.1.1.1 Data Entry by External Candidate in Distributed
System
The gure below provides an overview of the data ow for the following scenario: Data entry by the external
candidate in the distributed system
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 229
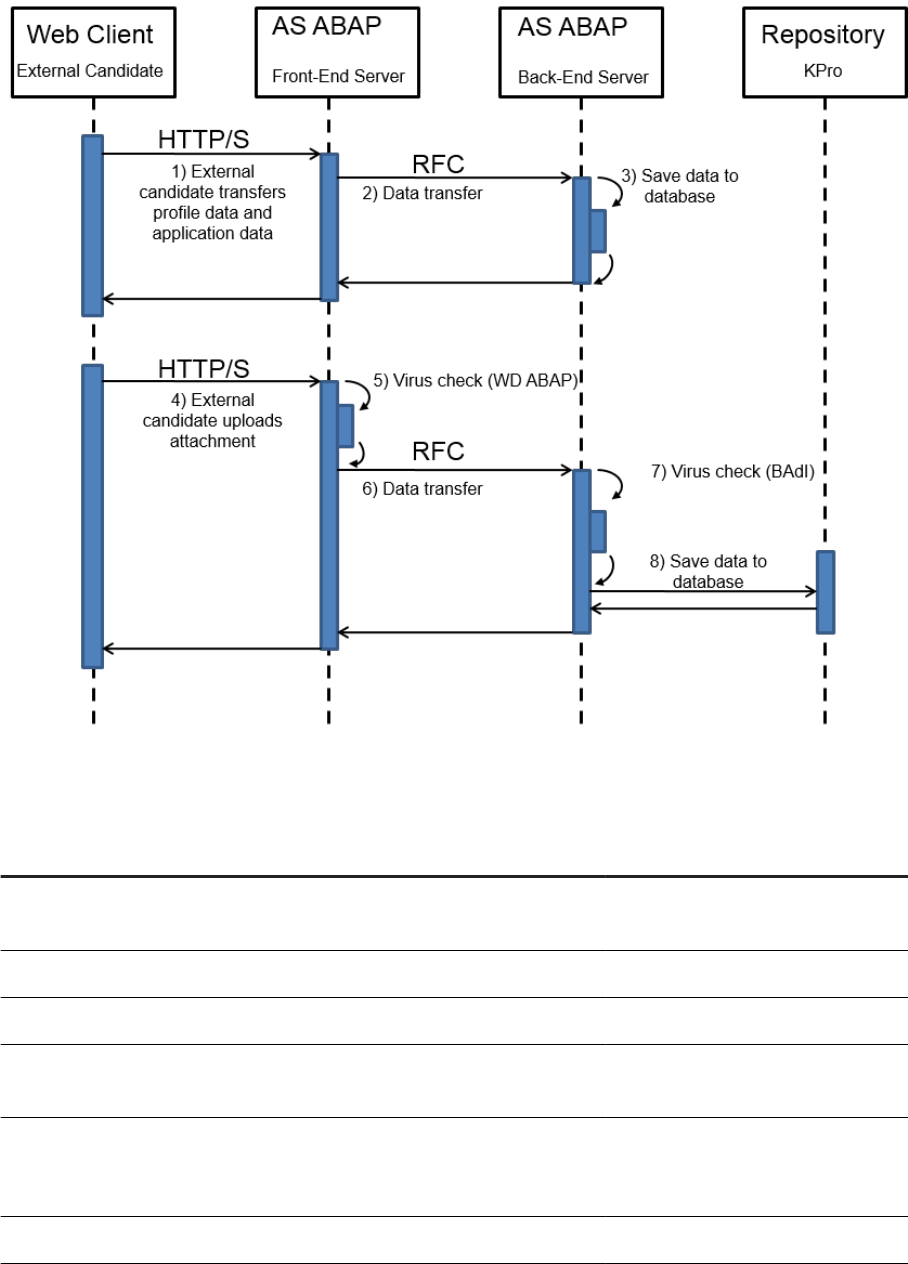
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Description Security Measure
1 External candidate transfers prole
data and application data
External candidate has to conrm the
data privacy statement.
2 Data transfer Access authorization using RFC user
3 Save data to database Not relevant
4 External candidate uploads attach
ments
Not relevant
5 Virus check (WD ABAP) Standard virus check provided by SAP
NetWeaver Application Server (front-
end server)
6 Data transfer Not relevant
230 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
7 Virus check (BAdI) Additional virus check using the BAdI
HRRCF00_ DOC _UPLOAD (backend
server) (see Customizing activity
BAdI:Upload Documents)
8 Save data to database Not relevant
13.4.5.1.1.2 Data Entry in Nondistributed System
The gure below provides an overview of the data ow for the following scenario: Data entry in nondistributed
system.
The data ow is relevant within the framework of the following scenarios:
● The internal or external candidate maintains his or her prole and application.
● The recruiter maintains a candidate’s prole.
● The recruiter or data entry clerk enters an application in the system.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 231
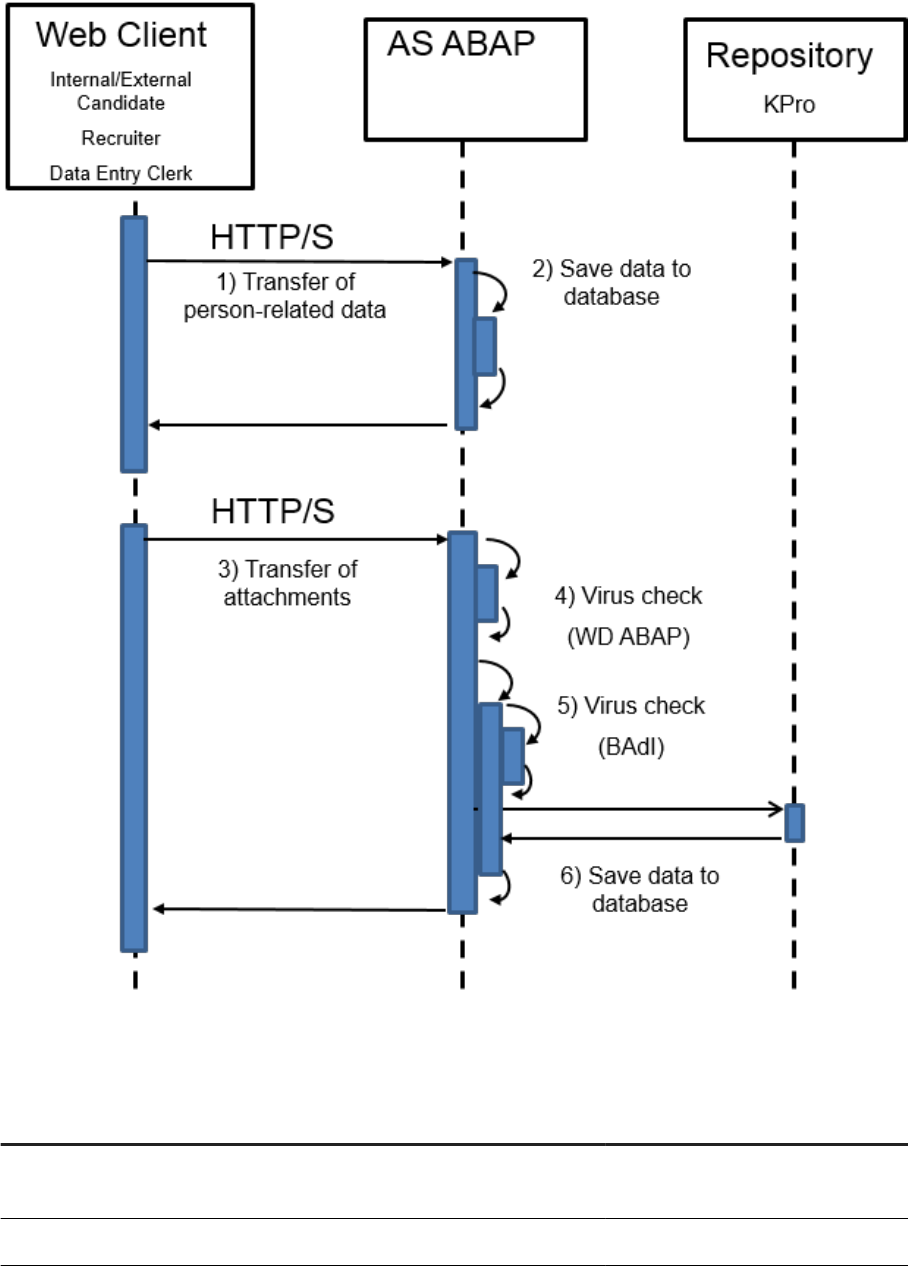
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Description Security Measure
1 Transfer of data External candidate has to conrm the
data privacy statement.
2 Save data to database Not relevant
232 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
3 Transfer of attachments Not relevant
4 Virus check (WD ABAP) Standard virus check provided by SAP
NetWeaver Application Server (front-
end server)
5 Virus check (BAdI) Additional virus check using the BAdI
HRRCF00_ DOC _UPLOAD (backend
server) (see Customizing activity
BAdI:Upload Documents)
6 Save data to database Not relevant
13.4.5.1.1.3 Integration of Org. Mgmt/E-Recruiting in
Distributed System
The gure below provides an overview of the data ow for the following scenario: Integration of Organizational
Management in SAP E-Recruiting in a distributed system.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 233
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Description Security Measure
1 The recruiter requests data overviews
for organizational units, positions, or
jobs.
Not Relevant
234 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
2 The SAP NetWeaver Application Server
requests the Organizational Manage
ment data using RFC in the connected
HR system.
Access authorization using RFC user
3 The HR system transfers the data using
XML to the SAP NetWeaver Application
Server.
XML encryption
13.4.5.1.1.4 Integration of Org. Mgmt/E-Recruiting in
Integrated System
The gure below provides an overview of the data ow for the following scenario: Integration of Organizational
Management in SAP E-Recruiting in an integrated system.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 235
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Description Security Measure
1 The recruiter requests data overviews
for organizational units, positions, or
jobs.
Not Relevant
236 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Measure
2 The SAP NetWeaver Application Server
requests the Organizational Manage
ment data in the integrated HR system.
Not relevant
3 The integrated HR system transfers the
data using XML to the SAP NetWeaver
Application Server.
XML encryption
13.4.5.1.1.5 Recommendation of Job Posting (Tell a Friend)
The gure below provides an overview of the data ow for the following scenario: The candidate uses the Tell A
Friend function to inform another person about an employment opportunity.
The process runs as described below if you enter the value MAILTO or MAILTO_REGONLY for the parameter
TF_SEND_METHOD in Customizing for SAP E-Recruiting under Technical Settings → User Interfaces →
Candidate → Backend Candidate → Assign Values to Interface Parameters (Web Dynpro ABAP).
We recommend that you do not use the default delivery TF_SEND_METHOD = ' ' as this means that the e-mails
with the recommendation letter are sent using your e-mail server. As the candidate is responsible for specifying
the recipient and content of the e-mail message to be sent, undesirable content could be sent from the sender
address of your e-mail server.
For more information, see the documentation for the Customizing activity Assign Values to Interface
Parameters (Web Dynpro ABAP) and SAP Note 1390162.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 237
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Name Security Measure
1 Trigger Tell a Friend function Not relevant
238 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Name Security Measure
2 Open local e-mail client The e-mail client (for example, Micro
soft Outlook) is opened locally on the
candidate’s computer. This client (and
not the central e-mail client) then sends
the e-mail. You activate this process us
ing the parameter TF_SEND_METHOD
in the Customizing activity Assign
Values to Interface Parameters (Web
Dynpro ABAP).
3 Send e-mail Not relevant
13.4.5.1.1.6 Resume Parsing (Candidate, Integrated System)
The gure below provides an overview of the data ow for the following scenario:
The candidate uploads his or her resume as an attachment and then sends it to a third-party vendor for
parsing. The front end and backend for the candidate’s user run on the same system.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 239
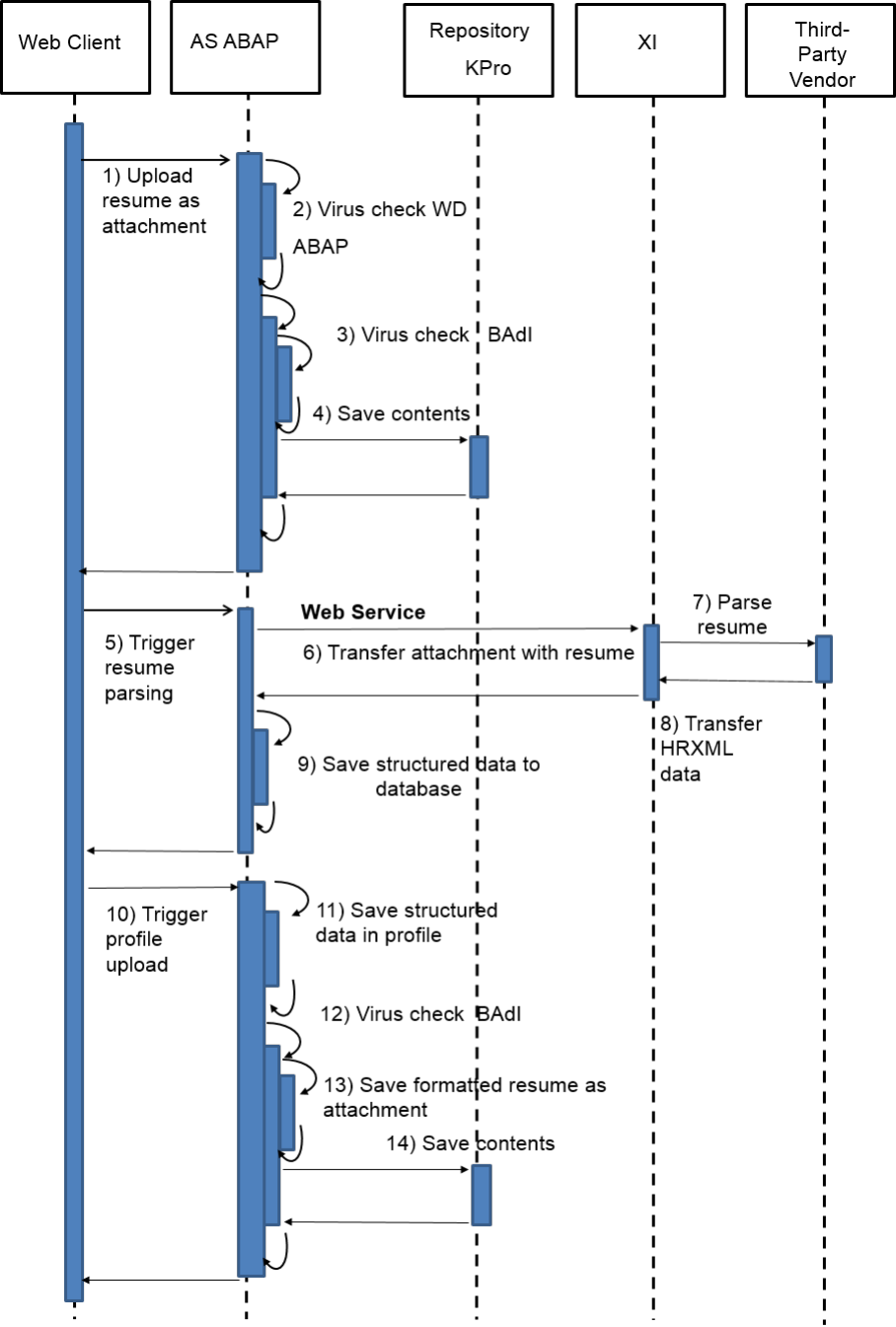
240 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Name Security Measure
1 Upload resume as attachment Not relevant
2 Virus check WD ABAP Standard virus check provided by SAP
NetWeaver Application Server (front-
end server)
3 Virus check BAdI Additional virus check using the BAdI
HRRCF00_ DOC _UPLOAD (backend
server)
(see Customizing activity BAdI: Upload
Documents)
4 Save contents Not relevant
5 Trigger Resume Parsing Not relevant
6 Transfer attachment with resume Not relevant
7 Parse resume For XI-relevant security topics, see
Process Integration (PI) Security
Guides.
8 Transfer HRXML data HRXML coding
9 Save structured data to database Not relevant
10 Trigger prole upload Not relevant
11 Save structured data in prole Not relevant
12 Virus check BAdI Additional virus check using the BAdI
HRRCF00_ DOC _UPLOAD (backend
server)
(see Customizing activity BAdI: Upload
Documents)
13 Save formatted resume as attachment Not relevant
14 Save contents Not relevant
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 241
13.4.5.1.1.7 Resume Parsing (Candidate, Distributed
Scenario)
The gure below provides an overview of the data ow for the following scenario: The candidate uploads his or
her resume as an attachment and then sends it to a third-party vendor for parsing. The front end and backend
for the candidate’s user run on dierent systems.
242 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
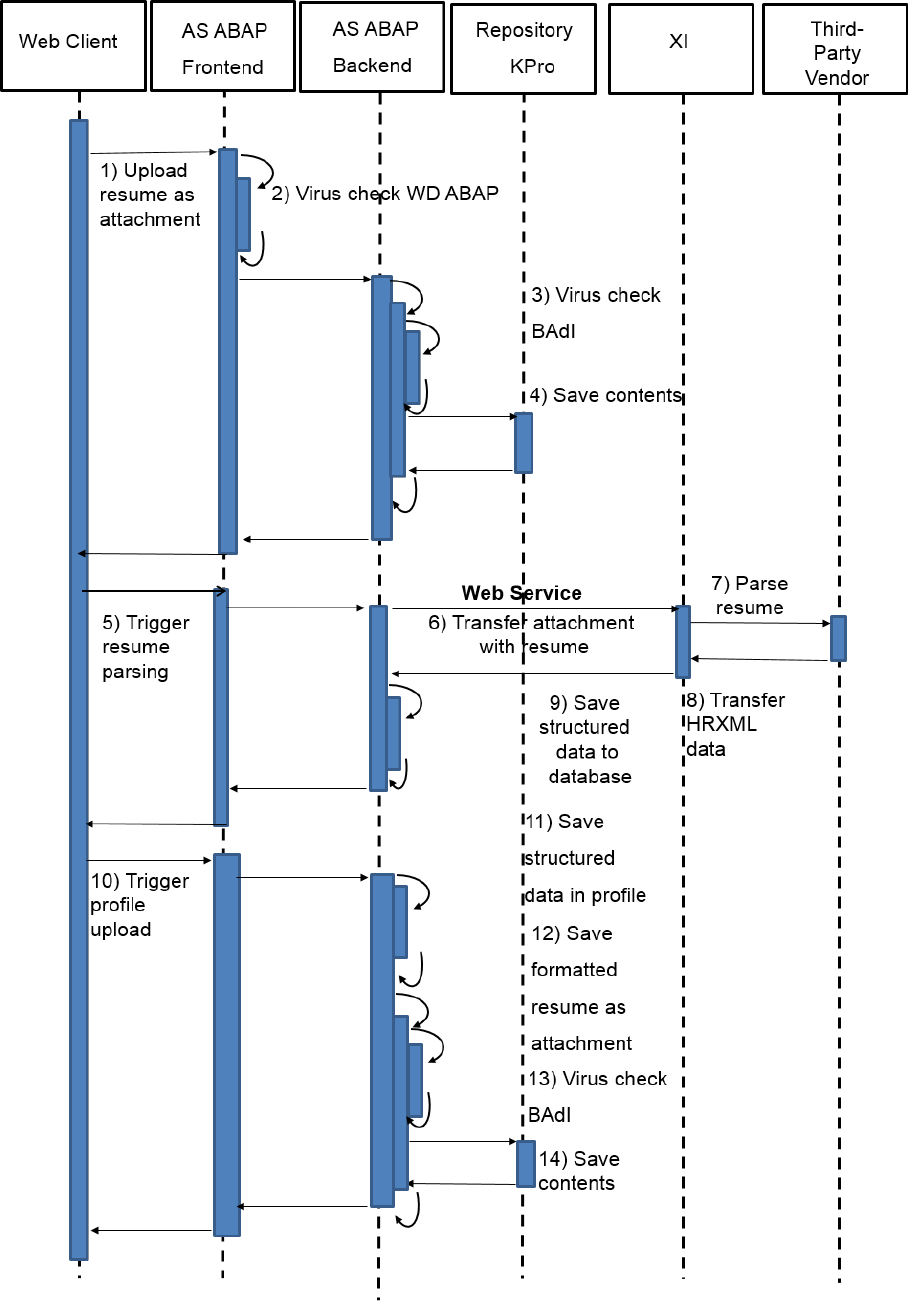
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 243
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Name Security Measure
1 Upload resume as attachment Not relevant
2 Virus check WD ABAP Standard virus check provided by SAP
NetWeaver Application Server (front-
end server)
3 Virus check BAdI Additional virus check using the BAdI
HRRCF00_ DOC _UPLOAD (backend
server)
(see Customizing activity BAdI: Upload
Documents)
4 Save contents Not relevant
5 Trigger Resume Parsing Not relevant
6 Transfer attachment with resume Not relevant
7 Parse resume For XI-relevant security topics, see SAP
Process Integration (PI) Security
Guides.
8 Transfer HRXML data HRXML coding
9 Save structured data to database Not relevant
10 Trigger prole upload Not relevant
11 Save structured data in prole Not relevant
12 Virus check BAdI Additional virus check using the BAdI
HRRCF00_ DOC _UPLOAD (backend
server)
(see Customizing activity BAdI: Upload
Documents)
13 Save formatted resume as attachment Not relevant
14 Save contents Not relevant
244 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.5.1.1.8 Resume Parsing (Recruiter)
The gure below provides an overview of the data ow for the following scenario:
The recruiter uploads a candidate’s resume as an attachment and then sends it to a third-party vendor for
parsing. The data is then transferred to the corresponding elds of the form for the Entry of External
Applications application.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 245
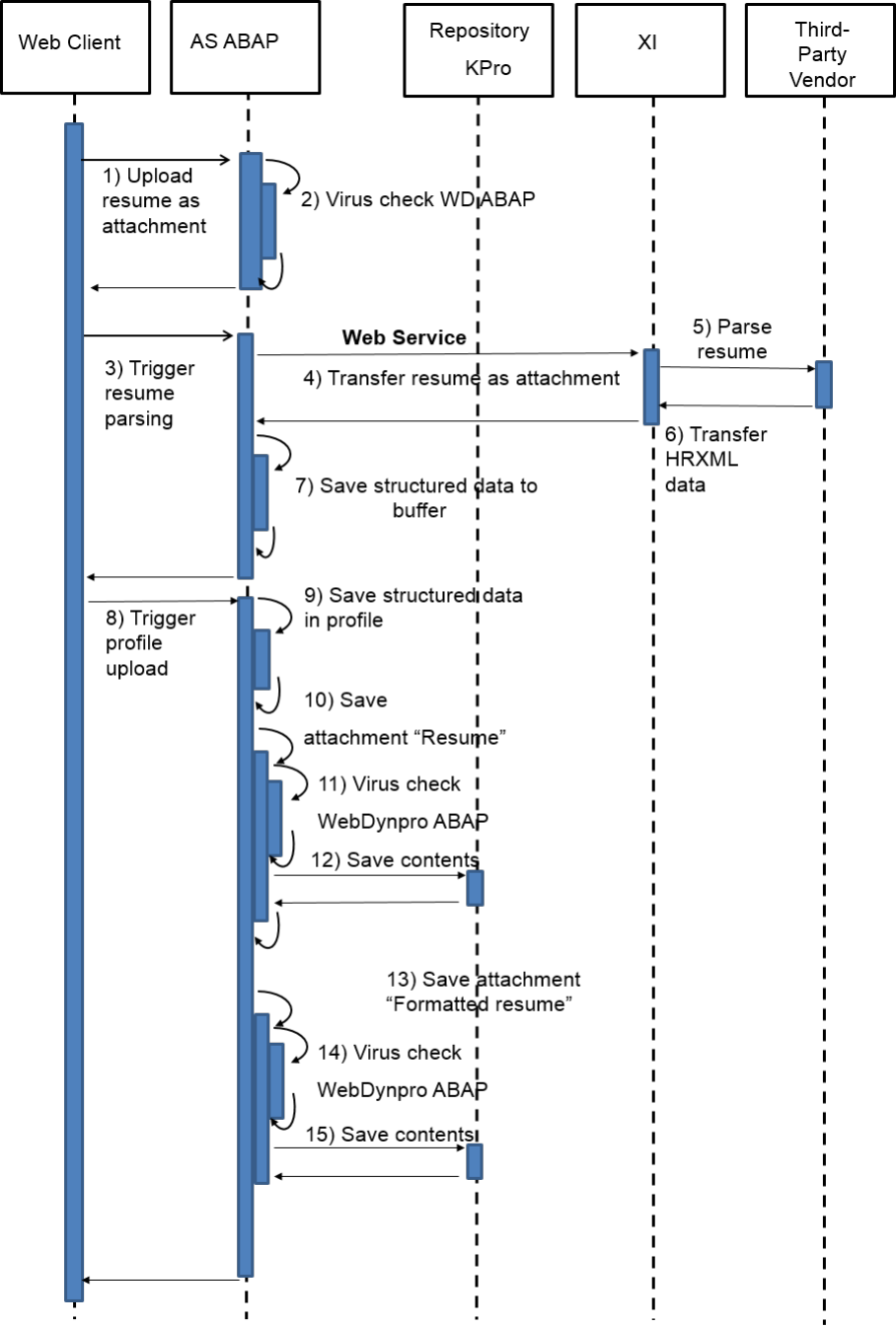
246 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Name Security Action
1 Upload resume as attachment Not relevant
2 Virus check WD ABAP Standard virus check provided by SAP
NetWeaver Application Server (front-
end server)
3 Trigger Resume Parsing Not relevant
4 Transfer resume as attachment Not relevant
5 Parse resume For XI-relevant security topics, see SAP
Process Integration (PI) Security
Guides .
6 Transfer HRXML data HRXML coding
7 Save structured data to buer Not relevant
8 Trigger prole upload Not relevant
9 Save structured data in prole Not relevant
10 Save attachment “Resume” Not relevant
11 Virus check WD ABAP Standard virus check provided by SAP
NetWeaver Application Server (front-
end server)
12 Save contents Not relevant
13 Save attachment “Formatted resume” Not relevant
14 Virus check WD ABAP Standard virus check provided by SAP
NetWeaver Application Server (front-
end server)
15 Save contents Not relevant
13.4.5.1.1.9 Background Check
The gure below provides an overview of the data ow for the following scenario: The recruiter forwards data
regarding a candidate’s education, work experience, or qualications to an external provider, who then checks
that this data is correct.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 247
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Name Security Measure
1 Initialize background check Not Relevant
2 Summarize prole data Not Relevant
3 Transfer prole data Not Relevant
4 Request background check For XI-relevant security topics, see: SAP
Process Integration Security Guide
5 Return order ID Not Relevant
6 Initialize request for processing status Not Relevant
7 Transfer request Not Relevant
248 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Step Name Security Measure
8 Request processing status For XI-relevant security topics, see: SAP
Process Integration Security Guide
9 Return processing status Not Relevant
10 Initialize request for access URL Not Relevant
11 Transfer request Not Relevant
12 Request URL For XI-relevant security topics, see: SAP
Process Integration Security Guide
13 Access to URL that the third-party ven
dor uses to display the report for the
background check
Not Relevant
13.4.5.1.1.10 Registration Process with E-Mail Verication
The gures below provide an overview of a candidate’s registration process with e-mail verication. This is
relevant for persons who want to register their details in the Talent Warehouse or for persons who want to
submit an application for an employment opportunity and who have to register their details rst in order to do
so. The process description is divided into two parts in the gures below. The rst gure shows the process up
to the point in time when the system sends a conrmation mail for the e-mail address. The second gure
shows the process from the moment that the candidate nds this e-mail in his or her e-mail inbox.
For more information about the registration process, see section Registration with E-Mail Verication in the SAP
Library for SAP S/4HANA under Human Resources Talent Management SAP E-Recruiting (PA-ER)
Candidate Storage of Data in Talent Warehouse Registration . For more information about the application
process with registration at the same time, see section Online Application of Unregistered Candidate in the SAP
Library for SAP S/4HANA under
Human Resources Talent Management SAP E-Recruiting (PA-ER)
Candidate .
Note
This process is relevant if the switch RECFA VERIF is set in the Customizing activity Set System
Parameters .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 249
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Description Security Action
Optional step The unregistered candidate nds a suit
able job posting and submits an appli
cation for this posting. In this case, the
candidate has to register his or her de
tails before the application can be sub
mitted. (Continue with step 1)
For the unregistered candidate, the sys
tem uses the service user that is as
signed to the corresponding ICF service
in the Customizing activity Specify E-
Recruiting Services (WebDynpro
ABAP) .
250 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Step Description Security Action
1 The unregistered candidate calls the
screen page for the registration and en
ters the data required for the registra
tion in the Talent Warehouse.
For the unregistered candidate, the sys
tem uses the service user that is as
signed to the corresponding ICF service
in the Customizing activity Specify E-
Recruiting Services (WebDynpro
ABAP) .
2 The unregistered candidate performs
the registration.
3 The system checks the information for
completeness and correctness and, if
applicable, asks the unregistered candi
date to correct the information.
4 The system creates an unveried candi
date.
In the Candidate Overview infotype
(5102) in the Status of E-Mail
Verication eld, the system enters the
value 1 ( Outstanding ). At the same
time, the system creates a user for the
candidate.
5a The system informs the candidate that
the registration process was triggered
and that he or she will receive a conr-
mation mail.
5b At the same time, the system sends a
conrmation mail via the mail server to
the e-mail address stored by the candi
date. This contains a link that the candi
date must use to conrm his or her e-
mail address and so complete the regis
tration.
If the user does not subsequently con
rm his or her e-mail address, the user
cannot access the Talent Warehouse.
In the Customizing activity Determine
Rules for Periodic Services , you can
specify for how long the link for con
rming the e-mail address is to be valid.
Optional step If the candidate has registered his or
her details as part of submitting an ap
plication, the system now displays the
application wizard. The candidate can
complete the application but cannot
send it until he or she has conrmed
the e-mail address and completed the
registration process.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 251
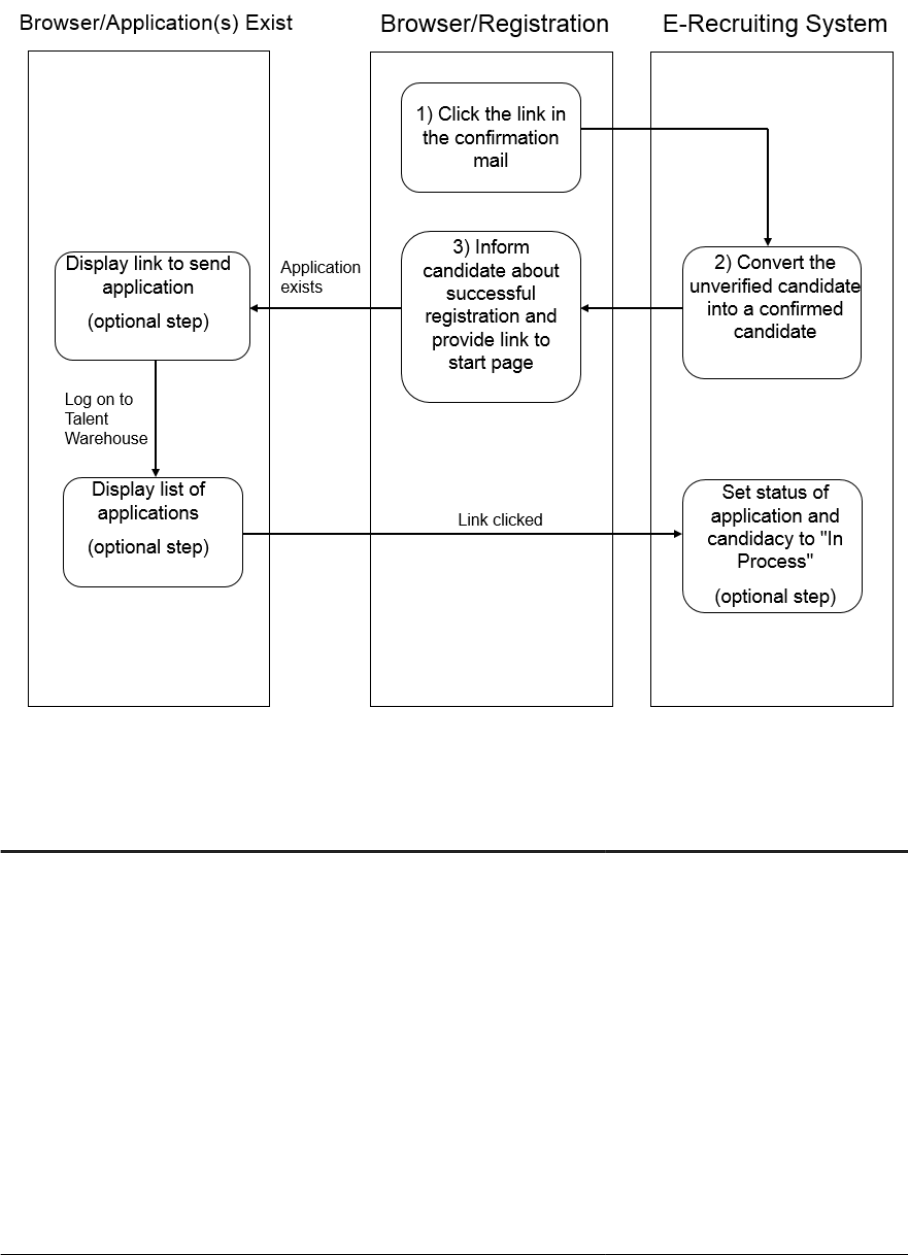
The table below lists the security aspect that has to be taken into account for the process step and the security
action that is taken.
Step Description Security Action
1 The unveried candidate nds the con
rmation mail in his or her e-mail inbox,
opens the mail, and clicks the link to
conrm the e-mail address.
In the Customizing activity Determine
Rules for Periodic Services , you can
specify the following (in addition to the
validity period of the link for the conr-
mation):
● Period after which a reminder mail
is sent to the unveried candidate
● Maximum number of possible re
quests for a new conrmation mail
● Option whether candidates can re
quest a new conrmation mail
even though the validity period of
the last conrmation mail sent was
exceeded
252
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Step Description Security Action
2 The system converts the unveried
candidate into a conrmed candidate.
In the Candidate Overview infotype
(5102) in the Status of E-Mail
Verication eld, the system enters the
value 0 ( Conrmed ).
3 The candidate is informed about the
successful registration. At the same
time, the candidate receives a link that
he or she can use to log on to the Talent
Warehouse.
For security reasons, the conrmation
does not contain the password that the
user needs to log on to the Talent Ware
house and which he or she entered on
the registration screen.
Optional step If the candidate registered his or her de
tails while submitting an application
and has already created one or more
applications, the system displays a link
that the candidate can then use to dis
play a list of the applications.
To do this, the candidate has to log on
to the Talent Warehouse with his or her
user alias and password.
Optional step The system displays a list of applica
tions that have not yet been sent. The
candidate submits an application.
The candidate can now submit applica
tions because his or her e-mail address
has now been conrmed.
Optional step The system set the status of the appli
cation and the candidacy to In Process .
Recruiters can now view the application
and the candidate prole.
13.4.5.1.1.11 Deregistration and Deletion of External
Candidates
Denition
In SAP E-Recruiting, there is a two-step process to delete a candidate. The rst step is deregistering the
external candidate. The second step is deleting the candidate data from the Talent Warehouse.
This document describes how the system handles the candidate’s data in the dierent scenarios.
Note
If you delete the external candidates via the HRRCF_CAND archiving object and the functions of the SAP
Information Lifecycle Management
(ILM) at the same time with the processes described here, data
inconsistencies may occur. For more information, see Destroying Candidate Data Using HRRCF_CAND.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 253

Candidates delete their registration themselves
For information about the service, see Deleting the Registration.
If the candidate requests the deletion of his or her own registration, the system performs the following steps:
● The Registration of Candidate Deleted indicator is set in infotype 5102 (Candidate Overview).
● The candidate’s user is locked.
● The workow ERCCandDerig is triggered. The workow runs automatically in the background. For
information about which data of the candidate is processed by the workow, see the documentation for the
Workow for Deleting a Candidate’s Registration.
The remaining data for the candidate is retained in the database.
Administrator deletes the registration of external candidates
For information about the service, see Deleting Registration of External Candidates.
If the administrator deletes the registration of an external candidate, the system performs the following steps:
● The Registration of Candidate Deleted indicator is set in infotype 5102 (Candidate Overview).
● The workow ERCCandDerig is triggered. The workow runs automatically in the background. For
information about which data of the candidate is processed by the workow, see the documentation for the
Workow for Deleting a Candidate’s Registration.
The remaining data for the candidate is retained in the database.
Administrator deletes the external candidates
Even after an external candidate is deregistered, the candidate’s data still exists in the system. To delete the
candidate completely from the system, the administrator has to delete the external candidate.
For information about the service, see Deleting External Candidates.
Note
The administrator can only delete candidates for whom there are no applications or assignments with the
status In Process or To Be Hired.
When deleting data, the system also takes into account the legal time limits for retaining data (see the end
of this document).
When the candidates are deleted, the associated business partners are not deleted, but are archived. You
can delete business partners later using the transaction BUPA_ DEL.
If the prerequisites for the deletion are met, the system executes the following steps:
● Deletion of the candidate’s applications and any related objects:
○ HR object Application
254
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

○ Audit Trails
○ Documents for the application in Knowledge Provider (KPro)
○ Activities
● Deletion of the candidate’s candidacies and any related objects:
○ HR object Candidacy
○ Documents for the candidacy in Knowledge Provider (KPro)
○ Activities
● Deletion of the job agents created by the candidate
● Deletion of the candidate and any related objects:
○ HR object Candidate
○ The candidate’s user in the backend system; in the distributed system, also the candidate’s user in the
front-end system
○ Documents for the candidate in Knowledge Provider (KPro)
○ Activities
Delete External Candidates (report)
Another option for deleting external candidates is to use the RCF _DELETE_EXT_ CAND report.
You call this report in Customizing for SAP E-Recruiting under Tools → Delete External Candidates. For more
information, see the documentation for the Customizing activity.
We recommend you use this report instead of using the Delete External Candidates service as the report
enables you to use multiple selection criteria. In this way, the user can specically select deregistered
candidates, for example.
The report is otherwise identical to the Delete External Candidates service.
Retention periods for candidate-based data
You enter the retention periods that the report has to take into account in Customizing for SAP E-Recruiting
under Store Legal Periods. For more information, see the documentation of the Customizing activity.
13.4.5.1.1.12 Sending E-Mails Using the Workow
SAP E-Recruiting uses workows that send various documents by e-mail.
The table below shows the workows and lists the e-mails that are sent using the relevant workows.
E-Mails Using Workows
Workow Template Description E-Mail Recipient E-Mail Content How E-Mail Is Sent
WS51800042 ERCAdjEntry - - -
WS51900003 ERCSendPwd Candidate Send password Method
WS51900005 ERCStatusChg Candidate Conrmation of receipt
of application
Method
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 255
Workow Template Description E-Mail Recipient E-Mail Content How E-Mail Is Sent
Candidate Correspondence: Re
jection
Method
Recruiter Notication that appli
cation is withdrawn
WF E-Mail
WS51900006 ERCCandDerig Candidate Conrmation that can
didate has been dereg
istered
Method
WS51900007 ERCApprReqWD Approver Notication to the ap
prover
WF E-Mail
Requester Notication of the de
cision
WF E-Mail
WS51900008 ERCObjCreate Candidate Acknowledge Candi
date
Method
Candidate Verication mail Method
WS51900009 ERCActCreate - - -
WS51900010 ERCStatChg_2 Candidate Conrmation of receipt
of application
Method
Candidate Correspondence: Re
jection
Method
Recruiter Notication that appli
cation is withdrawn
WF E-Mail
WS51900011 ERCActCrea_2 - - -
WS51900018 ERCSendVerif Candidate Conrmation mail Method
13.4.5.1.2 User Administration and Authentication
SAP E-Recruiting uses the user management and authentication mechanisms provided with the SAP
NetWeaver platform, in particular the SAP NetWeaver Application Server for ABAP. Therefore, the security
recommendations and guidelines for user administration and authentication as described in the SAP
NetWeaver Application Server for ABAP also apply to SAP E-Recruiting.
In addition to these guidelines, we include information about user administration and authentication that
specically applies to SAP E-Recruiting in the following topics:
● User Management
This topic lists the tools to use for user management, the types of users required, and the standard users
that are delivered with SAP E-Recruiting.
256
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

● Integration into Single-Sign-On Environments
This topic describes how SAP E-Recruiting supports Single Sign-On mechanisms.
13.4.5.1.2.1 User Management
Denition
User management for SAPE-Recruiting uses the mechanisms provided by SAP Web Application Server ABAP
such as tools, user types, and password policies. For an overview of how these mechanisms apply for SAPE-
Recruiting, see the sections below.
User Administration Tools
The following table shows the tools to use for user management and user administration for SAPE-Recruiting .
User Management Tools
Tool Detailed Description Prerequisites
User and Role Maintenance (transac
tion PFCG)
You can use the Role Maintenance
transaction PFCG to generate proles
for the SAPE-Recruiting users.
Technical Settings for User Manage
ment in SAPE-Recruiting
For more information on user proles
and the roles, see Customizing for SAP
E-Recruiting under
Technical
Settings User Administration.
Workow Settings For more information, see the Custom
izing for SAPE-Recruiting under
Technical Settings Workow
Workow in E-Recruiting .
You use the SAP Workow.
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively have to change their passwords on a regular
basis, but not users who run background processing jobs.
Note
For more information, see the Customizing for SAPE-Recruiting under Technical Settings User
Administration Create Special Users .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 257

The user types required for SAPE-Recruiting are:
● Reference user
You can create reference users to simplify authorization maintenance. You assign dierent roles to each
reference user. If you then assign a reference user to a user, the user inherits all of the reference user’s role
attributes and authorization prole.
● Service user
Some scenarios are accessible for registered users only; other scenarios are also accessible for
unregistered users (registration, job postings, direct application). You must assign a service user to these
services so that an unregistered user can use them.
● Background User for Workow
To be able to use the workow functions, you must create a system user (such as WF-BATCH) in the
standard system.
For more information, see the Customizing for SAP E-Recruiting under Technical Settings Workow
Workow in E-Recruiting .
In SAP E-Recruiting, you must assign a candidate to this user. To do this, you can use the report
RCF_CREATE_USER, irrespective of whether you run SAP E-Recruiting and the HR system on the same
instance or on dierent instances.
For more information, see Background User for Workow under Talent Management SAP E-Recruiting
Authorizations in the SAP S/4HANA Security Guide for Human Resources.
Standard Users
We do not deliver standard users within SAP E-Recruiting.
13.4.5.1.2.2 Integration into Single Sign-On Environments
The most widely-used supported mechanisms are listed below. For a complete list, see the link provided below.
● Secure Network Communications (SNC)
SNC is available for user authentication and provides for an SSO environment when using the SAP GUI for
Windows or Remote Function Calls.
● SAP logon tickets
SAP E-Recruiting supports the use of logon tickets for SSO when using a Web browser as the frontend
client. In this case, users can be issued a logon ticket after they have authenticated themselves with the
initial SAP system. The ticket can then be submitted to other systems (SAP or external systems) as an
authentication token. The user does not need to enter a user ID or password for authentication but can
access the system directly after the system has checked the logon ticket.
● Client certicates
As an alternative to user authentication using a user ID and passwords, users using a Web browser as a
frontend client can also provide X.509 client certicates to use for authentication. In this case, user
authentication is performed on the Web server using the Secure Sockets Layer Protocol (SSL Protocol)
and no passwords have to be transferred. User authorizations are valid in accordance with the
authorization concept in the SAP system.
● Security Assertion Markup Language (SAML) 2.0
258
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

SAML 2.0 provides a standards-based mechanism for SSO. The primary reason to use SAML 2.0 is to
enable SSO across domains.
SAP E-Recruiting supports the Single Sign-On (SSO) mechanisms provided by SAP NetWeaver. Therefore, the
security recommendations and guidelines for user administration and authentication as described in the SAP
NetWeaver Security Guide also apply to SAP E-Recruiting.
For more information about the available authentication mechanisms, see User Authentication and Single Sign-
On in the SAP NetWeaver Library.
13.4.5.1.3 Authorizations
SAP E-Recruiting uses the authorization concept provided by SAP NetWeaver AS for ABAP. Therefore, the
recommendations and guidelines for authorizations as described in the SAP NetWeaver AS Security Guide
ABAP also apply to SAP E-Recruiting .
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on theSAP Web AS ABAP .
Note
For more information about how to create roles, see section Role Administration under Identity
Management in the SAP Library for SAP S/4HANA.
The following section shows the standard roles and the relevant authorization objects that SAP E-Recruiting
uses. These are:
● Background User for Workow
● Recruiter, Administrator, and Data Entry Clerk
● Manager
● Candidate
Authorization Object S_ICF
We strongly recommend that you use the authorization object S_ICF to safeguard the Web Dynpro applications
in SAP E-Recruiting. For the relevant applications, see the ICF service tree (transaction SICF ) under /
default_host/sap/bc/webdynpro/sap . The names of the applications in SAP E-Recruiting start with ERC for
the recruiter and the administrator, and with HRRCF for the candidate.
You can safeguard each application by entering a character string for it in the SAP Authorization eld under
Service Data and using this character string in the eld ICF_VALUE of the authorization object S_ICF in the
corresponding user roles. For more information, see the documentation for Authorization Object S_ICF.
For information about services relevant for SAP E-Recruiting in the ICF service tree, see Internet
Communication Framework Security of SAP E-Recruiting .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 259

13.4.5.1.3.1 Background User for Workow
Standard Roles
The table below shows the standard role that SAP E-Recruiting uses for the background user. SAP E-Recruiting
requires this background user for the execution of the workow. The background user is usually the WF-BATCH
user.
Standard Role for the Workow
Role Description
SAP_RCF_INT_CANDIDATE_SERVER Internal Candidate (Server) under Roles (User Proles)
This role provides the necessary authorizations for an inter
nal candidate in SAP E-Recruiting that are required on the
backend system when using a separated system (front-end
and backend on dierent systems).
You have to create a corresponding candidate for the background user of the workow. You use the
RCF_CREATE_USER report to do this. For more information, see the Customizing for SAP E-Recruiting under
Technical Settings → Workow → Workow in E-Recruiting .
For the background user to be used in SAP E-Recruiting, the background user requires the authorization to
make status changes to the SAP E-Recruiting objects (authorization object P_RCF_STAT) in addition to all of
the authorizations usually assigned to an internal candidate.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by SAP E-Recruiting .
For more information, see section Authorizations for SAP E-Recruiting under Roles (User Proles) .
Standard Authorization Objects
Authorization Object Field Value Description
P_RCF_APPL RCF_APPL SAP E-Recruiting applica
tions
Authorization object that
species within SAP E-Re
cruiting which SAP E-Recruit
ing applications a user can
call.
The authorization object is
used for the (internal and ex
ternal) candidates' applica
tions.
260 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
R_RCF_VIEW RCF_VIEW SAP E-Recruiting data over
views
Authorization object that
species within SAP E-Re
cruiting which data overviews
a user can access.
P_RCF_POOL RCF_POOL The following ways to access
the candidate pool directly
are available:
● Status-Independent Ac
cess to Candidates (DI
RECT_ACC)
● Recognition of Multiple
Applicants
(DUPL_CHECK)
● Maintenance of Candi
date Data
(CAND_MAINT)
Authorization object that
species within SAP E-Re
cruiting which type of direct
access a user can have to the
candidates in the Talent Pool.
P_RCF_STAT OTYPE
RCF_STAT
SAP E-Recruiting objects and
permitted object status
Authorization object that
species within SAP E-Re
cruiting the authorization for
status changes to SAP E-Re
cruiting objects (for example,
candidate, application, candi
dacy).
P_RCF_ACT ACTVT
● Activities, processes,
and the following ac
cesses to the activities:
● Add or Create
● Change
● Delete
Authorization object that
species within SAP E-Re
cruiting which type of access
a user can have to activities.
An activity in SAP E-Recruit
ing is therefore identied
through the assigned proc
ess and through the activity
type.
13.4.5.1.3.2 Recruiter, Administrator, and Data Entry Clerk
Standard Roles
The following table shows the standard roles that are used by SAP E-Recruiting for recruiters, administrators,
and data entry clerks .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 261

Standard Roles for Recruiters, Administrators, and Data Entry Clerks
Role Description
SAP _ RCF _REC_ADMIN_ERC_CI_2 Recruiting Administrator (Obsolete)
Administrator for SAP E-Recruiting
Note
This role is obsolete and has been replaced with the role
SAP _ERC_REC_ADMIN_CI_4.
SAP _ RCF _REC_ADMIN_ERC_CI_4 Recruiting Administrator (NWBC) (Obsolete)
You need this role if you want to use the Recruiting Adminis
trator based on SAP Business Client for HTML. The role is a
composite role consisting of the single roles SAP _ RCF
_REC_ADMIN_SR_ERC_CI_4 and SAP _ RCF _REC_AD
MIN_ERC_CI_2.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_REC_ADMIN_CI_4.
SAP _ RCF _REC_ADMIN_SR_ERC_CI_4 Recruiting Administrator (NWBC) (Obsolete)
This role contains the recruiting administrator’s menu for
display based on SAP Business Client for HTML.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_REC_ADMIN_CI_4.
SAP _ERC_REC_ADMIN_CI_4 Recruiting Administrator
SAP _ RCF _ DATA _TYPIST_ERC_CI_2 Data Entry Clerk (Obsolete)
The role contains the authorization for minimum data entry
for incoming paper applications.
Note
This role is obsolete and has been replaced with the role
SAP _ RCF _ DATA _TYPIST_ERC_CI_4.
SAP _ RCF _ DATA _TYPIST_ERC_CI_4 Data Entry Clerk
262 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Role Description
SAP _ RCF _RECRUITER_ERC_CI_2 Recruiter (Obsolete)
The role has access to the following data:
● Candidate data: The data is displayed for all candidates
who stored their data in the Talent Pool.
● All publications
● All requisition data
● All application data
● All data for the selection processes
The role also contains the authorization for minimum data
entry for incoming paper applications.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_RECRUITER_CI_4.
SAP _ RCF _RECRUITER_ERC_CI_4 Recruiter (NWBC) (Obsolete)
You need this role if you want to use the Recruiter based on
SAP Business Client for HTML. The role is a composite role
consisting of the single roles SAP _ RCF _RE
CRUITER_SR_ERC_CI_4 and SAP _ RCF _RE
CRUITER_ERC_CI_2.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_RECRUITER_CI_4.
SAP _ RCF _RECRUITER_SR_ERC_CI_4 Recruiter (NWBC) (Obsolete)
This role contains the recruiter’s menu for display based on
SAP Business Client for HTML.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_RECRUITER_CI_4.
SAP _ERC_RECRUITER_CI_4 Recruiter
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 263

Role Description
SAP _ RCF _ RES _RECRUITER_ERC_CI_2 Restricted Recruiter (Obsolete)
This role contains the same authorizations as the Recruiter
role. However, restricted recruiters cannot change the status
of requisitions and publications (see authorization object P_
RCF _ STAT ).
Note
This role is available only if you activate the business
function HCM _ERC_CI_3.
This role is obsolete and has been replaced with the role
SAP _ERC_ RES _RECRUITER_CI_4.
SAP _ERC_ RES _RECRUITER_CI_4 Restricted Recruiter
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by SAP E-Recruiting .
For more information, see the documentation for SAP E-Recruiting under Authorizations.
Standard Authorization Objects
Authorization Object Field Value Description
P_ RCF _WDUI RCF _APPL SAP E-Recruiting applica
tions
Authorization object that
species within SAP E-Re
cruiting which SAP E-Recruit
ing application a user can
call.
The authorization object is
used for the recruiter's, ad
ministrator's, and data entry
clerk's applications.
R_ RCF _VIEW RCF _VIEW Data Overview Authorization object that
species within SAP E-Re
cruiting which data overviews
a user can access.
264 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
P_ RCF _ POOL RCF _ POOL The following ways to access
the candidate pool directly
are available:
● Status-Independent Ac
cess to Candidates (DI
RECT_ACC)
● Recognition of Multiple
Applicants
(DUPL_CHECK)
● Maintenance of Candi
date Data ( CAND
_MAINT)
Authorization object that
species within SAP E-Re
cruiting which type of direct
access a user can have to the
candidates in the Talent Pool.
P_ RCF _ STAT OTYPE
RCF _ STAT
SAP E-Recruiting objects and
permitted object status
Authorization object that
species within SAP E-Re
cruiting the authorization for
making status changes to
SAP E-Recruiting objects (for
example, candidate, applica
tion, candidacy).
P_ RCF _ACT ACTVT
● Add or Create
● Change
● Delete
Authorization object that
species within SAP E-Re
cruiting which type of access
a user can have to activities.
An activity in SAP E-Recruit
ing is therefore identied
through the assigned proc
ess and through the activity
type.
CA_ POWL POWL _APPID, POWL _ CAT ,
POWL _LSEL,
POWL _QUERY,
POWL _RA_AL,
POWL _TABLE
● POWL _APPID: ERC-
WORKCENTER
Authorization object that
species the authorizations
for the Personal Object Work
list ( POWL ) iViews.
13.4.5.1.3.3 Manager
Using the Manager Involvement in E-Recruiting business function (Manager Self-Service) aects the two
software components SAP Enterprise Extension HR (EA-HR) and SAP E-Recruiting (ERECRUIT). You have to
create an RFC connection from the HR system (EA-HR) to the E-Recruiting system (ERECRUIT). You store an
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 265

anonymous service user (that was dened in the E-Recruiting system) for this RFC connection. The SAP
_RFC_MANAGER_SERVICE role is assigned to the service user.
Standard Roles
The following table shows the standard roles that are used by SAP E-Recruiting for managers .
Standard Roles for Manager Scenario
Role Description
SAP _ RCF _MANAGER Manager
This role is required so that managers can access SAP E-Re
cruiting from the Portal ( Manager Self Service ).
The manager wants to ll the vacant jobs in his or her area.
To do this, the manager creates requisitions with the status
In Process that are then processed further by recruiters.
The role has access to the following data:
Candidate data: The manager can see only the candidate
data that is assigned to requisitions for which the manager is
responsible.
Requisition data and data for selection processes: The man
ager can only see data for which he or she is responsible.
The role also contains the authorization to respond to ques
tionnaires about candidates that are assigned to the relevant
requisitions.
SAP _RFC_MANAGER_SERVICE Service user
This role is required to request a requisition from the HR sys
tem. The service user to which this role is assigned must ex
ist in the E-Recruiting system.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by SAP E-Recruiting .
For more information, see the documentation for SAP E-Recruiting under Authorizations (Recruitment) .
266
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Standard Authorization Objects
Authorization Object Field Value Description
P_ RCF _APPL RCF _APPL SAP E-Recruiting applica
tions
Authorization object that
species within SAP E-Re
cruiting which SAP E-Recruit
ing applications a user can
call.
R_ RCF _VIEW RCF _VIEW SAP E-Recruiting data over
views
Authorization object that
species within SAP E-Re
cruiting which data overviews
a user can access.
P_ RCF _ POOL RCF _ POOL The following ways to access
the candidate pool directly
are available:
Status-Independent Access
to Candidates (DIRECT_ACC)
Recognition of Multiple Appli
cants (DUPL_CHECK)
Maintenance of Candidate
Data ( CAND _MAINT)
Authorization object that
species within SAP E-Re
cruiting which type of direct
access a user can have to the
candidates in the Talent Pool.
P_ RCF _ STAT OTYPE
RCF _ STAT
SAP E-Recruiting objects and
permitted object status
Authorization object that
species within SAP E-Re
cruiting the authorization for
status changes to SAP E-Re
cruiting objects (for example,
candidate, application, candi
dacy).
P_ RCF _ACT ACTVT Add or Create
Change
Delete
Authorization object that
species within SAP E-Re
cruiting which type of access
a user can have to activities.
An activity in SAP E-Recruit
ing is therefore identied
through the assigned proc
ess and through the activity
type.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 267

13.4.5.1.3.4 Candidate
Standard Roles
The table below shows the standard roles that are used by SAP E-Recruiting for candidates .
Standard Roles for Candidate Scenario
Role Description
SAP _ RCF _UNREG_CANDIDATE_CLIENT Unregistered Candidate (Client) (Obsolete)
This role contains the necessary authorizations for unregis
tered candidates/service users that are required on the
front-end system when using a separated system (front-end
and backend on dierent systems).
If you execute unregistered scenarios directly on the back
end system, you must also assign this role to the service
user in the backend system.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_ UNR _ CAND _CLIENT_CI_4.
SAP _ERC_ UNR _ CAND _CLIENT_CI_4 Unregistered Candidate (Client)
SAP _ RCF _UNREG_CANDIDATE_SERVER Unregistered Candidate (Server)
This role provides the necessary authorizations for an un
registered candidate/service user in SAP E-Recruiting that
are required on the backend system when using a separated
system (front-end and backend on dierent systems).
SAP _ RCF _UNREGISTERED_CANDIDATE (Unregistered) Candidate – Service User (Obsolete)
This role provides the necessary authorizations for an un
registered candidate/service user in SAP E-Recruiting that
are required when using the front-end and backend on one
system.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_ UNR _CANDIDATE_CI_4.
SAP _ERC_ UNR _CANDIDATE_CI_4 Unregistered Candidate
268 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Role Description
SAP _ RCF _EXT_CANDIDATE_CLIENT External Candidate (Client) (Obsolete)
This role contains the necessary authorizations for external
candidates that are required on the front-end system when
using a separated system (front-end and backend on dier-
ent systems).
Note
This role is obsolete and has been replaced with the role
SAP _ERC_EXT_ CAND _CLIENT_CI_4.
SAP _ERC_EXT_ CAND _CLIENT_CI_4. External Candidate (Client)
SAP _ RCF _EXT_CANDIDATE_SERVER External Candidate (Server)
This role provides the necessary authorizations for an exter
nal candidate in SAP E-Recruiting that are required on the
backend system when using a separated system (front-end
and backend on dierent systems).
SAP _ RCF _EXTERNAL_CANDIDATE External Candidate (Obsolete)
This role may only display its own data. The role can only see
job postings that you published via publications using the ex
ternal posting channels.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_EXT_CANDIDATE_CI_4.
SAP _ERC_EXT_CANDIDATE_CI_4 External Candidate
SAP _ RCF _ INT _CANDIDATE_CLIENT Internal Candidate (Client) (Obsolete)
This role contains the necessary authorizations for internal
candidates that are required on the front-end system when
using a separated system (front-end and backend on dier-
ent systems).
If you allow internal candidates direct access to the backend
system, you must also assign this role to the reference user
for internal candidates in the backend system.
Note
This role is obsolete and has been replaced with the role
SAP _ERC_ INT _ CAND _CLIENT_CI_4.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 269
Role Description
SAP _ERC_ INT _ CAND _CLIENT_CI_4 Internal Candidate (Client)
SAP _ RCF _ INT _CANDIDATE_SERVER Internal Candidate (Server)
This role provides the necessary authorizations for an inter
nal candidate in SAP E-Recruiting that are required on the
backend system when using a separated system (front-end
and backend on dierent systems).
SAP _ RCF _INTERNAL_CANDIDATE Internal Candidate (Obsolete)
This role may only display its own data. The role can only see
job postings that you published via publications using the in
ternal posting channels.
The role does not have access to the following data:
● Requisition data
● Posting data
● Application data
● Data for the selection process
Note
This role is obsolete and has been replaced with the
role SAP _ERC_ INT _ CAND _CLIENT_CI_4.
SAP _ERC_ INT _ CAND _CLIENT_CI_4 Internal Candidate
SAP _ RCF _ ESS _SR_ERC_CI_4 E-Recruiting Services for ESS (WDA) (Obsolete)
This role contains the authorizations in SAP E-Recruiting for
employees that use E-Recruiting services in ESS WDA (Em
ployee Self-Service Web Dynpro ABAP).
Note
This role is obsolete and has been replaced with the role
SAP _ERC_ INT _ CAND _CLIENT_CI_4.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by SAP E-Recruiting .
For more information, see the documentation for SAP E-Recruiting under Authorizations (Recruitment) .
270
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Standard Authorization Objects
Authorization Object Field Value Description
P_ RCF _APPL RCF _APPL SAP E-Recruiting applica
tions
Authorization object that
species within SAP E-Re
cruiting which SAP E-Recruit
ing applications a user can
call.
The authorization object is
used for the (internal and ex
ternal) candidates' applica
tions.
R_ RCF _VIEW RCF _VIEW SAP E-Recruiting data over
views
Authorization object that
species within SAP E-Re
cruiting which data overviews
a user can access.
P_ RCF _ STAT OTYPE
RCF _ STAT
SAP E-Recruiting objects and
permitted object status
Authorization object that
species within SAP E-Re
cruiting the authorization for
making status changes to
SAP E-Recruiting objects (for
example, candidate, applica
tion, candidacy).
P_ RCF _ACT ACTVT
● Add or Create
● Change
● Delete
Authorization object that
species within SAP E-Re
cruiting which type of access
a user can have to activities.
An activity in SAP E-Recruit
ing is therefore identied
through the assigned proc
ess and through the activity
type.
Additional Standard Authorization Objects when Using Candidate Scenario with Front-end and Backend on Separate
Systems
Authorization Object Field Value Description
S_ RCF ACTTV
RFC_NAME
RFC_TYPE
Authorization object for RFC
access
(For more information, see
the documentation for
Authorization Object
S_RFC .)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 271

Authorization Object Field Value Description
S_RFCALC ACTTV
RFC_CLIENT
RFC_EQUSER
RFC_ INFO
RCF _SYSID
RCF _TCODE
RCF _USER
Authorization check for RFC
users (for example, Trusted
System )
(For more information, see
the documentation for
Authorization Object
S_RFCACL .)
S_ICF ICF_FIELD Internet Communication
Framework Service
Authorization checks for us
ing services in Internet Com
munication Framework
(SICF), for calling remote
function modules using an
RFC destination (SM59), and
for conguring proxy settings
(SICF).
(For more information, see
the documentation for
Authorization Object S_ICF .)
Note
You can use the authori
zation object S_ICF to
safeguard the use of RFC
destinations and access
to individual SICF serv
ices.
13.4.5.1.4 Session Security Protection
Denition
To prevent access in JavaScript or plug-ins to the SAP logon ticket and security session cookies, we
recommend activating secure session management.
We also highly recommend using SSL to protect the network communications where these security-relevant
cookies are transferred.
272
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Session Security Protection on the AS ABAP
To prevent access in JavaScript or plug-ins to the SAP logon ticket and security session cookies
(SAP_SESSIONID_<sid>_<client>), activate Secure Session Management . With an existing security session,
users can then start applications that require a user logon without logging on again. When a security session is
ended, the system also ends all applications that are linked to this security session.
Use the transaction SICF_SESSIONS to specify the following parameter values shown in the table below in your
AB ABAP system:
Session Security Protection Prole Parameters
Prole Parameter Recommended Value Comment
icf/set_HTTPonly_ag_on_cookies 0 Client-dependent
login/ticket_only_by_https 1 Not client-dependent
For more information and detailed instructions, see section Activating HTTP Security Session Management on
AS ABAP in the AS ABAP security documentation.
13.4.5.1.5 Network and Communication Security
Your network infrastructure is extremely important in protecting your system. Your network needs to support
the communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats based on software aws (at both the operating system
and application level) or network attacks such as eavesdropping. If users cannot log on to your application or
database servers at the operating system or database layer, then there is no way for intruders to compromise
the machines and gain access to the backend system’s database or les. Additionally, if users are not able to
connect to the server LAN (local area network), they cannot exploit well-known bugs and security holes in
network services on the server machines.
The network topology for SAP E-Recruiting is based on the topology used by the SAP NetWeaver platform.
Therefore, the security guidelines and recommendations described in the SAP NetWeaver Security Guide also
apply to SAP E-Recruiting. Details that specically apply to SAP E-Recruiting are described in the following
topics:
● Communication Channel Security
This topic describes the communication paths and protocols used by SAP E-Recruiting.
● Network Security
This topic describes the recommended network topology for SAP E-Recruiting. It shows the appropriate
network segments for the various client and server components and where to use rewalls for access
protection. It also includes a list of the ports needed to operate SAP E-Recruiting.
● Communication Destinations
This topic describes the information needed for the various communication paths, for example, which
users are used for which communications.
For more information, see the following sections in the SAP NetWeaver Security Guide:
● Network and Communication Security
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 273
● Security Aspects for Connectivity and Interoperability
13.4.5.1.5.1 Communication Channel Security
Use
The table below shows the communication channels used by SAP E-Recruiting, the protocol used for the
connection, and the type of data transferred.
Communication Paths
Communication Path Protocol Used Type of Data Transferred
Data Requiring Particular
Protection
Front-end client that uses
SAP GUI for Windows as the
application server
DIAG All Customizing data Passwords
Front-end client that uses a
Web browser as the applica
tion server
HTTP, HTTPS
Note
We generally recom
mend using HTTPS
All application data Passwords, personal data
DIAG and RFC connections can be protected using Secure Network Communications (SNC). HTTP connections
are protected using the Secure Sockets Layer (SSL) protocol.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
Printing
SAP E-Recruiting has numerous options for printing contents. For information about security while printing,
see the SNC User's Guide.
274
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.5.1.5.2 Network Security
Denition
You can operate SAP E-Recruiting in dierent ways. You can run the front end and backend for candidates’
users on dierent systems. You can also operate SAP E-Recruiting and the HR system integrated on one
system or on dierent instances.
We recommend that you run the front end and backend of candidates’ users on dierent systems and that you
do not integrate SAP E-Recruiting and the HR system on one system.
Firewall Settings
For more information, see Using Firewall Systems for Access Control in the SAP NetWeaver Security Guide.
Ports
SAP E-Recruiting runs on SAP NetWeaver and uses the ports from AS ABAP. For more information, see the
topics for AS ABAP Ports in the corresponding SAP NetWeaver Security Guides.
For other components, for example, SAPinst, SAProuter, or SAP Web Dispatcher, see https://help.sap.com/
viewer/ports.
13.4.5.1.5.3 Communication Destinations
The following sections provide an overview of the communication destinations that are relevant for the user in
the SAP E-Recruiting roles.
13.4.5.1.5.3.1 Communication Destinations (Recruiter,
Administrator, and Data Entry Clerk)
The following table provides an overview of the communication destinations that SAP E-Recruiting uses.
You use the following communication destinations depending on which application you use to manage your HR
master data:
● If you use the SAP GUI transactions to maintain HR master data (for example, transactions PA*),
communication with SAP E-Recruiting runs via RFC connections.
● If you use the HR Administrative Services application, communication with SAP E-Recruiting runs via SAP
PI (Process Integration).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 275

Destination Delivered Type Users, Authorizations Description
SAP E-Recruiting to
SAP Human Resources
Management
No RFC See Customizing
IMG: SAP E-
Recruiting Applicant
Tracking
Activities
Set Up Data Transfer
for New Employees
From SAP Human Re
sources Management
to SAP E-Recruiting
No RFC See Customizing
SAP E-Recruiting
Technical Settings
SAP ERP Central
Component (ECC)
Integration
Software
Runs on Dierent
Instances Set Up
Data Transfer from SAP
ECC
From SAP E-Recruiting
to TREX
No RFC See Customizing
SAP E-Recruiting
Technical Settings
User Administration
Create Special Users
SAP E-Recruiting
Technical Settings
Search Engine Set
Up Search Engine for E-
Recruiting
From SAP E-Recruiting
to HR Administrative
Services
No XI messages Transfer external can
didate's data when hir
ing
From HR Administra
tive Services to SAP E-
Recruiting
No XI messages Return personnel num
ber of former external
candidate to SAP E-Re
cruiting
Note
Changes to the HR master data are transferred to SAP E-Recruiting using the master data distribution in
the ALE scenario.
276
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.5.1.5.3.2 Communication Destinations for Manager
Involvement
The following table provides an overview of the communication destinations that SAP E-Recruiting uses for
Manager Involvement.
Communication Destinations for Manager Involvement (Manager Self-Service)
Destination Delivered Type Users, Authorizations Description
From HR system (Man
ager Self-Service) to
SAP E-Recruiting
No RFC See Customizing SAP Customizing
Implementation Guide
→ Integration with
Other SAP
Components →
Business Packages /
Functional Packages →
Manager Self Service →
Recruitment → Create
RFC Connection to E-
Recruiting System.
In the HR system, the methods of the CL_IM_HRRCF_REQUI_REQUEST class use the RFC connection to call
function modules in the E-Recruiting system.
The IF_HRASR00 GEN _SERVICE_ADVANCED~FLUSH method transfers information from the requisition
request form to the corresponding infotypes of SAP E-Recruiting.
The methods call the following function modules in the E-Recruiting system:
● HRRCF_MDL_ UIS _ATT_TYPE_ GET
● ERC_SE_REQUI_CREATE_RC
The IF_HRASR00 GEN _SERVICE~ GET _HELP_VALUES method lls the value helps for input elds in the
requisition request form with values from SAP E-Recruiting.
The method calls the following function modules in the E-Recruiting system:
● HRRCF_MDL_ UIS _VH_COMMON
● HRRCF_ GET _MANAGERS_FOR_SUBST
● HRRCF_MDL_VH_EMPLOYMENT_FRACT
● HRRCF_MDL_VH_SALARY_CURRENCY
● HRRCF_MDL_VH_SALARY_RANGE
● HRRCF_MDL_VH_CONTRACT_TYPE
● HRRCF_MDL_ UIS _SUPPORT_GRPS_ GET
The IF_HRASR00 GEN _SERVICE~DO_OPERATIONS method determines the manager's substitutes in SAP E-
Recruiting. In addition, you can use the method to determine a user in SAP E-Recruiting for a personnel
number.
The method calls the following function modules in the E-Recruiting system:
● HRRCF_ GET _MANAGERS_FOR_SUBST
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 277

● HRRCF_MDL_ UIS _USER_ GET
● HRRCF_MDL_ UIS _ASSIGNED_ GRP _GET
13.4.5.1.5.3.3 Communication Destinations (Candidates)
The following table provides an overview of the communication destinations that SAP E-Recruiting uses for the
candidate scenario with the front-end and backend on separate systems.
Destinations Delivered Type Users, Authorizations Description
SAP E-Recruiting
(front-end) to SAP E-
Recruiting (backend)
No RFC See Customizing
SAP E-Recruiting
Technical Settings
User Interfaces
Candidate Frontend
Candidate
Enter RFC
Destination of
Receiving Backend
System
You enter the RFC des
tination as a value of
the
RECFA UI2BL
parameter.
SAP E-Recruiting
(backend) to SAP E-
Recruiting (front-end)
No RFC See Customizing
SAP E-Recruiting
Technical Settings
User Interfaces
Candidate Backend
Candidate
Specify
System Parameters for
Web Dynpro
You enter the RFC des
tination as a value of
the
RECFA BL2UI
parameter.
Note that the communication destination "SAP E-Recruiting (front-end) to SAP E-Recruiting (backend)" was
dened as a "trusted system connection". In this connection, no users can be stored in the credentials. For
more information, see consulting note 1017866.
278
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.5.1.6 Internet Communication Framework Security
You should only activate those services that are needed for the applications running in your system. For SAP E-
Recruiting, the following services are needed for the relevant roles:
● Administrator and Recruiter
○ All services with the prex ERC in the path /default_host/sap/bc/webdynpro/sap/
You activate the services in Customizing for SAP E-Recruiting under Technical Settings → User
Interfaces → Administrator and Recruiter → General Settings → Determine E-Recruiting Services.
● Candidates
○ All services with the prex hrrcf in the path /default_host/sap/bc/webdynpro/sap/
○ All services in the path /default_host/sap/bc/erecruiting/
○ All services with the prex hrrcf_wd in the path /default_host/sap/bc/bsp/sap/
You activate the services in Customizing for SAP E-Recruiting under Technical Settings → User
Interfaces → Candidate → Front-End Candidate → Specify E-Recruiting Services (Web Dynpro ABAP).
● Manager (within the framework of Manager Involvement)
○ default_host/sap/bc/erecruiting/dataoverview
○ default_host/sap/bc/webdynpro/sap/hrrcf_a_dataoverview
○ default_host/sap/bc/webdynpro/sap/hrrcf_a_requi_monitor
○ default_host/sap/bc/webdynpro/sap/hrrcf_a_req_assess
○ default_host/sap/bc/webdynpro/sap/hrrcf_a_tp_assess
○ default_host/sap/bc/webdynpro/sap/hrrcf_a_qa_mss
○ default_host/sap/bc/webdynpro/sap/hrrcf_a_substitution_manager
○ default_host/sap/bc/webdynpro/sap/hrrcf_a_substitution_admin
You activate the services in Customizing for SAP E-Recruiting under Technical Settings → User
Interfaces → Manager Involvement → Specify E-Recruiting Services for MSS.
If your rewall(s) use(s) URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information, see Activating and Deactivating ICF Services in the SAP NetWeaver documentation in
SAP Library.
For more information about ICF security, see the RFC/ICF Security Guide
13.4.5.1.7 Data Storage Security
Data Storage
The SAP E-Recruiting data is saved as follows:
● If you use SAP E-Recruiting integrated with other SAP applications, the data is saved in the SAP Web AS or
SAP ECC databases.
● If you use SAP E-Recruiting as a standalone application, the data is saved directly in the SAP E-Recruiting
databases. You do not need to use any other databases in addition to these standard databases.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 279

SAP E-Recruiting stores the data in the following locations:
Data Storage Location
Master data PD infotype tables
Attachments and user-dened texts Knowledge Provider (KPro)
Search query logs Cluster table PCL _ RCF (SI)
Audit Trails Cluster table PCL _ RCF (SI)
Infotype Log Cluster table PCI_ RCF (IL)
Cookies
The application uses a Web browser. The SAP Web AS must issue cookies as well as accepting them.
13.4.5.1.8 Enterprise Services Security
The following chapters in the SAP NetWeaver Security Guide and documentation are relevant for all enterprise
services delivered with SAP E-Recruiting:
● Security Guide Web Services
● Recommended WS Security Scenarios
● SAP Process Integration Security Guide
13.4.5.1.9 Other Security-Relevant Information
Virus scan when uploading attachments
SAP E-Recruiting allows the user to upload les as attachments at various times in the program. Since
attachments can potentially contain viruses, these viruses could enter your system when you upload the
attachments. To reduce this risk as much as possible, we recommend you use an external virus scanner and
restrict the MIME types of the attachments.
In the Virus Scan when Uploading Documents Customizing activity, you activate the virus scan prole /PAOC_
RCF _BL/HTTP_UPLOAD that you use in SAP E-Recruiting to perform a virus check when uploading
attachments. This enables you to include external virus scanners to increase the security of your system.
You can use the Business Add-In (BAdI) HRRCF00_ DOC _UPLOAD to check les that are uploaded as
attachments to the E-Recruiting system. When doing so, you can use the CHECK_ATTACH_ FILE _TYPE
method to specify which MIME types are permitted for the attachments. You call the BAdI using the BAdI:
Upload Documents Customizing activity.
280
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Access to attachments via Microsoft Internet Explorer
You use Microsoft Internet Explorer and want to display attachments in the browser. To do this, Microsoft
Internet Explorer checks the content of the attachment to determine the le type and display the attachment
correctly (
MIME Type Sning). In the worst case, it is thus possible that damaging les of an undesired le type
are displayed in the browser or cause damage in another way. To avoid this potential threat to security, deselect
MIME Type Sning in the security settings of Microsoft Internet Explorer.
13.4.5.1.10 Security-Relevant Logging and Tracing
Application Log
SAP E-Recruiting uses the logging and tracing mechanisms from SAP NetWeaver. SAP E-Recruiting then writes
exceptions in the Application Log. These exceptions can occur due to failed authorization checks, for example,
and are therefore relevant for security.
For information about logging and tracing mechanisms of SAP NetWeaver Application Server (ABAP), see
Auditing and Logging under Application Logging, there is more information about the application log.
You can access the part of the application log specic to SAP E-Recruiting by using the transaction SLG1
(Analyze Application Log) and entering the parameter Object = HRRCF .
Audit Trail
SAP E-Recruiting creates an audit trail with the candidate prole and search queries. For more information, see
Access Audit Trails.
13.4.5.1.11 Services in Lifecycle Management for Security
The following services are available from SAP Active Global Support to assist you in maintaining security in
your SAP systems on an ongoing basis.
Security Chapter in the EarlyWatch Alert (EWA) Report
This service regularly monitors the Security chapter in the EarlyWatch Alert report of your system. It tells you:
● Whether SAP Security Notes have been identied as missing on your system.
In this case, analyze and implement the identied Notes, if possible. If you cannot implement the Notes,
the report should be able to help you decide on how to handle the individual cases.
● Whether an accumulation of critical basis authorizations has been identied.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 281

In this case, verify whether the accumulation of critical basis authorizations is okay for your system. If not,
correct the situation. If you consider the situation okay, you should still check for any signicant changes
compared to former EWA reports.
● Whether standard users with default passwords have been identied on your system.
In this case, change the corresponding passwords to non-default values.
Security Optimization Service (SOS)
The Security Optimization Service can be used for a more thorough security analysis of your system, including:
● Critical authorizations in detail
● Security-relevant conguration parameters
● Critical users
● Missing security patches
This service is available as a self-service within the SAP Solution Manager or as a remote or on-site service. We
recommend you use it regularly (for example, once a year) and in particular after signicant system changes or
in preparation for a system audit.
Security Conguration Validation
The Security Conguration Validation can be used to continuously monitor a system landscape for compliance
with predened settings, for example, from your company-specic SAP Security Policy. This primarily covers
conguration parameters, but it also covers critical security properties like the existence of a non-trivial
Gateway conguration or making sure standard users do not have default passwords.
Security in the RunSAP Methodology / Secure Operations Standard
With the E2E Solution Operations Standard Security service, a best practice recommendation is available on
how to operate SAP systems and landscapes in a secure manner. It guides you through the most important
security operation areas and links to detailed security information from SAP’s knowledge base wherever
appropriate.
More Information
For more information about these services, see:
● SAP EarlyWatch Alert: https://support.sap.com/en/oerings-programs/support-services/earlywatch-
alert.html
● SAP Security Optimization Service / Security Notes Report: https://support.sap.com/en/oerings-
programs/support-services/security-optimization-services-portfolio.html
282
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

● Comprehensive list of SAP Security Notes: https://support.sap.com/en/my-support/knowledge-base/
security-notes-news.html
● Conguration Validation
● SAP Activate Methodology Roadmaps: https://support.sap.com/en/oerings-programs/methodologies/
implement.html
13.4.5.2 Performance Management
About This Chapter
This chapter of the Security Guide provides an overview of the security-relevant information for the
Performance Management (PA-PD-PM) application component.
Note
We use the name of the Performance Management to mean the same as the name Objective Setting and
Appraisals. Both names correspond to the technical application component ID PA-PD-PM.
Overview of the Main Sections of This Chapter
The following sections contain the security-relevant information that is specic to “Performance
Management”:
● Important SAP Notes
This section provides information on why security is necessary and how the document is used, as well as
references to other Security Guides on which this Security Guide is based.
● Security Aspects for Data, Data Flow, and Processes
This section provides an overview of the security aspects of the most frequently used processes in
Performance Management.
● Authorizations
This section provides an overview of the authorization concept used for Performance Management.
● Network and Communication Security
This section provides an overview of the following aspects:
○ Communication Channel Security
○ Network Security
● Internet Communication Framework Security
This section provides an overview of the services for the Internet Communication Framework (ICF) used by
Performance Management.
● Data Storage Security
This section provides an overview of all critical data used by the scenario, component, and application as
well as the security mechanisms used.
● Other Security-Relevant Information
This section contains information on uploading and displaying attachments.
● Security-Relevant Logging and Tracing
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 283
This section provides an overview of the trace and log les that contain security-relevant information and
that enable you to reproduce activities, for example, if there is a security violation.
13.4.5.2.1 Technical System Landscape
Overview of the technical system landscape for Performance Management:
● Front-end system: Web Dynpro for ABAP in applications in Manager Self-Service and Employee Self-
Service
● Back-end system: Customizing for the Objective Setting and Appraisals application component (for
example, Customizing for applications using Web Dynpro technology for ABAP).
● Back-end system: Transactions for administrators and HR specialists
● Download of Documents from the Back-End System in Knowledge Provider (KPRo)
● Workow
Example: Sending notications to mangers or employees
● SAP Interactive Forms by Adobe
For oine processing of the appraisal document (downloading and uploading of appraisal documents).
For more information, see the guide for SAP Interactive Forms by Adobe under SAP Interactive Forms by
Adobe Security Guide.
● Printing of Appraisal Documents
○ SAP Smart Forms
○ PDF-based print form
13.4.5.2.2 Security Aspects for Data, Data Flow, and
Processes
In Performance Management, data for the appraisal process are processed as follows:
● For Managers in the Manager Self-Service applications.
For more information about the Manager role, see the SAP S/4HANA Security Guide and choose:
Human Resources Self-Services Manager Self-Service .
● For Employees in the Employee Self-Service applications.
For more information about the Employee role, see the SAP S/4HANA Security Guide and choose
Human Resources Self-Services Employee Self-Service .
Example
Managers as well as employees can work on appraisal documents in the applications (Web Dynpro for
ABAP). The system saves the relevant data to the database. The system saves attachments to les (such
as appraisals by an additional appraiser) in the Knowledge Provider (KPro).
284
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.4.5.2.3 Authorizations
Performance Management uses the authorization concept provided by SAP NetWeaver Application Server for
ABAP (AS ABAP). Therefore, the security recommendations and guidelines for authorizations detailed in the
SAP NetWeaver Security Guide ABAP also apply to Performance Management.
The SAP NetWeaver authorization concept is based on the assignment of authorization to users based on role.
For role maintenance, use the prole generator (transaction: Role Maintenance (PFCG)) on the SAP NetWeaver
AS for ABAP.
Note
For more information about creating roles, see Role Maintenance under Identity Management.
Authorizations for personnel appraisal implemented in Human Resources have a special signicance. The
Performance Management application component uses objects from the following components, among others:
● Manager Self-Service
For more information, see Authorizations in Manager Self-Service.
● Employee Self-Service
For more information, see Authorizations in Employee Self-Service.
● Organizational Management
● Personnel Development
● Training and Event Management
● SAP Learning Solution
For more information, see Authorizations in SAP Learning Solution.
The Performance Management application component is therefore subject to the general authorization checks
in the corresponding application component. Furthermore, the object type Person (P) in Performance
Management is of central importance since this object type can be used for appraisers and appraisees
(particularly for personnel appraisals). This means that standard checks for people in the SAP system are also
valid for Performance Management. Furthermore, Performance Management has additional authorization
aspects for controlling authorizations in this application that are realized using specic authorization object
and authorization controlling in the Customizing settings for the appraisal template.
For more information about the authorization checks, see General Authorization Check and Structural
Authorization Check (see SAP Library for SAP S/4HANA and choose Human Resources HR Tools
Authorizations for Human Resources ).
13.4.5.2.3.1 SAP Standard Roles
The following SAP standard roles are used in Performance Management:
PFCG roles for the exible appraisal process
● SAP_HR_HAP_PMG_ADMIN_SR - Administrator
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 285
The authorizations for this role include the following:
○ Applications based on Web Dynpro technology for ABAP, such as Congure User Interfaces for
Template (HAP_CONFIGURATION)
○ Transactions (for example, administrator functions (PHAP_ADMIN_PA), appraisal catalog
(PHAP_CATALOG_PA), Change Appraisal (PHAP_CHANGE_PA), Transport Appraisal Template
(PHAP_TRANSPORT))
● SAP_HR_HAP_PMG_MANAGER_SR - Manager
For example, this role contains the authorizations for applications based on Web Dynpro technology for
ABAP:
○ Appraisal Document (HAP_MAIN_DOCUMENT)
○ Employee Document Overview (HAP_START_PAGE_POWL_UI_MSS)
○ Application based on Web Dynpro technology for ABAP: Creation and Cascading of Team Goals
(HAP_A_PMP_GOALS)
● SAP_HR_HAP_PMG_EMPLOYEE_SR - Employee
For example, this role for employees contains the authorization for applications based on Web Dynpro
technology for ABAP:
○ Appraisal Document (HAP_MAIN_DOCUMENT)
○ Employee Document Overview (HAP_START_PAGE_POWL_UI_ESS)
● SAP_HR_HAP_PMG_GOALS_SR - Specialist for Corporate Goals
This role for applications based on Web Dynpro technology for ABAP contains authorization for the
following: Creation and Cascading of Corporate Goals and Core Values (HAP_A_PMP_GOALS)
PFCG roles for the Predened Performance Management Process
● SAP_HR_HAP_PMP_ADMIN_SR - Administrator
The authorizations for this role include the following:
○ Applications based on Web Dynpro technology for ABAP (such as the creation wizard for appraisal
templates (HAP_A_TM_CONF), Edit Performance Management Process (HAP_A_PMP_TIMELINE))
○ Transactions (for example, administrator functions (PHAP_ADMIN_PA), appraisal catalog
(PHAP_CATALOG_PA), Change Appraisal (PHAP_CHANGE_PA), Transport Appraisal Template
(PHAP_TRANSPORT))
● SAP_HR_HAP_PMP_MANAGER_SR - Manager
For example, this role for managers contains the authorizations for applications based on Web Dynpro
technology for ABAP:
○ Appraisal Document (HAP_A_PMP_MAIN)
○ Employee Document Overview (HAP_A_PMP_OVERVIEW)
○ Application based on Web Dynpro technology for ABAP: Creation and Cascading of Team Goals
(HAP_A_PMP_OVERVIEW)
● SAP_HR_HAP_PMP_EMPLOYEE_SR - Employee
For example, this role for employees contains the authorization for applications based on Web Dynpro
technology for ABAP:
○ Appraisal Document (HAP_A_PMP_MAIN)
○ Employee Document Overview (HAP_A_PMP_EMPLOYEE)
● SAP_HR_HAP_PMP_GOALS_SR - Specialist for Corporate Goals
This role for applications based on Web Dynpro technology for ABAP contains authorization for the
following: Creation and Cascading of Corporate Goals and Core Values (HAP_A_PMP_GOALS)
286
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Additional PFCG Roles
Note
The following roles are also available in the system: In place of these roles, we recommend you use the roles
listed above.
● SAP_HR_HAP_ADMINISTRATOR
(Administrator – Appraisals and objective setting agreements)
● SAP_HR_HAP_MANAGER
(Manager Flexible – Appraisals and objective setting agreements)
● SAP_HR_HAP_EMPLOYEE
(Employee Flexible – Appraisals and objective setting agreements)
Caution
You can call standard roles with the role maintenance transaction (PFCG). You must copy these standard
roles into a customer-specic namespace for custom implementation to get custom specications for the
roles. When you enter a new name, note that it may not contain an SAP-specic name (SAP, "_"). This is to
ensure that a clear distinction can be made between customer-specic roles and standard SAP roles.
13.4.5.2.3.2 Overview of Authorization Objects
In Performance Management, the following authorization objects are essential for enabling users to access the
application component for the following roles:
● Transaction authorizations (S_TCODE, P_TCODE)
● Access to HR master data (P_ORGIN/CON, P_PERNR)
● Access to objects in the Personnel Planning database (PLOG)
● Access to appraisals (P_HAP_DOC)
You can control the following for users with named roles using various authorization object elds:
● Activity (display, edit, delete)
● Object set (persons, appraisal templates)
● Content (infotypes)
For more information about these authorizations, see SAP Library under ERP Central Component Human
Resources
Personnel Management Personnel Administration Technical Processes in Personnel
Administration Authorizations for Human Resources .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 287

13.4.5.2.3.2.1 Authorization Objects S_TCODE and P_TCODE
Authorization object that is used to check whether a user is authorized to start the dierent HR transactions.
The transaction code is checked.
Use
Regardless of the application, the authorization object S_TCODE is used to check authorizations for starting
the transactions dened for an application.
The authorization object P_TCODE is used to check the authorization for starting various HR transactions. The
additional check using P_TCODE provides added security for personal data and is therefore used for numerous
transactions in HCM applications (such as PA40, PHAP_CHANGE_PA). The authorization object P_TCODE is
not used in all HR transactions. Generally, it is used in HR applications where HR-specic authorization objects
are not checked when a transaction is called. For more information about this authorization object, see
P_TCODE (HR transaction code) .
Necessary Setting for Performance Management:
Transaction code eld: PHAP_*_PA (depending on role, specify exact transaction). For administrators, you
must include transactions starting with OOHAP_*.
For more information about the authorizations, see SAP Library under ERP Central Component Human
Resources Management Personnel Management Personnel Administration Technical Processes in
Personnel Administration
Authorizations for Human Resources Management .
13.4.5.2.3.2.2 Authorization object PLOG (Personnel
Planning)
An authorization object that is used to check the authorization for specic elds in the Personnel Management
components (Organizational Management, Personnel Development, Training and Event Management, SAP
Learning Solution, and so on).
Use
Necessary Setting for Performance Management:
INFOTYP: 1000, 1001, 1002, 1048, 5020, 5021, 5022, 5023, 5024, 5025, 5026
288
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

ISTAT: 4, 3
OTYPE: VA, VB, VC
PLVAR: *
PPFCODE: Change for Customizing/Administrators, Display for End-Users
SUBTYP: 0001, 5020, A605, A606, A607, B605, B606, B607
Note
The object types have the following meaning:
● VA = Appraisal template
● VB = Criteria group
● VC = Criterion
The Customizing settings for the appraisal templates are made in the aforementioned infotypes (transaction
PHAP_CATALOG_PA). Therefore, end users must have at least read authorization for these infotypes. If the
appraisal templates include further object types as a result of using free enhancements (such as Add Business
Event Type) or xed enhancements (such as Add Individual Development Plan Item), additional authorizations
are required for these object types, for example:
● Q = Qualications
● O = Organizational unit
● S = Position
● C = Job
● D = Course type
● F = Location
● A = Work center
Since individual development plans can also include further standard object types and customer-specic
object types, you must also include these when setting up authorizations according to the particular
implementation.
For more information on the authorizations, see the SAP Library under ERP Central Component Human
Resources Management
Personnel Management Personnel Administration Technical Processes in
Personnel Administration Authorizations for Human Resources Management .
13.4.5.2.3.2.3 Authorization Object P_HAP_DOC
An authorization object used to check authorizations for accessing appraisal documents.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 289

Use
Among other things, the distribution of authorization for appraisal templates and appraisal documents is
controlled using this authorization object. For more information about this authorization object, see
P_HAP_DOC (Appraisal Systems: Appraisal). The P_HAP_DOC authorization object contains the following
elds, which are tested during an authorization check:
Authorization Field Description
ACTVT Activity (display, change, delete)
PLVAR Plan version (usually active plan version 01)
HAP_CAT_G Appraisal category group ID (determines the appraisal cate
gory groups that a user can access). The appraisal category
groups are contained in table T77HAP_C_GRP (process us
ing transaction OOHAP_CAT_GROUP). For personnel ap
praisals, use category group 00000001 (see also SAP Note
number 497773).
HAP_CAT Appraisal category ID (determines the appraisal categories
that a user can access). Appraisal categories are customer-
specic and created in transaction PHAP_CATALOG_PA.
They are saved in table T77HAP_C. You can display the num
bering of the categories using transaction OOHAP_CATE
GORY.
HAP_TEMPL The appraisal template ID. An appraisal template is cus
tomer-specic and created in transaction PHAP_CATA
LOG_PA. It is an object of type VA. In this eld, enter the
eight-digit object ID from table HRP1000 of object type VA.
This dictates the appraisal templates a user can access.
PROFL Authorization prole. This eld is only used if structural au
thorizations are used. (See Structural Authorizations in Per
formance Management).
Necessary Settings for PM:
ACTVT: *
PLVAR: *
HAP_CAT_G: 00000001 (for personnel appraisals)
HAP_CAT:* HAP_TEMPL:* (restrict by customer if necessary)
PROFL: *
Note
You should not assign the authorization object P_HAP_DOC on its own since it is only eective when used in
combination with other authorization objects. You must assign it together with the authorization objects PLOG
and P_ORGIN(CON). The authorization object PLOG enables users to access appraisal templates and the
290
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

criteria they contain (see Authorization Object PLOG [page 288]). The authorization object P_ORGIN(CON)
enables users to access HR data (see Authorization Object P_ORGIN / P_ORGINCON). The authorization
object P_PERNR is also required to enable users to access their own HR master data (for example, for ESS
scenarios) (see Authorization Object P_PERNR).
For more information about the authorizations, see SAP Library under ERP Central Component Human
Resources Management Personnel Management Personnel Administration Technical Processes in
Personnel Administration
Authorizations for Human Resources Management .
13.4.5.2.3.2.4 Authorization Objects P_ORGIN
An authorization object used to check the authorization for accessing HR master data.
Use
The checks are run when HR infotypes have to be processed or read. In Performance Management, the persons
for whom the user is allowed to process appraisal documents must be authorized via authorization object
P_ORGIN. The authorization check is run here using the following elds:
Authorization Field Description
INFT Infotype
SUBTY Subtype
AUTHC Authorization level (such as read, write, matchcode)
PERSA Personnel area (from infotype 0001)
PERSG Employee group (from infotype 0001)
PERSK Employee subgroup (from infotype 0001)
VDSK1 Organizational key (from infotype 0001)
Necessary Settings for Performance Management:
INFTY: Usually, 0000, 0001, 0002 (depending on the organizational area for which the user is responsible)
SUBTY: *
AUTHC: Read and matchcode
PERSA: (depending on the organizational area for which the user is responsible)
PERSG: (depending on the organizational area for which the user is responsible)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 291

PERSK: (depending on the organizational area for which the user is responsible)
VDSK1: (depending on the organizational area for which the user is responsible)
Note
The authorization object P_ORGIN provides the user with the necessary authorizations he or she needs to
access personnel data. This authorization object is mandatory, that is, you cannot dene the use of this
authorization object as being optional by activating the structural authorizations in Performance Management
(table T77S0, switch HAP00/AUTHO). Rather, the structural authorizations comprise an additional lter for
accessing appraisal documents for the permitted set of persons (see Structural Authorizations in Performance
Management [page 294]). To assign authorizations for accessing infotypes in the authorization object
P_ORGIN, you do not need to assign specic infotypes in Performance Management. From a technical
perspective, it is sucient in Performance Management if a person is included in the elds PERSA, PERSG,
PERSK, VDSK1 in the permitted amount. However, to ensure consistency for the user (for example, in the
display of additional personal data in the appraisal document, in the search function for persons with particular
infotype values for lling out selection criteria in Performance Management) it is generally benecial to provide
the user with authorizations for the Actions (0000), Organizational Assignment (0001), and Personal Data
(0002) infotypes for the persons for whom the user is to process appraisal documents. It should not be
necessary that a user is able to process a person’s appraisal document but not read this person’s
organizational assignment. Such a requirement is not logical from the perspective of the process.
For more information on the authorizations, see the SAP Library under ERP Central Component Human
Resources Management Personnel Management Personnel Administration Technical Processes in
Personnel Administration
Authorizations for Human Resources Management .
13.4.5.2.3.2.5 Authorization Object P_ORGINCON
An authorization object that is used during the authorization check for HR data. This check takes place when
HR infotypes are edited or read.
Use
You can use this authorization object if structural authorizations are to be checked in context when checking
the authorization to access HR master data. This authorization object is used for the authorization check for
personnel data. This check takes place when HR infotypes are edited or read. This authorization object
consists of the same elds as the authorization object P_ORGIN, and also includes the eld PROFL (structural
prole). Running the check against this object enables user-specic contexts (using Organizational
Management) to be depicted in HR master data.
292
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
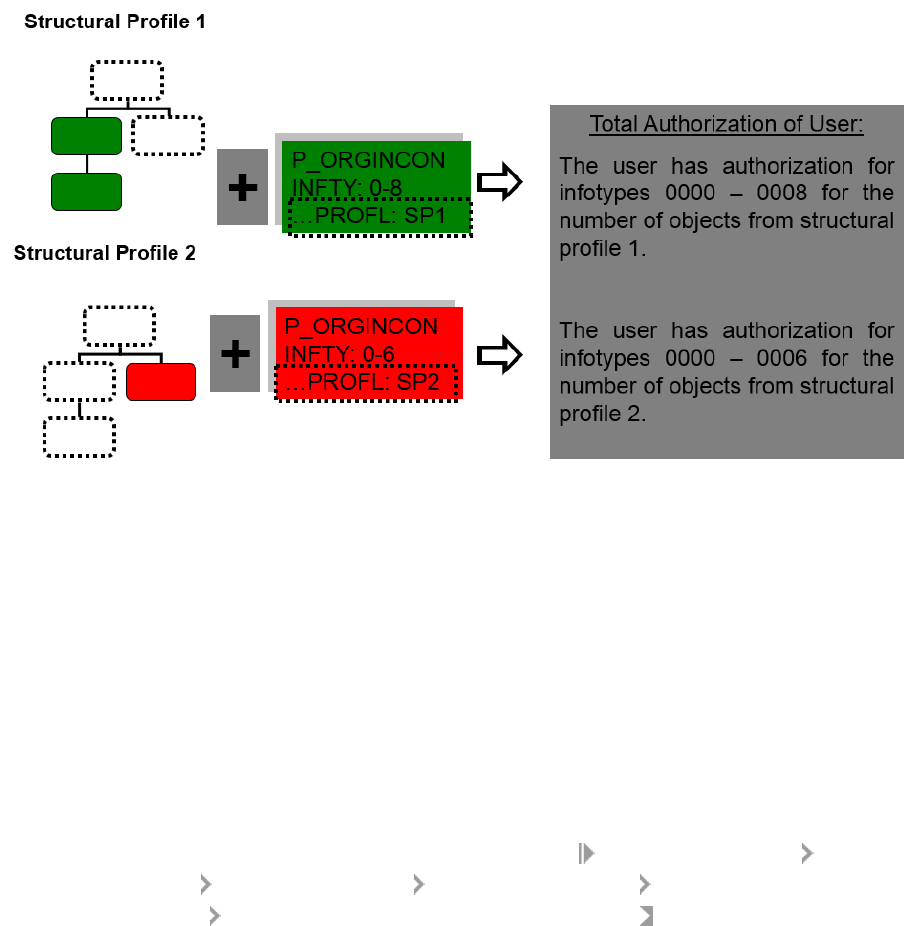
Example for context-sensitive authorization checks
The checks are made context-sensitive by controlling the various structural sets of persons to dierent
contexts as shown in the example above.
The PROFL eld determines the structural proles the user can access for a particular context. These
structural proles must be assigned to the user in table T77UA.
If you use the Business Add-In (BAdI) HRBAS00_GET_PROFL, you do not need to maintain table T77UA
manually. This BAdI enables you to implement an alternative method for determining structural proles. The
example source code in the standard system determines the user’s structural proles by reading the values
entered for the authorization object P_ORGINCON in the user master record.
Structural authorizations in authorization object P_ORGINCON can also be used in combination with structural
authorizations in Performance Management (see structural authorizations in Performance Management).
For more information on the authorizations, see the SAP Library under ERP Central Component Human
Resources Management Personnel Management Personnel Administration Technical Processes in
Personnel Administration
Authorizations for Human Resources Management .
13.4.5.2.3.2.6 Authorization Object P_PERNR
This authorization object is used to control the user’s access to his or her own personnel number and the
related HR data separately.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 293
Use
The personnel number is assigned to the user in the Communication infotype (0105) (subtype 0001 System
User Name). Access to an employee’s own master data is used primarily in ESS scenarios in which the user is
only to have access to his or her own master data to edit or display this information. To enable access
authorizations for the employee’s own personnel number to be controlled using the authorization object
P_PERNR, the main switch must be activated in table T77S0 (transaction OOAC, switch AUTSW/PERNR). The
authorization check is run for the following elds:
Authorization Field Description
INFTY Infotype
SUBTY Subtype
AUTHC Authorization level (such as read, write, matchcode)
PSIGN Interpretation of own personnel number (I, include own per
sonnel number, E, exclude own personnel number)
Necessary Settings for Performance Management:
INFTY: Dummy–depends on the ESS scenarios used outside of Performance Management.
SUBTY: Dummy–depends on the ESS scenarios used outside of Performance Management.
AUTHC: *
PSIGN: I (include)
Note
If you use the authorization object P_PERNR, the authorization object P_ORGIN/CON is superuous. That is, a
user who is to be permitted to access his or her own personnel number only (for example, for ESS scenarios),
is given all the authorizations required using the authorization object P_PERNR. Therefore, an additional
setting for the authorization object P_ORGIN/CON is not required. This also applies to Performance
Management.
For more information on the authorizations, see the SAP Library under ERP Central Component Human
Resources Management Personnel Management Personnel Administration Technical Processes in
Personnel Administration Authorizations for Human Resources Management .
13.4.5.2.3.3 Structural Authorizations in Performance
Management
Special structural authorizations exist for Performance Management. These authorizations enable you to
control access to appraisal documents for persons from dened areas of Organizational Management.
This extended authorization check (structural, context-sensitive authorizations) is activated using the switch
HAP00/AUTHO in table T77S0. This switch is specic to Performance Management authorizations.
294
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Example
Example A: Structurally controlled access
The standard SAP authorization check assumes that, once dened, the authorizations (such as change
appraisal documents) for a user always apply even when a manager takes on a substituting role for a
dierent organizational unit. If you activate the extended authorization check, you can dictate that a
manager can change appraisal documents for employees in his or her organizational unit while he or she
can only display appraisal documents for employees in the organizational unit for which he or she is a
substitute.
Example
Example B: Structurally controlled access
A user has authorization to read the mini-master record for all employees at a company (P_ORGINCON for
infotypes 0000, 0001, 0002 for structural prole A, which is valid for the entire company). This user can
maintain simultaneously all infotypes for the employees in his or area of responsibility, displayed via a link
between his or her position and the organizational unit for which the user is a substitute (P_ORGINCON for
all infotypes for a structural prole B that is valid for the entire area of responsibility). You can use the
authorization object P_HAP_DOC to enable the user to display and change the appraisal documents for
employees in his or her area of responsibility (structural prole B) and to specify that the user cannot
display or change the appraisal documents for employees with structural prole A.
Example
Example C: Structurally and context-sensitively controlled access
A user has the structural proles outlined in example B.
● Structural prole A for access across whole company
● Structural prole B for area of responsibility
You can also use the authorization object P_HAP_DOC to create a context-sensitive reference to the
permitted templates. This means the user can see appraisals from a certain appraisal template, such as
qualication checklists, for structural prole A, that is, company-wide. By dening a further setting for the
authorization object P_HAP_DOC, you can give the user authorization to access all appraisal templates
(such as objective setting agreements, assessments of potential, performance appraisals) that exist in his
or her area of responsibility (structural prole B) for the same user.
For more information about structural authorizations, see SAP Library under ERP Central Component
Human Resources Personnel Management Personnel Administration Technical Processes in Personnel
Administration
Authorizations for Human Resources .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 295

13.4.5.2.3.3.1 Activating HAP00/AUTHO and Using PA
Infotype Authorizations (P_ORGIN) without
Structural Authorizations
This combination means that structural restrictions are made during authorization checks only for
Performance Management and the associated access to personnel appraisals. This is opposed to Personnel
Administration, where no structural authorization checks are used.
This means that when HAP00/AUTHO is active, a structural prole must be entered in the authorization object
P_HAP_DOC and the user must be entered together with this structural prole in table T77UA.
If, in this authorization object, the value * remains in the Authorization Prole eld and the user has not been
entered in table T77UA, the system interprets this value as structural prole ALL. That is, the user has the
authorizations to access the same employee data as dened in the authorization object P_ORGIN. If no value,
or an invalid value, is entered in the
Authorization Prole eld for the authorization object P_HAP_DOC, the user
cannot access any personnel appraisals (he or she can, however, access the corresponding infotypes in
Personnel Administration).
Access using structural authorizations is only possible in Performance Management when a structural prole
has been entered in the authorization object P_HAP_DOC and the user in entered in table T77UA has a valid
entry for this structural prole.
If this is the case, the structural authorizations function as follows:
● Filter Function
Example
In Personnel Administration, a user has authorization for all employees in employee subgroup AT
Employees. However, the user is to be able to display and process appraisal documents only for those
AT employees who are in his or her area of responsibility. To enable this, the structural prole for the
user’s area of responsibility is entered in the authorization object P_HAP_DOC.
Explanation
The user can only access the personnel appraisals for persons included in his or her structural prole.
You can report on the object that can be accessed using the report RHUSERRELATIONS (up to Release
4.7) or using table T77UA (as of the Enterprise Release, using the Display Objects function).
This means that structural authorizations for Performance Management work like a lter for people
authorized by P_ORGIN: Users can see and process a certain number of people in Personnel
Administration via authorization object P_ORGIN. The user can display and maintain only those
appraisal documents for persons who are ALSO included in the structural prole of the authorization
object P_HAP_DOC (lter/subset).
● Context Sensitivity
Example
For persons in area A, a user is to be able to view and/or edit the appraisal template A, Objective Setting
Agreements, only. For persons in area B, the user is to be able to view and/or edit the appraisal
template B, Qualication Appraisals, only. This means that the user is not able to show or process the B
appraisals, or Qualication Appraisals, for employees from area A.
296
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

The role requires two instances of the authorization object P_HAP_DOC that dier in the following
elds:
Appraisal Template Field Authorization Prole Field
1st Prociency Template A: Objective Setting Agree
ments
Structural Prole A: Area A
2nd Prociency Template B: Qualication Appraisals Structural Prole B: Area B
Explanation
A distinction is made between the user's authorizations so that he or she can access dierent appraisal
templates and perform dierent activities in appraisal templates for the various areas in Organizational
Management (context sensitive).
Using report RHUSERRELATIONS (up to Release 4.7) or in table T77UA (as of Enterprise Release,
Display Objects function) you can determine the combination of structural proles possible for the user
(that is, for which persons he or she can access a particular appraisal template and perform specic
activities for this appraisal template).
13.4.5.2.3.3.2 Activating HAP00/AUTHO and Using
P_ORGINCON (with Structural HR
Authorizations)
This setting means that structural authorizations are used to control access to HR master data and personnel
appraisals in Performance Management.
To use the authorization object P_ORGINCON, activate the switch AUTSW/INCON in table T77S0.
You must also enter a structural prole in the authorization object P_ORGINCON and P_HAP_DOC.
The user requires a structural prole for all other object types in Organizational Management that do not
belong to Performance Management but for which the user nevertheless has authorization using the
authorization object PLOG.
In this combination, authorizations between HR master data and appraisals generally work in the same way as
described in Structural Authorizations in Performance Management [page 294]. In addition, further context-
sensitive authorization checks (in combination with structural proles from Organizational Management) are
possible.
If you use both structural, context-sensitive authorization objects P_ORGINCON and P_HAP_DOC, note the
following:
● It is not sucient to give the user a structural prole using authorization object P_HAP_DOC. To enable the
user to access employee master data, you must also make a setting for the authorization object
P_ORGINCON [page 292] (see also Authorization Object P_HAP_DOC [page 289]).
● You can give the user authorization to access a broader range of HR master data compared with appraisal
documents.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 297

Example
In the prole for P_ORGINCON, a user can access the infotypes 0000, 0001, 0002 for all employees at
the company who belong to the employee subgroup AT. The structural prole ALL in the authorization
object P_ORGINCON (structural prole A) provides the user with this authorization. The user also has a
further instance of the authorization object P_ORGINCON that permits him or her to maintain all
infotypes for employees in his or her area of responsibility (structural prole B for dening the area of
responsibility in Organizational Management).
In the user prole for the authorization object P_HAP_DOC, the user is given authorization to access
appraisal documents for employees in his or her area of responsibility (structural prole B) as opposed
to for the entire company, 'ALL' prole (structural prole A). This ensures that the user can access the
appraisal documents for employees in his or her area of responsibility but not the appraisal documents
for employees who belong to the employee subgroup AT, which is valid for the whole company.
● If you use the BAdI HRBAS00_GET_PROFL as opposed to maintaining table T77UA manually (see also
Authorization Object P_ORGINCON [page 292]), note that you must also consider the structural proles
from the authorization object P_HAP_DOC.
13.4.5.2.3.4 Controlling Authorizations and Access Using
Customizing
The following infotypes are displayed in the form of tab pages and control authorization and access:
● Column Access
● Processing
● Roles
13.4.5.2.3.4.1 Tab: Column Access (Infotype 5023)
On this tab page, you make the settings for access to columns within the (part) appraisal process. You specify
display and change authorizations for elements in the appraisal template. You make the following settings:
● You specify the column owner of each separate column group.
You can use an implementation of the BAdI HRHAP00_COL_OWNER to implement customer-specic
column access.
● You specify who is authorized to perform which activities in each phase of the appraisal process and which
columns are to be shown in the appraisal template.
You can only assign authorizations that are dependent on the various phases to either the column owner or all
other participants involved in the appraisal process. You dene who has authorization to execute an activity in a
particular phase separately for column owners and all other participants. You can exclude the appraiser from
the setting so that he or she has access in every phase (see example below).
298
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

You can dene the following column access authorizations, for example:
● Free column access for all participants during the entire appraisal process
This setting denes that all participants can display all part appraisals at any time and make changes to the
appraisal document.
● Change or display authorization for column owners only.
This setting denes that only column owners can display a column or make changes in a specic appraisal
phase.
● On this tab page you can use input help to dene that columns are only to be visible to certain participants
in the individual phases. To do this, choose the value Hide.
The infotype consists of:
● Checkbox: Default
Use input help to select default entries for access authorizations. Click on the Default Access button to
transfer the entries to the Column Access group box.
● Indicator: Changes
You can accept the transferred defaults without restriction or, if necessary, you can change entries in the
individual cells. If you make and save any changes, the changed eld is marked with an indicator. This
makes it easier for you to identify whether these settings are default entries.
● Group box: Column Access
In this group box, you make setting for column access.
Example
You depict a part appraisal process with one appraiser (manager), one appraisee (employee), and several
part appraisers (colleagues). In the Part Appraisal column, the Part Appraisee (employee) is the default
column owner. In the Part Appraisal phase, you assign the column owner change authorization and dene
that all other participants do not have access during this phase of the part appraisal.
In many cases, you might want the manager to have at least display authorization. You can assign the
manager with the necessary authorizations (for example, Display for Appraiser, Hide for Others) by using
input help. This ensures that the column is not displayed for all other part appraisers and that the appraiser
has display authorization for the part appraisal column.
Note
● The column access dened for the Part Appraisal (PAPP) and Final Appraisal (FAPP) columns is
possible when one of the following columns is present in the appraisal template:
○ In Process
○ Completed
○ Approved
○ Rejected
● The Objective Setting (OBJ0) column comprises all objective setting columns (OBJ* and QBH*). The
Part Appraisal (PAPP) column comprises the Part Appraisal Weighting (PWGT) and Part Appraisal
(PAPP) columns. This is because the SAP system always processes the relevant columns
simulataneously.
● If, for a particular phase, a user has Change access to the Objective Setting (OBJ0) column, he or she
can use the Free Enhancement function. If this column is not present, the SAP sytem checks whether
the user has Change access to the Final Appraisal (FAPP) column for this phase. If this is the case, the
user can use a Free Enhancement for this phase.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 299

● The column access dened for the Part Appraisal (PAPP) and Final Appraisal (FAPP) columns is
possible when one of the following columns is present in the appraisal template:
○ In Process
○ Completed
○ Approved
○ Rejected
You can use an implementation of the BAdI HRHAP00_COL_ACCESS to dene customer-specic column
access.
13.4.5.2.3.4.2 Tab: Processing (Infotype 5025)
● Setting: Self Appraisal Not Allowed
If this setting is activated, a user (that is the user who is logged on) cannot simulataneously perform the
role of appraiser and appraisee.
● Setting: No Authorization Check for Appraiser
If this setting is activated, an authorization check is not performed for the appraiser. This means that even
if a user does not have authorization for the appraiser’s person, he or she can nevertheless display and edit
all appraisal documents that include this appraiser.
Example
An appraiser has access only to the HR master data of employees in the employee subgroup Salaried
Employees. That is, he or she can display and edit the appraisal documents for these employees.
However, these employees can be appraised by an employee from a dierent employee subgroup (such
as Managing Employees). In this case, the administrator does not have access to the appraiser’s
person. To enable the administrator to nevertheless evaluate and edit appraisal documents for
employees in the Employees subgroup, you use the setting No Authorization Check for Appraiser
setting. Consequently, the appraiser’s data is not checked for authorization and the administrator can
also access the appraisal documents of appraisers in dierent areas.
● Setting: Processing Archived Appraisal Documents
Archived appraisal documents refer to completed appraisal documents. This setting determines whether
completed appraisal documents can be deleted in transaction PHAP_CHANGE_PA. If you want this to be
possible, select Delete or Reset and Delete. However, if you do not want this to be possible, select Do Not
Reset or Delete.
To enable the user to delete completed appraisal documents in transaction PHAP_CHANGE_PA, he or she
must have the relevant authorization in authorization object P_HAP_DOC (value 06 –Delete).
Regardless of this Customizing setting and the user’s authorizations dened for this setting 06 –Delete,
the user can always delete completed appraisal documents in transaction PHAP_ADMIN_PA provided that
he or she is permitted to use this transaction.
13.4.5.2.3.4.3 Tab: Roles (Infotype 5024)
The Roles tab denes which roles in the appraisal templates are to be used for part appraisals.
300
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
You can use roles to dene the relationship between the part appraiser and appraisee in the appraisal process.
You can edit roles explicitly in the SAP system or have a BAdI (HRHAP00_SELECTION) determine the roles
from the enterprise’s organizational structure.
You can use roles to restrict or control part appraisal authorizations at the level of individual elements. You
make the relevant settings for individual elements in the Customizing settings for the Roles tab. If you do not
use the role Colleague for a particular element in the appraisal template, this element cannot be appraised by
the appraisee's colleague, for example.
This allows you to dierentiate between the manager’s part appraisal authorizations and the employee’s part
appraisal authorizations in relation to part appraisal columns in the same appraisal template.
Caution
The roles to be used in the appraisal process must be selected at category and appraisal-template level.
Example
Roles delivered in the standard system:
● Colleague
The SAP system uses the organizational structure to identify this role. It interprets all employees
located on the same hierarchical level of the organizational structure as colleagues.
Caution
Organizational Management must be implemented.
● Manager
The SAP system uses the organizational structure to identify this role. It interprets the employee with a
managerial function who is located one level higher than the employee in the hierarchical structure as
the manager.
Caution
Organizational Management must be implemented.
● Self
The SAP system identies this role using the user and, if required user's personnel number (from the
Communication infotype (0105)). The SAP system can only read the personnel number via the user.
Caution
The Communication infotype (0105) must be available for people.
13.4.5.2.3.4.4 BSP-Specic Authorization Checks
For information about the authorizations for the BSP application, see SAP Note 616900 .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 301

13.4.5.2.3.4.5 BAdI for Authorization Checks
The BAdI HRHAP00_AUTHORITY is delivered for extended authorization checks and it can be used as a
customer-specic implementation.
13.4.5.2.4 Network and Communication Security
Your network infrastructure is extremely important in protecting your system. Your network needs to support
the communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats based on software aws (at both the operating system
level and application level) or network attacks such as eavesdropping. If users cannot log on to your application
or database servers at the operating system or database layer, then there is no way for intruders to
compromise the machines and gain access to the back-end system’s database or les. Additionally, if users are
not able to connect to the server LAN (local area network), they cannot exploit well-known bugs and security
holes in network services on the server machines.
The network topology for Performance Management is based on the topology used by the SAP NetWeaver
platform. Therefore, the security guidelines and recommendations described in the SAP NetWeaver Security
Guide also apply to Performance Management. Details that specically apply to Performance Management are
described in the following topics:
● Communication Channel Security
This topic describes the communication paths and protocols used by Performance Management.
● Network Security
This topic describes the recommended network topology for Performance Management. It shows the
appropriate network segments for the various client and server components and where to use rewalls for
access protection It also includes a list of the ports needed to operate Performance Management.
For more information, see the following sections of the SAP NetWeaver Security Guide:
● Network and Communication Security
● Security Aspects for Connectivity and Interoperability
13.4.5.2.4.1 Communication Channel Security
The table below shows the communication paths used by Peformance Management, the protocol used for the
connection, and the type of data transferred.
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
Front-end client with SAP
GUI for Windows for the ap
plication server
DIAG All application data Passwords and personal data
302 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
Front-end client with a Web
browser for the application
server
HTTP, HTTPS All application data Passwords and personal data
Upload document HTTP, HTTPS XML document Personal data
SAP Business Information
Warehouse (SAP BW)
Extractor program Performance Management
data
You can use Secure Network Communications (SNC) to protect DIAG and RFC connections. The Secure
Sockets Layer protocol (SSL protocol) protects HTTP connections.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
Printing
Peformance Management provides the options for printing content. For information about security while
printing, see the SNC User's Guide.
13.4.5.2.4.2 Network Security
Ports
Performance Management runs on SAP NetWeaver and uses the ports from the AS ABAP. For more
information, see the topic for AS ABAP Ports in the corresponding SAP NetWeaver Security Guides. For other
components, for example, SAPinst, SAProuter, or the SAP Web Dispatcher, see https://help.sap.com/viewer/
ports.
13.4.5.2.5 Internet Communication Framework Security
You should only activate those services that are needed for the applications running in your system. For the
Manager and Employee roles in Performance Management, all services with the prex HAP in the path /
default_host/sap/bc/webdynpro/sap/ are required.
● HAP_CONFIGURATION - Conguration
● HAP_DOCUMENT_LINK - Web Dynpro application hap_document_link
● HAP_MAIN_DOCUMENT - Appraisal Document
● HAP_QUALIFICATION_PROFILE - Application for Qualication Prole
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 303

● HAP_START_PAGE_POWL_UI_MSS - Web Dynpro application HAP_START_PAGE_POWL_UI_MSS
● HAP_START_PAGE_POWL_UI_ESS - Web Dynpro application HAP_START_PAGE_POWL_UI_ESS
Use the transaction Maintain Services (SICF) to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information, see Activating and Deactivating ICF Services in the SAP NetWeaver documentation in
SAP Library.
For more information about ICF security, see RFC/ICF Security Guide.
13.4.5.2.6 Data Storage Security
HANA
The Performance Management data is saved to the databases of SAP Web Application Server (Web AS) or S/
4HAN Component. You do not need to use any other databases in addition to these standard databases.
Performance Management stores the data in the following locations:
Data Storage Location
Appraisal Templates PD infotype tables
Cascaded goals PD infotype tables
Data from appraisal documents HRHAP* tables
Attachments Knowledge Provider (KPro)
Download PDF File system of client
13.4.5.2.7 Other Security-Relevant Information
Access to attachments via Microsoft Internet Explorer
You use Microsoft Internet Explorer and want to display attachments in the browser. To do this, Microsoft
Internet Explorer checks the content of the attachment to determine the le type and display the attachment
correctly (MIME Type Sning). In the worst case, it is thus possible that damaging les of an undesired le type
are displayed in the browser or cause damage in another way. To avoid this potential threat to security, deselect
MIME Type Sning in the security settings of Microsoft Internet Explorer.
304
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.4.5.2.8 Security-Relevant Logging and Tracing
Performance Management uses logging and tracing mechanisms from SAP NetWeaver in the appraisal
document. These mechanisms are described in detail under Auditing and Logging.
You can specify the following in the appraisal template:
● Do you want data to be logged?
● The specicity of logging of access to appraisal documents
● The specicity of loggingn of changes to appraisal documents
Changes to appraisal templates are logged using change documents.
13.4.5.3 Talent Management and Talent Development
About This Chapter
This chapter of the Security Guide provides an overview of the security-relevant information for Talent
Management and Talent Development (PA-TM).
Overview of the Main Sections of This Chapter
The following sections contain the security-relevant information that is specic to Talent Management and
Talent Development:
● Important SAP Notes
This section lists the most important SAP Notes with regard to the security of Talent Management.
● Authorizations
This section provides an overview of the authorization concept used for Talent Management.
● Network and communication security
This section provides an overview of the following aspects:
○ Communication Channel Security
○ Communication Destinations
● Internet Communication Framework Security
This section provides an overview of the services for the Internet Communication Framework (ICF) used by
Talent Management.
● Data Storage Security
This section provides an overview of the critical data used by Talent Management, as well as the security
mechanisms used.
● Security for Third-Party or Additional Applications
This section contains security information that applies to third-party or additional applications that are
implemented together with Talent Management.
● Other Security-Relevant Information
This section contains information on uploading and displaying attachments.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 305

13.4.5.3.1 Authorizations
Use
Talent Management uses the following authorization concepts:
● SAP NetWeaver authorization concept that is based on assigning authorizations to users based on roles
For this purpose, the roles mentioned under Standard Roles are available as a template. You can copy the
standard roles to the customer namespace and adjust them to suit your requirements. You use the prole
generator (transaction PFCG) to maintain roles.
● HR-specic concept for the structural authorization check
For this purpose, the authorization proles mentioned under Standard Roles are available as a template.
You can use the authorization proles as an example for creating your own authorization proles and then
assign these proles to the relevant users.
For more information about the authorization proles, see Customizing for Talent Management and Talent
Development and choose
Basic Settings Authorizations in Talent Management Dene Structural
Authorizations
For more information about the structural authorization check, see section Structural Authorization Check
(see SAP Library for SAP S/4HANA and choose Human Resources HR Tools Authorizations for
Human Resources
).
Role and Authorization Concept for Talent Management
Standard Roles
The table below shows the standard roles and structural authorization proles that can be used for Talent
Management.
Standard Roles and Structural Authorization Proles
Role Description Structural Authorization Prole
SAP_SR_TMC_TMS_6
Authorizations for talent management
specialists and talent management su
perusers (see Talent Management
Specialist under Single Roles in Talent
Management)
Talent Management Specialist:
TMS_PROFILE
Talent Management Superuser:
TMS_ALL
SAP_SR_TMC_MANAGER_6
Authorizations for managers with re
gard to Talent Management activities
(see Manager in Talent Management un
der Single Roles in Talent Management)
TMS_MAN_PROF
306 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Role Description Structural Authorization Prole
SAP_SR_TMC_EMPLOYEE_6
Authorizations for employees with re
gard to Talent Management activities
(see Employee in Talent Management
under Single Roles in Talent
Management)
None
For the documentation for the standard roles, see SAP Library for SAP S/4HANA and choose Human
Resources Talent Management Talent Management and Talent Development Roles in Talent Management
Single Roles in Talent Management .
The table below shows the roles that we recommend you no longer use.
Roles No Longer Recommended for Use
Role Description Note
SAP_TMC_TALENT_MANA_SPECIALIST
Authorizations for talent management
specialists (see Talent Management
Specialist under Single Roles in Talent
Management)
This role is obsolete and was replaced
by the role SAP_SR_TMC_TMS_6.
SAP_TMC_SUPER_TALENT_MANA_SPEC
Authorizations for talent management
superusers (see Talent Management
Superuser under Obsolete Single Roles
in Talent Management)
This role is obsolete and was replaced
by the role SAP_SR_TMC_TMS_6.
SAP_TMC_MANAGER
Authorizations for managers with re
gard to Talent Management activities
(see Manager in Talent Management un
der Single Roles in Talent Management)
We recommend that you use the role
SAP_SR_TMC_MANAGER_6 instead of
this role.
SAP_TMC_EMPLOYEE
Authorizations for employees with re
gard to Talent Management activities
(see Single Roles in Talent
Management)
This role is obsolete and was replaced
by the role SAP_SR_TMC_EMPLOYEE_6.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by Talent Management.
Standard Authorization Objects
Authorization Object Description More Information
B_BUPA_RLT
Authorizations for business partner
roles
Security Guide for SAP NetWeaver Ap
plication Server for ABAP under SAP
Business Partner Secuirty
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 307

Authorization Object Description More Information
CA_POWL
Authorizations for the personal object
worklist (POWL)
SAP Library for SAP S/4HANA under
Cross-Application Functions in SAP
ERP Cross-Application Components
Personal Worklist in the section
Assign Authorizations (Standard POWL)
S_RFC
Authorization check upon RFC access SAP NetWeaver Security Guide for Re
mote Function Call (RFC) and Internet
Communication Framework (ICF) un
der Authorization Object S_RFC
S_WFAR_OBJ
ArchiveLink: Authorizations for access
ing documents
SAP NetWeaver Library under SAP
NetWeaver by Key Capability
Application Platform by Key Capability
ArchiveLink in the section Authori
zations
PLOG
Authorization object that checks the
authorization for certain elds of Per
sonnel Planning components (Organi
zational Management, Personnel Devel
opment, Training and Event Manage
ment, and so on)
SAP Library for SAP S/4HANA under
PLOG (Personnel Planning)
P_HAP_DOC
Authorization object that controls a us
er's access to appraisal templates
SAP Library for SAP S/4HANA under
P_HAP_DOC (Appraisal Systems:
Appraisal)
P_ORGIN
Authorization object used to check the
authorization for accessing HR info
types
SAP Library for SAP S/4HANA under
P_ORGIN (HR: Master Data)
P_TCODE
Authorization object used to check
whether a user is authorized to start
various HR transactions
SAP Library for SAP S/4HANA under
P_TCODE (HR: Transaction Code)
P_PERNR
Authorization object used if dierent
authorizations are to be assigned for
accessing a user's personnel number
SAP Library for SAP S/4HANA under
P_PERNR (HR: Master Data - Personnel
Number Check)
For the documentation for the authorization objects PLOG, P_HAP_DOC, P_ORGIN, P_TCODE, and P_PERNR, see
SAP Library for SAP S/4HANA and choose Human Resources HR Tools Authorizations for Human
Resources Technical Aspects Authorization Objects .
Critical Combinations
● Talent Review Meetings
308
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
○ All users that have access to the personal object worklist (POWL) for talent review meetings may
create talent review meetings.
Note
In the standard SAP system, the POWL for talent review meetings is contained in the roles for
talent management specialists for SAP Enterprise Portal and SAP Business Client.
○ Users have display and change authorization for all talent review meetings to which they are assigned
as members of the support team. The POWL for talent review meetings provides users with a list of
talent review meetings, which they can display and edit.
Caution
All members of the support team for a talent review meeting have unrestricted access to all
information available within this talent review meeting (for example, to all assigned managers and
talents, and their proles). When this information is accessed, there is no additional authorization
check within the talent review meeting.
○ Those users that have display or change authorization for the related infotype record of the Object
infotype (1000) also have display or change authorization for a talent review meeting. The infotype
record is identied by the RM (Talent Review Meeting) object type and the ID of the talent review
meeting. Users that have display authorization for this infotype record can call the talent review
meeting in display mode. Users with change authorization for this infotype record can call the talent
review meeting in change mode.
● Talent Search
○ To be able to use the search, a user must be a talent management specialist with an assigned area of
responsibility. This means that there must be a relationship 741 (Is Responsible For/Is in Area of
Responsibility Of) between the user's central person (object type CP) and at least one organizational
unit (object type
O).
○ In Customizing, for the search elds that you want to use as search criteria, enter the infotype and the
object type, if required, to dene which authorization object is used for the authorization check. These
settings specify whether this eld is available to a user for selection in the search template and in the
search results.
Example
The user wants to use the talent group as a search criterion and search for all talents that are
assigned to a particular talent group. Therefore, the system checks whether the user has display
authorization for relationship 743 (Has Talent For/Comprises Talent) between the object types CP
(Central Person) and TB (Talent Group). To do so, it checks the authorization for the corresponding
subtype of the infotype Relationships (1001).
For more information, see Customizing for Talent Management and Talent Development and choose
Basic Settings Search Dene Search Requests and Search Field Names .
○ In the search results, the system displays only the objects for which the user has authorization through
the authorization object PLOG as well as the corresponding structural authorization. For the object
type CP, the system also checks whether the user has display authorization for the infotype
Organizational Assignment (0001).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 309
Note
If more than one person (object type P) is assigned to a central person (CP) (for example,
employees in concurrent employment), it is sucient for the talent search if the user has display
authorization for one of these persons.
Additional Functions
You can deactivate specic authorization checks that are performed in the standard SAP system when
assigning employees (object type CP (Central Person)) to positions, job families, and talent groups. In the
standard SAP system, when such relationships are created, the system checks whether the user (in this case,
the talent management specialist) has the following authorizations:
● For assigning employees to positions:
Authorizations for
○ Employee (object type CP)
○ Position (object type S)
○ Relationship 740 (Is Successor Of)
● For assigning employees to job families:
Authorizations for
○ Employee (object type CP)
○ Job family (object type JF)
○ Relationship 744 (Has Potential For)
● For assigning employees to talent groups:
Authorizations for
○ Employee (object type CP)
○ Talent group (object type TB)
○ Relationship 743 (Has Talent For)
So that a talent management specialist is also able to create these relationships for employees (object type CP)
for which he or she does not usually have change authorization (because of his or her structural authorization
prole), the authorization check can be deactivated for employees for the respective employee assignment.
The talent management specialist then only needs the change authorization for the object (of the object type
Position, Job Family, or Talent Group) to which he or she wants to assign the employee, and for the relationship.
For more information, see Customizing for Talent Management and Talent Development and choose Basic
Settings Authorizations in Talent Management Deactivate Authorization Check When Assigning
Employees .
13.4.5.3.2 Communication Channel Security
The table below shows the communication paths used by Talent Management, the protocol used for the
connection, and the type of data transferred.
310
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
Front-end client with SAP
GUI for Windows for the ap
plication server
DIAG Customizing data Passwords
Front-end client with a Web
browser for the application
server
HTTP(S) Application data Passwords, personal data
Front-end client with an SAP
Business Client for the appli
cation server
HTTP(S) Application data Passwords, personal data
Connection of PDF-based
print forms to the archive
HTTP(S) Person-related data (such as
an employee's photo)
SAP Business Information
Warehouse (SAP BW)
Extractor program HR master data, organiza
tional data, Talent Manage
ment data
You can use Secure Network Communications (SNC) to protect DIAG and RFC connections. The Secure
Sockets Layer protocol (SSL protocol) protects HTTP connections.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
Note
If you convert the protocol from HTTP to HTTPS and implement PDF-based print forms, see SAP Note
1461447 .
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
13.4.5.3.3 Communication Destinations
The table below shows an overview of the communication destinations used by Talent Management.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 311

Communication Destinations
Destination Delivered Type Users, Authorizations Description
Access to external ap
plications for Talent
Management
Yes RFCs of the function
group
HRTMC_SERVICES
The following roles re
quire authorization for
the authorization ob
ject S_RFC to have ac
cess to external appli
cations:
● SAP_TMC_TALENT
_MANA_SPECIALI
ST
● SAP_TMC_SUPER_
TALENT_MANA_SP
EC
● SAP_TMC_MANAGE
R
The function group
HRTMC_SERVICES
contains the Remote
Function Calls for ex
ternal applications that
can be used for Suc
cession Planning, for
example:
Transfer of talent
groups and successor
assignments from SAP
E-Recruiting to Talent
Management
Yes RFCs of the function
group
HRSCP_MIGRATION
To run the report
RPTMC_MIGRATE_SUC
CESSIONS or
RPTMC_MIGRATE_TAL
ENT_GROUPS
, a user
requires authorization
for the authorization
object S_RFC.
The function group
HRSCP_MIGRATION
contains the Remote
Function Calls for
transferring talent
groups and successor
assignments from SAP
E-Recruiting to Talent
Management.
Transfer of entries
from the candidate
prole in SAP E-Re
cruiting to the talent
prole in Talent Man
agement
Yes RFCs of the function
group
HRSCP_TP_SYNC
To run the report
HRSCP_TP_SYNC_GET
_EDU_WE_INFO, a user
requires authorization
for the authorization
object
S_RFC.
The function group
HRSCP_TP_SYNC con
tains the Remote Func
tion Calls for synchro
nizing the talent prole
in Talent Management
with the candidate pro
le in SAP E-Recruiting
Jump from queries in
SAP Business Informa
tion Warehouse (SAP
BW) to the talent pro
le
Yes RFC for transferring
the MEM_ID from the
BW system to the
S/
4HANA system
The user requires au
thorization for the au
thorization object
S_RFC.
312 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

The table below shows the function modules that the reports use to transfer data to Talent Management:
Function Modules for Transferring Data to Talent Management
Function Group Function Module Used by Report
HRSCP_MIGRATION HRSCP_MIG_SCP_GET_ALL
Transfer Successor Assignments to
Talent Management
(RPTMC_MIGRATE_SUCCESSIONS)
HRSCP_MIGRATION HRSCP_MIG_TG_GET_ALL
Transfer Talent Groups from E-
Recruiting to Talent Management
(RPTMC_MIGRATE_TALENT_GROUPS)
HRSCP_MIGRATION HRSCP_MIG_TG_GET_DETAILS
Transfer Talent Groups from E-
Recruiting to Talent Management
(RPTMC_MIGRATE_TALENT_GROUPS)
HRSCP_MIGRATION HRSCP_MIG_TG_GET_TALENTS
Transfer Talent Groups from E-
Recruiting to Talent Management
(RPTMC_MIGRATE_TALENT_GROUPS)
HRSCP_TP_SYNC HRSCP_TP_SYNC_GET_EDU_WE_INFO
Synchronization of Talent Prole with
Candidate Prole
(RPTMC_TP_SYNC_EDU_WE_RCF)
13.4.5.3.4 Internet Communication Framework Security
You should only activate those services that are needed for the applications running in your system. For Talent
Management the following services are needed:
● Talent Management Specialist
○ default_host/sap/bc/webdynpro/sap/HRTMC_EMPLOYEE_PROFILE
○ default_host/sap/bc/webdynpro/sap/HRTMC_LONG_PROFILE
○ default_host/sap/bc/webdynpro/sap/hrtmc_rm_maintenance
○ default_host/sap/bc/webdynpro/sap/hrtmc_rm_presentation
○ default_host/sap/bc/webdynpro/sap/hrtmc_search
○ default_host/sap/bc/webdynpro/sap/hrtmc_side_by_side
○ default_host/sap/bc/webdynpro/sap/hrtmc_talent_group
○ default_host/sap/bc/webdynpro/sap/HRTMC_TA_DEV_PLAN
● Manager
○ default_host/sap/bc/webdynpro/sap/HRTMC_EMPLOYEE_PROFILE
○ default_host/sap/bc/webdynpro/sap/HRTMC_LONG_PROFILE
○ default_host/sap/bc/webdynpro/sap/hrtmc_side_by_side
○ default_host/sap/bc/webdynpro/sap/hrtmc_talent_group
○ default_host/sap/bc/webdynpro/sap/HRTMC_TA_ASSESSMENT
○ default_host/sap/bc/webdynpro/sap/HRTMC_TA_DASHBOARD
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 313
○ default_host/sap/bc/webdynpro/sap/HRTMC_TA_DEV_PLAN
○ default_host/sap/bc/webdynpro/sap/hrtmc_teamviewer
● Employee
default_host/sap/bc/webdynpro/sap/HRTMC_EMPLOYEE_PROFILE
Use the transaction SICF to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly. For more information, see Activating and Deactivating ICF Services.
For more information about Internet Communication Framework security, see RFC/ICF Security Guide.
13.4.5.3.5 Data Storage Security
Data Storage
The Talent Management data is stored in the SAP NetWeaver Application Server or SAP S/4HANA databases.
You do not need to use any other databases in addition to these standard databases.
Talent Management stores the data in the following locations:
Data and Storage Locations
Data Storage Location
Master data, talent assessments HR infotype tables
Attachments, comments, calibration grid icon Knowledge Provider (KPro)
Business partner master data Business partner database
Employee photo ArchiveLink
Cookies
The application uses a Web browser. SAP NetWeaver Application Server must set and accept cookies.
13.4.5.3.6 Security for Additional Applications
You can implement Talent Management together with the product SAP Talent Visualization by Nakisa. SAP
Talent Visualization by Nakisa provides users with a graphical and organization-oriented view of Succession
Planning and the job architecture.
Note
Note that you need to purchase your own license for using the product SAP Talent Visualization by Nakisa.
314
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

If you implement SAP Talent Visualization by Nakisa, the roles for the talent management specialist, the talent
management superuser, and the manager need the authorization for the authorization object S_RFC to be able
to access applications that call the HRTMC_SERVICES function group. This function group comprises the
Remote Function Calls (RFCs) for external applications such as
SAP Talent Visualization by Nakisa. This
authorization is contained in the standard Talent Management roles. For more information about the standard
roles, see sectionAuthorizations under Talent Management and Talent Development.
For information about the security of SAP Talent Visualization by Nakisa, see the documentation for this
product.
13.4.5.3.7 Other Security-Relevant Information
Uploading and Displaying Attachments
Uploading Attachments
Talent Management uses the virus scan interface of SAP NetWeaver. You can use this interface to include
external virus scanners to increase the security of your system.
For Talent Management, the virus scan prole /HCM_TMC/DOCUMENT_UPLOAD is available for checking that
les or documents uploaded as attachments do not contain any viruses. This virus scan prole is not active in
the standard SAP system. To activate the virus scan prole, in Customizing for Talent Management and Talent
Development, make the settings under Basic Settings Attachments Dene Virus Scan Proles . In
Customizing for SAP NetWeaver under Application Server System Administration Virus Scan Interface ,
you need to rst set up the virus scan interface.
For more information about the virus scan interface, see SAP NetWeaver Library and choose SAP NetWeaver
by Key Capability Security System Security , and the Virus Scan Interface section.
You can also limit the size of les that are uploaded as attachments. To do so, in Customizing for Talent
Management and Talent Development, make the settings under
Basic Settings Attachments Assign
Storage Locations and Maximum File Size .
Displaying Attachments Using Microsoft Internet Explorer
If you display attachments in a browser and use Microsoft Internet Explorer for this, Microsoft Internet Explorer
checks the content of the attachment to determine the le type and display the attachment correctly based on
the type (MIME Type Sning). In the worst case, it is thus possible that damaging les of an undesired le type
are displayed in the browser or cause damage in another way. To avoid this potential threat to security, deselect
MIME Type Sning in the security settings of Microsoft Internet Explorer.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 315
13.4.5.4 Enterprise Compensation Management
About This Chapter
This chapter of the Security Guide provides an overview of the security-relevant information for the Enterprise
Compensation Management (PA-EC) application component.
Overview of the Main Sections of This Chapter
The following sections contain the security-relevant information that is specic to “Enterprise Compensation
Management”:
● Important SAP Notes
This section lists the most important SAP Notes with regard to the security of Enterprise Compensation
Management.
● Security Aspects for Data, Data Flow, and Processes
This section provides an overview of the security aspects of the most frequently used processes in
Enterprise Compensation Management.
● Authorizations
This section provides an overview of the authorization concept used for Enterprise Compensation
Management.
● Communication Channel Security
This section describes the communication paths and logs that Enterprise Compensation Management
uses.
● Internet Communication Framework Security
This section provides an overview of the services for the Internet Communication Framework (ICF) used by
Enterprise Compensation Management.
● Data Storage Security
This section provides an overview of all critical data used by Enterprise Compensation Management, as
well as the security mechanisms used.
● Security-Relevant Logging and Tracing
This section provides an overview of the trace and log les that contain security-relevant information and
that enable you to reproduce activities, for example, if there is a security violation.
13.4.5.4.1 Security Aspects for Data, Data Flow, and
Processes
Enterprise Compensation Management uses applications based on the following technology:
Role: Manager
● Web Dynpro for ABAP in the applications in Manager Self-Service
● Interactive forms based on Adobe software (Interactive forms) in the Total Compensation Statement and
Compensation Review Statement applications.
For more information, see the guide for SAP Interactive Forms by Adobe under SAP Interactive Forms by
Adobe Security Guide.
316
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

For more information about the Manager role, see the SAP S/4HANA Security Guide and choose the
following path: Self-Services Manager Self-Service .
Role: Employee
● Web Dynpro for ABAP in the applications in Employee Self-Service
● Interactive forms based on Adobe software (Interactive forms) in the Total Compensation Statement
application.
For more information, see the guide for SAP Interactive Forms by Adobe under SAP Interactive Forms by
Adobe Security Guide.
For more information about the Employee role, see the SAP S/4HANA Security Guide and choose the
following path: Self-Services Employee Self-Service .
Role: Administrator
● SAP Graphical User Interface (SAP GUI) in Customizing for Enterprise Compensation Management and
administrative reports.
● Business Server Page (BSP) in the Top-Down Budgeting functions
During compensation planning, Enterprise Compensation Management sends e-mails via workow. For
information about workow and sending e-mails, see Customizing for Enterprise Compensation Management
and choose Compensation Administration Workow Settings .
For more information about the settings, see Customizing for Enterprise Compensation Management.
13.4.5.4.2 Authorizations
Use
Enterprise Compensation Management uses the following authorization concepts:
● SAP NetWeaver authorization concept that is based on assigning authorizations to users based on roles
For this, the roles mentioned under “Standard Roles” are available as a template. You can copy the
standard roles to the customer namespace and adjust them to suit your requirements. For role
maintenance you use the prole generator (transaction PFCG).
● HR-specic concept for the general and structural authorization check
For more information about the authorization checks, see General Authorization Check and Structural
Authorization Check (see SAP Library for SAP S/4HANA and choose Human Resources HR Tools
Authorizations for Human Resources ).
Roles and Authorization Concept for Enterprise Compensation Management
Standard Roles
Enterprise Compensation Management does not provide its own standard roles. It uses roles from Manager
Self-Service and Employee Self-Service.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 317
For more information, see the following:
● Authorizations in Manager Self-Service.
● Authorizations in Employee Self-Service.
Standard Authorization Objects
Enterprise Compensation Management uses the same standard authorization objects as all of Human
Resources. For more information about the standard authorization objects in Human Resources, see
Authorizations. To do this, choose SAP S/4HANA Security Guide for Human Resources Authorizations .
13.4.5.4.3 Communication Channel Security
The following table shows the communication paths that Enterprise Compensation Management uses, the
protocol used for the connection, and the type of data transferred.
Communication Paths Protocol Used Type of Data Transferred Data Requiring Particular
Protection
Front-end client that uses
SAP GUI for Windows as the
application server
DIAG All Customizing data Passwords
Front-end client that uses a
Web browser as the applica
tion server
HTTP, HTTPS
Note
We generally recom
mend using HTTPS
All application data Passwords, personal data
SAP Business Information
Warehouse (SAP BW)
Extractor program HR master data, organiza
tional data, Enterprise Com
pensation Management data
You can use Secure Network Communications (SNC) to protect DIAG and RFC connections. The Secure
Sockets Layer protocol (SSL protocol) protects HTTP connections.
Recommendation
We strongly recommend that you use secure protocols (SSL, SNC) where possible.
For more information, see the SAP NetWeaver Security Guide under Transport Layer Security.
Printing
Enterprise Compesation Management provides a number of options for printing content. For information about
security while printing, see the SNC User's Guide.
318
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.4.5.4.4 Internet Communication Framework Security
You should only activate those services that are needed for the applications running in your system. For the
Manager role in Enterprise Compensation Management, all services with the prex HCM_ECM in the path /
default_host/sap/bc/webdynpro/sap/ are required.
● HCM_ECM_PLANNING_OVERVIEW_OIF - Compensation Planning Overview
● HCM_ECM_PLANNING_UI_GAF - Planning User Interface
● HCM_ECM_PROFILE_OIF - Compensation Prole
● HCM_ECM_SIDEBYSIDE_OIF - Side-by-Side Comparison
● HCM_ECM_TEAMVIEWER_OIF - Compensation Prole Team Overview
The Administrator role, the services with the prex HRECM_BDG in the path /default_host/sap/bc/bsp
are only required if you use top-down budgeting for compensation planning.
● HRECM_BDG_CHKRL - Check and Release Budget
● HRECM_BDG_MAINT - Budget Maintenance
● HRECM_BDG_RA_VL - Reassign Budget Value
● HRECM_BDG_SRV - Budgeting Services
● HRECM_BSG_SRV02 - Budget Structure Services
● HRECM_BDG_START - Overview
Use the transaction Maintain Services (SICF) to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information, see Activating and Deactivating ICF Services in the SAP NetWeaver documentation in
SAP Library.
For more information about ICF security, see RFC/ICF Secuirty Guide.
13.4.5.4.5 Data Storage Security
All data for Enterprise Compensation Management is stored in the database of the SAP system. The data is
stored in the Personnel Administration (PA) and Budget Management(PA-PM) application components as well
as in the database tables that govern the processes of Enterprise Compensation Management.
The applications in Enterprise Compensation Management store sensitive, personal data for compensation
planning. The data saved when managing the processes of Enterprise Compensation Management can be
deleted after the compensation review using the report Delete Compensation Planning History Data
(RHECM_DELETE_HISTORY_DATA).
For information about data storage security, go to http://help.sap.com/s4hana_op_1709, enter Security Guides
for the Operating System and Database Platforms into the search bar, press Enter , and open the search result
with that title.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 319

13.4.5.4.6 Security-Relevant Logging and Tracing
Enterprise Compensation Management uses logging and tracing mechanisms from SAP NetWeaver. These
mechanisms are described in detail under Auditing and Logging.
Changes to data in Enterprise Compensation Management that are made within the applications of Enterprise
Compensation Management are logged by the SAP system. The data can be checked with the following
reports:
● Display Compensation Planning Changes (RHECM_DISPLAY_CHANGES)
● Display Compensation Planning Progress (RHECM_DISPLAY_PROGRESS)
13.4.6 Time and Attendance Management
13.4.6.1 Personnel Time Management (PT)
Introduction
Note
This guide does not replace the administration or operation guides that are available for productive
operations.
Target Audience
● Technology consultants
● System administrators
This document is not included as part of the installation guides, conguration guides, technical operation
manuals, or upgrade guides. Such guides are only relevant for a certain phase of the software lifecycle, whereas
the security guides provide information that is relevant for all lifecycle phases.
Why Is Security Necessary?
With the increasing use of distributed systems and the Internet for managing business data, the demands on
security are also on the rise. When using a distributed system, you need to be sure that your data and
processes support your business needs without allowing unauthorized access to critical information. User
errors, negligence, or attempted manipulation of your system should not result in loss of information or
320
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
processing time. These demands on security apply likewise to the SAP Personnel Time Management. To assist
you in securing the SAP Personnel Time Management, we provide this security guide.
About this Document
This security guide provides an overview of the security-relevant information that applies to the SAP Personnel
Time Management.
Overview of the Main Sections
The security guide comprises the following main sections:
● Before You Start
This section contains information about why security is necessary, how to use this document, and
references to other security guides that build the foundation for this security guide.
● Technical System Landscape
This section provides an overview of the technical components and communication paths that are used by
the SAP Personnel Time Management.
● Security Aspects of Data, Data Flow, and Processes
This section provides an overview of security aspects involved throughout the most widely used processes
within the SAP Personnel Time Management.
● Authorizations
This section provides an overview of the authorization concept that applies to the SAP Personnel Time
Management.
● Session Security Protection
This section provides information about activating secure session management, which prevents JavaScript
or plug-ins from accessing the SAP logon ticket or security session cookie(s).
● Network and Communication Security
This section provides an overview of the communication paths used by the SAP Personnel Time
Management and the security mechanisms that apply. It also includes our recommendations for the
network topology to restrict access at the network level.
● Internet Communication Framework Security
This section provides an overview of the Internet Communication Framework (ICF) services that are used
by the SAP Personnel Time Management.
● Security-Relevant Logging and Tracing
This section provides an overview of the trace and log les that contain security-relevant information, for
example, so you can reproduce activities if a security breach does occur.
13.4.6.1.1 Important SAP Notes
The SAP Personnel Time Management is built using the HR backend system, CRM backend system and SAP
NetWeaver components. Therefore, the corresponding security guides also apply to the SAP Personnel Time
Management.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 321

Important SAP Notes
The most important SAP Notes that apply to the security of the SAP Personnel Time Management are shown in
the table below.
Title SAP Note
Authorization objects of shift planning
496993
Transaction authorization PA61 for shift planning
500844
Setting up the HR-PDC interface
647145
For a list of additional security-relevant SAP News and SAP Notes, see https://support.sap.com/securitynotes
.
Additional Information
For more information about specic topics, see the Quick Links as shown in the table below.
Content Quick Link
Security
https://www.sap.com/community/topic/security.html
Related SAP Notes
https://support.sap.com/notes
https://support.sap.com/securitynotes
Released platforms
https://support.sap.com/pam
SAP Solution Manager
https://support.sap.com/solutionmanager
SAP Community
https://www.sap.com/community/topics.html
13.4.6.1.2 User Management
Use
User management in SAP Personnel Time Management uses the mechanisms provided with the SAP
NetWeaver Application Server for ABAP, for example, tools, user types, and password policies. For an overview
of how these mechanisms apply for SAP Personnel Time Management, see the sections below. In addition, we
provide a list of the standard users required for operating the SAP Personnel Time Management.
322
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

User Administration Tools
The table below shows the tools to use for user management and user administration with SAP Personnel Time
Management.
User Management Tools
Tool Detailed Description Prerequisites
User and role maintenance with SAP
NetWeaver AS for ABAP (Transactions
SU01, PFCG)
For more information, see User and
Role Administration of AS ABAP.
User Types
It is necessary to specify dierent security policies for dierent types of users. For example, your policy may
specify that individual users who perform tasks interactively must change their passwords on a regular basis,
but not users who run background processing jobs.
The specic user types that are required for the SAP Personnel Time Management include:
Technical users
● To upload time events from the external time recording system you use the RPTCC106 report ( HR-PDC:
Download Upload Request for Time Events). You normally schedule the report as a background processing
job. For this you require a technical user. The authorizations of the technical user should be based on the
authorizations for the PT80 transaction ( Subsystem Connection). Time events are uploaded from the
subsystem by an IDOC, which stores the time events in the CC1TEV interface table. For the upload, you
need a technical user with authorizations for communication with an SAP system using Application Link
Enabling (ALE) and the relevant table authorizations. The technical user does not require authorizations
specic to the SAP HR solution. You need a technical user with authorizations for the PT45 transaction
( HR-PDC: Post Person Time Events) for the background processing job that transfers the time events from
the interface table to the relevant Time Management tables.
● You need two types of technical users for BAPIs that store data in one of the following interface tables:
○ PTEXDIR
○ PTEX2000
○ PTEX2003
○ PTEX2010
To ll the interface tables, you need a user with authorizations for ALE communication with an SAP system and
the relevant table authorizations. For the subsequent background processing job to transfer data from the
interface tables to the infotype database tables, you need a technical user with the same authorizations that
are required for the CAT6 transaction ( Transfer Time Data to Time Management).
● For technical users that have read access to the infotypes for the BAPIs, you can use the same
authorizations as contained in the SAP_HR_PT_TIMEADMINISTRATOR role.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 323

13.4.6.1.3 Authorizations
Use
The SAP Personnel Time Management component uses the authorization concept provided by SAP NetWeaver
AS ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP
NetWeaver AS Security Guide ABAP also apply to SAP Personnel Time Management.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the ABAP.
For more information about how to create roles, see Role Administration under Role and Authorization Concept
for SAP Personnel Time Management.
Standard Roles
The table below shows the standard roles that are used by the SAP Personnel Time Management.
Role Description
SAP_HR_PT_SHIFT-PLANNER Shift Planner
SAP_HR_PT_TIME-ADMINISTRATOR Time Administrator
SAP_HR_PT_TIME-LABOR-ANALYST Time and Labor Analyst
SAP_HR_PT_TIME-MGMT-SPECIALIST Time Management Specialist
SAP_HR_PT_TIME-SUPERVISOR Time Supervisor
SAP_ESSUSER_ERP05 Employee Self-Service
SAP_HR_PT_US_PS_TIME-ADM Time Recording Administrator
This role is used only in the Public Sector in the country ver
sion for the USA
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by SAP Personnel Time
Management.
Authorization Object Field Value Description
P_PERNR AUTHC E, R Used to assign dierent au
thorizations to users for ac
cessing their own personnel
number. P_PERNR is relevant
for Self-Service Scenarios
(Role SAP_EMPLOYEE)
324 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
P_PERNR INFTY 0000, 0001, 0002, 0007,
0416, 2001, 2002, 2003,
2004, 2005, 2006, 2007,
2010, 2011, 2012, 2013
Infotypes required
P_ORGIN AUTHC E, R Used during the authoriza
tion check for HR infotypes.
P_ORGIN INFTY 0000, 0001, 0002, 0007,
0416, 2001, 2002, 2003,
2004, 2005, 2006, 2007,
2010, 2011, 2012, 2013
Infotypes required
P_PCLX AUTHC W, R Relevant for both Time Evalu
ation and Time Recording.
P_PCLX RELID B1, B2, L1, G1, PC Clusters required
13.4.6.1.4 Data Storage Security
Archiving Objects and Reports
The following tools and reports are available for archiving data:
● Archiving Object: PA_TIME (Time Evaluation Results from Cluster B2)
● Data Writing Report: RPAR5W00
● Data Deletion Report: RPAR5D00
Archiving is done using transactions PU22 and SARA respectively.
Data Deletion Reports
The following tools and reports are available for deleting data:
RPTEXTPT: Using the DELETE option deletes the data already transferred (stored in PA-tables) from the
following interface tables:
● PTEX2000
● PTEX2010
● PTEX2003GEN
● PTEX2003SPEC
RPWI4100: Reorganizes interface table LSHR (Integration to Logistics).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 325
Using Logical Paths and File Names to Protect Access to the File System
Personnel Time Management saves data in les in the local le system. Therefore, it is important to assign
explicit access to the corresponding les in the le system without access to other directories or les (also
called directory traversal). This is achieved by entering logical paths and le names in the system that are
assigned to the physical paths and le names. This assignment is validated at runtime. If access to a directory
is requested that does not correspond to a stored assignment, an error occurs.
The following lists show the logical le names and paths that are used by Personnel Time Management, and the
reports for which these le names and paths are valid. The logical le names and logical le paths were created
using transaction
FILE to facilitate the validation of physical le names.
Logical File Names and Path Names Used in Personnel Time Management
Logical File Name Reports That Use These Logical File
Names
Logical File Path
HR_XX_DIR_RPTEDO00 RPTEDO00 HR_XX_DIR_RPTEDO00
HR_XX_DIR_RPTEUP00 RPTEUP00 HR_XX_DIR_RPTEUP00
HR_XX_DIR_RPTEUP10 RPTEUP10 HR_XX_DIR_RPTEUP10
HR_XX_DIR_RPTEZL00 RPTEZL00 HR_XX_DIR_RPTEZL00
HR_XX_DIR_RPTX2010 RPTX2010 HR_XX_DIR_RPTX2010
HR_XX_DIR_RPWI0000 RPWI0000 HR_XX_DIR_RPWI0000
13.4.6.2 Cross-Application Time Sheet (CA-TS)
13.4.6.2.1 User Administration and Authentication
The Cross-Application Time Sheet (CA-TS) uses the user management and authentication mechanisms
provided with the SAP NetWeaver platform, in particular the SAP NetWeaver Application Server for ABAP.
Therefore, the security recommendations and guidelines for user administration and authentication as
described in the SAP NetWeaver Application Server for ABAP also apply to the Cross-Application Time Sheet
(CA-TS) In addition to these guidelines, we include information about user administration and authentication
that specically applies to the Cross-Application Time Sheet (CA-TS) in the following topics:
● User Management
This topic lists the tools to use for user management, the types of users required, and the standard users
that are delivered with the Cross-Application Time Sheet (CA-TS).
● Integration into Single Sign-On Environments
This topic describes how the Cross-Application Time Sheet (CA-TS) supports Single Sign-On mechanisms.
326
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.4.6.2.1.1 User Management
User management for the Cross-Application Time Sheet (CA-TS) uses the mechanisms provided with the SAP
NetWeaver Application Server for ABAP, for example, tools, user types, and password policies. For an overview
of how these mechanisms apply for the Cross-Application Time Sheet (CA-TS), see the sections below.
User Administration Tools
The table below shows the tools to use for user management and user administration with the Cross-
Application Time Sheet (CA-TS).
User Management Tools
Tool Detailed Description Prerequisites
User and Role Maintenance (transac
tion PFCG)
You can use the Role Maintenance
transaction PFCG to generate proles
for the Cross-Application Time Sheet
(CA-TS) users.
For more information, see User and
Role Administration of AS ABAP.
Technical Settings for User Manage
ment in Cross-Application Time Sheet
(CA-TS)
For more information on user proles
and the roles, see Customizing for Time
Sheet
under Settings for All User
Interfaces Authorizations .
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively have to change their passwords on a regular
basis, but not those users under which background processing jobs run.
The user types that are required for the Cross-Application Time Sheet (CA-TS) include:
● Individual users:
○ Dialog users are used to maintain, release, and approve working times. They are used for SAPGUI and
WD ABAP Frontends
● Technical users:
○ System User: Background processing and communication within a system (such as RFC users for ALE,
Workow). They are used for transferring data to target components, to check data remotely, and to
process workow items.
○ Communication users are used for scenarios in which CATS BAPIs are called from external systems.
For more information on these user types, see User Types under User Authentication in the SAP NetWeaver
Application Server for ABAP Security Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 327
Standard Users
We do not deliver standard users within Cross-Application Time Sheet (CA-TS).
13.4.6.2.1.2 Integration into Single Sign-On Environments
The most widely-used supported mechanisms are listed below. For a complete list, see the link provided below.
● Secure Network Communications (SNC)
SNC is available for user authentication and provides for a single sign-on (SSO) environment when using
the SAP GUI for Windows or Remote Function Calls.
● SAP logon tickets
Cross-Application Time Sheet (CA-TS) supports the use of logon tickets for SSO when using a Web browser
as the frontend client. In this case, users can be issued a logon ticket after they have authenticated
themselves with the initial SAP system. The ticket can then be submitted to other systems (SAP or
external systems) as an authentication token. The user does not need to enter a user ID or password for
authentication but can access the system directly after the system has checked the logon ticket.
● Client certicates
As an alternative to user authentication using a user ID and passwords, users using a Web browser as a
frontend client can also provide X.509 client certicates to use for authentication. In this case, user
authentication is performed on the Web server using the Secure Sockets Layer Protocol (SSL Protocol)
and no passwords have to be transferred. User authorizations are valid in accordance with the
authorization concept in the SAP system.
● Security Assertion Markup Language (SAML) 2.0
SAML 2.0 provides a standards-based mechanism for SSO. The primary reason to use SAML 2.0 is to
enable SSO across domains.
The Cross-Application Time Sheet (CA-TS) supports the Single Sign-On (SSO) mechanisms provided by SAP
NetWeaver. Therefore, the security recommendations and guidelines for user administration and
authentication as described in the SAP NetWeaver Secuirty Guide also apply to the Cross-Application Time
Sheet (CA-TS).
For more information about the available authentication mechanisms, see user Authentication and Single Sign-
On in the SAP NetWeaver Library.
13.4.6.2.2 Authorizations
Use
The Cross-Application Time Sheet (CA-TS) uses the authorization concept provided by the SAP NetWeaver AS
for ABAP and AS Java. Therefore, the recommendations and guidelines for authorizations as described in the
SAP NetWeaver AS Security Guide ABAP and SAP NetWeaver AS Security Guide Java also apply to the Cross-
Application Time Sheet (CA-TS).
328
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP and the User Management
Engine's user administration console on the AS Java.
Note
For more information about how to create roles, see section Role Administration under the SAP Library for
SAP S/4 HANA Identity Management.
The following section shows the typical scenarios, the relevant roles and the authorization objects that Cross-
Application Time Sheet (CA-TS) uses. These are:
Enter Working Times in Time Sheet
Approve Working Times
Transfer Working Times to Target Components
Role and Authorization Concept for Cross-Application Time Sheet (CA-TS)
Enter Working Times
Standard Roles
The table below shows the standard roles that are used by the Cross-Application Time Sheet (CA-TS).
Role Description
SAP_HR_PT_TIME-ADMINISTRATOR Time Administrator: The Time Administrator role is per
formed by employees in the individual departments of a
company, such as secretaries and foremen. Their duties in
clude entering employees' documents in the system and re
acting to messages from time evaluation.
SAP_EMPLOYEE_WDA_1 (This includes single role SAP_EM
PLOYEE_XX_ESS_WDA_1 containing authorizations for
CATS)
Employee Self-Service (WD ABAP): You need this role if you
want to enable all your company's employees to record their
working times.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by the Cross-Application Time
Sheet (CA-TS).
Authorization Object Field Value Description
P_PERNR AUTHC E, R Used to assign users dier-
ent authorizations for ac
cessing their own personnel
number. P_PERNR is relevant
for Self Service Scenarios
(Role SAP_EMPLOYEE)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 329

Authorization Object Field Value Description
P_PERNR INFTY 0000, 0001, 0002, 0007,
0315, 0316, 2001, 2002,
2003, 2010
Needed infotypes
P_ORGIN AUTHC E, R Used during the authoriza
tion check for HR infotypes.
P_ORGIN is relevant for Ad
ministrator Scenarios (Role
AP_HR_PT_TIME-ADMINIS
TRATOR, SAP_ISR_RE
TAIL_STORE)
P_ORGIN INFTY 0000, 0001, 0002, 0007,
0315, 0316, 2001, 2002,
2003, 2010
Needed infotypes
P_PCLX AUTHC R Relevant for both Self Service
and Adminstrator Scenarios,
used when attendance/
absence types are recorded
and to display target hours.
P_PCLX RELID B2, PC Needed clusters
Approve Working Times
Standard Roles
The table below shows the standard roles that are used by the Cross-Application Time Sheet (CA-TS).
Role Description
SAP_HR_PT_TIME-SUPERVISOR The Time Supervisor role is performed by executive employ
ees in the individual departments of a company, such as
those with personnel responsibility, department heads,
project managers, or foremen.
The Time Supervisor plans and approves leave and altera
tions to working times. He or she orders overtime as re
quired, and regularly monitors the amount of overtime
worked in the department. He or she checks and approves
employees' activity reports, and monitors absence times.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by the Cross-Application Time
Sheet (CA-TS).
330
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Authorization Object Field Value Description
P_ORGIN AUTHC D, R http://help.sap.com/
erp2005_ehp_02/
helpdata/en/
35/26b181afab52b9e10000
009b38f974/
content.htmAuthorizationob
ject
that is used during
the authorization check for
HR infotypes.
P_ORGIN INFTY 0328, 2001, 2002 Needed infotypes
Transfer Working Times to Target Components
Standard Roles
The table below shows the standard roles that are used by the Cross-Application Time Sheet (CA-TS).
Role Description
SAP_HR_PT_TIME-MGMT-SPECIALIST The time management specialist is responsible for the
smooth operation of the time management system. He or
she is familiar with the technical side of the SAP System. The
time management activities for this role include controlling
the transfer of data to other SAP applications, such as the
transfer of data from the SAP Cross-Application Time Sheet.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by the Cross-Application Time
Sheet (CA-TS).
Authorization Object Field Value Description
P_ORGIN No proposal No proposal
P_PERNR No proposal No proposal
PCLX No proposal No proposal
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 331

13.4.6.2.3 Session Security Protection
To prevent access in javascript or plug-ins to the SAP logon ticket and security session cookie(s), we
recommend activating secure session management.
We also highly recommend using SSL to protect the network communications where these security-relevant
cookies are transferred.
Session Security Protection on the AS ABAP
To prevent access in javascript or plug-ins to the SAP logon ticket and security session cookie(s)
(SAP_SESSIONID_<sid>_<client>), activate secure session management. With an existing security session,
users can then start applications that require a user logon without logging on again. When a security session is
ended, the system also ends all applications that are linked to this security session.
Use the transaction SICF_SESSIONS to specify the following parameter values shown in the table below in your
AS ABAP system:
Session Security Protection Prole Parameters
Prole Parameter Recommended Value Comment
icf/set_HTTPonly_ag_on_cookies 0 Client-Dependent
login/ticket_only_by_https 1 Not Client-Dependent
For more information and detailed instructions, see Activating HTTP Security Session Management on AS ABAP
in the AS ABAP security documentation.
13.4.6.2.4 Network and Communication Security
Your network infrastructure is extremely important in protecting your system. Your network needs to support
the communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats based on software aws (at both the operating system
and application level), or network attacks such as eavesdropping. If users cannot log on to your application or
database servers at the operating system or database layer, there is no way for intruders to compromise the
machines and gain access to the backend system's database or les. Additionally, if users are not able to
connect to the server LAN (local area network), they cannot exploit well-known bugs and security holes in
network services on the server machines.
The network topology for the Cross-Application Time Sheet (CA-TS) is based on the topology used by the SAP
NetWeaver platform. Therefore, the security guidelines and recommendations described in the SAP NetWeaver
Security Guide also apply to the Cross-Application Time Sheet (CA-TS). Details that specically apply to the
Cross-Application Time Sheet (CA-TS) are described in the following topics:
● Communication Channel Security
This topic describes the communication paths and protocols used by the Cross-Application Time Sheet
(CA-TS).
332
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
● Network Security
This topic describes the recommended network topology for the Cross-Application Time Sheet (CA-TS). It
shows the appropriate network segments for the various client and server components, and where to use
rewalls for access protection. It also includes a list of the ports needed to operate the Cross-Application
Time Sheet (CA-TS).
● Communication Destinations
This topic describes the information needed for the various communication paths, for example, which
users are used for which communications.
For more information, see the following sections in the SAP NetWeaver Security Guide:
● Network and Communication Security
● Security Guides for Connectivity and Interoperability Technologies
13.4.6.2.4.1 Communication Channel Security
The table below shows the communication channels used by the Cross-Application Time Sheet (CA-TS), the
protocol used for the connection, and the type of data transferred.
Communication Path Protocol Used Type of Data Transferred Data Requiring Special Pro
tection
Front-end client that uses
SAP GUI for Windows for the
application server
DIAG All customizing data, applica
tion data entered by Non-WD
applications
Passwords
Front-end client that uses a
Web browser for the applica
tion server
RFC, HTTP(S)
We recommend you use
HTTPS.
Application data entered by
WD applications and Web
Services
Passwords
DIAG and RFC connections can be protected using Secure Network Communications (SNC). HTTP
connections are protected using the Secure Sockets Layer (SSL) protocol.
Note
We strongly recommend using secure protocols (SSL, SNC) whenever possible.
For more information, see Transport Layer Security in the SAP NetWeaver Security Guide.
13.4.6.2.4.2 Network Security
You can operate Cross-Application Time Sheet (CA-TS) in dierent ways. You can run the Cross-Application
Time Sheet (CA-TS) and the HR system and or cProject system integrated on one system, or on dierent
instances.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 333

Firewall Settings
For more information, see Using Firewall Systems for Access Control in the SAP NetWeaver Security Guide.
For more information, see Using Multiple Network Zones in the SAP NetWeaver Security Guide.
Ports
The Cross-Application Time Sheet (CA-TS) runs on SAP NetWeaver and uses the ports from the AS ABAP.
For more information, see the topic for AS ABAP Ports in the corresponding SAP NetWeaver Security Guides.
For other components, for example, SAPinst, SAProuter, or the SAP Web Dispatcher, see https://
help.sap.com/viewer/ports.
13.4.6.2.4.3 Communication Destinations
Use
The table below shows an overview of the communication destinations used by the Cross-Application Time
Sheet (CA-TS).
Destination Delivered Type User, Authorizations Description
Cross-Application
Time Sheet (CA-TS) to
Human Resources
Management
No RFC Anonympus dialog
user specied in con
nections between both
systems
Customizing: Time
Sheet → Settings for All
User
Interfaces → Data
Transfer
for Distributed Systems
(ALE)
Cross-Application
Time Sheet (CA-TS) to
cProjects
No RFC Anonympus dialog
user specied in con
nections between both
systems
Customizing: Time
Sheet → Settings for All
User Interfaces → Data
Transfer
for Distributed Systems
(ALE)
334 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Destination Delivered Type User, Authorizations Description
WD Java Frontend to
Cross-Application
Time Sheet (CA-TS)
Yes RFC/JCo See Customizing Customizing:
Integration with Other
SAP Components →
Business Packages /
Functional Packages→
Manager Self Service
(mySAP ERP).
External consumer/
external Web UI to
Cross-Application
Time Sheet (CA-TS)
No HTTP(S) and SOAP
messages
Specic dialog user Cross-Application
Time Sheet (CA-TS)
acts as service pro
vider.
13.4.6.2.5 Data Storage Security
The Cross-Application Time Sheet (CA-TS) data is saved in databases of the SAP system as follows:
Data Location
Application Data CATSDB
Attachments and user-dened texts SAPScript storage
Templates CATS_TEMP
Transfer data for HR PTEX2000, PTEX2010, PTEXDIR
Transfer data for CO CATSCO
Transfer data for PS CATSPS
Transfer data for PM CATSPM
Transfer data for MM-SRV CATSMM
Transfer data for cPro DPR_CONF_LI
13.4.6.2.6 Enterprise Services Security
The following chapters in the SAP NetWeaver Security Guide and documentation are relevant for all enterprise
services delivered with Cross-Application Time Sheet (CA-TS):
● Web Services Security
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 335
● Recommended WS Security Scenarios
● SAP Process Integration Security Guide
13.4.6.2.7 Security-Relevant Logging and Tracing
Cross-Application Time Sheet (CA-TS) relies on the logging and tracing mechanisms from SAP NetWeaver:
● Auditing and Logging
● Tracing and Logging
13.4.6.2.8 Services for Security Lifecycle Management
The following services are available from Active Global Support to assist you in maintaining security in your
SAP systems on an ongoing basis.
Security Chapter in the EarlyWatch Alert (EWA) Report
This service regularly monitors the Security chapter in the EarlyWatch Alert report of your system. It tells you:
● Whether SAP Security Notes have been identied as missing on your system.
In this case, analyze and implement the identied notes, if possible. If you cannot implement the notes, the
report should be able to help you decide on how to handle the individual cases.
● Whether an accumulation of critical basis authorizations has been identied.
In this case, verify whether the accumulation of critical basis authorizations is okay for your system. If not,
correct the situation. If you consider the situation okay, you should still check for any signicant changes
compared to former EWA reports.
● Whether standard users with default passwords have been identied on your system.
In this case, change the corresponding passwords to non-default values.
Security Optimization Service (SOS)
The Security Optimization Service can be used for a more thorough security analysis of your system, including:
● Critical authorizations in detail
● Security relevant conguration parameters
● Critical users
● Missing security patches
336
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

This service is available as a self service within the SAP Solution Manager or as a remote or on-site service. We
recommend you use it regularly (for example, once a year) and in particular after signicant system changes or
in preparation of a system audit.
Security Conguration Validation
The Security Conguration Validation can be used to continuously monitor a system landscape for compliance
to predened settings, for example, from your company-specic SAP Security Policy. This primarily covers
conguration parameters, but it also covers critical security properties like the existence of a non-trivial
Gateway conguration or making sure standard users do not have default passwords.
Security in the RunSAP Methodology / Secure Operations Standard
With the E2E Solution Operations Standard Security service, a best practice recommendation is available on
how to operate SAP systems and landscapes in secure manner. It guides you through the most important
security operation areas and links to detailed security information from SAP's knowledge base wherever
appropriate.
More Information
For more details on these services see
● EarlyWatch Alert: https://support.sap.com/en/oerings-programs/support-services/earlywatch-
alert.html
● Security Optimization Service / Security Notes Report: https://support.sap.com/en/oerings-programs/
support-services/security-optimization-services-portfolio.html
● Comprehensive list of Security Notes: https://support.sap.com/en/my-support/knowledge-base/security-
notes-news.html
● Conguration Validation
● SAP Activate Methodology Roadmaps: https://support.sap.com/en/oerings-programs/methodologies/
implement.html
13.5 Manufacturing
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 337
13.5.1 Production Planning
13.5.1.1 Data Storage Security
Using Logical Path and File Names to Protect Access to the File System
Production Planning and Detailed Scheduling saves data in les in the le system. Therefore, it is important to
explicitly provide access to the corresponding les in the le system without allowing access to other
directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
The data storage security of SAP NetWeaver and components installed on the base is described in the SAP
NetWeaver Security Guide. All business data in SAP PP/DS is stored in the system database. If SAP LiveCache
is used, some business data is also stored there. This business data is protected by the authorization concept
of SAP NetWeaver and SAP PP/DS. In some special cases, business-relevant data is stored in another location,
such as a le system. The special case is listed below:
Logical File Names Used
The following logical le name has been created in order to enable the validation of physical le names:
● SAP SCM Optimizer
Logical Path Names Used
The logical le names listed above all use the following logical le paths:
● <drive>:\usr\SAP\<SID>\<Gxx>\log (for Windows)
● \usr\sap\<SID>\<Gxx>\log (for Linux)
<SID>: Gateway ID on the SAP SCM Optimizer server
<Gxx>: Gateway number
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
338
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out which
paths are being used by your system, you can activate the corresponding settings in the Security Audit Log.
For more information, see about data storage security, see the respective chapter in the SAP NetWeaver
Security Guide.
13.5.2 Manufacturing Execution for Discrete Industries
13.5.2.1 Authorizations for Just-in-Time-Processing
Just-in-Time Processing (JIT) uses the authorization concept provided by the SAP NetWeaver AS for ABAP.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS
Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used.
Authorization Object Description
C_AUTO_JIT ISAUTO_JIT: Sequenced JIT Calls (seqJC)
C_JIT_CALL PP-FLW JIT Calls
C_JIT_OUT IS-A-JIT: JIT Outbound Calls
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 339

13.5.2.2 Deletion of Personal Data (Just-in-Time-Processing)
Use
Just-in-Time-Processing (IS-A-JIT) might process data (personal data) that is subject to the data protection
laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components
Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Just-in-Time-Processing (IS-A-JIT) Archiving Object
JIT_SJCAL
JITO_CALL
ILM Object
JIT_SJCALL
JITO_CALL
Report
DELETE_JIT_VENDOR_CUSTOMER
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Just-in-Time-Processing (IS-A-JIT) WUC
Checks tables JITCU
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
340
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.5.2.3 Authorizations for Production Backush
Production Backush uses the authorization concept provided by the SAP NetWeaver AS for ABAP. Therefore,
the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS Security Guide
ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used.
Authorization Object Description
C_BCKFLUSH Automotive: Production backush
C_APO_PPC APO Authorization Object: Production Backush
13.5.2.4 Deletion of Personal Data (Production Backush)
Use
Production Backush might process data (personal data) that is subject to the data protection laws applicable
in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the blocking and
deletion of personal data. For more information, see the product assistance for SAP S/4HANA on the SAP Help
Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components Data
Protection .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 341

Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Production Backush (IS-A-PPC) Archiving Object
PP_CONF
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
13.5.3 Quality Management
13.5.3.1 Internet Communication Framework Security (ICF)
You should only activate those services that are needed for the applications running in your system. For quality
management the following services are needed for the respective Web Dynpro applications:
● QI_INSPECTIONLOT_DETAIL_APP
● QI_RECORD_RESULTS_APPL
● QI_RECORD_RESULTS_ETI_APPL
Use the transaction SICF to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information about ICF security, see the respective chapter in the SAP NetWeaver Security Guide.
13.5.3.2 Communication Channel Security
The table below shows the communication channels used, the protocol used for the connection, and the type
of data transferred.
342
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Communication Path Protocol Used Type of Data Transferred Data Requiring Special Pro
tection
Communication with Sup
plier Network Collaboration
SOAP Quality notication data
Communication with the
Quality Inspection Engine
(QIE) of the Extended
Warehouse Management
(EWM)
SOAP, RFC Inspection lot data
Communication exchange of
quality certicates with ex
ternal partner
IDoc Quality certicates Digital signature
Quality master data replica
tion
IDoc Master inspection character
istics
Master inspection methods
Codes
Inspection plan
Communication with external
subsystem for inspection
RFC, SOAP Inspection lot data
Inspection results
Communication with external
subsystem for statistical
process control (SPC)
RFC Inspection lot data
Inspection results
Communication with SAP
Manufacturing Execution
(ME)
RFC, IDoc Inspection lot data
Inspection results
DIAG and RFC connections can be protected using Secure Network Communications (SNC). HTTP
connections are protected using the Secure Sockets Layer (SSL) protocol. SOAP connections are protected
with Web services security.
Note
We strongly recommend using secure protocols (SSL, SNC) whenever possible.
For more information, see Transport Layer Security and Web Services Security in the SAP NetWeaver Security
Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 343
13.5.3.3 Deletion of Personal Data
The Quality Management application might process data (personal data) that is subject to the data protection
laws applicable in specic countries as described in SAP Note 1825544.
The SAP Information Lifecycle Management (ILM) component supports the entire software lifecycle including
the storage, retention, blocking, and deletion of data. The Quality Management application uses SAP ILM to
support the deletion of personal data as described in the following sections.
SAP delivers an end of purpose check for the Quality Management application.
End of Purpose Check (EoP)
An end of purpose check determines whether data is still relevant for business activities based on the retention
period dened for the data. The retention period of data consists of the following phases.
● Phase one: The relevant data is actively used.
● Phase two: The relevant data is actively available in the system.
● Phase three: The relevant data needs to be retained for other reasons.
For example, processing of data is no longer required for the primary business purpose, but to comply with
legal rules for retention, the data must still be available. In phase three, the relevant data is blocked.
Blocking of data prevents the business users of SAP applications from displaying and using data that may
include personal data and is no longer relevant for business activities.
Blocking of data can impact system behavior in the following ways:
● Display: The system does not display blocked data.
● Change: It is not possible to change a business object that contains blocked data.
● Create: It is not possible to create a business object that contains blocked data.
● Copy/Follow-Up: It is not possible to copy a business object or perform follow-up activities for a business
object that contains blocked data.
● Search: It is not possible to search for blocked data or to search for a business object using blocked data in
the search criteria.
It is possible to display blocked data if a user has special authorization; however, it is still not possible to create,
change, copy, or perform follow-up activities on blocked data.
For information about the conguration settings required to enable this three-phase based end of purpose
check, see the Process Flow.
344
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
Inspection Lot The EOP check considers partners
(customers or vendors):
● that are stored directly in the in
spection lot (table QALS)
● that are available in the worklist of
the transfer table for subsystems
(QIWL)
● that are used in control charts
(QASH)
● that are assigned to a multiple
specication (QAOBJMS)
Each inspection lot is checked if the a
customer or supplier is still relevant. If a
customer or vendor is used in several
objects, he is relevant as long as only
one object is not completed. An object
is completed if
● an inspection lot is canceled
● an inspection lot has status All
inspections completed, an usage
decision was made and stock post
ings are completed if the inspec
tion lot is stock-relevant.
● Control charts are closed.
The following data is relevant for calcu
lating the retention rules and residence
rules (taking the latest date):
● Date of usage decision
● Last change date of the usage de
cision
● Last change date of the control
chart (if applicable)
You can start report
QM_CVP_EOP_SORT_ARC_CONTROL
to select all data that has already been
archived (backround job due to per
formance).
Archiving object QM_CONTROL
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 345
Application Object Detailed Description Provided Deletion Functionality
Sample Records Partners are assigned to the drawing of
material samples.
Material samples are only considered if
there are not part of an order, an in
spection lot or a notication since these
material samples are considered as se
perate business operations and are
checked during the EoP check for the
corresponding object (e.g. notication).
Only 'independent' material samples
are checked.
The assigned partners are no longer rel
evant, if the material sample is marked
for deletion or marked as no longer ex
istent. Then the latest change date is
taken as basis for the calculation of the
retention and residence rules.
You can start report
QM_CVP_EOP_SORT_ARC_SAMPLE to
select all data that has already been ar
chived (backround job due to perform
ance).
Archiving object QM_SAMPLE
346 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Object Detailed Description Provided Deletion Functionality
Quality Certicate
Only suppliers are relevant. Suppliers
are entered directly in the certicate.
A certicate is completed if it has one of
the following statuses:
● Certicate led and inspected
● Certicate receipt canceled
● Certifcate defective
If you want to send or receive the qual
ity data of a certicate using EDI, and
the inspection characteristics to be
sent have dierent descriptions in the
supplier and the customer system you
can set up a partner-specic identica-
tion and assignment of the respective
characteristics (characteristic map
ping). The communication partners are
dened by Partner Type and Partner
Number.
For the deletion of the partner-specic
settings and characteristic mappings
you have to run deletion report
RDEL_PARTNER_CHAR.
Archiving object QM_CERT
Failure Mode and Eects Analysis Only business partners on header level
are checked. Business partners entered
for actions are not checked.
It is checked that the FMEA has status
Completed, To Be Archived, or Archived.
You can start report
PLM_FMEA_EOP_AUD_ARC_EXTRACT
to select all data that has already been
archived.
Archiving object QM_FMEA
Audit Plans/Audits It is checked that the Audit has status
Completed, To Be Archived, or Archived.
Only audits are taken into account in
the check, but not audit plans or ques
tion lists.
You can start report PLM_AU
DIT_EOP_AUD_ARC_EXTRACT to se
lect all data that has already been ar
chived.
Archiving object PLM_AUD
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 347

Relevant Application Areas and Available EoP Functionality
Application Implemented Solution Further Information
Quality Management EoP check This includes the business in areas of:
● Quality Planning (QM-PT)
● Quality Inspection (QM-IM)
● Audit Management (CA-AUD)
Process
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available.
3. You do the following:
1. Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA).
2. Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner
3. Run transaction IRMPOL and maintain the required residence and retention policies for the customer
master and vendor master in SAP ERP (ILM objects: FI_ACCPAYB, FI_ACCRECV; for ILM objects in QM
see archiving objects above)
4. Run transaction CVP_PRE_EOP to enable the end of purpose check function for the customer master
and vendor master in SAP ERP
4. Business users can request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
5. If you have the needed authorizations, you can unblock data by running the transaction BUPA_PRE_EOP
and CVP_UNBLOCK_MD.
6. You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of Quality Management.
13.5.4 Maintenance Operations
13.5.4.1 Authorizations in Plant Maintenance
Standard Roles
SAP delivers business role templates which follow the naming convention SAP_BR_*. The delivered business
role templates are designed to cover typical activities of business users with a certain job prole.
348
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Example
The delivered business role template SAP_BR_MAINTENANCE_TECHNICIAN is designed for maintenance
technicians. The role contains business catalogs which cover all the functions that a maintenance technician
requires to carry out their work eectively and safely.
Another example business role template SAP_BR_MAINTENANCE_PLANNER is designed for maintenance
planners. The role contains business catalogs which cover a broad range of functions necessary for planning
and executing maintenance activities.
Each business catalog contains one or more applications and is designed to support segregation of duty.
Note
For more information about how to create roles, see Role Administration [page 16].
13.6 R&D / Engineering
13.6.1 Product Safety and Stewardship
13.6.1.1 Product Development for Discrete Industries
13.6.1.2 Product Compliance for Discrete Industries
13.6.1.2.1 User Administration and Authentication
Product Compliance for Discrete Industries uses the authorization concept provided by SAP NetWeaver.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver Security
Guide also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG).
For more generic information see User Administration and Authentication [page 13] in the Introduction section
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 349
13.6.1.2.1.1 User Management
The table below shows the standard users that are necessary for operating Product Compliance for Discrete
Industries. For more generic information, see User Management [page 13] in the Introduction section.
User ID Type Password Description
Business processing user Dialog user To be entered Business user of Product
Compliance
E-mail inbound processing
user
Communication user Not needed User to process the incoming
e-mails of Product
Compliance
Workow engine batch user Background user Not needed User for the background
processing of workows in
Product Compliance
You need to create users after the installation. Users are not automatically created during installation. In
consequence, there is no requirement to change user IDs and passwords after the installation.
Note
Several business processes within Product Compliance for Discrete Industries use SAP Business Workow
and e-mail inbound and outbound processing. It is not recommended that you grant the corresponding
system users (such as WF_BATCH for Workow System or SAPCONNECT for e-mail inbound processing)
all authorizations of the system (SAP_ALL).
13.6.1.2.2 Network and Communication Security
Your network infrastructure is important for protecting your system. Therefore, your network must support the
communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats based on software aws (at both the operating system
level and application level) or network attacks such as eavesdropping. If users cannot log on to your application
or database servers at the operating system or database layer, then there is no way for intruders to
compromise the machines and gain access to the backend system’s database or les. Additionally, if users are
not able to connect to the server LAN (local area network), they cannot exploit known bugs and security holes
in network services on the server machines.
The network topology for Product Safety and Stewardship is based on the topology used by the SAP NetWeaver
platform. Therefore, the security guidelines and recommendations described in the SAP NetWeaver Security
Guide also apply here. Details that specically apply to Product Safety and Stewardship are described in the
following sections:
● Communication Channel Security [page 355]
This topic describes the communication paths and protocols.
● Network Security [page 356]
350
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
This topic describes the recommended network topology. It shows the appropriate network segments for
the various client and server components and where to use rewalls for access protection. It also includes
a list of the ports required.
● Communication Destinations [page 356]
This topic describes the information needed for the various communication paths, for example, which
users are used for which communications.
For more information, see the following sections in the SAP NetWeaver Security Guide:
● Network and Communication Security
● Security Guides for Connectivity and Interoperability Technologies
13.6.1.2.2.1 Communication Destinations
The table below shows an overview of the communication destinations used by Product Compliance for
Discrete Industries. For more generic information, see in corresponding chapter in the Introduction section.
Destination Delivered Type Description
<PM system> No RFC Connection to plant maintenance system
<BuPa system> No RFC Connection to business partner system
<AC system> No RFC Connection to accounting system
<EHS system> No RFC Connection to SAP Product Safety and Stewardship as
part of SAP ERP system
Note
The user in the remote AC system needs to have all authorizations as proposed by the respective EHS user
roles.
For SAP EHS Management as part of SAP ERP, Product Compliance for Discrete Industries does not
provide any authorizations.
For detailed information about communication destinations, see Customizing for Environment, Health, and
Safety
under Foundation for EHS Integration Specify Destinations for Integration .
13.6.1.2.3 ICF Security in Product Safety and Stewardship
To use an app in Product Safety and Stewardship, you have to activate the internet communication framework
(ICF) service that is needed for this app.
For general information, see ICF Security [page 20] in the Introduction section.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 351
Product Compliance for Discrete Industries
To use Product Compliance for Discrete Industries apps, proceed as follows:
● In your back-end system, open transaction SICF. Under /default_host/sap/bc/webdynpro/sap/,
activate the following Web Dynpro services:
○ that start with EHFND
○ that start with EHPRC
○ POWL
○ IBO_WDA_INBOX
○ WDR_CHIP_PAGE
13.6.1.2.4 Data Storage Security
Using Logical Path and File Names to Protect Access
In Product Compliance for Discrete Industries, several applications save data in les in the le system. The
International Material Data System (IMDS) uses the le system to store downloaded les temporarily, before
they are imported. Additionally, it is possible for users to upload les to the application server manually prior to
further processing. Therefore, it is important to explicitly provide access to the corresponding les in the le
system without allowing access to other directories or les (also known as directory traversal). This is achieved
by specifying logical paths and le names in the system that map to the physical paths and le names. This
mapping is validated at runtime, and, if access is requested to a directory that does not match a stored
mapping, an error occurs.
The following lists show the logical le names and paths used by Product Compliance for Discrete Industries
and for which programs these le names and paths apply:
Logical File Names Used
The following logical le names have been created in order to enable the validation of physical le names:
● EHPRC_IMPORT_DIR
● EHPRC_ERROR_DIR
● EHPRC_ARCHIVE_DIR
For more information, see the Customizing activity Set Up Directory Structure for IMDS.
Logical Path Names Used
The logical le names listed above all use the logical le path EHPRC_HOME_PATH.
352
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out
which paths are being used by your system, you can activate the corresponding settings in the Security Audit
Log.
For more information about data storage security, see the respective chapter in the SAP NetWeaver Security
Guide.
13.6.1.2.5 Virus Scanning
The interactive forms of Product Compliance for Discrete Industries can contain JavaScript. Therefore,
JavaScript must be enabled in Adobe Acrobat Reader. In addition, e-mails with PDF attachments that contain
JavaScript must not be ltered out in the e-mail inbound and outbound process.
For more generic information see Virus Scanning [page 23] in the Introduction section.
13.6.1.3 Product Safety and Stewardship for Process
Industries
This section contains information that is valid for:
● Basic Data and Tools
● Product Safety
● Global Label Management
● Dangerous Goods Management
13.6.1.3.1 Technical System Landscape
Product Safety
Expert is a registering Remote Function Call (RFC) server that reads and writes specication data through RFC
from the SAP system.
Windows Wordprocessor Integration (WWI) is a registering RFC server that generates and prints reports.
Report shipping can be determined centrally in the product safety system, or product safety document data
can be distributed by ALE/IDOC to logistics systems. These logistics systems use their own WWI generation
servers (WWI servers) to print documents.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 353
Dangerous Goods Management
If you use separate logistics systems, dangerous goods data can be transferred to logistics systems by ALE/
IDOC.
Global Label Management
The technical system landscape for Global Label Management consists of the following elements:
● WWI is a registering RFC server. It can contain its own database that is used as a document cache and data
cache.
● Option 1: Label printing is possible with a printer that is connected to a local PC. WWI servers are hosted on
a central WWI server farm. Printing is executed by the SAP spool system or a printer that is connected to a
local PC.
● Option 2: Label printing is executed through print requests. WWI servers are decentralized. Therefore, the
data of the print requests is sent directly to the printer, or the print requests are printed through the SAP
spool system.
● Option 3: Label printing is possible via an extraordinary, distributed approach for product safety. In this
case, plants host their own SAP systems. Document data is maintained centrally and distributed by ALE.
Printing is determined directly or through the SAP spool system.
13.6.1.3.2 User Administration and Authentication
Product Safety and Stewardship for Process Industries uses the administration and authentication mechanisms
provided with the SAPNet Weaver platform.
For more generic information see User Administration and Authentication [page 13] in the Introduction section.
13.6.1.3.3 Network and Communication Security
Your network infrastructure is important for protecting your system. Therefore, your network must support the
communication necessary for your business needs without allowing unauthorized access. A well-dened
network topology can eliminate many security threats based on software aws (at both the operating system
level and application level) or network attacks such as eavesdropping. If users cannot log on to your application
or database servers at the operating system or database layer, then there is no way for intruders to
compromise the machines and gain access to the backend system’s database or les. Additionally, if users are
not able to connect to the server LAN (local area network), they cannot exploit known bugs and security holes
in network services on the server machines.
The network topology for Product Safety and Stewardship is based on the topology used by the SAP NetWeaver
platform. Therefore, the security guidelines and recommendations described in the SAP NetWeaver Security
354
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Guide also apply here. Details that specically apply to Product Safety and Stewardship are described in the
following sections:
● Communication Channel Security [page 355]
This topic describes the communication paths and protocols.
● Network Security [page 356]
This topic describes the recommended network topology. It shows the appropriate network segments for
the various client and server components and where to use rewalls for access protection. It also includes
a list of the ports required.
● Communication Destinations [page 356]
This topic describes the information needed for the various communication paths, for example, which
users are used for which communications.
For more information, see the following sections in the SAP NetWeaver Security Guide:
● Network and Communication Security
● Security Guides for Connectivity and Interoperability Technologies
13.6.1.3.3.1 Communication Channel Security
The following table lists the communication paths used by Product Safety and Stewardship for Process
Industries, the protocol used for the connection, and the type of data transferred.
Communication Path Protocol Used Type of Data Transferred Data Requiring Special Pro
tection
SAP PS&S for Process Indus
tries Application Server to
SAP BP Application Server
RFC Business Partner -
SAP PS&S for Process Indus
tries Application Server to
SAP PM Application Server
RFC Plant Maintenance -
SAP Logistics Application
Server to SAP PS&S for Proc
ess Industries Application
Server
RFC Logistics data for Report
Shipping
Logistics data for Substance
Volume Tracking
-
SAP PS&S for Process Indus
tries Application Server to
SAP Logistics Application
Server
ALE /IDOC Application data
Dangerous Goods data and
Reports can be transferred to
logistics systems
-
SAP Application Server to Ex
pert Server
RFC Application data Substance data may contain
corporate secrets such as
recipes.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 355
SAP Application Server to
WWI generation server (WWI
server)
RFC Application data, documents Usually MSDS or label data is
transferred. Depending on
the process, incident reports
that contain personal data or
corporate secrets may also
be transferred.
SAP PS&S for Process Indus
tries Application Server to
SAP Logistics Application
Server
RFC Application data:
For Global Label Manage
ment, material data is trans
ferred from logistics system
to the Product Safety system
-
Only for Global Label Man
agement systems with many
WWI servers:
WWI server to SQL database
server
TCP/IP
DB-specic protocol
Label data Usually no sensitive data, de
pending on the usage of the
label.
Note
Protect RFC connections with Secure Network Communications (SNC).
Use secure protocols (SSL, SNC) whenever possible.
13.6.1.3.3.2 Network Security
Ports
WWI generation servers (WWI servers) and Expert servers use Remote Function Call (RFC).
For more information, see https://help.sap.com/viewer/ports.
13.6.1.3.3.3 Communication Destinations
The table below lists the communication destinations that are used by Product Safety and Stewardship for
Process Industries.
For a description of the purpose of the RFC destinations, see the Customizing activities mentioned for Product
Safety and Stewardship for Process Industries.
Destination Delivered Type User, Authorizations Description
356 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Basic Data and
Tools Basic
Settings
Specify
Environment
Parameters
Environment parame
ter DEST_BU
No RFC RFC destination for
Business Partner
Basic Data and
Tools Basic
Settings
Specify
Environment
Parameters
Environment parame
ter DEST_HR
No RFC RFC destination for HR
Basic Data and
Tools Basic
Settings
Specify
Environment
Parameters
Environment parame
ter DEST_PM
No RFC RFC destination for
Plant Maintenance
Basic Data and
Tools Basic
Settings
Specify
Environment
Parameters
Environment parame
ter DEST_SRE_DS
No RFC RFC destination of
Report Shipping
Basic Data and
Tools Basic
Settings
Specify
Environment
Parameters
Environment parame
ter
SVT_EHS_RFCDEST
No RFC RFC destination for
Substance Volume
Tracking
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 357

Basic Data and
Tools Basic
Settings
Specify
Environment
Parameters
Environment parame
ter
WWI_GENSERVER_SYN
_DEST
No RFC Calling user Synchronous genera
tion of reports
Basic Data and
Tools Report
Denition
Window
Wordprocessor
Integration (WWI)
Conguration of
Generation PCs
Conguration of
Generation Servers
Manual Conguration
of Generation Servers
Specify Generation
Servers
Maintain the destina
tion
No RFC Congured Back
ground Job user See
Customizing activity
Start WWI Dispatcher
in Background
Background genera
tion of reports
Global Label
Management
Prerequisites for Global
Label Management
Dene WWI Settings
Congure WWI Server
for Print Request
Generation
No RFC Calling User Print and preview ta
bles in Global Label
Management
358 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Global Label
Management
Prerequisites for Global
Label Management
Dene WWI Settings
Congure WWI Server
for Print Request
Generation
No RFC Calling User or Cong-
ured background job
user
See Customizing activ
ity Background Jobs for
Processing Print
Requests
Process print requests
in Global Label
Management
Basic Data and
Tools Basic
Settings
Manage
User Exits
No RFC Calling User Determine secondary
data for specications
with Expert
Basic Data and
Tools Basic
Settings
Specify
Environment
Parameters
No RFC Calling User Mass change of speci
cation data with Easy
Expert
Note
The WWI servers and the Expert servers are registering RFC servers.
For more information about setting up RFC destinations, see the Customizing for Product Safety and
Stewardship
under Basic Data and Tools Tools Expert Set Up RFC Destination.
13.6.1.3.4 Application-Specic Virus Scan Prole (ABAP)
SAP provides an interface for virus scanners to prevent manipulated or malicious les from damaging the
system. To manage the interface and to nd out which le types are checked or blocked, use the virus scan
proles. Some applications rely on default proles, while others rely on application-specic proles.
To use a virus scanner with the SAP system, you must activate and set up the virus scan interface. During this
process, you also set up the default behavior. Here, SAP also provides the following default proles:
Application Prole Allowed MIME Types Blocked MIME Types
Product Safety and Steward
ship for Process Industries
/CBUI/WWI_REPORT_GEN
* -
Global Label Management
/CBGLMP_API/
WWI_GET_CONTENT
* -
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 359
When the application-specic virus scan prole is activated, this prole has the following impact:
● Documents generated by the WWI generation server (WWI server) are scanned for viruses
● Documents imported into Product Safety and Stewardship for Process Industries are scanned for viruses
13.6.1.3.5 Data Storage Security
For importing or exporting data between two SAP systems or an SAP system and an external system, Product
Safety and Stewardship for Process Industries uses transfer les.
After generating a transfer le either by exporting data or uploading a transfer le from a PC le system, the
transfer le is stored on the application server. If the export is started again or a new le is uploaded form a PC
le system, the transfer le that is stored on the application server will be overwritten.
Note
The transfer le of imported specication data is stored in le substance.dat on the application server. The
transfer le path is congured in logical path EHS_IMP_SUBSTANCES_PATH_2.
Using Logical Path and File Names to Protect Access
When importing or exporting data, Product Safety and Stewardship for Process Industries saves data in les in
the le system. Therefore, it is important to explicitly provide access to the corresponding les in the le
system without allowing access to other directories or les (also known as directory traversal). This is achieved
by specifying logical paths and le names in the system that map to the physical paths and le names. This
mapping is validated at runtime and if access is requested to a directory that does not match a stored
mapping, then an error occurs.
The following lists show the logical le names and paths used when importing or exporting data, and for which
programs these le names and paths apply:
Logical File Names Used in Export and Import
The following logical le names have been created in order to enable the validation of physical le names:
Logical File Names Programs Using these Logical File Names
EHS_EXP_PHRASES_2
Export of Phrase Libraries
EHS_EXP_ PROPERTY_TREE_2
Export of Property Tree
EHS_EXP_SOURCES_2
Export of Sources
360 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

EHS_EXP_SUBSTANCES_2
Export of Specication Master Data
EHS_EXP_TEMPLATE_2
Export of Report Templates
EHS_IMP_PHRASES_2
Import of Phrase Libraries
EHS_IMP_ PROPERTY_TREE_2
Import of Property Tree
EHS_IMP_SOURCES_2
Import of Sources
EHS_IMP_SUBSTANCES_2
Import of Specication Master Data
EHS_IMP_TEMPLATE_2
Import of Report Templates
EHS_IMP_REPORT_2
Import of Reports
EHS_FTAPPL_2
Uploade File; Downloade File
Logical Path Names Used During Export and Import
These logical le names use the following logical le path:
Logical File Names Logical Path Names
EHS_EXP_PHRASES_2 EHS_EXP_PHRASES_PATH_2
EHS_EXP_PROPERTY_TREE_2 EHS_EXP_PROPERTY_TREE_PATH_2
EHS_EXP_SOURCES_2 EHS_EXP_SOURCES_PATH_2
EHS_EXP_SUBSTANCES_2 EHS_EXP_SUBSTANCES_PATH_2
EHS_EXP_TEMPLATE_2 EHS_EXP_TEMPLATE_PATH_2
EHS_FTAPPL_2 EHS_FTAPPL_PATH_2
EHS_IMP_PHRASES_2 EHS_IMP_PHRASES_PATH_2
EHS_IMP_PROPERTY_TREE_2 EHS_IMP_PROPERTY_TREE_PATH_2
EHS_IMP_REPORT_2 EHS_IMP_REPORT_PATH_2
EHS_IMP_SOURCES_2 EHS_IMP_SOURCES_PATH_2
EHS_IMP_SUBSTANCES_2 EHS_IMP_SUBSTANCES_PATH_2
EHS_IMP_TEMPLATE_2 EHS_IMP_TEMPLATE_PATH_2
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 361

Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out
which paths are being used by your system, you can activate the corresponding settings in the Security Audit
Log (transaction SM19).
Relevant audit log numbers:
● DUA – EHS-SADM: Service &A on client &B created
● DUB – EHS-SADM: Service &A on client &B started
● DUC – EHS-SADM: Service &A on client &B stopped
● DUD – EHS-SADM: Service &A on client &B stopped
● DUE – EHS-SADM: Conguration of service &A on client &B was changed
● DUF – EHS-SADM: File &A from client &B transferred
● DUG – EHS-SADM: File &A transferred to client &B
13.6.1.3.5.1 Data Storage on WWI Servers and Expert Servers
Windows Wordprocessor Integration (WWI) and Expert read data from the SAP system using Remote Function
Call (RFC), process data, and store the results in the database of the SAP system. That is, the WWI generation
server (WWI server) and the Expert server save conguration data and cached data locally.
Note
Make sure that only as few users as possible can access the Windows servers that run the WWI server and
the Expert server.
To apply access permissions in Windows, execute the following steps for the following folders.
For more information on access control and on security auditing, see the Windows Help.
To congure access control for a local le or folder, proceed as follows:
1. Start the Windows Explorer.
2. In the context menu of the le or the folder that you want to audit, choose Properties, and go to the
Security tab page.
3. Choose Edit.
4. Add or remove the user names and set the permissions for each user.
Note
To improve data storage security, you can apply Windows le system encryption to the folders that hold
sensitive data.
362
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Expert Cache
If you use the specication data cache of Expert, it stores copies of the specication data locally in the Expert
server le system. The root folder of the cache is determined in the registry at HKEY_LOCAL_MACHINE
\SOFTWARE\Wow6432Node\TechniData\EHS-AddOns\CacheRoot.
To protect data, make sure that you set appropriate access permissions on the congured root folder of the
cache. Grant read or write access only to LocalSystem, to administrators and to selected users.
Expert Rules
Apply access permissions to the Expert rules directory. Expert rules are programs that are executed by Expert
altering specication data. Make sure that the rules are not altered by unauthorized users.
The rules are usually stored in the Rules folder of the Expert installation, but each rule can be congured
separately in the Windows Registry. For more information on the paths to the rules les, see
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\TechniData\EHS-AddOns\Instances.
Set appropriate access permissions on the Expert rules folder. Grant access only to LocalSystem,to
administrators and to selected users.
WWI Root Directory
WWI temporarily stores data in the Windows le system to process data in the WWI root directory.
If an error occurs, the temporary les might remain in the root directories. We recommend cleaning up the
folder regularly.
The path that indicates the WWI root directory depends on the process. For more information about the path,
check the Customizing settings for Product Safety and Stewardship for Process Industries.
● For synchronous generation, check the environment parameter WWI_GENSERVER_SYN_ANCHOR under
Basic Data and Tools Basic Settings Specify Environment Parameters
● For background generation, check the WWI root under Basic Data and Tools Report Denition
Windows Wordprocessor Integration (WWI) Conguration of Generation PCs Conguration of
Generation Servers
Manual Conguration of Generation Servers Specify Generation Servers
● For Global Label Management, check the temporary directory for synchronous WWI server under Global
Label Management Set Basic Data and Tools for Global Label Management Make Settings for Basic
Data
● For print request processing in Global Label Management, check HKEY_CLASSES_ROOT\WWIDOCUMENT
\AnchorRoot in the Windows registry.
Grant access on the WWI root folders only to LocalSystem,to administrators and to selected users.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 363

WWI Print Request Cache for Global Label Management
WWI caches templates and generated labels in the Windows le system.
The path that indicates the Windows le system is congured in the WWI.INI le under [DMS]. Set the
appropriate access permissions on the WWI root directories. Grant read or write access only to the WWI user,
to the
LocalSystem, to administrators and to selected users.
The database le or database connection is congured under dbConnection in the WWI.INI le: Set
appropriate access permissions on the database le or in the congured database management system. Grant
access only to the WWI user, to LocalSystem,to administrators and to selected users.
13.6.1.3.6 Dispensable Functions with Impacts on Security
You can compile and display system information for Windows Wordprocessor Integration (WWI) as follows:
● You can display system information in the WWI Monitor (transaction CG5Z): In the menu, choose Utilities
Test Server
● In WWI.INI, under [Global], enter as DisableWwiServerInfo the value 1. This prevents external access to
the WWI system information (through the WWI Server Monitor, for example). The default value is 0.
13.6.1.3.7 Security for Additional Applications
Windows Authorization for Windows Wordprocessor Integration
Windows Wordprocessor Integration (WWI) requires a Windows user account that is used to run the WWI
generation server services. This is because many printer settings and settings for Microsoft Word are user-
specic.
As an abbreviation, the user account is called WWI user.
● Create a new Windows user. This user is used to execute the WWI generation server (WWI server). The user
can be a local user or a domain user. We recommend creating a local user, for example, WWI-USER. Assign
this user to the Main users group or the Users group. Use a password that does not expire.
● In Microsoft Windows Vista, in Microsoft Windows Server 2008 and higher releases, assign the WWI user to
the administrators group.
● If the user is a domain user, ensure that the prole of the user is local.
● Check the security settings for the user that is used to execute the WWI server:
○ The user must have the Log on as a service authorization. In Microsoft Windows XP, Microsoft Windows
Server 2003 and higher releases, also set this authorization for users of the administrators group. You
can nd this authorization in the Control Panel under Administrative Tools Local Security Policy .
Navigate to
Local Policies User Rights Assignment . Here, you assign the user privileges to the
guideline Log on as a service.
○ Check the DCOM start authorization and access authorization for Microsoft Word using the
DCOMCNFG.EXE conguration program. For more information, see the SAP Note 580607 .
364
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

○ Ensure that the user has write (change) authorization for the WWI root directory. We recommend using
a local directory. The WWI work directory is congured in the Specify Generation Servers Customizing
activity.
○ Make sure that the Microsoft Windows TEMP directory exists. The TEMP directory is congured in
Microsoft Windows under Control Panel System Advanced Environment Variables . There,
check the user variables and system variables TMP and TEMP.
○ Ensure that the user has write (change) authorization for the Microsoft Windows TEMP directory.
For further information, see SAP Note 580586 .
Windows Authorization for Expert
The Expert server service is run as a local system account.
Windows Authorization for Administration Management Server
The Administration Management Server service is run as a local system account.
13.6.1.3.8 Security-Relevant Logging and Tracing
Windows Wordprocessor Integration (WWI) and Expert log all processing information in the Windows
Application Event Log. A separate Security Log for WWI and Expert does not exist. For security relevant
information from Windows, check the Windows Security Event Log.
For more information on maintaining a secure environment in Windows servers, check the Microsoft Windows
Security Guide and the Microsoft Security Compliance Manager.
Tracking Conguration Changes
To track conguration changes of WWI and Expert Server Administration that are executed by WWI and Expert
Server Administration (transaction CGSADM), enable the security audit log in the Security Audit (transaction
SM19).
Relevant audit log numbers:
● DUA – EHS-SADM: Service &A on client &B created
● DUB – EHS-SADM: Service &A on client &B started
● DUC – EHS-SADM: Service &A on client &B stopped
● DUD – EHS-SADM: Service &A on client &B stopped
● DUE – EHS-SADM: Conguration of service &A on client &B was changed
● DUF – EHS-SADM: File &A from client &B transferred
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 365

● DUG – EHS-SADM: File &A transferred to client &B
For more information on conguration changes, change documents are used. Creating change documents in
WWI and Expert Server Administration is enabled by default. To switch o the creation of change documents,
set the environment parameter CGSADM_NO_CHANGE_DOCS in the Specify Environment Parameters
Customizing activity to X.
To display change documents, start the program RSSCD110 (Display change documents (cross-client)) and
choose object class
ESSADM.
Tracking Conguration with Windows Features
To track WWI and Expert conguration changes, enable auditing in the Windows le system. For more
information on Access Control and Security Auditing, see the Windows Help.
Before setting up auditing for les and folders, enable object access auditing by dening auditing policy
settings for the object access event category.
To dene or modify auditing policy settings for an event category for your local computer, proceed as follows:
1. Choose Control Panel Administrative Tools Local Security Policy.
2. In the console tree, go to Local Policies Audit Policy.
3. 3.In the results pane, choose Audit object access to enable the auditing policy settings.
To congure auditing settings for a local le or folder, proceed as follows:
1. Open Windows Explorer.
2. In the context menu of the le or folder that you want to audit, choose Properties and go to the Security tab
page.
3. Choose Edit, and then choose Advanced.
4. In the Advanced Security Settings go to the Auditing tab page.
To congure auditing settings for a registry key:
1. Open Registry Editor.
2. Go to the registry key.
3. In the context menu of the registry key that you want to audit, choose Permissions.
4. On the Security tab page, choose Advanced.
5. In the Advanced Security Settings, choose the Auditing tab page.
Windows Wordprocessor Integration (WWI)
For WWI, the following les and folders must be covered by change auditing:
● WWI.INI
● SAPRFC.INI
● GRAPHICS
● Registry key: HKEY_CLASSES_ROOT\WWIDOCUMENT
366
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Expert
For Expert, the following les and folders must be covered by change auditing:
● SAPRFC.INI
● RULES
● Registry key: HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\TechniData\EHS-AddOns
\Instances
For 32bit systems, omit Wow6432Node
● Registry key: HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\TechniData\EHS-AddOns\Systems
For 32bit systems, omit Wow6432Node
13.6.2 Enterprise Portfolio and Project Management
13.6.2.1 Project System
13.6.2.1.1 Deletion of Personal Data
Use
The Project System might process data (personal data) that is subject to the data protection laws
applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components
Data Protection .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 367

Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
Project System (PS) The archiving objects are used for ar
chiving and deleting operative objects
and standard networks in the Project
System
Archiving Objects:
● PS_PROJECT
● PS_PLAN
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Project System (PS)
EoP An end of purpose check determines
whether data is still relevant for busi
ness activities based on the retention
period dened for the data. This check
is determined based on the date on
which the network activity is set to the
closed status. For more information, re
fer to sections
Process Flow and Con
guration: Simplied Blocking and
Deletion
.
368 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Implemented Solution (EoP or WUC) Further Information
Project System (PS) WUC A where-used check is a simple check
to ensure data integrity in case of po
tential blocking. The WUC in application
Project System checks whether any de
pendent data exists for:
● A certain customer in RSADD,
VSRSADD_CN, COFP, COER,
QMSM, QMUR, QMEL, IHPA.
● A certain vendor in RSADD,
VSRSADD_CN, AFVC,
VSAFVC_CN, RESB, VS_RESB_CN,
COFP, QMSM, QMUR, QMEL, IHPA.
● A certain contact person in QMSM,
QMUR, IHPA.
● A certain cBP in AD01DLI,
PSACL_TAB.
Note
If dependent data exists, that is, if
the data is still required for busi
ness activities, the system does not
block the corresponding customer,
vendor, or cBP. If you still want to
block data, the dependent data
must be deleted by using the exist
ing archiving and deletion tools or
by using any other customer-spe
cic solution.
Process Flow
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available.
3. You do the following:
○ Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA).
○ Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner.
○ Run transaction IRMPOL and maintain the required residence and retention policies for the customer
master and vendor master (ILM objects: FI_ACCPAYB, FI_ACCRECV, FI_ACCKNVK).
○ Run transaction CVP_PRE_EOP to enable the end of purpose check function for the customer master
and vendor master.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 369

4. Business users can request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
5. If you have the needed authorizations, you can unblock data by running the transaction BUPA_PRE_EOP
and CVP_UNBLOCK_MD.
6. You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of PS.
For information about how to congure blocking and deletion for PS, see Conguration: Simplied Blocking and
Deletion.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in
Customizing for Cross-Application Components under Data Protection .
● Dene the settings for authorization management under Data Protection Authorization
Management . For more information, see the Customizing documentation.
● Dene the settings for blocking in Customizing for Cross-Application Components under Data
Protection Blocking and Unblocking of Data Business Partner .
● You congure the settings related to the blocking and deletion of customer and vendor master data in
Customizing for:
○ Logistics - General Business Partner Deletion of Customer and Supplier Master Data
13.6.2.2 Commercial Project Management
13.6.2.2.1 Authorizations
The following section provides an overview of the authorizations that apply to Commercial Project
Management.
Based on your business needs, you can choose one of the following component combinations as a deployment
option:
Deployment Option Project Workspace
Project Cost and
Revenue Planning
Project Issue and
Change Management
SAP BusinessObjects
Analysis for Microsoft
Oce
Option 1 x x x x
Option 2 x x x
Option 3 x x x
Option 4 x x
The following standard roles can be used as templates to build your own roles, based on the option you have
deployed.
Standard Roles
370
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Commercial Project Management
Role Description
SAP_BPR_CPD_USER_1
Provides Display authorizations for Commercial Project
Management.
Project Workspace
Role Description
SAP_SR_CPD_PWS_USER_1
Provides Display authorizations for Commercial Project
Management.
SAP_SR_CPD_PM_1
Allows the creation, change, and display of commercial
projects and nancial plans and provides authorizations to
users working as project managers.
SAP_SR_CPD_PICM_PM_1
Provides Create, Change, and Display authorizations for
objects in Project Issue and Change Management.
SAP_BR_PRJTEAMMEMBER_COMMPRJ
Allows team members to use the following Fiori app:
● Commercial Projects: Activities
SAP_BR_PROJECTMGR_COMMPRJ
Allows project managers to use the following Fiori apps:
● Commercial Projects: Activities
● Commercial Projects: Multiproject Overview
● Commercial Projects: Single-Project Overview
● Commercial Projects: Billing and Receivables Overview
● Commercial Projects: Procurement Overview
Project Cost and Revenue Planning
Role Description
SAP_SR_CPD_PFP_USER_1
Provides Display authorizations for objects relevant to
Project Cost and Revenue Planning.
SAP_SR_CPD_PM_1
Allows the creation, change, and display of commercial
projects and nancial plans. The role provides
authorizations to users working as project managers.
SAP_SR_CPD_PICM_PM_1
Provides Create, Change, and Display authorizations for
objects in Project Issue and Change Management.
Project Issue and Change Management
Role
Description
SAP_SR_CPD_PICM_USER_1
Provides Display authorizations for objects in Project Issue
and Change Management.
SAP_SR_CPD_PICM_PM_1
Provides Create, Change, and Display authorizations for
objects in Project Issue and Change Management.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 371

13.6.2.2.2 Data Storage Security
In Commercial Project Management, the header data of the nancial plan is stored in the database tables of
Project Cost and Revenue Planning.
● Data is saved in the database tables of Project Cost and Revenue Planning when the user explicitly chooses
the Save pushbutton on the nancial planning screen.
● The planning data is stored in the BW InfoCube and can be transferred to the S4CORE database tables by
the user.
● Data is saved in the BW InfoCube when the user explicitly chooses the Save Data pushbutton in the
Analysis Oce workbook.
● Data is saved in S4CORE database tables when the user explicitly chooses the Transfer Data pushbutton
on the nancial planning screen.
13.6.2.2.3 Data Archiving
13.6.2.2.3.1 Archiving Commercial Projects
You can use Archiving Object for Commercial Projects (/CPD/PWS_M) to archive commercial projects that are
no longer needed. Archiving allows you to reduce the load on your database.
Structure
Tables
Tables for Commercial Projects
Table Description
/CPD/S_MP_HDR_K
Commercial Project Header
/CPD/D_MP_HDR_S
Commercial Project Header Short Text
/CPD/D_MP_ITEM
Commercial Project Structure Elements
/CPD/D_MP_MEMBER
Project Member
/CPD/D_MP_REP_AT
Reporting Attribute Node
/CPD/D_MP_RESP
Responsibility Node
/CPD/D_MP_STATUS
Status Header
/CPD/D_MP_ST_ARV
Table for Status Area Version
/CPD/D_MP_ST_HRA
Status Header Area
/CPD/D_MP_ST_VHR
Status Versions
372 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Table Description
/CPD/D_MP_TEAM
Team
/CPD/D_MP_TEAM_M
Team Member Subnode
/CPD/D_MP_TEAM_R
Team Role Subnodes
Programs
The following programs are available for /CPD/PWS_M:
● Preprocessing: /CPD/PWS_ARCH_MP_PRE
This program makes the following checks for commercial projects:
If both these conditions are satised, the program sets the archiving status of the commercial project to
Archiving in Process (02).
● Write: /CPD/PWS_ARCH_MP_WRITE
This program checks if an object has the status Archiving in Process (02). If the status is 02, the program
archives the object to the archive le.
● Delete: /CPD/PWS_ARCH_MP_DELETE
This program veries archived les against the data in the database, and deletes all objects in the database
that have been successfully archived.
Information Lifecycle Management (ILM)
Information Lifecycle Management (ILM) allows you to dene rules for storing archived business data, set legal
holds on stored data, and destroy the data in adherence to legal requirements.
The ILM object CPD_PWS_M is available for commercial projects and this ILM object allows you to model
retention rules based on the following elds:
● Condition Fields
○ Archiving Status
○ Commercial Project Type
○ Organization
● Time Reference Fields
○ End Date
You can use the transaction IRMPOL to dene policies and rules for ILM.
Prerequisites
The prerequisites for Retention Management are:
● You have activated the business function ILM
● You have assigned the following objects to an audit area:
○ CPD_PWS_M
More Information
To change the residence time, you can make settings in Customizing for Cross-Application Components under
Processes and Tools for Enterprise Applications Reusable Objects and Functions for BOPF Environment
Archiving Adapter Maintain BOSpecic Residence Periods .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 373

13.6.2.2.3.2 Archiving Financial Plans
You can use Archiving Object for Financial Plans (/CPD/PFP_P) to archive nancial plans that are no longer
needed. Archiving allows you to reduce the load on your database.
Structure
Tables
Tables for Financial Plans
Table Description
/CPD/D_PFP_PH
Plan Header
/CPD/D_PFP_PV
Plan Version
/CPD/D_PFP_PS
Plan Structure
/CPD/D_PFP_PER
Plan Exchange Rate
/CPD/D_PFP_PHTXT
Plan Header Text
/BOBF/D_ATF_RT
Attachment Root
/BOBF/D_ATF_DO
Attachment Document
/BOBF/D_TXCROOT
Text Collection Root
/BOBF/D_TXCTXT
Text Collection Text
/BOBF/D_TXCCON
Text Collection Text Content
Programs
The following programs are available for /CPD/PFP_P:
● Preprocessing: /CPD/PFP_ARCH_PH_PRE
This program checks whether a nancial plan is ready for archiving. A nancial plan is ready for archiving
when:
○ Related nancial plan versions have a status that indicates completion.
○ All related change requests and change request alternatives are ready for archiving, with the status as
Archiving in Process (02). This is only applicable if you are also using Project Issue and Change
Management.
○ The nancial plan has a status that indicates completion.
If the object is ready, this program sets the status as Archiving in Process (02) in the database.
Note
After the preprocessing program has run, the objects marked for archiving are no longer made
available on the UI. The program also deletes corresponding data from the real-time InfoCube (/CPD/
PFP_R01) and transfers the data into the InfoCube for archiving (/CPD/PFP_C01).
● Write: /CPD/PFP_ARCH_PH_WRITE
374
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

This program checks if an object has the status Archiving in Process (02). If the status is 02, the program
archives the object to the archive le.
● Delete: /CPD/PFP_ARCH_PH_DELETE
This program veries archived les against the data in the database; and deletes all objects in the database
that have been successfully archived.
Information Lifecycle Management (ILM)
Information Lifecycle Management (ILM) allows you to dene rules for storing archived business data, set legal
holds on stored data, and destroy the data in adherence to legal requirements.
The ILM object CPD_PFP_P is available for nancial plans and this ILM object allows you to model retention
rules based on the following elds:
● Condition Fields
○ Plan Scenario ID
○ Plan Type ID
○ Archiving Status
● Time Reference Fields
○ End Date
You can use the transaction IRMPOL to dene policies and rules for ILM.
Prerequisites
The prerequisites for Retention Management are:
● You have activated the business function ILM
● You have assigned the following objects to an audit area:
○ CPD_PFP_P
More Information
To change the residence time, you can make settings in Customizing for Cross-Application Components under
Processes and Tools for Enterprise Applications Reusable Objects and Functions for BOPF Environment
Archiving Adapter Maintain BOSpecic Residence Periods .
13.6.2.2.3.3 Archiving Issues and Change Requests
You can use Archiving Object for Issues and Change Requests (/PICM/BO_I) to archive issues and change
requests that are no longer needed. Archiving allows you to reduce the load on your database.
Structure
Tables
Tables for Issues and Change Requests
Table Description
/BOBF/D_ATF_DO
Document node of attachment folder
/BOBF/D_ATF_RT
Root nodes of attachment folder
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 375

Table Description
/BOBF/D_TXCCON
Text content
/BOBF/D_TXCROOT
Root node of text collection
/BOBF/D_TXCTXT
Text
/IAM/D_I_ATT
Attachment
/IAM/D_I_DATE
Date
/IAM/D_I_DESC
Description node
/IAM/D_I_DESC_TX
Language-dependent description text node
/IAM/D_I_OBJ_REF
Issue reference node
/IAM/D_I_OREF_DT
Language-dependent, reference, description text node
/IAM/D_I_PARTY
Party node
/IAM/D_I_QTY
Quantity
/IAM/D_I_ROOT
Root node
Programs
The following programs are available for /PICM/BO_I:
● Preprocessing: /PICM/ARCH_ISSUE_CR_ROOT_PRE
This program checks if an object is ready for archiving by verifying the following conditions:
○ The adherence to the specied residence time
○ The availability of activities for the object
If the object is ready, this program sets the status as Archiving in Process (02) in the database. After the
preprocessing program has run, the objects marked for archiving are no longer made available on the UI.
● Write: /PICM/ARCH_ISSUE_CR_ROOT_WRITE
This program checks if an object has the status Archiving in Process (02). If the status is 02, the program
archives the object to the archive le.
● Delete: /PICM/ARCH_ISSUE_CR_ROOT_DEL
This program veries archived les against the data in the database; and deletes all objects in the database
that have been successfully archived..
More Information
To change the residence time, you can make settings in Customizing for Cross-Application Components under
Processes and Tools for Enterprise Applications Reusable Objects and Functions for BOPF Environment
Archiving Adapter Maintain BOSpecic Residence Periods .
376
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.6.2.2.3.4 Archiving Activities
You can use Archiving Object for Activities (/PICM/BO_A) to archive activities that are no longer needed.
Archiving allows you to reduce the load on your database.
Structure
Tables
Tables for Activities
Table Description
/BOBF/D_ATF_DO
Document node of attachment folder
/BOBF/D_ATF_RT
Root nodes of attachment folder
/BOBF/D_TXCCON
Text content
/BOBF/D_TXCROOT
Root node of text collection
/BOBF/D_TXCTXT
Text
/IAM/D_ACT_ATT
Attachment
/IAM/D_ACT_DATE
Date
/IAM/D_ACT_DESC
Description node
/IAM/D_ACT_DTXT
Language-dependent description text node
/IAM/D_ACT_FOA
Follow-up action
/IAM/D_ACT_FOA_P
Follow-up action parameter
/IAM/D_ACT_OBJ_RF
Object reference
/IAM/D_ACT_OREF_DT
Language-dependent description texts
/IAM/D_ACT_PARTY
Party
/IAM/D_ACT_QTY
Activity quantity
Programs
The following programs are available for /PICM/BO_A:
● Preprocessing: /PICM/ARCH_ACTIVITY_ROOT_PPROC
This program checks if an object is ready for archiving by verifying the adherence to the specied
residence time. If the object is ready, this program sets the status as Archiving in Process (02) in the
database. After the preprocessing program has run, the objects marked for archiving are no longer made
available on the UI.
● Write: /PICM/ARCH_ACTIVITY_ROOT_WRITE
This program checks if an object has the status Archiving in Process (02). If the status is 02, the program
archives the object to the archive le.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 377

● Delete: /PICM/ARCH_ACTIVITY_ROOT_DEL
This program veries archived les against the data in the database; and deletes all objects in the database
that have been successfully archived.
More Information
To change the residence time, you can make settings in Customizing for Cross-Application Components under
Processes and Tools for Enterprise Applications Reusable Objects and Functions for BOPF Environment
Archiving Adapter Maintain BOSpecic Residence Periods .
13.6.2.2.3.5 Archiving Checklists Headers and Items
You can use the archiving objects Checklist Headers (/CPD/MC_H) and Checklist Items (/CPD/MC_I) to archive
checklist headers and items that are no longer needed. Archiving allows you to reduce the load on your
database.
Structure
Tables
Tables for Checklist Headers
Table Description
/BOBF/D_ATF_DO
Document node of attachment folder
/BOBF/D_ATF_RT
Root nodes of attachment folder
/BOBF/D_TXCCON
Text content
/BOBF/D_TXCROOT
Root node of text collection
/BOBF/D_TXCTXT
Text
/IAM/D_I_ATT
Attachment
/IAM/D_I_DATE
Date
/IAM/D_I_DESC
Description node
/IAM/D_I_DESC_TX
Language-dependent description text node
/IAM/D_I_OBJ_REF
Issue reference node
/IAM/D_I_OREF_DT
Language-dependent, reference, description text node
/IAM/D_I_PARTY
Party node
/IAM/D_I_QTY
Quantity
/IAM/D_I_ROOT
Root node
378 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Tables for Checklist Items
Table Description
/BOBF/D_ATF_DO
Document node of attachment folder
/BOBF/D_ATF_RT
Root nodes of attachment folder
/BOBF/D_TXCCON
Text content
/BOBF/D_TXCROOT
Root node of text collection
/BOBF/D_TXCTXT
Text
/IAM/D_ACT_ATT
Attachment
/IAM/D_ACT_DATE
Date
/IAM/D_ACT_DESC
Description node
/IAM/D_ACT_DTXT
Language-dependent description text node
/IAM/D_ACT_FOA
Follow-up action
/IAM/D_ACT_FOA_P
Follow-up action parameter
/IAM/D_ACT_OBJ_RF
Object reference
/IAM/D_ACT_OREF_DT
Language-dependent description texts
/IAM/D_ACT_PARTY
Party
/IAM/D_ACT_QTY
Activity quantity
Programs
The following programs are available for /CPD/MC_H:
● Preprocessing: /CPD/ARCH_MC_HEADER_PRE
This program checks if an object is ready for archiving by verifying the following conditions:
○ The adherence to the specied residence time
○ The availability of activities for the object
If the object is ready, this program sets the status as Archiving in Process (02) in the database. After the
preprocessing program has run, the objects marked for archiving are no longer made available on the UI.
● Write: /CPD/ARCH_MC_HEADER_WRITE
This program checks if an object has the status Archiving in Process (02). If the status is 02, the program
archives the object to the archive le.
● Delete: /CPD/ARCH_MC_HEADER_DELETE
This program veries archived les against the data in the database; and deletes all objects in the database
that have been successfully archived..
The following programs are available for /CPD/MC_I:
● Preprocessing: /CPD/ARCH_MC_ITEM_PRE
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 379
This program checks if an object is ready for archiving by verifying the adherence to the specied
residence time. If the object is ready, this program sets the status as Archiving in Process (02) in the
database. After the preprocessing program has run, the objects marked for archiving are no longer made
available on the UI.
● Write: /CPD/ARCH_MC_ITEM_WRITE
This program checks if an object has the status Archiving in Process (02). If the status is 02, the program
archives the object to the archive le.
● Delete: /CPD/ARCH_MC_IEM_DELETE
This program veries archived les against the data in the database; and deletes all objects in the database
that have been successfully archived.
Information Lifecycle Management (ILM)
Information Lifecycle Management (ILM) allows you to dene rules for storing archived business data, set legal
holds on stored data, and destroy the data in adherence to legal requirements.
The ILM objects CPD_MC_H and CPD_MC_I are available for checklist headers and items respectively, and these
ILM objects allow you to model retention rules based on the following elds:
● Condition Field
○ APPLICATION
● Time Reference Fields
○ Last Changed On
Note
The date of the last change of the checklist headers and items is considered in the time reference eld.
Note
When you create retention rules for a checklist item, ensure that the retention time specied does not
exceed the retention time specied for the parent (checklist header).
You can use the transaction IRMPOL to dene policies and rules for ILM.
Prerequisites
The prerequisites for Retention Management are:
● You have activated the business function ILM
● You have assigned the following objects to an audit area:
○ o CPD_MC_H
○ o CPD_MC_I
More Information
To change the residence time, you can make settings in Customizing for Cross-Application Components under
Processes and Tools for Enterprise Applications Reusable Objects and Functions for BOPF Environment
Archiving Adapter Maintain BOSpecic Residence Periods .
380
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.6.2.2.4 Deletion of Personal Data
The Commercial Project Management applications might process data (personal data) that is subject to the
data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM)
to control the blocking and deletion of personal data.
Project Workspace
Relevant Application Objects and Available Deletion Function
Application
Detailed Description Deletion Function
Project Workspace Project Workspace stores personal
information of business partners for
the Team function.
The ILM-enabled deletion program for
commercial projects: /CPD/
PWS_ARCH_MP_DELETE
Relevant Function Modules
Application Function Module Description
Project Workspace Risk
Management
/CPD/BUPA_EOP_CHECK
You can use this API to check the
retention period of business partners.
Project Workspace Risk
Management
/CPD/RM_BUPA_EVENT_ARCH1
You can use this API to archive
business partners.
Project Workspace Risk
Management
/CPD/RM_BUPA_EVENT_DELE1
You can use this API to delete business
partners.
Project Workspace
/CPD/PWS_WS_BUPA_EOP_CHECK
You can use this function module for
the end of purpose check.
Relevant Programs
Application Program Description
Project Workspace
/CPD/R_DPP_CONTACT_PERSON_S4H
This program is relevant for contact
persons who have been added using
the Create Contact feature in the Dene
Commercial Project Types view in
Customizing for Commercial Project
Management
Master Data
Commercial Project Make Settings
for Commercial Projects
.
When a contact person leaves a
company, to comply with data privacy
and protection rules, you can use this
program to identify all the projects that
this person is assigned to; and then
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 381

Application Program Description
proceed to delete the contact from all
projects in one go.
Project Cost and Revenue Planning
The Project Cost and Revenue Planning application (CA-CPD-FP) does not use SAP ILM to support the deletion
of personal data since the data required for transactional purposes is stored in a BW InfoCube.
Relevant Application Objects and Available Deletion Function
Application Detailed Description Deletion Function
Project Cost and Revenue Planning Project Cost and Revenue Planning
stores personal information of
business partners only when resources
are planned together with SAP
Multiresource Scheduling (MRS). This
information is then stored in a BW
InfoCube, for real-time planning.
The deletion program
/CPD/
PFP_EMP_DATA_CONSISTENCY
checks
the HR master and delete information
from the InfoCube, for employee
records that are not found in the HR
master.
Project Issue and Change Management
Relevant Application Objects and Available Deletion Function
Application Detailed Description Deletion Function
Project Issue and Change Management Project Issue and Change Management
stores personal information of
business partners for the Partner
function.
● The ILM-enabled deletion program
for issues and change requests: /
PICM/
ARCH_ISSUE_CR_ROOT_DEL
● The ILM-enabled deletion program
for activities:
/PICM/
ARCH_ACTIVITY_ROOT_DEL
●
Function module to check (before
deletion) if business partner is
used in the application:
/PICM/
BUPA_EVENT_DELE1
Relevant Function Modules
Application Function Module Description
Project Issue and Change Management
/PICM/BUPA_EOP_CHECK
You can use this function module for
the end of purpose check.
13.6.2.2.5 Security-Relevant Logging and Tracing
The Project Cost and Revenue Planning application of Commercial Project Management uses the tracing
functions of SAP BusinessObjects Analysis for Microsoft Oce (AO) to trace actions performed in the planning
382
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
workbook (AO). You can also activate a trace le for Project Cost and Reveue Planning using the Activate
Tracing button on the Financial Planning ribbon. Details of the items are recorded in the trace le
(CACPDFP_TRACE_LOG.log). Note that the le does not record user-specic personal information such as
user name or IP address.
For information about tracing related to Analysis Oce, see https://help.sap.com/viewer/p/
SAP_BUSINESSOBJECTS_ANALYSIS_OFFICE Installation, Conguration, Security and Administration
Administrator Guide .
13.6.2.2.6 Other Security-Relevant Information
Before you use the digitally-signed SAP BusinessObjects Analysis for Microsoft Oce (AO) workbooks
delivered by Commercial Project Management, you must follow these steps:
Caution
These settings are valid if you want to use the workbooks in a secure way by only enabling digitally-signed
macros. However, if you use custom workbooks or make any changes and save it back to the standard, you
must enable all macros.
1. Launch Microsoft Excel
1. Go to File Options Trust Center Settings Macro Settings
2. Choose Disable all macros except digitally signed macros
3. Mark the Trust access to the VBA project object model checkbox
2. Launch the digitally-signed workbook and implement the following steps to add the certicate as a trusted
publisher:
1. A security warning is show in File Info Enable Control
2. Seclect Advanced Options
3. In the next dialog box, select Trust all documents from this publisher
Note
Adding the certicate is a one-time activity
3. Follow these steps to change the default system in the workbook:
1. Go to File Commercial Project Settings
2. In the dialog box, choose Platform
3. Choose Replace System
4. Choose your relevant system in the Replace by System column
5. Save the workbook (with the correct standard workbook name) in the relevant system
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 383

13.6.2.3 SAP Portfolio and Project Management
13.6.2.3.1 Authorizations
Authorizations
In Project Management and Portfolio Management, authorizations are controlled in the following ways:
● ABAP authorization objects and roles
This is the standard method for controlling access to transactions and programs in an SAP ABAP system.
Authorizations are combined in an authorization prole that is associated with a role. User administrators
can then assign the corresponding roles via the user master record, so that the user can access the
appropriate transactions for his or her tasks.
● Access control lists
These allow you to add another level of security by controlling authorization at object level. For example,
you can control who has authorization to change a particular project denition.
You can dene the menu options in the navigation area using portal content adjustments or PFCG role
Customizing.
● Roles for SAP Fiori apps
To use SAP Fiori Apps, users must be assigned to roles. These roles dene which apps are displayed to the
user.
In Project Management only, you can use the following additional authorization mechanisms:
● System administrators can grant access to objects by choosing Portfolio and Project Administration
Project Authorization Administration in the application. This is an exception to the normal process and is
only used if the administrator of the object is not available due to illness, for example. The system sends
the “new” and “old” administrators an e-mail to inform them of the new authorization holder. For more
information, see the Granting Administration Authorization for an Object section of the Conguration Guide
for SAP Portfolio and Project Management.
● System administrators can assign PFCG roles in Customizing for SAP Portfolio and Project Management
under Common Functions Dene Superuser Authorizations . This ensures that the maintained PFCG
roles with the selected authorization will be automatically assigned to the corresponding project denition.
Authorizations regarding BAPIs, reports, and (RFC-enabled) function modules:
In SAP Portfolio and Project Management, multiple BAPIs, reports and (RFC-enabled) function modules are
available to create, read, change, edit, update, and delete the data of SAP Portfolio and Project Management.
Additionally, via (RFC-enabled) function modules and reports data is read from the SAP S/4HANA system.
Therefore, using these BAPIs, reports, and function modules access to and manipulation of Portfolio and
Project Management data as well as read access to SAP S/4HANA data is possible. Thus, the authorization for
using these BAPIs, reports, and function modules (via transactions, for example), should be restricted to users
who are intended to have these authorizations and the corresponding access to data.
Authorizations regarding search results
You can use the BAdI BADI_DPR_SEARCH to modify search results. You can lter the result set implementing
this BAdI depending on the specied search helps which exist for each Portfolio and Project Management
object. Thus, you can, for example, hide all results for which the user does not have read authorization from the
result list. In the standard, these results are displayed in the result list, but the user cannot open or display
these objects.
384
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Use
SAP Portfolio and Project Management uses the authorization concept provided by SAP NetWeaver for SAP S/
4HANA. Therefore, the recommendations and guidelines for authorizations as described in the Security Guide
for SAP NetWeaver for SAP S/4HANA also apply to SAP Portfolio and Project Management.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
You can maintain the following role authorizations in Project Management and Portfolio Management using the
SAP Prole Generator.
The following PFCG roles of SAP Portfolio and Project Management include authorizations to start the Web
Dynpro ABAP applications (authorization check
S_START) for Project Management and Portfolio Management:
● SAP_CPR_USER
● SAP_XRPM_USER
For details see the particular roles in transaction PFCG and choose Authorizations Display Authorization
Data
Cross-application Authorization Objects Start Authorization Check for TADIR Objects .
SAP recommends to adapt custom-specic roles accordingly.
Project Management Roles
The following single roles are delivered with Project Management:
Role Authorization
SAP_CPR_PROJECT_ADMINISTRATOR
Create projects (project denitions).
SAP_CPR_TEMPLATE_ADMINISTRATOR
Create, change, read, and delete all templates in Project
Management.
SAP_CPR_USER
Use Project Management, but no authorization to perform
any activities in a particular project. To do this users need
project-specic authorizations, which can be distributed ei
ther directly via ACLs or through their assignment to a role.
This role must be included in every Project Management
composite role.
SAP_CPR_BCV_USER
Project-Management-specic authorization for using BCV
content in resource management.
SAP_BPR_PPM
SAP Portfolio and Project Management PFCG role for NW BC
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 385

The following composite roles are delivered with Project Management:
Role Authorization
SAP_CPR_DECISON_MAKER
Decision maker in Project Management. Contains the role
SAP_CPR_USER.
SAP_CPR_INTERESTED
Interested party in Project Management. Contains the role
SAP_CPR_USER.
SAP_CPR_MEMBER
Team member in Project Management. Contains the role
SAP_CPR_USER.
SAP_CPR_PROJECT_LEAD
Project manager in Project Management. Contains the role
SAP_CPR_PROJECT_ADMINISTRATOR and SAP_CPR_USER
SAP_CPR_BCV_USER_COMP
Composite role containing the general role for using BCV
(SAP_BCV_USER) and the Project Management specic role
(
SAP_CPR_BCV_USER).
SAP_CPR_TEMPLATE_RESPONSIBLE
Project Management template responsible. Contains the
roles SAP_CPR_TEMPLATE_ADMINISTRATOR and
SAP_CPR_USER
SAP_CPR_RESOURCE_MANAGER
Resource manage in Project Management. Contains the role
SAP_CPR_USER.
You can use these SAP standard roles or create your own. For more information, see the Activating Single Roles
for Project Management section and the Creating Roles for the ProjectSpecic Authorization Checks section of
the Conguration Guide for SAP Portfolio and Project Management.
Portfolio Management Roles
For Portfolio Management, the following roles are available:
Roles Authorization
SAP_XRPM_ADMINISTRATOR
Super user authorization in Portfolio Management. Used to
create new portfolios. This role also provides the assigned
user full access to all Portfolio Management business ob
jects in the system.
SAP_XRPM_USER
General user in Portfolio Management. All users should be
assigned this role. Has general authorizations to use Portfo
lio Management, but no specic object access. This access
must be assigned to the user via ACLs.
386 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Roles Authorization
SAP_RPM_BCV_USER
Portfolio Management specic authorization for BCV con
tent in Portfolio Management
SAP_RPM_BCV_USER_COMP
Composite role containing the general role for using BCV
(SAP_BCV_USER) and the Portfolio Management specic
role (
SAP_RPM_BCV_USER).
SAP_BPR_PPM
PFCG role for NWBC in SAP Portfolio and Project Manage
ment
You can use these SAP standard roles or create your own. For more information about roles in Portfolio
Management, see the Activating Single Roles for Portfolio Management (PFCG) section and the Creating Roles
for the PortfolioSpecic Authorization Checks section of the Conguration Guide for SAP Portfolio and Project
Management.
SAP Fiori Roles
SAP Fiori roles (SAP_BR_*) need to be assigned on the front-end server on which the UIS4HOP1 software
component is installed. You can nd the roles in the implementation information for each application.
For more information and further implementation tasks on the front-end server, see the UI Technology Guide
for SAP S/4HANA.
13.6.2.3.2 Communication Channel Security
SAP Portfolio and Project Management Communication Channel Security
Communication Channel Communication Technology Data Transferred
Comment/Security Recom
mendation
SAP Portfolio and Project
Management front-end
(browser) to the SAP NW Ap
plication Server (SAP Net
Weaver AS)
HTTP(S) Files, metadata, and user
data (passwords, user
names)
Project Management front-
end (browser) to content or
cache servers
HTTP(S) Files
SAP NetWeaver AS to con
tent or cache servers
HTTP(S) Metadata, les
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 387
Communication Channel Communication Technology Data Transferred
Comment/Security Recom
mendation
SAP NetWeaver AS to other
application servers (for ex
ample, HR, CO)
RFC Metadata, les SAP Portfolio and Project
Management communicates
with 3rd party or SAP S/
4HANA systems to obtain or
create information on object
links between SAP Portfolio
and Project Management and
objects located in the 3rd
party/SAP system. The com
munication to 3rd party sys
tems has to be implemented
at the customer site. The 3rd
party/SAP system never calls
back.
For more information, see
the Setting Up Object Links
section of the Conguration
Guide for SAP Portfolio and
Project Management.
SAP Portfolio and Project
Management to Project Sys
tem (PS) component on a
separate system
RFC Files, metadata
SAP Portfolio and Project
Management to SAP HCM on
a separate system
SAP ALE
RFC
Files, metadata
Note
In SAP Portfolio and Project Management, there is no xed port for communication and the rewall settings
described in the SAP NetWeaver Security Guide. For more information, see http://help.sap.com/s4hana
SAP S/4HANA SAP NetWeaver for SAP S/4HANA Security Guide Security Guides for SAP
NetWeaver Functional Units
Security Guides for the Application Server Security Guides for the AS ABAP
SAP NetWeaver Application Server ABAP Security Guide Protecting Your Productive System (Change
and Transport System)
.
DIAG and RFC connections can be protected using Secure Network Communications (SNC). HTTP
connections are protected using the Secure Sockets Layer (SSL) protocol.
Recommendation
We strongly recommend using secure protocols (SSL, SNC) whenever possible.
388
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

For more information, see http://help.sap.com/s4hana SAP S/4HANA SAP NetWeaver for SAP S/
4HANA Security Guide Network and Communication Security Transport Layer Security .
13.6.2.3.3 Network Security
SAP supports the installation of SAP Portfolio and Project Management within the intranet (for internal
collaboration only).
Installation Scenarios
Scenarios A and B can be used for SAP Portfolio and Project Management:
● Scenario A: No content server
● Scenario B: One hidden content server
Installation scenario B, with one hidden content server, is the installation scenario with the highest level of
security.
Scenario A: No Content Server
In scenario A, the complete installation consists only of SAP Portfolio and Project Management server (SAP
NetWeaver AS).
The server is located in the intranet.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 389
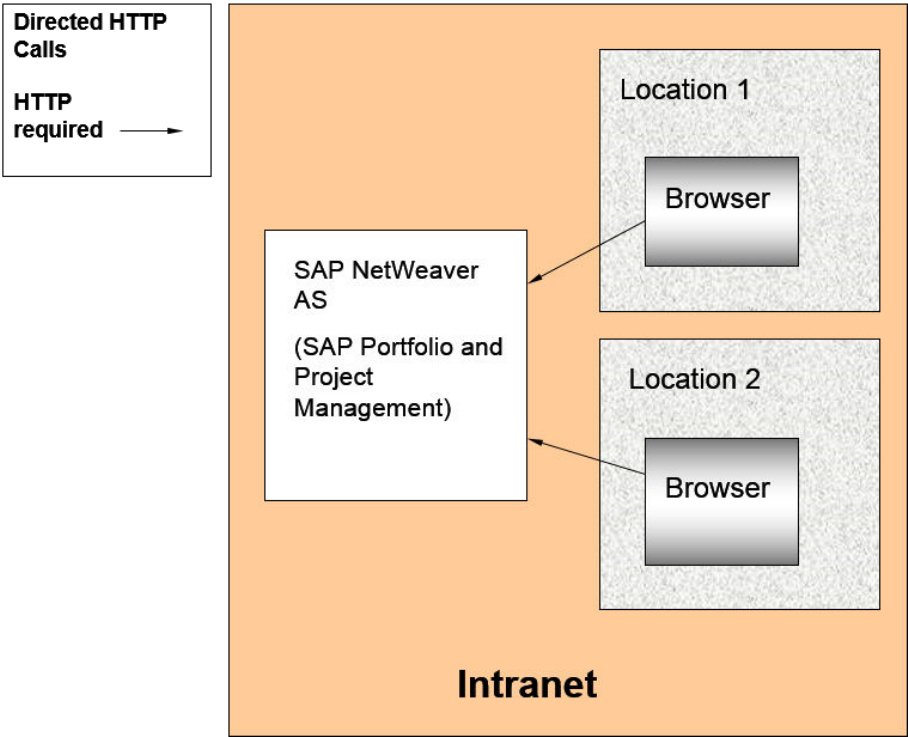
Scenario A: No Content Server
Scenario B: One Hidden Content Server
In the second type of installation, one content server is added to the network environment.
For SAP Portfolio and Project Management, the SAP NetWeaver AS and the content server are both located in
the intranet.
390
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
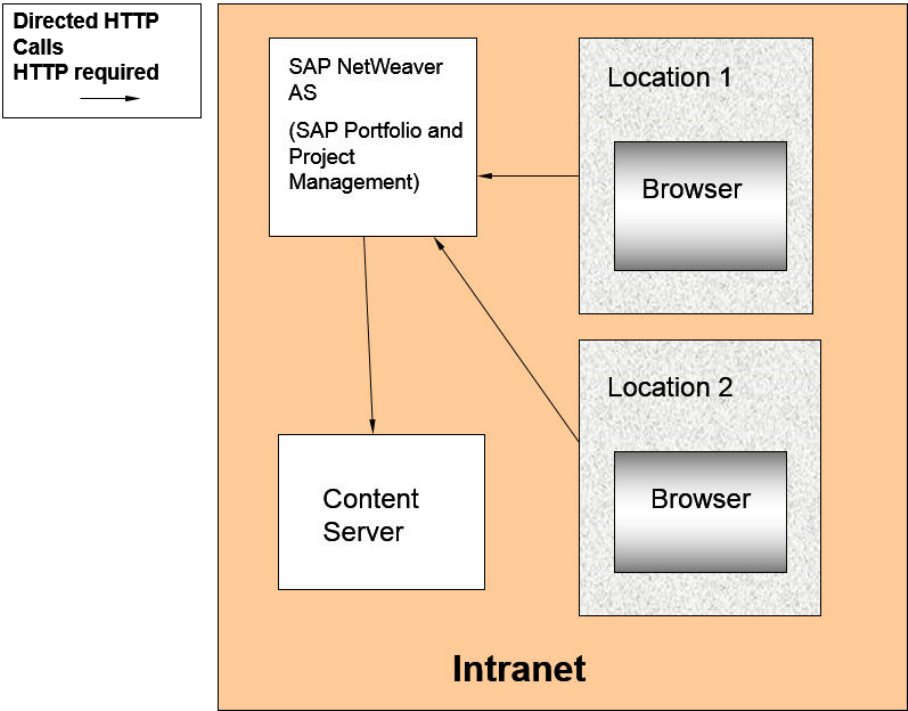
Scenario B: One Hidden Content Server
13.6.2.3.4 Communication Destinations
For the default SAP Portfolio and Project Management scenarios, no RFC destination pointing to external
systems is required. However, if you are using the Project Management application programming interfaces
(APIs) via the SOAP wrapper, the APIs consist of RFC function modules.
SAP Portfolio and Project Management
● FI/CO integration / Accounting Integration
● Adobe Document Services (ADS)
● Object links to e.g. SAP R/3, SAP ERP
● HR integration
In the following areas, Portfolio Management RFCs are called from an external application:
● Project integration
The Project Management APIs are required for:
● Portfolio Management Integration
● If a user needs to use the APIs they must have the basic RFC authorization for the relevant API function
modules. The SOAP wrapper adheres to the authorization rules that apply if the RFC module is called
directly. The function group name for Project Management is CPR_API.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 391

To view the application-specic and basis authorization objects used in SAP Portfolio and Project Management,
see Authorizations [page 384].
For more information about authorization objects and roles, see http://help.sap.com/s4hana SAP S/
4HANA SAP NetWeaver for SAP S/4HANA Security Guide User Administration and Authentication User
Management
Identity Management User and Role Administration of Application Server ABAP AS ABAP
Authorization Concept .
13.6.2.3.5 Internet Communication Framework Security
You should only activate those services that are needed for the applications running in your system. For more
information about the services that are needed for SAP Portfolio and Project Management, see the Activating
Services section of the Conguration Guide for SAP Portfolio and Project Management.
Use the transaction SICF to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information, see http://help.sap.com/s4hana SAP S/4HANA SAP NetWeaver for SAP S/
4HANA Function-Oriented View Application Server Application Server Infrastructure Functions and
Tools of SAP NetWeaver Application Server
Connectivity Components of SAP Communication Technology
Communication Between ABAP and Non-ABAP Technologies Internet Communication Framework
Development Server-Side Development Creating and Conguring ICF Services Activating and
Deactivating ICF Services.
For more information about ICF security, see http://help.sap.com/s4hana SAP S/4HANA SAP
NetWeaver for SAP S/4HANA
Security Guide Security Guides for Connectivity and Interoperability
Technologies RFC/ICF Security Guide. .
13.6.2.3.6 Data Storage Security
Data Storage
Note
In the default setting for SAP Portfolio and Project Management, data is protected using the ACL concept
already described in Authorizations [page 384]. A Web browser is required for both scenarios. However, no
cookies are used to store data on the front end.
392
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Data Protection
In SAP Portfolio and Project Management, data is mainly stored on the SAP NetWeaver Application Server
(SAP NetWeaver AS) database. An exception to this is when les are checked out for editing. In this case, les
are stored locally on the user’s hard drive and it is their responsibility to protect the les according to company
security policy.
Depending on which installation scenario you have chosen for SAP Portfolio and Project Management, les
might also be stored on content servers. For information about security measures to be taken in this case, see
the Network Security chapter of this document.
For more information about data protection, see the Data Protection chapter of this document.
13.6.2.3.7 Deletion of Personal Data
Use
SAP Portfolio and Project Management might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
Portfolio Management For more information, see the Product
Assistance documentation for SAP
Portfolio and Project Management un
der Archiving Portfolio and Project
Management Data.
Archiving Objects:
● RPM_PORT (Portfolios)
● RPM_BUCKET (Buckets)
● RPM_ITEM (Items)
● RPM_COLL (Collections)
● RPM_INIT (Initiatives)
● RPM_REVW (Reviews)
Project Management Archiving Objects:
● CDOCS_CONT (Documents)
● CPROJECTS (Projects)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 393

Application Detailed Description Provided Deletion Functionality
Portfolio and Project Management Once a business partner is destructed
using the central Business Partner ap
plication, all references of this particu
lar business partner to objects in Port
folio Management and Project Manage
ment must be removed.
Run the corresponding deletion pro
gram on a regular basis.
Deletion program PPM_DPP_DELETE
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented solution (EoP or WUC) Further Information
Portfolio and Project Management EoP Checks whether business partner data
is still needed for Portfolio and Project
Management processes.
● If a business partner is still needed:
next check date = initial
● If a business partner is no longer
needed and the end of residence
date is in the future (> today): next
check date = end of residence
● If a business partner is no longer
needed and the end of residence is
reached (<= today): next check
date = initial; start of retention
date is calculated
Use Business Add-In
PPM_BUPA_EOP_CHECK to implement a
customer-specic logic.
Process Flow
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available.
3. You do the following:
○ Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA).
394
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

○ Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner.
4. Business users can request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
5. If you have the needed authorizations, you can unblock data by running the transaction BUPA_PRE_EOP
and CVP_UNBLOCK_MD.
6. You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of Portfolio and Project
Management.
For information about how to congure blocking and deletion for SAP Portfolio and Project Management, see
Conguration: Simplied Blocking and Deletion.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
● Dene the settings for authorization management under Data Protection Authorization
Management . For more information, see the Customizing documentation.
● Dene the settings for blocking in Customizing for Cross-Application Components under Data Protection
Blocking and Unblocking Business Partner .
13.6.2.3.8 Security for Additional Applications
You can only (import or) export data to Microsoft Project if you have the required authorizations, see Access
Control Lists – Import and Export. The protection of this downloaded data is not part of the Project
Management security model. When the user saves the project to his or her hard drive, the system does not
perform an authorization check if somebody else opens the project again in Microsoft Project.
13.6.2.3.9 Other Security-Relevant Information
Import from Microsoft Excel
You can import projects from a Microsoft Excel le to Project Management. This enables you to transfer mass
data in a quick and easy manner.
If you want to restrict the import function, you have to make sure that only allowed users receive authorization
for transaction DPR_DX_PROJECT and report DPR_DX_PROJECT.
Moreover, you can import nancial and/or capacity data from a Microsoft Excel le to nancial and capacity
planning in Portfolio Management. To use this function, you require an ERP system, an appropriate client, user,
and password. This import is only allowed if the required authorization has been granted.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 395

13.6.2.3.10 Security-Relevant Logging and Tracing
Floorplan Manager Message Logging to the Application Log
The Web Dynpro ABAP UI of SAP Portfolio and Project Management uses the Floor Plan Manager (FPM). The
FPM Message Manager has a connection to the ABAP application log and oers the option to write error
messages occurring in the FPM Message Manager also to the application log in the backend. To activate this
feature, go to transaction SAAB and activate the check point group FPM_RUNTIME_MESSAGES for your user or
for all users in the server.
For more information about FPM, see http://www.sdn.sap.com/irj/sdn/nw-ui under Custom UI
Development Web Dynpro ABAP Floorplan Manager (FPM) Developer's Guide .
For more information about security in the ABAP area, see
● http://help.sap.com/s4hana SAP S/4HANA SAP NetWeaver for SAP S/4HANA Security Guide
Security Guides for SAP NetWeaver Functional Units Security Guides for the AS ABAP SAP NetWeaver
Application Server ABAP Security Guide
● http://help.sap.com/s4hana SAP S/4HANA SAP NetWeaver for SAP S/4HANA Security Guide
Security Guides for SAP NetWeaver Functional Units Security Guides for the Application Server
Security Guides for the AS ABAP SAP NetWeaver Application Server ABAP Security Guide Web
Dynpro ABAP Security Guide
Reports Logging to the Application Log
SAP Portfolio and Project Management logs application errors for background reports to transaction SLG1.
Background reports are executed in the areas of nancial integration, migration, import from Microsoft Excel,
versioning, and replace user and resource. You can display these application logs via the objects
RPM_DOCUMENT, RPM_DX, RPM_INTEGRATION, RPM_MIGRATION, RPM_PLANNING, RPM_UC,
RPM_VERSIONING, DPR_DX, DPR_REPLACE_USER_BP.
Logon Attempts
For more information about logon attempts, see http://help.sap.com/s4hana SAP S/4HANA SAP
NetWeaver for SAP S/4HANA
Security Guide Security Aspects for Lifecycle Management Auditing and
Logging The Security Audit Log .
396
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Change Document
You can use change document to track changes of objects of Project Management and Portfolio Management.
If the function is active, the system also records changes to dependent objects. You can activate the change
document function for the following objects:
● Project Management
○ Checklist templates
○ Project templates
○ Projects
You can activate this function in Customizing for Project Management under Basic Settings Activate
Change Documents.
If the function is active for one of these main objects, changes to dependent objects are also recorded. For
example, if you select the indicator for the object category project, the system records all changes to the
project as well as to the following objects:
○ Project denitions
○ Phases
○ Tasks
○ Mirrored tasks
○ Checklists
○ Checklist items
○ Documents
○ Object links
○ Entity links
○ Business partner favorites
○ Business partner links
○ Roles
○ Approvals
○ Qualications
○ Collaborations
○ Templates
The system only records changes to database table DPR_DOCUMENT. This table contains unusable
document attributes only.
The important attributes of the documents and les (such as name, location, and size) as well as the le
content are saved to the KPro storage system without the support of a change document function.
Project Management supports versioning for les instead of the change document function. To track the
changes, the user must always create a new document version. However, if he or she always overwrites the
existing version, it is not possible to track the changes.
Project Management supports evaluations for the following objects:
○ Project denitions
○ Phases
○ Tasks
○ Mirrored tasks
○ Checklists
○ Checklist items
○ Object links
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 397

○ Entity links
○ Business partner links
○ Roles
● Portfolio Management
○ Portfolio
○ Bucket
○ Initiative
○ Item
○ Decision point
○ Review
○ Collection
○ What-if scenario
○ Relational associations of business objects
○ Financial and capacity category for bucket and item
In the standard system, this function is not activated.
You can activate this function in Customizing for Portfolio Management under Global Customizing
Process and Service Settings Activate Change Document .
The system does not record changes to the following objects:
● Project Management
○ Documents
● Portfolio Management
○ Long texts
○ Comments/notes
○ Documents
○ Financial and capacity planning values
For more information, see http://help.sap.com/s4hana SAP S/4HANA SAP NetWeaver for SAP S/
4HANA
Security Guide
● Security Aspects for Lifecycle Management Auditing and Logging
● Security Guides for SAP NetWeaver Functional Units Security Guides for the Application Server
Security Guides for the AS Java SAP NetWeaver Application Server Java Security Guide Tracing and
Logging.
13.6.3 Integrated Product Development for Discrete
Industries
13.6.3.1 Classication Reuse UI Component
398
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.6.3.1.1 Data Protection
Data protection is associated with numerous legal requirements and privacy concerns. In addition to
compliance with general data privacy acts, it is necessary to consider compliance with industry-specic
legislation in dierent countries. This section describes the specic features and functions that SAP provides
to support compliance with the relevant legal requirements and data privacy.
This section and any other sections in this Security Guide do not give any advice on whether these features and
functions are the best method to support company, industry, regional or country-specic requirements.
Furthermore, this guide does not give any advice or recommendations with regard to additional features that
would be required in a particular environment; decisions related to data protection must be made on a case-by-
case basis and under consideration of the given system landscape and the applicable legal requirements.
Note
In the majority of cases, compliance with data privacy laws is not a product feature.
SAP software supports data privacy by providing security features and specic data-protection-relevant
functions such as functions for the simplied blocking and deletion of personal data.
SAP does not provide legal advice in any form. The denitions and other terms used in this guide are not
taken from any given legal source.
Glossary
Term Denition
Personal Data Information about an identied or identiable natural per
son.
Business purpose A legal, contractual, or in other form justied reason for the
processing of personal data. The assumption is that any pur
pose has an end that is usually already dened when the
purpose starts.
Blocking A method of restricting access to data for which the primary
business purpose has ended.
Deletion Deletion of personal data so that the data is no longer usa
ble.
Retention period The time period during which data must be available.
End of purpose (EoP) A method of identifying the point in time for a data set when
the processing of personal data is no longer required for the
primary business purpose. After the EoP has been reached,
the data is blocked and can only be accessed by users with
special authorization
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 399
Some basic requirements that support data protection are often referred to as technical and organizational
measures (TOM). The following topics are related to data protection and require appropriate TOMs:
● Access control: Authentication features as described in section User Administration and Authentication.
● Authorizations: Authorization concept as described in section Authorizations.
● Read access logging: as described in section Read Access Logging.
● Communication Security: as described in section Network and Communication Security.
● Availability control as described in:
○ Section Data Storage Security
○ SAP NetWeaver Database Administration documentation
○ SAP Business Continuity documentation in the SAP NetWeaver Application Help under Function-
Oriented View Solution Life Cycle Management SAP Business Continuity .
● Separation by purpose: Is subject to the organizational model implemented and must be applied as part
of the authorization concept
Note
The extent to which data protection is ensured depends on secure system operation. Network security,
security note implementation, adequate logging of system changes, and appropriate usage of the system
are the basic technical requirements for compliance with data privacy legislation and other legislation.
Conguration of Data Protection Functions
Certain central functions that support data protection compliance are grouped in Customizing for Cross-
Application Components under Data Protection.
Additional industry-specic, scenario-specic or application-specic conguration might be required. For
information about the application-specic conguration, see the application-specic Customizing in SPRO.
13.6.3.1.1.1 Data Privacy
The Classication Reuse UI Component must not process any sensitive personal data that is subject to the
data protection laws applicable in specic countries as described in SAP Note 1825544 .
Data Archiving and Deletion
Classication and characteristic data is dependent on the business object of the embedding application. You
can only archive or delete classication and characteristic data with the business object of the embedding
application, once the business object reaches its end of purpose. The embedding application is responsible for
applying data protection and privacy rules.
Characteristics Containing Sensitive Personal Data
Characteristics are not intended for storing any sensitive personal data.
400
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.6.3.2 Advanced Variant Conguration
13.6.3.2.1 Data Protection
Data protection is associated with numerous legal requirements and privacy concerns. In addition to
compliance with general data privacy acts, it is necessary to consider compliance with industry-specic
legislation in dierent countries. This section describes the specic features and functions that SAP provides
to support compliance with the relevant legal requirements and data privacy.
This section and any other sections in this Security Guide do not give any advice on whether these features and
functions are the best method to support company, industry, regional or country-specic requirements.
Furthermore, this guide does not give any advice or recommendations with regard to additional features that
would be required in a particular environment; decisions related to data protection must be made on a case-by-
case basis and under consideration of the given system landscape and the applicable legal requirements.
Note
In the majority of cases, compliance with data privacy laws is not a product feature.
SAP software supports data privacy by providing security features and specic data-protection-relevant
functions such as functions for the simplied blocking and deletion of personal data.
SAP does not provide legal advice in any form. The denitions and other terms used in this guide are not
taken from any given legal source.
Glossary
Term Denition
Personal Data Information about an identied or identiable natural per
son.
Business purpose A legal, contractual, or in other form justied reason for the
processing of personal data. The assumption is that any pur
pose has an end that is usually already dened when the
purpose starts.
Blocking A method of restricting access to data for which the primary
business purpose has ended.
Deletion Deletion of personal data so that the data is no longer usa
ble.
Retention period The time period during which data must be available.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 401
Term Denition
End of purpose (EoP) A method of identifying the point in time for a data set when
the processing of personal data is no longer required for the
primary business purpose. After the EoP has been reached,
the data is blocked and can only be accessed by users with
special authorization
Some basic requirements that support data protection are often referred to as technical and organizational
measures (TOM). The following topics are related to data protection and require appropriate TOMs:
● Access control: Authentication features as described in section User Administration and Authentication.
● Authorizations: Authorization concept as described in section Authorizations.
● Read access logging: as described in section Read Access Logging.
● Communication Security: as described in section Network and Communication Security.
● Availability control as described in:
○ Section Data Storage Security
○ SAP NetWeaver Database Administration documentation
○ SAP Business Continuity documentation in the SAP NetWeaver Application Help under Function-
Oriented View Solution Life Cycle Management SAP Business Continuity .
● Separation by purpose: Is subject to the organizational model implemented and must be applied as part
of the authorization concept
Note
The extent to which data protection is ensured depends on secure system operation. Network security,
security note implementation, adequate logging of system changes, and appropriate usage of the system
are the basic technical requirements for compliance with data privacy legislation and other legislation.
Conguration of Data Protection Functions
Certain central functions that support data protection compliance are grouped in Customizing for Cross-
Application Components under Data Protection.
Additional industry-specic, scenario-specic or application-specic conguration might be required. For
information about the application-specic conguration, see the application-specic Customizing in SPRO.
13.6.3.2.1.1 Data Privacy
The Advanced Variant Conguration UI must not process any personal data or sensitive personal data that is
subject to the data protection laws applicable in specic countries as described in SAP Note 1825544 .
Data Archiving and Deletion
Characteristic data is dependent on the business object of the embedding application. You can only archive or
delete characteristic data with the business object of the embedding application, once the business object
402
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

reaches its end of purpose. The embedding application is responsible for applying data protection and privacy
rules.
Characteristics Containing Sensitive Personal Data
Characteristics are not intended for storing any personal data or sensitive personal data.
13.6.4 Product Lifecycle Management
13.6.4.1 Maintenance, Repair, and Overhaul
13.6.4.1.1 Authorizations (Specication 2000)
Specication 2000 (IS-ADEC-SPC) uses the authorization concept provided by the SAP NetWeaver AS for
ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver
AS Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used:
Authorization Object Description
C_ADSPCIP Spec2000: Authorization object
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 403

13.6.4.1.2 Deletion of Personal Data (Specication 2000)
Use
Specication 2000 (IS-ADEC-SPC) might process data (personal data) that is subject to the data protection
laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
the SAP Help Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components
Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Specication 2000 (IS-ADEC-SPC) Archiving Object
ADS2KIP_AR
ILM Object
ADS2KIP_AR
Report
AD_SCIP_ILM_DEL_01
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Specication 2000 (IS-ADEC-SPC) EoP Checks tables EDP21, EDP13
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
404
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.6.4.1.3 Deletion of Personal Data (Spare Parts Stock
Calculation)
Use
Spare Parts Stock Calculation (IS-ADEC-SPSC) might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components
Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Spare Parts Stock Calculation (IS-ADEC-SPSC) Report
AD_SPSC_ILM_DEL_01
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
13.6.4.1.4 Authorizations (Manufacturer Part Number)
Manufacturer Part Number (MPN) uses the authorization concept provided by the SAP NetWeaver AS for
ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver
AS Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 405

Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used:
Authorization Object Description
M_PIC_RIC Authorization for MPN Restricted Interchangeability
ADPIC_RIC Authorization object for MPN Restricted Interchangeability
M_PIC_EXCH Authorization for material exchange
13.6.4.1.5 Deletion of Personal Data (MPN)
Use
Manufacturer Part Number (IS-ADEC-MPN) might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components
Data Protection .
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Manufacturer Part Number (IS-ADEC-
MPN)
EoP Checks table MARA-MFRPN
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
406
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.6.4.1.6 Deletion of Personal Data (Sharing of Spare Parts
and Customer Stock)
Sharing of Spare Parts and Customer Stock (IS-AD-SSP) might process data (personal data) that is subject to
the data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management
(ILM) to control the blocking and deletion of personal data. For more information, see the product assistance
for SAP S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance
Cross Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Customer Stock
(IS-AD-SSP)
Destruction Object
MM_STO_SOBES_DEST
ILM Object
MM_STO_SOBES
Report
MM_STO_SOBES_DES
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Customer Stock (IS-AD-SSP) EoP check Checks tables MSCD_MD, MCSS_MD,
MSCD_MD, MSCS_MD
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 407

13.6.4.1.7 Deletion of Personal Data (Subcontracting for MRO
Processes)
Subcontracting for MRO Processes ((IS-AD-SUC) might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Subcontracting for MRO Processes (IS-AD-SUC) - Special
Stocks
Destruction Object
MM_STO_SOBES_DEST
ILM Object
MM_STO_SOBES
Report
MM_STO_SOBES_DES
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Subcontracting for MRO Processes (IS-
AD-SUC) - Special Stock
EoP check Checks tables MSFS_MD, MSFD_MD,
MSIS_MD, MSID_MD, MSRS_MD,
MSRD_MD
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
408
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.7 Sales
Standard Authorization Objects
The following table explains where you can nd the standard authorization objects available for line of business
Sales and related functionality (transaction SU21):
Class Description
SD
Sales and Distribution
LE_T
Logistics Execution - Transportation
LE_V
Logistics Execution - Shipping
WG
For Global Trade Management (GTM): Retailing
● Trading Contract: Authorization for Organizational Data (W_WBHK_ORG)
● Trading Contract: Authorization for Trading Contract Type (W_WBHK_TCT)
13.7.1
Deletion of Personal Data in Sales
Use
Applications in the line of business Sales might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA
on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Sales documents Archiving object SD_VBAK
Billing documents Archiving object SD_VBRK
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 409

Application Provided Deletion Functionality
Self-billing Archiving object SBWAP_TRN
Empties management: Archiving of monthly empties stock Archiving object BEV1_EMBD
Empties management: Archiving of empties update Archiving object BEV1_EMFD
Agreements Archiving object SD_AGREEM
Condition records Archiving object SD_COND
Customer master data Archiving object FI_ACCRECV
Deliveries Archiving object RV_LIKP
Shipment documents Archiving object SD_VTTK
Shipment cost documents Archiving object SD_VFKK
Advanced Returns Management data
Archiving object MSR_TRC
Trading contracts
● Archiving object WB2
● Report WB2_UPDATE_EOP_FROM_ARCHIVE
Campaigns Data destruction object SD_CAMPAIGN_DESTRUCTION
Relevant Application Objects and Available EoP Functionality
Application Implemented Solution (EoP or WUC) Further Information
● Sales & Distribution (ERP_SD)
EoP check This EoP check includes business in the
areas of the following:
● Sales
● Billing
● Delivery
●
Empties Management in SD
(ERP_SD_BIL_EM)
EoP check This EoP check includes business in the
areas of the following:
● Supplier
Empties data from invoice receipt
● Customer
Empties account for customers
410 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Implemented Solution (EoP or WUC) Further Information
● Global Trade Management Position
Management (LO_GT_PM)
● Global Trade Management Trading
Contract (LO_GT_TC)
● Global Trade Management Trading
Expenses (LO_GT_TE)
● Global Trade Management TEW
(LO_GT_TEW)
EoP check This EoP check includes business in
Global Trade Management (LO-GT).
More Information
For more information about application objects and deletion functionality, see the product assistance for SAP
S/4HANA
on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 under Product Assistance
Enterprise Business Applications Sales Order and Contract Management System Administration .
13.7.2 Global Trade Management
13.7.2.1 Network and Communication Channel Security
The information below shows the communication channels used, the protocol used for the connection, and the
type of data transferred.
Connection to a SAP FSCM System
For Global Trade Management, you have the option to use an external SAP FSCM system to create forward
exchange transactions. If you install SAP FSCM on a separate system, you require an RFC connection. If you
install SAP FSCM together with Global Trade Management on one system, no RFC connection is necessary.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 411

Communication Path Protocol Used Type of Data Transferred Data Requiring Special Pro
tection
SAP S/4HANAsystem - SAP
FSCM system (Financial Sup
ply Chain Management)
RFC Application data n/a
RFC connections can be protected using Secure Network Communications (SNC). For more information about
setting up the RFC connection, and the prerequisites (authorizations), see Customizing for SAP S/4HANA
under Logistics General Global Trade Management Currency Hedging Maintain RFC Destination of CFM
System
.
Connection to an External Global Trade Services System
You can connect Global Trade Management to an external Global Trade Services (GTS) system in order to
check whether the contract data for Global Trade Management adheres to the prevailing legal requirements
(import/export controls, global trade data).
Communication Path Protocol Used Type of Data Transferred Data Requiring Special Pro
tection
SAP S/4HANA system – GTS
system
RFC Application data n/a
All users in the SAP S/4HANA system can call the functions on the GTS server using an RFC entry. In this RFC
entry, you specify a user that is used uniquely for communication with GTS. Assign this communication user to
the following roles for SAP Compliance Management.
Roles for Compliance Management
Role Description
/SAPSLL/LEG_ARCH GTS
Archiving
/SAPSLL/LEG_LCE_APP GTS
Legal Control Export: Specialist
/SAPSLL/LEG_LCI_APP GTS
Legal Control Import: Specialist
/SAPSLL/LEG_SPL_APP GTS
Sanctioned Party List: Specialist
/SAPSLL/LEG_SYS_COMM GTS
(Technical) System Communication
DIAG and RFC connections can be protected using Secure Network Communications (SNC). HTTP
connections are protected using the Secure Sockets Layer (SSL) protocol. SOAP connections are protected
with Web services security.
Note
We strongly recommend using secure protocols (SSL, SNC) whenever possible.
412
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

For more information, see Transport Layer Security and Web Services Security in the SAP NetWeaver Security
Guide.
13.7.2.2 Deletion of Personal Data
Use
The Global Trade Management (LO-GT) application might process data (personal data) that is subject to the
data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM)
to control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
Trading Contract Archiving Trading Contract (LO-GT) Archiving object WB2
Report:
WB2_UPDATE_EOP_FROM_ARCHIVE.
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution Further Information
Global Trade Management:
● LO-GT-PM
● LO-GT-TE
● LO-GT-TEW
● LO-GT-TC
EoP check This includes the business in the areas
of:
Trading Contract (LO-GT-TC)
Conguration: Simplied Blocking and Deletion
You congure the settings the related to the blocking and deletion of customer and supplier master data in
Customizing for
Logistics - General under Business Partner Deletion of Customer and Supplier Master
Data. .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 413
13.8 Service
13.8.1 Warranty Management
13.8.1.1 Authorizations
Warranty (LO-WTY) uses the authorization concept provided by the SAP NetWeaver AS for ABAP. Therefore,
the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS Security Guide
ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used.
Authorization Object Description
C_WTY_ACT Warranty: Actions Authorization Object
C_WTY_OBJ Warranty: Process Object Authorization Object
C_WTY_STAT Warranty: Status Authorization Object
414 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.8.1.2 Deletion of Personal Data
Use
Warranty (LO-WTY) might process data (personal data) that is subject to the data protection laws applicable in
specic countries. You can use SAP Information Lifecycle Management (ILM) to control the blocking and
deletion of personal data. For more information, see the product assistance for SAP S/4HANA on the SAP Help
Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components Data
Protection
.
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Warranty (LO-WTY) Archiving Object
WTY_CLAIM
ILM Object
WTY_CLAIM
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Warranty (LO-WTY) EoP check
Checks tables:
PNWTYH, PNWTYV
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 415

13.9 Sourcing and Procurement
13.9.1 Authorizations
Front-End Roles
To use the Fiori Launchpad in SAP S/4HANA, you have to apply the SAP S/4HANA role concept based on
business catalogs that are assigned to business roles. For the front-end, the following standard business roles
are available for Sourcing and Procurement. You can use these roles as templates for your own roles. For more
information, see the SAP S/4HANA UI Technology Guide at the SAP Help Portal under http://help.sap.com/
s4hana_op_1709
Product Documentation .
Business Roles
Role Description
SAP_BR_AP_ACCOUNTANT_PROCUREMT
Accounts Payable Accountant - Procurement
SAP_BR_BUYER
Strategic Buyer
SAP_BR_EMPLOYEE_PROCUREMENT
Employee - Procurement
SSAP_BR_PURCHASER
Purchaser
SAP_BR_PURCHASING_MANAGER
Purchasing Manager
Back-End Roles
In the back-end, you have to create roles in transaction PFCG and assign business catalogs to the roles. For
more information, see the SAP S/4HANA UI Technology Guide at the SAP Help Portal under http://
help.sap.com/s4hana_op_1709 Product Documentation .
If you have converted your system from SAP ERP to SAP S/4HANA, you may still be accessing transactions via
the SAP Easy Access menu. To support this case, the standard role templates for back-end roles are still
available and are listed below:
Back-End Roles (Relevant for System Converted from SAP ERP)
Role Description
SAP_MM_PUR_ADDITIONAL_FUNC Non-Assigned Purchasing Functions
SAP_MM_PUR_ARCHIVE Archive Purchasing Documents
416 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Role Description
SAP_MM_PUR_ARCHIVE_LISTS Analyses Using the Purchasing Archive
SAP_MM_PUR_CONDITIONS Conditions in Purchasing - Overview
SAP_MM_PUR_CONDITIONS_DISCOUNT Discounts in Purchasing
SAP_MM_PUR_CONDITIONS_PRICES Prices in Purchasing
SAP_MM_PUR_CONFIRMATION Conrmations
SAP_MM_PUR_CONTRACT_LISTS Lists for Outline Agreements
SAP_MM_PUR_CONTRACT_MESSAGE Output Outline Agreements
SAP_MM_PUR_CONTRACT_MESSAGE_MT General Message Maintenance for Outline Agreements
SAP_MM_PUR_CONTRACT_RELEASE Release Outline Agreements
SAP_MM_PUR_CONTRACTING Process Contracts
SAP_MM_PUR_DISPLAY_OBJECTS General Display Functions in Purchasing
SAP_MM_PUR_GENERAL General Functions in Purchasing
SAP_MM_PUR_INFORECORD Maintain Purchasing Info Record
SAP_MM_PUR_INFORECORD_LISTS Lists of Purchasing Info Records
SAP_MM_PUR_LIS_GENERAL General Analyses for LIS
SAP_MM_PUR_LIS_SERVICE LIS Analyses for Services
SAP_MM_PUR_LIS_STOCK_MATERIAL LIS Analyses for Stock Material
SAP_MM_PUR_LIS_VE LIS Analyses for Vendor Evaluation
SAP_MM_PUR_LISTS_GENERAL General Analyses in Purchasing
SAP_MM_PUR_MASS_CHANGE Mass Maintenance in Purchasing
SAP_MM_PUR_MESSAGE Output Purchasing Documents
SAP_MM_PUR_MESSAGE_MAINTENANCE General Message Maintenance in Purchasing
SAP_MM_PUR_MPN_AMPL Approved Manufacturer Parts
SAP_MM_PUR_MPN_AMPL_ARCHIVE Archive Approved Manufacturer Parts List
SAP_MM_PUR_NEGOTIATION_LISTS Lists for Purchasing Negotiations
SAP_MM_PUR_PO_RELEASE Release Purchase Orders
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 417

Role Description
SAP_MM_PUR_PR_LISTS Lists of Purchase Requisitions
SAP_MM_PUR_PR_RELEASE Release Purchase Requisitions
SAP_MM_PUR_PURCHASEORDER Process Purchase Orders
SAP_MM_PUR_PURCHASEORDER_LISTS Lists of Purchase Orders
SAP_MM_PUR_PURCHASEREQUISITION Process Purchase Requisitions
SAP_MM_PUR_QUOTA_ARRANGEMENT Maintain Quota Arrangement
SAP_MM_PUR_QUOTA_MAINTENANCE Revise Quota Arrangement
SAP_MM_PUR_QUOTATION Maintain Quotation
SAP_MM_PUR_RFQ Process Request for Quotation
SAP_MM_PUR_RFQ_LISTS Lists of Requests for Quotations
SAP_MM_PUR_SCHEDULE Maintain Scheduling Agreement Delivery Schedules and Re
leases
SAP_MM_PUR_SCHEDULE_MAINTENANC Administer Scheduling Agreements
SAP_MM_PUR_SCHEDULEAGREEMENT Process Scheduling Agreements
SAP_MM_PUR_SERVICE Service Entry Sheet
SAP_MM_PUR_SERVICE_CONDITIONS Service Conditions for Service
SAP_MM_PUR_SERVICE_LISTS Lists of Service Entry Sheets
SAP_MM_PUR_SERVICE_TRANSFER Data Transfer for Services
SAP_MM_PUR_SOURCE_LIST Maintain Source List
SAP_MM_PUR_SRV_CONDITIONS_GEN Service Conditions for Services (General)
SAP_MM_PUR_SRV_MODEL_SPEC Maintain Model Service Specications
SAP_MM_PUR_SRV_STANDARD_SPEC Maintain Standard Service Specications
SAP_MM_PUR_SRV_VENDOR_COND Service Conditions for Vendor
SAP_MM_PUR_SRV_VENDOR_PLANT_CO Service Conditions for Vendor and Plant
SAP_MM_PUR_SUPPLIER_LOGISTICS Logistics information for the vendor on the Internet
SAP_MM_PUR_TAXES Taxes in Purchasing
418 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Role Description
SAP_MM_PUR_VE Maintain Vendor Evaluation
SAP_MM_PUR_VE_LISTS Lists of Vendor Evaluations
SAP_MM_PUR_VE_MAINTENANCE Vendor Evaluation in the Background
SAP_MM_PUR_VENDOR_PRICE Change Prices for Vendor
SAP_MM_PUR_SOURCE_LIST Maintain Source List
SAP_AUDITOR_BA_MM_PUR This transaction role allows evaluations to be collected,
structured, and congured for the audit area:
● Business Audit - Process View
● Purchasing: From Purchase Order to Outgoing Payment
● Purchasing
SAP_AUDITOR_BA_MM_PUR_A This role provides read access for the audit area:
● Business Audit - Process View
● Purchasing: From Purchase Order to Outgoing Payment
● Purchasing
SAP_MM_IV_CLERK_BATCH1 Enter Invoices for Verication in the Background
SAP_MM_IV_CLERK_BATCH2 Manual Processing of Invoices Veried in the Background
SAP_MM_IV_CLERK_GRIR_MAINTAIN GR/IR Clearing Account Maintenance
SAP_MM_IV_CLERK_GRIR_MAITAIN GR/IR Clearing Account Maintenance
SAP_MM_IV_CLERK_ONLINE Online Invoice Verication
SAP_MM_IV_CLERK_PARK Park Invoices
SAP_MM_IV_CLERK_RELEASE Invoice Release
SAP_MM_IV_SUPPLIER_FINANCE Settlement Information for Vendor (External Supplier) on
the Internet
SAP_MM_IV_CLERK_AUTO Automatic Settlements
SAP_AUDITOR_BA_MM_IV This transaction role allows evaluations to be collected,
structured, and congured for the audit area:
● Business Audit - Individual Account Closing
● Prot and Loss Statement
● Material Expense
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 419
Role Description
SAP_AUDITOR_BA_MM_IV_A This authorization role provides read access for the audit
area:
● Business Audit - Individual Account Closing
● Prot and Loss Statement
● Material Expense
Standard Authorization Objects
The table below shows the security-relevant authorization objects that you can use in SAP S/4HANA when you
create back-end roles. These objects were also used in the above listed standard back-end roles.
Authorization Object Description
M_AMPL_ALL Approved Manufacturer Parts List
M_AMPL_WRK Approved Manufacturer Parts List - Plant
M_ANFR_BSA Document Type in RFQ
M_ANFR_EKG Purchasing Group in RFQ
M_ANFR_EKO Purchasing Organization in RFQ
M_ANFR_WRK Plant in RFQ
M_ANFR_LGO Storage Locations in RFQ
M_ANGB_BSA Document Type in Quotation
M_ANGB_EKG Purchasing Group in Quotation
M_ANGB_EKO Purchasing Organization in Quotation
M_ANGB_WRK Plant in Quotation
M_ANGB_LGO Storage Locations in Quotation
M_BANF_BSA Document Type in Purchase Requisition
M_BANF_EKG Purchasing Group in Purchase Requisition
M_BANF_EKO Purchasing Organization in Purchase Requisition
M_BANF_FRG Release Code in Purchase Requisition
M_BANF_WRK Plant in Purchase Requisition
420 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Authorization Object Description
M_BANF_LGO Storage Location in Purchase Requisition
M_BEST_BSA Document Type in Order
M_BEST_EKG Purchasing Group in Purchase Order
M_BEST_EKO Purchasing Organization in Purchase Order
M_BEST_WRK Plant in Purchase Order
M_BEST_LGO Storage Location in Purchase Order
M_EINF_EKG Purchasing Group in Purchasing Info Record
M_EINF_EKO Purchasing Organization in Purchasing Info Record
M_EINF_WRK Plant in Purchasing Info Record
M_EINK_FRG Release Code and Group (Purchasing)
M_LFM1_EKO Purchasing Organization in Vendor Master Record
M_LIBE_EKO Vendor Evaluation
M_LPET_BSA Document Type in Scheduling Agreement Delivery Schedule
M_LPET_EKG Purchasing Group in Scheduling Agreement Delivery Sched
ule
M_LPET_EKO Purchasing Org. in Scheduling Agreement Delivery Schedule
M_LPET_WRK Plant in Scheduling Agreement Delivery Schedule
M_LPET_LGO Storage Location in Scheduling Agreement Delivery Sched
ule
M_ORDR_EKO Purchasing Organization in Source List
M_ORDR_WRK Plant in Source List
M_QUOT_EKO Purchasing Organization (Quotas)
M_QUOT_WRK Plant (Quotas)
M_RAHM_BSA Document Type in Outline Agreement
M_RAHM_EKG Purchasing Group in Outline Agreement
M_RAHM_EKO Purchasing Organization in Outline Agreement
M_RAHM_WRK Plant in Outline Agreement
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 421
Authorization Object Description
M_RAHM_LGO Storage Location in Outline Agreement
M_RAHM_STA Status in Contract
M_SRV_LS Authorization for Maintenance of Service Master
M_SRV_LV Authorization for Maintenance of Model Serv. Specications
M_SRV_ST Authorization for Maintenance of Standard Service Catalog
S_ME_SYNC Mobile Engine: Synchronization of Oine Applications
V_KONH_EKO Purchasing Organization in Master Condition
M_TEMPLATE Create/Change/Delete Public Templates
M_POIVVEND Read Invoices of a Vendor
CMM_MEV_WL CMM: Worklist
CMM_MEV_AD CMM: Accrual Document
M_RECH_BUK Invoices: Company Code
M_RECH_CPY Copy Invoice: Company Code
M_RECH_WRK Invoices: Plant
M_RECH_AKZ Invoices: Accept Invoice Verication Dierences Manually
M_RECH_EKG Invoice Release: Purchasing Group
M_RECH_SPG Invoices: Blocking Reasons
M_RECH_UPL Invoice: Upload
F_BKPF_BUK Accounting Document
13.9.2 Data Storage Security
Using Logical Path and File Names to Protect Access to the File System
Materials Management saves data in les in the le system. Therefore, it is important to explicitly provide
access to the corresponding les in the le system without allowing access to other directories or les (also
known as directory traversal). This is achieved by specifying logical paths and le names in the system that
map to the physical paths and le names. This mapping is validated at runtime and if access is requested to a
directory that does not match a stored mapping, then an error occurs.
422
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
The following lists show the logical le names and paths used by Materials Management and for which
programs these le names and paths apply:
Logical File Names Used
The following logical le names have been created in order to enable the validation of physical le names:
● MM_PURCHASING_INFORECORDS_NEW
○ Programs using this logical le name and parameters used in this context:
○ RM06IBIS
○ RM06IBIE
● MM_PURCHASING_REQUISITIONS_NEW
○ Programs using this logical le name:
○ RM06BBIS
○ RM06BBIE
● SAP_SOURCING_CUSTOMIZING_DOWNLOAD_FILE
○ Programs using this logical le name:
○ BBP_ES_CUST_DOWNLOAD
Logical Path Names Used
The logical le names MM_PURCHASING_INFORECORDS_NEW and MM_PURCHASING_REQUISITIONS_NEW
use the logical le path MM_PUR_ROOT. The logical le name
SAP_SOURCING_CUSTOMIZING_DOWNLOAD_FILE uses the logical le path
SAP_SOURCING_CUSTOMIZING_DOWNLOAD.
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To add the aliases
for the view V_FILEALIA, use transaction SM31.
For more information, see about data storage security, see the respective chapter in the SAP NetWeaver
Security Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 423
Using Data Storage Security
Check whether the conditions are classied as sensitive data. You can protect conditions with the following
authorization objects:
Authorization Object Description
V_KONH_EKO Purchasing Organization in Master Condition
V_KONH_VKS Condition: Authorization for Condition Types
Prices are also potential sensitive data. You can protect the display authority for prices with the value 09 of the
authorization eld ACTVT (Activity) of the purchasing document-specic authorization objects listed below:
Authorization Object Description
M_ANFR_BSA Document Type in RFQ
M_ANFR_EKG Purchasing Group in RFQ
M_ANFR_EKO Purchasing Organization in RFQ
M_ANGB_BSA Document Type in Quotation
M_ANGB_EKG Purchasing Group in Quotation
M_ANGB_EKO Purchasing Organization in Quotation
M_BEST_BSA Document Type in Order
M_BEST_EKG Purchasing Group in Purchase Order
M_BEST_EKO Purchasing Organization in Purchase Order
M_BEST_WRK Plant in Purchase Order
M_BEST_LGO Storage Location in Purchase Order
M_LPET_BSA Document Type in Scheduling Agreement Delivery Schedule
M_LPET_EKG Purchasing Group in Scheduling Agreement Delivery Sched
ule
M_LPET_EKO Purchasing Org. in Scheduling Agreement Delivery Schedule
M_RAHM_BSA Document Type in Outline Agreement
M_RAHM_EKG Purchasing Group in Outline Agreement
M_RAHM_EKO Purchasing Organization in Outline Agreement
424 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Description
M_RAHM_WRK Plant in Outline Agreement
M_RAHM_LGO Storage Location in Outline Agreement
13.9.3 Other Security-Relevant Information
Open Catalog Interface
Use
The Open Catalog Interface (OCI) incorporates external product catalogs into SAP S/4HANA applications
using Hyper Text Transfer Protocol (HTTP). This way, the data required to create purchasing document items in
SAP S/4HANA can be transferred directly from the external catalog to the SAP S/4HANA application.
Reason and Prerequisites
SAP S/4HANA and the catalog communicate via HTTP/HTTPS URL parameters. It is possible for an end user
to identify these parameters and also change them using specialized tools. Security depends heavily on the
fact whether the catalogue system resides before or behind the rewall.
Solution
SAP recommends the following to the customers who wish to integrate SAP S/4HANA and catalogs using
Open catalog Interface (OCI):
● Double check the values transferred from the catalogue into the SAP S/4HANA application manually.
Check whether the values are the same one as the one in the catalogue.
● In addition to that, authority checks are happening on SAP S/4HANA side: the application checks whether
the user is allowed to change the data on SAP S/4HANA side which is transferred from the catalogue.
Example: if a price is transferred from the catalogue into the purchasing document, the system checks
whether the user has the authority to change the price in the purchasing document in general.
● To prevent end users from sning the catalog login data (User names, password), avoid specifying the
login information in the OCI Catalog conguration in Customizing. Instead, congure the catalog to accept
individual user authentication information from the end user. This can be done in the form of SSO (Single
Sign-On) tools, Digital Certicates or Individual Login Information (User name/password). These features
are dependent upon whether the Catalog provider supports the above mentioned features to logon.
You dene the setting for the OCI in Customizing for Materials Management under Purchasing
Environment Data Web Services: ID and Description .
Security-Relevant Logging and Tracing
Use
Purchasing uses change documents to track changes made to purchasing documents. This includes changes
to security-sensitive data such as prices. The following authorization objects specic to purchasing documents
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 425

allow the restriction of the visibility of those change documents using the value 08 of the authorization eld
ACTVT (Activity):
Authorization Object Description
M_ANFR_BSA Document Type in RFQ
M_ANFR_EKG Purchasing Group in RFQ
M_ANFR_EKO Purchasing Organization in RFQ
M_ANFR_WRK Plant in RFQ
M_ANFR_LGO Storage Locations in RFQ
M_ANGB_BSA Document Type in Quotation
M_ANGB_EKG Purchasing Group in Quotation
M_ANGB_EKO Purchasing Organization in Quotation
M_BANF_BSA Document Type in Purchase Requisition
M_BANF_EKG Purchasing Group in Purchase Requisition
M_BANF_EKO Purchasing Organization in Purchase Requisition
M_BANF_FRG Release Code in Purchase Requisition
M_BANF_WRK Plant in Purchase Requisition
M_BANF_LGO Storage Location in Purchase Requisition
M_BEST_BSA Document Type in Order
M_BEST_EKG Purchasing Group in Purchase Order
M_BEST_EKO Purchasing Organization in Purchase Order
M_BEST_WRK Plant in Purchase Order
M_BEST_LGO Storage Location in Purchase Order
M_EINF_EKG Purchasing Group in Purchasing Info Record
M_EINF_EKO Purchasing Organization in Purchasing Info Record
M_EINF_WRK Plant in Purchasing Info Record
M_LFM1_EKO Purchasing Organization in Vendor Master Record
M_LPET_BSA Document Type in Scheduling Agreement Delivery Schedule
426 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Authorization Object Description
M_LPET_EKG Purchasing Group in Scheduling Agreement Delivery Sched
ule
M_LPET_EKO Purchasing Org. in Scheduling Agreement Delivery Schedule
M_ORDR_EKO Purchasing Organization in Source List
M_ORDR_WRK Plant in Source List
M_QUOT_EKO Purchasing Organization (Quotas)
M_QUOT_WRK Plant (Quotas)
M_RAHM_BSA Document Type in Outline Agreement
M_RAHM_EKG Purchasing Group in Outline Agreement
M_RAHM_EKO Purchasing Organization in Outline Agreement
M_RAHM_WRK Plant in Outline Agreement
M_RAHM_LGO Storage Location in Outline Agreement
M_RAHM_STA Status in Contract
13.9.4 Deletion of Personal Data
Use
Purchasing (MM-PUR), Invoice Vericaton (MM-IV), and Supplier and Category Management might process
data (personal data) that is subject to the data protection laws applicable in specic countries. You can use
SAP Information Lifecycle Management (ILM) to control the blocking and deletion of personal data.
Business partner master data can be blocked as soon as business activities that use this data are completed
and the residence period for the data has elapsed; after this time, only users with additional authorizations can
access this data. In Sourcing and Procurement, dierent app types have dierent ways of allowing authorized
users (who must have the role BR_EXTERNAL_AUDITOR) to display the blocked supliers. For the business
documents listed below, users with this role can choose between the listed options:
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 427

Blocked Documents and Display Options
Business Document Display Options for Blocked Documents
● Purchase requisition
● Purchase order
● Purchase contract
● Scheduling agreement
● Shopping cart
● Purchasing info record
●
Using the "Advanced" or "Professional" versions of the
Fiori apps, if available
● Accessing the corresponding transactions in the SAP
Fiori Launchpad via the Me area App Finder SAP
Menu
● Using the corresponding SAP GUI transactions in the
back-end system
If users with the BR_EXTERNAL_AUDITOR role want to display blocked suppliers in the Manage Quota
Arrangements
app or in the Manage Supplier Invoices app, they can do so directly in the Fiori app.
In apps of Supplier and Category Management, all entries related to blocked suppliers are displayed as
Blocked Supplier, and all supplier-related links are disabled. Evaluation scorecards for the blocked suppliers are
not displayed in the scorecards list in the Display Scorecards app. The standard Web Dynpro apps can be used
to display the blocked data. For more information, see the section
Supplier and Category Management
Deletion of Personal Data .
When the retention period for data expires, personal data of the business partner can be destroyed completely
so that it can no longer be retrieved. Retention periods must be dened in the customer system.
For more information about blocking of data, see the product assistance for SAP S/4HANA on the SAP Help
Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components Data
Protection .
Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
Purchase Requisitions Archiving Purchase Requisitions (MM-
PUR)
Archiving object MM_EBAN
Purchasing Documents Archiving Purchasing Documents (MM-
PUR)
Archiving object MM_EKKO
Purchasing Info Records Archiving Purchasing Info Records
(MM-PUR)
Archiving object MM_EINA
Invoice Documents Archiving Invoice Documents (MM-IV) Archiving object MM_REBEL
For documentation about application objects and deletion functionality, see the product assistance for SAP S/
4HANA
on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 under Product Assistance
Enterprise Business Applications Sourcing and Procurement Materials Management (MM) Data
Archiving in Materials Management (MM)
.
428
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Prerequisite: End of Purpose Check
Before objects can be archived, and end of purpose check must be performed. For more information, see the
product assistance for SAP S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 under
Product Assistance Enterprise Business Applications Sourcing and Procurement Materials
Management (MM)
Data Blocking End of Purpose (EoP) Check for Business Partners in MM-PUR, MM-IM,
and MM-IV .
Application Implemented Solution (EoP or WUC) Further Information
Materials Management (MM) End of purpose check (EoP)
For more information about the end of
purpose check, see the product assis
tance for
SAP S/4HANA on the SAP
Help Portal at http://help.sap.com/
s4hana_op_1709 under Product
Assistance Enterprise Business
Applications Sourcing and
Procurement
Materials Management
(MM) Data Blocking End of
Purpose (EoP) Check for Business
Partners in MM-PUR, MM-IM, and MM-
IV .
Conguration of Simplied Blocking and Deletion
To use SAP Information Lifecycle Management (ILM) to simplify the deletion of application-specic personal
data, you have to do the following:
● Activate the following business functions:
○ ILM-Based Deletion of Business Partner Data (BUPA_ILM_BF)
○ ILM-Based Deletion of Customer and Supplier Master Data (ERP_CVP_ILM_1)
○ Information Lifecycle Management (ILM)
● Perform the necessary customizing settings related to SAP Information Lifecycle Management (ILM) in
Customizing for
SAP NetWeaver Application Server Basis Services Information Lifecycle
Management .
● Perform the necessary customizing settings related to the blocking and deletion of business partner
master data in Customizing for Cross-Application Components Data Protection .
● Run transaction ILMARA and maintain and activate the required audit areas for the ILM objects of the
application.
● Run transaction IRMPOL and maintain the required retention policies for the ILM objects of the application.
● Congure the settings related to the blocking and deletion of customer and supplier master data in
Customizing under Logistics - General Business Partner Deletion of Customer and Supplier Master
Data
.
See Also
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 429

For general information about the deletion of personal data, see the following chapters in the product
assistance for SAP S/4HANA that is available on the SAP Help Portal at http://help.sap.com/s4hana <choose a
release> Product Assistance Cross Components :
● SAP Information Lifecycle Management
● Data Protection Deletion of Business Partner Customer and Supplier Master Data
● Data Protection Conguring Data Protection Features Activating Business Functions
13.9.5 Specic Read Access Log Congurations
In Read Access Logging (RAL), you can congure which read-access information to log and under which
conditions.
SAP delivers sample congurations for applications.
Invoice Verication (MM-IV) logs data in order to track who has accessed the bank details in supplier invoices.
You can nd the congurations as described in the Read Access Logging [page 31] chapter.
Fields are logged in the following congurations:
Channel Conguration Fields Logged
Dynpro Recording:
MM_IV/DPP_BANK
IBAN
SWIFT
BANKN
BANKA
SAP Gateway Service ID:
MM_SUPPLIER_INVOICE_MANAGE
IBAN
SWIFT
BANKN
BANKA
RFC Function modules:
BAPI_INCOMINGINVOICE_CHANGE
BAPI_INCOMINGINVOICE_CREATE
BAPI_INCOMINGINVOICE_CREATE1
BAPI_INCOMINGINVOICE_PARK
BAPI_INCOMINGINVOICE_SAVE
MRM_XMLBAPI_INCINV_CREATE
ADDRESSDATA-BANK_ACCT
ADDRESSDATA-BANK_CTRY
ADDRESSDATA-BANK_NO
430 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Channel Conguration Fields Logged
RFC Function modules:
BAPI_INCOMINGINVOICE_GETDETAIL
MRM_XMLBAPI_INCINV_GETDETAIL
ADDRESSDATA-BANK_ACCT
ADDRESSDATA-BANK_CTRY
ADDRESSDATA-BANK_NO
RFC Function module:
MRM_INVOICE_GETLIST
DOC_HEADER_LIST[]-BANKL
DOC_HEADER_LIST[]-BANKN
DOC_HEADER_LIST[]-BANKS
Web Service Interface name:
SupplierInvoiceERPByIDQueryRes
ponse_In
SupplierInvoice/BillFromParty/Bank
AccountID
SupplierInvoice/BillFromParty/Bank
AccountStandardID
SupplierInvoice/BillFromParty/BankIn
ternalID
SupplierInvoice/BillFromParty/Bank
Name
Read access logging can be switched on for the following apps of MM-IV:
● Enter Invoice (MIRO)
● Park Invoice (MIR7)
● Display Invoice Document (MIR4)
● Enter Invoice for Invoice Verication in Background (MIRA)
Read access logging can be switched on for the following SAP Fiori apps of MM-IV:
● Manage Supplier Invoices
● Create Supplier Invoice (Advanced)
13.9.6 Ariba Network Integration
If you want to use integration scenarios with the Ariba Network, see chapter “Business Network Integration” at
the end of this guide.
13.9.7 Supplier and Category Management
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 431
13.9.7.1 Authorizations
Supplier Information and Master Data uses the authorization concept provided by the SAP NetWeaver AS for
ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver
AS Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the SAP NetWeaver Security Guide under User
Administration and Authentication.
Standard Roles
The table below shows the standard roles that are used.
Role Description
/SRMSMC/CATEGORY_MANAGER
Category Manager
/SRMSMC/DNB_REQUESTOR
Role for Requesting Reports from D&B
/SRMSMC/EVALUATION_APPRAISER
Appraiser
/SRMSMC/ACTIVITY_MANAGER
Activity Manager
/SRMSMC/ACTIVITY_PARTICIPANT
Participant in Activity
/SRMSMC/QUESTIONNAIRE_MANAGER
Questionnaire Manager
/SRMSMC/TRANSLATOR
Translator
/SRMSMC/DISPLAY_ALL
Display Role for All Objects in Supplier and Category Man
agement
/SRMSMC/REPORT_EXEC_ADMIN
Technical Role with Authorization to Start Reports in Sup
plier and Category Management
/SRMSMC/BG_SUP_EVAL_BUYSIDE
RFC Background Processing in Supplier Evaluation
We recommend that you do not assign the Appraiser and the Category Manager role to the same person. Under
exceptional circumstances, such as Category Managers lling out questionnaires for other colleagues, you can
grant both roles to the same person.
432
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Note
Please note, that each user has to be assigned to a business partner Employee(I_EMPLOYEE)to have
access to Supplier and Category Management apps. You create a business partner role in the transaction
Maintain HR Master Data and assign it to a user in the transaction User Maintenance .
Authorization Objects Specic to Supplier Information and Master Data
The table below shows the security-relevant authorization objects that are specic to Supplier Information and
Master Data:
Authorization Object Field Value Description
/SRMSMC/DB ACTVT
Reload Enables users to initiate a
download of up-to-date data
from D&B. Since download
ing data from D&B is subject
to charges, you should assign
this role only to employees
who are aware of this impli
cation.
Enables users to interact with
an instance of a business ob
ject of Supplier Information
and Master Data in a specic
way. The authorization object
is used in the /SRMSMC/
DNB_REQUESTOR
role.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 433

Authorization Object Field Value Description
/SRMSMC/BO /BOFU/BO
/SRMSMC/BO_QNR (Ques
tionnaire)
/SRMSMC/BO_SEP (Supplier
Evaluation Prole)
/SRMSMC/BO_SES (Supplier
Evaluation Scorecard)
/SRMSMC/BO_SEV (Supplier
Evaluation)
/SRMSMC/BO_SRS (Supplier
Evaluation Response)
/SRMSMC/MO_PUC (Purchas
ing Category)
/SRMSMC/MO_QLIB (Ques
tion Library)
/SRMSMC/BO_ACT (Activity)
/SRMSMC/BO_TSK (Task)
/SRMSMC/MO_BUPA
As the type of business ob
ject that the user can access,
you can specify the values
listed.
/SRMSMC/AM ACT_TYP
Customizing, activity type This authorization object is
used to dene authorization
settings for accessing activi
ties in SAP Supplier and Cat
egory Management.
Personalization Object “SLC: PFCG Role Attributes”
The personalization object SLC: PFCG Role Attributes (/SRMSMC/PFCG_ROLE_ATTRIBUTES) oers the
following checkboxes:
● Appraiser Role
● Category Manager Role
● Questionnaire Manager Role
● Activity Manager Role
● Activity Participant Role
Setting one of the above checkboxes in a role has the following eects on users to whom the role has been
assigned:
● The users can perform the activities intended for this role. Note that, in addition to the checkbox in the
personalization object, performing these activities also depends on the authorization objects assigned to
the role.
434
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
● Only users for whom the personalization object checkbox is selected are considered during a search, for
example for an appraiser or for a purchaser responsible.
Example:
For a user to be found in a search for a purchaser responsible, the Category Manager Role, the
Questionnaire Manager Role, or the Activity Manager Role checkbox is required, depending on
the process where the search is performed.
13.9.7.2 Internet Communication Framework Security (ICF)
You should only activate those services that are needed for the applications running in your system. For
Supplier Information and Master Data, the following services are needed:
● /sap/bc/ui5_ui5/sap/slc_qnr_resps1
● /sap/bc/ui5_ui5/sap/slc_eval_resps1
● /sap/bc/ui5_ui5/sap/slc_sup_evals1
● /sap/bc/webdynpro/srmsmc/WDA_I_BP_SUPPLIER
● /sap/bc/webdynpro/srmsmc/WDA_I_QNR_OVP
● /sap/bc/webdynpro/srmsmc/WDA_I_SEP_OVP
● /sap/bc/webdynpro/srmsmc/WDA_I_SES
● /sap/bc/webdynpro/srmsmc/WDA_I_SEV_OVP
● /sap/opu/odata/sap/slc_questionnaire_response_srv
● /sap/opu/odata/sap/C_SUPLREVALRSPEVALUATEST_CDS
● /sap/opu/odata/sap/C_SUPLREVALRESPST_CDS
● /sap/bc/webdynpro/srmsmc/wda_puc
● /sap/bc/webdynpro/srmsmc/wda_puc_t
● /sap/bc/webdynpro/srmsmc/WDA_QLB_OVP_MAIN
● /sap/bc/webdynpro/srmsmc/WDA_QLB_OVP_TRNS
● /sap/bc/webdynpro/srmsmc/WDA_QNR_OVP_TRNS
● /sap/bc/webdynpro/srmsmc/wda_sep_ovp_trns
● /sap/bc/webdynpro/srmsmc/wda_act
● /sap/bc/webdynpro/srmsmc/wda_tsk
Use the transaction SICF to activate these services.
For more information about ICF security, see the respective chapter in the SAP NetWeaver Security Guide.
13.9.7.3 Data Storage Security
Cookies
Supplier Information and Master Data uses a Web Dynpro user interfaces. The SAP Web AS must issue cookies
and accept them.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 435

Attachments
You restrict the allowed MIME types and the le size of attachments. You do this in Customizing for Materials
Management under Purchasing Supplier and Category Management for all business processes you want
to use. You can do this in the following Customizing activities:
● Dene MIME Types for Attachments
● Dene Maximum Size for Attachments
The above listed activities are available under each of the business processes nodes in Customizing.
For information about virus scanning for attachments, see Virus Scanning [page 23] and Application-Specic
Virus Scan Prole (ABAP) [page 436].
13.9.7.4 Application-Specic Virus Scan Prole (ABAP)
SAP provides an interface for virus scanners to prevent manipulated or malicious les from damaging the
system. To manage the interface and what le types are checked or blocked, there are virus scan proles.
Dierent applications rely on default proles or application-specic proles.
The Web Dynpro user interfaces of Supplier Information and Master Data require that you activate the virus
scan prole /SIHTTP/HTTP_UPLOAD.
You must make the settings for the virus scan prole in Customizing for Materials Management under
Purchasing Supplier and Category Management Virus Scan Interface
For more information about virus scanning, see Virus Scanning [page 23].
13.9.7.5 Deletion of Personal Data
Use
Supplier and Category Management might process data (personal data) that is subject to the data protection
laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
the SAP Help Portal at http://help.sap.com/s4hana <choose your current on-premise release> Product
Assistance
Cross Components Data Protection .
436
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available EoP/WUC functionality
Supplier and Category Management uses the standard archiving and deletion functions that are available for
the business partner functionality. Therefore, there is no dedicated end of purpose check (EoP) nor a where-
used check (WUC) for Supplier and Category Management.
Application Provided Deletion Functionality
Supplier and Category Management Transaction used for deletion: SARA
Archiving object relevant for deletion: CA_BUPA
For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal at http://
help.sap.com/s4hana <choose your current on-premise release> Product Assistance Cross
Components
Data Protection Archiving .
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of customer and supplier master data in
Customizing under Logistics General Business Partner Deletion of Customer and Supplier Master Data .
Display of Blocked Suppliers
If suppliers have been blocked, they can no longer be used in any Supplier and Category Management
WebDynpro applications. The supplier data is not deleted, but it is no longer visible. Any supplier-related
entries are displayed as Blocked Supplier and all supplier-related links are disabled. Evaluation scorecards for
the blocked suppliers are not displayed in the scorecards list in the Display Scorecards app.
This change is relevant for the following apps:
● Manage Activities
● Monitor Tasks
● Manage Templates
Supplier blocking via CDS view functions in the following apps:
● Manage Purchasing Categories
● Display Scorecards
● Quick Create for Procurement-Related Activities
● Open Activities card on the Procurement Overview Page
● Monitor Responses
● Evaluate Suppliers
● Monitor Responses
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 437

13.9.8 Integration
13.9.8.1 SAP S/4HANA Procurement Hub Integration
SAP S/4HANA currently supports integration with the SAP ERP back-end systems.
13.9.8.1.1 Direct Connectivity
The SAP S/4HANA hub system communicates with the connected SAP ERP back-end systems through XML
messages using peer-to-peer connectivity options in an asynchronous mode.
13.9.8.1.2 Mediated Connectivity
For mediated connectivity, the SAP S/4HANA hub system is connected through SAP Process Integration. The
communication with the connected SAP ERP back-end systems is performed through XML messages in
asynchronous mode.
13.9.8.1.3 Roles and Authorizations in the SAP S/4HANA Hub
System
To process messages coming from the SAP ERP back-end systems, a technical user is needed in the SAP S/
4HANA hub system.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. To
maintain roles for ABAP technology, you use the prole generator (transaction PFCG).
Note
For more information about creating roles, see Role Maintenance.
The table below shows the security-relevant authorization objects that the technical user needs:
438
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Roles and Authorizations in the SAP S/4HANA Hub System
Authorization Object Field Value Description
S_RFC RFC_TYPE Function Module
Type of RFC object for which
access is to be allowed
RFC_NAME /IWNGW/
FM_IN_CREATE_NOTIF
Name of RFC object for
which access is allowed
/IWNGW/
FM_IN_DELETE_NOTIF
ACTVT
Execute
Activity
S_SERVICE SRV_NAME WS
PURCHASEREQUISITION
REPLICATIO3/
PURCHASE_REQUISITIO
N_REPLICATI
Program, transaction, or
function module name
WS
PURCHASEREQUISITION
REPLICATION/
PURCHASE_REQUISITIO
N_REPLICATI
WS
PURCHASEREQUISITION
SOURCINGNO1/
PURCHASE_REQUISITIO
N_SOURCING
/AIF/PROC SRV_TYPE Hash Value for
External Service
Type of check ag and au
thorization for default values
ACTVT Import, Export,
Resubmit
Activity
/AIF/NS
/MMHUB
Namespace
/AIF/IF
PRRECOIN, PRSRCNOTIN
Interface Name
/AIF/IFVER
*
Interface Version
/AIF/VNS
*
Variant Namespace
/AIF/VNAME
*
Name of Interface Variant
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 439

13.9.8.1.4 Roles and Authorizations in the SAP ERP Back-end
System
You can activate Forward Error Handling (FEH) to monitor and process purchase requisitions that fail to copy
be copied to the SAP ERP back-end system.
Users that process entries in FEH need specic authorizations assigned to their users , as well as the following
authorization objects:
Authorization Object Description
S_FEH_INTF
Interfacespecic authorization for FEH
/SAPPO/FLT
Postprocessing Order Filter
/SAPPO/ORD
Postprocessing Order (DISPLAY and EDIT)
/SAPPO/WLA
Assignment of Worklist
13.10 Supply Chain
13.10.1 Ecient Logistics and Order Fulllment
13.10.1.1 Inventory Management
13.10.1.1.1 Deletion of Personal Data
Use
The Materials Management application might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
440
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
Physical Inventory Documents Archiving Physical Inventory Docu
ments (MM-IM)
Archiving object MM_INVBEL
Special Stocks Archiving Special Stock Records (LO-
MD-MM)
Archiving object MM_SPSTOCK
Empties Management Archiving of Empties Update Archiving object BEV1_EMFD
Relevant Application Areas and Available EoP Functionality
Application Implemented Solution Further Information
Materials Management (MM) End of purpose check (EoP) This includes the business in the areas
of:
● External Services Management
(MM-SRV)
● Inventory Management (MM-IM)
● Logistics Invoice Verication (MM-
IV)
● Empties Management (MM-PUR-
EM)
For more information about the end of
purpose check, see the product assis
tance for
SAP S/4HANA on the SAP
Help Portal at http://help.sap.com/
s4hana_op_1709 under Product
Assistance Enterprise Business
Applications Sourcing and
Procurement Materials Management
(MM) Data Blocking End of
Purpose (EoP) Check for Business
Partners in MM-PUR, MM-IM, and MM-
IV
.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 441

● Dene the settings for authorization management in Customizing for Cross-Application Components
under Data Protection Authorization Management . For more information, see the Customizing
documentation.
● Dene the settings for blocking in Customizing for Cross-Application Components under Data Protection
Blocking and Unblocking Business Partner .
13.10.1.2 Direct Store Delivery
13.10.1.2.1 Deletion of Personal Data
Use
The Direct Store Delivery application might process data (personal data) that is subject to the data protection
laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
the SAP Help Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components
Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
Visit List Archiving Visit Lists (LE-DSD) Archiving object /DSD/VL
Settlement Documents Archiving Settlement Documents (LE-
DSD)
Archiving object /DSD/SL
DEX Archiving DEX Streams (LE-DSD) Archiving object /DSD/DEX
Route Settlement Data destruction in Route Settlements
(LE-DSD)
Destruction object /DSD/
HH_RAHD_DESTRUCTION
DSD Connector Data destruction in DSD Connector
(LE-DSD)
Destruction object /DSD/
ME_TOUR_HD_DESTRUCTION
DSD Loading Data destruction in DSD Loading (LE-
DSD)
Destruction object /DSD/
SV_LC_HD_DESTRUCTION
Visit Plan Data destruction in Visit Plants (LE-
DSD)
Destruction object /DSD/
VC_VPH_DESTRUCTION
Deal Conditions Data destruction in Deal Conditions
(LE-DSD)
Destruction object /DSD/
PR_HEAD_DESTRUCTION
442 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available EoP Functionality
Application Implemented Solution (EoP or WUC) Further Information
Logistics Execution (LE) EoP check This includes the business in the areas
of:
● Direct Store Delivery (Backend)
(LE-DSD)
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
● Dene the settings for authorization management in Customizing for Cross-Application Components
under Data Protection Authorization Management . For more information, see the Customizing
documentation.
● Dene the settings for blocking in Customizing for Cross-Application Components under Data Protection
Blocking and Unblocking Business Partner .
13.10.1.3 Internet Communication Framework Security (ICF)
You should only activate those services that are needed for the applications running in your system. For
Logistics Execution, the following services are needed:
● LECI
● VL31W
● VL32W
● VLPODW1
● VLPODW2
Use the transaction SICF to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information about ICF security, see the respective chapter in the SAP NetWeaver Security Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 443

13.10.1.4 Deletion of Personal Data (Returnable Packaging
Logistics)
Use
Returnable Packaging Logistics might process data (personal data) that is subject to the data protection laws
applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components
Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Returnable Packaging Logistics (IS-A-RL) Archiving Object
VHURL_AC
VHURL_CP
VHURL_PO
VHURL_ST
VHURL_TR
Destruction Objects
VHURL_CP_DESTRUCTION
VHURL_RR_DESTRUCTION
ILM Objects
VHURL_AC
VHURL_PO
VHURL_ST
VHURL_TR
VHURL_CP_DEST
VHURL_RR_DEST
444
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Returnable Packaging Logistics (IS-A-
RL)
EoP check
Checks tables:
RLACCT, RLPSHPA, RLPSHP
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection→Blocking and Unblocking of Data→Customer Master/
Supplier Master Deletion.
13.10.2 Extended Warehouse Management
13.10.2.1 Authorizations
Extended Warehouse Management (EWM) uses the authorization concept provided by the SAP NetWeaver AS
for ABAP or AS Java. Therefore, the recommendations and guidelines for authorizations as described in the
SAP NetWeaver AS Security Guide ABAP and SAP NetWeaver AS Security Guide Java also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP and the User Management
Engine’s user administration console on the AS Java.
Note
For more information about how to create roles, see the SAP NetWeaver Security Guide under User
Administration and Authentication.
Standard Authorization Objects
To gain an overview of the authorization objects for EWM, proceed as follows:
1. Open transaction AUTH_DISPLAY_OBJECTS to display active authorization objects.
2. In the overview, expand the following subtree of authorizations related to EWM.
1. Authorizations Extended Warehouse Management (SCWM)
2. Dock Appointment Scheduling (SCDS)
3. Authorizations SCM Basis (SCMB)
4. Master Data Authorization Objects (SCMD)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 445

If you want to display the technical names of the authorization objects, choose Edit Technical Names
On .
3. If you want to get a detailed description, choose the Information button next to the authorization object you
are interested in.
Warehouse-Based Authorization
Warehouse-Specic Field in Authorization Objects
If you have multiple warehouses modelled in EWM, you may need people working in one warehouse to be able
to access data from another warehouse. Many authorization objects in EWM contain a specic authorization
eld for this purpose, for example:
● /SCWM/LGNU (Warehouse Number/Warehouse Complex)
This is the most commonly used authorization eld. It is used, for example, in EWM monitor authorization
object /SCWM/MO.
● /SCWM/ORG (Location/Organizational Unit)
● /SCMB/LGNU (Warehouse Number/Warehouse Complex)
Warehouse in Customizing or Administration
In other cases, such as in administration or Customizing, EWM does not use specic authorization objects.
Instead, you can use generic authorization objects to limit the access to tables and views, for example:
● S_TABU_NAM (Table Access by Generic Standard Tools)
● S_TABU_LIN (Authorization for Organizational Unit)
Example
The Customizing activity Dene Storage Bin Types has the assigned Customizing object /SCWM/T303. The
underlying database table /SCWM/T303 contains eld LGNUM (warehouse number) with data element /SCWM/
LGNUM (Warehouse Number/Warehouse Complex). You can use generic authorization objects to limit the
access to tables and views, as follows:
● Use authorization object S_TABU_NAM to limit access to Customizing object /SCWM/T303.
● Use authorization object S_TABU_LIN to limit access based on organizational criteria.
You can also use authorization eld ORG_CRIT (Organization Criterion for KeySpecic Authorization) and
use value /SCWM/LGNU (Warehouse Number/Warehouse Complex) to be able to enter a warehouse in
ORG_FIELD1.
For more information, see the documentation of authorization objects S_TABU_NAM and S_TABU_LIN in
transaction SU21.
BRFplus
BRFplus is sometimes used in EWM, for example, in Labor Management. However, BRFplus does not recognize
organizational units such as the warehouse. Therefore, if BRFplus entities should be separated based on
warehouse, you must consider this during the implementation phase so that you can use alternative BRFplus
mechanisms.
446
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
For information about the authorization concept of BRFplus, see SAP Library for SAP NetWeaver at https://
help.sap.com/netweaver. In SAP Library, search for Business Rule Framework plus (BRFplus) and then choose
Concepts Authorizations .
Critical Combinations
Appointment Planner for Carrier
Note
These authorizations are relevant only if you are using SAP Dock Appointment Scheduling.
SAP Dock Appointment Scheduling oers a collaboration scenario where appointment planners for carriers
can log on to the SAP Dock Appointment Scheduling system, and view and maintain appointments for their
carrier. Since this potentially means that employees of a dierent company access SAP Dock Appointment
Scheduling from outside the company network, you must put a special focus on authorizations. This kind of
user should have very limited authorizations. As well as this, they should be able to access data of their own
carrier only, and not be able to access other carriers’ data. They should not be able to see internal data, like
overall capacities of loading points. Therefore, you must be very careful and restrictive when assigning roles
and authorizations to this kind of user.
SAP Dock Appointment Scheduling delivers a special authorization eld for this.
Note
We recommend that you dene, in the roles, the loading points for which a user may view or create
appointments. You can do this in the Loading Point authorization eld (/SCWM/DSLP) in the authorization
objects Loading Appointment (/SCWM/DSAP) and Slot (/SCWM/DSSL).
In addition, the authorization eld User Process Scope for Dock Appointment Scheduling (/SCWM/DSPS) is very
important. It is available on the Loading Appointment and Slot authorization objects. For appointment planners
for carriers, set this eld to Scope for an Appointment Planner for Carrier. This ensures that this user can create
and view appointments only for the carrier that is assigned to him or her. Otherwise such a user could create
appointments for any carrier.
Warehouse Management Monitor: Authorization to Display Batch Execution Data
In the warehouse management monitor (/SCWM/MON), you can execute selections using batch jobs. You can
view the results in the warehouse management monitor. During the selection, the system performs the normal
authorization checks and selects and stores only data for which the user has authorization in the data
containers for the warehouse management monitor. But if these data containers are then displayed by other
users, the system does not perform these authorization checks. Therefore, you should only grant the
authorization to display batch execution data for monitor nodes or users where these checks are not critical.
The authorization object used for the authorization to display batch execution data in the warehouse
management monitor is /SCWM/DATC. For more information about this authorization object and the warehouse
management monitor, see SAP Library for SAP S/4HANA at https://help.sap.com/s4hana . In SAP Library,
choose SAP S/4HANA Enterprise Business Applications Supply Chain Extended Warehouse
Management Monitoring Warehouse Management Monitor .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 447

Maintaining Authorizations for Integration with SAP Components
Maintaining Authorizations for Integration of EWM Within Supply Chain
Note
This is not relevant for standalone SAP Dock Appointment Scheduling.
For the integration of EWM within Supply Chain, that is, with Logistics Execution (LE) and Logistics – General
(LO), use the authorization roles for the remote function call (RFC) destination users. For more information
about these roles, see SAP Library for SAP S/4HANA at https://help.sap.com/s4hana . In SAP Library,
choose SAP S/4HANA Enterprise Business Applications Supply Chain Extended Warehouse
Management
Roles for Extended Warehouse Management (EWM) .
For the integration from Supply Chain to EWM, for example, the role /SCWM/ERP_EWM_INTEGRATION exists.
For the integration from EWM to Supply Chain, the corresponding RFC users also require the proper
authorizations. For more information, see SAP Note
2081387 .
In some cases, for example, for migration functions like transaction /SCWM/MIG_PRODUCT, the RFC enabled
function module RFC_READ_TABLE is called on the Supply Chain side from EWM. For such scenarios, the
corresponding RFC user requires this authorization. To avoid misuse, you should restrict the tables to be
accessed to a minimum. You can therefore use the authorization objects S_TABU_NAM or S_TABU_DIS.
If you grant the usage of RFC function RFC_READ_TABLE to an RFC user, it is very important that you restrict
the tables that can be accessed to a minimum to avoid misuse.
Maintaining Authorizations for Data Transfer to SAP Business Warehouse
Note
This is not relevant for standalone SAP Dock Appointment Scheduling.
You can exclude DataSources from the extraction to SAP Business Warehouse (SAP BW).
Data that is stored in the extraction structure of this DataSource cannot be transferred to SAP BW.
1. In Customizing for Extended Warehouse Management, choose Integration with Other SAP Components
Data Transfer to Business Warehouse General Settings Limit Authorizations for Extraction .
2. Choose New Entries and choose a DataSource that you want to exclude from the extraction.
3. Choose the SAP BW system for which you want no more data for this DataSource to be extracted.
4. In the Ex. Extr. eld, enter whether or not you want to exclude the DataSource from the extraction.
5. Save your entries and specify a transport request.
Maintaining Authorizations for Data Transfer Between Shipping and Receiving (EWM) and
SAP Dock Appointment Scheduling
Note
This is not relevant for standalone SAP Dock Appointment Scheduling.
SAP Dock Appointment Scheduling and Shipping and Receiving (S&R) are two independent components. But
it is also possible to integrate the components, for example, so that the system communicates appointment
448
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

status changes in SAP Dock Appointment Scheduling to S&R and appointment status changes in S&R to SAP
Dock Appointment Scheduling. For more information, see SAP Library for SAP S/4HANA at https://
help.sap.com/s4hana . In SAP Library, choose SAP S/4HANA Enterprise Business Applications Supply
Chain Extended Warehouse Management SAP Dock Appointment Scheduling Integration with SAP
EWM
.
For integration between SAP Dock Appointment Scheduling and S&R, the system uses queued RFC (qRFC)
technology.
Using Standard Roles for SAP Dock Appointment Scheduling to EWM Integration
For the integration from SAP Dock Appointment Scheduling to S&R, the technical role /SCWM/
DAS_TO_EWM_INTEGRATION is available. It contains the necessary authorizations to update the relevant S&R
objects. The role does not contain any menu entries or transactions, as it is only a technical role for RFC
communication. You must assign this role to the SAP Dock Appointment Scheduling user or RFC user,
depending on if you use RFC communication, with which the integration is done.
Maintaining RFC Authorizations for Internal Communication in EWM
For RFC communication, users usually require the authorizations for authorization object S_RFC. As RFCs are
potential security risks, you should be very restrictive in granting them. In certain cases, EWM also uses RFCs
for internal purposes, for example for parallel processing or for asynchronous communication. For these
purposes, no RFC authorizations have to be granted as these calls are within the SAP S/4HANA system.
EWM also uses specic RFC-enabled function modules, which are used to extract content from qRFCs. For
example, these function modules are used to extract the warehouse number or delivery number from qRFCs.
These function modules do not perform data changes in EWM and also do not return data to a caller. They are
required for delivery processing and for displaying of message queue entries in the warehouse management
monitor.
The function modules are in the following special function groups:
● /SCWM/CORE_MQ_REPLAY (Message Queue Moni: Replay Functions)
● /SCWM/CORE_RF_MQ_REPLAY (Replay Function Modules for RF)
● /SCWM/DELIVERY_MQ_REPLAY (Replay Function Modules for Deliveries)
● /SCWM/ERP_MQ_REPLAY (Replay Function Modules - ERP Interface)
● /SCWM/SR_MQ_REPLAY (Replay Function Modules - S&R)
● /SCWM/VAS_MQ_REPLAY (Replay Function Modules for VAS)
● /SCWM/WC_SERVICE_MQ_REPLAY (Replay Function Modules for Workcenter)
● /SCWM/WAVE_MGMT_MQ_REPLAY (Replay Function Modules for Wave)
If you use the message queue monitor node in the warehouse management monitor, you must add these
function groups to authorization S_RFC. Use the activity Execute (16) and the Function Group (FUGR) type of
RFC object.
For delivery and warehouse task processing, for example, conrming and creation of warehouse tasks, you
must add the function group /SCWM/DELIVERY_MQ_REPLAY (Replay Function Modules for Deliveries) to
authorization S_RFC.
These authorizations are already in the standard roles in EWM, so they are only relevant if you create your own
roles.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 449

13.10.2.2 Internet Communication Framework Security (ICF)
You should only activate those services that are needed for the applications running in your system. For this
area the following services are needed:
● /sap/bc/gui/sap/its/scwm/rfui
This service can be used, for example, to allow warehouse workers to use transaction /SCWM/RFUI from
mobile applications. The service can be accessed from the SAP console or by using ITS mobile. For more
information, see SAP Library for
SAP S/4HANA at https://help.sap.com/s4hana . In SAP Library choose
SAP S/4HANA Enterprise Business Applications Supply Chain Extended Warehouse Management
Radio Frequency Framework Work Processing Using Radio Frequency Resource Management Using
Radio Frequency
.
● /sap/bc/webdynpro/scwm/
In this path various Web Dynpro user interfaces (UIs) for Extended Warehouse Management as well as for
SAP Dock Appointment Scheduling are contained.
● /sap/bc/srt/xip/scwm
Contains services which are used for SAP Process Integration communication.
● /sap/bc/srt/rfc/scwm
Contains services which are used for remote function call (RFC) communication. For example,
RFID_AII_EWM which is used to exchange radio frequency identication information with SAP Auto-ID
Infrastructure (SAP AII).
Use the transaction SICF to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information about ICF security, see the respective chapter in the SAP NetWeaver Security Guide.
13.10.2.3 Data Storage Security
Using Logical Path and File Names to Protect Access to the File System
Extended Warehouse Management (EWM) saves data in les in the le system. Therefore, it is important to
explicitly provide access to the corresponding les in the le system without allowing access to other
directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
450
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

The following lists show the logical le names and paths used by EWM and for which programs these le names
and paths apply:
Logical File Names Used
The following logical le names have been created in order to enable the validation of physical le names:
● EWM_PI_DOWNLOAD
○ Transactions or programs using this logical le name and parameters used in this context:
○ Transaction /SCWM/PI_DOWNLOAD
○ Program /SCWM/R_PI_STOCK_DWNLD
○ Parameters used in this context:
○ <PARAM1> = Warehouse number (CHAR 4)
○ <PARAM2> = Counter (NUM2)
○ Logical le path used: EWM_GLOBAL_PATH
Note
The logical lename is xed and cannot be changed. The logical le contains a physical lename.
The logical le path contains a physical path. The validation and alias denition do not apply for
this logical lename.
● EWM_PI_UPLOAD
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/PI_UPLOAD
○ Program /SCWM/R_PI_FILEUPLD
○ Parameters used in this context:
○ <PARAM1> = Warehouse number (CHAR 4)
○ <PARAM2> = Creation Date (DATS8)
○ <PARAM2> = Counter (NUM2)
○ Logical le path used: EWM_GLOBAL_PATH
Note
The logical lename is xed and cannot be changed. The logical le contains a physical lename.
The logical le path contains a physical path. The validation and alias denition do not apply for
this logical lename.
● EWM_STOCK_UPLOAD
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/ISU
○ Program /SCWM/R_INITIALSTOCKUPLOAD
○ Parameters used in this context: <PARAM1> = Warehouse number (CHAR 4)
○ Logical le path used: EWM_STOCK_UPLOAD_PATH
● EWM_STOBIN_UPLOAD
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 451

○ Transactions or programs using this logical le name:
○ Transaction /SCWM/SBUP
○ Program /SCWM/TLAGP_UPLOAD
○ Logical le path used: EWM_STOBIN_UPLOAD_PATH
● EWM_STOBIN_SORT_UPLOAD
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/SRTUP
○ Program /SCWM/TLAGPS_UPLOAD
○ Logical le path used: EWM_STOBIN_SORT_UPLOAD_PATH
● EWM_MS_RESULT
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/MS_RESULT
○ Program /SCWM/R_MS_RESULT_READ
○ Parameters used in this context: <PARAM1> = Warehouse number (CHAR 4)
○ Logical le path used: EWM_GLOBAL_PATH
Note
The logical lename is xed and cannot be changed. The logical le contains a physical lename.
The logical le path contains a physical path. The validation and alias denition do not apply for
this logical lename.
● EWM_ELS_FRML
● EWM_ELS_ST
● EWM_ELS_STE
● EWM_ELS_SEQ
● EWM_ELS_ASS
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/ELS_UPLOAD
○ Program /SCWM/ELS_UPLOAD
○ Logical le path used: EWM_GLOBAL_PATH
Note
The logical lename is xed and cannot be changed. The logical le contains a physical lename.
The logical le path contains a physical path. The validation and alias denition do not apply for
this logical lename.
● EWM_MS_RESULT
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/PI_SAMP_UPDATE
○ Program /SCWM/PI_SAMP_UPDATE_RESULT
○ Parameters used in this context: <PARAM1> = Warehouse number (CHAR 4)
○ Logical le path used: EWM_GLOBAL_PATH
452
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Note
The logical lename is xed and cannot be changed. The logical le contains a physical lename.
The logical le path contains a physical path. The validation and alias denition do not apply for
this logical lename.
● EWM_PRODUCT_UPLOAD
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/MIG_PRODUCT
○ Program /SCWM/R_MIG_PRODUCT
○ Logical le path used: EWM_PRODUCT_UPLOAD_PATH
● EWM_PACKSPEC_UPLOAD
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/MIG_PRODUCT
○ Transaction /SCWM/IPU
○ Program /SCWM/R_MIG_PRODUCT
○ Program /SCWM/R_PS_DATA_LOAD
○ Logical le path used: EWM_PACKSPEC_UPLOAD_PATH
● EWM_PI_COMPL_UPLOAD
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/MIG_PI_COMPL
○ Program /SCWM/R_MIG_PI_COMPL
○ Logical le path used: EWM_PI_COMPL_UPLOAD_PATH
● EWM_TDC_EDGE and EWM_TDC_RSRC
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/TDC_UPLOAD
○ Program /SCWM/TDC_UPLOAD
○ Logical le path used: EWM_GLOBAL_PATH
● EWM_TATT_UPLOAD (Logical File for Upload of Time and Attendance Events)
○ Transactions or programs using this logical le name:
○ Transaction /SCWM/TATT_UPLOAD
○ Program /SCWM/R_LM_TATT_UPLOAD
○ Parameters used in this context: <PARAM1> = Warehouse number (CHAR 4)
○ Logical le path used: EWM_GLOBAL_PATH
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out
which paths are being used by your system, you can activate the corresponding settings in the Security Audit
Log.
For more information about data storage security, see the respective chapter in the SAP NetWeaver Security
Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 453

13.10.2.4 Deletion of Personal Data
Extended Warehouse Management (EWM) might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 under Product Assistance
Cross Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
EWM Warehouse Request Processing
(for example, inbound deliveries, out
bound delivery orders, and production
material requests)
Business partner data is stored in the
warehouse request. For example:
● Partner data in the warehouse re
quest header/item
● Ship-to data and ship-from data
● Owner and entitled-to-dispose
data on item level
You can delete the objects by using the
archiving services. The archiving ob
jects are:
● DLV_INB (Internal Warehouse Re
quest (Inbound Delivery))
● DLV_OUT (Internal Warehouse Re
quest (Outbound Delivery))
● DLV_REQ (Warehouse Request
from External Systems)
● DLV_PROD (Production Material
Request)
EWM Labor Management The processor is recorded in several
EWM documents in Labor Manage
ment, for example, in warehouse orders
and executed workload.
You can delete the objects by using the
archiving services. The archiving ob
jects are:
● WME_WO (Warehouse Order)
● WME_EWL (Executed Workload)
● WME_EPD (Performance Docu
ment)
● WME_ILT (Indirect Labor Task)
EWM Shipping and Receiving In Shipping and Receiving, business
partner data may be stored as carrier
data in transportation units.
You can delete the objects by using the
archiving services. The archiving object
is WME_TU (TU Activity).
EWM Value-Added Services If you use value-added services (VAS),
business partner data may be stored as
owner data or entitled-to-dispose data
in VAS orders.
You can delete the objects by using the
archiving services. The archiving object
is WME_VAS (Value-Added Service Or
der).
EWM Proof of Delivery If you use proof of delivery (transac
tion /SCWM/POD_IMP), business part
ner data may be stored as carrier data,
entitled-to-dispose data, or processor
data in the proof of delivery object.
You can delete by using transaction /
SCWM/POD_IMP
.
454 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Detailed Description Provided Deletion Functionality
EWM Stock Data In EWM, stock data may store business
partner data as, for example, owner
data or entitled-to-dispose data.
You cannot delete directly. You must
clear the corresponding stock so that
the stock does not exist anymore by us
ing the Delete Obsolete Table Entries (/
LIME/BACKGROUND_DELETE_EXEC
) re
port.
EWM Dock Appointment Scheduling In SAP Dock Appointment Scheduling,
business partner data may be stored as
carrier data in loading appointments.
You can delete by using the Delete Slots
and Appointments (/SCWM/
R_DAS_DELETE
) report.
Transportation Management in EWM Business partner data is contained in
shipment objects and freight document
objects.
You can delete the objects by using the
archiving services. The archiving ob
jects are:
● TM_SHP (Shipment)
● TM_FRD (Freight Document)
EWM Warehouse Billing In Warehouse Billing, snapshots may
contain a business partner.
You can delete billing measurements
(BOPF object /SCWM/BM) using archiv
ing object
EWM_WBM.
You can delete billing measure requests
(BOPF object /SCWM/WB_BMR) using
deletion report Deletion of WBMR and
WBMS (/SCWM/WB_WBMR_DELETION).
Relevant Application Objects and Available EoP/WUC Functionality
Application Implemented Solution (EoP or WUC) Further Information
EWM Warehouse Request Processing
(for example, inbound deliveries, out
bound delivery orders, and production
material requests)
A where-used check (WUC) is imple
mented for the business partner object.
A WUC is done for the following data
base tables:
● /SCDL/DB_BPLOC
● /SCDL/DB_EXTNO
● /SCDL/DB_PROCI_O
● /SCDL/DB_PROCI_I
● /SCDL/DB_PROCI_P
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 455

Application Implemented Solution (EoP or WUC) Further Information
EWM Labor Management A WUC is implemented for the business
partner object.
A WUC is done for the following data
base tables:
● /SCWM/EWRKL
● /SCWM/EPD
● /SCWM/WHO
● /SCWM/EPD
For indirect labor tasks, the data is
stored using order document manage
ment (ODM).
The ODM data type is ILT. The corre
sponding header component is ILT with
structure /SCWM/S_ILT_ODM.
EWM Shipping and Receiving A WUC is implemented for the business
partner object.
A WUC is done for the /SCWM/TUNIT
database table.
EWM Value-Added Services A WUC is implemented for the business
partner object.
The data is stored using ODM. The
ODM data type is VASO. The corre
sponding item component is VASI with
structure /SCWM/S_VAS_ODM_ITM.
EWM Proof of Delivery A WUC is implemented for the business
partner object.
A WUC is done for the SCWM/POD data
base table.
EWM Stock Data A WUC is implemented for the business
partner object.
A WUC check is done for the following
database tables:
● /SCWM/STOCK_IW01
● /SCWM/STOCK_IW02
● /SCWM/STOCK_IW03
● /SCWM/STOCK_IW04
EWM Dock Appointment Scheduling A WUC is implemented for the business
partner object.
A WUC is done for the /SCWM/D_DSAPP
database table.
456 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Implemented Solution (EoP or WUC) Further Information
Transportation Management in EWM A WUC is implemented for the business
partner object.
The data is stored using ODM.
● For shipments the ODM data type
is TMSH. The corresponding
header component is TSHD with
structure
/SCMB/
TMDL_ODM_SHP_HDR_STR.
● For freight documents the ODM
data type is TMFR. The corre
sponding header component is
TMFH with structure /SCMB/
TMDL_ODM_FRD_HDR_STR.
Transportation Management in EWM
Warehouse Billing
A WUC is implemented for the business
partner object.
A WUC is done for the following tables:
● /SCWM/D_WB_FDO
● /SCWM/D_WB_PDI
● /SCWM/D_WB_STOCK
● /SCWM/D_WB_WT
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection .
13.10.2.5 Enterprise Services Security
For general information, see the chapters on Web Services Security in the SAP NetWeaver Security Guide and
in the SAP Process Integration Security Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 457
13.10.2.6 Other Security-Relevant Information
Security Aspects of Data Flow and Processes
The following table describes some typical processes and communication channels, along with appropriate
security measures:
Process Security Measure
Mobile devices can be connected using HTTP/ITS mobile (it
is also possible to use the SAP console). This is done based
on the Internet Communication Framework (ICF) service for
RFUI.
For more information, see Internet Communication Frame
work Security (ICF) [page 450].
For certain scenarios, such as connecting automated physi
cal processes (for example, conveyor systems) using SAP
Plant Connectivity, remote function calls (RFCs) are used.
Depending on the scenario, Idocs may also be used (for ex
ample, when warehouse control units are used).
For more information, see the SAP NetWeaver Security
Guide.
Extended Warehouse Management (EWM) oers the possi
bility of uploading and downloading data. In many of these
transactions it is possible to either choose a local le system
(PC) or les on the application server.
Ensure that only a few people can access these transactions
and that access to the application server le system is re
stricted. You should design logical paths and lenames to re
strict the access. For more information, see Data Storage
Security [page 450].
EWM oers a collaborative scenario for SAP Dock Appoint
ment Scheduling. This enables appointment planners for
carriers to access the system using SAP Gateway or Web
Dynpro ABAP technology, for example, from outside the
company network.
In this scenario, users outside of the company or rewall
may access the system. For such scenarios, special atten
tion must be paid to assigning authorizations to these users,
and to the system setup and how the access from outside
the company is granted.
EWM oers a scenario for Warehouse Billing where there is
an integration with the SAP Transportation Management
(SAP TM) system.
In this scenario, EWM can extract billing-relevant information
from SAP TM and send order and settlement information
back to SAP TM. The communication is performed using en
terprise services or Web services.
EWM Fiori apps, for example, for deliveries or returns proc
essing.
In this scenario, SAP Fiori accesses EWM using SAP
Gateway. For more information, see SAP Library for SAP
Fiori.
Security for Additional Applications
Geocoding
EWM can, in some cases, make use of third party geocoding applications, for example, PTV eServer. The
software could be used, for example, to calculate geographical information for the locations or distances for
458
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
transportation lanes. To connect to the third party software, this software may require an RFC destination on
the EWM side. For more information on geocoding, see SAP Library for SAP S/4HANA at https://help.sap.com/
s4hana . In SAP Library, choose SAP S/4HANA Enterprise Business Applications Supply Chain SCM
Basis SCM Basis Master Data Location . For any security issues regarding the third party application, for
example, PTV eServer software, see the third party documentation.
SAP Plant Connectivity for Scale Integration
EWM can, in some cases, integrate an external scale. The software could be used, for example, to calculate the
weight of a handling unit. A sample implementation exists for this in the Determination of HU Weight Using
Scale (/SCWM/EX_WRKC_UI_GET_WEIGHT) Business Add-In. In this example, the system uses SAP Plant
Connectivity to integrate an external scale. This software may require an RFC destination on the EWM side to
connect to SAP Plant Connectivity.
For information about SAP Plant Connectivity, see SAP Help Portal at https://help.sap.com/pco .
13.10.3 Deletion of Personal Data
Use
Location master data may contain personal data that is subject to the data protection laws applicable in
specic countries. You can use SAP Information Lifecycle Management (ILM) to control the blocking and
deletion of personal data. For more information, see the product Assistance for SAP S/4HANA on the SAP Help
Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Enterprise Business Applications
Manufacturing Production Planning and Detailed Scheduling Master Data Location Data Protection
Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
SCM Location Without ILM
You can run the report /SAPAPO/
DELETE_LOCATIONS
from the SAP Easy
Access menu, under
SAP Menu
Logistics SCM Extended Warehouse
Management SCM Basis Master
Data Location ; select the location,
then choose Extras Delete
Location
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 459

Application Detailed Description Provided Deletion Functionality
ILM-enabled SCM Location Refer to What's New for ILM-related
Information for SCM Location
(SCMB_LOC)
Destruction object /SCMB/LOC
ILM object SCMB_LOC
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
SCM Location
End of Purpose (EoP) check
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of location master data in Customizing for SCM
Extended Warehouse Management under SCM Basis Master Data Location Location Master Data
Deletion
.
13.10.4 Transportation Management
This section of the Operations Guide for SAP S/4HANA, on-premise edition contains information on operations
tasks specic to Transportation Management.
13.10.4.1 Security Aspects of Data, Data Flow and Processes
E-mail-Based Tendering Scenario
The gure below shows an overview of the e-mail based tendering scenario for Transportation Management
(TM).
460
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
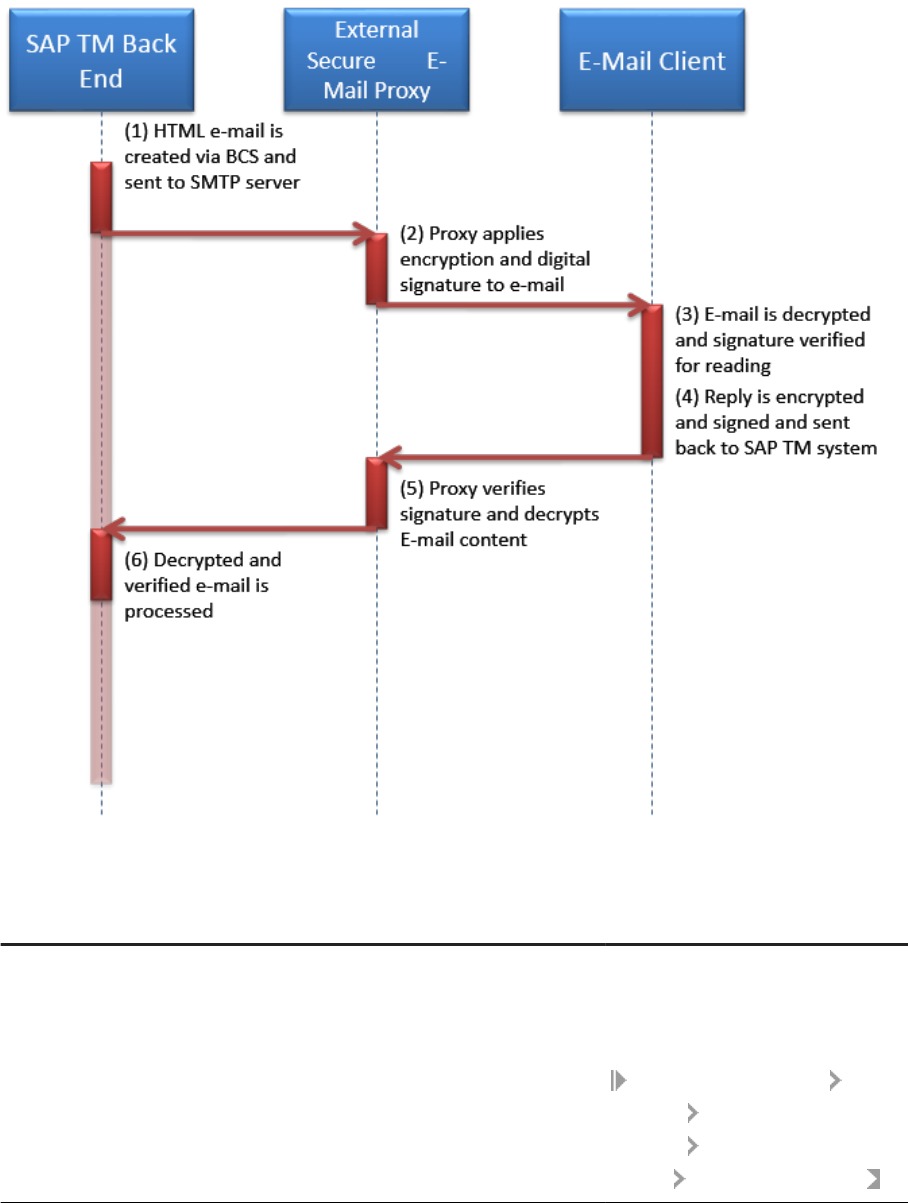
E-Mail-Based Tendering Scenario
Steps for E-Mail Based Tendering Scenario
Step Description Security Measure
1 HTML e-mail is created via BCS and
sent to SMTP server
In Customizing for TM, the use of en
cryption and digital signatures needs to
be enabled. In Customizing for
Transportation Management, choose
Freight Order Management
Tendering Dene General Settings for
Tendering
03 – E-mail and SMS
Content E-Mail Security Settings .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 461
Step Description Security Measure
2 Proxy applies encryption and digital sig
nature to e-mail
External secure e-mail proxy needs to
be maintained and activated for the TM
system. For more information, see SAP
Note
149926 . Keys must be ex
changed between the sender and recip
ient prior to sending the e-mail. We
highly recommend that you set up the
policy for the e-mail proxy in such a way
that e-mails can be sent only if encryp
tion and digital signatures are enabled.
If this is not possible, for example, due
to missing keys, e-mails must not be
sent in an insecure way.
3 E-mail is decrypted and signature veri
ed for reading
The e-mail client of the recipient must
support encryption and digital signa
tures, and keys must have been ex
changed beforehand by the sender and
the recipient.
4 Reply is encrypted and signed and sent
back to TM system
Refer to step 3
5 Proxy veries signature and decrypts e-
mail content
Refer to step 2
6 Decrypted and veried e-mail is proc
essed
Not applicable
Recommendation
To access the TM system externally, we recommend that you dene a system alias in the web dispatcher.
The web dispatcher redirects the request to the correct hostname and port so that an external user can use
a hyperlink, which contains the alias, to access the system.
You create a tendering notication e-mail in the TM system. The system sends this e-mail to the carrier with
a hyperlink to the carrier's worklist in the TM system or in the TM collaboration portal. The hyperlink
contains the system alias instead of the physical hostname and port. To use the alias, ensure that you have
implemented SAP Note 1748036 or 1747651 , and SAP Note 1783590 . Subsequently, you need to
specify the following settings in the TM system:
1. Create an alias in transaction SM59.
2. In the Target Host eld, enter the system alias as specied in the web dispatcher.
3. Enter the alias in the 03 E-Mail and SMS Content screen in Customizing for Transportation Management
under Freight Order Management Tendering Dene General Settings for Tendering .
462
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
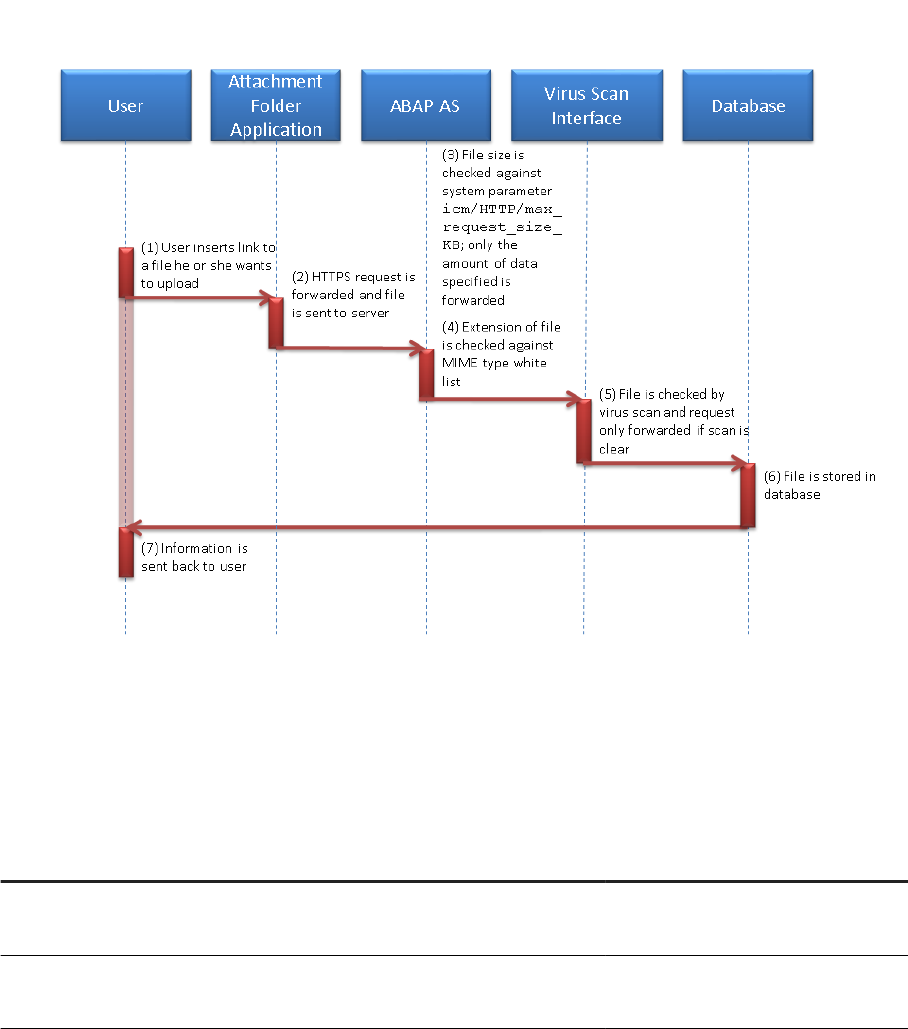
File Upload Scenario
The gure below shows an overview of the le upload scenario for TM.
File Upload Scenario
The table below shows the security aspects to be considered for the process step and what mechanism
applies.
Steps for File Upload Scenario
Step Description Security Measure
1 User inserts link to a le he or she
wants to upload
User needs to be aware of the le he or
she wants to upload
2 HTTPS request is forwarded and le is
sent to server
Not applicable
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 463

Step Description Security Measure
3 File size is checked against system pa
rameter icm/HTTP/
max_request_size_KB
; only the
amount of data specied is forwarded
Maximum le size needs to be re
stricted to secure the server; for more
information, see the Security Guide for
SAP NetWeaver 7.5. In the Security
Guide, choose
Security Guides for
SAP NetWeaver Functional Units
Security Guides for the Application
Server
Security Guides for the AS
ABAP Web Dynpro ABAP Security
Guide
Security Notes for FileUpload
UI Elements .
4 MIME type of le is checked against
white list
The extension of the uploaded le (but
not its content) is checked against
MIME type white list; as a prerequisite
for using the white list, SAP Note
1514253 must be implemented.
5 File is checked by virus scan and re
quest only forwarded if scan is clear
Virus scan needs to be active in your
system. For more information, see SAP
Library for SAP NetWeaver 7.5 at http://
help.sap.com/nw
. In SAP Library,
choose SAP NetWeaver SAP
NetWeaver Library: Function-Oriented
View
Security Security Developer
Documentation Secure Programming
Secure Programming – Java Secure
Programming SAP Virus Scan
Interface
. We strongly recommend
that you create a virus scan prole with
linkage type All steps successful.
6 File is stored in database Not applicable
7 Information is sent back to user Not applicable
Caution
Only le extensions are compared to the entries in the white list, not the content of the les.
The le upload function can be disabled to prevent users from uploading les to your system. To disable the
le upload function, you must implement SAP Note 1514253 . We recommend that you disable the
upload function if it is not required by your business scenarios.
464
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Always ensure that your virus scan is set up and working correctly before enabling le uploads. If your virus
scan is not up and running, do not use the le upload.
For information about uploading TACT rates to TM, see SAP Library for TM at http://help.sap.com/tm . In
SAP Library for TM, choose Master Data Charge Management and Service Product Catalogs Setup of
Service Product Catalogs and Charge Management MD
TACT Rates TACT Rate Upload .
13.10.4.2 Authorizations
Transportation Management (TM) uses the authorization concept provided by the SAP NetWeaver AS ABAP.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver
Application Server ABAP Security Guide, Java Security Guide, and ABAP and Java Security Guides also apply to
TM.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP and the User Management
Engine’s user administration console for the AS Java.
Role and Authorization Concept for Transportation Management
Authorization objects are delivered with TM. For more information about the authorization objects and how to
use them, see the following section.
Standard Authorization Objects
For TM, there are two kinds of authorization objects:
● Static checks of the technical business objects along with their nodes and actions, or of organizational data
objects
● Instance-based authorization objects, with which you can check authorization for the specied business
documents or other objects, depending on business-relevant data such as organization information
For instance-based authorization checks, there are two basic concepts. First, you can dene authorization
values based on identiers for all proles or other objects that cannot be classied any further by specic
types, but only depending on their identier. Second, you can dene authorization values based on category,
type, and further characteristics such as organizational data that can classify business documents beyond
their identier.
Besides the standard activities that can be dened for each authorization object for authorization eld ACTVT,
you can also dene whole groups of activities for several authorization actions as an activity area. This means
that you can dene a distinct activity area, thereby allowing or preventing a whole set of actions related to this
area. For example, you do not have to dene all actions relating to subcontracting activities separately for a
role, but only to dene the activity area for subcontracting.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 465
For information about authorizations in TM, see SAP Library for TM on SAP Help Portal at http://help.sap.com/
transportationmanagement94 . In SAP Library, choose Basic Functions Authorizations .
If you want to display the authorization objects in TM, on the SAP Easy Access screen, choose Tools ABAP
Workbench
Development Other Tools Authorization Objects Objects and open object class SCTS.
Note
You can also create your own authorization objects and implement the corresponding checks in BAdIs
Authorization Check and Data Retrieval Before Authorization Check.
For more information, see Customizing for Transportation Management under Business Add-Ins (BAdIs)
for Transportation Management Basic Functions Authorizations .
In TM, you have a special permission object T_ADMIN. System users who run batch jobs can use this
permission object. To use this permission object, you must have all application specic permissions. Note that
if you maintain this object in a certain role, all other TM permission objects will not be checked for this role
anymore.
The table below shows the security-relevant authorization objects from other components that are used by
TM. The list does not include basis authorization objects used for central functions or administration.
Standard Non-TM Authorization Objects
Authorization Object Field Value Description
SAP SCM Basis 7.0
/SCMB/PESL
ACTVT, USER (06) Delete
(34) Write
In the USER eld, you can en
ter the user for which you
want to execute the activities
in the
ACTVT eld.
Dene Planning Service Man
ager (PSM) Selection. The
authorization object enables
the specied user to save
and delete his or her selec
tions.
/SCTM/SCU /SCMB/SCU ACTVT
Use of supply chain units in
routes.
C_MD_SCU
/SCMB/SCU, ACTVT
Business Context Viewer
BCV_USAGE ACTVT
(70) Administer (US) Business Context Viewer us
age
BCV_PERS ACTVT
BCV_CTXKEY
BCV_QRYVID
Personalize BCV User Inter
face for Query View
Business Rules Framework
466 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
FDT_OBJECT FDT_ACT
FDT_APPL
FDT_OBJTYP
You use this authorization
object to control usage of ob
jects of the specied type in
BRFplus.
FDT_WORKB FDT_WB_ACT
This authorization object
controls whether a user is
authorized to use the
BRFplus workbench and its
tools.
APO
C_APO_DEF
ACTVT, APO_PLNR,
APO_DEFT, APO_DEFN
(01) Create or generate
(02) Change
(03) Display
(06) Delete
APO Authorization Object:
Master Data, Resource De-
nitions
C_APO_LOC
ACTVT, APO_LOC (01) Create or generate
(02) Change
(03) Display
(06) Delete
(16) Execute
(32) Save
APO Authorization Object:
Master Data, Locations
C_APO_PROD
ACTVT, APO_LOC, APO_PROD (01) Create or generate
(02) Change
(03) Display
(06) Delete
(16) Execute
APO Authorization Object:
Master Data, Products
C_APO_RES
ACTVT, APO_PLNR, APO_LOC,
APO_RES
(01) Create or generate
(02) Change
(03) Display
(06) Delete
(16) Execute
APO Authorization Object:
Master Data, Resources
EH&S
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 467
Authorization Object Field Value Description
C_EHSP_TPP
ACTVT, LANGUAGE,
ESECATPIN, ESEPHRGRP,
PPSTAT
(02) Change
(03) Display
This authorization is checked
in the transactions for phrase
management for entry into
the hit list.
C_SHEP_TPG
ACTVT, ESECATPIN,
ESEPHRGRP
(01) Create or generate
(02) Change
(03) Display
(59) Distribute
This authorization object is
checked in the phrase man
agement transactions when
entering and leaving the hit
list. The activities “change”
and “display” are also
checked here.
M_MATE_DGM ACTVT
(01) Create or generate
(02) Change
(03) Display
(06) Delete
(61) Export
(82) Supplement
Using the authorization ob
ject M_MATE_DGM, you can
prevent dangerous goods
master data from being dis
played or edited.
Formula & Derivation Tool
FDT_OBJECT
FDT_APPL, FDT_OBJTYP,
FDT_ACT
(1) Create
(2) Change
(3) Display
(4) Delete
(5) Activate
You use this authorization
object to control the authori
zation to display, create,
change, or delete objects in
the Formula & Derivation
Tool (including functions, ex
pressions, expression types,
lters, and applications).
Human Resources
PLOG
PLVAR, OTYPE, INFOTYP,
SUBTYP, ISTAT, PPFCODE
Not applicable The present object is used by
the authorization check for
PD data.
SAP SCM Optimizer
S_RFC
ACTVT, RFC_NAME,
RFC_TYPE
(16) Execute Required authorization to
start the SAP SCM Optimizer
and use most of the adminis
trator transactions.
SAP Event Management
468 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
X_EM_EH
ACTVT, /SAPTRX/PN, /
SAPTRX/PV
(03) Display
(10) Post
Event handler authorization
X_EM_EH_CH
ACTVT, /SAPTRX/SO (01) Create or generate
(02) Change
(05) Lock
(06) Delete
(63) Activate
(95) Unlock
Event handler changes
X_EM_EVM
ACTVT, /SAPTRX/CS, /
SAPTRX/CD
(32) Save the sender code
set and sender code ID
Event messages
Cross-Application Authorization Objects
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 469

Authorization Object Field Value Description
CA_POWL
POWL_APPID, POWL_QUERY,
POWL_CAT, POWL_LSEL,
POWL_TABLE, POWL_RA_AL
POWL_QUERY:
(01) Users are allowed to cre
ate, change, and delete their
own queries for all POWL ob
ject types assigned to them
(compare with Customizing
tables POWL_TYPE_USR and
POWL_TYPE_ROL).
(02) Users are only allowed
to create their own queries
on the basis of admin queries
assigned to them in Custom
izing tables
POWL_QUERY_USR and
POWL_QUERY_ROL respec
tively. (Note: this is also sub
ject to the user – POWL ob
ject type assignments.)
(03) (and other values):
Users are only allowed to
change admin queries as
signed to them with respect
to the select options restric
tions of those admin queries
(thus creating a separate
“derivation” for each admin
query transparently)
POWL_CAT:
(01) Users are allowed to cre
ate, change, and delete their
own categories and assign
queries to them.
(02) Users are only allowed
to assign queries to the exist
ing categories and change
the order of queries.
(03) (and other values):
Users are not allowed to re
assign queries or change the
query order. Note: if eld
POWL_QUERY is set to 01 or
03, setting POWL_CAT to 03
Species the authorities for
Personal Object Worklist
(POWL) iViews
470 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
is not advisable. Therefore,
the value is implicitly set to
02 in this case.
S_SERVICE
SRV_NAME, SRV_TYPE This authorization object is
automatically checked when
external services are started.
This is required for Gateway
Services used by the TM Col
laboration Portal
S_RFCACL
RFC_SYSID,
RFC_CLIENT,RFC_USER,
RFC_EQUSER, RFC_TCODE,
RFC_INFO,ACTVT
(16) Execute Authorization check for RFC
users, especially for trusted
systems. This is required for
Gateway Services used by
the TM Collaboration Portal.
S_WFAR_OBJ ACTVT
OAARCHIV
OADOKUMENT
OAOBJEKTE
(01) Create or generate This authorization object is
used to control access to ar
chived documents.
S_ARCHIVE ACTVT
APPLIC
ARCH_OBJ
This authorization object is
used in SAP archiving pro
grams to protect the access
to archive les
B_BUPA_RLT ACTVT
RLTYP
With this authorization ob
ject you dene which BP
roles can be edited.
B_BUPR_BZT ACTVT
RELTYP
With this authorization ob
ject you establish which rela
tionship categories can be
processed.
S_DATASET ACTVT
FILENAME
PROGRAM
You use this object to assign
authorizations for accessing
operating system les.
S_WF_WI TASK_CLASS
WFACTVT
WI_TYPE
Authorization object for
working with work items in
SAP Business Workow
S_SCD0 ACTVT
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 471

Recommendation
To segregate duties using roles and authorization values in TM, we recommend that you restrict the
authorizations of the dierent roles to the business-related minimum.
With the authorization concept provided by TM, you can restrict authorization based on business
document categories, such as Freight Order or Freight Booking, or on business document types, which you
can create for the supplied business document categories. Furthermore, all critical business-related
activities can be restricted for the dierent roles. These activities include creating business documents,
displaying business documents or master data, triggering charge calculations, subcontracting freight
documents, requesting customs declarations, and others activities or activity areas for the authorization
objects of object class SCTS. Duties can, therefore, be segregated according to your business and
scenarios.
Note that we do not recommend providing one role with full authorization for a business document or
process, so that one role cannot be used, for example, to create and maintain a business document, add
charge data to it, send it to a business partner, and create the invoice for that document. Such activities
should be spread over dierent roles.
In addition, one user must not be assigned to dierent roles that would provide full authorization for a
business document or process as described above.
Note
If your scenario contains an approval workow process, you need to create or maintain user WF-BATCH
accordingly.
For general information about creating and maintaining the WF-BATCH user, see SAP Note 1251255 .
13.10.4.3 Deletion of Personal Data
Use
Transportation Management (TM) might process data (personal data) that is subject to the data protection
laws applicable in specic countries as described in SAP Note 1825544 .
For more information see also the specic notes for TM:
● 2149395 – Deletion and Blocking of cBP in TM
● 2149396 – Simplied Data Deletion based on SAP ILM in TM
The SAP Information Lifecycle Management (ILM) component supports the entire software lifecycle including
the storage, retention, blocking, and deletion of data. TM uses SAP ILM to support the deletion of personal data
as described in the following sections.
SAP delivers an end of purpose check for business partners and locations in TM using a two-step approach:
1. The system lls a new data base table with the Start of Retention Time (SoRT) information per business
partner or location business object and application rule variant as soon as a ’completed’ document is
saved.
472
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

2. The system uses the EoP check to decide whether a business partner or location can be blocked. During
the EoP check, the system determines the SoRT information relevant for that business partner or location
from the database table containing the SoRT information. The SoRT information is required to determine
the relevant ILM policies and to calculate the correct end-of-purpose time depending on the dened ILM
policies.
For more information, see http://help.sap.com/s4hana under Product Assistance Enterprise Business
Applications Supply Chain Transportation Management (TM) Basic Functions Data Management in
Transportation Management
Blocking and Deletion of Personal Data in TM End-of-Purpose Framework .
SAP delivers a where-used check (WUC) for business partners and locations in TM including master data
objects such as transportation charge rates, transportation charge scales, locations, and resources.
TM registers an EoP check in the Customizing settings for the blocking and deletion of business partners and
locations and in addition provides a WUC for business partners and locations. For information about the
Customizing of blocking and deletion for TM, see below, Conguration: Simplied Blocking and Deletion.
Features
End of Purpose (EoP) Check
An end of purpose check determines whether data is still relevant for business activities based on the retention
period dened for the data. The retention period of data consists of the following phases.
● Phase one: The relevant data is actively used.
● Phase two: The relevant data is actively available in the system.
● Phase three: The relevant data needs to be retained for other reasons.
For example, processing of data is no longer required for the primary business purpose, but to comply with
legal rules for retention, the data must still be available. In phase three, the relevant data is blocked.
Blocking of data prevents the business users of SAP applications from displaying and using data that may
include personal data and is no longer relevant for business activities.
Blocking of data can impact system behavior in the following ways:
● Display: The system does not display personal data of a blocked business partner or location.
● Change: It is not possible to change a completed business document that contains a blocked business
partner or location.
● Create: It is not possible to create a business document using a blocked business partner or location. As
soon as a blocked business partner or location is entered, the system raises a suitable error message.
● Copy/Follow-Up: It is not possible to copy a business object or perform follow-up activities for a business
object that contains blocked data.
● Search: The system does not display blocked data in the result list of search helps. The same is true for
technical queries based on the business object for business partner /SCMTMS/BUPA and the business
object for locations (/SCMTMS/LOCATION).
It is possible to display blocked data if a user has special authorization (SAP_CA_BP_DP_ADMIN). However, it is
still not possible to create, change, copy, or perform follow-up activities on blocked data.
Relevant Application Objects and Available EoP functionality
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 473

Application Implemented solution (EoP or WUC) Further information
TM End of Purpose Check (EoP)
EoP Function Module:
/SCMTMS/DPP_EOP_CHECK
The End of Purpose check (EoP) for
business partners includes the follow
ing business objects:
● /SCMTMS/BUS_SHARE
● /SCMTMS/CUSTFREIGHTINVREQ
● /SCMTMS/FREIGHTAGREEEMENT
● /SCMTMS/SUPPFREIGHTINVREQ
● /SCMTMS/TOR
● /SCMTMS/TRQ
● /SCMTMS/TAL
● /SCMTMS/WAYBILLNO
The End of Purpose check (EoP) for lo
cations includes the following business
objects
● /SCMTMS/CUSTFREIGHTINVREQ
● /SCMTMS/SUPPFREIGHTINVREQ
● /SCMTMS/TOR
● /SCMTMS/TRQ
TM Where-Used-Check (WUC) In addition to the business objects han
dled in the EoP Check, the Where-Used
Check (WUC) for business partners in
cludes also master data objects such
as:
● Transportation Charge Calculation
Sheets
● Transportation Charge Rates
● Transportation Charge Scales
● Locations
● Resources
Process Flow
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
○ Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA) or location . (ILM object SCMB_LOC).
○ Run transaction IRMPOL and maintain the required retention policies for the ILM objects of TM.
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available.
3. To determine which business partners or locations have reached end of purpose and can be blocked, you
do the following, if you have the necessary authorization:
○ Run transaction BUPA_PRE_EOP to execute the end of purpose check function for the central business
partner.
474
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

○ Run transaction /SCMB/LOC_PRE_EOP to execute the end of purpose check function for the location.
4. To unblock blocked business partner or location data, you do the following, if you have the necessary
authorization:
○ Request unblocking of blocked business partner data by using the transaction BUP_REQ_UNBLK.
○ You can unblock the requested data by running the transaction BUPA_PRE_EOP.
○ For unblocking location data you can run the transaction /SCMB/LOC_UNBLOCK_MD.
5. You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of TM.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of data in Customizing for Cross-Application
Components under Data Protection.
● Dene the settings for authorization management under Data Protection Authorization
Management
. For more information, see the Customizing documentation.
● Dene the settings for blocking in Customizing for.
○ Business Partner
Cross-Application Components under Data Protection Blocking and Unblocking Business
Partner
○ Location
Transportation Management Master Data Transportation Network Location Location Master
Deletion
● Dene the Customizing settings for TM. For more information, see http://help.sap.com/s4hana under
Product Assistance Enterprise Business Applications Supply Chain Transportation Management
(TM) Basic Functions Data Management in Transportation Management Blocking and Deletion of
Personal Data in TM
Customizing Settings for Data Protection and Privacy .
13.10.4.4 Security-Relevant Logging and Tracing
SAP systems have a variety of logs for system administration, monitoring, problem solving, and auditing
purposes. Audits and logs are important for monitoring the security of your system and to track events, in case
of problems.
Note
Auditing and logging for Netweaver component is described in detail in the NetWeaver Security Guide. For
more information, see
http://help.sap.com/nw75 . Choose Security Guide Security Aspects for
Lifecycle Management Auditing and Logging .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 475

Security Audit Log Triggered by Virus Scan Interface (VSI)
Class CL_VSI automatically creates entries in the Security Audit Log for infections and scan errors found,
together with the following information:
● Prole
● Prole step allowing the detection of the scanner-group
● Kind of virus found, with internal virus ID of the scan engine, if available
● User name and timestamp
The messages logged are located in message class VSCAN using system log messages BU8 and BU9 (created in
transaction SE92). The severities are set to High and Medium respectively. The severity of the audit class is set
to Miscellaneous.
For more information, see Customizing for SAP Supply Chain Management under SAP Web Application
Server System Administration Virus Scan Interface .
Audit Information System (AIS)
Information about auditing and logging for the Audit Information System (AIS) is described in detail in the SAP
NetWeaver 7.5 Security Guide.
For more information, see The Audit Info System (AIS) at http://help.sap.com/nw75 . Choose Security
Guide Security Aspects for Lifecycle Management Auditing and Logging The Audit Info System (AIS)
For more information about security logs for the SAP Gateway, see Logging in SAP Gateway section of the SAP
Gateway Developer Guide for SAP Gateway SP06.
Transportation Management (TM)
Tracing and Logging of Business Objects
In TM, you can log messages raised by business objects in the application log.
In the standard system, logging is deactivated. To activate logging, in Customizing for Transportation
Management, choose Basic Functions User Interface Dene Message Settings (note that this has
negative impact on overall system performance; this is why SAP recommends to switch on logging only when
required).
To access the application log, on the SAP Easy Access or in SAP NetWeaver Business Client screen, choose
Application Administration Application Log: Display Logs . Alternatively, call transaction SLG1.
For more information, see Application Logging under Logging of Specic Activities in the SAP NetWeaver 7.5
Security Guide on SAP Help at http://help.sap.com/nw .
Activating Change Documents
In TM, you can activate change documents to log changes to master data, business objects, and so on.
476
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
You must activate change documents in Customizing before the system can store them. For information about
the objects for which you can activate change documents and where to activate them, see the corresponding
section in the TM documentation:
Object Customizing Path
Location
Transportation Management Master Data
Transportation Network Location Activate Change
Documents
Transportation lane
Transportation Management Master Data
Transportation Network Transportation Lane Activate
Change Documents
Product
SCM Basis Master Data Product Activate Change
Documents
Freight unit
Transportation Management Planning Freight Unit
Dene Freight Unit Types (Track Changes checkbox)
Freight order
Transportation Management Freight Order Management
Freight Order Dene Freight Order Types (Track
Changes checkbox)
Freight booking
Transportation Management Freight Order Management
Freight Booking Dene Freight Booking Types (Track
Changes checkbox)
Freight agreement
Transportation Management Master Data
Agreements and Service Products Dene Freight
Agreement Types
(Track Changes checkbox).
Forwarding agreement
Transportation Management Master Data
Agreements and Service Products Dene FWA and Service
Product Catalog Types
(Track Changes checkbox).
Forwarding order
Transportation Management Forwarding Order
Management Forwarding Order Dene Forwarding Order
Types
(Track Changes checkbox).
Forwarding quotation
Transportation Management Forwarding Order
Management Forwarding Quotation Dene Forwarding
Quotation Types
(Track Changes checkbox).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 477

Object Customizing Path
Forwarding settlement
Transportation Management Settlement Forwarding
Settlement Dene Forwarding Settlement Document
Types
(Track Changes checkbox).
Freight settlement
Transportation Management Settlement Freight
Settlement Dene Freight Settlement Document Types
(Track Changes checkbox).
Order-based transportation requirement
Transportation Management Integration ERP
Logistics Integration Order-Based Transportation
Requirement
Dene Order-Based Transportation
Requirement Types (Track Changes checkbox).
Delivery-based transportation requirement
Transportation Management Integration ERP
Logistics Integration Delivery-Based Transportation
Requirement
Dene Delivery-Based Transportation
Requirement Types
Service order
Transportation Management Freight Order Management
Service Order Dene Service Order Types (Track
Changes checkbox).
SAP SCM Optimizer
For information about the trace and log les for the SAP SCM Optimizer, see the SAP SCM 7.0 Component
Security Guide.
For more information about the logging and tracing mechanisms from SAP NetWeaver, go to http://
help.sap.com/nw75 . Choose Security Guide Security Aspects for Lifecycle Management Auditing and
Logging
.
13.11 Cross-Line-of-Business
478
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.11.1 Commodity Management
13.11.1.1 Commodity Procurement
13.11.1.1.1 Deletion of Personal Data
Use
Commodity Procurement and Commodity Sales might process data (personal data) that is subject to the data
protection laws applicable in specic countries as described in SAP Note 1825544 .
For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal under Product
Assistance Cross Components Data Protection .
Please note that Commodity Procurement and Commodity Sales do not use SAP Information Lifecycle
Management (ILM).
Relevant Application Objects and Available Deletion Functionality
Application Objects Provided Deletion Functionality
BRFplus Decision Table Entries for CPE Formula Assembly See Section BRFplus Decision Table Entries for CPE Formula
Assembly below
Pricing Condition Records in CPE Formula Assembly See section Pricing Conditon Records for CPE Formula As
sembly below
Records of Versioned Logistics Pricing Data Persistency See section Versioned Logistics Pricing Data Persistency be
low
BRFplus Decision Table Entries for CPE Formula Assembly
In the Commodity Pricing Engine (CPE), the Formula Assembly (FA) is used for logistics document items like
sales order items or purchase order items to create default settings as, for example, the formula ID. These
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 479

settings depend on properties of the underlying logistics document such as the vendor/customer,
organizational and material data.
The Business Rules Framework plus (BRFplus) is used to implement rules for entering these settings. To use
decision tables in BRFplus (as recommended by SAP), the required BRFplus content is provided (BRFplus
application, BRFplus functions which use BRFplus decision tables). The standard content includes, for
example, decision tables, which require customer or vendor, material and other input elds, and the formula ID
as result eld. Decision tables can contain customer or vendor data, which eventually need to be deleted.
In the deletion report RCPE_BRF01 (Delete BRFplus Decision Table Entries for CPE Formula Assembly) you
enter a selected customer or vendor. When selecting the test mode, the report checks, whether the entered
customer or vendor exists in the system, and whether he is blocked. After this, the report checks all BRFplus
decision tables in BRFplus applications used for the Formula Assembly, and displays the respective row
numbers of the BRFplus decision tables and the column containing the selected customer or vendor. If the Test
Mode ag is not set, the report deletes all entries found, and creates an application log entry for object CMM and
subobject
DPP_FA_BRF (transaction SLG1).
The Customizing settings can be found in the SAP Implementation Guide under Sales and Distribution
Basic Functions Commodity Pricing Settings for Formula Assembly Assign BRFplus Application to Pricing
Procedure
or Materials Management Purchasing Commodity Pricing Settings for Formula Assembly
Assign BRFplus Application to Pricing Procedure .
Pricing Condition Records in CPE Formula Assembly
To check the tables used for the formula assembly, whether there is a certain customer or vendor used,
perform transaction MCPE_FA_GCM (for Commodity Procurement) or VCPE_FA_GCM (for Commodity Sales) .
To delete entries for a single customer or vendor, use report RCPE_CT01. First, choose the test mode, to see all
entries of the selected table, which would be deleted.
If you perform this transaction in productive mode, the selected entries will be deleted, and a log of transaction
SLG1 for object CMM and subobject DDP_FA_AP is displayed.
Note: Condition tables used for the CPE Formula Assembly must be selected and processed individually.
Versioned Logistics Pricing Data Persistency
Transaction CMM_DEL_DOC_VERSIONS allows you to delete all records of the versioned logistic pricing data
persistency (table CMM_VLOGP), which are stored for a certain blocked customer/vendor.
Transaction CMM_DEL_DOC_VERSIONS allows you to update all records of the versioned logistic pricing data
persistency (table CMM_VLOGP), which are stored for a certain blocked customer/vendor in a way that the
identier of the respective customer/vendor is masked with a blank space.
The authorization to perform this transaction is checked by the authorization object S_TCODE, and explicitly in
the underlying report. It is ensured that, even if the report is performed by transaction SA38, only authorized
experts can execute it. In addition, the authorization object
CMM_VLOGP is checked by activity 06 (Delete). This
480
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

enables the authorized user to delete records from the versioned logistic pricing data persistency (table
CMM_VLOGP).
Note: It is checked, whether the entered customer is used as Sold-to-Party and/or Ship-to-Party. Records are
deleted and masked accordingly.
This transaction must be performed to mask or to delete records as soon as a certain customer or vendor is
blocked.
Relevant Application Objects and Available EoP/WUC Functionality
Application Implemented Solution (EoP or WUC) Further Information
n/a n/a
n/a
13.11.1.1.2 Information Report
Use
Commodity Procurement and Commodity Sales provide information about stored personal data in the
versioned persistency of logistics pricing data (VLOGP).
Versioned Persistency of Logistics Pricing Data
To display information about stored personal data in in the versioned persistency of logistics pricing data
(VLOGP) of Commodity Procurement and Commodity Sales, run transaction CMM_DEL_DOC_VERSIONS.
The authorization to perform this transaction is checked by the authorization object S_TCODE, and in the
underlying report. It is ensured that, even if the report is launched by transaction SA38, only authorized experts
can execute it.
In case of blocked customers, vendors, business partners, the authorization object B_BUP_PCPT (actvitity 03)
is additionaly checked.
Table / Business Object Archiving Object Personal Data
CMM_VLOGP n/a LIFNR, KUNNR, KUNWE
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 481

13.11.1.2 Commodity Sales
13.11.1.2.1 Deletion of Personal Data
Use
Commodity Procurement and Commodity Sales might process data (personal data) that is subject to the data
protection laws applicable in specic countries as described in SAP Note 1825544 .
For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal under Product
Assistance
Cross Components Data Protection .
Please note that Commodity Procurement and Commodity Sales do not use SAP Information Lifecycle
Management (ILM).
Relevant Application Objects and Available Deletion Functionality
Application Objects Provided Deletion Functionality
BRFplus Decision Table Entries for CPE Formula Assembly See Section BRFplus Decision Table Entries for CPE Formula
Assembly below
Pricing Condition Records in CPE Formula Assembly See section Pricing Conditon Records for CPE Formula As
sembly below
Records of Versioned Logistics Pricing Data Persistency See section Versioned Logistics Pricing Data Persistency be
low
BRFplus Decision Table Entries for CPE Formula Assembly
In the Commodity Pricing Engine (CPE), the Formula Assembly (FA) is used for logistics document items like
sales order items or purchase order items to create default settings as, for example, the formula ID. These
settings depend on properties of the underlying logistics document such as the vendor/customer,
organizational and material data.
The Business Rules Framework plus (BRFplus) is used to implement rules for entering these settings. To use
decision tables in BRFplus (as recommended by SAP), the required BRFplus content is provided (BRFplus
application, BRFplus functions which use BRFplus decision tables). The standard content includes, for
482
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

example, decision tables, which require customer or vendor, material and other input elds, and the formula ID
as result eld. Decision tables can contain customer or vendor data, which eventually need to be deleted.
In the deletion report RCPE_BRF01 (Delete BRFplus Decision Table Entries for CPE Formula Assembly) you
enter a selected customer or vendor. When selecting the test mode, the report checks, whether the entered
customer or vendor exists in the system, and whether he is blocked. After this, the report checks all BRFplus
decision tables in BRFplus applications used for the Formula Assembly, and displays the respective row
numbers of the BRFplus decision tables and the column containing the selected customer or vendor. If the Test
Mode ag is not set, the report deletes all entries found, and creates an application log entry for object CMM and
subobject
DPP_FA_BRF (transaction SLG1).
The Customizing settings can be found in the SAP Implementation Guide under Sales and Distribution
Basic Functions Commodity Pricing Settings for Formula Assembly Assign BRFplus Application to Pricing
Procedure
or Materials Management Purchasing Commodity Pricing Settings for Formula Assembly
Assign BRFplus Application to Pricing Procedure .
Pricing Condition Records in CPE Formula Assembly
To check the tables used for the formula assembly, whether there is a certain customer or vendor used,
perform transaction MCPE_FA_GCM (for Commodity Procurement) or VCPE_FA_GCM (for Commodity Sales) .
To delete entries for a single customer or vendor, use report RCPE_CT01. First, choose the test mode, to see all
entries of the selected table, which would be deleted.
If you perform this transaction in productive mode, the selected entries will be deleted, and a log of transaction
SLG1 for object CMM and subobject DDP_FA_AP is displayed.
Note: Condition tables used for the CPE Formula Assembly must be selected and processed individually.
Versioned Logistics Pricing Data Persistency
Transaction CMM_DEL_DOC_VERSIONS allows you to delete all records of the versioned logistic pricing data
persistency (table CMM_VLOGP), which are stored for a certain blocked customer/vendor.
Transaction CMM_DEL_DOC_VERSIONS allows you to update all records of the versioned logistic pricing data
persistency (table CMM_VLOGP), which are stored for a certain blocked customer/vendor in a way that the
identier of the respective customer/vendor is masked with a blank space.
The authorization to perform this transaction is checked by the authorization object S_TCODE, and explicitly in
the underlying report. It is ensured that, even if the report is performed by transaction SA38, only authorized
experts can execute it. In addition, the authorization object CMM_VLOGP is checked by activity 06 (Delete). This
enables the authorized user to delete records from the versioned logistic pricing data persistency (table
CMM_VLOGP).
Note: It is checked, whether the entered customer is used as Sold-to-Party and/or Ship-to-Party. Records are
deleted and masked accordingly.
This transaction must be performed to mask or to delete records as soon as a certain customer or vendor is
blocked.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 483

Relevant Application Objects and Available EoP/WUC Functionality
Application Implemented Solution (EoP or WUC) Further Information
n/a n/a
n/a
13.11.1.2.2 Information Report
Use
Commodity Procurement and Commodity Sales provide information about stored personal data in the
versioned persistency of logistics pricing data (VLOGP).
Versioned Persistency of Logistics Pricing Data
To display information about stored personal data in in the versioned persistency of logistics pricing data
(VLOGP) of Commodity Procurement and Commodity Sales, run transaction CMM_DEL_DOC_VERSIONS.
The authorization to perform this transaction is checked by the authorization object S_TCODE, and in the
underlying report. It is ensured that, even if the report is launched by transaction SA38, only authorized experts
can execute it.
In case of blocked customers, vendors, business partners, the authorization object B_BUP_PCPT (actvitity 03)
is additionaly checked.
Table / Business Object Archiving Object Personal Data
CMM_VLOGP n/a LIFNR, KUNNR, KUNWE
13.12 Analytics Technology
484
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.12.1 Process Performance Monitoring
13.12.1.1 Process Observer
13.12.1.1.1 Roles for Process Observer
Process Observer uses the authorization concept provided by the SAP NetWeaver for Application Server ABAP.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS
Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the SAP NetWeaver Security Guide under User
Administration and Authentication.
Standard Roles
SAP delivers the following standard roles for Process Observer. You can use these roles as a template for your
own roles.
Role Description
Administration (SAP_POC_ADMINISTRATION) This single role contains all the functions that you need to
set up process monitoring:
● Maintain Customizing
● Implement tracing in the application
● Schedule jobs
● Delete log entries and execute mass deletion of log en
tries
● Update the master registry
● Carry out conguration activities
Dene Process (SAP_POC_MODEL) This single role contains all the functions that you need to
create a process denition:
● Dene a process
● Dene BRFplus rules
● Create a process simulation
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 485
Role Description
View Process (SAP_POC_MONITOR) This single role contains all the functions that you need to
view process details in the Process Monitor SAP GUI screen:
● Display process details
Analytics (SAP_POC_ANALYTICS) This single role contains all the functions that you need to
access the process-monitoring-relevant analytics content in
the SAP Business Information Warehouse:
● Display analytics information
Launchpad for Order to Cash Dashboard
(SAP_BW_POC_O2C_ANALYTICS)
This single role contains all the functions required to launch
the Dashboard for O2C Scenario.
Side Panel for Process Observer Data
(SAP_POC_SIDEPANEL)
This single role enables the user to see Process Observer
data for standard transactions such as display sales order,
display enquiry etc in a sidepanel using SAP Business Client.
Administration (SAP_POC_ADMIN) This composite role contains all the functions that you need
to set up process monitoring.
Business Process Expert (SAP_POC_BPX) This composite role contains all the functions that you need,
as a business process expert, to set up process denitions:
● Dene a process
● Dene BRFplus rules
● Create a process simulation
● Display process details
Standard Authorization Object
The basis for all roles used for data security for Process Observer is the authorization object POC_AUTH.
13.12.1.1.2 Data Protection and Privacy in Process Observer
Caution
If you congure Process Observer in a way that it stores personal data, you are responsible for ensuring
that you are compliant with the data protection laws applicable in the relevant countries.
For more information about conguring Process Observer, see the product assistance for SAP S/4HANA on the
SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components
Process Observer (CA-EPT-POC) Process Monitoring and Analytics Process Monitoring Setup .
486
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.12.1.1.3 Deletion of Personal Data in Process Observer
Depending on your conguration, Process Observer might process data (personal data) that is subject to the
data protection laws applicable in specic countries. You can use the following transactions to delete process
log data:
● POC_DELETE_LOG
● POC_MASS_DELETE
For more information about the deletion and mass deletion of process log data, see the product assistance for
SAP S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components
Process Observer (CA-EPT-POC) Operations Reports Reports Used in Operations for
Process Monitoring .
13.13 Enterprise Technology
13.13.1 Central Master Data
13.13.1.1 Deletion of Personal Data
The business partner, customer and supplier master data might process data (personal data) that is subject to
the data protection laws applicable in specic countries.
The SAP Information Lifecycle Management (ILM) component supports the entire software lifecycle including
the storage, retention, blocking, and deletion of data. The business partner, customer and supplier master data
uses SAP ILM to support the blocking and deletion of personal data as described in the following sections.
Personal data collected in business partner, customer and supplier master data can be blocked as soon as
business activities for which this data is needed are completed and the residence time for this data has
elapsed. After this time, only users who are assigned additional authorizations can access this data. After the
retention period for data expires, personal data can be destroyed completely such that it can no longer be
retrieved. Residence and retention periods are dened in the customer system. For information about the
Customizing of blocking and deletion, see Conguration: Simplied Blocking and Deletion.
End of Purpose Check (EoP)
An end of purpose (EoP) check determines whether data is still relevant for business activities based on the
retention period dened for the data. The retention period is part of the overall lifecycle of personal data which
consists of the following phases:
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 487
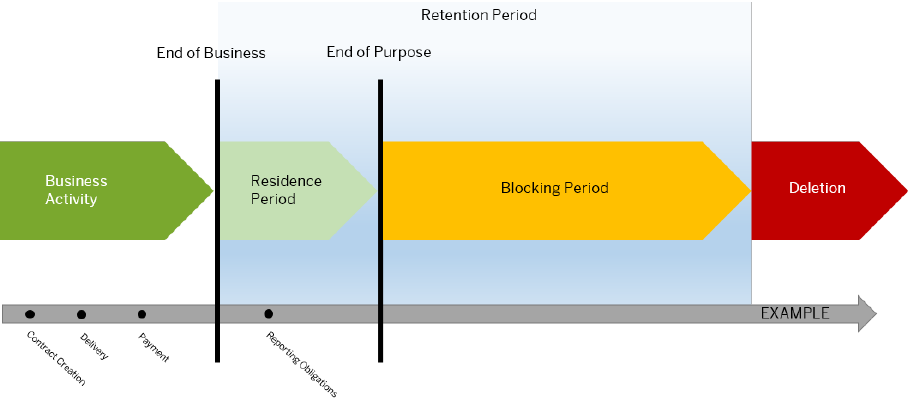
● Business activity: The relevant data is used in ongoing business, for example contract creation, delivery or
payment.
● Residence period: The relevant data remains in the database and can be used in case of subsequent
processes related to the original purpose, for example reporting obligations.
● Blocking period:The relevant data needs to be retained for legal reasons. During the blocking period,
business users of SAP applications are prevented from displaying and using this data; it can only be
processed in case of mandatory legal provisions.
● Deletion: The data is deleted and no longer exists in the database.
Personal Data Lifecycle
Blocking of data can impact system behavior in the following ways:
● Display: The system does not display blocked data.
● Change: It is not possible to change a business object that contains blocked data.
● Create: It is not possible to create a business object that contains blocked data.
● Copy/Follow-Up: It is not possible to copy a business object or perform follow-up activities for a business
object that contains blocked data.
● Search: It is not possible to search for blocked data or to search for a business object using blocked data in
the search criteria.
It is possible to display blocked data if a user has special authorization; however, it is still not possible to create,
change, copy, or perform follow-up activities on blocked data.
For information about the conguration settings required to enable the end of purpose check, see sections
Process Flow and Conguration: Simplied Blocking and Deletion.
488
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available Deletion Functionality
Application Object Provided Deletion Functionality
Business Partner Data Archiving object: CA_BUPA
ILM object: CA_BUPA
Prerequisites:
● Business function BUPA_ILM_BF is activated
● To use ILM enablement, the EoP check is mandatory be
fore archiving or deletion (transaction BUPA_PRE_EOP).
Customer Master Data Archiving object: FI_ACCRECV
ILM object: FI_ACCRECV
Prerequisites:
● Business function ERP_CVP_ILM_1 is activated.
● To use ILM enablement, the EoP check is mandatory be
fore archiving or deletion (transaction CVP_PRE_EOP).
Supplier Master Data Archiving object: FI_ACCPAYB
ILM object: FI_ACCPAYB
Prerequisites:
● Business function ERP_CVP_ILM_1 is activated.
● To use ILM enablement, the EoP check is mandatory be
fore archiving or deletion (transaction CVP_PRE_EOP).
Contact Person related to business partner, customer and
supplier master data
Destruction object: FI_ACCKNVK
ILM object: FI_ACCKNVK
Prerequisites:
● Business function ERP_CVP_ILM_1 is activated.
● To use ILM enablement, the EoP check is mandatory be
fore archiving or deletion (transaction CVP_PRE_EOP).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 489

Relevant Application Objects and Available EoP functionality
Application Implemented Solution Further Information
Business Partner (BUP) End of purpose (EoP) check EoP is determined based on the last
change date of the business partner
master data (from database table
BUT000).
Business Partner Relationship (BUB) End of purpose (EoP) check EoP is determined based on the Valid-To
eld of the relationship.
ERP Customer Master (ERP_CUST) End of purpose (EoP) check EoP is determined based on the last
change date of the customer master
data (from database table KNA1 or
change document object
DEBI), last
change date of assigned credit cards
(change document object VCNUM) or
last change date of assigned addresses
of the customer or contact persons.
ERP Supplier Master (ERP_VEND) End of purpose (EoP) check EoP is determined based on the last
change date of the supplier master data
(from database table LFA1 or change
document object
KRED) or the last
change date of assigned addresses of
the supplier or contact persons.
ERP Contact Persons (ERP_CON
TACT_PERSON)
End of purpose (EoP) check EoP is determined based on the last
change date of the contact person
(from the contact person related
change documents of the customer or
supplier) or the last change date of as
signed addresses of the contact person.
Process Flow
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
○ Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object:
CA_BUPA)
○ Run transaction IRMPOL and maintain the required residence and retention policies for the customer
master and supplier master (ILM objects: FI_ACCPAYB, FI_ACCRECV, FI_ACCKNVK).
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available.
490
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

3. To determine which business partners have reached end of purpose and can be blocked, you do the
following:
○ Run transaction BUPA_PRE_EOP to execute the end of purpose check for the central business partner
and the dependent customer master and supplier master.
○ Run transaction CVP_PRE_EOP to enable the end of purpose check function for the customer master
and supplier master.
4. To unblock a blocked business partner data, you do the following:
○ Request unblocking of the blocked data by using the transaction BUP_REQ_UNBLK.
○ If you have the needed authorization for unblocking business partner data, you can unblock the
requested data by running the transaction BUPA_PRE_EOP for the central business partner data and
CVP_UNBLOCK_MD for the customer master and supplier master.
5. You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of business partner data.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner, customer and supplier
master data in Customizing (transaction SPRO) using the following path:
SAP Customizing Implementation Guide Cross-Application Components Data Protection Blocking and
Unblocking of Data
For more information, go to http://help.sap.com/s4hana_op_1709 under Product Assistance Cross
Components
Data Protection .
13.13.2 Specic Read Access Log Congurations
Use
In Read Access Logging (RAL), you can congure which read-access information to log and under which
conditions.
SAP delivers sample congurations for applications.
The supplier master data display and maintain log data in order to track the disclosure of the supplier minority
indicator. You can nd the congurations as described in the Read Access Logging chapter.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 491
In the following congurations, elds are logged in combination with additional elds, in the following business
contexts:
Conguration Fields Logged Business Context
VEND_MINDK LFB1-MINDK
LFB1-LIFNR
LFB1-BUKRS
Log access to minority indicator only if
all elds are shown together.
13.13.3 Legal Content Management
13.13.3.1 Authorizations and Roles Used by Legal Content
Management
Legal Content Management uses the authorization concept provided by the SAP NetWeaver AS for ABAP.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS
Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Standard Roles
The table below shows the standard roles that are used.
Role Description
SAP_BR_ADMINISTRATOR_LCM
Administrator - Legal Content Management
SAP_BR_EMPLOYEE_LEGAL_CONTENT
Employee - Legal Content Management
SAP_BR_LEGAL_COUNSEL
Legal Counsel
492 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used.
Authorization Object Description
LCM_GEN
General Activities
LCM_CTXADM
Auth. Obj. for Task in LCM Context Admin. actions
LCMDOCSTMP
Auth. object for Stamps in LCM Document
LCMSTMPACT
Auth. object for Stamp activities in LCM Document
LCM_LTACT
Auth. Obj. for Task in LCM Legal Transaction Actions
13.13.3.2 Blocking of Personal Data
The Legal Content Management applications might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709 under Product Assistance
Cross Components Data Protection .
For Legal Content Management, data protection and privacy (DPP) is implemented for the following data:
● Entity types Customer and Supplier
● External contact type Business Partner
The DPP checks are enabled in DCL les which inherit the authorization of the respective standard DCL les. If
the user uses in a legal transaction the value help for a customer, supplier or business partner, the DCL
authorization check is executed and the blocked data is ltered out from the list that is shown in the value help.
If the user enters a customer, supplier or business partner directly, without using the value help, the Business
Object Processing Framework (BOPF) validation methods check the data against the CDS views and the
blocked data is not displayed.
The same logic is applied in the API. If an API call creates or updates data for a legal transaction, the BOPF
validation is is done based on the DPP authorization checks.
The following eld indicates if the legal transaction is blocked:
● IsBusinessPurposeCompleted - if set to X (true)
End of Purpose Check
The End of Purpose (EoP) check identies if all business applications have completed their purpose in use of
master data, so that it can be later blocked. Basically, the check is performed to see if a master data (customer,
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 493

supplier or business partner) can be blocked. In Legal Content Management (LCM), the EoP check is reached
when the legal transaction has reached one of the following status:
● Cancelled
● Terminated
● Expired
The central EoP check report calls the LCM modules to check if any business data is in use. And the LCM
module checks the data in legal transaction and returns the respective status back. Whether or not the
customer, supplier or business partner is blocked, is determined based on the following scenarios, which can
coexist in the same installation:
LCM determines the EoP: The business logic is hosted in LCM and as long as any of the data is still in use, it
cannot be removed or blocked.
Conguration
You congure the settings related to the blocking and deletion of customer, supplier, and business partner
master data in Customizing under
Cross Application Components Data Protection Blocking and
Unblocking of Data Business Partner . For more information, see the documentation of the respective
Customizing activities.
The application name for the EoP check is LCM-LT. You need to congure the blocking for the following objects:
Object
Type EoP Check Object
Legal Transaction External contact type / Business
partner
LCM_LEGALTR_BUPA_EOP_CHECK
Legal Transaction Entity type / Customer or supplier
CL_LCM_LEGALTR_CVP_EOP_CHE
CK
13.13.4 Geographical Enablement Framework
13.13.4.1 Authorizations
The framework uses the authorization concept provided by the SAP NetWeaver Application Server for ABAP
and SAP HANA Platform. Therefore, the recommendations and guidelines for authorizations as described in
the SAP NetWeaver Application Server, ABAP Security Guide and HANA platform also apply to SAP
Geographical Enablement Framework. The SAP authorization concept is based on assigning authorizations to
users based on roles. For role maintenance in application server ABAP (AS ABAP), use the prole generator
transaction PFCG in the backend system.
494
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Standard Roles
The table below provides the standard roles that are used by the framework.
Roles Description
sap.gef.data::gef_user
Delivered in SAP HANA DU for the SAP Geographical Enable
ment Framework; it provides basic authorization to access
the framework schema in SAP HANA (SAP_GEF). You can
assign this role to SAP_GEF_USER or other reference users
that are created.
sap.gef.data::gef_admin
In addition to all the authorizations provided in the
gef_user role, this admin role provides advanced authori
zations for administrative tasks.
For AS ABAP, the PFCG role template, SAP_GEF_USR is delivered. This template provides basic authorizations
for the framework. Other authorization roles, if needed for accessing application data, need to be added to
create
PFCG roles for consuming the framework services.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used.
Authorization Object Field Value
G_GEF_GEOM GEF_BO_ID
Business Object ID
GEF_CONTXT
Geometry Context ID
ACTVT
Activity
13.13.4.2 Internet Communication Framework Security (ICF)
You should only activate the services that are needed for the applications running in your system. For this area
the following services are needed:
● /default_host/sap/ca/GEF/arcgis/rest/services
In this path, the framework can provide services that conform to the specications of dierent GIS service
providers, if a custom GIS plug-in is developed and customized. For more information, see the Application
Implementation section in the Geographical Enablement Framework documentation.
● /default_host/sap/ca/GEF/rest/cong
In this path, the framework provides conguration information. This service is independent from any GIS
service providers.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 495
● /default_host/sap/bc/ui5_ui5/sap/gef_ui
The UI (Geometry Explorer and Geometry Editor) has been delivered to work with our framework. The UI
starts from this path.
Use transaction SICF to activate these services.
If your rewall(s) uses URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information about ICF security, see the respective chapter in the SAP NetWeaver Security Guide.
13.13.4.3 Data Protection and Privacy
The SAP Geographical Enablement Framework does not collect, store, or process users' personal data.
However, applications built on it may. Therefore, SAP recommends activating secure session management. We
also recommend that you use SSL to protect the network communications where these security-relevant
cookies are transferred.
Read access logging (RAL) monitors and logs read access to sensitive data, if any. It is required for applications
to comply with legal regulations or public standards such as data privacy. In most cases, applications rely on
the underlying business suite to save sensitive data. Therefore, it is also recommended to refer to the
documents of the underlying platforms and activate the RAL based on the needs.
13.13.4.4 Enterprise Services Security
A technical limitation (tracked in security message 1670119508) has been identied; not all the user controlled
inputs are suciently validated or encoded. This may cause security issues like Cross-Site Scripting (XSS).
This issue has been investigated and a solution is being implemented at this time. Contact SAP for the
availability of this solution.
13.13.5 Master Data Governance
13.13.5.1 Deletion of Personal Data in Master Data
Governance
Use
For personal data processed in the Master Data Governance (MDG) application, you can use SAP
Information Lifecycle Management (ILM) to control the blocking and deletion of personal data. For more
496
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

information, see the product assistance for SAP S/4HANA on the SAP Help Portal under Product Assistance
Cross Components Data Protection .
Relevant Application Object
Application Provided Deletion Functionality
MDG Change Requests Archiving object USMD_CR
For more information about the application object, see the product assistance for SAP S/4HANA on the SAP
Help Portal under Product Assistance Cross Components Master Data Governance Data Protection in
Master Data Governance
Data Archiving in Master Data Governance .
Conguration: Simplied Blocking and Deletion
● You congure the settings related to the blocking and deletion of business partner, customer, and supplier
master data in Customizing under
Cross-Application Components Data Protection Deletion of Data
Deletion of Business Partner Data .
● For information on dening ILM rules, see the product assistance for SAP S/4HANA on the SAP Help Portal
under
Product Assistance Cross Components SAP Information Lifecycle Management Using ILM
Retention Management in the Application System Editing ILM Policies Editing Retention Rules .
● For information on dening End of Purpose checks, see the product assistance for SAP S/4HANA on the
SAP Help Portal under Product Assistance Cross Components Data Protection Simplied Blocking
and Deletion
End of Purpose (EoP) Check .
End of Purpose
Master Data Governance for Business Partner (MDG-BP), Master Data Governance for Supplier (MDG-S), and
Master Data Governance for Customer (MDG-C) are applications that are providing a workow-based
governance process for business partners. Within this process, the applications MDG-BP, MDG-S, and MDG-C
do not store business partners permanently. In any case, MDG-BP, MDG-S, and MDG-C do not process
business partners with the end of purpose indicator assigned.
For Master Data Governance, consolidation and Master Data Governance, mass processing, we recommend to
use only business partner records that are not selected for End of Purpose (EoP).
The MDG, consolidation application and the MDG, mass processing application do not process business
partners with the end of purpose indicator assigned.
For MDG, consolidation, we recommend to delete source data after the end of the consolidation process.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 497

Storage of Personal Data
All Master Data Governance applications store data only temporarily.
Changes to Personal Data
The system logs changes to personal data using change documents.
Read Access Logging for MDG
For information on read access logging, see Read Access Logging under Data Protection of this Security Guide.
Enhancements
● For Master Data Governance for Custom Objects, we do not recommended to enhance personal data in
your own objects. If it is necessary, you need to ensure to archive and delete enhanced data for the End of
Purpose (EoP) goal.
● For Master Data Governance, central governance, we recommend to use backend tables of SAP-BP for
enhancements and enhance the MDG data model accordingly. .
13.13.6 Agent Framework
13.13.6.1 Deletion of Personal Data in Agent Framework
The Agent Framework might process data (personal data) that is subject to the data protection laws applicable
in specic countries as described in SAP Note 1825544 .
The Agent Framework works in conjunction with the Change Notication Service (CA-GTF-TS-CNS). The
Change Notication Service represents an Agent Framework Event (such as a limit change to an account) in
the form of a change pointer. Each change pointer is based on an export object.
In addition to the change pointers generated for an export object, the CNS can be congured to also provide
images of the export object events. Depending on the export object type, these images might contain personal
data. For data protection reasons, you must delete the image data at regular intervals. You should therefore
schedule a regular job to call one of the two deletion reports CNS_CP_DELETE or CNS_DP_DELETE_MULT. For
498
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

this, you can use the simplied, integrated job control in the Agent Framework available in Customizing for
Cross-Application Components General Application Functions Agent Framework .
More Information
For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal at http://
help.sap.com/s4hana_op_1709 and go to
● Cross Components Data Protection .
13.14 SAP S/4HANA Industries
13.14.1 Automotive
13.14.1.1 Vehicle processes for Wholesale and Retail
13.14.1.1.1 Authorizations
Vehicle Processes for Wholesale and Retail uses the authorization concept provided by the SAP NetWeaver AS
for ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP
NetWeaver AS Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 499

Authorization Object Description
C_AUTO_VMS Vehicle Management System (VMS): Controls whether a
user is allowed to execute VMS actions
C_AUTO_DPV Dealer Portal VMS: Controls whether a user is allowed to ex
ecute dealer portal functions, for example, create a sales or
der without a vehicle
13.14.1.1.2 Deletion of Personal Data
Use
The Vehicle Management System (VMS) might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA
on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Vehicle Management System (IS-A-VMS) Archiving Object
VEHICLE
ILM Object
VEHICLE
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Vehicle Management System (IS-A-
VMS)
EoP Check table
VLCVEHICLE
500 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
13.14.2 Banking
13.14.2.1 SAP Business Partner for Financial Services (FS-BP)
The security policy with SAP Business Partner for Financial Services (FS-BP) is very similar to the security
policy with the central SAP Business Partner (SAP BP).
13.14.2.1.1 Authorizations
You create roles in Customizing for SAP Banking under SAP Business Partner for Financial Services General
Settings Business Partner Basic Settings Authorization Management .
The authorization objects are the responsibility of the SAP Business Partner. SAP Financial Customer
Information Management (FS-BP) is only responsible for the following authorization objects:
● T_BP_DEAL (Standing Instructions/Transactions)
You can use this authorization object to control the company code-dependent authorizations for
displaying/creating/changing standing instructions.
There are standing instructions for:
○ Payment details
○ Derived ows
○ Correspondence
○ Transaction authorizations
● B_BUPA_SLV (Selection Variant for Total Commitment)
A selection variant includes various settings for the total commitment (such as which business partner
roles and relationships can be used for the selection, or whether detailed information can be displayed).
If you activate the SACF scenario FSBP_RATINGS (FS-BP: Scenario for Ratings and Credit Standing Data) in the
Workbench for Switchable Authorization Check Scenarios (transaction SACF), the following FS-BP
authorization objects are also available:
● B_BUPA_RAT (Business Partner: Ratings)
You can use this authorization object to check whether a user has the authorization to create, change,
display, or delete rating procedures. For each rating procedure, you can dierentiate between an
authorization for a permitted period or an authorization for any period. The prerequisite for this is that you
have made the settings for the periods in Customizing for
SAP Banking under SAP Business Partner for
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 501

Financial Services Settings for Financial Services General Settings Ratings/Credit Standing Ratings
Set Rating Procedures and Ratings .
● B_BUPA_CRS (Business Partner: Credit Standing Data)
You can use this authorization object to check whether a user has the authorization to display and change
credit standing data.
13.14.2.1.2 Network and Communication Security
In the case of Total Commitment, SAP ERP communicates with other SAP systems (such as Account
Management (FS-AM)). Communication with non-SAP systems is also possible.
Communication takes place using Remote Function Call (RFC).
13.14.2.1.2.1 Communication Destinations
Depending on the scenario, an RFC user is required for communication via Remote Function Call (RFC). This
user requires the appropriate authorizations for the target system (such as FS-CML or FS-AM).
13.14.2.1.3 Data Protection
The data protection concept with SAP Business Partner for Financial Services (FS-BP) is very similar to the
data protection concept with the central SAP Business Partner (SAP BP).
Integration with Agent Framework (FS-FND-AF)
SAP Business Partner for Financial Services can be used in conjunction with the Agent Framework to provide
other participating applications with all changes made to business partner master data. The Agent Framework
uses the Change Notication Service (CA-GTF-TS-CNS) and adds to it.
If you made the necessary settings in Customizing, the CNS generates so-called change pointers for each
change made to a business partner. These change pointers can then be processed by the Agent Framework
which sends the updated information to the participating applications. In addition to the change pointers, the
system generates an image of the export object. These images are stored in table FSBP_CNS_IMAGE and
contain personal data of the corresponding business partner. For data privacy reasons, you have to delete the
processed change pointers regularly. You should therefore schedule a regular job to call one of the two deletion
reports
CNS_CP_DELETE or CNS_CP_DELETE_MULT.
502
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

More Information
For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal at http://
help.sap.com/s4hana_op_1709 and go to
● Cross Components Data Protection .
13.14.2.1.4 Data Storage Security
The authorization object B_CCARD controls access to the credit card information that is stored in the business
partner. This control falls under the area of responsibility of the central SAP Business Partner.
You can use authorization groups (authorization object B_BUPA_GRP) to protect employee data.
If you activate the SACF scenario FSBP_RATINGS (FS-BP: Scenario for Ratings and Credit Standing Data) in the
Workbench for Switchable Authorization Check Scenarios (transaction SACF), the following FS-BP
authorization objects are also available:
● B_BUPA_RAT (Business Partner: Ratings)
● B_BUPA_CRS (Business Partner: Credit Standing Data)
13.14.2.2 Bank Customer Accounts (BCA)
13.14.2.2.1 Authorizations
The following standard roles are available in Bank Customer Accounts (BCA):
Role Description
SAP_ISB_ACCOUNTS_ADMIN_AG SAP Banking BCA: Administrator in Account Management
SAP_ISB_ACCOUNTS_ASSISTANT_AG SAP Banking BCA: Assistant in Account Management
SAP_ISB_ACCOUNTS_STAFF_AG SAP Banking BCA: Clerical Sta in Account Management
For more information on authorization management and the authorization objects in Bank Customer
Accounts, see the product assistance documentation, under
Enterprise Business Applications Finance
SAP Banking Bank Customer Accounts (BCA) General SubjectsAuthorization Administration , and its
subtopic Authorization Objects.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 503

Bank Customer Accounts (BCA) also contains the following business transaction events on the subject of
authorizations:
Business Transaction Event Description
SAMPLE_INTERFACE_00011040 AUTH1 account
SAMPLE_INTERFACE_00011700 Authorization checks in the information system
SAMPLE_INTERFACE_00011701 Authorization check in the information system (RFC)
SAMPLE_INTERFACE_00010950 Check management
SAMPLE_INTERFACE_00010210 Payment item dialog
SAMPLE_INTERFACE_00010410 Payment order dialog
SAMPLE_INTERFACE_00010411 Standing order dialog
13.14.2.2.2 Network and Communication Security
Bank Customer Accounts (BCA) communicates with the following external systems:
● Payment transaction systems
● Interest income tax
● Financial Accounting (FI), if Financial Accounting (FI) runs on another system
Encrypt communication with external systems in accordance with the SAP standards.
Communication with all external systems is performed via Remote Function Call (RFC).
13.14.2.2.3 Data Storage Security
The security of sensitive objects such as savings accounts and checking accounts is guaranteed by the general
authorization concept of Bank Customer Accounts (BCA).
For employee accounts, the following security mechanisms are available in addition to the general
authorization concept:
The following special authorization objects
F_EMAC_MTH
F_EMAC_TRN
The following special eld modication criterion of the Business Data Toolset (BDT)
FMOD1
This criterion is applied to employee accounts.
504
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Using Logical Path and Filenames to Protect Access to the File System
The Bank Customer Accounts (BCA) application saves data in les in the le system. Therefore, you must
provide access to the corresponding les in the le system without allowing access to other directories or les
(also known as directory traversal).
You can do this by specifying logical paths and le names in the system that map to the physical paths and le
names. The system validates this mapping at runtime and if access is requested to a directory that does not
match a dened mapping, then the system issues and error message.
The following lists the logical le names and paths used by Bank Customer Accounts (BCA) and the programs
for which these le names and paths apply:
Logical File Names Used in This Application
The following logical le names have been created to enable the validation of physical le names:
BKK_PAYMEX_DE_DTA_FILE
Program using this logical le name:
RFBKPAYMEX_DE_DTA
Parameters used in this context: None
BKK_PAYMIN_DE_DTA_FILE
Program using this logical le name:
RFBKPAYMIN_DE_DTA
RFBKPAYMINREST_DE_DTA
RFBKPAYMINREV_DE_DTA
Parameters used in this context: None
Logical File Paths Used in This Application
The logical le name BKK_PAYMEX_DE_DTA_FILE uses the logical le path BKK_PAYMEX_DE_DTA.
The logical le name BKK_PAYMIN_DE_DTA_FILE uses the logical le path BKK_PAYMIN_DE_DTA.
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out which
paths are being used by your system, you can activate the corresponding settings in the Security Audit Log.
13.14.2.2.4 Deletion of Personal Data in IS-B-BCA
Use
The Bank Customer Accounts (IS-B-BCA) component might process data (personal data) that is subject to the
data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 505

to control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
BKK For more information, see SAP Note
2023415 .
BKK_BUPA_EVENT_EOP_CHECK
ILM object FIBA_BUPA
BKK For more information, see Archiving or
Destroying Bank Customer Accounts
Data
, and SAP Note 2023417 .
ILM objects:
● BKKPRENOTE
● FIBA_ACCNT
● FIBA_BKST
● FIBA_CFBAL
● FIBA_EFTEX
● FIBA_EFTIN
● FIBA_ENRCH
● FIBA_EVLIM
● FIBA_GL
● FIBA_GLBAL
● FIBA_HIERA
● FIBA_HOLD
● FIBA_INCAL
● FIBA_ITEM
● FIBA_ORDER
● FIBA_PECAL
●
FIBA_PXPO
● FIBA_STORD
● FIBA_TERM
● FIBA_TOTAL
Available Check
Implemented Solution: End of Purpose Check
506
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
13.14.2.2.5 Specic Read Access Log Congurations
Use
In Read Access Logging (RAL), you can congure which read-access information to log and under which
conditions. SAP delivers sample congurations for applications.
The scenario Payment Document Display/Change/Create (Tx WZR(1/2/3)) in Settlement Management (LO-AB)
logs data in order to record any access to banking data related to a customer or a vendor. You can nd the
congurations as described in the Read Access Logging [page 31] chapter.
In the following congurations, elds are logged in combination with additional elds, in the following business
contexts:
Conguration Fields Logged Business Context
LOAB_BANK KOMWBRD-BANKL
Bank Keys
LOAB_BANK KOMWBRD-BANKN
Bank account number
LOAB_BANK KOMWBRD-BANKS
Bank country key
LOAB_BANK KOMWBRD-BKONT
Bank country key
LOAB_BANK KOMWBRD-BKREF
Reference specications for bank de
tails
LOAB_BANK KOMWBRD-DTAMS
Instruction key for data medium ex
change
LOAB_BANK KOMWBRD-DTAWS
Indicator for Data Medium Exchange
13.14.2.3 Loans Management (FS-CML)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 507

13.14.2.3.1 Authorizations
Authorization management for mortgage loans is based on the existing authorization concept in Loans
Management(FS-CML).
The authorization check is performed according to the principle of inclusion, that is to say, if a user has
authorization to activate a business transaction, he or she also has authorization to delete it. The authorization
for making a posting includes the authorization for making a cancellation.
If other functions are called from a business transaction, the relevant authorization check is performed in this
business transaction before the other function is accessed. This avoids any termination of the functions that
are being called.
To set up your authorization management for mortgage loans, you can use the following roles included in the
delivery scope:
Role Description Scope
Loans Ocer SAP_CML_LOANS_OFFICER
● Create, change, display, delete
business partner
● Collateral value calculation, credit
standing calculation and decision-
making
● Maintain objects and securities
● Create contracts, or transfer from
application or oer
● Enter disbursements
● Process correspondence
● Release loan (colleague or supe
rior)
● Process business operations (such
as charges, individual posting, pay
o)
Credit Analyst SAP_CML_CREDIT_ANALYST
● Create, change, display, delete
business partner
● Maintain loan enquiries, applica
tions and oers
● Calculate credit standing
● Decision-making
● Maintain limits
● Calculate the collateral value
● Maintain objects and securities
Rollover Ocer SAP_CML_ROLLOVER_OFFICER
● Loan rollover (individual and mass)
● Process correspondence
● Management of rollover le
● Maintain condition tables
508 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Role Description Scope
Sta Accountant for Loans SAP_CML_STAFF_ACCOUNTANT
● Post transactions
● Clearing
● Create payments
● Post and monitor incoming pay
ments
● Process waivers and write-os
● Cancellation
● Accrual/deferral
● Valuation
● Generating accounting reports
Manager of Loans Department SAP_CML_DEPARTM_MANAGER
● Release
● Maintain condition tables
● Change limits
● Risk analysis
● Monitor le (rollover or process
management)
● Monitor portfolio and portfolio
trend using reports; reports and
queries
Product Administrator SAP_CML_PRODUCT_ADMIN
● Update reference interest rates
● Maintain condition tables
● Maintain new business tables
Technical Administrator SAP_CML_TECHNICAL_ADMIN
● Perform mass runs (such as mass
print run), set status of plan to
completed, post planned records
● Currency Conversion
● Update reference interest rates
and currency rates
● Reorganization and data archiving
● Dene queries, drilldown reporting
forms and reports
● Maintain performance parameters
● Analyze change pointers
● Dene export interfaces
You can assign these roles to the users in your company. Do not make any changes to the original roles, as
these changes would be overwritten by the standard settings when the system is upgraded.
If you want to make adjustments, copy these roles. To do so, in the SAP Easy Access menu, choose Tools
Administration User Administration Role Administration Roles . Here you can group together
authorizations for consumer loans into your own dened roles, and assign these to users in your departments,
for example. In the rst step you maintain the role menu. You can structure this yourself by adding and, if
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 509
necessary, renaming les, transactions, and reports. In addition to manually grouping together the relevant
transactions, you can also transfer these from the SAP menu or another role. You then maintain the
authorizations for your role. The system proposes certain authorizations and their characteristics. You can also
add more objects. Then you need to generate the authorization prole. Finally, you maintain the users who are
to have the authorizations contained in the role. You can also use elements from organizational management,
such as position in the organization. The advantage here is that you do not have to maintain the user
assignment individually in each role if a person changes jobs. You can also use this function in release.
13.14.2.3.2 Network and Communication Security
Loans Management (FS-CML) does not communicate with other systems.
The only exception is the loan origination process. In this process, CRM serves as the entry system, and FS-
CML as the back-end system. Communication takes place by means of XI.
13.14.2.3.3 Data Storage Security
The security of sensitive data in Loans Management (such as loan contracts, consumer loans, collateral values,
credit standing calculations, collateral) is guaranteed by the general authorization concept of Loans
Management (FS-CML).
It is possible to display business partner data from Loans Management. You can use the authorization concept
of central SAP Business Partner to protect this data.
For more information about authorizations and security of data storage, see http://help.sap.com under SAP
Business Partner Security.
Using Logical Path and Filenames to Protect Access to the File System
The Loans Management (FS CML) application saves data in les in the le system. Therefore, you must provide
access to the corresponding les in the le system without allowing access to other directories or les (also
known as directory traversal).
You can do this by specifying logical paths and le names in the system that map to the physical paths and le
names. The system validates this mapping at runtime and if access is requested to a directory that does not
match a dened mapping, then the system issues and error message.
The following lists the logical le names and paths used by Loans Management (FS CML) and the programs for
which these le names and paths apply:
Logical File Names Used in This Application
The following logical le names have been created to enable the validation of physical le names:
● CML_PAYMENT_US
● Program using this logical le name:
510
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
● RFVD_AUTODRAFT_PROCESS
● RFVD_PAY_STOP
● Parameters used in this context: None
● CML_CREDIT_BUREAU
● Program using this logical le name:
● RFVD_CBR_PROCESS
● Parameters used in this context: None
● CML_MIGRATION_OBJECTS_LOGFILE_IN
● Program using this logical le name:
● RFVOBJ01
● Parameters used in this context: None
● CML_MIGRATION_OBJECTS_LOGFILE_OUT
● Program using this logical le name:
● RFVOBJ01
● RFVOBJ01_CREATE_STRUCTURE
● Parameters used in this context: None
● CML_MIGRATION_OBJECTS_PHYSFILE_IN
● Program using this logical le name:
● RFVOBJ01
● Parameters used in this context: None
● CML_MIGRATION_OBJECTS_PHYSFILE_OUT
● Program using this logical le name:
● RFVOBJ01
● RFVOBJ01_CREATE_STRUCTURE
● Parameters used in this context: None
● CML_MIGRATION_COLLATERALS_LOGFILE_IN
● Program using this logical le name:
● RFVSIC01
● Parameters used in this context: None
● CML_MIGRATION_COLLATERALS_LOGFILE_OUT
● Program using this logical le name:
● RFVSIC01
● RFVSIC01_CREATE_STRUCTURE
● Parameters used in this context: None
● CML_MIGRATION_COLLATERALS_PHYSFILE_IN
● Program using this logical le name:
● RFVSIC01
● Parameters used in this context: None
● CML_MIGRATION_COLLATERALS_PHYSFILE_OUT
● Program using this logical le name:
● RFVSIC01
● RFVSIC01_CREATE_STRUCTURE
● Parameters used in this context: None
Logical File Paths Used in This Application
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 511

● The logical le names CML_PAYMENT_US and CML_CREDIT_BUREAU use the logical le path CML_ROOT.
● The logical le names CML_MIGRATION_OBJECTS_LOGFILE_IN,
CML_MIGRATION_OBJECTS_LOGFILE_OUT, CML_MIGRATION_OBJECTS_PHYSFILE_IN,
CML_MIGRATION_OBJECTS_PHYSFILE_OUT, CML_MIGRATION_COLLATERALS_LOGFILE_IN,
CML_MIGRATION_COLLATERALS_LOGFILE_OUT, CML_MIGRATION_COLLATERALS_PHYSFILE_IN and
CML_MIGRATION_COLLATERALS_PHYSFILE_OUT use the logical le path CML_MIGRATION
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out which
paths are being used by your system, you can activate the corresponding settings in the Security Audit Log.
13.14.2.3.4 Deletion of Personal Data in FS-CML
Use
The Consumer Mortgage Loans (FS-CML) component might process data (personal data) that is subject to
the data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management
(ILM) to control the blocking and deletion of personal data. For more information, see the product assistance
for
SAP S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance
Cross Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
CMLCONTRCT Loan Master Data Archiving object CMLCONTRCT
ILM object CMLCONTRCT
CMLMODCALC Model Calculation Archiving object CMLMODCALC
ILM object CMLMODCALC
CMLCRSTND Credit Standing Calculation Destruction object CML_CRSTAND
CALC_DESTRUCTION
ILM object CML_CRSTANDCALC_DE
STRUCTION
512 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Object Detailed Description Provided Deletion Functionality
CMLINTPAR Interested Party Destruction object CML_INTEREST
PARTY_DESTRUCTION
ILM object CML_INTERESTPARTY_DE
STRUCTION
CMLCOLLATE Collaterals Destruction object CMLCOLLATE
ILM object CMLCOLLATE
CMLCOLOBJ Collateral Objects Destruction object CMLCOLOBJ
ILM object CMLCOLOBJ
Relevant Application Objects and Available EoP functionality
Application Object Implemented Solution (End of Pur
pose Check)
Further Information
CMLCONTRCT Loan Master Data FLBP_CONTR_EVENT_EOP_CHECK
CMLMODCALC Model Calculation FLBP_MODEL
CALC_EVENT_EOP_CHECK
CMLCRSTND Credit Standing Calculation FLBP_CR_STND_EVENT_EOP_CHECK
CMLINTPAR Interested Party FLBP_INT_PAR_EVENT_EOP_CHECKN
CMLCOLLATE Collaterals FLBP_COLLTRL_EVENT_EOP_CHECK
CMLCOLOBJ Collateral Objects FLBP_COLLOBJ_EVENT_EOP_CHECK
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in
Customizing for Cross-Application Components under Data Protection.
13.14.2.4 Collateral Management (CM)
Purpose
The purpose of this guide is to explain the security-specic features built-in for the SAP Collateral Management
( CM ).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 513
To understand the security features provided in CM, you must read the SAP Netweaver Application Server
security guide that describes the basic security aspects and measures for SAP systems.
13.14.2.4.1 Authorizations
A multitude of standard roles are shipped with SAP Collateral Management ( CM ) in the SAP ECC 6.0. These
roles are of exemplary character. The standard roles must be modied by the Customers based on their
requirements.
Note
The Customers must not use the standard roles in their production systems only with some medications. It
is advisable without any modications. Use the Prole Generator (transaction PFCG) to identify the
standard roles and create additional roles.
The following roles are available in CM for banks:
Role Purpose
SAP_FS_CMS_DISPLAY_ALL Displaying all the entity objects in CM .
SAP_FS_CMS_MAINTAIN_ALL Maintaining (Create, change and display only) all entity ob
jects.
SAP_FS_CMS_MAINTAIN_ALL_PRC Executing all the process related activities in addition to
maintenance of objects
SAP_FS_CMS_CUST_ALL Customizing
SAP_FS_CMS_ADMIN CM administrator role
SAP_FS_CMS_COL_AUDITOR Maintaining all the entity objects and the access to run all
the reports in CM.
SAP_FS_CMS_CREDIT_MANAGER Displaying collateral objects and collateral agreements.
SAP_FS_CMS_CREDIT_RISK_MANAGER Maintaining collateral objects and collateral agreements and
displaying receivables.
SAP_FS_CMS_LIQUIDATION_OFFICER Maintaining liquidation measures.
Authorization Objects in CM
Technical name Name
CMS_PCN_02 Authorization for activities (change request mode)
CMS_PCN_01 Authorization for activities (normal mode)
514 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Technical name Name
CMS_OMS1 Authorization for all collateral objects other than real estate
(replace CMS_OMS from ECC 6.0 onwards
CMS_OMS Authorization for all collateral objects other than real estate
(obsolete from ECC 6.0 onwards)
CMS_CAG Authorization object for collateral agreements
CMS_RE Authorization object for real estate objects in CM.
CMS_RBL Authorization object for receivable in CM.
Characteristic Based Authorizations
In the Collateral Management, all the objects must belong to an administration organizational unit. The
authorization objects for collateral objects(real estate and other collateral objects) and collateral agreements
are based on a combination of the administration organizational unit and the entity type(assigned using a
process control key). For receivables, the authorizations are based on the receivable organizational unit, the
receivable status and the product. Authorizations for receivables is valid only for the receivables created in the
CM or even the local copies of the receivables in external credit systems.
Note
For example, you can use the attribute administration organization unit to dierentiate between
employee ,VIP and normal customers objects. You can also create objects in these organizational units as
characteristics, which can then also be used to protect application data.
13.14.2.4.2 Network Communication and Security
The table below shows the communication paths used by the SAP Collateral Management ( CM ), the protocol
used for the connections and the type of data transferred.
Communication Path Protocol Used Type of Data Transferred
Data Requiring Special Pro
tection
Financial Customer Informa
tion System (FS- Business
Partner)
RFC Business partner master
data
SAP Document Management
System (DMS)
RFC Document data
Loans Management (CML) RFC Loan data
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 515

Communication Path Protocol Used Type of Data Transferred
Data Requiring Special Pro
tection
SAP Business Information
Warehouse (BIW)
IDoc and RFC Collateral agreements, collat
eral objects, charges, collat
eral agreement – receivable
assignment and calculations
data
SAP Bank Analyzer ( Basel II) IDoc and RFC Collateral agreements, collat
eral objects, charges, collat
eral agreement – receivable
assignment andcalculations
data
The following RFC connections have to be set up for operating the CM . You are advised not to create the users
belonging to these as dialog users.
● RFC communication with the Tool BW
● RFC communication within the Tool BW
● RFC communication in the context of import methods for the client copy. The relevant authorization
objects are:
● S_TABU_DIS; S_RS_ICUBE; S_RS_ADMWB; S_RS_ISOUR; S_BTCH_ADM; S_ADMI_FCD; S_BTCH_JOB;
S_RS_ODSO; S_RS_ISET
CM provides the following business application programming interfaces (BAPIs) for allowing external systems
to connect to it:
● BAPI_CM_AST_GET_MULTI
● BAPI_CM_CAG_CREATE
● BAPI_CM_CAG_GETDETAIL_MULTI
● BAPI_CM_CAG_GET_BY_RBL
● BAPI_CM_GENLNK_RBL_ON_RBL_01
● BAPI_CM_GENLNK_RBL_ON_RBL_02
● BAPI_CM_SEC_GETDETAIL_MULTI
● BAPI_CM_RE_GETDETAIL_MULTI
● BAPI_CM_RIG_GETDETAIL_MULTI
● BAPI_CM_MOV_GETDETAIL_MULTI
BAPIs are standard SAP interfaces and are important in the technical integration and in exchange of business
data between SAP components and between the SAP and non-SAP components. BAPIs enable you to integrate
these components. They are therefore an important part of developing integration scenarios where multiple
components are connected to each other, either on a local network or on the internet.
BAPIs allow integration at the business level and not at the technical level. This provides for greater stability of
the linkage and independence from the underlying communication technology.
The current requirement for BAPIs in CM caters mainly to the migration scenarios. Hence these BAPIs are not
protected by special authorizations. Authorization checks for BAPIs can be provided (in the future releases), if
there are requirements for them.
516
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

CM also provides an extensive enhancement concept that oers user exits in the form of Business Add-Ins
(BADIs).
Network Security and Communication Channels
Collateral Management ( CM ) uses the same communication channels that are described in the SAP
NetWeaver AS security guide. No further customer-specic communication channels are provided. Hence the
aspects and actions described in the SAP NetWeaver AS security guide (such as use of SAPRouter in
combination with Firewall, use of Secure Network Communication (SNC), Communication Front-End-
Application Server, connection to the database) also apply for CM .
13.14.2.5 Reserve for Bad Debt (FS-RBD)
Please Note: Monitor System Storage before le import and restrict access authority for RBD le upload.
13.14.2.5.1 Authorizations
The authorization concept used by Reserve for Bad Debt (RBD) is the same as the SAP authorization concept.
The authorization checks in RBD dierentiate between the following dimensions:
● Activity
You use the activity to control what a user is permitted to do.
● Organization
At the level of the RBD-specic objects RBD Area or Organizational Unit, you specify which data the user is
permitted to display or edit in accordance with the activity.
Standard Proles
Precongured standard roles are not shipped with RBD. The following standard proles are shipped with the
SAP system:
Standard Proles
Role Description
S_A.SYSTEM
Access authorizations for the basis system only
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 517
Role Description
S_A.ADMIN
Access authorizations for administration of the operational
SAP system, but without access authorization for the follow
ing areas:
● ABAP/4 Development Workbench
● Maintenance of super users
● Maintenance of standard proles beginning with “S_A”
S_A.DEVELOP
Access authorizations for users who work with ABAP/4 De
velopment Workbench
S_A.CUSTOMIZ
Access authorizations for basis settings in the Customizing
system
S_A.USER
Access authorizations for end users (without access authori
zation for SAP work areas)
Authorization Objects
The following authorization objects are shipped with Reserve for Bad Debt (RBD).
RBD Authorization Objects
Object Description
Authorization Field
Activity
Authorization Field
RBD Area
Authorization Field
Organizational Unit
RBD_CUST
RBD: Customizing 16(Execute) Not relevant Not relevant
RBD_EDIT
RBD: Dialog & Batch 01(Add or Create)
02(Change)
03(Display)
05(Lock)
10(Post)
66(Update)
85(Reverse)
86(Transfer Post)
91(Reactivate)
95(Unlock)
H1(Deactivate)
According to Custom
izing (table /IBS/
CRB_RBD_P
)
According to Custom
izing (table /IBS/
CRB_ORGEIN
)
518 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Object Description
Authorization Field
Activity
Authorization Field
RBD Area
Authorization Field
Organizational Unit
RBD_REPO
RBD: Reporting Not relevant According to Custom
izing (table /IBS/
CRB_RBD_P
)
According to Custom
izing (table /IBS/
CRB_ORGEIN
)
/IBX/EDIT
IPX: Dialog & Batch 02(Change)
03(Display)
06(Delete)
10(Post)
21(Transfer Valuation)
23(Maintain)
41(Delete on
Database)
43(Release)
46(Aggregate
Valuation)
60(Import)
69(Delete Valuation)
71(Analyze)
78(Assign)
85(Reverse)
93(Calculate)
94(Override)
C8 (Conrm Change)
According to Custom
izing (table /IBS/
CRB_RBD_P
)
Not relevant
Caution
For the RBD Area and Organizational Unit authorization elds, you can use the wildcard symbol “*”. If you
use the wildcard symbol, access authorization is not checked for the relevant authorization eld.
Example
Description in relation to these authorization objects:
● The assignment of authorization object RBD_CUST with activity 16 authorizes the user to use the
function RBD: Duplicate Customizing Account Determination(/IBS/MRB_CUST_KTOFI).
● The assignment of authorization object RBD_EDIT with activity 01 and RBD area 0001 enables a user
to display the data for an RBD account in RBD area 0001.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 519
● The assignment of authorization object RBD_EDIT with activity 02, RBD area 0002, and organizational
unit London enables a user to change data for an RBD account in RBD area 0002 that is assigned to
the organizational unit “London”.
However, if the user is not assigned any other access authorizations, he or she cannot change an RBD
account from RBD area 0002 that is assigned to the organizational unit “Tokio”.
● The assignment of authorization object RBD_EDIT with activities 02 and 10, and RBD area 0003
enables a user to create and post planned records for an RBD account in RBD area 0003.
However, a prerequisite for this is that the principle of multiple control for posting planned records (risk
provision proposals) has not been activated in Customizing for RBD.
● The assignment of authorization object RBD_REPO with RBD area “*” and organizational unit “*” allows
a user to display the RBD data for all RBD areas and all organizational units, using the reports of the
RBD information system.
Use of RBD Authorization Objects
RBD Area Menu, Account Management Folder
Transaction Object (Activity) RBD Area + Organizational Unit
Create RBD Account /IBS/
RB_KTO_INS
RBD_EDIT (01) Relevant + Relevant
Change RBD Account /IBS/
RB_KTO_UPD
RBD_EDIT (02, 05, 10, 85, 95, H1) Relevant + Relevant
Display RBD Account /IBS/
RB_KTO_DIS
RBD_EDIT (03) Relevant + Relevant
Reactivate RBD account /IBS/
RB_KTO_REACT
RBD_EDIT (91) Relevant + Relevant
Balance Sheet Transfer RBD /IBS/
RB_RECLAS
RBD_EDIT (not relevant) Not Relevant + Not Relevant
ECF: Balance Sheet Transfer /IBS/
RB_ECF_RECLAS
RBD_EDIT (86) Relevant + Not Relevant
ECF: Contract Reallocation /IBS/
RB_REALLOC
RBD_EDIT (86)
RBD_REPO (not relevant)
Relevant + Not Relevant
Relevant + Not Relevant
ECF: Manual Contract Manage
ment /IBS/RB_MANCON
RBD_EDIT (01, 02, 03) Relevant + Not Relevant
520 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

RBD Area Menu, Information System Folder
Transaction Object (Activity) RBD Area + Organizational Unit
Worklist - Processor /IBS/
RB_WORKLIST
and /IBS/
RB_WORKLIST_SEL
RBD_REPO (not relevant)
RBD_EDIT (not relevant)
Relevant + Relevant
Not Relevant + Not Relevant
Monitoring - Planned Record
Change /IBS/RB_MAN_PLAN_CHG
RBD_REPO (not relevant)
RBD_EDIT (not relevant)
Not Relevant + Relevant
Not Relevant + Relevant
Decision Template for Past Analy
sis /IBS/RB_PROPRES_HGB
RBD_REPO (not relevant)
S_GUI (61)
Not Relevant + Not Relevant
Not Relevant + Not Relevant
Decision Template for Future Analy
sis /IBS/RB_PROPRES_IAS
RBD_REPO (not relevant)
S_GUI (61)
Not Relevant + Not Relevant
Not Relevant + Not Relevant
Decision Template for ECF Proce
dure /IBS/RB_PROPRES_ECF
RBD_REPO (not relevant)
S_GUI (61)
Not Relevant + Not Relevant
Not Relevant + Not Relevant
Reporting Function /IBS/
RB_REPORTING
RBD_REPO (not relevant) Not Relevant + Not Relevant
Development List /IBS/RB_DEVL RBD_REPO (not relevant) Relevant + Relevant
Development List per Source System
Contract /IBS/RB_DEVL_SINGLE
RBD_REPO (not relevant) Relevant + Relevant
Individual Document Table - Source
System /IBS/MRB_VS_SALDO
Not relevant Not Relevant + Not Relevant
Posting Log /IBS/RB_LOG_POST RBD_EDIT (03)
S_APPL_LOG (03)
Relevant + Not Relevant
● Drilldown Reporting with Referen
ces
/IBS/RB_REF
● IRP: Filling Report ECF Gate /IBS/
RB_ECF_FILL
● IVA: List of Notes for Multiple
Source Systems /IBS/RB_HINTM
RBD_REPO (not relevant) Relevant + Not Relevant
RBD Area Menu, Flat-Rate Value Adjustment Procedure Folder
Transaction Object (Activity) RBD Area + Organizational Unit
FVA: Fill RBD Gate for FS-CML /IBS/
RB_FILL_GATE
Not relevant Not Relevant + Not Relevant
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 521

Transaction Object (Activity) RBD Area + Organizational Unit
FVA: Enrich RBD Gate /IBS/
RB_GATE_MODIFY
RBD_REPO (not relevant) Relevant + Not Relevant
FVA: Update Run /IBS/RB_PWV_UPD RBD_EDIT (10) Relevant + Not Relevant
FVA: Update Run (PPF) /IBS/
RB_PWV_UPD_PPF
RBD_EDIT (10) Relevant + Not Relevant
RBD Area Menu, Periodic Processing Folder
Transaction Object (Activity) RBD Area + Organizational Unit
IVA: Update Run - Past Analysis /IBS/
RB_EWB_UPD
RBD_EDIT (10) Relevant + Relevant
● IVA: Filling Report Future Analy
sis
/IBS/RB_IAS_FILL
● IVA: Update Run - Future Analy
sis /IBS/RB_IAS_UPD
● IVA: Update Run - Future Analysis
(PPF) /IBS/RB_IAS_UPD_PPF
● IVA: Unwinding Run Future Analy
sis /IBS/RB_IAS_UPD_UNW
RBD_EDIT (02) Relevant + Relevant
● IVA: Posting Run - Future Analy
sis
/IBS/RB_IAS_POST
● IVA: Posting Run - Future Analysis
(PPF) /IBS/RB_IAS_POST_PPF
● IVA: Unwinding Posting Run Future
Analysis /IBS/
RB_IAS_POST_UNW
RBD_EDIT (10) Relevant + Relevant
● IRP: Filling Report ECF Gate /IBS/
RB_ECF_FILL
RBD_EDIT (02) Not Relevant + Not Relevant
● IRP: Deletion Report ECF
Gate
/IBS/RB_ECF_CLEAR
Not relevant Not Relevant + Not Relevant
● IRP: Update Run ECF /IBS/
RB_ECF_UPDATE
● IRP: Update Run ECF (PPF) /IBS/
RB_ECF_UPD_PPF
● IRP: Unwinding Run ECF /IBS/
RB_ECF_UPD_UNW
● IRP: Unwinding Run ECF
(PPF) /IBS/RB_ECF_UNW_PPF
RBD_EDIT (02, 10) Relevant + Not Relevant
522 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Transaction Object (Activity) RBD Area + Organizational Unit
IRP: Creation Process ECF /IBS/
RB_ECF_A_CREATE
RBD_EDIT (02) Relevant + Not Relevant
RBD Area Menu, Administration Folder
Transaction Object (Activity) RBD Area + Organizational Unit
RBD: Assign Administrator /IBS/
RB_ASSIGN_CO
RBD_EDIT (02) Not Relevant + Not Relevant
RBD: Automatic Account Crea
tion /IBS/RB_ACC_CREATION
RBD_REPO (not relevant) Relevant + Not Relevant
IVA: Initialization Run for Future Analy
sis /IBS/RB_IAS_UPD_INIT
RBD_EDIT (02) Relevant + Relevant
IRP: Initial Run ECF /IBS/
RB_ECF_UPD_INIT
RBD_EDIT (02, 10) Relevant + Not Relevant
IRP: Initialization ECF (PPF) /IBS/
RB_ECF_INIT_PPF
RBD_EDIT (02, 10) Relevant + Not Relevant
Archive: RBD Account Data (Gen
eral) /IBS/RB_CSARA_ACC
S_ARCHIVE
Not Relevant + Not Relevant
Archive: RBD Flow Data ECF /IBS/
RB_CSARA_ECO
S_ARCHIVE
Not Relevant + Not Relevant
Archive: RBD Flow Past /IBS/
RB_CSARA_HCO
S_ARCHIVE
Not Relevant + Not Relevant
Remove Obsolete Postings
(Past) /IBS/RB_HCO_DEL_POST
RBD_EDIT (02) Relevant + Relevant
Man. Contr.: Data Cleansing /IBS/
RB_MANCON_DEL
RBD_EDIT (02) Relevant + Relevant
RBD Area Menu, Impairment Processing Extension - Environment Folder
Transaction Object (Activity) RBD Area
Upload Files to Application
Server /IBX/FILE_UPLOAD
/IBX/EDIT (60) Not relevant
Import CSV Files /IBX/CSV_IMPORT /IBX/EDIT (60) Not relevant
Maintain Import Data /IBX/IMP_CHNG /IBX/EDIT (43, 60) Not relevant
Main Dialog /IBX/MAIN /IBX/EDIT (02, 03, 10, 23, 94) Not relevant
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 523
Transaction Object (Activity) RBD Area
Restrict Data Selection /IBX/
SELECTION
Not relevant Not relevant
Adjustment of Initial Comparative
Data /IBX/CH_IN_RAT
/IBX/EDIT (C8) Not relevant
Maintain Initial PDs /IBX/MPD /IBX/EDIT (C8) Not relevant
RBD Area Menu, Impairment Processing Extension - Processes Folder
Transaction Object (Activity) RBD Area
Start Migration /IBX/MIGRATION /IBX/EDIT (10, 78, 93) Not relevant
Fill Import Interface Using CSV
Files /IBX/IMPORT
/IBX/EDIT (60) Not relevant
Import CML Files /IBX/CML_IMPORT /IBX/EDIT (60, 93) Not relevant
Build CF-Based Time Slices /IBX/
CR_SLICE_FRM_CF
/IBX/EDIT (93) Not relevant
Rene Imported Data /IBX/
IMP_REFINE
/IBX/EDIT (60, 93) Not relevant
Delete Import Data /IBX/IMP_DELETE /IBX/EDIT (06) Not relevant
Start Import Data Check /IBX/
IMP_CHECK
/IBX/EDIT (60, 78) Not relevant
Start LPD Recalculation /IBX/
RECALC_LPD
/IBX/EDIT (93) Not relevant
Start Impairment Categorization /IBX/
IC_ASSIGN
/IBX/EDIT (78) Not relevant
Start Impairment Calculation /IBX/
CALCULATION
/IBX/EDIT (93) Not relevant
Delete Open Valuations /IBX/
VALUA_DELETE
/IBX/EDIT (69) Not relevant
Compress Open Valuations /IBX/
VALUA_COMPRESS
/IBX/EDIT (46) Not relevant
Transfer Simulated Valuations /IBX/
VALUA_TRANSFER
/IBX/EDIT (21) Not relevant
Reverse Valuations /IBX/REVERT /IBX/EDIT (85) Not relevant
524 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Transaction Object (Activity) RBD Area
Display Logs /IBX/COCKPIT Not relevant Not relevant
RBD Area Menu, Impairment Processing Extension - Archiving Folder
Transaction Object (Activity) RBD Area
Delete Records /IBX/
DEL_FLOW_RECORD
/IBX/EDIT (93) Not relevant
Delete Technical Process Run Informa
tion /IBX/DEL_RUN_INFO
Not relevant Not relevant
Display Archived Data /IBX/
ARCHIVE_SHOW
Not relevant Not relevant
Denition of Customer-Specic Roles
The following information is required for the denition of customer-specic roles:
● SAP logon names of all employees who are to work with RBD
● Relevant transactions that are to be executed in the respective role
● Relevant activities that are to be executed within the relevant transactions
● RBD areas and organizational units aected
To avoid having to dene a separate role for each employee, we recommend that you form groups of employees
that are permitted to execute the same functions. You can then assign a dened role to all of the employees in
the group.
13.14.2.5.2 Network and Communication Security
Depending on the risk provision method used and analysis horizon, the Reserve for Bad Debt (FS-RBD)
application communicates with the following systems:
● SAP Loans Management for Banking, Suite Edition (FS-CML)
● SAP Deposits Management for Banking, Suite Edition (IS-B-BCA)
● SAP Deposits Management for Banking (FS-AM)
● SAP Collateral Management for Banking, Suite Edition (FS-CMS)
● SAP General Ledger Accounting (FI-GL)
Communication takes place using Remote Function Call (RFC). Please use sparate users / passwords for RFC
an Web services. Also do not use technical users because of better tracability.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 525

13.14.2.5.2.1 Communication Destinations
For Remote Function Call (RCF) connections to SAP Deposits Management for Banking (FS-AM), technical
users are required.
These technical users require read authorization, for example, to read balances and account master data.
Please use sparate users / passwords for RFC an Web services. Also do not use technical users because of a
better tracability.
13.14.2.5.3 Trace and Log Files
Trace or log les are created during processing. These can contain security-relevant information – such as
master data, balances, and ow data from source system contracts.
13.14.3 Higher Education and Research
13.14.3.1 Authorizations
The SAP ECC Industry Extension Higher Education & Research component uses the authorization
concept provided by SAP NetWeaver. Therefore, the recommendations and guidelines for authorizations as
described in the SAP NetWeaver Security Guides also apply to the SAP ECC Industry Extension Higher
Education & Research component. The SAP NetWeaver authorization concept is based on assigning
authorizations to users based on roles. For role maintenance, use the prole generator (transaction PFCG)
when using ABAP technology and the User Management Engine's user administration console when using
Java.
Note
For more information about how to create roles, see the SAP NetWeaver Security Guide under User
Administration and Authentication.
Standard Roles
The table below shows the standard roles that are used by SAP Student Lifecycle Management (SLCM).
526
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Role Description
Composite Roles
SAP_CM_ADM_COORDINATOR Admission coordinator
SAP_CM_ADM_OFFICER Admission ocer
SAP_CM_ASM_COORDINATOR Assessment coordinator
SAP_CM_ASM_OFFICER Assessment ocer
SAP_CM_STREC_COORDINATOR Student records coordinator
SAP_CM_STREC_OFFICER Student records ocer
Single Roles
SAP_CM_ACCOUNT_DATA_UPDATE Technical user for automatic update of student account data
after changes to account-relevant student master data
SAP_CM_ADMIN_ACAD_STRUCTURE Administrator for the academic structure (internal single
role)
SAP_CM_ADMOFF_STUDYDATA Activities for the admission coordinator
SAP_CM_ADMREGDATA_DISP Display study data
SAP_CM_ALL
SAP_CM_ASMCO_ADDACT Additional activities for the assessment coordinator
SAP_CM_ASMDATA_DISP Display progression and grades
SAP_CM_ASMOFF_ACT Activities for the assessment ocer
SAP_CM_STMASTERDATA_DISP Display student master data
SAP_CM_STMASTERDATA_MAINT Edit student master data
SAP_CM_STRCO_ADDACT Additional activities for the student records coordinator
SAP_CM_ASMDATA_DISP Display progression and grades
SAP_CM_ASMOFF_ACT Activities for the assessment ocer
SAP_CM_STMASTERDATA_DISP Display student master data
SAP_CM_STMASTERDATA_MAINT Edit student master data
SAP_CM_STRCO_ADDACT Additional activities for the student records coordinator
SAP_CM_STROFF_ACT Activities for the student records coordinator
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 527
Role Description
SAP_CM_MODULEBOOK Module booking (only up to release CM 4.72)
SAP_CM_REGIST Activities for registration (only up to release CM 4.72)
SAP_CM_STUDENTMASTER Student master data processing (only up to release CM 4.72)
All of the above roles are automatically generated by the system.
Note
SAP_IQ_CAMPUS and SAP_CM_ALL are critical roles because they contain a comprehensive authorization
for all
Student Lifecycle Management functions. The following roles are obsolete as of the SAP ECC
Industry Extension Higher Education & Research 6.0 release:
● SAP_IQ_CAMPUS
● SAP_CM_MODULEBOOK
● SAP_CM_REGIST
● SAP_CM_STUDENTMASTER
Standard PFCG Roles in SAP Student Lifecycle Management
If a user does not want to use the portal role, you can choose the PFCG role option. The SLCM application
provides the following PFCG roles:
Name of PFCG Role Relevance to NWBC Relevance to Portal Role
SAP_SR_ACADEMIC_ADVISOR_5 NWBC role for advisor Equivalent to the portal role Academic
Advisor
SAP_SR_UNIVERSITY_INSTRUCTOR_5 NWBC role for university instructor No equivalent portal role available
SAP_SR_STUDENT_5 NWBC role for student Equivalent portal role Student
Once you congured these roles you can access the applications attached to the role using SAP NetWeaver
Business Client. You can use these as entry points to the dierent applications that can be accessed by the
academic advisor, the instructor or the student.
528
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Standard Authorization Objects
If a user does not want to use the portal role, you can choose the PFCG role option. The SLCM application
provides the following PFCG roles:
Authorization Object Description
P_CM_AUDCT Student Lifecycle Management: requirement catalogs
P_CM_AUDIT Audits
P_CM_AUDPR Requirement prole
P_CM_CORR Correspondence
P_CM_FCDOC Student accounting document
P_CM_PROC Activity
P_CM_UCAS Authorization Object Student Lifecycle Management UCAS
(only for Great Britain)
P_CM_UCASR Authorization Object Student Lifecycle Management UCAS
for Reports (only for Great Britain)
P_CM_NLPAY NL Payment Details Authorization Object
P_CM_NLVER NL Verication Authorization Object
Basic Authorizations in SAP Student Lifecycle Management
There are three important authorization objects within SLCM to simplify authorization assignment: :
● S_TCODE
S_TCODE checks whether a user is allowed to start a given transaction. Every time the user starts a menu
command or a transaction code using the command line, the roles assigned to the user are checked to see
whether the user has the authority to execute this transaction.
● PLOG
PLOG checks whether a user is allowed to read, write or insert specic HR Infotypes.
● P_CM_PROC
P_CM_PROC checks whether a user has the authority for a specic Student Lifecycle Management
process.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 529

Structural Authorizations in SAP Student Lifecycle Management
Structural authorizations enable you to dene the set of objects the user is authorized to process. You
determine these objects using evaluation paths. For example, you can dene whether the user receives a
display authorization or a maintenance authorization for these objects.
● Evaluation Paths
An evaluation path is an instruction for the system that determines which object types and relationships
are to be included in an evaluation of the organizational plan. It describes the chain of relationships that
exist between objects in a hierarchical structure. The report takes into account only the objects that lie
along the specied evaluation path.
● Organizational Structure
One or more relationships are then used as paths to evaluate structural information in your organizational
plan (relating to the organizational or reporting structures) or matrix organization. The sequence of the
relationships included in the evaluation path is decisive in how the results of the evaluation are displayed.
Note
As functions of other applications areas, for example, Training and Event Management, Notication
Processing or Student Accounting are integrated into SLCM, users also need authorizations for these
areas.
Note
SLCM contains a number of single roles, which you can combine with the roles of other application areas to
create composite roles. You can either assign a composite role or individual roles to users.
Authorizations in Business Rule Framework plus (BRFplus)
To handle the BRFplus security, the standard authorizations are available in the BRFplus framework.
For more information, see application help for Business Rule Framework plus (BRFplus) in SAP Library for SAP
NetWeaver on SAP Help Portal at http://help.sap.com/netweaver SAP NetWeaver 7.0 (2004s) SAP
Netweaver 7.0 including Enhancement Package 3
SAP NetWeaver SAP NetWeaver by Key Capability
Application Platform by Key Capability Business Services Business Rule Framework plus (BRFplus)
Concepts Authorizations
13.14.3.2 Deletion of Personal Data
Use
The student administration of the Student Lifecycle Management application might process data
(personal data) that is subject to the data protection laws applicable in specic countries as described in SAP
Note 1825544. The SAP Information Lifecycle Management (ILM) component supports the entire software
530
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

lifecycle including the storage, retention, blocking, and deletion of data. The Student Lifecycle Management
(SLCM) solution uses SAP ILM to support the blocking and deletion of personal data as described in the
following sections. SAP delivers an end of purpose check (EoP) for the students registered in the SLCM
application. SAP delivers a end-of-purpose check (EOP) for the blocking of business partner data if the SLCM
application has a student linked to a business partner. All applications register either an end of purpose check
(EoP) in the Customizing settings for the blocking and deletion of the business partner data or a where-used
check (WUC). n.
You can use SAP Information Lifecycle Management (ILM) to control the blocking and deletion of personal
data. For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal at http://
help.sap.com/s4hana_op_1709 Product Assistance Cross Components Data Protection .
End of Purpose Check (EoP)
An end of purpose check determines whether data is still relevant for business activities based on the retention
period dened for the data. . This check determines whether data is still relevant for business activities based
on the retention period dened for the data. The retention period of data consists of the following phases:
● Phase one: The relevant data is actively used.
● Phase two: The relevant data is actively available in the system.
● Phase three: The relevant data needs to be retained for other reasons.
For example, processing of data is no longer required for the primary business purpose, but to comply with
legal rules for retention, the data must still be available. In phase three, the relevant data is blocked. Blocking of
data prevents the business users of SAP applications from displaying and using data that may include personal
data and is no longer relevant for business activities. Blocking of data can impact system behavior in the
following ways:
● Display: The system does not display blocked data.
● Change: It is not possible to change a business object that contains blocked data.
● Create: It is not possible to create a business object that contains blocked data.
● Copy/Follow-Up: It is not possible to copy a business object or perform follow-up activities for a business
object that contains blocked data.
● Search: It is not possible to search for blocked data or to search for a business object using blocked data in
the search criteria.
It is possible to display blocked data if a user has special authorization; however, it is still not possible to create,
change, copy, or perform follow-up activities on blocked data. For information about the conguration settings
required to enable this three-phase based end of purpose check, see the Process Flow and Conguration:
Simplied Blocking and Deletion.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 531

End of Purpose Check (EoP) in SLCM
The end-of-purpose check for SLCM is a simple check to ensure data integrity in the event of potential
blocking. It checks whether there is any dependent data for a business partner that is a student in the SLCM
application and returns one of the following statuses:
● If the business partner is not a student the system returns status as ‘1’ (No business with business
partner).
● If the business partner exists as a student in the SLCM system, then the system checks for the SORT (Start
of retention time), and depending on the date,returns the status ‘2’ (business is ongoing ) or ‘3’ (business
is complete).
The system does not block the business partner related to the student if the status is '3', business is ongoing .
Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
PSCM Student Lifecycle Management: Public
Sector Campus Management
HRIQ_ATTDNData Destruction in Stu
dent Lifecycle Management
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
PSCM EoP implemented EoP checks if the business for the stu
dent and related business partner is
complete or ongoing.
Process Flow
1. Before archiving data, you must rst dene residence time and retention periods in SAP Information
Lifecycle Management (ILM).
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available.
3. You do the following:
○ Run transaction IRMPOL and enter the required retention policies for the central business partner (ILM
object: CA_BUPA).
○ Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner.
532
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
○ Run transaction IRMPOL and maintain the required residence and retention policies for the customer
master and vendor master in SAP S/4HANA (ILM objects: HRIQ_STMD).
○ Run transaction CVP_PRE_EOP to enable the end of purpose check function for the customer master
and vendor master in SAP S/4HANA .
4. Business users can request unblocking of blocked data for customers, vendors and central business
partners by using the transaction BUP_REQ_UNBLK.
5. 5.If you have the necessary authorizations, you can unblock data by running the transaction
BUPA_PRE_EOP and CVP_UNBLOCK_MD.
6. 6.You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of SLCM.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
● Dene the settings for authorization management under Data Protection Authorization Managemen .
For more information, see the Customizing documentation.
● •Dene the settings for blocking in Customizing for Cross-Application Components under Data
Protection Blocking and Unblocking Business Partner
13.14.3.3 Data Storage Security
Data Storage
The data for the application are saved in the database tables. Only the data for academic structure can come
from a le system, the security aspects of which is described in the next section. There is structural
authorization and role based authorization to control access to these data. For more information, see
Authorizations.
Using Logical Path and File Names to Protect Access to the File System
The SAP Student Lifecycle Management applications save data in les in the le system. Therefore,
provide access to the corresponding les in the le system without allowing access to other directories or les
(also known as directory traversal). This is achieved by specifying logical paths and le names in the system
that map to the physical paths and le names. This mapping is validated at runtime and if access is requested
to a directory that does not match a stored mapping, then an error occurs.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 533
The following lists show the logical le names and paths used by the Student Lifecycle Management
application and for which programs these le names and paths apply:
Logical File Names Used
The following logical le names have been created in order to enable the validation of physical le names:
● ISHER_WEBCATALOGXML
○ Programs using this logical le name and parameters used in this context:
○ ◦RHIQ_XML_ACADSTRUC (XML Files of Academic Structure)
Logical Path Names Used
The logical le names listed above all use the logical le path ISHER_WEBCATALOG.
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out which
paths are being used by your system, you can activate the corresponding settings in the Security Audit Log.
For more information, see about data storage security, see the respective chapter in the SAP NetWeaver
Security Guide.
13.14.3.4 Read Access Logging (Industry Applications)
Use
In Read Access Logging (RAL), you can congure which read-access information to log and under which
conditions.
Read access to personal data is partially based on legislation, and it is subject to logging functionality. The
Read Access Logging (RAL) component can be used to monitor and log read access to data and provide
information such as which business users accessed personal data (for example, elds related to bank account
data), and when they did so. In RAL, you can congure which read-access information to log and under which
conditions. SAP delivers sample congurations for applications. For more information, see the application-
specic chapters of the Security Guide.
534
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

You can display the congurations in the system by performing the following steps:
1. In transaction SRALMANAGER, on the Administration tab page, choose Conguration.
2. Choose the desired channel, for example, WebDynpro.
3. Choose Search.
The system displays the available congurations for the selected channel.
4. Choose Display Conguration for detailed information on the conguration. For specic channels, related
recordings can also be displayed.
Prerequisites
Before you can use the delivered RAL congurations, the following prerequisites are met:
● You are using:
○ SAP NetWeaver 7.1 SP0
○ AS ABAP 7.51
○ Kernel 7.45 SP21 and above
○ SAP_UI 7.51 (UI5 1.40)
● The RAL congurations have been activated.
● You have enabled RAL in each system client.
More Information
For general information on Read Access Logging, see the product assistance for SAP NetWeaver on SAP Help
Portal at Start of the navigation path http://help.sap.com/netweaverInformation SAP NetWeaver Library
Function-Oriented View System Security for SAP NetWeaver AS for ABAP Only
13.14.4 Professional Services
13.14.5 Commercial Project Inception and Lean Stang
The following guide covers the information that you require to operate Commercial Project Inception and Lean
Stang securely.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 535

13.14.5.1 Introduction
Introduction
Note
This guide does not replace the administration or operation guides that are available for productive
operations.
Target Audience
● Technology consultants
● System administrators
This document is not included as part of the Installation Guides, Conguration Guides, Technical Operation
Manuals, or Upgrade Guides. Such guides are only relevant for a certain phase of the software life cycle,
whereas the Security Guides provide information that is relevant for all life cycle phases.
Why Is Security Necessary?
With the increasing use of distributed systems and the Internet for managing business data, the demands on
security are also on the rise. When using a distributed system, you need to be sure that your data and
processes support your business needs without allowing unauthorized access to critical information. User
errors, negligence, or attempted manipulation on your system should not result in loss of information or
processing time. These demands on security apply likewise to Commercial Project Inception and Lean Stang.
To assist you in securing Commercial Project Inception and Lean Stang, we provide this Security Guide.
About this Document
The Security Guide provides an overview of the security-relevant information that applies to Commercial
Project Inception and Lean Stang .
Overview of the Main Sections
The Security Guide comprises the following main sections:
● Before You Start
This section references to other Security Guides that build the foundation for this Security Guide.
● Authorizations
This section provides an overview of the authorization concept that applies to Commercial Project
Inception and Lean Stang .
536
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.14.5.2 Before You Start
It is important that you read and understand the information contained in the Authorizations [page 537]
section that is specic to Commercial Project Inception and Lean Stang. In addition, you should be aware of
the information listed in the table below:
Fundamental Security Guides
Scenario, Application or Component Security Guide Most-Relevant Sections or Specic Restrictions
SAP NetWeaver Application Server SAP NetWeaver Security Guide - All sections
SAP ECC SAP ERP Central Component Security Guide - All sections
13.14.5.3 User Management and Authentication
SAP ECC Industry Extension Professional Services uses the user management and authentication mechanisms
provided with the SAP NetWeaver platform, particularly the SAP NetWeaver Application Server ABAP .
Consequently, the security recommendations and guidelines for user management and authentication that are
described in the SAP NetWeaver Application Server ABAP Security Guide also apply to SAP ECC Industry
Extension Professional Services .
User Types
It is often necessary to specify dierent security policies for dierent types of users. For example, your policy
may specify that individual users who perform tasks interactively have to change their passwords on a regular
basis, but not those users under which background processing jobs run.
User type required for SAP ECC Industry Extension Professional Services is Dialog user. Dialog users are
Individual users used for SAP GUI for Windows.
13.14.5.4 Authorizations
Use
The business function Commercial Project Inception and Lean Stang uses the authorization concept provided
by the SAP NetWeaver AS for ABAP. Therefore, the recommendations and guidelines for authorizations as
described in the SAP NetWeaver AS Security Guide ABAP also apply to Commercial Project Inception and Lean
Stang.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 537
Standard Roles
The table below shows the standard roles that are used by Commercial Project Inception and Lean Stang.
Standard Roles
Role Description
SAP_SAWE_UNIVERSAL Maintenance of sta assignments and forecasts
SAP_CATS_LEAN_STAFFING Maintenance of cross-application time sheet (Web Dynpro
application)
SAP_BC_EMPLOYEE Access to HCM data (for employee search, for example)
SAP_BPR_INT_SALES_REP_14 Maintenance of assignment objects of type “SD order”
SAP_PS_STRUCT Maintenance of assignment objects of type “project”
SAP_BC_ENDUSER Non-critical basis authorizations for all users
In addition, users must be assigned to:
● the authorization prole K_ORDER for the maintenance of assignment objects of the type “internal order”
● the authorization prole I_PM_ALL for the maintenance of assignment objects of the type “service order”.
Note
As the authorization proles K_ORDER and I_PM_ALL comprise all available authorizations for internal
orders and service orders respectively, we recommend that you narrow the granted authorization range to
suit your specic requirements.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used by Commercial Project
Inception and Lean Stang.
Standard Authorization Objects
Authorization Object Field Value Description
P_ORGIN and P_PERNR (Au
thorization check for HR info
types)
INFTY
SUBTY
AUTHC
0002
<blank>
R
The employee search in the
Lean Stang application and
in the Lean Stang reporting
lists only employees for
whose info type 0002 the
user has a read authoriza
tion.
538 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
PRS_LS_CUS (new) ACTVT 02, 03, 06 The system checks this au
thorization object when sta
assignments to customers
are made.
V_PRS_LS_H (new) VKORG
VTWEG
SPART
KDGRP
KOSTL
ACTVT
VBAK-VKORG
VBAK-VTWEG
VBAK-SPART
KNVV-KDGRP
VBAK-KOSTL
02, 03, 06
The system checks this au
thorization object when sta
assignments to SD orders
are made. The user must be
authorized for the sales area,
distribution channel, division,
customer group and cost
center of the SD order.
V_PRS_LS_I (new) PRCTR
ACTVT
VBAP-PRCTR
02, 03, 06
The system checks this au
thorization object when sta
assignments to SD orders
are made. The user must be
authorized for the prot cen
ter of the SD sales document
item.
C_PRPS_LS (new) PS_FKOKR
PS_FKSTL
PRCTR
ACTVT
PRPS-FKOKR
PRPS-FKSTL
PRPS-PRCTR
02, 03, 06
The system checks this au
thorization object when sta
assignments to WBS ele
ments are made. The user
must be authorized for the
controlling area, cost center
and prot center of the WBS
element.
K_PRS_LS PRCTR
ACTVT
AUFK-PRCTR
02, 03, 06
The system checks this au
thorization object when sta
assignments to internal or
service orders are made. The
user must be authorized for
the prot center of the order.
PRS_LS_FC EMP_LEVEL
ACTVT
Level 1, 2 or 3
02, 03, 06
See description below.
The authorization for sta assignments is based on the assignment object to which it refers; it is independent
of the employee for whom the assignment is made. As shown in the table above, dierent types of assignment
objects (SD order, project and so on) use dierent elds for this authorization.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 539
The authorization for forecasting is based on the employee whose time is forecast; it is independent of the
assignment object for which it is made. There are several levels ( EMP_LEVEL) of authorization concerning the
employee:
● Level 1: The user is authorized to change and display own forecasts (the forecasts for the employee ID
contained in the user’s master record).
● Level 2: The user is authorized to change and display forecasts for the members of his or her team (note
that level 2 does not necessarily imply level 1). The team is determined on the basis of the employee ID
contained in the user’s master record, as follows:
● The HCM organizational model is queried (current relationships according to info type 1001, subtype
A008; for details, see method CL_SAWE_API_PROVIDER_FC-> GET_TEAM_OF_EMP). The result of this
query is the same for managers and their assistants.
● You can inuence the list of employee IDs returned by this query by adding or removing entries in an
implementation of the Business Add-In (BadI) SAWE_AUTHORITY_CHECK, method
TEAM_OF_EMPLOYEE.
● If neither the HCM organizational model nor the BAdI implementation is used, the team does not contain
any employees.
● Level 3: The user is authorized to change and display forecasts for all employees.
The system checks both authorizations (authorization for sta assignments and authorization for forecasting)
in the following cases:
● ACTVT = ‘02’ (change): Checked when the Lean Stang or Forecasting application is executed in the
change mode (this refers to the UI-based application and to the A2X Enterprise Services).
● ACTVT = ‘03’ (display): Checked when the Lean Stang or Forecasting application is executed in the
display-only mode.
● ACTVT = ‘06’ (delete): Checked when the deletion of an assignment object triggers the deletion of its sta
assignments and forecasts (without further user interaction).
This is dierent from the deletion of individual entries in the Lean Stang and Forecasting applications,
because users who are authorized to delete assignment objects (for example, SD order items) may need this
authorization, even if they do not have authorization to execute the Lean Stang or Forecasting application.
The authorizations for reporting are based on the specic user group ‘SAWE’, which you can maintain using
transaction SQ03. Users who are authorized to analyze employee assignments, resource consumption,
employee utilization and skill utilization need to be assigned to this user group.
13.14.5.5 Data Storage Security
Use
Commercial Project Inception and Lean Stang stores additional employee-related data besides data stored in
the HR Master Data database.
The following additional data can be stored in the respective objects (technical table names in parentheses):
• Employee assignment to projects, customer orders, or internal orders (SAWE_D_SA_HDR and
SAWE_D_SA_ITM).
• Employee forecast for the above-mentioned assignments, and also for generic assignments such as training
(SAWE_D_TIME_PS and SAWE_D_TIME_PSI).
540
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
For more information, see the product assistance for SAP S/4HANA on the SAP Help Portal at http://
help.sap.com/s4hana_op_1709 under Product Assistance Enterprise Business Applications Industries
SAP for Professional Services Lean Stang Data Archiving in Lean Stang
13.14.5.6 Deletion of Personal Data
Use
The Lean Stang (IS-PRS-LS) component might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
Lean Stang (IS-PRS-LS) For more information, see the product
assistance for SAP S/4HANA on the
SAP Help Portal at http://
help.sap.com/s4hana_op_1709 under
Product Assistance Enterprise
Business Applications Industries
SAP for Professional Services Lean
Stang Data Archiving in Lean
Stang
Archiving object SAWE_SA
ILM object SAWE_SA
Report
SAWE_SA_CLEAN_CANDIDATE_LIST
Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Lean Stang (IS-PRS-LS)
End of Purpose (EoP) check
Class registered for the EoP check:
CL_WUC_IS_PRS_LS_EOP_CHECK
For more information, see SAP note
2390575 .
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 541

Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of customer and vendor master data in
Customizing for
Logistics - General under Business Partner Deletion of Customer and Vendor Master
Data .
13.14.6 Public Sector
13.14.6.1 Finance
13.14.6.1.1 Public Sector Management
Data Storage
Using Logical Paths and File Names to Protect Access to the File System
Public Sector Management stores data in les in the le system. For this reason, it is important to be able to
grant access to the les in the le system explicitly without granting access to other folders or les (also known
as folder traversals). You do this in the system by entering logical paths and le names that are assigned to the
physical paths and le names. This assignment is validated during runtime, whereby an error message is
issued whenever a user tries to access a folder that does not correspond to a stored assignment.
The following lists provide an overview of the logical le names and paths that are used by Public Sector
Management and of the programs for which these le names and paths are valid:
Logical File Names Used in Public Sector Management
The logical le name PSM_EXECUTION_DATA_EXPORT has been created to enable the validation of physical
le names.
The program RFEXBLK0 uses this logical le name.
Logical Path Names Used in Public Sector Management
The above-mentioned logical le name uses the logical le path PSM_ROOT.
Activating the Validation of Logical Paths and File Names
These logical paths and le names are entered in the system for the corresponding programs. For reasons of
downward compatibility, validation is deactivated by default during runtime. To activate validation during
542
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
runtime, dene the physical path using transactions FILE (across all clients) and SF01 (client-specic). To
determine which paths are used by your system, you can activate the relevant settings in the Security Audit
Log.
13.14.6.1.1.1 Funds Management
Standard roles for Funds Management (PSM-FM)
Role Name
SAP_IS_PS_CENTRAL_FUNCTION Funds Management Central Function
SAP_IS_PS_PO_CONSUMPTION Postings: Consume Funds
SAP_IS_PS_MD_STRUCTURE Master Data Funds Management: Maintain Structure
SAP_IS_PS_BCS_AVC_TOOLS Availability Control - Tools
SAP_IS_PS_BCS_BUD_TOOLS Budgeting - Tools
SAP_IS_PS_PO_RECONCILE Reconciling Data with Feeder Applications
SAP_IS_PS_BCS_BUD_MAINTENANCE Maintain Budget Data
SAP_IS_PS_BCS_BUD_PLANNING Plan Budget Data
SAP_IS_PS_BCS_DISPLAY Display Budget Values (BCS)
SAP_IS_PS_BCS_STATUS_MAINTAIN Budgeting – Assign Status
SAP_IS_PS_BCS_STRUCT_DEF Maintain Budget Structure
SAP_IS_PS_BCS_STRUCT_TOOLS Budget Structure - Tools
SAP_IS_PS_CASH_DESK Payment at Cash Desk
SAP_IS_PS_CF_CHECK Check Budget Closing
SAP_IS_PS_CF_OI_EXECUTE Carry Forward Consumable Budget
SAP_IS_PS_CF_OI_PREPARE Prepare Carryforward of Consumable Budget
SAP_IS_PS_MD_DISPLAY Funds Management Master Data: Display Functions
SAP_IS_PS_MD_ZUOB Funds Management Master Data: Assignment to CO Struc
tures
SAP_IS_PS_PO_COMMITMENTS Postings: Commit Funds
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 543

Role Name
SAP_IS_PS_PO_CONSUMPTION_DISP Postings: Consumed Funds Display
SAP_IS_PS_PO_FOR Postings: Forecast of Revenue
SAP_IS_PS_PO_TRANSFERS Postings: Transfer Consumable Budget
SAP_FI_GL_REORG_MANAGER Reorganization Manager
SAP_FI_GL_REORG_OBJLIST_OWNER Object List Owner
Authorization objects for Funds Management (PSM-FM)
Authorization Object Name
F_FICB_FKR Cash Budget Management/Funds Management FM Area
F_FICB_VER Cash Budget Management/Funds Management Version
F_FICA_FOG Funds Management: Authorization Group of Fund
F_FICA_FSG Funds Management: Authorization Group for Funds Center
F_FICA_SEG Funds Management: Authorization Group for All Funds Cen
ters
F_FICA_SIG Funds Management: Authorization Group Internal Funds
Centers
F_FICA_FPG Funds Management: Authorization Group for Commitment
Item
F_FICA_TRG Funds Management: Authorization Groups of FM Acct As
signment
F_FMMD_FAR Funds Management: Functional Area (Authorization Group)
F_FMMD_MES Funds Management: Funded Program (Authorization Group)
F_FMMD_BPG F_FMMD_BPG
F_FMMD_FPG Funds Management: Funded Program Sets
F_FICA_FNG Funds Management: Fund Groups
F_FICA_FAG Funds Management: Function Groups
544 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Name
F_FICA_CIG Funds Management: Commitment Item Group
F_FICA_FCG Funds Management: Funds Center Groups
F_FMCA_SHE Clarication Worklist (FMSHERLOCK)
See also the documentation for Funds Management on the SAP Help Portal at help.sap.com S/4 HANA
Accounting Public Sector Management Funds Management Authorizations .
Authorization objects of the Budget Control System (BCS)
Authorization Object Name
F_FMBU_ACC Budgeting: Account Assignment
F_FMBU_STA Budgeting: Status
F_FMBU_KYF Budgeting: Key Figure
F_FMBU_DOC Budgeting: Document Type
F_FMBU_VER Budgeting: Version and Budget Category
You can use the following BAdI to implement enhancements to the authorization concept:
BAdI Name
FM_AUTHORITY_CHECK Enhance Authorization Check in PSM-FM
13.14.6.1.1.2 Grants Management
Standard roles for Grants Management (PSM-GM)
Function Name Function
SAP_FI_GM_GRANT_ANALYST
Grants Management: Grant Analyst M aster data maintenance, execution of
reports
SAP_FI_GM_GRANT_MANAGER
Grants Management: Grant Manager New entry, check, and approval of mas
ter data, execution of billing program
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 545

Function Name Function
SAP_FI_GM_PROGRAM_ANALYST
Grants Management: Program Analyst Creation of master data, processing of
proposals and budget
SAP_FI_GM_PROGRAM_MANAGER
Grants Management: Program Manager Check and approval of proposals and
budget
SAP_FI_GM_PROJECT_MANAGER
Grants Management: Project Manager Management of grants and budget, exe
cution of reports
Authorization Objects for Grants Management (PSM-GM)
Authorization Object Name
F_FIGM_BUD
Grants Management: Authority for Budget
F_FIGM_CLS
Grants Management: Authority for Class
F_FIGM_GNG
GM: Grant Groups
F_FIGM_GNT
Grants Management: Authority for Grant
F_FIGM_PRG
Grants Management: Authority for Programs
F_FIGM_SCG
GM: Sponsored Class Groups
F_FIGM_SPG
GM: Sponsored Program Groups
The master data objects and business processes of Grants Management are protected by standard
authorization objects.
US Federal Government uses the authorization concepts of the components that it deploys, such as Funds
Management and Material Management. See also the documentation for Funds Management on http://
help.sap.com/s4hana_op_1709 under Product Assistance Enterprise Business Applications Finance
Public Sector Management Funds Management Authorizations .
You can use the following BAdI to implement enhancements to the authorization concept:
BAdI Name
GM_AUTHORITY_CHECK
Grants Management: Authorization Check
GM_BILL_AUTHORITY
GM: User Authorization for DP90 in GM
GM_POST_AUTHORITY
Grants Management Coding Block Authority Check
546 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.14.6.1.1.3 Network and Communication Security
Public Sector Management communicates with:
● Human Capital Management (HCM) as part of the scenario Position Budgeting and Control
● Customer Relationship Management (CRM) as part of the scenario Grantor Management
The communication with these internal SAP components takes place per Remote Function Call (RFC). See the
corresponding sections in the RFC/ICF Security Guide.
The US Federal Government has both payment and collection outbound interfaces at its disposal for Treasury
Conrmation and Intragovernment Payment and Collections (IPAC). This outbound interface uses payment
methods and at les.
The inbound interface of the Central Contractor Registration (CCR) uses IDocs.
For registering portal users in the backend system, we recommend that the user is assigned in both the portal
and the backend system. In other words, the user ID of a user in the portal and the backend system should
match.
13.14.6.1.1.4 More Security Information
Authorization checks only take place in Public Sector Management and Funds Management when the
authorization group of a master data object is entered. To ensure that an adequate check is carried out, SAP
recommends that you dene the aected elds as required entry elds in the eld status control. You dene
this setting in Customizing for Public Sector Management:
● Funds ManagementSpecic Postings Earmarked Funds and Funds Transfers Field Control for
Earmarked Funds and Funds Transfers
Dene Field Status Variant / Assign Field Status Variant to
Company Code / Dene Field Status Groups
● Actual and Commitment Update/Integration Integration Maintain Field Status for Assigning FM
Account Assignments
For more information, see the documentation on Funds Management on SAP Help Portal at help.sap.com
ERP Central Component Accounting Public Sector Management .
For Grants Management, note the following system settings in Customizing for Public Sector Management
under Funds Management Government Master Data Grant :
● GM Grant Control:Field Group for Authorizations
● Maintain Grant Authorization Types
● Maintain Grant Authorization Groups
13.14.6.2 Public Sector Collection and Disbursement
The following security chapter of SAP Public Sector Collection and Disbursement (PSCD) also applies security
information for SAP Tax and Revenue Management (TRM).
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 547
13.14.6.2.1 Authorizations
SAP Public Sector Collection and Disbursement (SAP PSCD) and SAP Tax and Revenue Management (SAP
TRM) uses the authorization concept provided by the SAP NetWeaver AS for ABAP or AS Java. Therefore, the
recommendations and guidelines for authorizations as described in the SAP NetWeaver AS Security Guide
ABAP and SAP NetWeaver AS Security Guide Java also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP and the User Management
Engine’s user administration console on the AS Java.
Note
For more information about how to create roles, see the SAP NetWeaver Security Guide under User
Administration and Authentication.
Standard Roles
The table below shows the standard roles that are used.
Role Description
SAP _FMCA_CA_ ALL Sample role including all transactions for SAP PSCD
SAP _FMCA_CA_ ALL _EHP5_TRM_NWBC Sample role for the SAP NetWeaver Business Client (NWBC)
for SAP TRM
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used for SAP PSCD.
Authorization Object Field Value Description
F_PSDO_BEG BEGRU 01 Document Generation
02 Document Changes
03 Document Display
85 Reversal of Documents
and Resetting of a Clearing
PSCD Document: Authoriza
tion Group for Contract Object
548 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
F_PSDO_VGT PSOBTYP_PS 01 Document Generation
02 Document Changes
03 Document Display
85 Reversal of Documents
and Resetting of a Clearing
PSCD Document: Contract
Object Type Authorization
F_PSOB_ATT AUTHTYP_PS 01 Create
02 Change
03 Display
* All Activities
PSCD Contract Object: Au
thorization Types
F_PSOB_BEG BEGRU 01 Create or Generate
02 Change
03 Display
06 Delete
08 Display Change Docu
ments
PSCD Contract Object: Au
thorization Group
F_PSOB_FDG FLDGR_PS 01 Create or Generate
02 Change
03 Display
PSCD Contract Object: Field
Groups
F_PSOB_VGT PSOBTYP_PS 01 Create or Generate
02 Change
03 Display
06 Delete
08 Display Change Docu
ments
64 Generate
PSCD Contract Object: Object
Type Authorization
F_FMCA_WOF ABGRD 10 Post
B5 Display History
F1 Approve
PSCD Write O: Approval for
Write-O Reason
F_FMCA_WOM ACTVT For more information, see
transaction SU21.
PSCD Write-O: Authorization
for Mass Approval
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 549

Authorization Object Field Value Description
F_PSFA_SET F_PSFA_SET 01 Create or Generate
02 Change
03 Display
06 Delete
PSCD Facts: Authorization for
Fact Sets
F_PSFA_TYP F_PSFA_TYP 01 Create or Generate
02 Change
03 Display
06 Delete
PSCD Facts: Autorization for
Fact Set Parts
F_PSFA_CAT BEGRU 01 Create or Generate
02 Change
03 Display
06 Delete
PSCD Facts: Authorization for
Fact Type Parts
F_FMCA_IPM F_FMCA_IPM F1 Approve PSCD Installment Plan: Au
thorization for Mass Approval
F_KKCOL ACTVT 01 Create or Generate
02 Change
03 Display
06 Delete
16 Execute
39 Check
AF Prompts
PSCD Co-Liability: Authoriza
tion for Co-Liabilities
The following authorization objects are only relevant for customers who use SAP Tax and Revenue
Management (TRM) for Public Sector that is based on SAP Public Sector Collection and Disbursement (PSCD).
Authorization Object Field Value Description
F_PSFH_FVW FMCA_PHASE 01 Create or Generate
02 Change
03 Display
06 Delete
F1 Approve
TRM Object: Authorization for
Form Handling and Form View
550 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Authorization Object Field Value Description
F_PSFH_ REV FMCA_ABTYP 01 Create or Generate
02 Change
03 Display
06 Delete
F1 Approve
TRM Object: Authorization for
Form Handling and Revenue
Type
F_PSFH_ACT ACTVT 01 Create
02 Change
03 Read
TRM Object: Authorization for
Form Handling
F_PSFH_FBT FBTYP 01 Create or Generate
02 Change
03 Display
06 Delete
F1 Approve
TRM Object: Authorization for
Form Handling and Form Bun
dle Type
F_PSFH_STA FMCA_FBSTA 01 Create or Generate
02 Change
03 Display
06 Delete
F1 Approve
TRM Object: Authorization for
From Handling and Status
F_PSFH_ AMD AMD_ACTION 16 Execute TRM Object: Authorization for
Amendment Actions in the
Tax Ocer Work Center
F_FMCA_RLT COREL_TYPE 01 Create or Generate
02 Change
03 Display
06 Delete
TRM Object: Authorization for
Master Data Relationship Cat
egory
13.14.6.2.2 Data Storage Security
Using Logical Path and File Names to Protect Access to the File System
The Industry Solution Migration Workbench (ISMW) saves data in les in the le system. Therefore, it is
important to explicitly provide access to the corresponding les in the le system without allowing access to
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 551
other directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
Logical File Names / Path Names Used
The Migration Workbench uses the logical le name ISMW_FILE with the logical le path ISMW_ROOT to enable
the validation of physical le names.
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out
which paths are being used by your system, you can activate the corresponding settings in the Security Audit
Log.
For more information, see about data storage security, see the respective chapter in the SAP NetWeaver
Security Guide.
13.14.6.3 Multichannel Foundation for Utilities and Public
Sector (Public Sector)
13.14.6.3.1 Internet Communication Framework Security
(ICF)
You should only activate the services that are required by the applications running in your system.
The following services must be activated for Multichannel Foundation for Utilities and Public Sector:
● ERP_FMCA_MC (logon user/current user)
● ERP_FMCA_MC_PUBLIC_SRV
ERP_FMCA_MC_PUBLIC_SRV is to be used for the anonymous payment or anonymous form submission
scenario and needs to be linked to a predened
“SU01” user.
Use transaction SICF to activate these services. If your rewalls use URL ltering, also note the URLs used for
the services and adjust your rewall settings accordingly.
For more information about ICF security, see the relevant chapter in the SAP NetWeaver Security Guide.
552
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.14.7 Retail
13.14.7.1 Network and Communication Security
The following information is relevant for specic SAP S/4HANA Retail solutions. For general information about
network and communication security in SAP S/4HANA, see Network and Communication Security [page 18].
Communication Paths for SAP Forecasting and Replenishment
For information about the security of communication paths for integration with SAP Forecasting and
Replenishment, see the Security Guide for SAP Forecasting and Replenishment.
Other Communication Paths for SAP S/4HANA Retail
The following table shows the communication paths for all remaining system connections for SAP S/4HANA
Retail solutions.
Communication Paths for SAP S/4HANA Retail
Application Communication Path Protocol Used
Type of Data Transfer
red
Data Requiring Spe
cial Protection
Store physical inven
tory
SAP S/4HANA – store
system
RFC (or other protocol
that supports IDocs)
Application data -
POS interface SAP S/4HANA – POS
system
RFC (or other protocol
that supports IDocs)
Application data Credit card informa
tion
Interface to space
management systems
SAP S/4HANA – space
optimization system
RFC Application data -
13.14.7.2 Authorizations in Retail
Note
For general information about the authorization concept used by SAP S/4HANA, see User Administration
and Authentication [page 13].
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 553
SAP S/4HANA Retail uses the authorization concept provided by the SAP NetWeaver AS ABAP or AS Java.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver AS
Security Guide ABAP and SAP NetWeaver AS Security Guide Java also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP and the User Management
Engine’s user administration console on the AS Java.
Standard Roles
The following table shows the standard roles that are used for SAP S/4HANA Retail for merchandise
management and in SAP S/4HANA for fashion and vertical business solutions.
Role Description
SAP_BR_ADMINISTRATOR_RFM
Administrator (Retail)
SAP_BR_ALLOCATOR_RETAIL
Allocator (Retail)
SAP_BR_ASSORT_SPECIALIST_RFM
Assortment Specialist - Retail
SAP_BR_CAT_MAN_RFM
Category Manager (Retail)
SAP_BR_DEMAND_PLANNER_RFM
Demand Planner (Retail)
SAP_BR_MD_SPECIALIST_ITEM_RFM
Master Data Specialist - Product Data (Retail)
SAP_BR_MD_SPECIALIST_SITE_RFM
Master Data Specialist - Location Data (Retail)
SAP_BR_PRICING_SPECIALIST_RFM
Pricing Specialist (Retail)
SAP_BR_PROMOTION_SPEC_RFM
Promotion Specialist (Retail)
SAP_BR_PURCHASER_RFM
Purchaser (Retail)
SAP_BR_RETAIL_STORE_ASSOCIATE
Retail Store Associate
SAP_BR_RETAIL_STORE_MANAGER
Retail Store Manager
SAP_BR_STORE_DESIGN_MGN_RFM
Store Design Manager (Retail)
The following table shows the standard roles that are used for specic SAP S/4HANA for fashion and vertical
business solutions.
Role Description
SAP_BR_INTERNAL_SALES_REP_RET
Internal Sales Representative (Retail)
SAP_BR_ORDER_FULFILLMNT_MNGR_R
Order Fulllment Manager (Retail)
554 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Standard Authorization Objects
The following table shows the standard authorization objects that are used in SAP S/4HANA Retail and SAP S/
4HANA for fashion and vertical business solutions.
Authorization Object Description
W_ASORT
Authorization for assortment maintenance
W_ASORT_ST
Authorization for assigning assortments to plants
W_AUFT_BAA
Authorization for allocation table type
W_AUFT_BAR
Authorization for allocation rule type
W_AUFT_RMB
Authorization for allocation table: Display/Reply per plant
W_FRM
Authorization for merchandise distribution
W_GROUPTYP
Authorization for managing site groupings
W_LISTVERF
Authorization to use listing procedure
W_LIST_EAC
Authorization to ignore listing errors
W_MARKDOWN
Authorization for markdown planning: MTYP, MATCL, SOrg,
DChl
W_PRICATIN
Authorization for creating and maintaining PRICAT per pur
chasing group
W_REF_SITE
Authorization to clean MMSITEREF table
W_SRS_POS
SAP Retail Store authorization for physical inventory in open
store
W_SRS_VKPF
SAP Retail Store authorization for daily price maintenance
W_STRU_CHG
Authorization to allow changes to structured materials
W_STWB_WRK
SAP Retail Store authorization for store
W_VKPR_PLT
Authorization for sales price calculation: Distribution chan
nel/price list
W_VKPR_VKO
Authorization for sales price calculation: Distribution chan
nel
W_VKPR_VTL
Authorization for sales price calculation: Organizational level
distribution channel and various material groups
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 555
Authorization Object Description
W_VKPR_WRK
Authorization for sales price calculation: Distribution chan
nel/plant
W_WAKH_EKO
Authorization for promotions: Purchasing organization/
purchasing group
W_WAKH_MAT
Authorization for promotions: Material number
W_WAKH_THE
Authorization for promotions: Theme
W_WAKH_VKO
Authorization for promotions: Sales organization/distribu
tion channel
W_WBEF_WRK
Authorization for sales price revaluation: Distribution chan
nel/plant
W_WIND_TYP
Automatic journal entry adjustment: Authorization for jour
nal entry type
W_WTAD_AM
Authorization for additionals monitor
W_WTAD_ASL
Authorization for additionals: Supplier/purchase order list
W_WTAD_IR
Request additionals IDoc via BAPI call function
W_WTAD_ISU
Authorization for status update for additionals IDoc
WLM
Assignment of articles for layout modules
WLMLOCLIST
Creation of assortments per layout module and store
WLMVREL
Release of layout module version
WLMVV
Layout module version variants maintenance
WLWBENT
Access to layout workbench
WPLGACT
Call external space management
WRF_CDT_H
Article hierarchy: Horizontal hierarchy maintenance
WRF_CDT_V
Article hierarchy: Vertical hierarchy and attribute mainte
nance
WRF_FOLUP
Authorization: Follow-up/Replacement material relation
ships
WRF_GH_AUT
Generic hierarchy: Authorization check
W_BUDG_TY
Budget type
556 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Authorization Object Description
W_RF_MPA
Authorization for markdown prole assignment
W_RF_WLAY
Authorization for layout
C_WRFCHVAL
Authorization for characteristic value maintenance
Additional Standard Authorization Objects for Fashion and Vertical Business
The following table shows the standard authorization objects that are used for specic SAP S/4HANA for
fashion and vertical business solutions.
Authorization Object Description
ARUN_WB
Authorization for the order allocation run (ARun) workbench
ARUN_LOG
Authorization for message logging during the order alloca
tion run
This authorization is required to perform the order allocation
run in online, batch, and parallel modes.
ARUN_ON
Authorization for performing the order allocation run in on
line mode
FSH_ATTRB
Authorization for the maintenance of article attributes in
fashion and vertical business (information)
ARUN_CCR
Authorization for the consistency check report
C_SGTSETUP
Authorization for segmentation setup
C_SGT_DEFT
Authorization for default segmentation maintenance
SWB_DISPLA
Authorization for Season Workbench
SWB_TREE
Authorization to create/edit/delete the tree view in Season
Workbench
SWB_PUR_V
Authorization to create/edit/delete the purchasing view in
Season Workbench
SWB_SALE_V
Authorization to create/edit/delete the sales view in Season
Workbench
FSH_SRL
Authorization for the stock/requirement list for fashion and
vertical business
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 557

Authorization Object Description
SWB_PROD_V
Authorization to create/edit/delete the production view in
Season Workbench
FSH_ITAARN
Authorization for the Insight to Action report
FSH_COD
Authorization to create/edit/delete cut-o dates
FSH_DPR
Authorization to create/generate/change distribution curve
FSH_QDP
Authorization to create/generate/change quantity distribu
tion prole
FSH_MRK
Authorization to create/change/display marker information
RFM_PSST
Authorization for PSST: Grouping rules and groups
13.14.7.3 Deletion of Personal Data in Retail
SAP S/4HANA Retail solutions might process data (personal data) that is subject to the data protection laws
applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
SAP Help Portal at https://help.sap.com/viewer/product/SAP_S4HANA_ON-PREMISE/. Choose a version and
then go to
Product Assistance Cross Components Data Protection .
Relevant Application Objects (Data) and Available Deletion Functionality
Application Application Objects Provided Deletion Functionality
Allocation Application-specic data used in the
following transactions:
WA01
WA02
WA03
WA04
WA08
WA30
WA35
Transaction WA09
558 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Application Objects Provided Deletion Functionality
Alternate Historical Data Application-specic data used in the
following transactions:
MDRD1 - MDRD3
MAHD1 - MAHD3
Transaction MAHD4 can be used to de
lete entries in the Alternate Historical
Data tables.
Transaction MDRD4 can be used to de
lete delivery relationships.
Article Discontinuation Application-specic data used in the
following transactions:
WRF_DIS_SEL
WRF_DIS_MON
ILM object MM_MATNR
Assortment Application-specic data used in the
following transactions:
WSOA1
WSOA2
WSOA3
WSO1
WSO2
WSO3
WSO4
WSO5
Tables:
WRSZ
WLK1
WSOH
Transaction WSOA4 can be used to de
lete assortments.
Transactions WSOA2/WSOA6 can be
used to delete assortment users (cus
tomers).
Assortment List Application-specic data used in the
following transactions:
WDBM_HPR
WJB5
WBBS
WBBS_ALV
Assortment List Reorganization: report
RWDPOSRS
Automatic Document Adjustment Transactions MEI1 - MEI5 ILM object MM_EKKO
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 559

Application Application Objects Provided Deletion Functionality
Investment Buying Application-specic data used in the
following transactions:
WLB1
WLB2
WLB6
Report RWFWW_DELETE_CUSTOMERS
Load Building Application-specic data used in the
following transactions:
WLB4
WLB5
WLB7
WLBA
WLBB
WLB13
Report RWVLB_DELETE_LOGTABLES
Merchandise Distribution Application-specic data used in the
following transactions:
WF10
WF10A
WF20
WF30
WF60
WF70
Transaction WA40 can be used to de
lete
FRET entries that have status
Completed.
Planning Workbench Transaction WWP1 For non-application-specic data, func
tionality is provided by other relevant
applications.
POS Interface – Inbound For non-application-specic data, func
tionality is provided by other relevant
applications.
POS Interface – Monitor Deletion reports RWPUDTST and
RWPUDLST
POS Interface – Outbound For non-application-specic data, func
tionality is provided by other relevant
applications.
560 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Application Objects Provided Deletion Functionality
Price Catalog Processing – Inbound
W_PRICAT_MAINTAIN
W_SYNC
Reports:
W_PRICAT_DELETE (Delete Inbound
Price Catalogs
)
W_PRICAT_DELPOS (Delete PRICAT
Items)
Price Planning Workbench Reports for the deletion of budgets and
price plans:
RWRF_PPW_BUDG_DELETE
RWRF_PPW_PPD_DELETE
RWRF_PPW_PPD_DELETE_DIRECT
Destruction object:
RWRF_PPW_PPD_DESTRUCTION
Promotions Table WALE
Transaction WAK5
ILM objects:
W_PROMO_AD
W_MARKDOWN
Replenishment Application-specic data used in the
following transactions:
WRMO
WR60
ILM object MM_MATNR
Sales Price Calculation Application-specic data used in the
following transactions:
VKP1-VKP8
VKPB
ILM object W_KALK
Site Master Transactions WB01-WB03 ILM object WS_ACSITE
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 561

Application Application Objects Provided Deletion Functionality
Subsequent Settlement Application-specic data used in the
following transactions:
MEB2
MEB3
MEB5
MEB6
MEB8
MEB9
MEBS
MEBB
MEBV
MEB7
MEU3
ILM object SD_AGREEM
Tickets and Additionals Application-specic data used in the
following transactions:
WTAM
WTR1
ILM object WTADDI
Vendor Managed Inventory Application-specic data used in the
following transactions:
WVM1
WVM2
WVM3
WVM4
Report RWVMI_DELETE_EDMMS
Relevant Application Objects and Available Deletion Functionality Provided
by Other Applications Used by SAP S/4HANA Retail solutions
● Sales
For information, see Deletion of Personal Data in Sales [page 409].
● Sourcing and Procurement
For information, see Deletion of Personal Data [page 427].
● Customer and supplier master data
For information, see Deletion of Personal Data [page 487].
562
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Areas and Available EoP/WUC Functionality
Application Solution Implemented for Applica
tion-Specic Data
Further Information
Allocation End of purpose (EoP) check
CL_ALLOCATION_CV_EOP_CHECK
CVP_IF_APPL_EOP_CHECK~CHECK_PA
RTNERS
Alternate Historical Data not applicable Tables do not contain any customer or
supplier data.
Article Discontinuation not applicable For non-application-specic data, func
tionality is provided by Sourcing and
Procurement.
Assortment not applicable An end of purpose (EoP) check is not
provided because customer and sup
plier numbers used in the tables do not
indicate any business relationships.
Assortment List not applicable An end of purpose (EoP) check is not
provided because supplier numbers
used in the tables do not indicate any
business relationships.
Automatic Document Adjustment not applicable For non-application-specic data, func
tionality is provided by Sourcing and
Procurement.
Investment Buying not applicable For non-application-specic data, func
tionality is provided by Sales.
Load Building not applicable For non-application-specic data, func
tionality is provided by Sales.
Merchandise Distribution End of purpose (EoP) check
CL_ALLOCATION_CV_EOP_CHECK
CVP_IF_APPL_EOP_CHECK~CHECK_PA
RTNERS
Planning Workbench not applicable For non-application-specic data, func
tionality is provided by Sales.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 563

Application Solution Implemented for Applica
tion-Specic Data
Further Information
POS Interface – Inbound not applicable POS interface uses documents that al
ready exist in other SAP applications.
These documents can be archived us
ing the relevant archiving objects and
deleted using the solutions (and end of
purpose (EoP) checks) provided by the
other SAP applications.
An end of purpose (EoP) check for Cus
tomizing is not provided because part
ner information is stored anonymously
in Customizing tables.
POS Interface – Monitor not applicable POS interface uses documents that al
ready exist in other SAP applications.
These documents can be archived us
ing the relevant archiving objects and
deleted using the solutions (and end of
purpose (EoP) checks) provided by the
other SAP applications.
POS Interface – Outbound not applicable POS interface uses documents that al
ready exist in other SAP applications.
These documents can be archived us
ing the relevant archiving objects and
deleted using the solutions (and end of
purpose (EoP) checks) provided by the
other SAP applications.
An end of purpose (EoP) check for log
tables is not provided because partner
information is not shown in the applica
tion at this time, a deletion report ex
ists, and there is no business need to
archive the log status of data prepara
tion.
Price Catalog Processing – Inbound End of purpose (EoP) check
CL_PRICAT_EOP_CHECK_CV
CVP_IF_APPL_EOP_CHECK~CHECK_PA
RTNERS
Price Planning Workbench not applicable An end of purpose (EoP) check is not
provided because supplier numbers in
pricing documents represent supply
source information but do not indicate
any business relationship to the sup
plier.
564 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Application Solution Implemented for Applica
tion-Specic Data
Further Information
Promotions End of purpose (EoP) check
CL_PROMOTION_CV_EOP_CHECK
CVP_IF_APPL_EOP_CHECK~CHECK_PA
RTNERS
Replenishment not applicable For non-application-specic data, func
tionality is provided by Sourcing and
Procurement.
Sales Price Calculation not applicable An end of purpose (EoP) check is not
provided because supplier numbers in
pricing documents represent supply
source information but do not indicate
any business relationship to the sup
plier.
Site Master Where-used check (WUC)
CL_T001W_WUC
Subsequent Settlement End of purpose (EoP) check
CVP_SD_EOP_CHECK_MM_REBATE
Tickets and Additionals not applicable For non-application-specic data, func
tionality is provided by Sourcing and
Procurement.
Vendor Managed Inventory not applicable For non-application-specic data, func
tionality is provided by Sourcing and
Procurement.
Conguration: Simplied Blocking and Deletion
● You dene the settings or authorization management in Customizing for Cross-Application Components
under Data Protection Authorization Management .
For more information, see the Customizing documentation.
● You congure the settings the related to the blocking and deletion of customer and supplier master data in
Customizing for Logistics - General under Business Partner Deletion of Customer and Supplier Master
Data
.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 565
13.14.7.4 Deletion of Personal Data in Fashion and Vertical
Business
Use
SAP S/4HANA for fashion and vertical business fashion might process data (personal data) that is subject to
the data protection laws applicable in specic countries. You can use SAP Information Lifecycle Management
(ILM) to control the blocking and deletion of personal data. For more information, see the product assistance
for SAP S/4HANA on SAP Help Portal at https://help.sap.com/viewer/product/SAP_S4HANA_ON-PREMISE/.
Choose a version and then go to Product Assistance Cross Components Data Protection
For more information about the deletion of personal data that might be used in fashion and vertical business
applications refer to Deletion of Personal Data in Retail [page 558].
Relevant Application Areas and Available Deletion of Personal Data
Functionality
Application Implemented functionality
Stock requirements/Pegging (MD04P) Not applicable
Note
An End of Purpose (EoP) check is not provided be
cause customer and supplier information displayed do
not indicate any business relationships.
Season Workbench EoP check
Mass Repricing Report EoP check
Mass ATP Report EoP check
Season Redetermination Report for Sales Order EoP check
Season Redetermination Report for Purchase Order EoP check
Season Redetermination Report for Stock Transport Order EoP check
VAS Redetermination Report for Sales Order EoP check
VAS Redetermination Report for Purchase Order EoP check
566 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Application Implemented functionality
VAS Redetermination Report for Stock Transport Order EoP check
Multi Ship to Order (MSO) Explosion Report for Sales Order EoP check
Split and Change of Purchase Orders EoP check
Transportation Chain – Dateline Workbench Report EoP check
13.14.7.5 Payment Card Security According to PCI-DSS
Note
The Payment Card Industry Data Security Standard (PCI-DSS) was jointly developed by major credit card
companies in order to create a set of common industry security requirements for the protection of
cardholder data. Compliance with this standard is relevant for companies processing credit card data. For
more information, see the ocial website of the PCI Security Standards Council at https://
www.pcisecuritystandards.org .
This section of the security guide supports you in implementing payment card security aspects and outlines
steps that need to be considered to be compliant with the PCI-DSS.
Please note that the PCI-DSS covers more than the following steps and considerations. Complying with the
PCI-DSS lies completely within the customer’s responsibility, and we cannot guarantee the customer’s
compliance with the PCI-DSS.
For current information about PCI-DSS, see also SAP Note 1609917 .
PCI-relevant POS (Point-of-Sale) sales can be processed in SAP S/4HANA Retail for merchandise management
for nancial postings and inventory management. Depending on the conguration of the POS solution, the data
transferred to SAP S/4HANA Retail for merchandise management can contain credit card information that
needs to be handled according to the PCI Standard. In this case, the card data has to be encrypted during
inbound processing. The relevant asynchronous communication methods are the IDocs with the message type
WPUBON (Upload Sales Documents per Receipt), and message type WPUTAB (Upload End-of-Day Closing POS).
For more information about Archiving, RFC Debugging, Forward Error Handling (FEH) and Card Verication
Values (CVV)
, see Payment Card Security According to PCI-DSS [page 62].
Interfaces (IDoc/Services)
Note
Note that IDoc segments cannot store credit card numbers in clear text due to the PCI security standard
compliance. Once an IDoc is being processed within the IDoc Framework, all values are temporarily stored,
including the clear text credit card number.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 567
For more information about how to process customer-specic IDocs containing credit card information,
see the SAP NetWeaver Security Guide under Security Guides for Connectivity and Interoperability
Technologies Security Guide ALE (ALE Applications) Handling Sensitive Data in IDocs in SAP
NetWeaver Release 7.50.
Encryption/Decryption and Storage of the Encrypted Number
IDoc Encryption/Encryption process: IDoc data records are sent to the BAdI implementation
IDOC_PCI_ENCR_IM that is used for the PCI DSS inbound IDoc encryption. The process of encrypting the
credit card number starts by identifying the segment with credit card information in the IDoc record structure.
The data from the relevant segments E1WPZ02 and E1WPB06 is mapped to the internal record structure in
order to retrieve the card GUID, the name of the credit card institution number, and the credit card number.
After this, the security level of the credit card institution is veried in Customizing:
● If the security level is set to 2, the credit card number is encrypted.
● If the security level is set to 1, the credit card number is masked.
The card GUID and the encryption type are mapped to the structure for decryption and a message is displayed
that informs the user whether the encryption was successful. After this, the nal check for consistency is
performed.
Decryption process: The process of decrypting the credit card number starts by identifying the segment in the
IDoc record structure that contains the credit card information. The data from the relevant segments E1WPZ02
and E1WPB06 is mapped to the internal record structure in order to retrieve the card GUID, the type of
encryption, and the credit card number. The encryption type is set to the xed value 2. The credit card number
is decrypted and a message is displayed that informs the user whether the encryption was successful.
● The BAdI implementation name for PCI DSS inbound IDoc decryption is IDOC_PCI_DECRYPTION_IM.
● One of the IDoc database encryption/decryption (IDOC_DATA_MAPPER, IDOC_DATA_CRYPTION)is called
before saving to the IDoc database and the other after reading from it.
Customizing
Maintain the following settings in Customizing:
● The basic settings for payment cards: In Customizing for SAP Customizing Implementation Guide under
Cross-Application Components Payment Cards Basic Settings Assign Checking Rule .
● The settings for the encryption save mode: Dene whether existing GUIDs for credit cards are reused. The
default setting is set to reuse the existing GUID. You can adapt the default with a customer-specic BAdI
implementation, using the enhancement spot ES_WPOS_PCA_SECURITY and the BAdI denition
WPOS_PCA_SECURITY.
● The security settings for the credit card institute: In Customizing for SAP Customizing Implementation
Guide under Cross-Application Components Payment Cards Basic Settings Make Security Settings
for Payment Cards . For an example for security settings for payment cards, refer to the following entries:
○ Security Level:Masked Display and Encrypted When Saved
○ Access Log: Logging of unmasked display
○ Visible Characters for Masking:
At start: 4
At end: 4
● The settings for masking the credit card number: In the customizing table of the transaction
WECRYPTDISPLAY, maintain the settings for the Assignment of Encrypted Segment eld as follows:
568
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
○ Message Type: WPUBON
○ Segment Type: E1WPB06
○ Field Name: KARTENNR
and
○ Message Type: WPUTAB
○ Segment Type: E1WPZ02
○ Field Name: KARTENNR
13.14.8 Utilities
13.14.8.1 Data Storage Security
Using Logical Path and File Names to Protect Access to the File System
The Industry Solution Migration Workbench (ISMW) saves data in les in the le system. Therefore, it
is important to explicitly provide access to the corresponding les in the le system without allowing access to
other directories or les (also known as directory traversal). This is achieved by specifying logical paths and le
names in the system that map to the physical paths and le names. This mapping is validated at runtime and if
access is requested to a directory that does not match a stored mapping, then an error occurs.
Logical File Names / Path Names Used
The Migration Workbench (ISMW) uses the logical le name ISMW_FILE with the logical le path ISMW_ROOT
to enable the validation of physical le names.
Activating the Validation of Logical Path and File Names
These logical paths and le names are specied in the system for the corresponding programs. For downward
compatibility, the validation at runtime is deactivated by default. To activate the validation at runtime, maintain
the physical path using the transactions FILE (client-independent) and SF01 (client-specic). To nd out
which paths are being used by your system, you can activate the corresponding settings in the Security Audit
Log.
For more information, see about data storage security, see the respective chapter in the SAP NetWeaver
Security Guide.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 569

13.14.8.2 Enterprise Services Security
For general information, see the chapters on Web Services Security in the SAP NetWeaver Security Guide. For
Utilities-specic processes, during which system-to-system communication (A2A communication) takes place
within a system landscape and processes that prepare for market communication with other market
participants as part of intercompany data exchange, note the following:
Note
If, as part of your company-specic processes, you have communication interfaces with other systems, you
must also take their recommended security measures into account.
A2A Communication Within a System Landscape
During A2A communication, data is exchanged between an SAP system and an external system. This
communication is based on enterprise services and can ow via a PI system as a data hub or directly between
the respective systems (point-to-point). As identifying parameters, the SAP system uses internal values (such
as the prole number) or parameters that are generally understood in the market (such as external point of
delivery IDs). For information about the security measures relevant to A2A communication, see the
SAP
NetWeaver Security Guide. The authorization objects of the respective transactions provide these processes
with additional security.
Market Communication in Intercompany Data Exchange
As part of intercompany data exchange, messages are sent from an SAP Utilities system to a PI system or a
comparable upstream system to prepare for market communication with other market participants. The
messages are then converted into a universally valid market format and sent on to other systems. As
identifying parameters, the SAP system uses values that are generally understood in the market (such as
external point of delivery IDs). Communication can take place using enterprise services or IDocs (ALE
communication).
For more information about the necessary security measures, see the SAP NetWeaver Security Guide. The
authorization objects of the respective transactions provide these processes with additional security.
13.14.8.3 Deletion of Personal Data
SAP Utilities might process data that is subject to the data protection laws applicable in specic countries as
described in SAP Note 1825544 .
The SAP Information Lifecycle Management (ILM) component supports the entire software lifecycle including
the storage, retention, blocking, and deletion of data. SAP Utilities uses SAP ILM to support the deletion of
personal data. SAP delivers end of purpose checks for SAP Utilities-specic objects.
570
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

End of Purpose Check (EoP)
An end of purpose check determines whether data is still relevant for business activities based on the retention
period dened for the data. The retention period of data consists of the following phases.
● Phase one: The relevant data is actively used.
● Phase two: The relevant data is actively available in the system.
● Phase three: The relevant data needs to be retained for other reasons.
For example, processing of data is no longer required for the primary business purpose, but to comply with
legal rules for retention, the data must still be available. In phase three, the relevant data is blocked.
Blocking of data prevents the business users of SAP applications from displaying and using data that may
include personal data and is no longer relevant for business activities.
Blocking of data can impact system behavior in the following ways:
● Display: The system does not display blocked data.
● Change: It is not possible to change a business object that contains blocked data
● Create: It is not possible to create a business object that contains blocked data.
● Copy/Follow-Up: It is not possible to copy a business object or perform follow-up activities for a business
object that contains blocked data.
● Search: It is not possible to search for blocked data or to search for a business object using blocked data in
the search criteria.
It is possible to display blocked data if a user has special authorization; however, it is still not possible to create,
change, copy, or perform follow-up activities on blocked data.
For information about the conguration settings required to enable this three-phase based end of purpose
check, see Process Flow and Conguration: Simplied Blocking and Deletion.
Integration with Other Solutions
The end of purpose checks for SAP Utilities are based on those of the Contract Accounts Receivable and
Payable (FI-CA) solution. You use transaction FPDPR1 in the SAP menu under Contract Accounts Receivable
and Payable
Periodic Processing For Data Protection Check If Business Partner Can Be Blocked to
check for which business partners the end of purpose has been reached.
SAP Utilities is also integrated with SAP Sales and Distribution (SD) and SAP Customer Relationship
Management (CRM). Cross-system and cross-application end of purpose checks exist in both cases.
If, for example, a business partner is used in SAP Utilities (as part of SAP S/4HANA) and in SAP CRM, the end
of purpose checks cover both applications so that data for a blocked business partner cannot be accessed in
either application.
Relevant Application Objects and Available Deletion Functionality
SAP Utilities uses SAP ILM to support the deletion of personal data. For more information, see the
documentation for Information Lifecycle Management.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 571

Relevant Application Objects and Available EoP Functionality
The following end of purpose checks exist:
● Check for open contracts without any open items in their contract account
● Check if all invoicing documents have been printed
● Check if all billing documents have been invoiced
● Check if business partner is used in a franchise fee contract
● Check if business partner is used in a loyalty account
● Check if business partner is used as a service provider
● Check if business partner is used as an owner
● Check for open disconnection documents for business partner
● Check if business partner is used in role ISUI (installer)
● Check for open error messages for business partner in CRM replication monitoring
The checks for the SAP Utilities-specic object types are included in the enhancement spot
ISU_DPP_EOP_CHECK. For more information, see the documentation for the Business Add-Ins in the system.
Process Flow
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available
3. You do the following:
○ Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA).
○ Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner.
○ Run transaction IRMPOL and maintain the required residence and retention policies for the customer
master and vendor master in SAP S/4HANA (ILM objects: FI_ACCPAYB, FI_ACCRECV, FI_ACCKNVK)
○ Run transaction CVP_PRE_EOP to enable the end of purpose check function for the customer master
and vendor master in SAP S/4HANA.
○ Business users can request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
○ If you have the needed authorizations, you can unblock data by running the transaction
BUPA_PRE_EOP and CVP_UNBLOCK_MD
○ You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of SAP Utilities.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
● Dene the settings for authorization management under Data Protection Authorization Management
For more information, see the Customizing documentation.
● Dene the settings for blocking under Data Protection Blocking and Unblocking Business Partner
572
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.14.8.4 Read Access Logging
The Read Access Logging (RAL) component can be used to monitor and log read access to data and provide
information such as which business users accessed personal data, for example, of a business partner, and in
which time frame.
In RAL, you can congure which read-access information to log and under which conditions. SAP delivers
sample congurations for applications. In order to use these congurations, save the ZIP attachments from the
SAP Note 2370371 . Extract these ZIP les and import the RAL congurations using the import function for
congurations in transaction SRALMANAGER.
SAP Utilities logs bank account and social security number.
For more information about Read Access Logging, see the System Security for SAP NetWeaver AS for ABAP
Only guide. You can nd this guide using the search at https://help.sap.com/viewer/p/SAP_NETWEAVER_750
13.14.8.5 SAP Waste & Recycling
13.14.8.5.1 Internet Communication Framework Security
You should only activate those services that are needed for the applications running in your system. For SAP
Waste and Recycling the service EHWV_WASTE is needed. Use the transaction SICF to activate the service.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information about Internet Communication Framework Services, see the SAP NetWeaver 7.5
Connectivity guide. You can nd this guide by searching for Activating and Deactivating ICF
Services at https://help.sap.com/viewer/p/SAP_NETWEAVER_750.
13.14.8.5.2 Deletion of Personal Data
SAP Waste and Recycling might process data that is subject to the data protection laws applicable in specic
countries as described in SAP Note 1825544.
The SAP Information Lifecycle Management (ILM) component supports the entire software lifecycle including
the storage, retention, blocking, and deletion of data. SAP Waste and Recycling uses SAP ILM to support the
deletion of personal data as described in the following sections.
SAP provides a check for the end of the usage and WUC (Where use Check) for SAP Waste and Recycling. The
business partner assignments at the waste disposal facility (transaction EWAEL04) are checked (debtor,
vendor and cBP for the owner of the waste disposal facility) due to the fact that waste disposal facilities are not
part of the ILM implementation. If the assignment of the business partner data to the waste disposal facility is
no longer valid, this data has to be removed from the waste disposal facility. After the removal of the business
partner data from the waste disposal facility, this data is not further considered in the WUC.
All applications register either an end of purpose check (EoP) in the Customizing settings for the blocking and
deletion of the customer, vendor and central business partner.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 573

End of Purpose Check (EoP)
An end of purpose check determines whether data is still relevant for business activities based on the retention
period dened for the data. The retention period of data consists of the following phases:
● Phase one: The relevant data is actively used.
● Phase two: The relevant data is actively available in the system.
● Phase three: The relevant data needs to be retained for other reasons.
For example, processing of data is no longer required for the primary business purpose, but to comply with
legal rules for retention, the data must still be available. In phase three, the relevant data is blocked.
Blocking of data prevents the business users of SAP applications from displaying and using data that may
include personal data and is no longer relevant for business activities.
Blocking of data can impact system behavior in the following ways:
● Display: The system does not display blocked data.
● Change: It is not possible to change a business object that contains blocked data.
● Create: It is not possible to create a business object that contains blocked data.
● Copy/Follow-Up: It is not possible to copy a business object or perform follow-up activities for a business
object that contains blocked data.
● Search: It is not possible to search for blocked data or to search for a business object using blocked data in
the search criteria.
It is possible to display blocked data if a user has special authorization; however, it is still not possible to create,
change, copy, or perform follow-up activities on blocked data.
For information about the conguration settings required to enable this three-phase based end of purpose
check, see Process Flow and Conguration: Simplied Blocking and Deletion.
Integration with Other Solutions
In the majority of cases, dierent installed applications run interdependently as shown in following graphic.
Relevant Application Objects and Available Deletion Functionality
SAP Utilities uses SAP ILM to support the deletion of personal data. For more information, see the
documentation for Information Lifecycle Management at https://help.sap.com.
Deletion Functionality
Application Description Deletion Functionality
Transaction EWAORDER Standard application for changing
waste disposal orders
ILM object ISU_EORDER
574 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Application Description Deletion Functionality
Transaction EWAWA01 Standard application for maintaining
single position weighing processes
ILM object ISU_WPROC
Transaction EWAWA_MULTI Standard application for maintaining
multi position weighing processes
ILM object ISU_MWPROC
Transaction ELOC Maintaining service time slices for con
tainers
ILM Object ISU_SERVFQ
Relevant Application Objects and Available EoP/WUC Functionality
The following end of purpose checks exist:
● Check for customer and vendor assignments for waste disposal facilities
● Check for partner assignment of bulky orders
The checks for the SAP Waste and Recycling object types can be enhanced in the enhancement spot
EEWA_BF_DPP. For more information, see the documentation for the Business Add-Ins in the system.
Process Flow
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available.
3. You do the following:
○ Run transaction IRMPOL and maintain the required residence and retention policies for the central
business partner (ILM object: CA_BUPA).
○ Run transaction BUPA_PRE_EOP to enable the end of purpose check function for the central business
partner.
○ Run transaction IRMPOL and maintain the required residence and retention policies for the customer
master and vendor master in SAP ERP (ILM objects: ISU_ROUTE, ISU_SERVFQ, ISU_WPROC).
○ Run transaction CVP_PRE_EOP to enable the end of purpose check function for the customer master
and vendor master in SAP ERP.
4. Business users can request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
5. If you have the needed authorizations, you can unblock data by running the transaction BUPA_PRE_EOP
and CVP_UNBLOCK_MD.
6. You delete data by using the transaction ILM_DESTRUCTION for the ILM objects of <application,
component, scenario>.
For information about how to congure blocking and deletion for <application, component, scenario>, see
Conguration: Simplied Blocking and Deletion.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 575

Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
● Dene the settings for authorization management in under Data Protection Authorization Management.
For more information, see the Customizing documentation.
● Dene the settings for blocking in Customizing for Cross-Application Components under Data Protection
Blocking and Unblocking Business Partner .
13.14.8.6 Multichannel Foundation for Utilities and Public
Sector
13.14.8.6.1 Authorizations
The Multichannel Foundation for Utilities and Public Sector solution uses the authorization concept provided
by the SAP NetWeaver Application Server for ABAP.
Therefore, the recommendations and guidelines for authorizations as described in the SAP NetWeaver
Application Server ABAP Security Guide also apply to the Multichannel Foundation for Utilities and Public
Sector solution. The SAP NetWeaver authorization concept is based on assigning authorizations to users
based on roles. For role maintenance, use the prole generator transaction on the Application Server ABAP (AS
ABAP).
Reference Role Templates and Authorizations in SAP CRM
You create a reference user (UMC_REF_USR) during system installation. The reference user provides the
necessary authorizations for each online user. This means the reference user can access data in the back end
systems and Gateway.
PFCG role templates (SAP_CRM_UMC_ODATA and SAP_ISU_UMC_ODATA for SAP CRM and SAP S/4HANA,
respectively) are delivered with SAP CRM and SAP S/4HANA, which can be used (together with role templates
delivered by Gateway, for example, /IWBEP/RT_USS_INTUSR) to create the PFCG role for the reference user.
Reference Role Templates and Authorizations in SAP S/4HANA
For SAP S/4HANA, the PFCG role template (SAP_ISU_UMC_ODATA) is delivered with the SAP S/4HANA
system, which can be used together with role templates delivered by Gateway, for example, /IWBEP/
RT_USS_INTUSR to create the PFCG role for the reference user.
576
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Service Role Templates and Authorizations in SAP CRM
In addition to the reference user, you create a service user (UMC_SRV_USR) during installation. The service user
is responsible for creating the application users. Since the service user is used for anonymous logon, the user
should be granted minimum authorizations.
PFCG role templates (SAP_CRM_UMC_SRV and SAP_ISU_UMC_SRV for SAP CRM and SAP S/4HANA,
respectively) are delivered in SAP CRM and SAP S/4HANA systems, which can be used (together with role
templates delivered by Gateway, for example, /IWBEP/RT_USS_SRVUSR) to create the PFCG role for the
service user.
For more information, see the SAP Help Portal at:http://help.sap.com/nwgateway SAP Gateway Security
Guide
Authorizations in the SAP System Roles in the SAP Gateway Landscape .
Service Roles and Authorizations in SAP S/4HANA
For SAP SAP S/4HANA, the PFCG role template SAP_ISU_UMC_SRV is delivered in SAP S/4HANA system,
which can be used together with role templates delivered by Gateway, for example, /IWBEP/RT_USS_SRVUSR
to create the PFCG role for the service user.
Creating and Assigning Roles in SAP CRM
To create the required users (UMC_SRV_USR, UMC_REF_USR), you must perform the following steps in SAP S/
4HANA, SAP CRM, and the Gateway systems.
Note
In role maintenance, choose Utilities Templates to display the available templates, copy templates
delivered by SAP, change the copies, and create templates for yourself. You will need the authorization User
Master Record Maintenance: User Groups (S_USER_GRP) with value * in the elds CLASS and ACTVT. SAP
template names start with the letter S; therefore, templates that you create must not start with S.
You require administrator authorizations to create roles and users, and to assign roles to users.
1. Create a role and enter a description.
2. Insert the authorizations using the role templates.
Depending on the system and the role type, you can combine dierent role templates; see the following
table:
Templates SAP CRM System SAP S/4 HANA System Gateway
UMC_SRV_USR SAP_CRM_UMC_SRV
/IWBEP/RT_USS_SRVUSR
SAP_ISU_UMC_SRV
/IWBEP/RT_USS_SRVUSR
/IWFND/RT_GW_USR
/IWBEP/RT_USS_SRVUSR
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 577

Templates SAP CRM System SAP S/4 HANA System Gateway
UMC_REF_USR SAP_CRM_UMC_ODATA
/IWBEP/RT_USS_INTUSR
SAP_ISU_UMC_ODATA
/IWBEP/RT_USS_INTUSR
/IWBEP/RT_USS_INTUSR
Note
Add additional required authorization objects /IWFND/SRV, S_SECPOL and S_TCODE
3. You must manually add authorization object CRM_IUPROC to the reference user in the SAP CRM system.
The recommendation is to add activity 16 (execute) on all the processes (*) as shown below:
4. Verify and edit the authorizations, if necessary.
For the UMC_SRV_USR, check role access to the following services (authorization object: S_SERVICE):
○ Activate OData Services in the Gateway system.
○ CRM_UTILITIES_UMC_URM (SAP CRM and Gateway)
○ CRM_UTILITIES_UMC_PUBLIC_SRV (SAP CRM and Gateway)
○ /IWBEP/USERMANAGEMENT (SAP CRM and Gateway)
For the UMC_REF_USR, check role access to the following services (authorization object: S_SERVICE):
○ Activate OData Services in the Gateway system.
○ CRM_UTILITIES_UMC (for SAP CRM system and Gateway)
○ ERP_UTILITIES_UMC (for SAP S/4HANA system and Gateway)
○ /IWBEP/USERMANAGEMENT (for SAP CRM system and Gateway)
This is especially true when some function enhancements are carried out.
5. Generate the authorizations.
A prole is automatically generated for the role.
6. Assign the role to users (UMC_SRV_USR, UMC_REF_USR) and run a user master comparison to enter the
generated prole into the user master record.
Creating and Assigning Roles in SAP S/4HANA
To create the required users (UMC_SRV_USR, and UMC_REF_USR), you must perform the following steps in SAP
S/4HANA and the Gateway systems.
Note
In role maintenance, choose Utilities Templates to display the available templates, copy templates
delivered by SAP, change the copies, and create templates for yourself. You will need the authorization User
Master Record Maintenance: User Groups (S_USER_GRP) with value * in the elds CLASS and ACTVT. SAP
template names start with the letter S; therefore, templates that you create must not start with S.
You require administrator authorizations to create roles and users, as well as to assign roles to users.
1. Create a role and enter a description.
2. Insert the authorizations using the role templates.
578
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
Depending on the system and the role type, you can combine dierent role templates; see the following
table:
Templates SAP S/4HANA System Gateway System
UMC_SRV_USR SAP_ISU_UMC_SRV
/IWBEP/RT_USS_SRVUSR
/IWFND/RT_GW_USR
/IWBEP/RT_USS_SRVUSR
UMC_REF_USR SAP_ISU_UMC_ODATA
/IWBEP/RT_USS_INTUSR
/IWBEP/RT_USS_INTUSR
Note
Add additional required authorization objects /WFND/SRV, S_SECPOL and S_TCODE
3. Verify and edit the authorizations, if necessary.
For the UMC_SRV_USR, check role access to the following services (authorization object: S_SERVICE):
○ ERP_UTILITIES_UMC_URM (SAP S/4HANA and Gateway)
○ /IWBEP/USERMANAGEMENT (SAP S/4HANA and Gateway): This only applies to the standalone SAP S/
4HANA scenario
For the UMC_REF_USR, check role access to the following services (authorization object: S_SERVICE):
○ ERP_UTILITIES_UMC (for SAP S/4HANA system and Gateway)
○ /IWBEP/USERMANAGEMENT (for SAP S/4HANA system and Gateway)
This is especially true when some function enhancements are carried out.
4. Generate the authorizations.
A prole is automatically generated for the role.
5. assign the role to users (UMC_SRV_USR, UMC_REF_USR) and run a user master comparison to enter the
generated prole into the user master record.
Related Information
Gateway Security Guide
See http://help.sap.com/nwgateway
User and Role Administration for SAP NetWeaver AS for ABAP
See http://help.sap.com/netweaver under Identity Management
Authorization Templates
See http://help.sap.com/netweaver , under System Administration Tasks Authorizations Maintaining
Authorizations
Setting up Authorizations with Role Maintenance
See http://help.sap.com/netweaver , under System Administration TasksAuthorizationsMaintaining
Authorizations
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 579
13.14.8.6.2 Internet Communication Framework Security
(ICF)
Security for the Multichannel Foundation for Utilities and Public Sector solution consists of SAP Gateway
OData services and HTML5/SAP UI5-based Web-enabled content managed by the Internet Communication
Framework (ICF) (transaction SICF).
You must activate the ICF services required for the applications you want to use.
Note
You can also activate these services during the technical conguration.
The Multichannel Foundation for Utilities and Public Sector solution relies on the following services in SAP
CRM:
● UMCUI5: An HTML5/SAP UI5-based Web-enabled interface to access the OData services
● CRM_UTILITIES_UMC: OData services from the SAP CRM system
● CRM_UTILITIES_UMC_URM: Multichannel Foundation for Utilities and Public Sector extension of the SAP
Gateway USERREQUESTMANAGEMENT OData service
● CRM_UTILITIES_UMC_PUBLIC_SRV: Anonymous OData Service for products in SAP CRM
● ERP_UTILITIES_UMC_URM (logon user UMC_SRV_USR): OData services from the SAP S/4HANA system
In addition, the application also uses service USERMANAGEMENT from SAP Gateway.
The Multichannel Foundation for Utilities and Public Sector S/4HANA stand-alone solution relies on the
following services:
● ERP_ISU_UMC (logon user/current user): Multichannel Foundation for Utilities and Public Sector extension
of the Gateway USERREQUESTMANAGEMENT OData Service
● ERP_UTILITIES_UMC: OData services from the SAP S/4HANA system
● ERP_ISU_UMC_PUBLIC (logon user UMC_SRV_USR)
In addition, the application also uses the service USERMANAGEMENT from SAP Gateway.
Related Information
RFC/ICF Security Guide
See http://help.sap.com/netweaver under SAP NetWeaver 7.0 Including Enhancement Package 1 SAP
NetWeaver Security Guide
Security Guides for Connectivity and Interoperability .
13.14.9 SAP for Insurance
Note that the following security information applies to SAP Claims Management (FS-CM) only and not to other
SAP for Insurance solutions.
580
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.14.9.1 SAP Claims Management
13.14.9.1.1 Data Storage Security
Using Logical Path and File Names to Protect Access to the File System
SAP Claims Management save data in les in the le system. Therefore, it is important to explicitly provide
access to the corresponding les in the le system without allowing access to other directories or les (also
known as directory traversal). This is achieved by specifying logical paths and le names in the system that
map to the physical paths and le names. This mapping is validated at runtime and if access is requested to a
directory that does not match a stored mapping, then an error occurs.
The following list shows the logical le names and paths used by SAP Claims Management and for which
programs these le names and paths apply:
Logical File Names Used in SAP Claims Management
The following logical le names have been created in order to enable the validation of physical le names:
● ICLVEH
○ Program using this logical le name and parameters used in this context: ICL_VEHCATALOG_UPLOAD
○ Customizing path: SAP Insurance Claims Management Claim Business Settings Damaged
Objects/Diagnoses Damaged Objects/Injured Persons Import Catalog for Insured Objects
● ICLDIAG
○ Program using this logical le name and parameters used in this context: ICL_DIAG_UPLOAD
○ Customizing path: SAP Insurance Claims Management Claim Business Settings Damaged
Objects/Diagnoses
Damaged Objects/Injured Persons Diagnoses Import Diagnosis Groups and
Diagnoses
● ICLSUPPL
○ Program using this logical le name and parameters used in this context:
ICL_ICLCLAIMDATA_UPLOAD
● ICLDI
○ Program using this logical le name and parameters used in this context: ICL_DATA_UP_DOWNLOAD
Activating the Validation of Logical Path and File Names
These logical paths and le names, as well as any subdirectories, are specied in the system for the
corresponding programs. For downward compatibility, the validation at runtime is deactivated by default. To
activate the validation at runtime, maintain the physical path using the transactions FILE (client-independent)
and SF01 (client-specic). To nd out which paths are being used by your system, you can activate the
corresponding settings in the Security Audit Log.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 581

13.14.9.1.2 Data Protection
13.14.9.1.2.1 User Consent
It is the responsibility of insurance companies themselves to obtain the consent of all of their business partners
with regard to the use of their personal data.
13.14.9.1.2.2 Read Access Logging
In Read Access Logging, you can congure which read-access information to log and under which conditions. In
the following table, you can nd the congurations (shipped with SAP Claims Management), the elds are
logged, and the relevant business context:
Conguration Fields Logged Business Context
ICL_SSN
● Tax Number Category (eld
TAXTYPE in for instance table
ICLC_ICL_BP_MINI_SCREEN-)
● Business Partner Tax Number
(
TAXNUM)
SAP Claims Management logs tax data.
Note
In the Mini Business Partner the tax
number is only logged if the user
has selected the tax number cate
gory
US1.
ICL_BANK
● Bank details ID (BKEXT)
● Bank country key (BANKS)
● Bank Key (BANKL)
● Bank account number (BANKN)
● IBAN (IBAN)
SAP Claims Management logs bank ac
count data.
582 P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Conguration Fields Logged Business Context
ICL_HEALTH
The elds in the following categories
are logged:
● Claim item groupings and the rele
vant items with subclaim type, cov
erage, coverage type, benet type,
benets catalog
● Diagnosis
● Procedures
● Tooth notation and eyeglass pre
scription
● Level of care
● Suspension of care
● Insured persons and claimant
● Facts capture
● Payments
SAP Claims Management logs health
data.
For Read Access Logging of health data, you have to activate specic views in Customizing for SAP Insurance
under Claims Management Claim Technical Settings Data Protection Read Access Logging
Activate Specic Views for Read Access Logging .
13.14.9.1.2.3 Deletion of Personal Data
SAP Claims Management might process data (personal data) that is subject to the data protection laws
applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to control the
blocking and deletion of personal data. For more information, see the product assistance for SAP S/4HANA on
the SAP Help Portal at
http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components
Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Object Provided Deletion Functionality
Archiving of Claims
(Archiving Object ICLCLAIM)
ILM Object ICLCLAIM (see SAP Note 1976123 )
)
Archiving of Claim Bundles
(Archiving Object ICLECCEVT)
ILM Object ICLECCEVT (see SAP Note 1976123 )
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 583

Application Object Provided Deletion Functionality
Archiving of Subclaims
(Archiving Object ICLSUBCL)
ILM Object ICLSUBCL
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
● Dene the settings for authorization management in Customizing for Cross-Application Components under
Data Protection Authorization Management . For more information, see the Customizing
documentation.
● Dene the settings for blocking in Customizing for Cross-Application Components under Data Protection
Blocking and Unblocking Business Partner .
You congure the settings related to the blocking and deletion of customer master data in Customizing for SAP
Insurance
under Claims Management Claim Technical Settings Archiving .
13.14.9.1.2.4 Change Log
In order to log personal data in FS-CM, you can use the following standard function of FS-CM:
● Log of changes in a claim and in a claim bundle
When you are processing a claim or a claim bundle, you can view a structured overview showing the
changes in the relevant claim or claim bundle. To call up the structured change overview, choose
Tools
Claim Changes (Overview) in claim processing, or Tools Bundle Changes (Overview) in claim
bundle processing. In the next dialog screen you see the overview tree with the changes that have been
made.
For more information, see Application Help of SAP Claims Management under Claim Administration of
the Claims Management System
Display of Changes in Claim and Claim Bundle .
Note
Changes of business partner data will be locked in the business partner system since business partner data
cannot be locked in FS-CM.
13.14.9.2 SAP Statutory Reporting for Insurance
584
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

13.14.9.2.1 Deletion of Personal Data in FS-SR
Use
The Statutory Reporting (FS-SR) might process data (personal data) that is subject to the data protection laws
applicable in specic countries. The business partners in the statutory reports can only be legal entities (in
German: juristische Personen), not natural persons. You can use SAP Information Lifecycle Management (ILM)
to control the blocking and deletion of personal data in the applications providing the data, for example, in
Loans Management (FS-CML). For more information, see the product assistance for SAP S/4HANA on the SAP
Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross Components Data
Protection
. In FS-SR, business partner data can only be deleted manually, using deletion reports.
Relevant Application Objects and Available Deletion Functionality
Application Object Detailed Description Provided Deletion Functionality
Ledger Data Table For more information, see SAP Note
2304306 .
● Transaction ISSR_NB2
● Transaction ISSR_MIG5
Stored List Transaction ISSR_OUT_ALV
Business Partner Change List Transaction ISSR_DEL_CNS_GPCH
13.14.10 Oil and Gas
13.14.10.1 Upstream Operations Management
13.14.10.1.1 Internet Communication Framework Security
(ICF)
● For Oil and Gas, Upstream Operations Management (UOM) module the following services are needed:
○ Allocation
○ GHO_WDA_ALLOC_MC_OIF (Capture Measurements)
○ GHO_WDA_ALLOC_RESULTS_OIF (Display Allocation Results)
○ GHO_WDA_ALLOC_RULES_OIF (Process Allocation Rules)
○ GHO_WDA_ALLOC_MRH_OIF (Process MRH Rules)
○ Network Object
○ o GHO_WDA_NETOBJ_OIF (Create a Network Object)
○ o GHO_WDA_NETOBJ_OIF (Change a Network Object)
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 585
○ o GHO_WDA_NETOBJ_OIF (Display a Network Object)
○ o GHO_WDA_OG_ENTITY (Create an Oil & Gas Entity)
○ o GHO_WDA_OG_ENTITY (Change an Oil & Gas Entity)
○ o GHO_WDA_OG_ENTITY (Display an Oil & Gas Entity)
● Ownership
○ Division of Interest
○ GHO_WDA_OWN_OIF (Create a Division of Interest (DOI)
○ GHO_WDA_OWN_OIF (Change a Division of Interest (DOI)
○ GHO_WDA_OWN_OIF (Display a Division of Interest (DOI)
○ GHO_WDA_OWN_NET_ASG_OIF (Assign a Division of Interest to Network Objects)
○ Scale Method
○ GHO_WDA_OWN_SM_OIF (Create a Sliding Scale Method)
○ GHO_WDA_OWN_SM_OIF (Change a Sliding Scale Method)
○ GHO_WDA_OWN_SM_OIF (Display a Sliding Scale Method)
○ Business Partner
○ Process Business Partner
○ Owner Transfer Request
○ GHO_WDA_OWN_TRO_GAF (Create an Owner Request)
○ GHO_WDA_OWN_TRO_GAF (Change an Owner Request)
○ GHO_WDA_OWN_TRO_GAF (Display an Owner Request)
○ Reports (Display Only)
○ GHO_WDA_OWN_RPT_OIF (Oil & Gas Business Partner Report)
○ GHO_WDA_OWN_RPT_OIF (Division of Interest Owners)
○ GHO_WDA_OWN_RPT_OIF (Well Completions Assigned to Division of Interest)
○ GHO_WDA_OWN_RPT_OIF (Division of Interest History Report)
○ GHO_WDA_OWN_RPT_OIF (Ownership Entitlement Results)
● Network Modeling
○ GHO_NETWORK_OIF (Model a Production Network Structure)
○ GHO_NETWORK_OIF (Display a Production Network Structure)
For running SAP Fiori applications for Upstream Operations Management please activate some of the common
SICF node. These SICF node needs to be activated on the front end server (SAP NetWeaver Gateway).
Activate the following SICF nodes specic to Upstream Operations Management Fiori Applications:
● UIS4HOP1 - UI for S/4HANA On Premise
○ /sap/bc/ui5_ui5/sap/ups_alloc_ress1
○ /sap/bc/ui5_ui5/sap/ups_alloc_stas1
○ /sap/bc/ui5_ui5/sap/ups_blkuploads1
○ /sap/bc/ui5_ui5/sap/ups_commonss1
○ /sap/bc/ui5_ui5/sap/ups_defer_evts1
○ /sap/bc/ui5_ui5/sap/ups_defer_ress1
○ /sap/bc/ui5_ui5/sap/ups_def_woevts1
○ /sap/bc/ui5_ui5/sap/ups_fc_accesss1
○ /sap/bc/ui5_ui5/sap/ups_fc_apfcsts1
○ /sap/bc/ui5_ui5/sap/ups_fc_calfcts1
586
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

○ /sap/bc/ui5_ui5/sap/ups_fc_cmpress1
○ /sap/bc/ui5_ui5/sap/ups_fc_ghdatas1
○ /sap/bc/ui5_ui5/sap/ups_fc_mngpros1
○ /sap/bc/ui5_ui5/sap/ups_fc_results1
○ /sap/bc/ui5_ui5/sap/ups_fdcs1
○ /sap/bc/ui5_ui5/sap/ups_xerrorss1
○ /sap/bc/ui5_ui5/sap/ups_mnghiers1
● Activate the following SICF nodes of OData services being used by Fiori applications:
○ /sap/opu/odata/sap/ups_bulk_upld
○ /sap/opu/odata/sap/ups_common
○ /sap/opu/odata/sap/ups_def_event
○ /sap/opu/odata/sap/ups_def_result
○ /sap/opu/odata/sap/ups_def_work_order
○ /sap/opu/odata/sap/ups_fc_appr_pub
○ /sap/opu/odata/sap/ups_fc_calc_fcst
○ /sap/opu/odata/sap/ups_fc_gatherdata
○ /sap/opu/odata/sap/ups_fc_mng_access
○ /sap/opu/odata/sap/ups_fc_mng_project
○ /sap/opu/odata/sap/ups_fc_view_res
○ /sap/opu/odata/sap/ups_eld_data_capture
○ /sap/opu/odata/sap/ups_x_error
○ /sap/opu/odata/sap/ups_hca_result
○ /sap/opu/odata/sap/ups_hca_status
○ /sap/opu/odata/sap/ups_mng_hierarchy
13.14.10.1.2 Other Security-Relevant Information
The following table shows an overview of the data ow in UOM in a two system DMZ environment. Data access
is separated from the presentation layer, which is running on the second machine. The UI is accessed using
HTTP or HTTPs.
Step Description Security Measure
User Interface: FPM-based ABAP Web
Dynpro with Unied Rendering
Data requests, updates, and actions are
triggered from the UI.
ABAP WebDypro, unied rendering, ac
cess using HTTP or HTTPS
PLM UI Framework Infrastructure for communication be
tween GUIBBs/WebDynpro context and
SPI connector
SPI Connector (DMZ System) Acting like a proxy for the back end SPI
connector.
Metadata is read from back end only
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 587

Step Description Security Measure
RFC RFC based data transfer between DMZ
system and ERP back end system;
xstring based data transfer
Protocol switch to RFC; White list for ta
ble based data transfer; Sync with meta
data model in connector
SPI Connector (Back End System) A standardized interface that is used to
transfer data from the application serv
ice provider to the UI framework con
sumer.
Validation against metadata denition
during data transfer
Application Service Provider Implementation Additional metadata denition
13.14.10.2 IS-OIL Downstream
13.14.10.2.1 Internet Communication Framework Security
(ICF)
You should only activate those services that are needed for the applications running in your system. For the
Fiori apps My Nominations , Regional Inventory View and Mass Change Events in the TSW area, following
services are needed:
● TSW_MYNOMINATIONS_SRV_01
● TSW_REGIONAL_INVENTORY_SRV_01
● TSW_MYEVENTS_SRV
Use the transaction SICF to activate these services.
If your rewall(s) use URL ltering, also note the URLs used for the services and adjust your rewall settings
accordingly.
For more information about ICF security, see the respective chapter in the SAP NetWeaver Security Guide.
13.14.10.2.2 Deletion of Personal Data
The IS-OIL Downstream might process data that is subject to the data protection laws applicable in specic
countries as described in SAP Note 1825544.
The SAP Information Lifecycle Management (ILM) component supports the entire software lifecycle including
the storage, retention, blocking, and deletion of data. The IS-OIL Downstream uses SAP ILM to support the
deletion of personal data as described in the following sections.
● SAP delivers an end of purpose check for the IS-OIL Downstream
● SAP delivers a where-used check (WUC) for the IS-OIL Downstream
588
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
All applications register either an end of purpose check (EoP) in the Customizing settings for the blocking and
deletion of the customer and vendor master or a WUC. For information about the Customizing of blocking and
deletion for IS-OIL Downstream application , see Conguration: Simplied Blocking and Deletion.
End of Purpose Check (EoP)
An end of purpose check determines whether data is still relevant for business activities based on the retention
period dened for the data. The retention period of data consists of the following phases.
● Phase one: The relevant data is actively used.
● Phase two: The relevant data is actively available in the system.
● Phase three: The relevant data needs to be retained for other reasons.
For example, processing of data is no longer required for the primary business purpose, but to comply with
legal rules for retention, the data must still be available. In phase three, the relevant data is blocked.
Blocking of data prevents the business users of SAP applications from displaying and using data that may
include personal data and is no longer relevant for business activities.
Blocking of data can impact system behavior in the following ways:
● Display: The system does not display blocked data.
● Change: It is not possible to change a business object that contains blocked data
● Create: It is not possible to create a business object that contains blocked data.
● Copy/Follow-Up: It is not possible to copy a business object or perform follow-up activities for a business
object that contains blocked data.
● Search: It is not possible to search for blocked data or to search for a business object using blocked data in
the search criteria.
It is possible to display blocked data if a user has special authorization; however, it is still not possible to create,
change, copy, or perform follow-up activities on blocked data.
For information about the conguration settings required to enable this three-phase based end of purpose
check, see Process Flow and Conguration: Simplied Blocking and Deletion.
Integration with Other Solutions
In the majority of cases, dierent installed applications run interdependently as shown in following graphic.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 589
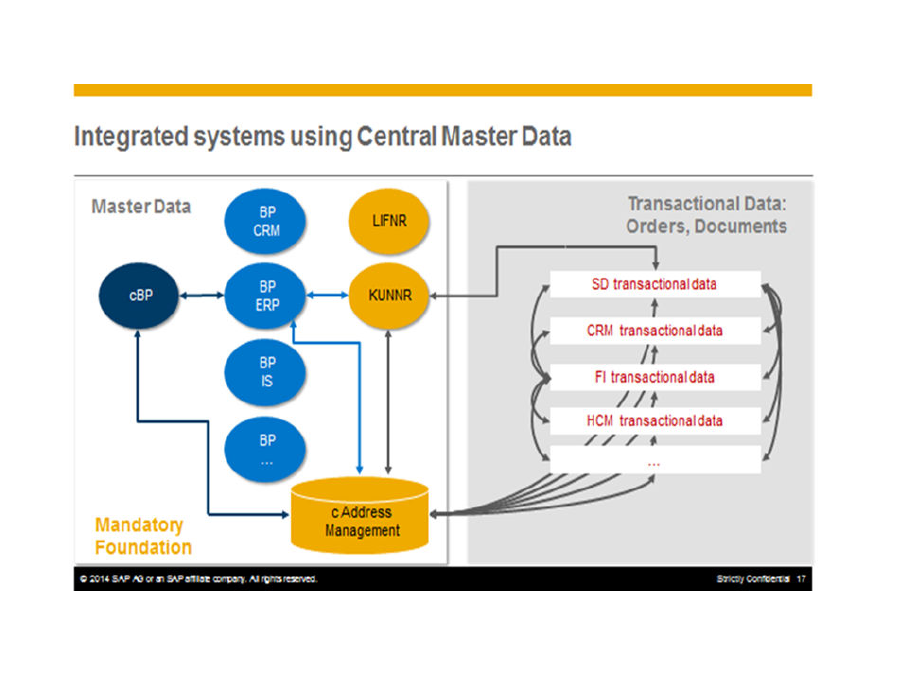
An example of an application that uses central master data is an SAP for Healthcare (IS-H) application that
uses the purchase order data stored in Financial Accounting (FI) or Controlling (CO).
590
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available Deletion Functionality
Application Detailed Description Provided Deletion Functionality
IS-OIL Downstream The customer/vendor blocking report
will check the consuming application to
determine end of purpose of the cus
tomer/vendor.
In an IS-OIL system, in addition to the
EOP checks performed by SD,MM ,FI
application the checks for usage of the
customer/vendor in IS-OIL Downstream
application has to be made.
The IS-OIL application has to register it
self under the customer master data
and vendor master data as consuming
applications that need to be checked
for EoP . EOP. Check logic in IS-OIL will
be delivered in the class
CVP_OIL_EOP_CHECK.
ILM Enabled Archiving objects:
OIG_DRIVER
OIG_VEHCLE
OIG_TPUNIT
OIJ_NOMIN
OIJ_TICKET
IS_OIFSPBL
Data Destruction objects:
OIJ_SCHED_DESTRUCTION
OIJ_PARTNER_DESTRUCTION
OIA_EXGDOCU_DESTRUCTION
OIL_TAS_TPI_DESTRUCTION
Decoupled TSW TSW_ECC The customer/vendor blocking report
will check the consuming application
to determine end of purpose of the cus
tomer/vendor.
In a Decoupled TSW scenario , the
checks for usage of customer/vendor in
TSW application specic documents
like nomination is made.
The TSW_ECC application has to regis
ter itself under the customer master
data and vendor master data as con
suming applications that need to be
checked for EoP . EOP Check logic in
TSW_ECC will be delivered in the class
CVP_TSW_ECC_CHECK.
ILM Enabled Archiving objects:
OIG_VEHCLE
OIG_TPUNIT
OIJ_NOMIN
OIJ_TICKET
IS_OIFSPBL
Data Destruction objects:
OIJ_SCHED_DESTRUCTION
OIJ_PARTNER_DESTRUCTION
Process Flow
1. Before archiving data, you must dene residence time and retention periods in SAP Information Lifecycle
Management (ILM).
○ Run transaction IRMPOL and maintain the required residence and retention policies for the customer
master and vendor master in SAP S/4HANA (ILM objects: FI_ACCPAYB, FI_ACCRECV, FI_ACCKNVK).
○ Run transactionIRMPOL and maintain the required retention policies for the ILM objects of IS OIL
Downstream, application or Decoupled TSW .
2. You choose whether data deletion is required for data stored in archive les or data stored in the database,
also depending on the type of deletion functionality available
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 591

3. To determine which business partners have reached end of purpose and can be blocked, you do the
following:
○ Run transaction CVP_PRE_EOP to execute the end of purpose check function for the customer master
and vendor master in SAP S/4HANA.
4. To unblock blocked business partner data, you do the following
○ Request unblocking of blocked data by using the transaction BUP_REQ_UNBLK.
○ If you have the needed authorization for unblocking business partner data, you can unblock the
requested data by running the transaction CVP_UNBLOCK_MD for customer master data and vendor
master data in SAP S/4HANA.
5. You delete data by using the transactionILM_DESTRUCTION for the ILM objects of IS OIL Downstreamor
Decoupled TSW.
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components under Data Protection.
● Dene the settings for authorization management under Data Protection Authorization Management
For more information, see the Customizing documentation.
● Dene the settings for blocking under Data Protection Blocking and Unblocking Business Partner
13.14.10.2.3 Read Access Logging
If no trace or log is stored that records which business users have accessed data, it is dicult to track the
person(s) responsible for any data leaks to the outside world. The Read Access Logging (RAL) component can
be used to monitor and log read access to data and provide information such as which business users
accessed personal data, for example, of a business partner, and in which time frame.
In RAL, you can congure which read-access information to log and under which conditions.
For more information, see Read Access Logging in the documentation for SAP NetWeaver on the SAP Help
Portal under http://help.sap.com .
13.14.11 Engineering, Construction, and Operations
13.14.11.1 Equipment and Tools Management
592
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
13.14.11.1.1 Authorizations
Equipment and Tools Management (ETM) uses the authorization concept provided by the SAP NetWeaver AS
for ABAP. Therefore, the recommendations and guidelines for authorizations as described in the SAP
NetWeaver AS Security Guide ABAP also apply.
The SAP NetWeaver authorization concept is based on assigning authorizations to users based on roles. For
role maintenance, use the prole generator (transaction PFCG) on the AS ABAP.
Note
For more information about how to create roles, see the NetWeaver Security Guide under User
Administration and Authentication.
Standard Authorization Objects
The table below shows the security-relevant authorization objects that are used:
Authorization Object Description
J_3GBLART Authorizations for document types
J_3GEQART2 CEM – Equipment Types for Document Category 2
J_3GEMPGR2 CEM - Recipient Groups, Document Category 2
J_3GBEWTP2 CEM – Transaction Types, Document Category 2
J_3GACTVT CEM Allowed Activities
J_3GABRLST Call CEM Settlement List for Organizational Units
J_3GDISPGR MRP Group in Equipment
J_3GDBER Planning Area in Recipient
J_3G_TCODE Transaction Code
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 593

13.14.11.1.2 Deletion of Personal Data
Use
Equipment and Tools Management (ETM) might process data (personal data) that is subject to the data
protection laws applicable in specic countries. You can use SAP Information Lifecycle Management (ILM) to
control the blocking and deletion of personal data. For more information, see the product assistance for SAP
S/4HANA on the SAP Help Portal at http://help.sap.com/s4hana_op_1709 Product Assistance Cross
Components Data Protection .
Relevant Application Objects and Available Deletion Functionality
Application Provided Deletion Functionality
Equipment and Tools Management (IS-ADEC-ETM) Archiving Object
/SAPCEM01
/SAPCEM02
/SAPCEM03
/SAPCEM04
/SAPCEM05
/SAPCEM06
/SAPCEM07
ILM Object
SAPCEM_01
SAPCEM_02
SAPCEM_07
Reports
/SAPCEM/ILM_DELETION_REP_01
594
P U B L I C
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications

Relevant Application Objects and Available EoP/WUC functionality
Application Implemented Solution (EoP or WUC) Further Information
Equipment and Tools Management (IS-
ADEC-ETM)
EoP Checks tables /SAPCEM/BDPO,
J_3GBELP
Conguration: Simplied Blocking and Deletion
You congure the settings related to the blocking and deletion of business partner master data in Customizing
for Cross-Application Components→Data Protection.
Security Guide for SAP S/4HANA 1709
SAP S/4HANA Business Applications
P U B L I C 595

14 Business Network Integration
SAP S/4HANA currently supports integration scenarios with the Ariba Network (including Ariba Sourcing via
the Ariba Network), and with SAP Fieldglass.
14.1 Security Aspects for Connectivity Types
In all of the connectivity types described below, only the on-premise system opens the connection to the Cloud,
thus supporting the highest level of security. A proxy or reverse proxy in the demilitarized zone (DMZ) is not
required.
The SAP S/4HANA system communicates with the business networks through the HTTPS protocol, encrypting
transmitted data.
Direct Connectivity
For direct connectivity, SAP S/4HANA always opens the connection by executing the following actions:
● SAP S/4HANA pushes cXML messages to the business networks (synchronous)
● The Polling Agent in SAP S/4HANA fetches pending messages from the business networks (synchronous)
Mediated Connectivity
For mediated connectivity, the SAP S/4HANA system connects through SAP PI. The connection functions as
follows:
● SAP S/4HANA pushes cXML messages to SAP PI (asynchronous)
● The Ariba Network Adapter for SAP NetWeaver triggers its Polling Agent to fetch pending cXML messages
from Ariba Network. The Polling Agent in the PI adapter then pushes the cXML messages to the SAP S/
4HANA system (asynchronous).
If SAP S/4HANA communicates with Ariba Network through SAP PI, there are no special security
requirements.
Note
For mediated connectivity, Ariba provides information on how to communicate with Ariba Network in the
Ariba Network Adapter for SAP NetWeaver Setup Guide. You can contact Ariba for more information.
596
P U B L I C
Security Guide for SAP S/4HANA 1709
Business Network Integration
14.2 Direct Connectivity: SAP S/4HANA as Client
When sending a cXML message to a business network, the sender must authenticate itself:
● SAP Fieldglass supports authentication by client certicate.
● Ariba Network oers authentication with client certicate or with shared secret password. Both
authentication methods are also supported by SAP S/4HANA. For more information about the
authentication methods on Ariba Network, contact SAP Ariba.
Note
Communication with the Ariba Network and with SAP Fieldglass is based on HTTPS. For HTTPS SSL
encryption, SAP Cryptographic Library is required. For information about installing the SAP
Cryptographic Library, search for “The SAP Cryptographic Library Installation Package” in the
documentation of SAP NetWeaver at http://help.sap.com/nw.
Authentication with Client Certicate (Ariba Network Only)
For authentication with client certicate it is strongly recommended that you use the latest version of the SAP
Cryptographic Library (SAPCRYPTOLIB). For more information about latest SAP Cryptographic Library
versions, bugs, and xes see SAP Note 455033 .
Note
Only certicates in Personal Security Environment (PSE) format can be imported. Certicates in other
formats must rst be converted to PSE format. The conversion can be done using the command line tool
SAPGENPSE. The tool can be installed with SAP Cryptographic Library installation package.
For example, to convert from P12 (Public-Key Cryptography Standards) format to PSE format, enter the
following command line:
sapgenpse import_p12 -v -r <root certificate> -p <Target PSE file> <Source File>
Setting up authentication with client certicate includes the following steps:
1. Get the client certicate from a Certication Authority (CA) that is trusted by Ariba.
2. Import the private key of the certicate into the SAP S/4HANA system by using Trust Manager (transaction
STRUST).
1. To store the client certicate in SAP S/4HANA, you have to create a new Client Identity in Trust
Manager. Proceed as follows:
1. Choose Environment SSL Client Identities , enter ARIBA as the identity name and Ariba
Network Client as the description.
2. Save your entries.
2. Import the private key of the certicate in Trust Manager. Proceed as follows:
1. Select the created ARIBA SSL Client ID and choose PSE Import to import the PSE le.
2. Enter the password for the certicate, if required.
Security Guide for SAP S/4HANA 1709
Business Network Integration
P U B L I C 597

3. Save your PSE le by choosing PSE Save as SSL Client , and enter ARIBA as the SSL
Client.
4. Navigate to the Own Certicate group box on the Trust Manager screen, and double-click the
certicate to add it to the certicate list. The certicate is now shown in Trust Manager in
Certicate List.
3. Import the root certicate into the SAP S/4HANA system by using Trust Manager. Proceed as follows:
1. Double-click the SSL Client Identity ARIBA that you have created.
2. Navigate to the Certicate group box and choose Import certicate. Add the imported certicate to the
certicate list by clicking Add to Certicate List.
4. For HTTPS SSL encryption, obtain the server certicate from Ariba. Proceed as follows:
1. Go to buyer.ariba.com.
2. Download the certicate using your browser.
For example, if you are using Internet Explorer, choose View Security Report View Certicates .
On the Details tab page, choose Copy to File and export it in the Base-64 encoded X.509 format.
3. Import the server certicate into the SAP S/4HANA system using Trust Manager.
4. Double click the ARIBA SSL Client ID that you have created.
5. Navigate to the Certicate group box and choose Import certicate. Add the imported certicate to the
certicate list by clicking Add to Certicate List.
5. To activate the changes, restart the Internet Communication Manager (ICM) using transaction SMICM and
choose
Administration ICM Restart Yes . For more information, search for the phrase Using the
ICM Monitor in the documentation of SAP NetWeaver at help.sap.com.
6. Congure the Web services in SOA Manager (transaction SOAMANAGER). Find the following consumer
proxies:
○ cXMLSynchronousOutboundAdapterMessage_Out (CO_ARBFND_PRX_OADP_OUT)
○ cXMLGetPendingDataRequest_Out (CO_ARBFND_PRX_GPDQ_OUT)
In the Details of Consumer Proxy group box, navigate to the Congurations tab page and select the logical
port. In the Conguration of Logical Port group box, navigate to the Consumer Security tab page, choose
the X.509 SSL Client Certicate radio button, and enter Ariba in the SSL Client PSE of transaction STRUST
eld.
7. For Ariba Network: In the prole of your account on Ariba Network, select the Certicate authentication
method in the cXML setup and enter the public key of the certicate.
Authentication with User and Password
To set up authentication with a user and a password, proceed as follows:
1. Maintain the user and the password in the Dene Credentials and Endpoints for Ariba Network Customizing
activity or in the Dene Credentials for SAP Fieldglass Customizing activity, respectively.
The password is stored in the secure storage of your SAP S/4HANA system. SAP S/4HANA supports
passwords with a maximum length of 36 characters.
Note
According to security requirements, passwords must not be written to logs, protocols, or traces.
Therefore, the password is not visible in transactions such as SRT_MONI where the XML message
monitoring and tracing takes place, as business users can also have authorization for the message
598
P U B L I C
Security Guide for SAP S/4HANA 1709
Business Network Integration

monitoring transactions. However, when activating an Internet Communication Framework (ICF)
recording using transaction SICF, the system logs the password in the corresponding ICF trace. ICF
recording is only intended for administrators and requires the S_ADMI_FCD authorization.
Ariba Network integration only: For authentication with shared secret password, the shared secret
password has to be provided in the Sender element of the cXML payload.
2. For HTTPS SSL encryption, obtain the server certicate from the business network. Proceed as follows:
1. Go to buyer.ariba.com or to eldglass.net, respectively.
2. Download the certicate using your browser.
For example, if you are using Internet Explorer, choose View Security Report . Choose View
Certicates. On the Details tab page, choose Copy to File and export the certicate in the Base-64
encoded X.509 format.
3. Import the server certicate into the SAP S/4HANA system using Trust Manager.
4. Double-click the SSL Client SSL Client (Anonymous) node.
Navigate to the Certicate group box and choose Import certicate. Add the imported certicate to the
certicate list by clicking Add to Certicate List.
3. To activate the changes, restart the Internet Communication Manager (ICM) using transaction SMICM and
choose Administration ICM Restart Yes .
4. In the prole of your account in the Ariba Network, select the shared secret authentication method in the
cXML setup.
14.3 Direct Connectivity: SAP S/4HANA as Server
No proxy or reverse proxy is required. The asynchronous inbound application service interfaces are called
either internally in the SAP S/4HANA system or by SAP PI.
14.4 Roles and Authorizations (Ariba Network)
A technical user is required in the SAP S/4HANA system to process messages coming from the Ariba Network.
This user must not have the SAP_ALL authorization. Assign the following roles to this user:
● SAP_ARBFND_INTEGRATION
The authorization object ARBFND_ARB is required to execute reports and to process inbound messages.
This object can be added by assigning the role SAP_ARBFND_INTEGRATION.
● Process Purchase Orders (SAP_MM_PUR_PURCHASEORDER)
This role provides authorization for purchase orders and is required to process incoming messages that
update purchase orders.
● Process Inbound Deliveries (SAP_LE_INB_DEL_PROCESSING).
This role provides authorization for inbound deliveries and is required to process incoming messages that
create inbound deliveries with receiving point.
● Enter Invoices for Verication in the Background (SAP_MM_IV_CLERK_BATCH1)
Security Guide for SAP S/4HANA 1709
Business Network Integration
P U B L I C 599
This role provides authorization to post or park incoming invoice documents in the background.
Alternatively, you can assign any other role that contains the authorization object M_RECH_WRK.
Depending on whether you use direct or mediated connectivity, you also have to assign one of the following
roles:
● For direct connectivity:
Web Service Consumer (SAP_BC_WEBSERVICE_CONSUMER)
This role is required for using Web service protocol to communicate in direct connectivity.
● For mediated connectivity:
Exchange Infrastructure: Service User for Application Systems (SAP_XI_APPL_SERV_USER)
This role is required to communicate through XI protocol in mediated connectivity.
To make sure the corresponding proles are available and active, you must generate the role proles using
transaction PFCG.
14.5 Roles and Authorizations (SAP Fieldglass)
A technical user is required in the SAP S/4HANA system to process messages coming from SAP Fieldglass.
This user must not have the SAP_ALL authorization. Instead, you have to do the following:
1. Create a role that contains the authorization object ARBFND_FG, enter your SAP Fieldglass buyer company
code in the eld
FG_BUY_CC, and assign this role to the technical user.
2. Assign the role Enter Invoices for Verication in the Background (SAP_MM_IV_CLERK_BATCH1) to the
technical user. This role provides authorization to post or park incoming invoice documents in the
background. Alternatively, you can assign any other role that contains the authorization object
M_RECH_WRK.
3. Depending on whether you use direct or mediated connectivity, you also have to assign one of the following
roles:
○ For direct connectivity:
Web Service Consumer (SAP_BC_WEBSERVICE_CONSUMER)
This role is required for using Web service protocol to communicate in direct connectivity.
○ For mediated connectivity:
Exchange Infrastructure: Service User for Application Systems (SAP_XI_APPL_SERV_USER)
This role is required to communicate through XI protocol in mediated connectivity.
To make sure the corresponding proles are available and active, you must generate the role proles using
transaction PFCG.
600
P U B L I C
Security Guide for SAP S/4HANA 1709
Business Network Integration

Important Disclaimers and Legal Information
Hyperlinks
Some links are classied by an icon and/or a mouseover text. These links provide additional information.
About the icons:
● Links with the icon : You are entering a Web site that is not hosted by SAP. By using such links, you agree (unless expressly stated otherwise in your
agreements with SAP) to this:
● The content of the linked-to site is not SAP documentation. You may not infer any product claims against SAP based on this information.
● SAP does not agree or disagree with the content on the linked-to site, nor does SAP warrant the availability and correctness. SAP shall not be liable for any
damages caused by the use of such content unless damages have been caused by SAP's gross negligence or willful misconduct.
● Links with the icon : You are leaving the documentation for that particular SAP product or service and are entering a SAP-hosted Web site. By using such
links, you agree that (unless expressly stated otherwise in your agreements with SAP) you may not infer any product claims against SAP based on this
information.
Beta and Other Experimental Features
Experimental features are not part of the ocially delivered scope that SAP guarantees for future releases. This means that experimental features may be changed by
SAP at any time for any reason without notice. Experimental features are not for productive use. You may not demonstrate, test, examine, evaluate or otherwise use
the experimental features in a live operating environment or with data that has not been suciently backed up.
The purpose of experimental features is to get feedback early on, allowing customers and partners to inuence the future product accordingly. By providing your
feedback (e.g. in the SAP Community), you accept that intellectual property rights of the contributions or derivative works shall remain the exclusive property of SAP.
Example Code
Any software coding and/or code snippets are examples. They are not for productive use. The example code is only intended to better explain and visualize the syntax
and phrasing rules. SAP does not warrant the correctness and completeness of the example code. SAP shall not be liable for errors or damages caused by the use of
example code unless damages have been caused by SAP's gross negligence or willful misconduct.
Gender-Related Language
We try not to use gender-specic word forms and formulations. As appropriate for context and readability, SAP may use masculine word forms to refer to all genders.
Videos Hosted on External Platforms
Some videos may point to third-party video hosting platforms. SAP cannot guarantee the future availability of videos stored on these platforms. Furthermore, any
advertisements or other content hosted on these platforms (for example, suggested videos or by navigating to other videos hosted on the same site), are not within
the control or responsibility of SAP.
Security Guide for SAP S/4HANA 1709
Important Disclaimers and Legal Information
P U B L I C 601

www.sap.com/contactsap
© 2020 SAP SE or an SAP aliate company. All rights reserved.
No part of this publication may be reproduced or transmitted in any form
or for any purpose without the express permission of SAP SE or an SAP
aliate company. The information contained herein may be changed
without prior notice.
Some software products marketed by SAP SE and its distributors
contain proprietary software components of other software vendors.
National product specications may vary.
These materials are provided by SAP SE or an SAP aliate company for
informational purposes only, without representation or warranty of any
kind, and SAP or its aliated companies shall not be liable for errors or
omissions with respect to the materials. The only warranties for SAP or
SAP aliate company products and services are those that are set forth
in the express warranty statements accompanying such products and
services, if any. Nothing herein should be construed as constituting an
additional warranty.
SAP and other SAP products and services mentioned herein as well as
their respective logos are trademarks or registered trademarks of SAP
SE (or an SAP aliate company) in Germany and other countries. All
other product and service names mentioned are the trademarks of their
respective companies.
Please see https://www.sap.com/about/legal/trademark.html for
additional trademark information and notices.
THE BEST RUN
