
IT Commercial Price List
ManTech International Corporation
March 2024
Table of Contents
ADVANCED CYBER TRAINING PROGRAM (ACTP)............................................................................................................................3
LABOR CATEGORY RATES AND DESCRIPTIONS................................................................................................................. 5
PORTAL CONTENT MANAGEMENT SERVICES................................................................................................................... 14
INTRODUCTION TO THE ANDROID INTERNALS COURSE.................................................................................................15
INTRODUCTION TO ANDROID PROGRAMMING................................................................................................................. 17
LINUX CNO PROGRAMMER COURSE..................................................................................................................................19
WINDOWS CNO PROGRAMMER SYLLABUS....................................................................................................................... 21
COMMERCIAL SOFTWARE & SERVICES.......................................................................................................................................... 24
BIDS - OTA Lifecycle Management & Evaluation Tool.............................................................................................................25
DECISIONPOINT™ - FAR-based RFP Evaluation Tool...........................................................................................................26
DOCUMENT DETECTIVE - File Sanitization & Inspection Tool.............................................................................................. 28
INFINISTRUCTURE™ - Hyper-realistic Hypervisor.................................................................................................................32
ONTARGET® - RFP Response Evaluation Tool for Industry...................................................................................................34
SENTRIS® - Data Classification Labeling & Access Control................................................................................................... 35
CONTACT INFORMATION....................................................................................................................................................................41
IT Commercial Price List - March 2024

ADVANCED CYBER TRAINING PROGRAM (ACTP)
ADVANCED CYBER TRAINING PROGRAM (ACTP)
ManTech’s ADVANCED CYBER TRAINING PROGRAM (ACTP) provides tailored, industry-leading training on
Computer Network Operations Programming. ACTP began in 2009 as a ManTech Independent Research and
Development project for internal training and is now a world-class cyber training program.
ACTP exclusively trains ManTech employees and US Government personnel within our military and intelligence
community. ACTP’s course portfolio provides mission-essential training in Windows, Linux, and Android
environments to industry customers. Course delivery is a combination of group lecture, one-on-one instruction,
and experiential learning lab exercises. The Linux CNO and Windows CNO Programmer Courses are intensive,
hands-on courses focused on developing experienced systems programmers into CNO professionals on the
Linux and Windows platforms. These classes are formatted to combine lectures and demonstrations with
practical assignments.
An ACTP student in the CNO Programmer Course develops technologies to defend, attack and exploit
computer networks. This requires a deep understanding of operating systems and software internals, combined
with advanced skills in C, assembly, networking, and reverse engineering. It also requires specialized
knowledge and experience that cannot be gained through conventional education or programming work.
Students who complete either CNO Programmer course will return to their team or report for duty on-contract
ready to participate in and support the full CNO tool development process.
ACTP instructors perform work on ManTech contract assignments and instruct solely in their areas of subject
matter expertise. Instructors are selected and screened based on their technical knowledge, industry
experience, and ability to provide instruction in both group and one-on-one training environments.
ManTech's instructors perform this work professionally, continuing to support our customer’s most critical
missions as they bring those experiences to the classroom.
For additional information on ACTP or to connect with a member of the team, please email
ACTP@ManTech.com.
IT Commercial Price List - March 2024
3 of 41

ADVANCED CYBER TRAINING PROGRAM (ACTP)
TERMS & CONDITIONS
The terms and conditions outlined below govern the ManTech Advanced Cyber Training Program (ACTP) training
courses offered by ManTech Advanced Systems International, Inc. These terms and conditions shall be
incorporated into each order for any of the ACTP training courses.
1. ACCEPTANCE OF TERMS. ManTech’s delivery of the ACTP Training Program is expressly conditioned on
Buyer's acceptance of all the terms and conditions set forth herein. No change, modification or revision of these
terms and conditions shall be valid unless agreed to in writing by ManTech. In the event ManTech accepts
Buyer’s purchase order/ credit card/ or any other form of payment for the training services, the parties
acknowledge that these terms and conditions shall be incorporated into and made a part of each order.
2. PAYMENT. Payment for an Advanced Cyber Training Class is due in full after completion of the course.
Payment can be made via purchase order, check or credit card unless another mutually agreed upon payment plan
has been agreed to by the parties.
3. INVOICES. ManTech will invoice for the ACTP in accordance with ManTech’s standard invoicing
procedures or in accordance with a mutually agreed upon payment schedule.
4. REPRODUCTION RIGHTS. The number of students permitted to attend the course and view the training
materials is specified on the quotation. Buyer shall ensure that no additional Buyer employees receive access to
the course materials, and shall be liable for an additional course fee for each unauthorized copy made or additional
employee permitted to access the materials. Copyright law prohibits unauthorized copying of copyrighted
materials. Buyer and all of Buyer’s students that take the training shall not make or use any unauthorized copies of
software or copyrighted material or forward newsletters or other materials (whether electronic or hard-copy) in
violation of license restrictions. Buyer acknowledges and shall comply with all license and copyright restrictions
pertaining to all software and copyrighted material presented and or received in the ACTP training program. The
ManTech ACTP course materials constitute proprietary ManTech information and content. The materials are
copyrighted works of ManTech and third parties.
5. TITLE TO PROGRAM MATERIALS. ManTech claims and holds title to all documents and materials
furnished to the Buyer for use in connection with the training. Buyer shall not disclose such documents or materials
to any person, firm or corporation. The Buyer shall, upon ManTech’s request, promptly return all such documents
and materials to ManTech.
6. NONDISCLOSURE OF TRADE SECRETS. Buyer and all of Buyer’s students agree to keep ManTech's
trade secrets, whether or not prepared or developed by ManTech, in the strictest confidence. Buyer will not
disclose such secrets to anyone outside ManTech without ManTech's prior written consent. Nor will Buyer make
use of any ManTech trade secrets for their own purposes or the benefit of anyone other than ManTech without
ManTech's prior written consent.
7. NON-TRANSFER OF RIGHTS. Except for the limited rights set forth herein, no right, title, or license,
express or implied, under any patent, copyright, trade secret, and/or other intellectual property proprietary right is
granted hereunder. All rights not expressly granted by this Agreement are retained by ManTech.
8. EXPORT CONTROL COMPLIANCE FOR FOREIGN PERSONS. Buyer shall comply with U.S. State
Department (International Traffic in Arms Regulations (ITAR)) and Commerce Department (Export Administration
Regulations (EAR)), as well as Industrial Security Requirements. Buyer shall not provide a foreign person (a
person who is not a U.S. citizen or permanent resident or a U.S. citizen employee of a foreign owned company not
incorporated to do business in the U.S.) access to export controlled technology without proper governmental
authorization under the ITAR or EAR, as applicable. Accordingly, Buyer certifies that it will not permit a foreign
person to receive the training without the prior written consent of ManTech. Any foreign person’s access to
ManTech’s or ManTech’s customer’s facilities and computer networks will be restricted and controlled to ensure the
foreign person does not have access to ITAR or EAR controlled hardware, technical data, or software/code other
than as specifically authorized by the U.S. Department of State or Department of Commerce, as applicable.
IT Commercial Price List - March 2024
4 of 41
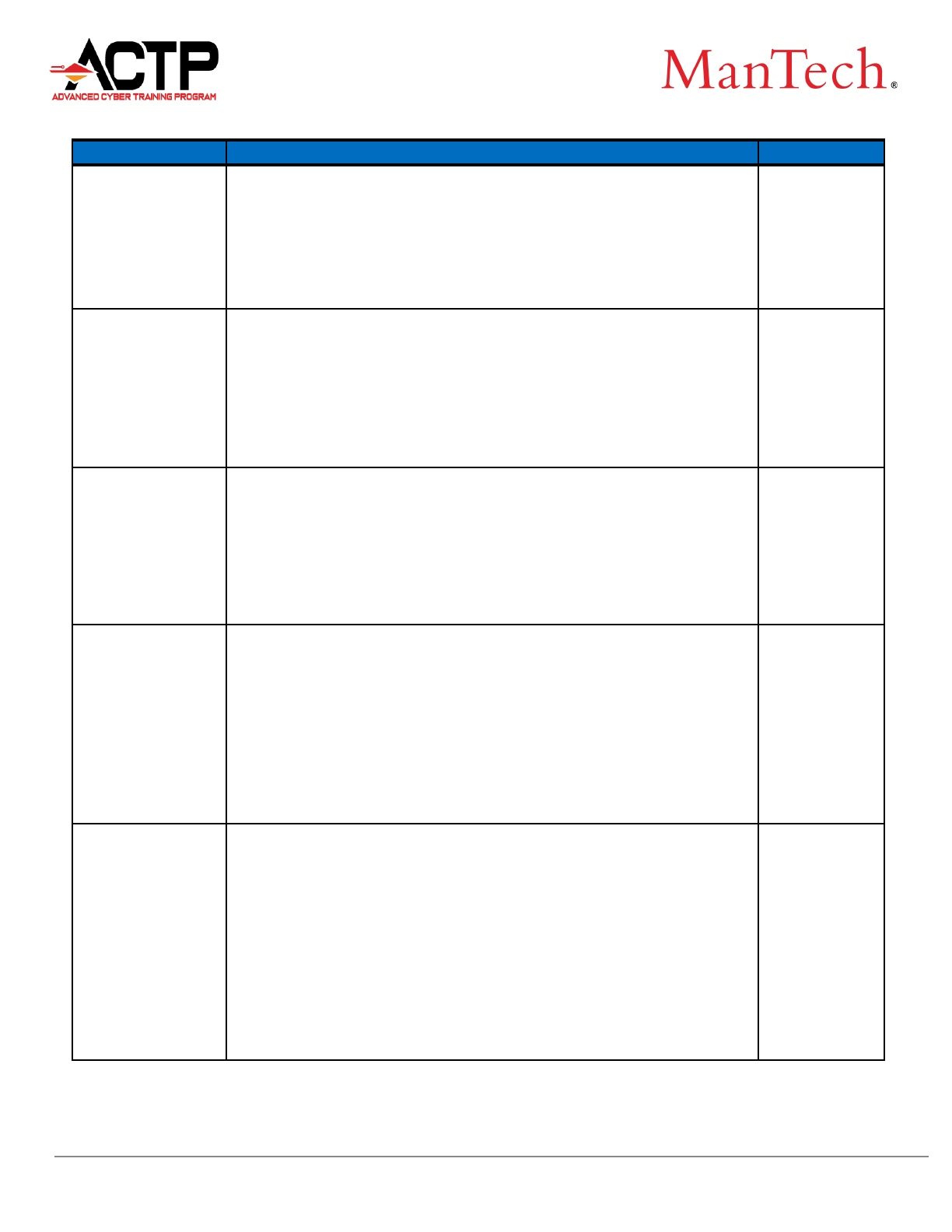
LABOR CATEGORY RATES AND DESCRIPTIONS
Labor Category
Labor Category Description
Rate
Cyber Security
Operations
Specialist 1
Performs analysis of enterprise defensive technologies to include COTS
and GOTS products / point solutions. Conducts analysis of security
incidents and/or malware incidents/outbreaks. Performs cyber threat
analysis and assesses organizations' cyber risk posture. Provides
security engineering consulting services related to enterprise cyber
defensive tools and technologies. Bachelor's degree preferred, but not
required. Specialized training in cyber defense technologies required.
$110.00
Cyber Security
Operations
Specialist 2
Performs analysis of enterprise defensive technologies to include COTS
and GOTS products / point solutions. Conducts analysis of security
incidents and/or malware incidents/outbreaks. Performs cyber threat
analysis and assesses organizations' cyber risk posture. Provides
security engineering consulting services related to enterprise cyber
defensive tools and technologies. Bachelor's degree preferred plus one
year relevant experience. Specialized training in cyber defense
technologies required.
$125.00
Cyber Security
Operations
Specialist 3
Performs analysis of enterprise defensive technologies to include COTS
and GOTS products / point solutions. Conducts analysis of security
incidents and/or malware incidents/outbreaks. Performs cyber threat
analysis and assesses organizations' cyber risk posture. Provides
security engineering consulting services related to enterprise cyber
defensive tools and technologies. Bachelor's degree preferred plus two
years relevant experience. Specialized training in cyber defense
technologies required.
$150.00
Cyber Security
Operations
Specialist 4
Performs analysis of enterprise defensive technologies to include COTS
and GOTS products / point solutions. Conducts analysis of security
incidents and/or malware incidents/outbreaks. Performs cyber threat
analysis and assesses organizations' cyber risk posture. Provides
security engineering consulting services related to enterprise cyber
defensive tools and technologies. Bachelor's degree preferred plus 4
years relevant experience. Relevant product or security certification can
substitute for 4 years experience. Specialized training in cyber defense
technologies required.
$175.00
Cyber Security
Operations
Specialist 5
Performs analysis of enterprise defensive technologies to include COTS
and GOTS products / point solutions. Conducts analysis of security
incidents and/or malware incidents/outbreaks. Performs cyber threat
analysis and assesses organizations' cyber risk posture. Provides
security engineering consulting services related to enterprise cyber
defensive tools and technologies. Bachelor's degree required plus 4
years relevant experience. Master's degree may be substituted for 4
years of experience. Relevant product or security certification may be
substituted for 4 years experience. An additional 6 years of relevant
experience may be substituted for a Bachelor's degree. Specialized
training in cyber defense technologies required.
$200.00
IT Commercial Price List - March 2024
5 of 41

Labor Category
Labor Category Description
Rate
Cyber Security
Operations
Specialist 6
Performs analysis of enterprise defensive technologies to include COTS and GOTS
products / point solutions. Conducts analysis of security incidents and/or malware
incidents/outbreaks. Performs cyber threat analysis and assesses organizations'
cyber risk posture. Provides security engineering consulting services related to
enterprise cyber defensive tools and technologies. Bachelor's degree required plus
6 years relevant experience. Master's degree may be substituted for 4 years of
experience. Relevant product or security certification may be substituted for 4 years
experience. An additional 6 years of relevant experience may be substituted for a
Bachelor's degree. Specialized training in cyber defense technologies required.
$225.00
Cyber Security
Operations
Specialist 7
Performs analysis of enterprise defensive technologies to include COTS and GOTS
products / point solutions. Conducts analysis of security incidents and/or malware
incidents/outbreaks. Performs cyber threat analysis and assesses organizations'
cyber risk posture. Provides security engineering consulting services related to
enterprise cyber defensive tools and technologies. Conducts network and memory
forensics analysis and is skilled at conducting reverse engineering of malicious
binaries. Bachelor's degree required plus 8 years relevant experience. Master's
degree may be substituted for 4 years of experience. Relevant product or security
certification may be substituted for 4 years experience. An additional 6 years of
relevant experience may be substituted for a Bachelor's degree. Specialized training
in cyber defense technologies required.
$250.00
Cyber Security
Operations
Specialist 8
Performs analysis of enterprise defensive technologies to include COTS and GOTS
products / point solutions. Conducts analysis of security incidents and/or malware
incidents/outbreaks. Performs cyber threat analysis and assesses organizations'
cyber risk posture. Provides security engineering consulting services related to
enterprise cyber defensive tools and technologies. Conducts network and memory
forensics analysis and is skilled at conducting reverse engineering of malicious
binaries. Bachelor's degree required plus 10 years relevant experience. Master's
degree may be substituted for 4 years of experience. Relevant product or security
certification may be substituted for 4 years experience. An additional 6 years of
relevant experience may be substituted for a Bachelor's degree. Specialized
training in cyber defense technologies required.
$300.00
Cyber Security
Operations
Specialist 9
Performs analysis of enterprise defensive technologies to include COTS and GOTS
products / point solutions. Conducts analysis of security incidents and/or malware
incidents/outbreaks. Performs cyber threat analysis and assesses organizations'
cyber risk posture. Provides security engineering consulting services related to
enterprise cyber defensive tools and technologies. Conducts network and memory
forensics analysis and is skilled at conducting reverse engineering of malicious
binaries. Bachelor's degree required plus 12 years relevant experience. Master's
degree may be substituted for 4 years of experience. Relevant product or security
certification may be substituted for 4 years experience. An additional 6 years of
relevant experience may be substituted for a Bachelor's degree. Specialized
training in cyber defense technologies required.
$350.00
Cyber Security
Operations
Specialist 10
Performs analysis of enterprise defensive technologies to include COTS and GOTS
products / point solutions. Conducts analysis of security incidents and/or malware
incidents/outbreaks. Performs cyber threat analysis and assesses organizations'
cyber risk posture. Provides security engineering consulting services related to
enterprise cyber defensive tools and technologies. Conducts network and memory
forensics analysis and is skilled at conducting reverse engineering of malicious
binaries. Bachelor's degree required plus 14 years relevant experience. Master's
degree may be substituted for 4 years of experience. Relevant product or security
certification may be substituted for 4 years experience. An additional 6 years of
relevant experience may be substituted for a Bachelor's degree. Specialized
training in cyber defense technologies required.
$400.00
IT Commercial Price List - March 2024
6 of 41
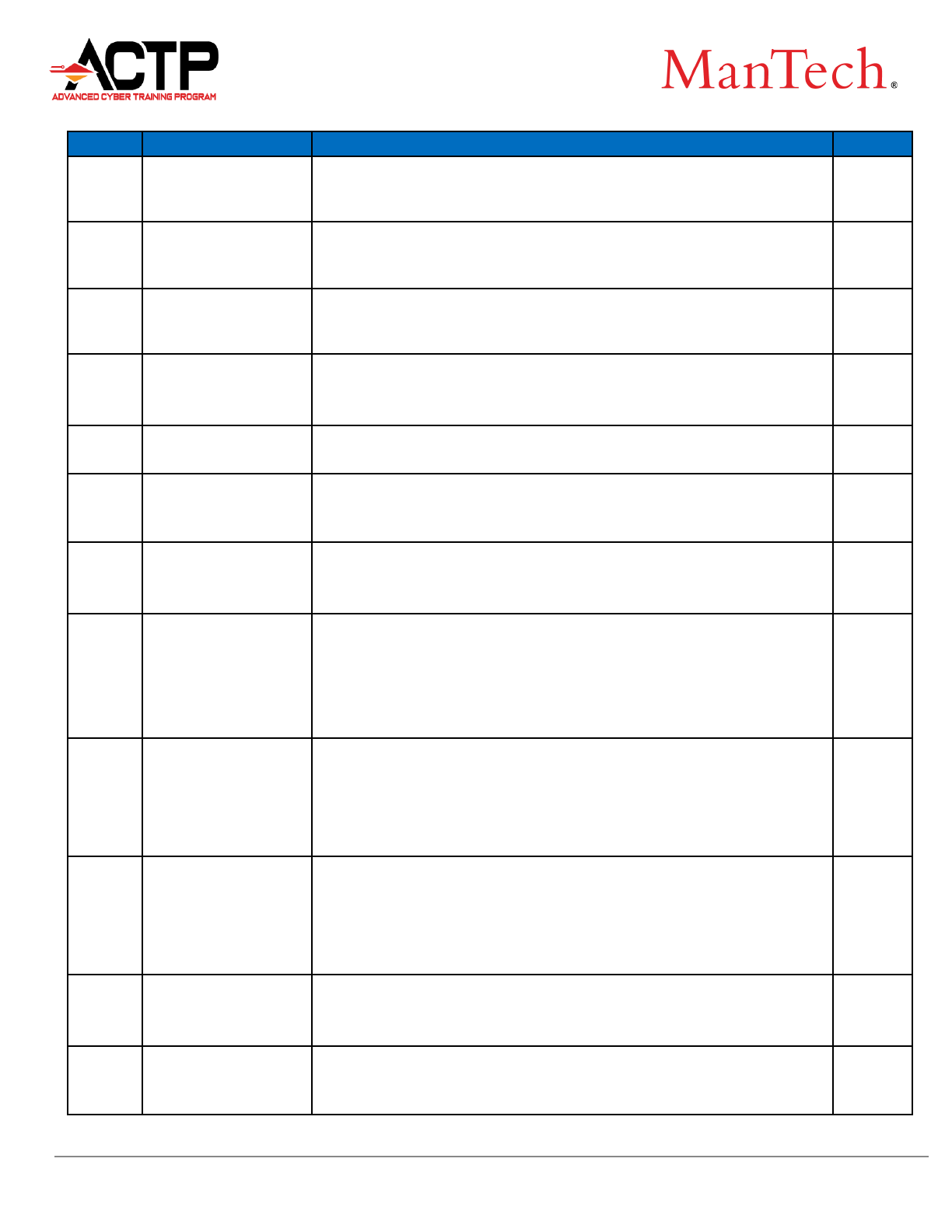
Code
Labor Category
Labor Category Description
Rate
IT-1
IT Scientist 6
Employees in this category should have combined education and
experience as follows: B.S. + 20 years of experience M.S. + 15
years of experience Ph.D. + 10 years of experience.
$493.00
IT-2
IT Scientist 5
Employees in this category should have combined education and
experience as follows: B.S. + 15 years of experience M.S. + 10 years
of experience
$457.00
IT-3
IT Scientist 4
Employees in this category should have combined education and
experience as follows: B.S. + 10 years of experience M.S. + 6 years of
experience
$426.00
IT-4
IT Scientist 3
Employees in this category should have combined education and
experience as follows: B.S. + 6 years of experience M.S. + 3
years of experience Ph.D. + 2 years of experience.
$333.00
IT-5
IT Scientist 2
Employees in this category should have combined education and
experience as follows: B.S. + 4 years of experience
$316.00
IT-6
IT Scientist 1
Bachelor's Degree in Mathematics, Physics, Chemistry, or a related
field. A minimum of 2 years related experience involving application of
scientific principles. Masters Degree preferred.
$274.00
IT-7
Corporate IT
Staff Officers
Bachelor’s or Master’s Degree in Business Administration, a related
discipline or equivalent experience of nine or more years in positions of
increasing responsibility including supervisory/management experience.
$340.00
IT-8
Executive IT
Director
Bachelor's Degree plus seven years of relevant technical,
professional or management positions or 11.5 years of similar
experience. Typically advances through one of the professional areas
supervised and is conversant with the spectrum of professional and
technical disciplines represented in the organization. Must include
previous supervisory/management experience.
$304.00
IT-9
Technical IT Director
Bachelor's Degree plus five years in relevant technical, professional or
management positions or 8.5 years of related experience. Typically
advances through performance in and management of a discipline
within the area which is supervised. Should have a working knowledge
of other disciplines represented in the department. Background must
include supervisory/management experience.
$223.00
IT-10
IT Director
Bachelor's Degree plus two years in relevant technical, professional or
management positions. Typically advances through performance in and
management of a discipline within the area which is supervised. Should
have a working knowledge of other disciplines represented in the
department. Background must include supervisory/management
experience.
$187.00
IT-11
Lead Functional IT
Analyst
Bachelor’s or Master's Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Ten years
of increasingly complex and responsible systems analysis experience.
$232.00
IT-12
Senior Functional IT
Analyst
Bachelor’s/Master’s Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Six years
of increasingly complex and responsible systems analysis experience.
$164.00
IT Commercial Price List - March 2024
7 of 41
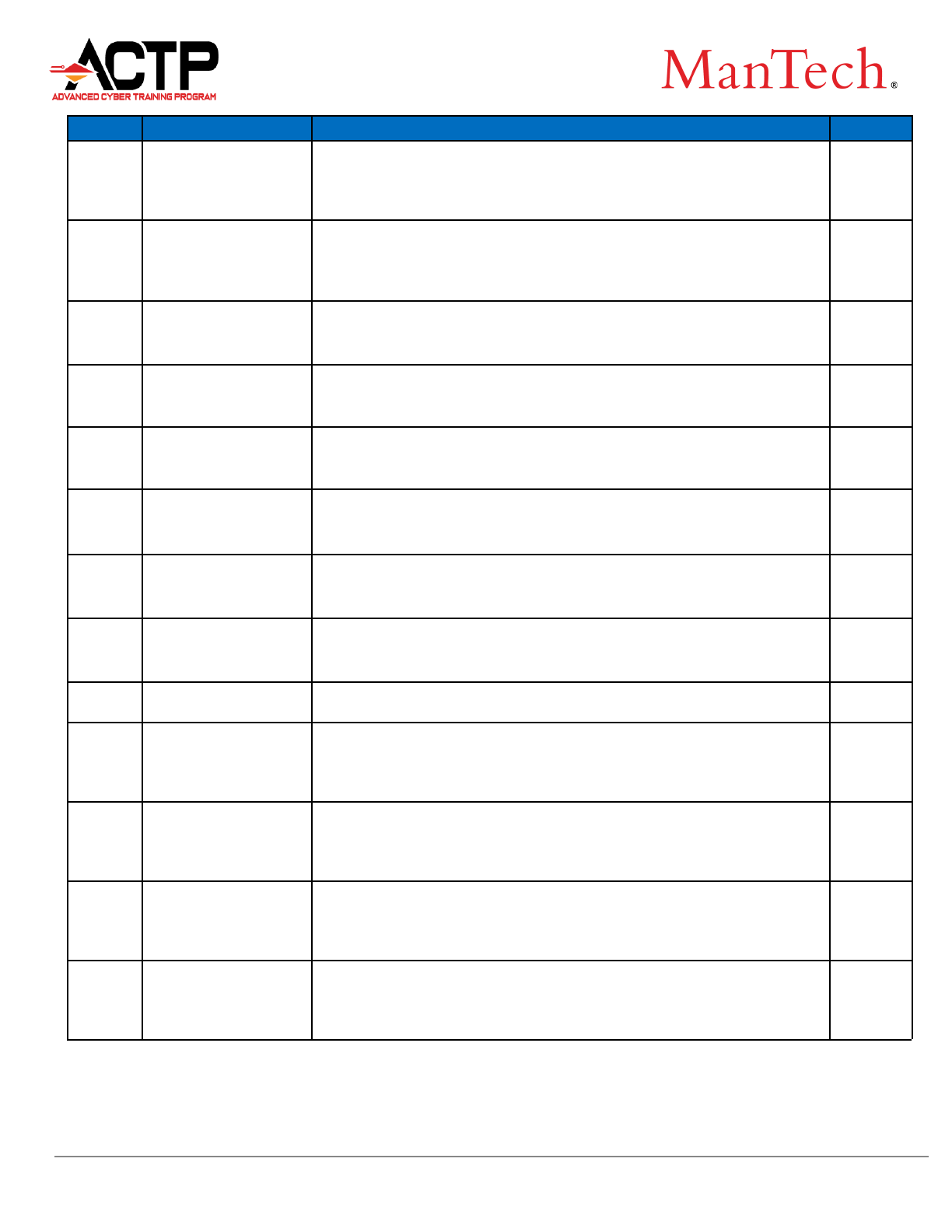
Code
Labor Category
Labor Category Description
Rate
IT-13
Principal IT Systems
Architect
Master’s Degree or Ph.D. in Computer Science, a related field or
equivalent experience. Ten or more years of applicable progressively
complex system design experience including hardware/software
integration of complex systems.
$262.00
IT-14
Senior IT Systems
Architect
Master’s Degree in Computer Science, a related field or equivalent
experience. Eight or more years of applicable progressively complex
systems design experience, including hardware/software integration of
complex systems.
$232.00
IT-15
Staff IT Systems
Architect
Bachelor's Degree (Master’s preferred) in Computer Science, a
related field or equivalent experience. Five years system design
experience, including hardware/software integration.
$177.00
IT-16
IT Engineer -
Software 6
Master’s Degree or Ph.D. in Computer Science, a related field or
equivalent experience. Ten or more years of progressively complex
software design experience.
$255.00
IT-17
IT Engineer -
Software 5
Master’s/Bachelor's Degree in Computer Science, a related field or
equivalent experience. Eight or more years of applicable,
progressively more complex software design experience.
$232.00
IT-18
IT Engineer -
Software 4
Master’s/Bachelor's Degree in Computer Science, a related field or
equivalent experience. Six or more years of applicable, progressively
more complex software design experience.
$207.00
IT-19
IT Engineer -
Software 3
Master’s/Bachelor's Degree in Computer Science, a related field or
equivalent experience. Four or more years of applicable
software design experience.
$194.00
IT-20
IT Engineer -
Software 2
Bachelor's Degree in Computer Science, a related field or
equivalent experience. Two years applicable software design
experience.
$188.00
IT-21
IT Engineer -
Software 1
One year applicable software design experience.
$110.00
IT-22
IT Systems -
Analyst 6
Bachelor’s or Master's Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Ten
years of increasingly complex and responsible systems analysis
experience.
$243.00
IT-23
IT Systems -
Analyst 5
Bachelor’s/Master’s Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Eight
years of increasingly complex and responsible systems analysis
experience.
$213.00
IT-24
IT Systems -
Analyst 4
Bachelor’s/Master’s Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Six
years of increasingly complex and responsible systems analysis
experience.
$182.00
IT-25
IT Systems -
Analyst 3
Bachelor’s/Master’s Degree in Computer Science, Management
Information Systems, a related field or equivalent experience.
Four years of increasingly complex and responsible systems analysis
experience.
$152.00
IT Commercial Price List - March 2024
8 of 41
Code
Labor Category
Labor Category Description
Rate
IT-26
IT Systems -
Analyst 2
Bachelor's Degree in Computer Science, Management
Information Systems, or related field or equivalent experience.
$134.00
IT-27
IT Systems -
Analyst 1
Two years of systems analysis experience.
$90.00
IT-28
Lead IT Analyst –
Systems
Bachelor’s or Master’s Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Nine
years of increasingly complex and responsible systems analysis
experience.
$201.00
IT-29
Senior IT Analyst -
Systems
Bachelor’s/Master’s Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Six
years of increasingly complex and responsible systems analysis
experience.
$177.00
IT-30
Senior IT Applications
Engineer
Master’s/Bachelor’s Degree in Computer Science, a related field or
equivalent experience. Eight or more years of applicable,
progressively more complex software design experience.
$218.00
IT-31
Staff IT Application
Engineer
Master’s/Bachelor’s Degree in Computer Science, a related field or
equivalent experience. Seven or more years of applicable,
progressively more complex software design experience.
$188.00
IT-32
Junior IT
Application Engineer
Master’s/Bachelor's Degree in Computer Science, a related field or
equivalent experience. Five or more years of software design
experience.
$152.00
IT-33
Senior IT Analyst -
Programming
Requires a bachelor's degree or equivalent experience and six
or more years of related experience.
$164.00
IT-34
Staff IT Analyst -
Programming
Requires a bachelor's degree or equivalent experience and
four- five years of related experience.
$146.00
IT-35
Assoc. IT Analyst -
Programming
Requires a bachelor's degree or equivalent experience and one-
three years related experience.
$97.00
IT-36
IT Engineer -
Systems 6
Master’s Degree or Ph.D. in Computer Science, a related field or
equivalent experience. Fifteen or more years of applicable
progressively complex system design experience including
hardware/software integration of complex systems.
$274.00
IT-37
IT Engineer -
Systems 5
Master’s Degree in Computer Science, a related field or equivalent
experience. Eight or more years of applicable progressively complex
systems design experience, including hardware/software integration of
complex systems.
$262.00
IT-38
IT Engineer -
Systems 4
Bachelor's degree in computer science, a related field, or
equivalent experience. Eight of more years of applicable systems
design experience, including hardware/software integration.
$252.00
IT-39
IT Engineer -
Systems 3
Bachelor's degree in computer science, a related field, or equivalent
experience. Six of more years of applicable systems design
experience, including hardware/software integration.
$245.00
IT-40
IT Engineer -
Systems 2
Bachelor's Degree (Master’s preferred) in Computer Science, a
related field or equivalent experience. Five years system design
experience, including hardware/software integration.
$213.00
IT-41
IT Engineer -
Systems 1
Bachelor's Degree in Computer Science, a related field or
equivalent experience. Two years system design experience including
hardware/software integration experience.
$158.00
IT Commercial Price List - March 2024
9 of 41
Code
Labor Category
Labor Category Description
Rate
IT-42
Lead IT Analyst –
Database Design
Bachelor’s or Master's Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Eight
years of progressively responsible database design and implementation
experience.
$218.00
IT-43
Senior IT Analyst -
Database Design
Bachelor’s/Master's Degree in Computer Science, Management
Information Systems, a related field or equivalent experience. Six years
of progressively responsible database design and implementation
experience.
$164.00
IT-44
Staff IT Analyst -
Database Design
Bachelor’s/Master's Degree in Computer Science, Management
Information Systems, a related field or equivalent experience.
Two years related database design and implementation experience.
$110.00
IT-45
Staff IT Data
Entry Clerk
Normally requires at least eighteen months of experience.
$66.00
IT-46
Senior IT Analyst -
Training
Bachelor's Degree or equivalent experience. Five years of related
experience.
$177.00
IT-47
Staff IT Analyst -
Training
Bachelor's Degree or equivalent experience. Two to five years of related
experience.
$146.00
IT-48
Staff IT Software
Trainer
Bachelor's Degree or equivalent experience. Four years of related
experience.
$146.00
IT-49
Technical IT Specialist -
Engineering
Technical training equal to an Associates Degree and six years of
related technical experience.
$146.00
IT-50
Senior IT Technician -
Engineering
Requires technical training or equivalent experience and four to five
years experience as an engineering technician.
$121.00
IT-51
IT Network
Engineer 6
Master’s Degree in Computer Science, a related field or equivalent
experience. Eight or more years of applicable progressively
complex systems design experience, including hardware/software
integration of complex systems.
$258.00
IT-52
IT Network
Engineer 5
Bachelor's Degree in Computer Science, a related field or equivalent
experience. Six or more years of applicable progressively complex
systems design experience, including hardware/software integration of
complex systems.
$245.00
IT-53
IT Network
Engineer 4
Bachelor's Degree (Masters preferred) in Computer Science, a related
field or equivalent experience. Five years system design experience,
including hardware/software integration.
$188.00
IT-54
IT Network
Engineer 3
Bachelor's Degree in Computer Science, a related field or equivalent
experience. Two years system design experience including
hardware/software integration experience.
$134.00
IT-55
IT Network
Engineer 2
Bachelor's Degree in Computer Science, a related field or equivalent
experience.
$104.00
IT-56
IT Network
Engineer 1
One year experience required.
$90.00
IT-57
Senior IT Manager -
LAN Admin.
Requires a bachelor's degree and two years of related experience.
Additional experience may be substituted for the degree.
$121.00
IT Commercial Price List - March 2024
10 of 41
Code
Labor Category
Labor Category Description
Rate
IT-58
Staff IT
Technician - Writing
Bachelor's Degree in an applicable technical field or equivalent
experience and excellent written communication skills. Two years
technical writing and editing experience.
$110.00
IT-59
Secretary/Admin
IT Asst - 3
Normally requires three years of relevant work experience and a
high school diploma.
$121.00
IT-60
Secretary/Admin
IT Asst - 2
Normally requires one year of relevant work experience and a high
school diploma.
$90.00
IT-61
Secretary/Admin
IT Asst - 1
Requires no experience.
$50.00
IT-62
IT Project
Engineer - 7
Bachelor's Degree in Engineering, or equivalent. Seven years of project
engineering experience.
$237.00
IT-63
IT Project
Engineer - 6
Bachelor's Degree (Masters preferred) in engineering or a related
field. Four years of engineering experience.
$199.00
IT-64
IT Project
Engineer - 5
Bachelor's degree in engineering or equivalent experience. Three years
of engineering experience.
$175.00
IT-65
IT Project
Engineer - 4
Bachelor's degree in engineering and two years of equivalent
engineering experience.
$158.00
IT-66
IT Project
Engineer - 3
Bachelor's degree in engineering and one year of equivalent engineering
experience.
$146.00
IT-67
IT Project
Engineer - 2
High School Diploma and four years of equivalent engineering
experience.
$135.00
IT-68
IT Project
Engineer - 1
One year engineering experience.
$115.00
IT-69
Computer Forensics
and Intrusion
Task Manager
Requires a bachelor's degree in a related field. Ten (10) years of
increasing responsibilities in IA technical guidance and leadership.
Seven (7) years in computer intrusion analysis and investigation,
intrusion operations and detection; computer network
surveillance/monitoring; vulnerability assessments; hacker
methodologies and techniques; computer network exploitation
methodology and techniques; computer attack and exploitation
methodologies and techniques; firewall exploitation. Seven (7) years in
network protocols; network devices; computer security devices;
multiple operating systems; secure architecture, methodologies, and
tools; hardware and software configurations; and network LAN/WAN
system administration in support of computer intrusion operations.
$609.00
IT-70
Computer
Forensics and
Intrusion Principal
Analyst
Requires a bachelor's degree in a related field. Eight (8) years of
increasing responsibilities in IA technical guidance and leadership. Five
(5) years in computer intrusion analysis and investigation, intrusion
operations and detection; computer network surveillance/monitoring;
vulnerability assessments; hacker methodologies and techniques;
computer network exploitation methodology and techniques; computer
attack and exploitation methodologies and techniques; firewall
exploitation. Five (5) years in network protocols; network devices;
computer security devices; multiple operating systems; secure
architecture, methodologies, and tools; hardware and software
configurations; and network LAN/WAN system administration in support
of computer intrusion operations.
$542.00
IT Commercial Price List - March 2024
11 of 41
Code
Labor Category
Labor Category Description
Rate
IT-71
Computer
Forensics and
Intrusion Senior
Analyst
Requires a bachelor's degree in a related field. Five (5) years experience
in IA. Demonstrated ability to work independently or under only general
supervision. Three (3) years in computer intrusion analysis and
investigation, intrusion operations and detection; computer network
surveillance/monitoring; vulnerability assessments; hacker
methodologies and techniques; computer network exploitation
methodology and techniques; computer attack and exploitation
methodologies and techniques; firewall exploitation. Three (3) years in
network protocols; network devices; computer security devices; multiple
operating systems; secure architecture, methodologies, and tools;
hardware and software configurations; and network LAN/WAN system
administration in support of computer intrusion operations.
$432.00
IT-72
Computer
Forensics and
Intrusion Staff
Analyst
Requires a bachelor's degree in a related field. Two (2) years experience
in IA to include computer network surveillance/monitoring; vulnerability
assessments; network protocols; network devices; computer security
devices; hardware and software configurations; and network LAN/WAN
system administration in support of information assurance.
$322.00
IT-73
Computer
Forensics and
Intrusion Junior
Analyst
One (1) year of experience in IA to include computer network
surveillance/monitoring; vulnerability assessments; network protocols;
network devices; computer security devices; hardware
and software configurations; and network LAN/WAN system
administration in support of information assurance.
$213.00
IT-74
IT Information
Assurance
Specialist
Bachelor's degree preferred. Ten years of information security
experience
$182.00
IT-75
IT Acquisition
Specialist
Bachelor's degree and 10 years of experience providing technology
solutions for acquisition management.
$232.00
IT-76
Database
Administrator
Bachelor's degree preferred. Two or more years of experience
administering databases to include testing backups, data integrity, and
ensuring maximum uptime.
$171.00
IT-77
IT Analyst 6
Bachelor's degree preferred. Seven years of experience providing the
highest authoritative analytic leadership and consultation.
$292.00
IT-78
IT Analyst 5
Bachelor's degree preferred. Six years of experience providing the
highest authoritative analytic leadership and consultation.
$263.00
IT-79
IT Analyst 4
Bachelor's degree preferred. Five years of experience providing the
highest authoritative analytic leadership and consultation.
$234.00
IT-80
IT Analyst 3
Bachelor's degree preferred. Four years of experience providing the
highest authoritative analytic leadership and consultation.
$205.00
IT-81
IT Analyst 2
Bachelor's degree preferred. Two years of experience providing skilled
analytic leadership and consultation.
$182.00
IT-82
IT Analyst 1
High School and three years of relevant experience. Assists senior
analysts in providing analysis and consultation.
$152.00
IT-83
Documentation
Specialist 2
Bachelor's degree preferred. One year experience developing
drafts and finalizing information technology documentation.
$129.00
IT Commercial Price List - March 2024
12 of 41
Code
Labor Category
Labor Category Description
Rate
IT-84
Documentation
Specialist 1
High School and three years of relevant experience. Develops drafts
and finalizes information technology documentation.
$90.00
IT-85
Project Administration 5
Bachelor's degree preferred. Four years experience preparing project
management administrative plans and reports.
$158.00
IT-86
Project Administration 4
Bachelor's degree preferred. Three years experience preparing project
management administrative plans and reports.
$146.00
IT-87
Project Administration 3
Bachelor's degree preferred. Two years experience preparing project
management administrative plans and reports.
$123.00
IT-88
Project Administration 2
High school and three years of relevant experiences. Assists in
preparing project management administrative plans and reports.
$111.00
IT-89
Project Administration 1
High school and two years of relevant experiences. Assists in preparing
project management administrative plans and reports.
$87.00
IT-90
System Intern
Performs general entry level information technology support duties
under direct supervision.
$50.00
IT-91
Risk Mgmt. Specialist
Bachelor's degree required. Five years of experience in identifying
critical information that must be protected, performing
risk assessments of client activities using proprietary tools, and
developing mitigation measures.
$146.00
IT-92
Sr. Risk Mgmt.
Specialist
Bachelor's degree required. Ten years of experience in identifying
critical information that must be protected, performing risk assessments
of client activities using proprietary tools, and developing mitigation
measures. May provide security awareness, education and training.
$171.00
IT-93
Sr. Info. Sys. Risk
Mgmt Analyst
Bachelor's degree required. Ten years experience performing system
security analyses including security audits, evaluations, and risk
assessments of complex operational data processing communications
systems and facilities and provide recommendations for countering
detected vulnerabilities
$182.00
IT-94
Principal Info. Sys. Risk
Mgmt Analyst
Bachelor's degree required. Thirteen years experience performing
system security analyses including security audits, evaluations, and risk
assessments of complex operational data processing communications
systems and facilities and provide recommendations for countering
detected vulnerabilities
$207.00
IT-95
Principal Risk
Mgmt. Analyst
Bachelor's degree required. Thirteen years of experience in
identifying critical information that must be protected, performing risk
assessments of client activities using proprietary tools, and developing
mitigation measures. May provide security awareness, education and
training.
$194.00
IT-96
System Security
Engineer
Bachelor's degree required. Five or more years experience applying
computer science technologies to the design, development, evaluation,
and integration of computer systems and networks to maintain system
security.
$182.00
IT-97
Security Specialist
Associate's Degree required. Four years of experience monitoring
security standards and compliance
$171.00
IT-98
System Administrator
High School and 2 years relevant systems administration experience.
$130.00
IT Commercial Price List - March 2024
13 of 41

PORTAL CONTENT MANAGEMENT SERVICES
Portal Content Management Services – Onsite/Customer site support including:
Network Engineering Services and Administration Support
- Encompasses the Digital Library System TCP/IP network
- Includes customized integration and WAN distribution of non-network based
commercial application databases.
Product Installation Services
- Level of product installation service dependent on specific requirements.
Training for Support and End-users
- Provided on-site
- Customized to the application and audience
- Remote training and troubleshooting applications also included
Maintenance of a bank of URL links
- URLs are built, tested, stored, maintained and available to users via the portal
- Service includes up to 150 links
- Service for greater than 150 links is available in increments of up to 50 links
Documentation of services provided
- Provided to the customer annually in electronic format
Unit Prices:
Up to 150 links:
$530,000
Additional 50 links:
$180,000
These prices are for work at a customer facility, using customer-provided equipment. Prices are set for a
1- year contract period. Payments may be made in one up-front, lump sum amount; or as a monthly
payment, at the beginning of each month. At any time during the contract period, you may purchase a
higher level of service for the duration of the established contract period. At the end of the established
contract period, new services terms may be elected, and a new contract term will be set.
IT Commercial Price List - March 2024
14 of 41
INTRODUCTION TO ANDROID PROGRAMMING
Course Description
The Android Programming course is a unique course offering students the ability to explore the
Android operating system. This lab-driven class exposes students to the entire OS API, covering
everything from development of Android applications using the SDK and Android Studio to how these
APIs map to native libraries, the Linux kernel, and Android specific kernel components. There is also a
heavy emphasis on security at each level covered, including features and developments from the latest
releases of Android.
PREREQUISITE(S)
Students should have a Bachelor’s degree in Computer Science or Computer Engineering, or equivalent
experience. Students should also possess high academic achievement or operational/technical
experience and an intense desire to learn. This course assumes basic knowledge of Java and C
programming.
COURSE DETAILS
● 5 days
● 19 Labs
● 3 quizzes, 1 practical exam
● Android devices and development environment is provided
ENROLLMENT
Submit student enrollment requests to ACTP@ManTech.com. The training administrator will expedite
your request and payment requirements. At this time, enrollment is limited to ManTech employees and
government employees. Please contact ACTP@ManTech.com with any questions.
TUITION
Tuition Price for the course which includes all material is $3300 per seat.
INSTRUCTORS
Our instructors are members of an elite group of cyber professionals and have been chosen for
their technical knowledge, industry experience, and facilitation skills. Instructors who understand
the real challenges facing programmers because they perform the work professionally every day.
CLASS SIZE
Maximum class size is sixteen students. Minimum class size is eight students. An assistant instructor will
be provided for class sizes exceeding eight students.
TRAINING FACILITY
We have training facilities in Hanover, Maryland, Jessup, Maryland and San Antonio, Texas. Our VTC and
Virtual Instructor Led Training are available as well as on-site training.
GRADING
This class features one or more quizzes and a final exam. An exam score of 80% is a passing grade.
Students who complete the course with an 80% or better are awarded a certificate acknowledging
successful completion of the course. Students that do not receive a certifying grade will receive certificates
of attendance.
IT Commercial Price List - March 2024
15 of 41

Agenda and Course Content
Day 1:
● Understand the overall Android architecture
● Explore the Android Open Source Project (AOSP) and learn about it’s structure
● Learn to use the Android Debugging Bridge (ADB) to install APKs, push and pull files from a device, view
logs, and gain shell access
● Learn about the various Android device modes and what they are used for
● Use Android Studio to build applications
● Understand the structure and lifecycle Android applications
● Explore the use of Application Manifests and how they relate to intents and permissionsUnderstand the
various states of a process (foreground, visible, cached, etc.)
● Understand what rooting is and why you might want to root a device
● Discuss bootloaders (locked and unlocked) and how they relate to the security of a device
● Understand the Android file system by finding where applications, shared libraries, media content and
other core files are stored on the device
● Learn about the steps an Android device takes to boot
● Root and flash your phone
Day 2:
● Learn about the activity lifecycle
● Gain hands on experience using explicit and implicit intents as well as intent filters
● Use the application manager utility to send various kinds of intents
● Implement Foreground and Background services
● Explore the service lifecycle
● Send and receive broadcast intents
● Learn about the various Android permissions and how they are granted
● Android Services: development, types, AIDL interface language
● Implement applications that use explicit and implicit intents
Day 3:
● Understand the nature of Android Content Providers and their role in application development
● Understand what Framework Services are and their role
● Learn about the Binder driver – functionality, implementation
● Interact with various sensors on the device
● Understand how to access sensor services on the device
● Write an application using Android JNI
● Native Code and Native Development Kit (NDK) introduction
Day 4:
● Android Native Sensors
● Android Native Service development
● Cross-compilation process
● Android Native to Java Communication Models
● Understand how a call from an application flows down to the hardware
● Learn about the various types of hardware abstraction layers (HAL) throughout the versions
● Understand how the init initializes the Android operating system
Day 5:
● In-depth Practical. This includes completing various tasks that cover concepts taught throughout the
course. Some tasks are standalone, and others require you to complete a previous task before being able
to complete the next one.
IT Commercial Price List - March 2024
16 of 41

INTRODUCTION TO THE ANDROID INTERNALS COURSE
COURSE DESCRIPTION
The Android Internals course builds on the foundation established in the Android Programming course. This course dives
deeper into the Android operating system to explore concepts such as the internals of APKs, Package Manager, Activity
Manager, Zygote, Android Services and other core components of Android.
Students will have a strong understanding of the Android Radio Interface layer. They will know how to hide phone calls, send
hidden text messages, alter text messages, etc. Students will be able to describe how Wi- Fi works on Android, and how
network technology preference works (Wi-Fi over Cellular). Students will also learn about security on Android and be able to
determine which security mechanism is stopping a particular action from occurring.
PREREQUISITE(S)
Students should have a Bachelor’s degree in Computer Science or Computer Engineering, or equivalent experience.
Students should also possess high academic achievement or operational/technical experience and an intense desire to
learn. This course assumes basic knowledge of Java and C programming.
WHO SHOULD ATTEND
● Developers and researchers looking to learn how to write code for mobile platforms.
● Android developers looking to write more secure code
● Security researchers looking to gain insight into the Android OS architecture.
COURSE DETAILS
● 5 days
● 19 Labs
● 3 quizzes, 1 practical exam
● Android devices and development environment is provided
ENROLLMENT
Submit student enrollment requests to ACTP@ManTech.com. The training administrator will expedite your request and
payment requirements. At this time, enrollment is limited to ManTech employees and government employees. Please
contact ACTP@ManTech.com with any questions.
TUITION
Tuition Price for the course which includes all material is $3300 per seat.
INSTRUCTORS
Our instructors are members of an elite group of cyber professionals and have been chosen for their technical knowledge,
industry experience, and facilitation skills. Instructors who understand the real challenges facing programmers because they
perform the work professionally every day.
TRAINING FACILITIES
We have training facilities in Hanover, Maryland, Jessup, Maryland and San Antonio, Texas. Our VTC and Virtual Instructor
Led Training are available as well as on-site training.
CLASS SIZE
Minimum class size is six (6). Two instructors will be provided for class sizes exceeding ten students.
GRADING
Quizzes and Labs are administered as knowledge checks during the course regularly. Class culminates in a final exam.
IT Commercial Price List - March 2024
17 of 41

COURSE CONTENT
Day 1:
● Explore the various partitions of an Android device
● Understand each phase of the boot process for Android
● Learn about the role that Verified boot plays in protecting Android devices
● Learn about A/B slots
● Understand the changes that came from project Treble in Android 8.0
● Analyze the init script in Android to understand how it initializes the OS
● Learn about the various daemons that init starts and what their roles are
● Learn about the various stages of init (i.e. first, second, early-init, init, late-init etc)
● Understand the role that Properties plays in configuring and initializing Android
● Students will be able to freely navigate, build, and deploy Android builds from source
● Students will be able to dump the device’s bootloaders and understand the different stages of verified boot in
Android
● Students will learn how to redirect files that are mounted on a read only filesystem
Day 2:
● Understand the crucial role Zygote plays in initializing apps
● Explore the differences between the Dalvik VM and ART
● Write a program to communicate directly with Zygote to spawn a new process
● Understand the relationship between System Server and Service Manager
● Understand and describe how the core services are laid out, and what functionality is provided by which service
● Understand how services are managed and located
● Learn about the internals of the APK structure
● Learn about .dex, .odex, .art files
● Understand the various ways to sign an APK and the security implications of each one
Day 3:
● Decompile APKs
● Reverse engineering APKs
● Learn about smali and baksmali
● Understand each step of installing an APK to an Android device
● Be able to manually create Java applications outside of the Android Framework
● Understand the Package Manager and its role
● Know how to interact with the Activity Manager via native code
● Understand the internals of Binder
● Use Binder using native code
● Understand exploit vulnerabilities from cross-app permission use
Day 4:
● Learn the Android Bluetooth Stack
● Covertly communicate over Bluetooth with other devices
● Learn how Android communicates with the baseband on the device
● Understand how vendors provide proprietary libraries to implement the radio interface layer
● Students will have a strong understanding of the Android Radio Interface layer. They will know how to hide phone
calls, send hidden text messages, fake text messages, alter text messages etc
● Learn about the various Wi-Fi protocols and what a Wi-Fi looks like
● Learn about the various Wi-Fi technologies supported by Android (Wi-fi direct, Wi-Fi aware etc)
Day 5:
● Learn about the many security mechanisms added to Android from 1.5 up to current
● Learn about DAC vs MAC
● Understand how Android leverages users and groups in Linux to enforce access control and sandboxing
● Understand the role SELinux plays in securing Android devices
● Understand the role capabilities plays in securing Android devices
● Understand how permissions at the application manifest level are enforced in the kernel
● Explore the role of seccomp
IT Commercial Price List - March 2024
18 of 41
LINUX CNO PROGRAMMER COURSE
The Linux Computer Network Operations (CNO) Programmer course is an intensive, hands-on course
focused on providing students with the skills and knowledge needed to become an advanced CNO
programmer, with emphasis in the Linux environment. Students embark on a 10-week journey, beginning
at using user space POSIX APIs, continuing to advanced topics such as manipulating ELF files and
exploiting vulnerable services, and ending with the design and deployment of CNO tools within the Linux
kernel itself. The class format combines lecture and demonstrations with practical lab assignments,
including two “crucible labs” that function as culminating exercises.
Full course enrollment is $32,220. Modular and weekly enrollments are offered based on seat availability.
Online and remote enrollments are also available upon request. Please see pricing below.
To enroll, contact the ACTP team via email at ACTP@ManTech.com.
CNO CORE (17 DAYS)
Python
3 Days
The Python class is an
introduction to the Python
programming language with an
emphasis on tools and
techniques that are useful for
CNO tasks such as test
development and vulnerability
research.
Networks
5 Days
The Networks class is a
practical exploration of IPv4 and
IPv6 networks and sockets
programming.
Assembly
3 Days
The Assembly class covers the
x86 (IA-32) and x86-64 (AMD64)
assembly languages.
Software Reverse Engineering
5 Days
The Software Reverse
Engineering class introduces
tools and techniques for
analyzing x86 and x86-64
executable files.
Core Crucible
1 Day
In the Core Crucible, students
work in teams to analyze and
exploit a botnet.
CNO Core Modular Enrollment $11,220
IT Commercial Price List - March 2024
19 of 41
LINUX USER MODE DEVELOPMENT (20 DAYS)
Linux Systems Programming
4 Days
The Linux Systems
Programming class introduces
Linux development tools and the
POSIX and Linux APIs.
Linux Internals
4 Days
Linux Internals delves further
into Linux with advanced uses
of the POSIX API, C library
internals, parsing and
manipulation of ELF files, and
Linux-specific system calls.
Linux CNO User Mode
Development
5 Days
Building on the material from
the preceding classes, the CNO
User Mode Development class
provides instruction on
fundamental techniques and
best practices for CNO tool
development.
Linux Vulnerability Research and
Exploitation
5 Days
Students in the Vulnerability
Research and Exploitation class
learn how to analyze and
exploit vulnerabilities in
software.
Linux User Mode Crucible
2 Days
In the User Mode Crucible,
students work in teams to
analyze and exploit a vulnerable
network service.
User Mode Development Modular Enrollment $14,000
LINUX KERNEL MODE DEVELOPMENT (8
DAYS)
Linux Kernel Internals
3 Days
The Kernel Internals class
introduces students to the major
subsystems, configuration and
compilation, and module/driver
development for the Linux
kernel.
Linux CNO Kernel Mode
Development
5 Days
The CNO Kernel Mode
Development class builds on the
previous class to introduce
techniques useful for Linux
Kernel CNO.
Kernel Mode Development Enrollment $7,000
IT Commercial Price List - March 2024
20 of 41

WINDOWS CNO PROGRAMMER SYLLABUS
COURSE DESCRIPTION
The Windows Computer Network Operations Programmer course is an intensive, hands-on course focused
on providing a programmer with the skills and knowledge needed to become an advanced CNO
programmer, with emphasis in the Windows environment. The class format combines both lecture and labs
for practical application of knowledge, including two labs that function as culminating exercises.
LEARNING OUTCOME
After the completion of the three modules, the student will be capable of assisting in the CNO tool
development lifecycle. The student will understand the tool objectives, environments, obstacles and
pitfalls associated with development, as well as strategies to meet objectives effectively and efficiently.
COURSE OUTLINE
The course contains the following modules:
Core Module
● Python (3 Days)
● Networks (5 Days)
● Assembly (3 Days)
● Software Reverse Engineering (5 Days)
● Core Crucible (1 Day)
User Mode Development Module
● Windows System Programming (4 Days)
● Windows Internals (4 Days)
● CNO User Mode Development (5 Days)
● Vulnerability Research and Exploitation (5 Days)
● User Mode Crucible (2 Days)
Kernel Mode Development Module
● Kernel Internals (5 Days)
● CNO Kernel Mode Development (3 Days)
PREREQUISITE(S)
Students should have a Bachelor’s degree in Computer Science or Computer Engineering, or equivalent
experience. Students should also possess high academic achievement or operational/technical
experience and an intense desire to learn. This course requires previous programming experience in C.
Students should possess experience in Windows Programming and IA-32 assembly.
ENROLLMENT
Submit student enrollment requests to ACTP@ManTech.com. The training administrator will expedite
your request and payment requirements. Please contact ACTP@ManTech.com with any questions.
TUITION
Full course enrollment is $26,250. Modular and weekly enrollments are offered based on seat availability.
Online and remote enrollments are also available upon request.
COURSE LENGTH
The entire course is approximately 45 days in length.
IT Commercial Price List - March 2024
21 of 41
We also offer modular enrollment, based on seat availability (please see pricing below).
WINDOWS CNO CORE (17 DAYS)
Python
3 Days
The Python class is an introduction to
the Python programming language
with an emphasis on tools and
techniques that are useful for CNO
tasks such as test development and
vulnerability research.
Networks
5 Days
The Networks class is a practical
exploration of IPv4 and IPv6
networks and sockets programming.
Assembly
3 Days
The Assembly class covers the x86
(IA-32) and x86-64 (AMD64)
assembly languages.
Software Reverse
Engineering
5 Days
The Software Reverse Engineering
class introduces tools and techniques
for analyzing x86 and x86-64
executable files.
Core Crucible
1 Day
In the Core Crucible, students
work in teams to analyze and
exploit a botnet.
CNO Core Modular Enrollment $11,220
WINDOWS USER MODE DEVELOPMENT (20 DAYS)
Windows Systems Programming
4 Days
The Windows Systems Programming
class introduces Windows
development tools and the Win32
API.
Windows Internals
4 Days
Windows Internals moves beyond the
Win32 API introduced in the previous
class to describe the advanced
Windows operating system concepts
used to implement it.
Windows CNO User Mode
Development
5 Days
Building on the material from the
preceding classes, the CNO User
Mode Development class provides
instruction on fundamental
techniques and best
practices for CNO tool development.
Windows Vulnerability Research
and Exploitation
5 Days
Students in the Vulnerability
Research and Exploitation class
learn how to analyze and exploit
vulnerabilities in software.
Windows User Mode Crucible
2 Days
In the User Mode Crucible, students
work in teams to analyze and exploit
a vulnerable network service.
User Mode Development Modular Enrollment $13,200
IT Commercial Price List - March 2024
22 of 41
WINDOWS KERNEL MODE DEVELOPMENT (8 DAYS)
Windows Kernel Internals
5 Days
The Kernel Internals class expands
on the user mode content to
introduce students to the Windows
Kernel architecture and
fundamentals of driver
development.
Windows CNO Kernel
Mode Development
3 Days
The CNO Kernel Mode
Development class builds on the
previous class to introduce
techniques useful for Windows
Kernel CNO.
Kernel Mode Development Enrollment $6,600
INSTRUCTORS
Our instructors are members of an elite group of cyber professionals and have been chosen for their
technical knowledge, industry experience, and facilitation skills. Instructors are rotated between the
classroom and contract positions to ensure their skills are current and operationally relevant.
TRAINING FACILITIES
We have training facilities in Hanover, Maryland, Jessup, Maryland and San Antonio, Texas. Our VTC and
Virtual Instructor-Led Training are available as well as on-site training.
CLASS SIZE
Minimum class size is six (6). Two instructors will be provided for class sizes exceeding ten students.
GRADING
Each class features one or more quizzes and a final exam. An average exam score of 80% is a passing
grade. Students who complete all 10 graded classes, with an 80% average or better, are recognized as
ManTech Certified Advanced Cyber Programmers (CACPs), and receive certification. Students who
achieve a 95% or higher receive honors. Students that do not receive a certifying grade will receive
certificates of attendance, or graduation
IT Commercial Price List - March 2024
23 of 41

MERCIAL SOFTWARE & SERVICES
Commercial Software & Services
IT Commercial Price List - March 2024
24 of 41
BIDS
What is BIDS?
Many R&D organizations use information gathering tools such as OTAs , BAAs, RFIs, SBIRs, sought
sources, white papers, etc. to collect and evaluate information in regards to their mission. The process
has traditionally been paper intensive and plagued with information dissemination and collection
problems….until now.
BIDS is a web accessible, secure, fully automated and paperless knowledge management application that
not only streamlines the dissemination and proposal gathering process but allows for real time on-line
evaluations while reducing the demand on personnel resources and maintaining the highest levels of
information security. BIDS is easily tailored to the “client’s process” to ensure process consistency.
BIDS allows our clients to:
● Post, gather and evaluate responses to OTAs, BAAs, RFIs
● Secure evaluation of submissions
● Integrate group evaluations for decision making
By using the BIDS application, leaders can efficiently and effectively manage the process without leaving
the office. Web accessibility not only provides a secure link to the information for the vendors and users but
allows Management to quickly assess, control and obtain status reports, in real time. All from a single,
secure, browser-based console that moves when- and where-needed, leaves no footprint on the client’s IT
structure and removes the need for expensive IT and networking support.
BIDS LICENSING – PRICE LIST
Description
Firm Fixed Price
BIDS database set-up and user training for max of 25 users
Includes:
- Requirements gathering with client
- Routine tailoring (nomenclature changes, client logo, text configuration, etc.)
- Creation of client portal for access
- Database validation with client
- One day on-site training
$17,325.00
BIDS Product License
Includes:
- BIDS Software License
- Tier 1 Help Desk Support
- BIDS Application Guide and Quick Sheets
$6,000.00/month
IT Commercial Price List - March 2024
25 of 41

DECISIONPOINT™
What is DecisionPoint™?
DecisionPoint™ is a secure, web-based collaboration tool which reduces protest risk and increases award
schedule efficiency for government agency contract teams. Government entities of all sizes rely on the
security, functionality, and efficiency of DecisionPoint™ to support their source selection strategies and
success.
Who does DecisionPoint™ target?
DecisionPoint™ is designed for federal agency program managers and contracting officers that supervise
evaluation teams during the source selection process. By using DecisionPoint™ agency officials are able to
assess evaluation team progress and quality, while reducing cycle time to meet award schedules.
The ultimate test of any contract award decision is the agency’s ability to stand up to protest. With
DecisionPoint™, agencies can virtually eliminate this worry.
DecisionPoint™ is a powerful, collaborative source selection management solution, enabling government
agencies to streamline operations and optimize evaluation efficiency. DecisionPoint™ significantly exceeds
all source selection regulatory requirements.
Standardized evaluation templates and intuitive workflow routines ensure both consistent proposal
evaluation and strict compliance to award evaluation criteria. A structured approach to process integrity and
comprehensive audit trails ensures quality and control. Protests are not only less likely, they are less likely
to succeed. In fact, to date, no protest has ever been sustained where DecisionPoint™ has been utilized.
Sophisticated paperless functionality. Unparalleled process integrity. Bulletproof security. Fast, flexible
implementation. Streamlined performance and collaborative ease-of-use. Little or no IT investment or ramp
up. And unwavering commitment to automated source selection. Introducing DecisionPoint™.
Benefits:
● Eliminate protests
● Increase evaluation efficiency
● Maximize online collaboration
● Provide comprehensive documentation
● Focus efforts on the quality and substance of the evaluation; not administration, process and logistics
Features:
User-Friendly Interface. The DecisionPoint™ interface is intuitive, straightforward and consistent. The tool
uses standardized input templates that promote documentation quality and consistency, reducing the
administrative burden on source selection management. User training and orientation sessions help team
members feel comfortable and confident with the tool from the first day of the source selection.
DecisionPoint™ enables evaluation teams to focus on the quality and substance of their evaluations, not
on source selection administration, process and logistics.
Facilitates Process Integrity. By tailoring to the agency’s environment and ways of doing business,
DecisionPoint™ helps enforce the evaluation team’s source selection process. Evaluator strengths,
weaknesses ratings and risks clearly link to RFP evaluation criteria.
IT Commercial Price List - March 2024
26 of 41

Rapid Online Consensus. DecisionPoint™ delivers an efficient consensus process to facilitate collaboration
between acquisition teams. Through built in reporting, integrated messaging and bulletin board functionality,
customers are able to facilitate effective communication between managers and end- users. Consensus
findings are easily posted and interactively accessible to the entire team in real-time, displaying progress and
status metrics.
Online Library and Data Warehouse. DecisionPoint™ lets customers create and securely maintain an online
reference library of agency and offeror documents in a searchable, structured format that maintains 100%
source document integrity. Coherent, comprehensive and secure records are permanently maintained.
Document quality is upheld through logical workflow and user interface to help ensure consistent and complete
evaluator ratings and narrators.
Real Time Process Control. DecisionPoint™ presents evaluation managers with a panoramic view of the
entire source selection process, enabling them to monitor the status of the overall process, drill down to a
discrete element or gauge progress with total ease at any time, from anywhere. DecisionPoint™ facilitates
effective communication with helpful features including integrated messaging and bulletin boards.
Fully Customizable. DecisionPoint™ was designed to ensure that customized modifications, including unique
source selection language and process alterations are fast, straightforward and trouble-free.
Fast, Flexible Implementation. DecisionPoint™ is a rapidly deployable application that can be plugged into
almost any acquisition environment or specification with minimal intervention and expense.
Management Insight. DecisionPoint™ will provide source selection management the ability to monitor
evaluator progress and comment quality from their desktop. As part of their DecisionPoint™ access protocol,
source selection management can monitor all evaluator/advisor comments and provide real-time feedback and
direction via a built-in Q&A and bulletin board feature. This capability is invaluable for making in- process
corrections and proactively managing the source selection schedule.
Scalability and Stability. DecisionPoint™ software designers have ensured the application provides a
scalable and stable platform for conducting large-scale or multiple-user source selection efforts. Through a
multiple source selection environment, the DecisionPoint™ application and associated infrastructure have a
proven record of maintaining complete integrity and security between the source selections with no loss of
performance or compromise of sensitive evaluation data.
Responsive Customer Service and Support. AcqCenter is committed to providing customers with the most
responsive support available throughout the entire evaluation process. DecisionPoint™ is not just software – it
is a full-service capability that ensures your evaluation team receives our best customer support, from initial
DecisionPoint™ install to final data archiving at the end of the selection process.
IT Commercial Price List - March 2024
27 of 41
DecisionPoint™ Licensing – PRICE LIST
Public Internet Access License
1. Secure access to DecisionPoint™ via the Internet via the Customer’s desktop.
2. Hosted on the AcqCenter’s Secure System in Microsoft Azure.
ManTech Hosted Access License Options
Cost
Set-Up & User Training
Includes:
- One-day onsite user application training session
- Application set-up, configuration, and routine customizations
- Network performance testing and validation
$13,240/source
selection
Licenses Fees
Includes:
- 24x7 customer-access to DecisionPoint™ Technical Support Desk
(email/telephone support during business hours and pager notification during
non- business hours)
- DecisionPoint™ software upgrades at no extra cost
- AcqCenter’s commitment to customer satisfaction (DecisionPoint™
Customer Warranty - see EULA)
$1,950/month
OPTIONAL: Acquisition Consulting
$174/hour
*Travel expenses required for support outside the local Washington, DC area are additional
Private Intranet Access License/Leased Server
Purchase of DecisionPoint™ software license and installation on Customer’s private intranet.
Customer Hosted Access License Options
Cost
Installation, Set-Up & User Training
Includes:
- One-day onsite user application training session
- One-day onsite server installation and testing*
- Application set-up, configuration, and routine customizations
$15,025/source
selection
Software License/Leased Server Fees
Includes:
- 24x7 customer-access to DecisionPoint™ Technical Support Desk
(email/telephone support during business hours and pager notification during
non- business hours)
- DecisionPoint™ software upgrades at no extra cost
- AcqCenter’s commitment to customer satisfaction (DecisionPoint™
Customer Warranty - see EULA)
$1,145/month
(per server)
OPTIONAL: Fully Configured DecisionPoint™ Environment installed on
customer LAN
Custom Pricing
OPTIONAL: Acquisition Consulting
$174/hour
*Travel expenses required for support outside the local Washington, DC area are additional
IT Commercial Price List - March 2024
28 of 41

DOCUMENT DETECTIVE
What is Document Detective?
ManTech’s Document Detective is a desktop application designed to redact, sanitize, and review popular
electronic document formats like Microsoft Office and Adobe Portable Document Format (PDF). It meets
the U.S. Government’s rigorous security requirements for a “100 percent Reliable Human Review” for
protecting National Security Information that could be compromised by hidden data in electronic
documents. Document Detective is critical for business and commercial applications where the
protection of proprietary information and a client’s private and personal data is of paramount importance.
The following file types are supported in Document Detective:
Analysis and Flattening (remove hidden data / deep object inspection):
● Microsoft Word documents and templates
● Microsoft Excel documents and templates
● Microsoft PowerPoint documents and templates
● Rich Text Files (Microsoft Word)
Keyword Search:
● Text files (TXT, CSV, ASC, etc.)
● Adobe Portable Document Format (PDF)
● Image (JPEG)
● Audio (MP3)
● Binary file types
Document Detective detects over 100 hidden data types, including:
● Ad Hoc Review (automatically enables Tracked Changes without warning) when documents are emailed
● Tracked Changes (Word, PowerPoint, and Excel)
● Document fragments caused by Fast Save
● Macros and Scripts
● Embedded OLE objects and media files
● Paste and Paste Special security problems
● 12 font formats that obscure text in Word
● Cropped and resized images
● Overlapping and off-page objects
● Metadata (document properties)
● Malicious OLE streams
● Deleted text and images in Adobe PDF
IT Commercial Price List - March 2024
29 of 41
Document Detective Licensing – PRICE LIST
A Subscription License allows the Licensee to use the software for a specific period of time, typically 12
months from date of purchase. At the end of the subscription period, the software license expires and the
Licensee must terminate use of the software unless they renew the software subscription for a fee.
ManTech provides commercial pricing rates for Document Detective Subscription Licenses. Rates are
provided in the following table.
License Options
Annual Subscription
(Per User)
Individual License*
Includes:
- Full access to all software features and updates
- Standard support subscription for two (2) Technical Points of Contact
(TPOCs)
$275.00
Enterprise (100+ Users) License
Includes:
- Full access to all software features and updates
- Standard support subscription for two (2) Technical Points of
Contact (TPOCs)
Custom Pricing
*License installation is assessed per machine. Minimum license purchase quantity: 5 users
ManTech reserves the right to change prices at any time.
Document Detective Enhanced Support Annual Subscription – PRICE LIST
Level
Description
Cost
PREMIUM
Provides enhanced (Tier 3+) troubleshooting and
analysis of Document Detective deployments in an
enterprise environment.
Includes:
- Two (2) Additional TPOCs
- Email and Phone Support
- Four (4) business hour response time
- Scheduled after hours/weekend support via
phone/email (Requires 5 business days
advance notice)
$10,000
IT Commercial Price List - March 2024
30 of 41
Document Detective Instructor-Led Training Certification – PRICE LIST
ManTech International Corporation provides Instructor-Led Certification Training for Document
Detective. Individuals or groups charged with protecting data are strongly encouraged to attend a formal
Instructor- Led Training session to ensure that Data Transfer Agents (DTAs) are certified in the use of
Document Detective. The certification provides fundamental understanding of the product capabilities,
as well as how users and organizations can leverage the product to provide a record of action should
the threat of a spill arise in the future. From an organizational level, having DTAs certified is one
additional step in risk mitigation and helps to show that an organization is doing everything possible to
protect data.
Course Options
Cost
Option One: Virtual - 4 hour course, Minimum of 5 students
Add-On Student Rate $750/student
Maximum course capacity is 10 students
$3,750
Option Two: Virtual - 4 hour course, Minimum of 5 students
Installable demo software provided for each student
Add-On Student Rate $1,000/student
Maximum course capacity is 10 students
$5,000
Option Three: In-Person - Full Day Course
Customer responsible for securing classroom and equipment
Maximum course capacity is 10 students
Custom Pricing
ManTech is happy to accept purchase orders and credit card orders for Document Detective licenses and
training. Payment by credit card is required for any purchase under $5,000 and is due prior to delivery of any
product and/or services. Please contact Commercial.Services@ManTech.com for more information and details
on our certification training.
IT Commercial Price List - March 2024
31 of 41
INFINISTRUCTURE™
What is InfiniStructure™?
InfiniStructure™: Limitless IT Landscape is ManTech-developed software that enables users to rapidly
create and deploy a digital cyber environment, scaling any number of servers, whether a few or thousands,
in minutes. InfiniStructure™ works on any hardware or cloud platform of choice. Customers can purchase
InfiniStructure™ individually and use it on their own to build digital twins and create a testing, simulation
and training environment. If you just want the tool to enable your own experts to work it, you can do so, the
same as with a commercial service. The versatility of InfiniStructure™ can help virtually any customer
protect their critical infrastructure via rapid deployment, development, testing and simulation to meet their
most challenging needs.
Benefits:
● Rapid Deployment on Multiple Services
● User Friendly Visualization
● Drag and Drop Interface for Connectivity to Devices and Virtual Machine (VM) Templates
InfiniStructure™ Licensing – PRICE LIST
Description
Cost
Set-Up and User Training
Includes:
- One-day virtual user application training session for up to 10 users
- Application installation, configuration and routine customizations,
including:
• Platform Administration
• Building Virtual Machine Templates
• Importing and Exporting SDIs
• Importing Disk Images
$13,500
InfiniStructure™ Annual License Subscription
Includes:
- Up to 10 InfiniStructure™ User Licenses
- Customer-access to InfiniStructure™ Technical Support which includes:
• 24x7 access to InfiniStructure™ User Documentation and
Knowledge Base Articles
• Standard Tier 1 and 2 Support via live technicians during
designated business hours
- InfiniStructure™ software assurance at no extra cost
$24,000/year
IT Commercial Price List - March 2024
32 of 41
InfiniStructure™ Enhanced Support Annual Subscription – PRICE LIST
Level
Description
Cost
ELITE
Provides enhanced (Tier 3+) troubleshooting and analysis of
InfiniStructure™ deployments in an enterprise environment.
Includes:
- Priority email and ticketing support with 4 business
hour response time
- One (1) monthly 45-minute web-based meeting or
phone call engagement (optional) for the duration of
the period of performance (monthly engagements do
not rollover)
- Scheduled after hours/weekend support via
phone/email (Requires 5 business days advance
notice)
- One (1) annual 3-day onsite engagement (optional)
for routine InfiniStructure™ health check and/or
troubleshooting during the period of performance
$30,000
PRIORITY
Provides enhanced (Tier 3+) troubleshooting and analysis of
InfiniStructure™ deployments in an enterprise environment.
Includes:
- Priority email and ticketing support with 4 business hour
response time
- One (1) monthly 45-minute web-based meeting or phone
call engagement (optional) for the duration of the period of
performance (monthly engagements do not rollover)
- Scheduled after hours/weekend support via phone/email
(Requires 5 business days advance notice)
$15,000
IT Commercial Price List - March 2024
33 of 41

ONTARGET®
What is OnTarget®?
OnTarget® is a proposal development and review solution enabling government contractors to focus their
proposals on the source selection criteria from the outset and to increase their contract win rate.
OnTarget® is based on DecisionPoint™, AcqCenter's software platform used in over 950 procurements by
government agencies, with an eye toward the proposal team and the unique challenges behind contract
wins.
Who does OnTarget® target?
Many organizations employ a group of independent reviewers known as Red Teams to objectively assess
the proposal and ensure compliance with RFPs. Red Team processes are loosely defined and often
haphazard; therefore, it is imperative they use a source selection tool to streamline their workflow.
OnTarget® is a software management tool designed with the Red Team specifically in mind.
Benefits:
● Develop clear and concise linkage between your proposal and the specific evaluation criteria
● Make the job of government evaluators and contract officers easy and painless
● Increase win rate
Features:
User-Friendly Interface. The OnTarget® interface is intuitive and straightforward. Standardized input
templates promote documentation quality and consistency while reducing the administrative burden. Minimal
user training and orientation is required so you spend time on the proposal, not on learning the tool.
Streamline Operations. OnTarget® maximizes collaboration with intuitive workflow, making proposal
development activities seamless and efficient.
Simplify Evaluations. OnTarget® allows Red Teams to review proposals in the same way as a government
evaluator would, gathering feedback on the content and organization of the material.
Develop Strategy / Win Themes. The effectiveness of proposals meeting capture strategies can be
evaluated, allowing the team to provide feedback on areas where enhancements should be made.
Match Your Proposal to Evaluation Criteria. OnTarget® focuses proposal teams on the same criteria the
government will use – this process is critical as proposals are evaluated against criteria, not competitors.
Build Rapid Online Consensus. OnTarget® delivers an efficient consensus process to facilitate
collaboration between proposal teams, allowing consensus findings to be easily posted and accessed by the
entire team in real-time, displaying progress and status metrics.
Online Proposal Development Library and Data Warehouse. An easy-to-access reference library of
documents can be created. Coherent, comprehensive and secure records are permanently maintained.
Document quality is upheld through logical workflow to help ensure consistency.
Fast, Flexible Implementation. OnTarget® can be plugged into almost any proposal environment with
minimal intervention and expense.
Responsive Customer Service and Support. AcqCenter is committed to providing customers with the
most responsive support available throughout their entire proposal development process.
IT Commercial Price List - March 2024
34 of 41
OnTarget® Licensing – PRICE LIST
Private Intranet Access License/Customer Provided Server:
Purchase of OnTarget® software license and installation on Customer-supplied web server on
Customer’s Intranet LAN.
Description
Firm Fixed Price
Installation, Set-up, Super User Training and New Software License
Includes:
- 1-Day onsite super user application training session for up to 10 students
- 1-Day onsite server installation and testing*
- (2) Annual 1-Day Onsite engagements (optional) for routine OnTarget®
Health Check/Onsite OnTarget® Troubleshooting
- Application set-up, configuration and routine tailoring to client process
- First year annual software license cost
$75,000
Annual Software Maintenance for Current Software License
Includes:
- Annual software license cost
- Technical Support Desk (email/telephone support during business hours)
- OnTarget® software upgrades at no extra cost
- AcqCenter’s commitment to customer satisfaction (OnTarget® Customer
Warranty - see EULA)
Annual Software Maintenance for current software licenses pricing in effect as long
as the annual license subscription remains current and does not lapse or expire.
$10,000/year
(After initial year)
Annual Software Maintenance for Expired Software License
Includes:
- Annual software license cost
- Technical Support Desk (email/telephone support during business hours)
- OnTarget® software upgrades at no extra cost
- AcqCenter’s commitment to customer satisfaction (OnTarget® Customer
Warranty - see EULA)
$25,000/year
Installation, Set-up and Super User Training
Includes:
- 1-Day onsite super user application training session for up to 10 students
- 1-Day onsite server installation and testing*
- (2) Annual 1-Day Onsite engagements (optional) for routine OnTarget®
Health Check/Onsite OnTarget® Troubleshooting
- Application set-up, configuration and routine tailoring to client process
$50,000
*Cleared staff available for secure installs
IT Commercial Price List - March 2024
35 of 41

SENTRIS®
What is Sentris®?
Sentris® is a flexible security labeling and access control platform, developed by ManTech for Microsoft
Windows® environments that require a high degree of data security and confidentiality. Sentris® provides end
users with easy-to-use tools to label and secure content using common applications, such as Microsoft
Windows®, Office®, SharePoint®, Skype for Business®, and Outlook®. Sentris® is unique in its capability to
control access to data based on three criteria:
1. Who is accessing the information?
2. Where are they located?
3. What system are they using?
This innovative approach to attribute-based access control (ABAC) allows organizations to easily and efficiently
manage access to information in complex, high-security environments where traditional access control
mechanisms are ineffective and cumbersome. Sentris® is designed to support the DoD Risk Management
Framework (RMF) requirements to prevent inadvertent disclosure of restricted information. Sentris® is equally
customizable to meet the security requirements for virtually any organization.
ManTech offers commercially-available annual subscription licenses in addition to optional Feature Packs,
training and enhanced support offerings for the Sentris® Platform.
● Sentris® Core Components (included with an annual Sentris® Core License Subscription)
- Sentris® Platform Server
- Sentris® Platform Client
- Sentris® Administration Tool
- Sentris® Labeling for Microsoft Office®.
- Sentris® Extended Infrastructure Components – Sentris® External Access Data Provider (ADP)
Synchronization Service
- Sentris® Standard Support Subscription for two (2) Technical Points of Contact (TPOC)
● Sentris® Feature Pack Licenses (optional add on perpetual licenses)
- Sentris® Protection for Microsoft SharePoint®
- Sentris® Protection for Microsoft Exchange®
- Sentris® Protection for Microsoft Skype for Business®
- Sentris® Protection for Windows Server® File Shares
- Sentris® Labeling for PDF
- Sentris® API Documentation and Toolkit***
● Sentris® Platform Add-Ons (optional)
- Sentris® ProStart - a 90 day training and support engagement package to get your team and
environment up and running
- Sentris® Additional Technical Point of Contact (TPOC)
● Sentris® Platform Training and Enhanced Support (optional)
- Sentris® Certified Engineer Instructor Led 5-Day Trainings (In-Person and Virtual options)
- Tier 3+ Enhanced Support Level Offerings (Platinum, Gold, Silver and Bronze packages)
IT Commercial Price List - March 2024
36 of 41
Sentris® Platform Licensing – PRICE LIST
ManTech licenses the Sentris® Platform Core Components on an annual subscription per named-user
basis at the following price:
Component
Includes
Annual
Subscription
(Per User)
Core
Sentris® Platform Server
Sentris® Platform Client
Sentris® Administration Tool
Sentris® Labeling for Microsoft Office®
Sentris® ADP Synchronization Service
Sentris® Standard Support Subscription for two (2)
Technical Points of Contact (TPOC) per Sentris
Organization
$165.00
Minimum license purchase quantity: 100 users. Additional TPOC seats available for purchase.
ManTech reserves the right to change prices at any time.
Sentris® Feature Packs – PRICE LIST
Feature Pack
Description
Cost
Sentris® Protection
for Microsoft
SharePoint®
Protection of SharePoint® sites, lists, and items.
Protects collaborative features.
$60,000.00
Sentris® Protection for
Microsoft Exchange®
Transport service to validate email markings.
$35,000.00
Sentris® Protection
for Microsoft Skype
for Business®
Client and Server extensions to label and manage
instant messaging conversations with Microsoft Skype
for Business®.
$35,000.00
Sentris® Protection for
File Shares
Leverages the Windows® File Classification
Infrastructure to assign classification properties to files
and govern access based on the assigned classification
attribute.
$30,000.00
Sentris® Labeling
for PDF
Windows® shell extension for applying markings and
labels to PDF document format.
$30,000.00
Requires Enhanced Support Subscription of SILVER or above
Sentris® API
Documentation and
Toolkit
Implement solutions developed with the Sentris® API
Documentation and access to Sentris® Management
Shell and Scripts.***
$20,000.00
Feature Packs are a one-time charge as long as the Sentris® Core annual license subscription remains current and has not
lapsed/expired. If the Sentris® Core annual license subscription is not renewed, any feature packs previously purchased will need to be
repurchased with the new Sentris® Core license set. Feature pack licenses are purchased for every 10,000 users for each network and
may be installed on as many servers or desktops within that network to support load balancing, clustering and high availability models.
ManTech reserves the right to change prices at any time.
IT Commercial Price List - March 2024
37 of 41
Sentris® Platform Add-Ons – PRICE LIST
Option
Description
Cost
Sentris® ProStart
Add-On
The Sentris® ProStart combines two on-site engagements with
members of the Sentris® Product Team. The engagement
provides Sentris® Certified Engineer Training and Sentris®
installation and configuration support for Sentris® Systems and
Features, as well as emulation of Sentris® deployments.
Includes:
- 1 (5-Day) Sentris® Certified Engineer Instructor-Led
Training for up to 10 Students
- 1 (5-Day) On-Site Engagement for Installation &
Configuration Support of a Sentris® Environment (to be
scheduled and completed within 90-days of the 5-day
training)
- 90 Days of Tier 3+ Email and Phone Support with one (1)
business day response time to begin once the 5-day training
is completed
ProStart Sentris® Certified Engineer Instructor-Led Training for
up to 10 Students to be scheduled within 90 days of purchase.
$100,000.00
Sentris® Additional
Technical Point of
Contact (TPOC)
Add-On
Additional TPOC seats are $300/month/person and will align
with the Sentris® Core license expiration date (prorating
available).
$3,600.00
Sentris® Certified Engineer Instructor-Led Training – PRICE LIST
Option
Description
Cost
Sentris® Certified
Engineer
Instructor-Led 5-Day
Training (In-Person)
Installation Planning Installation Configuration Advanced
Architectures For SAs, SEs, IAT, IAM, PSO
Maximum course capacity is 10 students
$35,000.00
Sentris® Certified
Engineer
Instructor-Led 5-Day
Training (Virtual)
Installation Planning Installation Configuration Advanced
Architectures For SAs, SEs, IAT, IAM, PSO
Maximum course capacity is 10 students
$25,000.00
ManTech prefers to keep class size limited to allow for maximum instructor–student engagement and
personal interaction and training. However, if more than 10 students per class is needed, please
contact us at Commercial.Services@ManTech.com.
IT Commercial Price List - March 2024
38 of 41
Sentris® Enhanced Support Annual Subscriptions
Level
Description
Cost
PLATINUM
Provides enhanced (Tier 3+) troubleshooting and analysis of
Sentris® deployments in an enterprise environment. Supports
analysis of Sentris® configurations and errors.
Includes:
- Two (2) Additional TPOCs
- Email and Phone Support**
- Two (2) Business Hours Response Time
- Eight (8) Annual 3-Day Onsite engagements (optional)
for routine Sentris® Health Check/Onsite Sentris®
Troubleshooting /Virtual Training
- Access to Sentris® API Documentation and Toolkit***
- Scheduled after hours/weekend support (Requires 5
business days advance notice)
One (1) onsite engagement can be swapped out for the 5-day
virtual training for up to 10 students*
$275,000.00
GOLD
Provides enhanced (Tier 3+) troubleshooting and analysis of
Sentris® deployments in an enterprise environment. Supports
analysis of Sentris® configurations and errors.
Includes:
- One (1) Additional TPOC
- Email and Phone Support**
- Four (4) Business Hours Response Time
- Four (4) Annual 3-Day Onsite engagements (optional)
for routine Sentris® Health Check/Onsite Sentris®
Troubleshooting /Virtual Training
- Access to Sentris® API Documentation and Toolkit***
- Scheduled after hours/weekend support (requires 10
business days advanced notice)
One (1) onsite engagement can be swapped out for the 5-day
virtual training for up to 10 students*
$165,000.00
Continued on next page
IT Commercial Price List - March 2024
39 of 41
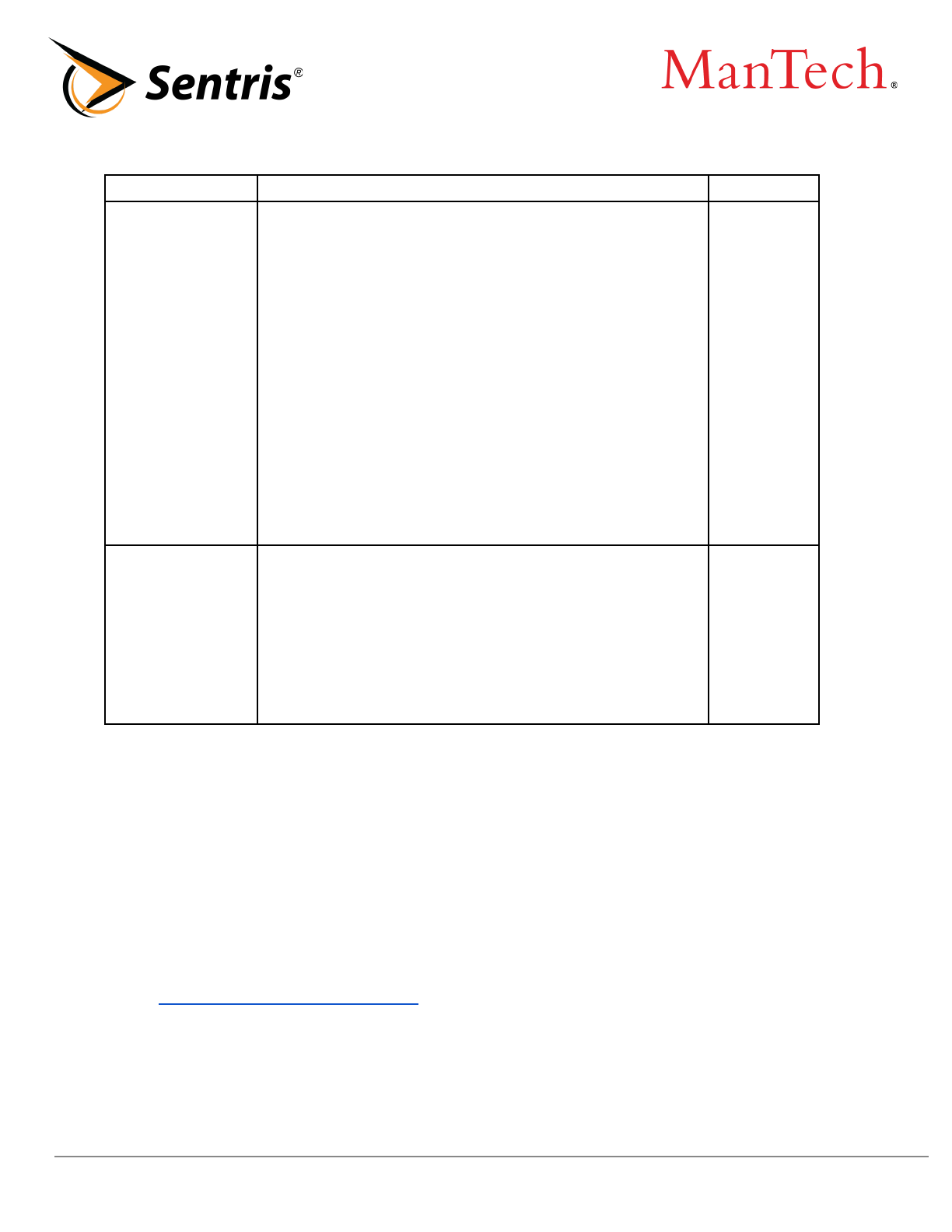
Sentris® Enhanced Support Annual Subscriptions Cont’d
Level
Description
Cost
SILVER
Provides enhanced (Tier 3+) troubleshooting and analysis of
Sentris® deployments in an enterprise environment. Supports
analysis of Sentris® configurations and errors.
Includes:
- Email and Phone Support**
- One (1) Business Day Response Time
- One (1) Annual 3-Day Onsite engagement (optional)
for routine Sentris® Health Check/Onsite Sentris®
Troubleshooting /Virtual Training
- Scheduled after hours/weekend support (requires 10
business days advanced notice)
One (1) onsite engagement can be swapped out for the 5-day
virtual training for up to 10 students*
$85,000.00
BRONZE
Provides enhanced (Tier 3+) troubleshooting and analysis of
Sentris® deployments in an enterprise environment. Supports
analysis of Sentris® configurations and errors.
Includes:
- Email and Phone Support**
- One (1) Business Day Response Time
$60,000.00
*Site visits associated with Enhanced Support Subscriptions do not rollover and are all optional.
On-site visits and after-hours/weekend support are subject to resource availability.
**Web-based meetings and/or phone calls shall be offered as two 45-minute sessions per month for
the duration of the period of performance. Monthly web-based meetings and/or phone call allotments
do not rollover.
***Access and continued use of the Sentris® Management Shell and Scripts (included in the Sentris®
API Documentation and Toolkit) requires an Enhanced Support Subscription of SILVER or above.
Sentris® API Documentation and Toolkit is included at no additional cost with an Enhanced Support
Subscription of GOLD or PLATINUM.
ManTech is happy to accept purchase orders and credit card orders for Sentris® Software sales. Please
contact Commercial.Services@ManTech.com for further information.
IT Commercial Price List - March 2024
40 of 41

CONTACT INFORMATION
For Commercial Software inquiries and quotes, please contact: Commercial.Services@ManTech.com
For questions or additional information, please contact:
SVP-Pricing C.W. Etzler
Phone 703-218-6320
Email CW.Etzler@ManTech.com
Address 2251 Corporate Park Drive Herndon, VA 20171
IT Commercial Price List - March 2024
41 of 41
