
BUSINESS DEVELOPMENT GUIDEAUGUST 2023, VERSION 1.0
ZSCALER AND GITLAB
DEPLOYMENT GUIDE

2©2024 Zscaler, Inc. All rights reserved.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
Contents
Terms and Acronyms 5
Trademark Notice 6
About This Document 7
Zscaler Overview 7
GitLab Overview 7
Audience 7
Soware Versions 7
Zscaler and GitLab Introduction 8
ZPC Overview 8
Zscaler Resources 9
GitLab Overview 10
GitLab Resources 10
Version Control and CI/CD Systems 11
Configuring IaC Scan for GitLab 11
About Security Policies 11
Prerequisites 11
Configuring the Zscaler IaC Scan Action for GitLab 12
Choose GitLab Repositories 14
Viewing the IaC Scan Summary in GitLab 17
Viewing Specific IaC Scan Summary in GitLab 18
Viewing the IaC Scan Summary in the ZPC Admin Portal 19
Resolving Failed Integrations 24
Use Case 1 24
Use Case 2 24

3©2024 Zscaler, Inc. All rights reserved.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
Zscaler Data Protection for GitLab 25
ZIA Cloud Browser Isolation 26
ZIA Data Loss Protection and Malware Detection for GitLab 26
What Makes Zscaler SaaS Security unique? 27
ZIA Cloud Application Control 27
ZPC and GitLab Integration 28
Configure Cloud Browser Isolation 29
Configure the Cloud Browser Isolation Profile 29
Configure GitLab SaaS Application Tenant 37
GitLab SaaS Tenant Configuration Wizard 38
Configure GitLab Policies and Scan Configuration 41
Scoping the Policies and Remediation 41
Creating a DLP Policy 42
Creating a DLP Engine 42
Configure a SaaS DLP Policy for GitLab 44
SaaS DLP Policy Details 45
Configure a SaaS Malware Policy for GitLab 46
GitLab SaaS Malware Policy Wizard 47
GitLab SaaS Malware Policy 47
Configure a Scan Schedule Configuration for GitLab 48
Start the Scan Schedule for GitLab 49
GitLab Reporting and Visibility 49
SaaS Assets Summary Report 50
SaaS Security Insights 51

4©2024 Zscaler, Inc. All rights reserved.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
Cloud App Control 52
Cloud App Control Policy 52
Cloud App Control Policy Wizard 52
Cloud App Control Logs 54
Appendix A: Requesting Zscaler Support 55

ZSCALER AND GITLAB DEPLOYMENT GUIDE
5©2024 Zscaler, Inc. All rights reserved.
Terms and Acronyms
The following table defines acronyms used in this deployment guide. When applicable, a Request for Change (RFC) is
included in the Definition column for your reference.
Acronym Definition
API Application Programming Interface
AWS Amazon Web Services
CA Central Authority (Zscaler)
CSV Comma-Separated Values
DLP Data Loss Prevention
DNS Domain Name Service
DPD Dead Peer Detection (RFC 3706)
GDRP General Data Protection Regulation
GRE Generic Routing Encapsulation (RFC2890)
IaC Infrastructure as Code
ICMP Internet Control Message Protocol
IdP Identity Provider
IKE Internet Key Exchange (RFC2409)
IPS Intrusion Prevention System
IPSec Internet Protocol Security (RFC2411)
NIST National Institute of Standards and Technology
PFS Perfect Forward Secrecy
PSK Pre-Shared Key
SaaS Soware as a Service
SSL Secure Socket Layer (RFC6101)
TLS Transport Layer Security
VDI Virtual Desktop Infrastructure
XFF X-Forwarded-For (RFC7239)
ZCP Zscaler Cloud Protection (Zscaler)
ZDX Zscaler Digital Experience (Zscaler)
ZIA Zscaler Internet Access (Zscaler)
ZPA Zscaler Private Access (Zscaler)
ZPC Zscaler Posture Control (Zscaler)
ZSCALER AND GITLAB DEPLOYMENT GUIDE
6©2024 Zscaler, Inc. All rights reserved.
Trademark Notice
© 2023 Zscaler, Inc. All rights reserved. Zscaler™ and other trademarks listed at zscaler.com/legal/trademarks are either (i)
registered trademarks or service marks or (ii) trademarks or service marks of Zscaler, Inc. in the United States and/or other
countries. Any other trademarks are the properties of their respective owners.

ZSCALER AND GITLAB DEPLOYMENT GUIDE
7©2024 Zscaler, Inc. All rights reserved.
About This Document
The following sections describe the organizations and requirements of this deployment guide.
Zscaler Overview
Zscaler (NASDAQ: ZS) enables the world’s leading organizations to securely transform their networks and applications for
a mobile and cloud-first world. Its flagship Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) services create
fast, secure connections between users and applications, regardless of device, location, or network. Zscaler delivers its
services 100% in the cloud and offers the simplicity, enhanced security, and improved user experience that traditional
appliances or hybrid solutions can’t match. Used in more than 185 countries, Zscaler operates a massive, global cloud
security platform that protects thousands of enterprises and government agencies from cyberaacks and data loss. To
learn more, see Zscaler’s website.
GitLab Overview
GitLab Inc. (NASDAQ: GTLB) is an open-core company that operates GitLab, a DevOps soware package which can
develop, secure, and operate soware. The open-source soware project was created by Ukrainian developer Dmytro
Zaporozhets and Dutch developer Sytse Sijbrandij.
What started in 2011 as an open-source project to help one team of programmers collaborate is now the platform millions
of people use to deliver soware faster, more efficiently, while strengthening security and compliance. To learn more,
refer to GitLab’s website.
Audience
This guide is for network administrators, endpoint and IT administrators, and security analysts responsible for deploying,
monitoring, and managing enterprise security systems. For additional product and company resources, see:
• Zscaler Resources
• GitLab Resources
• Appendix A: Requesting Zscaler Support
Soware Versions
TThis document was authored using ZPC and GitLab Production 2022 Release. A GitLab free account was used to create
and verify the features enabled and used as examples.
Create a free GitLab Account.
Request for Comments
• For prospects and customers: Zscaler values reader opinions and experiences. Contact partner-doc-support@
zscaler.com to offer feedback or corrections for this guide.
• For Zscaler employees: Contact z-bd-sa@zscaler.com to reach the team that validated and authored the
integrations in this document.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
8©2024 Zscaler, Inc. All rights reserved.
Zscaler and GitLab Introduction
Overviews of the Zscaler and GitLab applications are described in this section.
ZPC Overview
Zscaler Posture Control (ZPC) is a multi-tenant soware-as-a-service (SaaS) platform that detects and responds to cloud
security risks and helps businesses adopt the digital transformation journey towards the cloud faster. The service enables
your organization to correlate across multiple security engines to prioritize hidden risks caused by misconfigurations,
threats, and vulnerabilities, and achieve continuous security, compliance, and governance.
ZPC offers data protection, high availability, and resiliency for all imported, stored, and exported data types. ZPC leverages
cloud service provider APIs to connect to your hybrid, multi-cloud environments and collect real-time configuration
metadata for your cloud infrastructure, such as web servers, databases, and virtual machines. ZPC evaluates the metadata
and offers visibility into your security, compliance, and risk posture.
ZPC helps detect cloud security risks in the development lifecycle, as well as threats like ransomware aacks, account
takeover, privilege escalation once the business applications are deployed in the cloud infrastructure across Amazon Web
Services (AWS), Microso Azure, and Google Cloud Platform (GCP).
ZPC is part of Zscaler Cloud Protection, a comprehensive multi-cloud security platform covering misconfigurations,
entitlements, exposed aack surfaces, lateral threat movement, and data loss.
ZPC comprises functionality previously covered by several point products, including:
• Cloud Security Posture Management (CSPM): Ensure cloud resources have proper configurations for authentication,
data encryption, internet connectivity, and more for compliance and a strong security posture.
• Cloud Infrastructure Entitlement Management (CIEM): Identify and remediate excessive permissions that humans
and machines have by using machine learning analysis for increased visibility into access policies, resource policies,
actions, and roles.
• Security and Compliance: Benchmark and validate public cloud configurations against best practices standards and
compliance frameworks to report misconfigurations, policy violations, and automate remediation.
• Infrastructure-as-Code (IaC) Security: Monitor your IaC infrastructure and implement security controls to address
any misconfigurations or security issues before deployment and thereby ensure the code is secure and compliant
with standard security policies.
• Vulnerability Management: Monitor and detect any known vulnerabilities and security weaknesses in the cloud
infrastructure and take immediate action to protect networks from potential threats.
If you are using this guide to implement a solution at a government agency, some of the content might be
different for your deployment. Efforts are made throughout the guide to note where government agencies might
need different parameters or input. If you have questions, contact your Zscaler Account team.

ZSCALER AND GITLAB DEPLOYMENT GUIDE
9©2024 Zscaler, Inc. All rights reserved.
Zscaler Resources
The following table contains links to Zscaler resources based on general topic areas.
Name Definition
ZIA Help Portal Help articles for ZIA.
ZPC Help Portal Help articles for ZPC.
Zscaler Tools Troubleshooting, security and analytics, and browser extensions that help Zscaler
determine your security needs.
Adding SaaS Application
Tenants
Help articles on using Zscaler API for visibility and security for sanctioned SaaS
applications used in your organization.
About SaaS Application Tenants Help articles on adding SaaS applications to Zscaler.
SaaS Security API DLP Policy Help articles on creating rules to discover and protect sensitive data at rest in
sanctioned SaaS applications.
About Data Loss Prevention Help article on DLP.
About DLP Dictionaries Help article on DLP dictionaries.
About DLP Engines Help article on DLP engines.
SaaS Security Insights Help article providing SaaS security information.
Zscaler Training and Certification Training designed to help you maximize Zscaler products.
Submit a Zscaler Support Ticket Zscaler Support portal for submiing requests and issues.
The following table contains links to Zscaler resources for government agencies.
Name Definition
ZIA Help Portal Help articles for ZIA.
ZPC Help Portal Help articles for ZPC.
Zscaler Tools Troubleshooting, security and analytics, and browser extensions that help Zscaler
determine your security needs.
Adding SaaS Application
Tenants
Help articles on using Zscaler API for visibility and security for sanctioned SaaS
applications used in your organization.
About SaaS Application Tenants Help articles on adding SaaS applications to Zscaler.
SaaS Security API DLP Policy Help articles on creating rules to discover and protect sensitive data at rest in
sanctioned SaaS applications.
About Data Loss Prevention Help article on DLP.
About DLP Dictionaries Help article on DLP dictionaries.
About DLP Engines Help article on DLP engines.
SaaS Security Insights Help article providing SaaS security information.
Zscaler Training and Certification Training designed to help you maximize Zscaler products.
Submit a Zscaler Support Ticket Zscaler Support portal for submiing requests and issues.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
10©2024 Zscaler, Inc. All rights reserved.
GitLab Overview
GitLab is a web-based Git repository that provides free open and private repositories, issue-following capabilities, and
wikis. It is a complete DevOps platform that enables professionals to perform all the tasks in a project—from project
planning and source code management to monitoring and security. Additionally, it allows teams to collaborate and build
beer soware.
GitLab helps teams reduce product lifecycles and increase productivity, which in turn creates value for customers. The
application doesn’t require users to manage authorizations for each tool. If permissions are set once, then everyone in the
organization has access to every component.
GitLab allows all the team members to collaborate in every phase of the project. GitLab offers tracking from planning to
creation to help developers automate the entire DevOps lifecycle and achieve the best possible results. More and more
developers have started to use GitLab because of its wide assortment of features and brick blocks of code availability.
• Accelerate your digital transformation: GitLab can help you achieve your digital transformation objectives with the
most comprehensive DevSecOps platform. GitLab can help simplify your soware delivery toolchain by ditching the
plugins, simplifying integration, and helping your teams get back to delivering great soware.
• Deliver soware faster: Automated soware delivery with GitLab helps you adopt cloud native, Kubernetes, and
multi-cloud with ease, achieve faster velocity with lower failures and improve developer productivity by eliminating
repetitive tasks.
• Ensure compliance: Soware compliance is no longer just about checking boxes. Cloud native applications present
entirely new aack surfaces via containers, orchestrators, web APIs, and other Infrastructure as Code (IaC). These
new aack surfaces, along with complex DevOps toolchains, have resulted in notorious soware supply chain
aacks and led to new regulatory requirements. Continuous soware compliance is becoming a critical way to
manage risk inherent in cloud native applications and DevOps automation—beyond merely reducing security flaws
within the code itself.
• Improve collaboration and visibility: Give everyone one platform to collaborate and see everything from planning to
production.
• Build in security: Integrating security into your DevOps lifecycle is easy with GitLab. Security and compliance are built
in, out of the box, giving you the visibility and control necessary to protect the integrity of your soware.
GitLab Resources
The following table contains links to GitLab support resources.
Name Definition
GitLab Documents GitLab Documentation
GitLab Learn GitLab Learning Portal
Get Started with GitLab Get Started with GitLab
GitLab Community GitLab Community
GitLab Architecture Overview GitLab Architecture Overview

ZSCALER AND GITLAB DEPLOYMENT GUIDE
11©2024 Zscaler, Inc. All rights reserved.
Version Control and CI/CD Systems
The following sections describe how to configure version control and CI/CD systems for a Zscaler and GitLab integration.
Configuring IaC Scan for GitLab
The Zscaler IaC Scan app scans and identifies security misconfigurations in the IaC Terraform, Helm, Kubernetes, and
CloudFormation templates within GitLab. When you add or update the code and make a merge request, the IaC Scan
action automatically triers a scan of the IaC templates, identifies security misconfigurations, and displays the scan
results within the code. This allows you to fix the configuration errors before deployment, and ensure your code is secure
and compliant with the security policies.
About Security Policies
Security policies protect your cloud deployment from asset misconfigurations and excessive permissions by defining a
condition or parameter for how a particular cloud asset must be configured. ZPC offers over 400 security policies across
multiple cloud service providers (CSPs), including Amazon Web Services, Microso Azure, and Google Cloud Platform.
ZPC has created security policies to protect both your runtime and build time environments. You cannot modify the
security policies, but you can create new custom security policies tailored for your cloud deployment.
ZPC also bundles security policies to emulate cybersecurity benchmarks (e.g., NIST) or compliance benchmarks (e.g.,
GDPR).
The Policies page provides the following benefits and enables you to:
• View all cloud and IaC policies offered by ZPC.
• Gain cloud posture overview based on whether the policies are passing or failing for your cloud deployment.
• Create custom security policies to cater to your cloud deployment’s compliance requirements.
Prerequisites
The administrator with an owner role can onboard the GitLab accounts and authorize the IaC Scan app to scan the IaC
repositories.
You can configure only one GitLab integration per tenant.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
12©2024 Zscaler, Inc. All rights reserved.
Configuring the Zscaler IaC Scan Action for GitLab
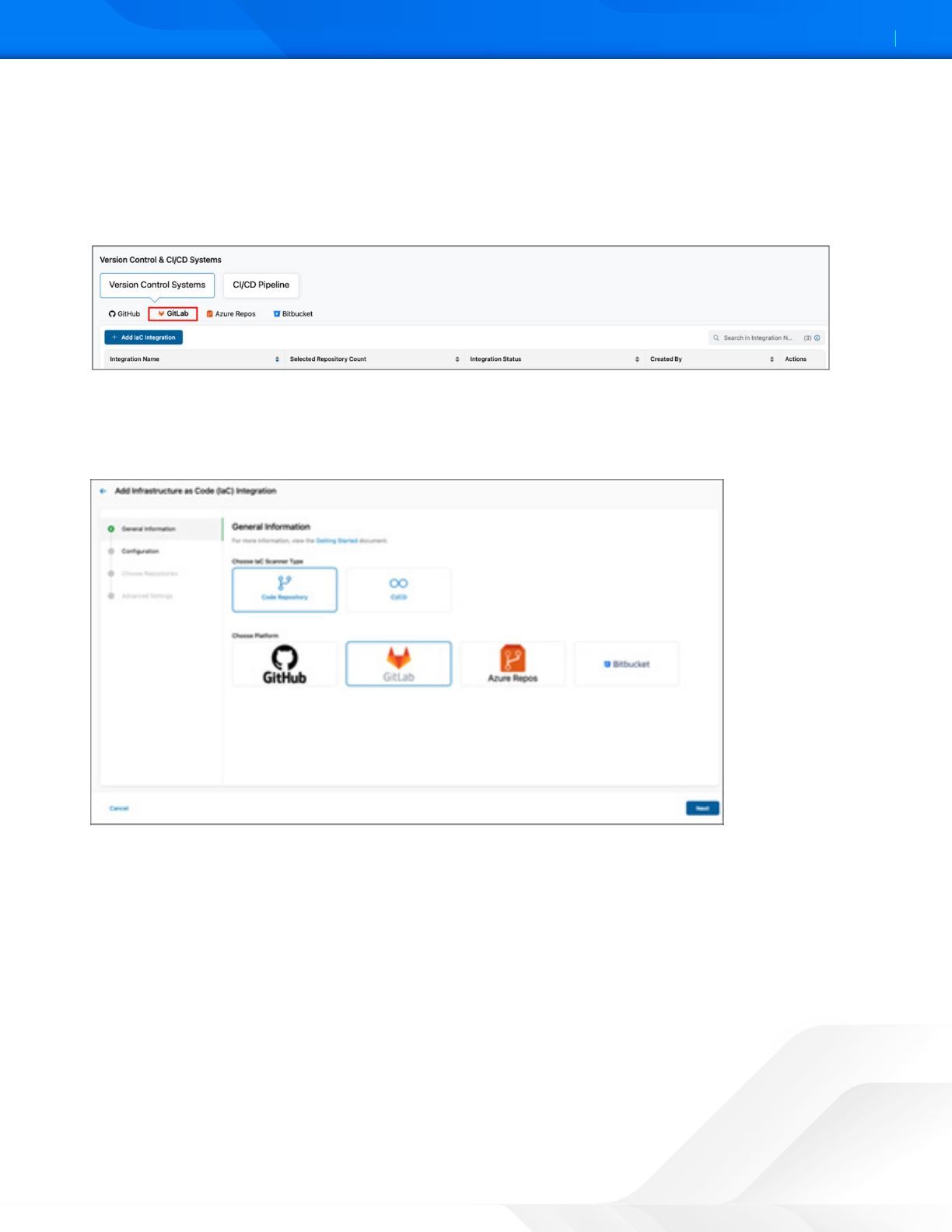
To configure the Zscaler IaC Scan action for GitLab:
1. Go to Administration > Version Control & CI/CD Systems.
2. On the IaC Integrations page, click Add IaC Integration.
Figure 1. GitLab Version Control and CI/CD Systems
3. Under General Information:
a. For IaC Scanner Type, select Code Repository.
b. For Platform, select GitLab.
Figure 2. General Information
ZSCALER AND GITLAB DEPLOYMENT GUIDE
13©2024 Zscaler, Inc. All rights reserved.
4. Click Next.
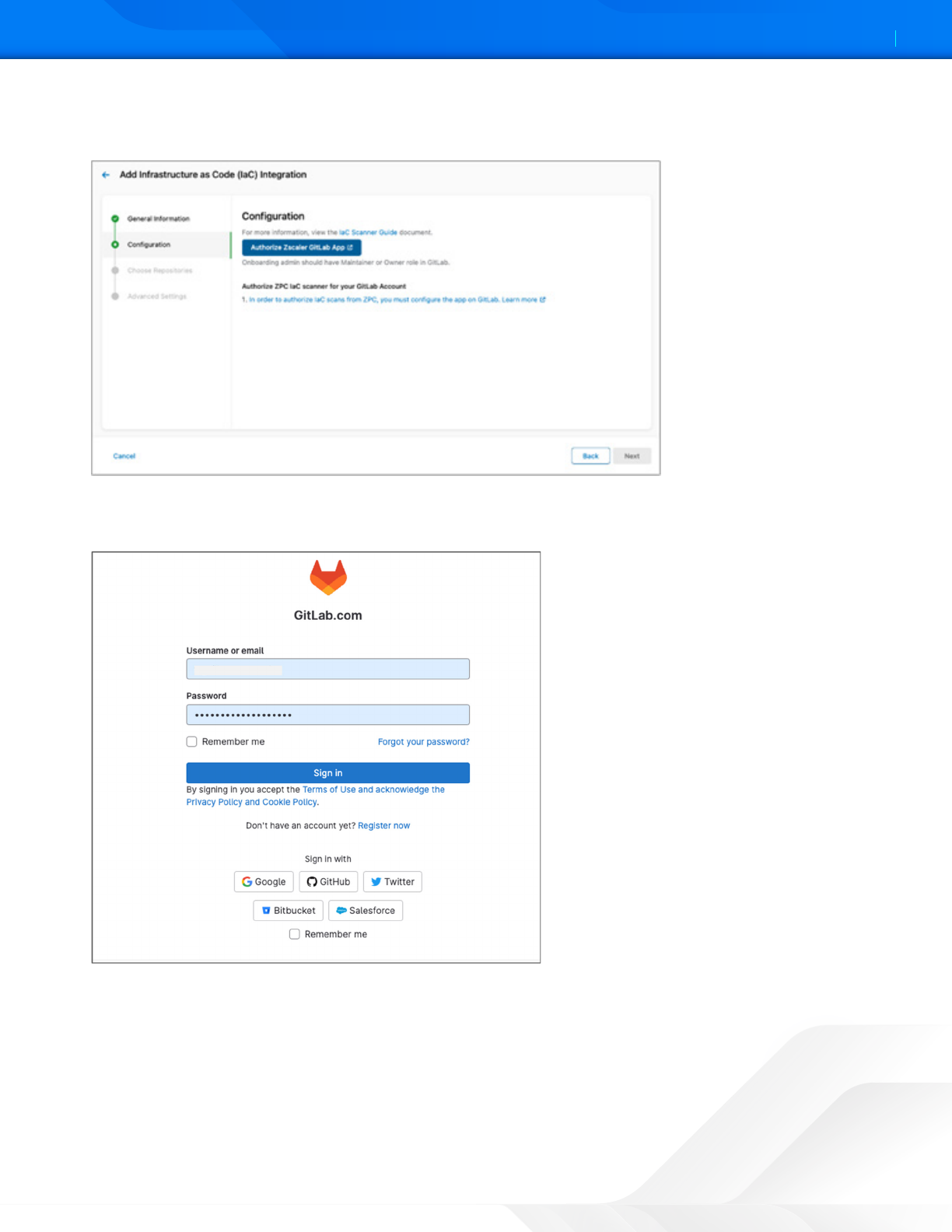
5. Click Authorize Zscaler GitLab App.
Figure 3. Authorize Zscaler GitLab App
The GitLab Sign-in page appears. If you are already loed in to your GitLab account, then the GitLab
Authorization page appears.
Figure 4. Authorize Zscaler GitLab App
6. Sign in to your GitLab account.
7. On the GitLab Authorization page, click Authorize. Aer completing the authorization, you are redirected back to
the ZPC Admin Portal.
8. Click Next.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
14©2024 Zscaler, Inc. All rights reserved.
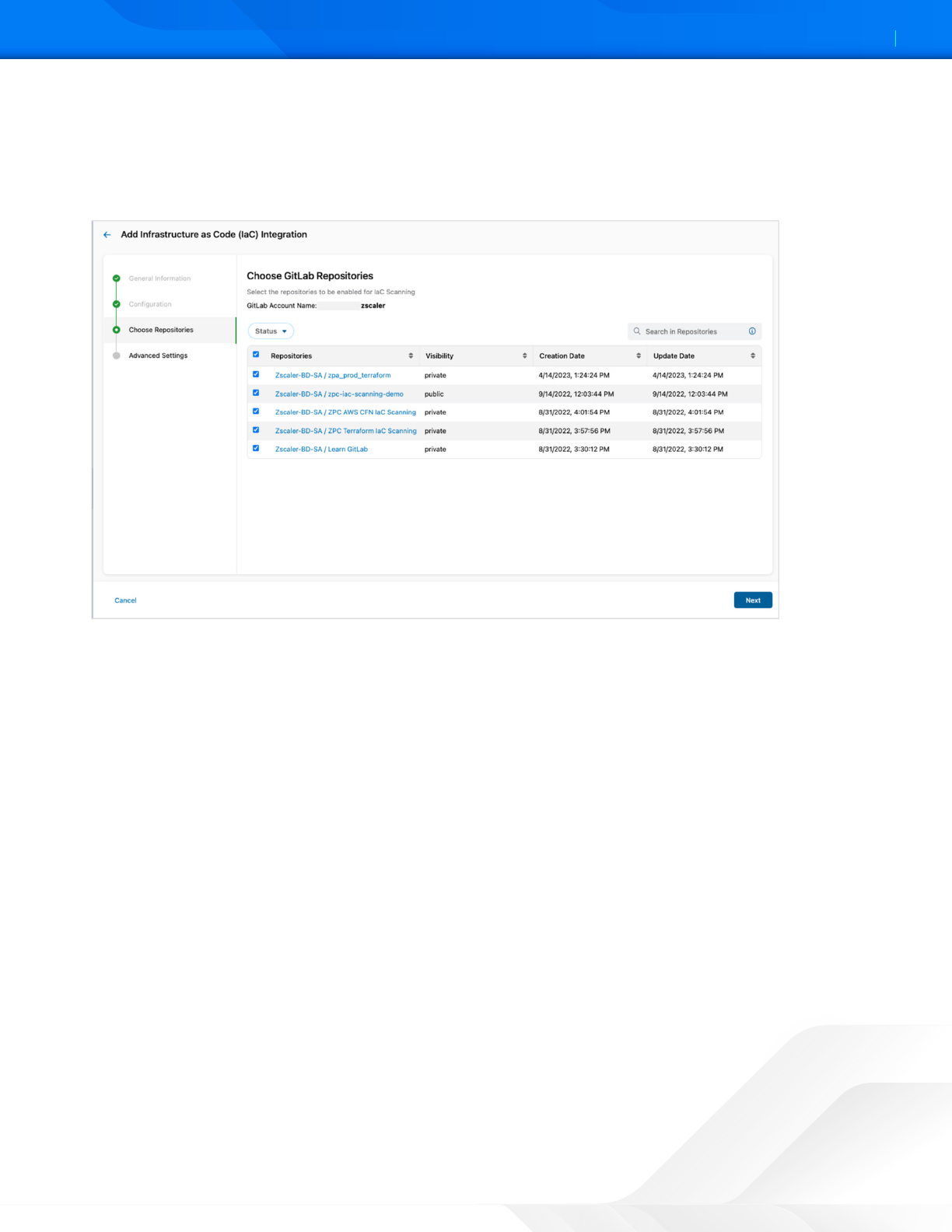
Choose GitLab Repositories
Under Choose GitLab Repositories, you can view the onboarded GitLab account and the list of repositories within this
account.
1. Select the repositories that must be enabled for scanning.
Figure 5. Choose GitLab Repositories
2. Click Next.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
15©2024 Zscaler, Inc. All rights reserved.
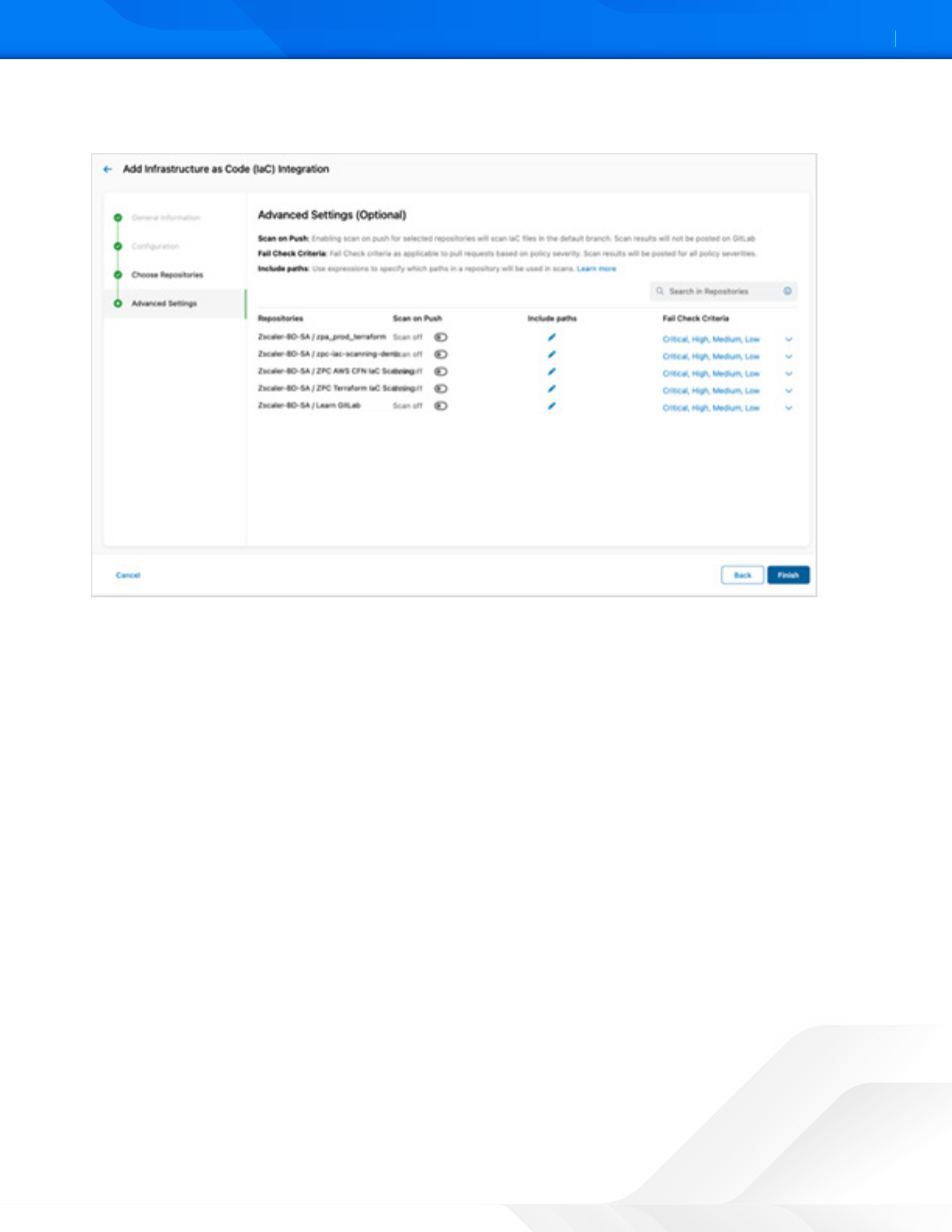
3. (Optional) Under Advanced Seings:
• Scan on Push: Click the tole to scan the code for a push command. The IaC Scan app performs the scan in
the background and triers alert notifications for any policy violations and displays the alerts in the ZPC Admin
Portal. To learn more, see About Alerts.
• Include Paths: Click Edit to include the path of the specific folder within the repository that must be scanned. For
example, if you define an include path for a single file, then only that file is scanned and all other files and folders
within the repository are ignored. You can also use regular expressions (regex) to search for and include files or
folders that must be scanned:
Regex Paern Description Example
/**/ Match zero or more
directories
If you type charts/**/, then the following files are included:
• charts / docker.yml
• charts / stub
• charts / stub / config.yml
• charts / server / config / app1 / app.yml
**/ Match any directory/
directories, start of
paern only
If you type **/internal/test/**, then the following files are included:
• root/internal/test/stub.txt
• internal/test/stub.txt
• /internal/test/server
• root/internal/test
/** Match any directory/
directories, end of
paern only
If you type monorepo/**/terraform/**, then the following files are
included:
• monorepo/terraform/doc.tf
• monorepo/app1/terraform
• monorepo/app1/terraform/stub.yml
• monorepo/app1/app2/terraform
* Match any non-
separator character
If you type *repo/**/terraform/**, then the following files are included:
• monorepo/terraform/doc.tf
• monorepo/app1/terraform
• publicrepo/app1/terraform/stub.yml
• newrepo/app1/app2/terraform
! Excludes all matches
from the result set,
start of paern only
If you type !**/internal/test/**, then the following files are excluded:
• root/internal/test/stub.txt
• internal/test/stub.txt
• /internal/test/server
• root/internal/test
You can apply a security threshold to each repository. For example, you can fail a merge request that introduces
Critical or High issues from a repository that is used to deploy to a production environment. If the same
merge request has a Low threshold and the code must be merged to a repository that is used to deploy in a
development environment, then you can pass the request. However, the alert notification is generated in both
scenarios.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
16©2024 Zscaler, Inc. All rights reserved.
• Fail Check Criteria: Fail check criteria is applicable to only merge requests based on policy severity. Select the
security threshold (Critical, High, Medium, or Low) for the policy from the drop-down list.
Figure 6. Advanced Seings
4. Click Finish.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
17©2024 Zscaler, Inc. All rights reserved.
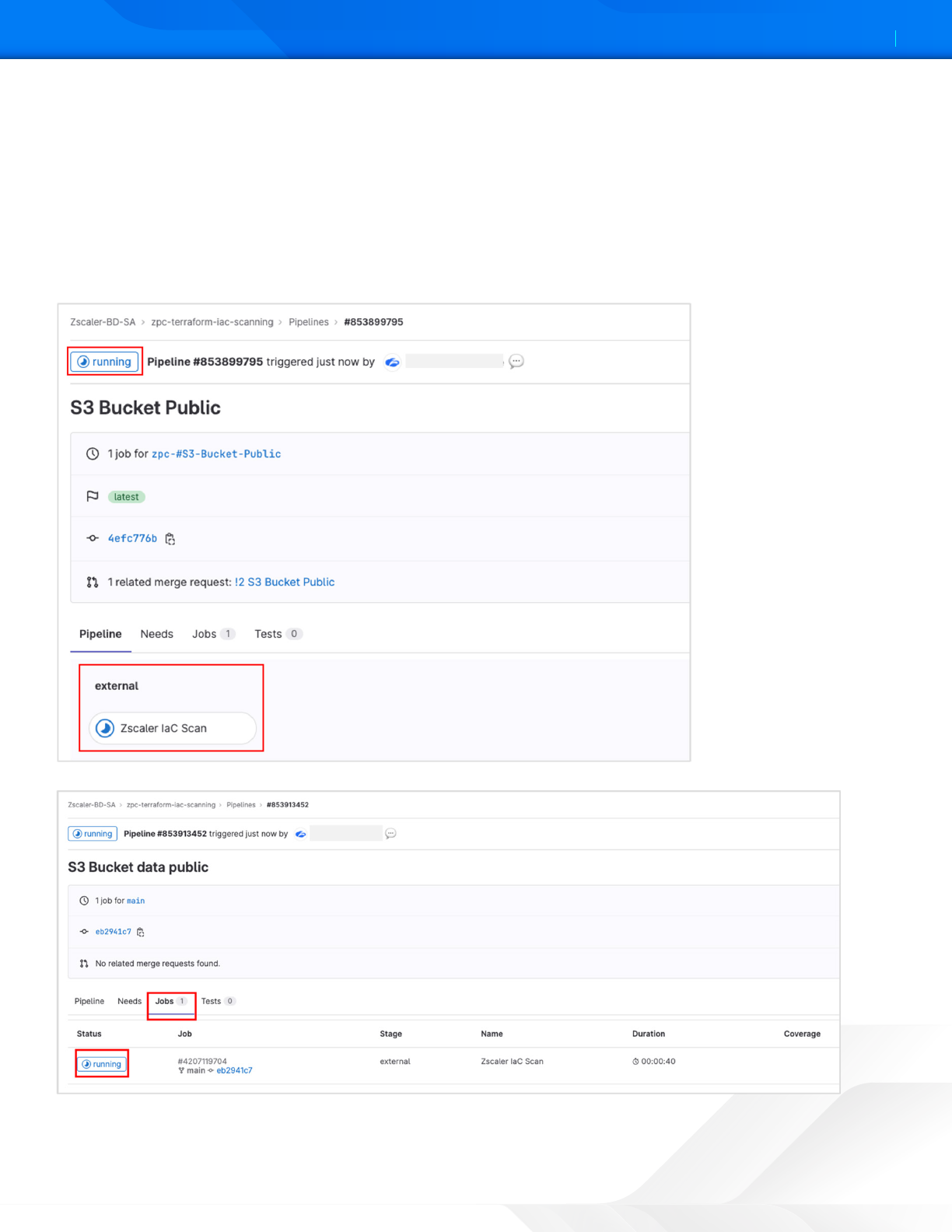
Viewing the IaC Scan Summary in GitLab
Aer you enable the selected repositories for scanning, the IaC Scan app performs a scan every time you add or update a
code and make a merge request. The IaC Scan app identifies security misconfigurations and displays policy violations and
remediation steps within the code. You can fix the issues and then merge the code.
You can see the total policies along with passed and failed findings. This information indicates if the code is violation-free
for the policies evaluated or if none of the policies were evaluated for this resource. You can see the policy title and ID,
severity, and resource details aer the line of code that has issues.
Figure 7. GitLab Pipeline execution
Figure 8. GitLab Job execution
ZSCALER AND GITLAB DEPLOYMENT GUIDE
18©2024 Zscaler, Inc. All rights reserved.
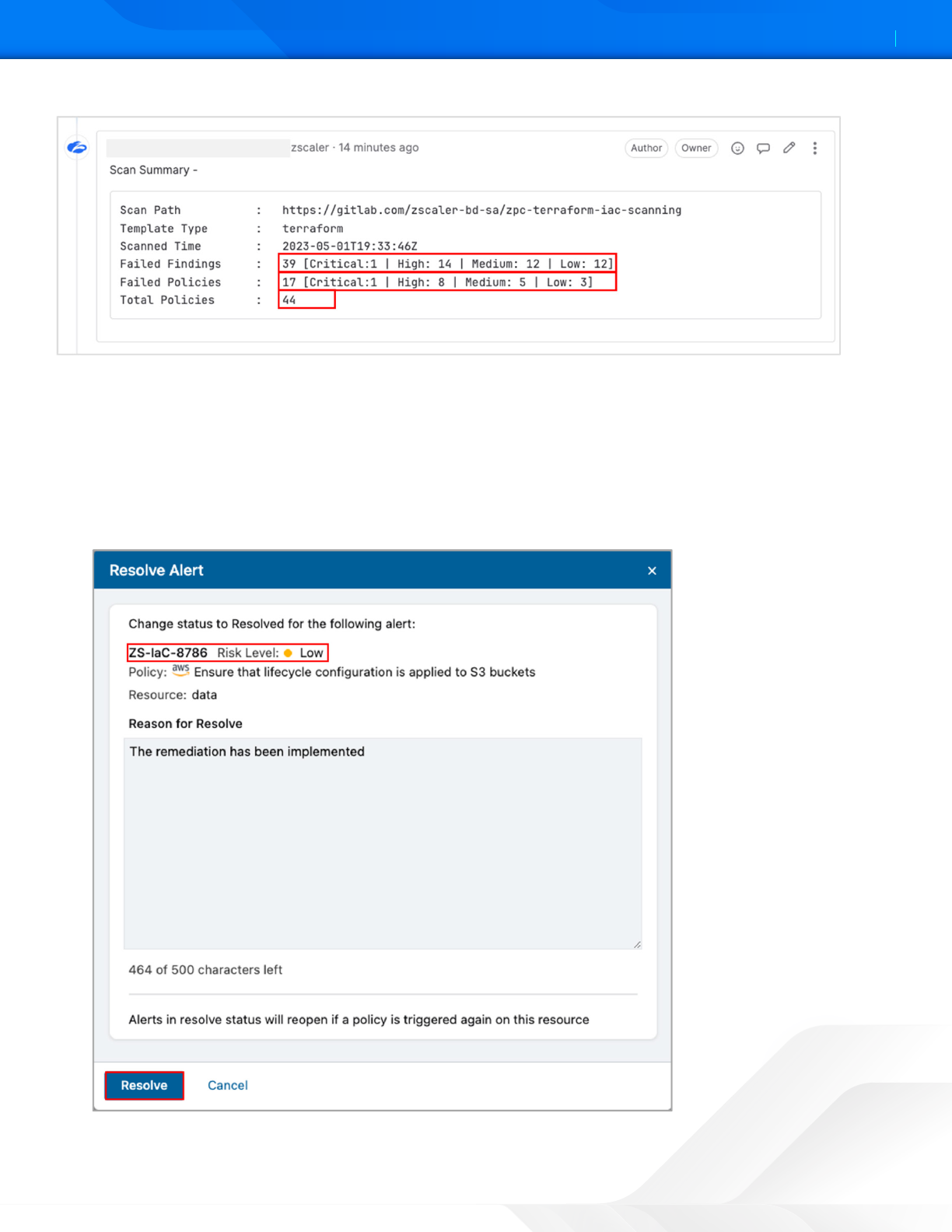
Figure 9. Zscaler IaC Scan results
Viewing Specific IaC Scan Summary in GitLab
In addition to the scan summary, the GitLab integration with ZPC also provides visibility and details on specific alerts.
To resolve a specific alert via the GitLab portal:
1. Select the check mark icon.
2. (Optional) Enter a Reason to Resolve.
Figure 10. Resolve Alert
ZSCALER AND GITLAB DEPLOYMENT GUIDE
19©2024 Zscaler, Inc. All rights reserved.
Viewing the IaC Scan Summary in the ZPC Admin Portal
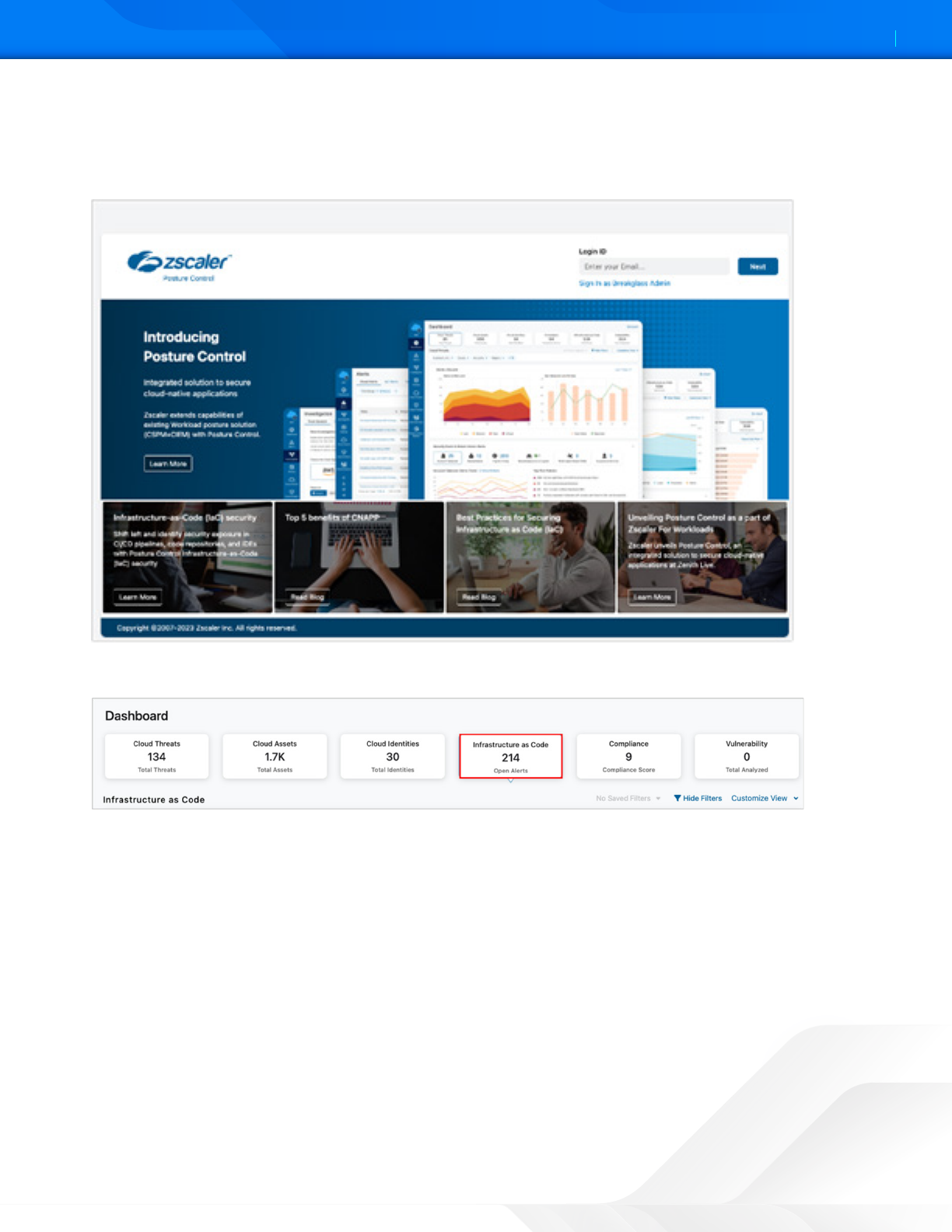
To visualize the GitLab alerts generated by the Zscaler IaC Scan tool:
1. Login to the ZPC Admin Portal.
Figure 11. ZPC Admin Portal
2. Select Infrastructure as Code.
Figure 12. ZPC Infrastructure as Code widget
ZSCALER AND GITLAB DEPLOYMENT GUIDE
20©2024 Zscaler, Inc. All rights reserved.
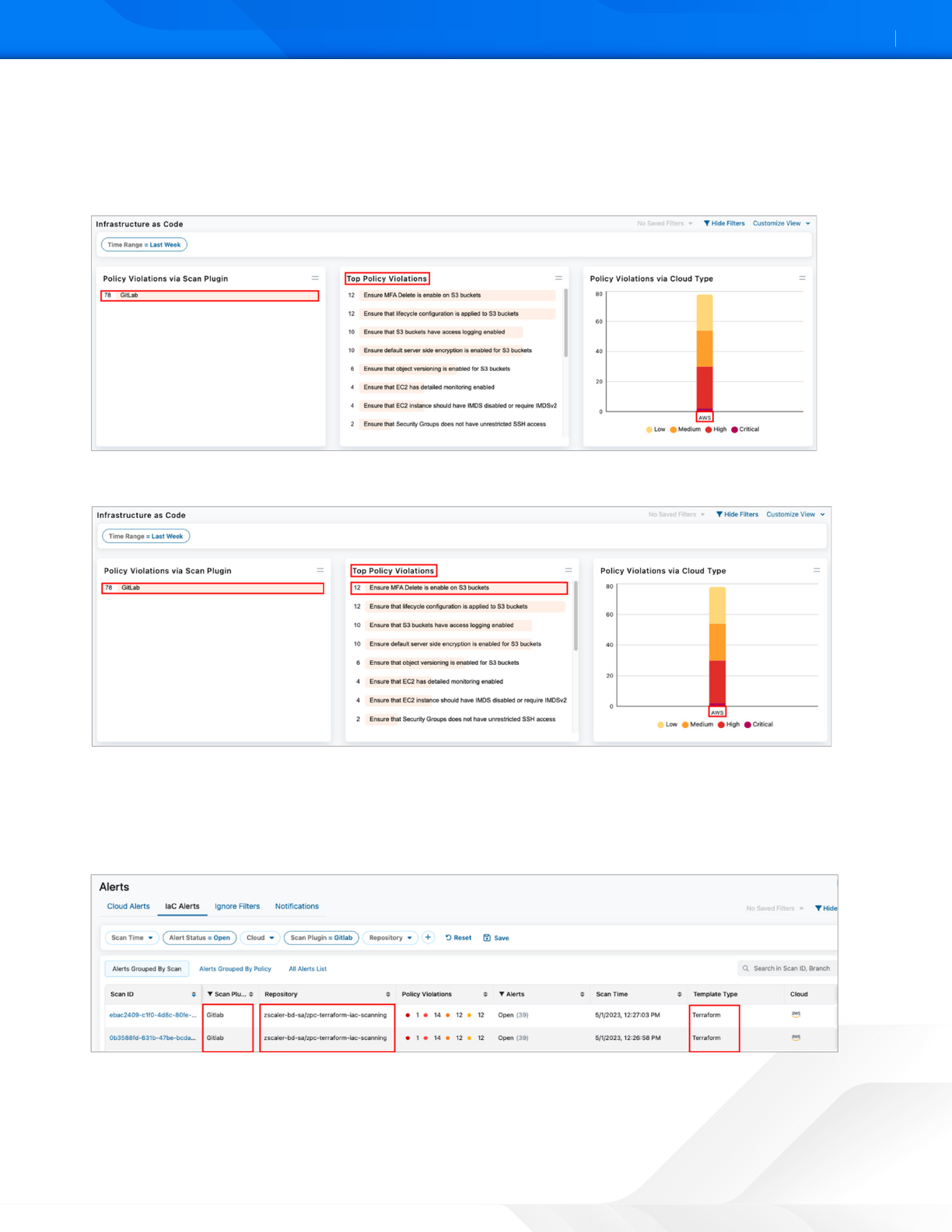
3. In the main Infrastructure as Code dashboard, Zscaler provides a summary of the following:
• Policy Violations via Scan Plugin
• Top Policy Violations
• Policy Violations via Cloud Type
Figure 13. ZPC Infrastructure as Code dashboard summary
4. Select one of the Top Policy Violations. In this example, Ensure MFA Delete is enabled on S3 buckets is selected.
Figure 14. ZPC Infrastructure as Code Top Policy Violations
5. The administrator can also group the IaC alerts by scan type. In the following example, the filter only displays Scan
Plugin = GitLab.
a. Other filters are also available (e.g., Scan Time, Alert Status, Cloud, and Repository).
b. You can add other filters by selecting the Add icon (+) in the filter area.
Figure 15. ZPC IaC Alerts by Scan Plugin
ZSCALER AND GITLAB DEPLOYMENT GUIDE
21©2024 Zscaler, Inc. All rights reserved.
6. (Optional) Select the top violations and automatically create an IaC alerts filter containing all violations originated by
the GitLab scan plugin.
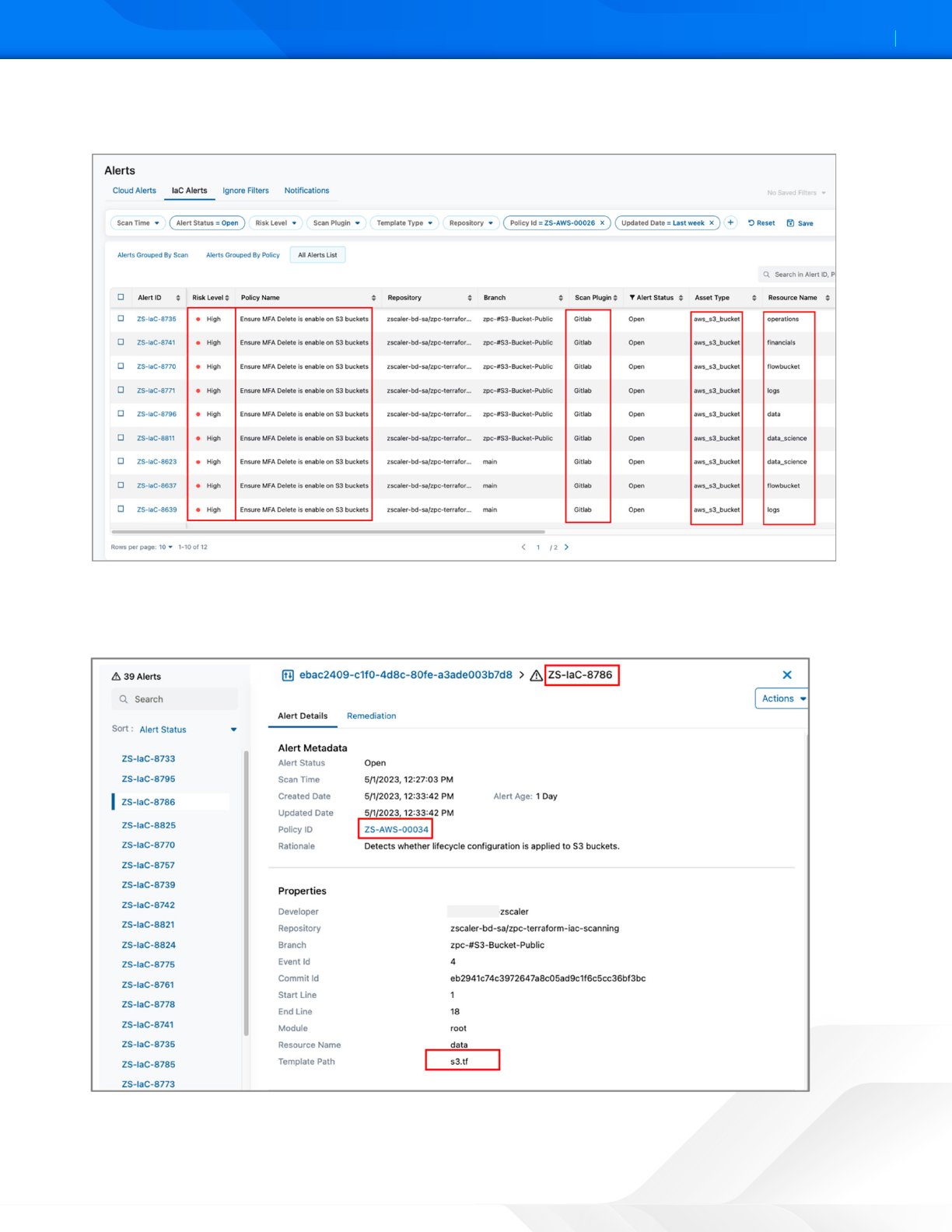
Figure 16. ZPC IaC Alerts
7. Select one of the alerts listed in the Alert ID column. This example selects the alert ID ZS-IaC-8786, which indicates
that ZPC has detected a violation associated with a Policy ID: ZS-AWS-00034. This policy detects whether the
lifecycle configuration is applied to the S3 bucket.
Figure 17. ZPC Alert Details
ZSCALER AND GITLAB DEPLOYMENT GUIDE
22©2024 Zscaler, Inc. All rights reserved.
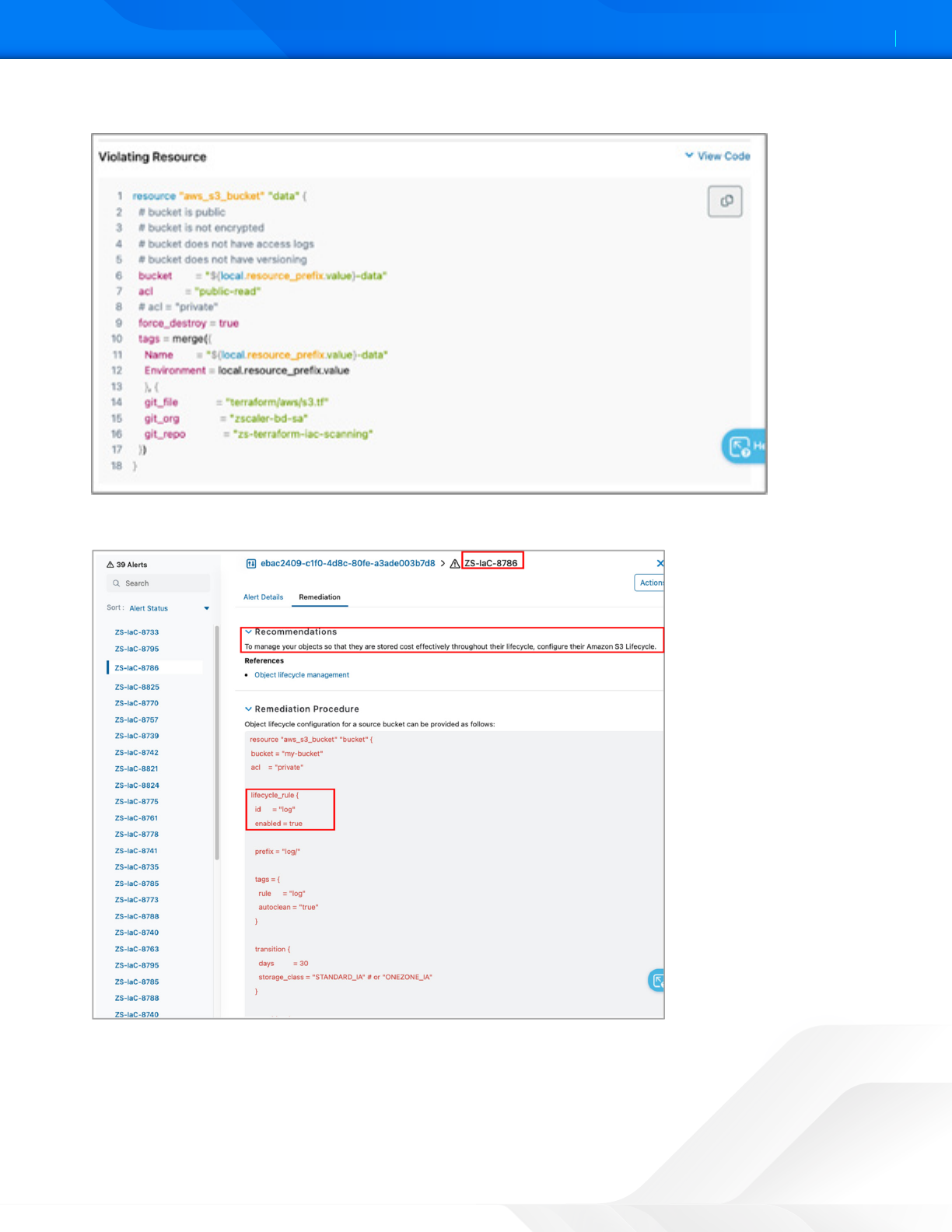
8. See the code snippet with information about the Violating Resource.
Figure 18. ZPC Violating Resource
9. To remediation recommendation procedures, select the Remediation tab.
Figure 19. ZPC Remediation
ZSCALER AND GITLAB DEPLOYMENT GUIDE
23©2024 Zscaler, Inc. All rights reserved.
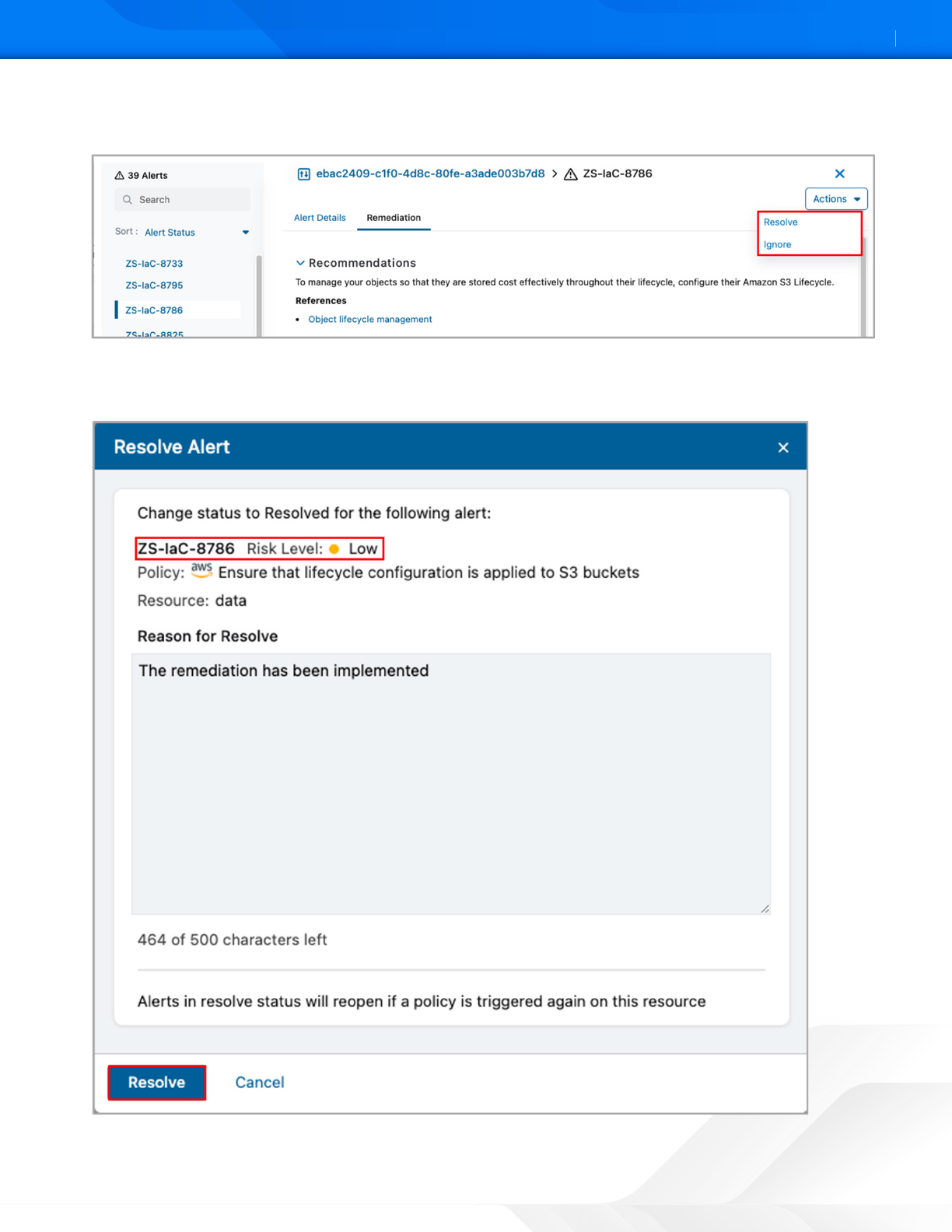
10. To resolve or ignore the alert, select the Actions option, and then select Resolve or Ignore. This example uses
Resolve. The Resolve Alert screen is displayed..
Figure 20. Alert Actions
11. Enter a reason to resolve the alert.
12. Click Resolve.
Figure 21. Resolve Alert
ZSCALER AND GITLAB DEPLOYMENT GUIDE
24©2024 Zscaler, Inc. All rights reserved.
Resolving Failed Integrations
Use Case 1
GitLab integration that worked previously can be disrupted (e.g., if a user accidentally unauthorizes the Zscaler IaC Scan
in GitLab or if the authorization token is corrupted in the ZPC Admin Portal). Instead of deleting the GitLab account and
repeating the configuration steps again, you can reauthorize the existing integration.
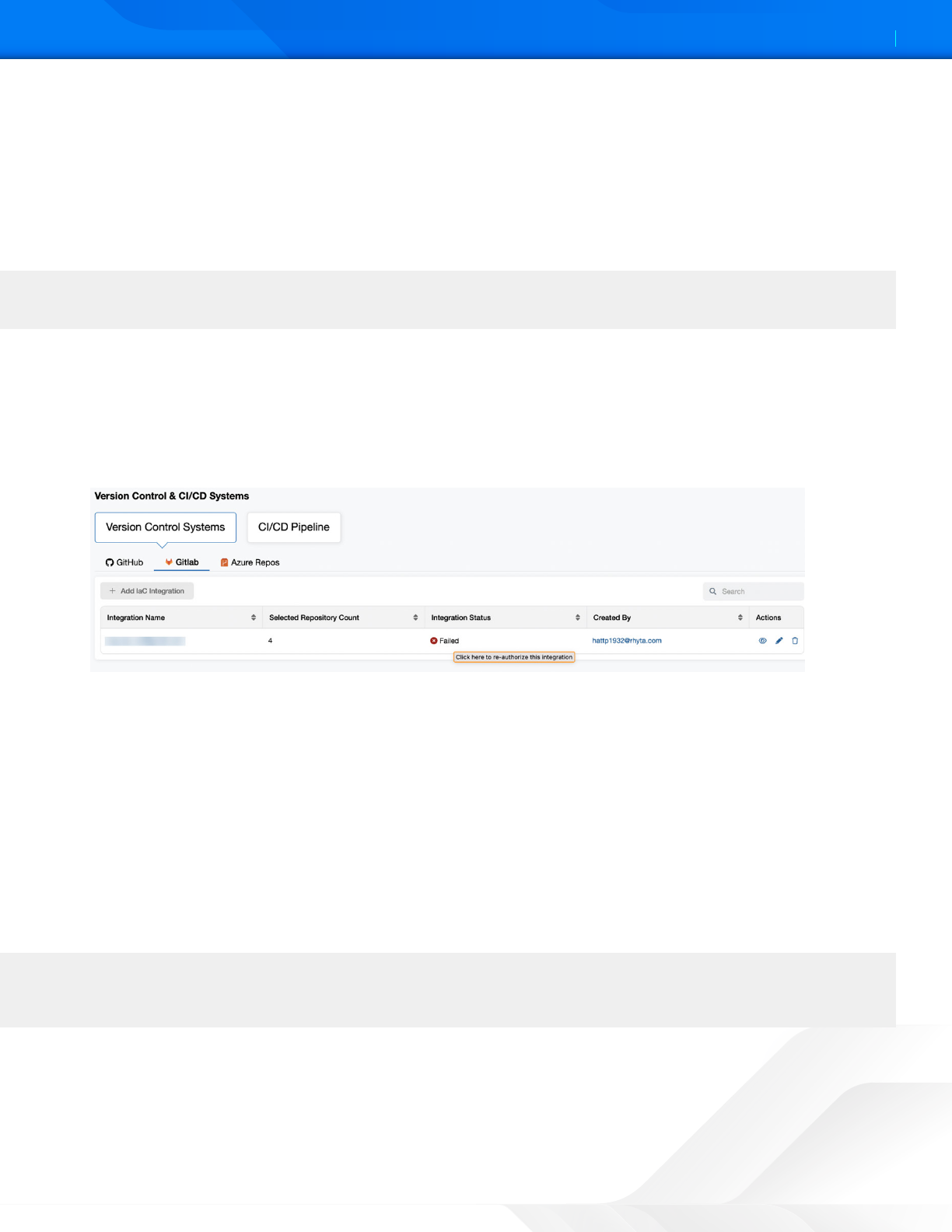
To reauthorize a GitLab integration:
1. Go to Version Control & CI/CD Systems.
2. Under Version Control Systems, click the GitLab tab.
3. Search for the integration that failed.
4. Hover the mouse over the Failed status to see the following tooltip: Click here to reauthorize this integration.
Figure 22. Failed GitLab integration
5. Click the tooltip to go to the GitLab Authorization page.
6. Click Authorize Zscaler GitLab App to re-establish the connection between GitLab and the ZPC Admin Portal and
enable IaC scanning of the GitLab repositories.
A confirmation message appears indicating that the reauthorization is successful, and you are redirected to the Version
Control & CI/CD Systems page. The Integration Status is displayed as Success for that integration.
Use Case 2
For failed integrations, the Integration Status is displayed as Failed in the ZPC Admin Portal. In this case, if you offboard
the tenant or unsubscribe from the IaC service entitlement, then the integration is deleted from ZPC, but the webhooks
are not deleted from the GitLab repository. You need to manually delete the webhooks.
When an integration fails, the Integration Status is displayed as Failed in the ZPC Admin Portal.
If you don’t delete the webhooks, then you can’t integrate the GitLab account whenever you subscribe for the IaC
entitlement again.

ZSCALER AND GITLAB DEPLOYMENT GUIDE
25©2024 Zscaler, Inc. All rights reserved.
Zscaler Data Protection for GitLab
Gitlab is a service that provides remote access to Git repositories. In addition to hosting your code, the services provide
additional features for managing the soware development lifecycle.
There are two soware distributions of GitLab:
• The open source Community Edition (CE).
• The open core Enterprise Edition (EE).
GitLab is available under different subscriptions. New versions of GitLab are released from stable branches, and the main
branch is used for bleeding-edge development. To learn more, refer to the GitLab release process.
Both distributions require additional components. These components are described in the Component details section,
and all have their own repositories. New versions of each dependent component are usually tags, but staying on the
main branch of the GitLab codebase gives you the latest stable version of those components. New versions are generally
released around the same time as GitLab releases, with the exception of informal security updates deemed critical.
Ensuring every employee always uses the best SaaS application safety practices is impossible, which leads to costly
mistakes for the organization. Risk associated with accidental data exposure, malicious intent, and compliance violations
forces companies to restrict or prevent use of these incredible business tools. This is where Zscaler helps GitLab users.
The following diagram shows a conceptualization of the integration between Zscaler and GitLab.
Figure 23. Zscaler solutions for GitLab
ZIA provides security for GitLab SaaS platform through access control, identity control, SaaS Security Posture
Management, a SaaS API to scan the aachments for malicious content, and DLP. ZIA also provides complete security for
clients whether they are in the corporate office or their home office.
This guide covers the following ZIA features for GitLab security:
• ZIA Cloud Browser Isolation
• SaaS Security Data Loss Protection and Malware Detection
• ZIA Cloud Application Control
• ZPC and GitLab Integration
ZSCALER AND GITLAB DEPLOYMENT GUIDE
26©2024 Zscaler, Inc. All rights reserved.
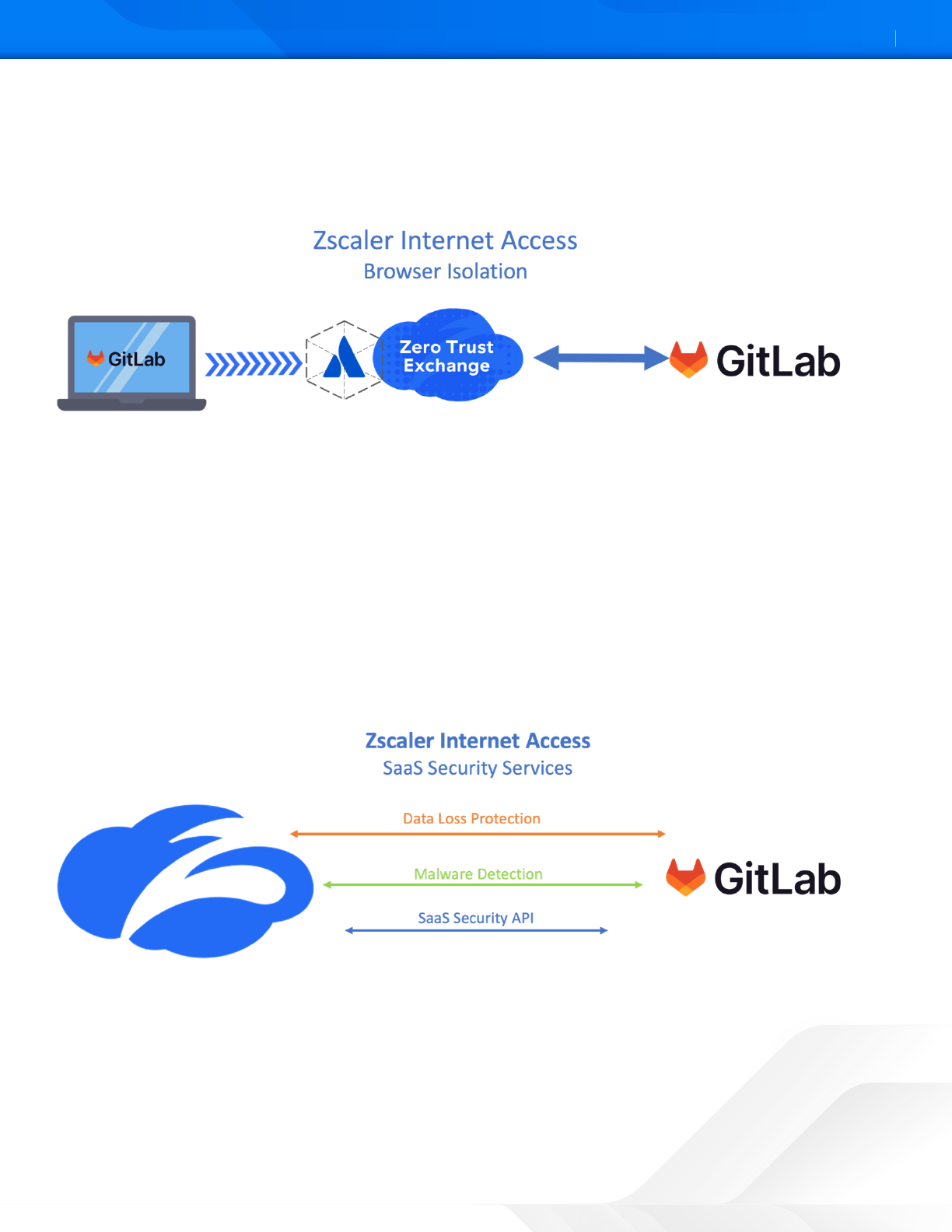
ZIA Cloud Browser Isolation
Most new threats that target organizations are browser-based. As a result, organizations are le struling to keep these
threats from reaching endpoint devices and preventing sensitive data from leaking out, while concurrently providing
unobstructed internet access for users.
Figure 24. ZIA Cloud Browser isolation in use with GitLab product
Zscaler Cloud Browser Isolation provides safe access to active web content for your users by rendering browser content
in an isolated environment, and by minimizing the browser aack surface. Sensitive information is protected from web-
based malware and data exfiltration.
By defining granular policies based on user group or department, you can effectively protect endpoint devices and
prevent confidential data exposure from business-critical applications by managing user activity within the isolation
environment enabling viewing actions within GitLab platform, while preventing the downloading and copying-and-
pasting of confidential business data.
ZIA Data Loss Protection and Malware Detection for GitLab
The Zscaler SaaS Security API is part of the ZIA security cloud and designed specifically to help manage the risks of our file
collaboration SaaS partners, preventing data exposure and ensuring compliance across the SaaS application.
Figure 25. ZIA SaaS Security in use with GitLab Product
The Zscaler SaaS Security API enables organizations to securely adopt and govern the use of multiple SaaS applications.
It provides real-time visibility and controls access and user activity across sanctioned and unsanctioned applications. The
fully integrated platform eliminates overlay architectures and simplifies policy creation and administration, ensuring data
is protected and compliance is maintained.

ZSCALER AND GITLAB DEPLOYMENT GUIDE
27©2024 Zscaler, Inc. All rights reserved.
What Makes Zscaler SaaS Security unique?
• Data exposure reporting and remediation: Zscaler SaaS Security API checks SaaS applications and cloud providers’
configurations and compares them to industry and organizational benchmarks to report on violations and automate
remediation.
• Threat identification and remediation: Zscaler SaaS Security API checks SaaS applications for hidden threats being
exchanged and prevents their propagation.
• Compliance assurance: Zscaler SaaS Security API provides compliance visibility across SaaS and cloud providers and
can mitigate violations automatically.
• Part of a larger data protection platform: The Zscaler Cloud Security Platform provides unified data protection with
DLP, and malware scanning capabilities for internet, data center, and SaaS applications, and ensures that public cloud
applications are configured to prevent data exposure and maintain compliance. Zscaler also offers Zscaler Private
Access (ZPA) for zero-trust access to internal applications, ZDX for active monitoring of users’ experience to SaaS
applications, and Zscaler Cloud Protection (ZCP). Zscaler provides end to end connectivity, security, and visibility
from any location on-prem or remote.
To learn more, see the resources in Zscaler Resources.
ZIA Cloud Application Control
The ZIA security cloud is a fully integrated cloud-based security stack that sits in-line between users and the internet,
inspecting all traffic (including SSL) flowing between them. Zscaler Cloud Application Visibility and Control delivers
full visibility into application usage. Granular policies ensure the proper use of both sanctioned and unsanctioned
applications. SaaS tenant security is referred to as out-of-band for data-at-rest. Zscaler cloud application security is
referred to as in-line.
Figure 26. Cloud App Control
Cloud App Control provides SaaS application intelligence to consolidate all associated URLs and functions of an
application in a single security seing. This allows the control of specific users, groups, locations, or departments, and only
allows the required users access to the application.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
28©2024 Zscaler, Inc. All rights reserved.
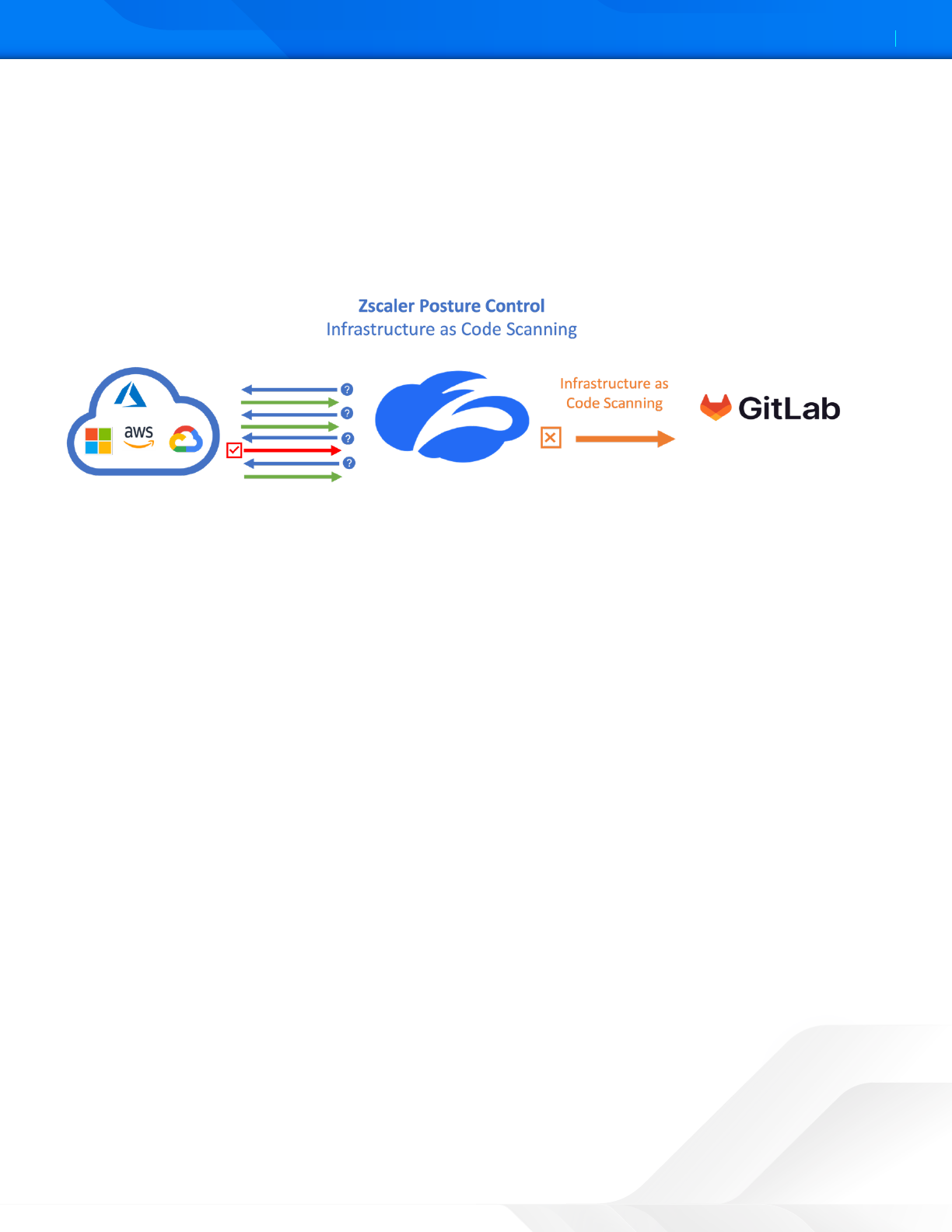
ZPC and GitLab Integration
The ZPC IaC Scan app scans and identifies security misconfigurations in the IaC Terraform, Helm, Kubernetes, and
CloudFormation templates within GitLab. When you add or update the code and make a merge request, the IaC Scan
action automatically triers a scan of the IaC templates, identifies security misconfigurations, and displays the scan
results within the code. This allows you to fix the configuration errors before deployment, and ensure your code is secure
and compliant with the security policies.
Figure 27. ZPC and GitLab integration
ZSCALER AND GITLAB DEPLOYMENT GUIDE
29©2024 Zscaler, Inc. All rights reserved.
Configure Cloud Browser Isolation
Zscaler Cloud Browser Isolation provides safe access to active web content for your users by rendering browser content
in an isolated environment, and by minimizing the browser aack surface. Sensitive information is protected from web-
based malware and data exfiltration.
Figure 28. ZIA Cloud Browser Isolation in use with GitLab
By defining granular policies based on user group or department, you can effectively protect endpoint devices and
prevent confidential data exposure from business-critical applications by managing user activity within the isolation
environment enabling viewing in GitLab platform while preventing the downloading and cuing-and-pasting of
confidential business data.
Configure the Cloud Browser Isolation Profile
To begin the Cloud Browser Isolation configuration, log into the ZIA Admin Portal with administrator credentials.
You must configure a Browser Isolation Profile (or multiple profiles) to use Zscaler Cloud Browser Isolation features
specifically for GitLab products, along with an individual user profile for the user using Browser Isolation.
For example, you could have a policy to control file uploads for one client and copy and paste for another.
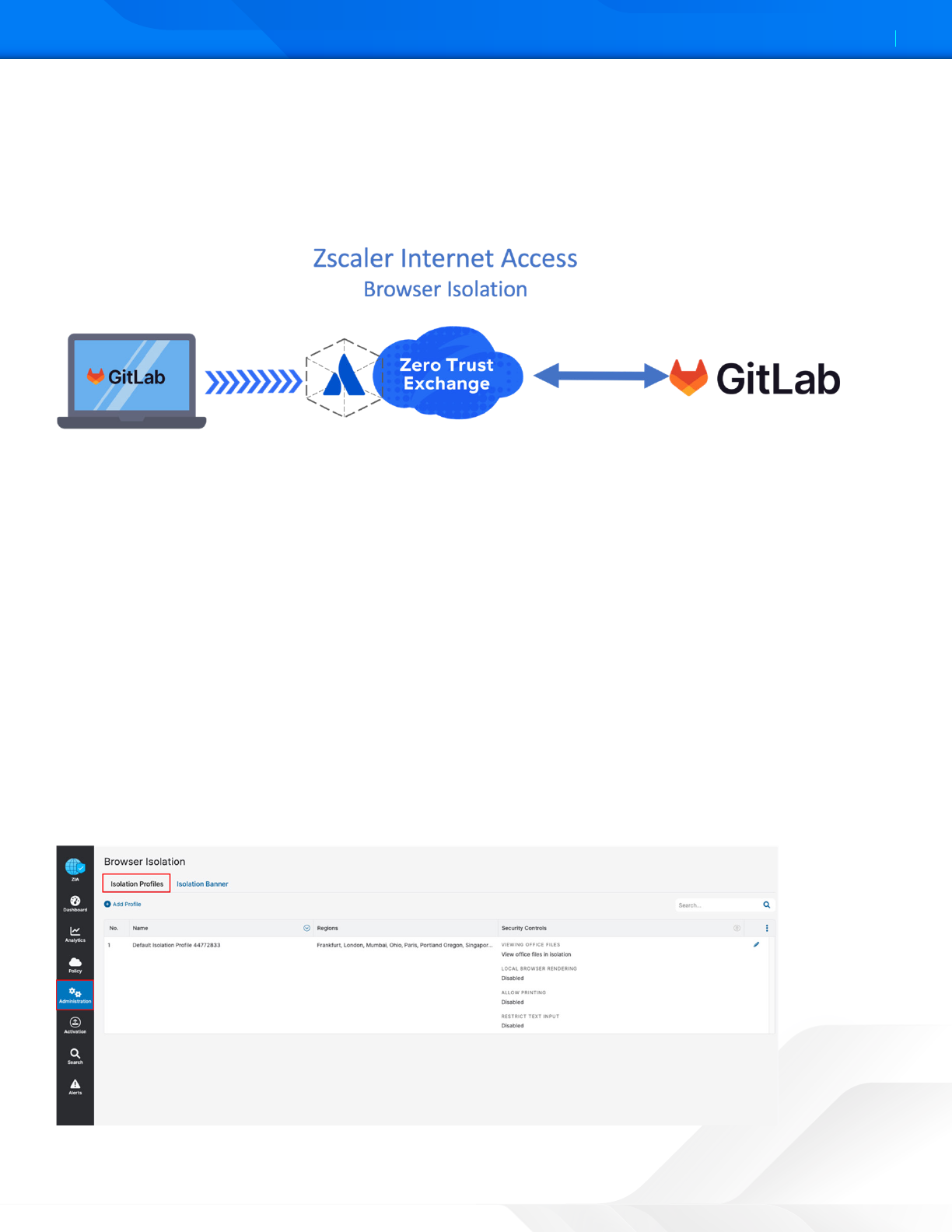
To start the Policy Wizard:
1. Go to Administration > Secure Browsing > Browser Isolation.
2. Select the Isolation Profiles tab.
3. Click Add Profile.
Figure 29. Cloud Browser Isolation Profile
ZSCALER AND GITLAB DEPLOYMENT GUIDE
30©2024 Zscaler, Inc. All rights reserved.
This starts the Browser Isolation wizard and steps you through enabling General Information, Company Seings, Security
Controls, Regional Connectivity, and the End User Notification.
For General Information, give the profile an intuitive name and description. It is selected in the Isolation Policy on the ZIA
portal and should be clear to the use case:
1. Name the profile.
2. Give the profile a detailed Description.
Figure 30. Cloud Browser General Information
ZSCALER AND GITLAB DEPLOYMENT GUIDE
31©2024 Zscaler, Inc. All rights reserved.
Make your selections in the Company Seings section:
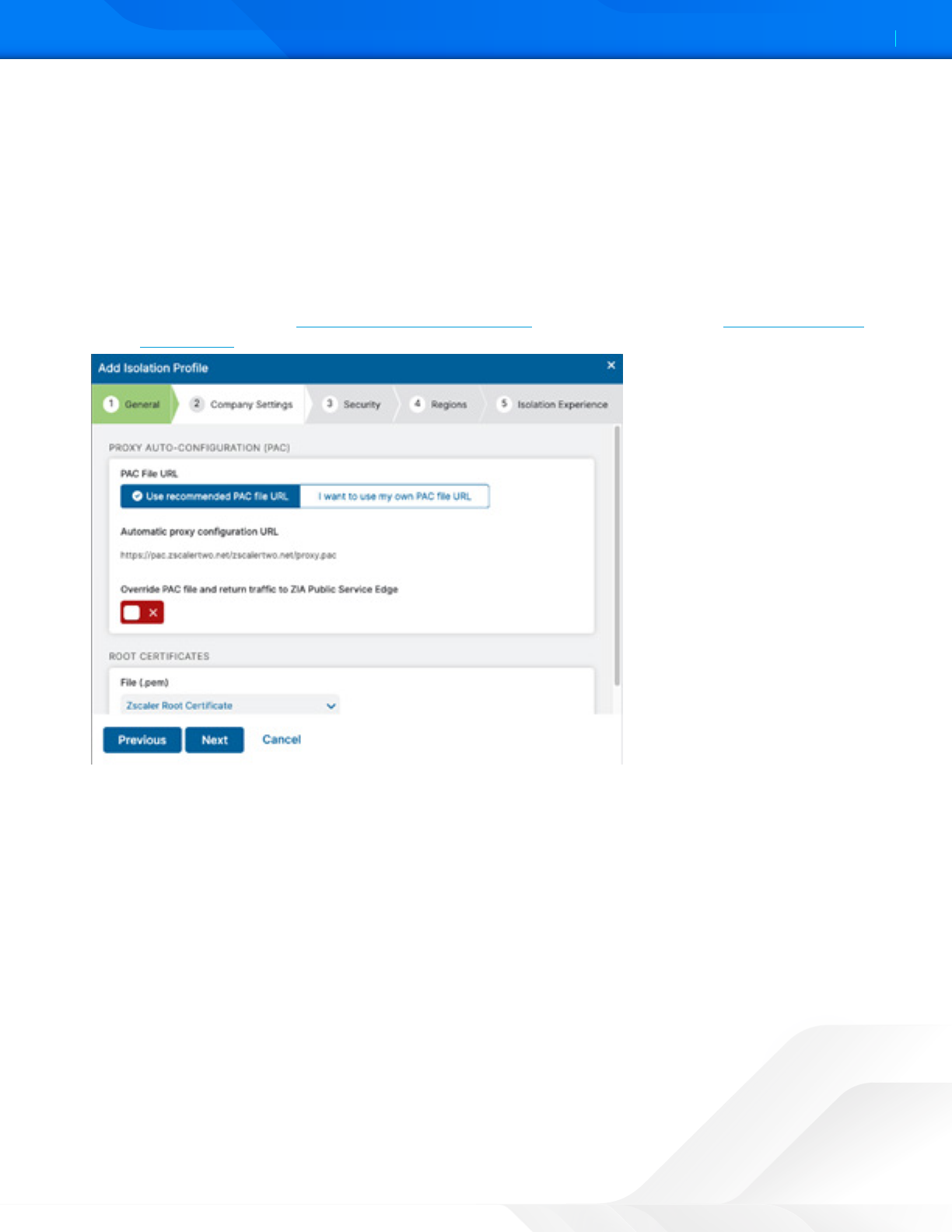
a. Choose to either use the recommended PAC file URL or to use your own manually configured PAC file URL:
• If you choose to use the recommended PAC file URL, the Automatic proxy configuration URL field is
populated by default with the recommended PAC file from your Hosted PAC Files list in ZIA. This PAC file
is configured onto the isolation browser within the endpoint experience containers, and any traffic to the
internet from the isolated browser is also forwarded through the ZIA cloud.
• Enable or disable the option to Override the PAC File and return traffic to the ZIA Public Service Edge. The
ZIA Public Service Edges use auto-geo proximity, meaning that the traffic is returned to the service edge
closest to the location of the user, not the location of the isolation browser. To see the full list of ZIA Public
Service Edges, see the Cloud Enforcement Node Ranges (government agencies, see Cloud Enforcement
Node Ranges).
Figure 31. Proxy Auto-Configuration (PAC)
ZSCALER AND GITLAB DEPLOYMENT GUIDE
32©2024 Zscaler, Inc. All rights reserved.
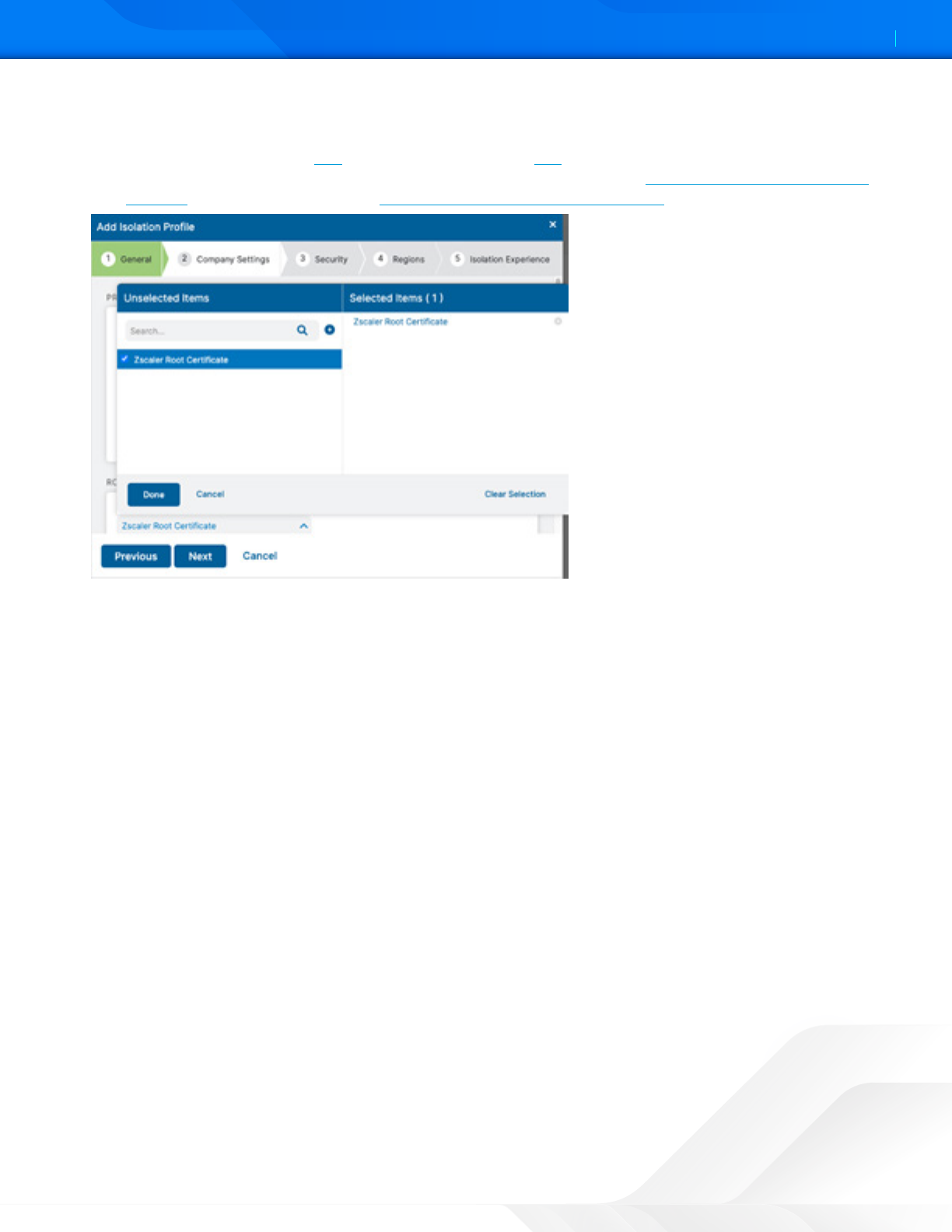
b. Select from the drop-down menu at least one Root Certificate. The Zscaler Root Certificate used for SSL
inspection by ZIA is listed by default in the drop-down menu. If your organization uses custom root certificates
for SSL inspection, you can add (government agencies, see add) them before creating isolation profiles. You
can add up to ten root certificates for your organization. To learn more, see About ZIA Root Certificates for
Isolation (government agencies, see About ZIA Root Certificates for Isolation).
Figure 32. Zscaler Root Certificate
3. Click Done.
4. Click Next.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
33©2024 Zscaler, Inc. All rights reserved.
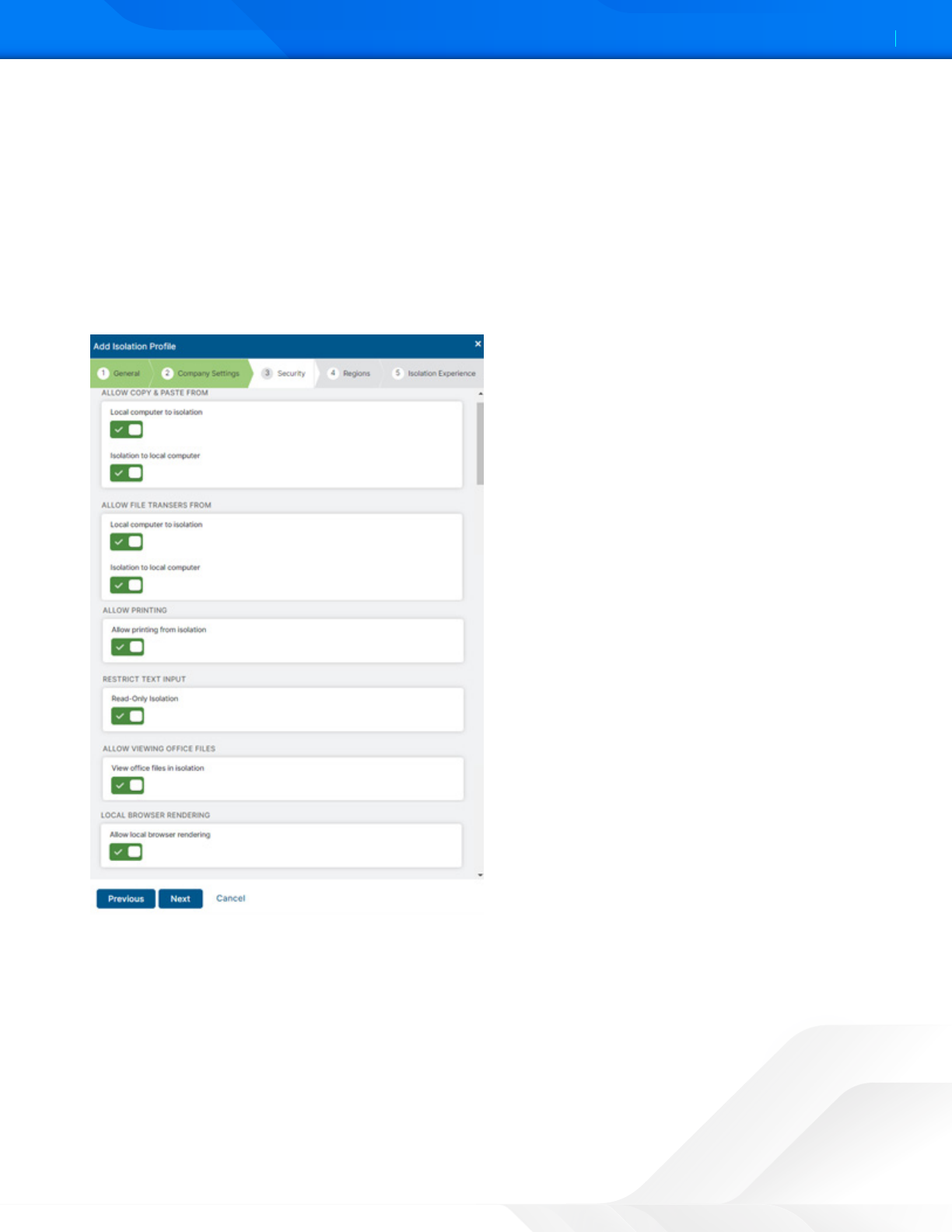
5. The Security Control of Browser Isolation allows administrators to maintain a complete air gap between the user and
GitLab or allow some level of control of the GitLab application in the Isolation Session. Enable or disable the different
seings in the Security section:
• Allow copying and pasting to and from your computer and the isolation browser.
• Allow file transfers to and from your computer and the isolation browser.
• Allow printing of web pages and inline content from isolation.
• Restrict keyboard/text input to isolated web pages.
• Allow viewing office files while in isolation.
• Allow local browser rendering while in isolation.
Figure 33. Security seings
ZSCALER AND GITLAB DEPLOYMENT GUIDE
34©2024 Zscaler, Inc. All rights reserved.
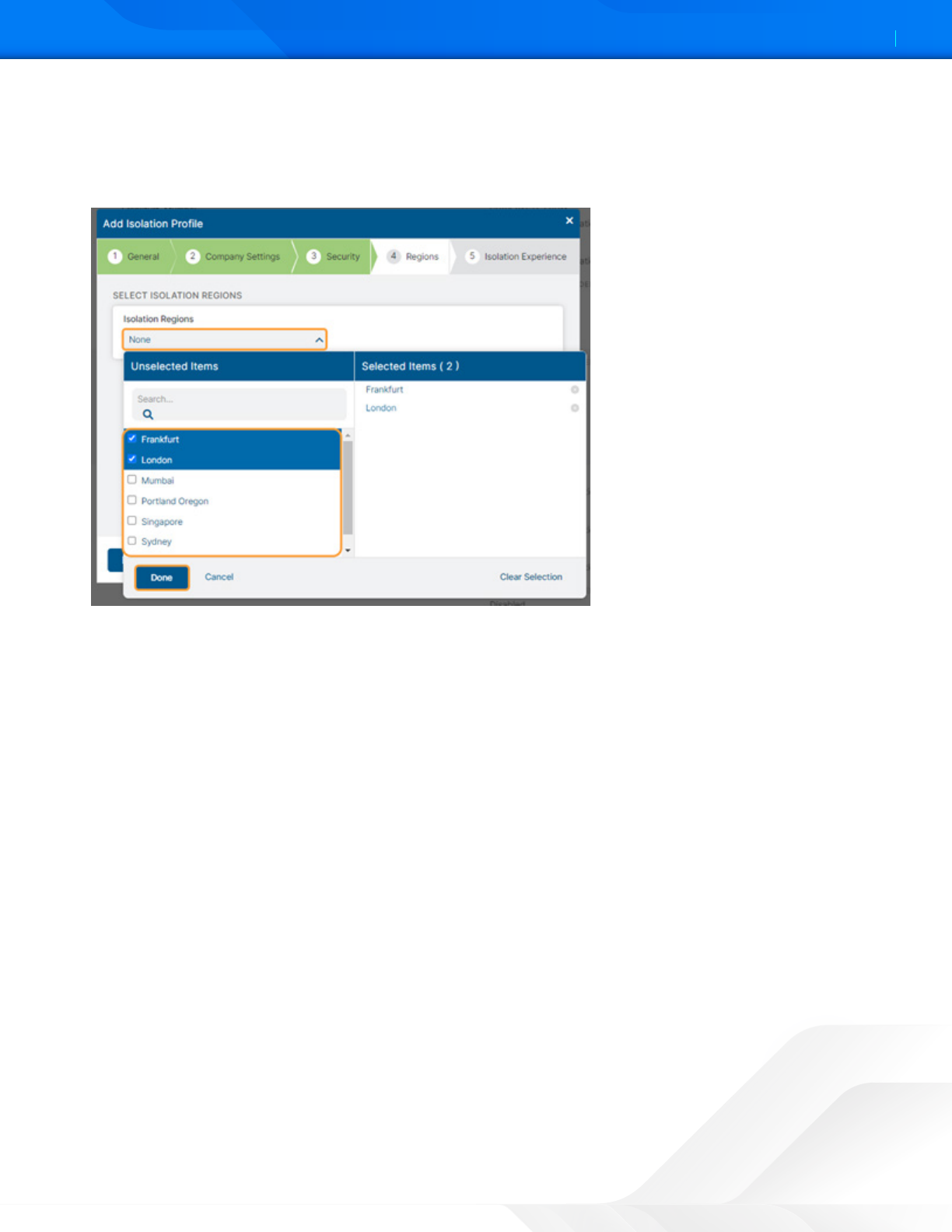
6. Enable at least two Regions for the isolation profile by selecting from the drop-down menu. The isolation containers
are leased to the user only from the selected regions based on the least network latency.
7. Click Done.
8. Click Next.
Figure 34. Select Isolation Regions
ZSCALER AND GITLAB DEPLOYMENT GUIDE
35©2024 Zscaler, Inc. All rights reserved.
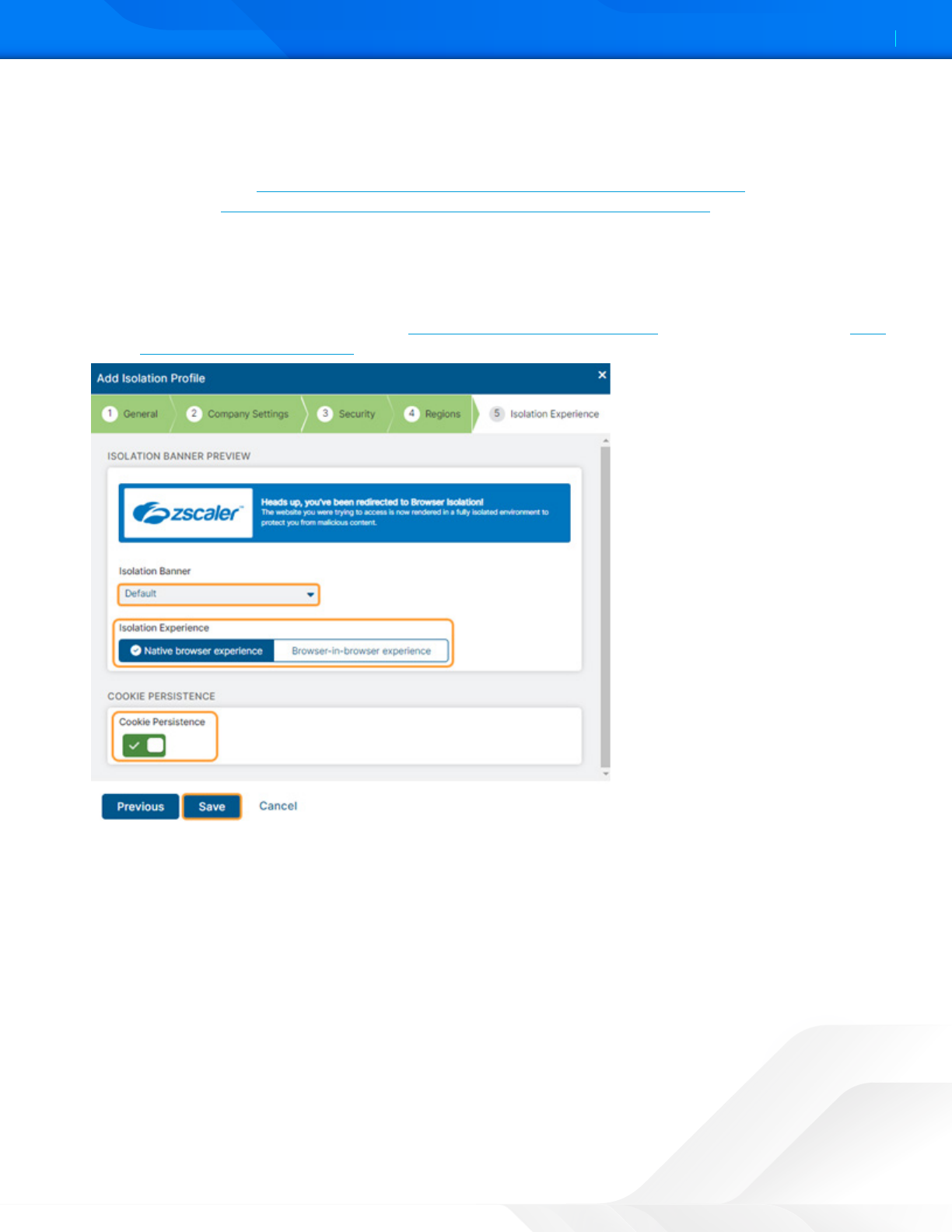
9. Make your selections for the user’s Isolation Experience:
a. Select an Isolation Banner from the drop-down menu. The option you choose shows a preview banner in the
window. You choose from existing banners or create custom isolation banners to use for your isolation profiles.
To learn more, see Adding a Banner Theme for the Isolation End User Notification in ZIA (government
agencies, see Adding a Banner Theme for the Isolation End User Notification in ZIA).
b. Select the Isolation Experience mode:
• Native browser experience: This mode provides the user with a browsing experience similar to accessing the
native web page natively typical browser. You can also customize this view.
• Browser-in-browser experience: This mode provides the user with the complete look and feel of an isolated
session experience. To learn more, see User Experience Modes in Isolation (government agencies, see User
Experience Modes in Isolation).
Figure 35. Isolation Experience
ZSCALER AND GITLAB DEPLOYMENT GUIDE
36©2024 Zscaler, Inc. All rights reserved.
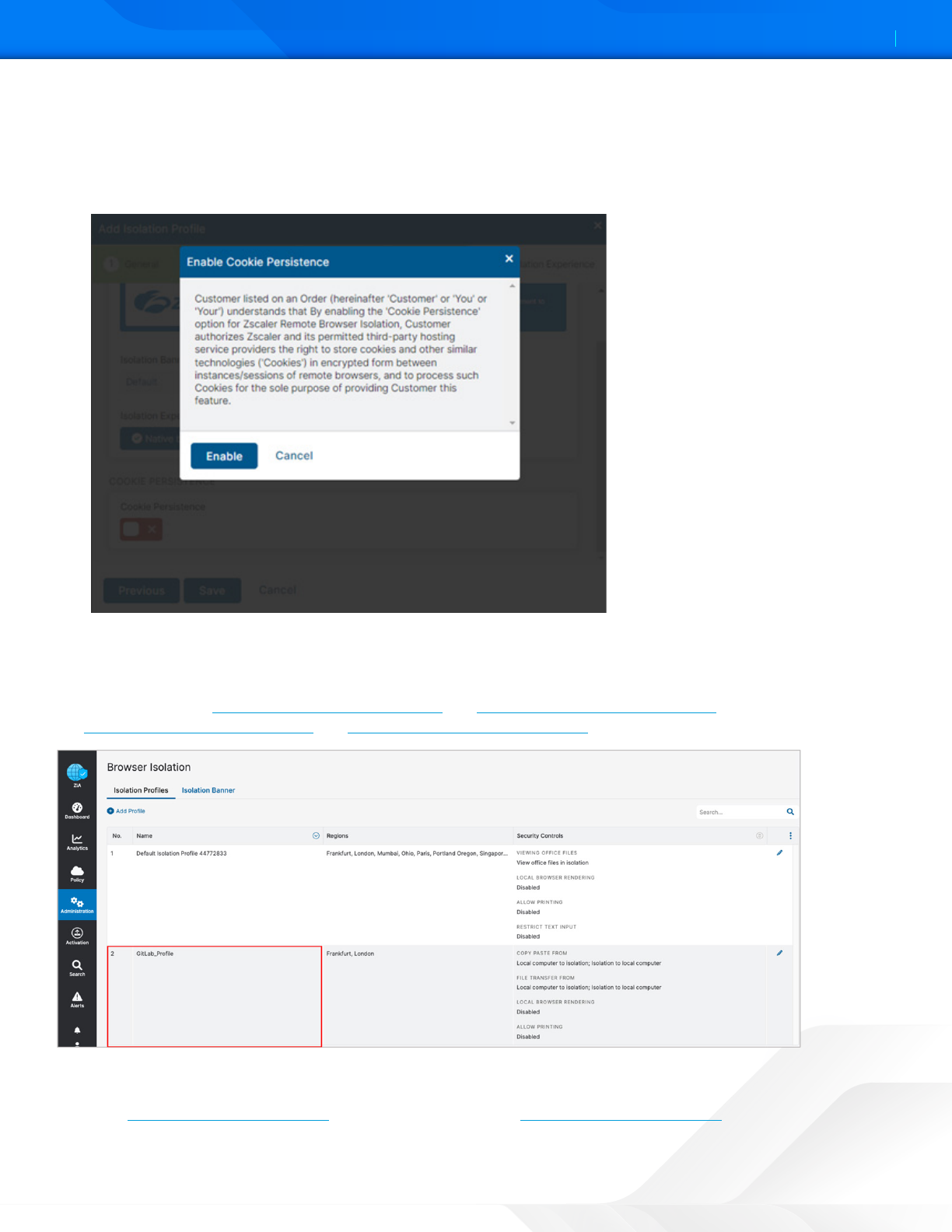
c. (Optional) Enable Cookie Persistence. Upon enabling, the Enable Cookie Persistence window displays the
consent message for the admin to read before enabling. This action means the cookies set by the websites
and accessed by a user through isolation persist across browsing sessions. If this option is enabled, the cookies
are stored in an encrypted storage. If not enabled, no cookies persist, meaning they are destroyed with the
container upon the user’s logout or upon exceeding the session timeout.
Figure 36. Enable cookie persistence
d. Click Save.
When saved, your new isolation profile appears in the list of ZIA Isolation Profiles. You can edit a profile directly from the
list. To learn more, see Editing Your ZIA Isolation Profile and Deleting Your ZIA Isolation Profile (government agencies,
see Editing Your ZIA Isolation Profile and Deleting Your ZIA Isolation Profile).
Figure 37. Isolation Profile
You can use this isolation profile to create a policy in ZIA to allow traffic forwarding through browser isolation. To learn
more, see Configuring ZIA for Isolation (government agencies, see Configuring ZIA for Isolation).
ZSCALER AND GITLAB DEPLOYMENT GUIDE
37©2024 Zscaler, Inc. All rights reserved.
Configure GitLab SaaS Application Tenant
To launch the SaaS Application Tenants wizard for the ZIA Admin Portal:
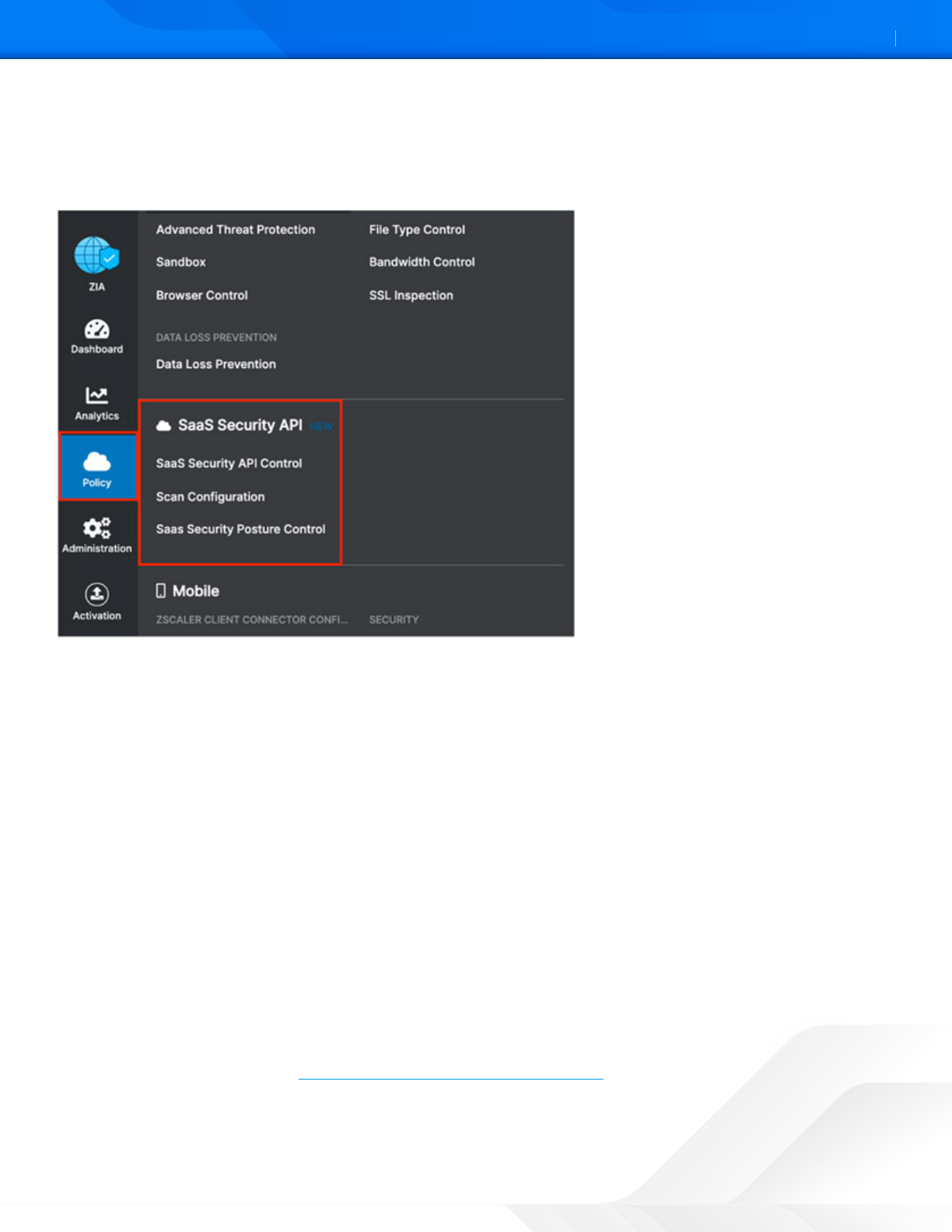
1. Go to Administration > SaaS Application Tenants.
2. In the SaaS Application Tenants window, select Add SaaS Application Tenant.
Figure 38. ZIA SaaS Application Tenant

ZSCALER AND GITLAB DEPLOYMENT GUIDE
38©2024 Zscaler, Inc. All rights reserved.
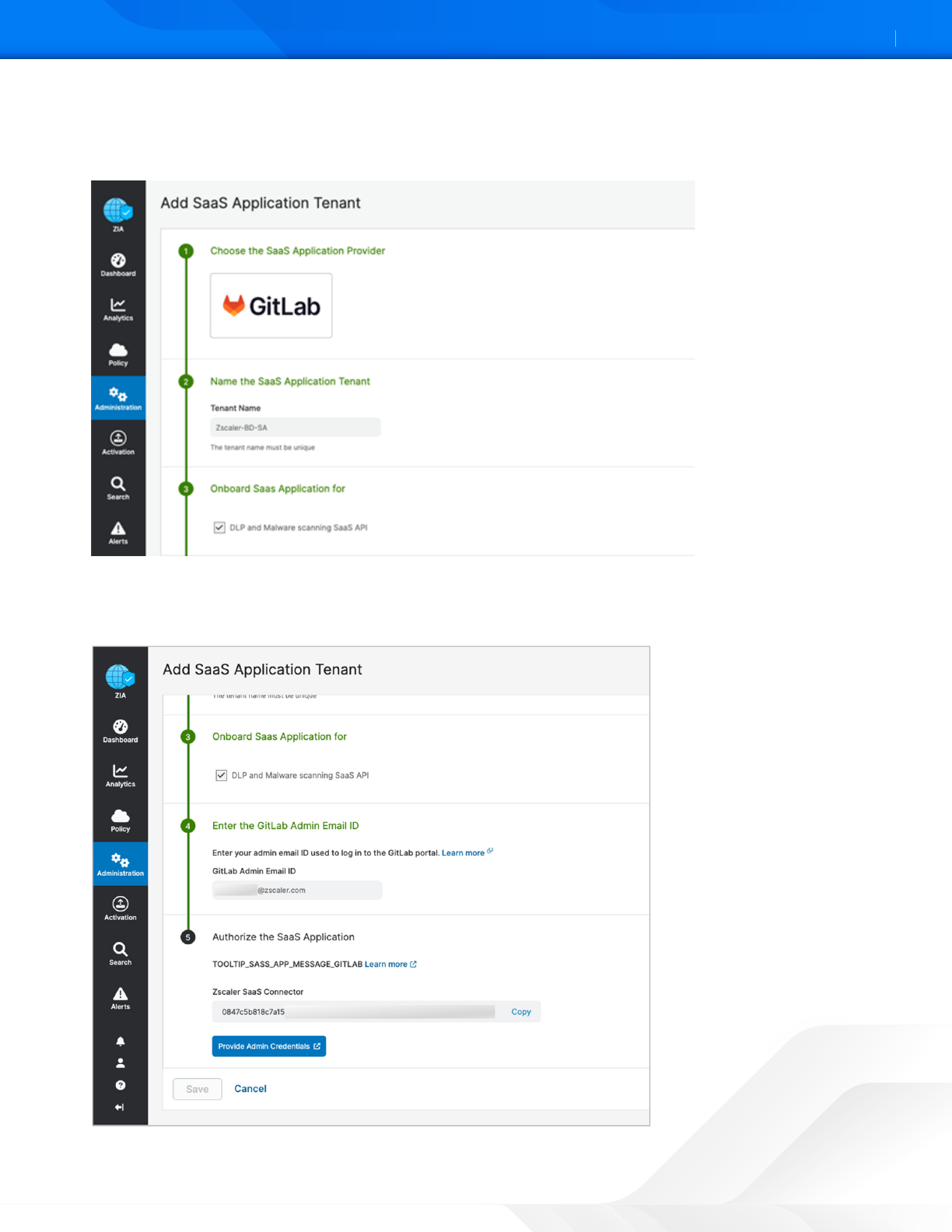
GitLab SaaS Tenant Configuration Wizard
To start the wizard:
1. Select Add SaaS Application Tenant on the tenant page.
2. Select the GitLab tile on the wizard.
Figure 39. GitLab SaaS Application Tenant
ZSCALER AND GITLAB DEPLOYMENT GUIDE
39©2024 Zscaler, Inc. All rights reserved.
3. Enter a name in the Tenant Name. This is the name that is selected when assigning a policy for the Zscaler security
features.
4. Select the DLP and Malware Scanning SaaS API checkbox.
Figure 40. SaaS Application Tenant configuration
5. Enter the GitLab Admin Email ID.
6. Click Provide Admin Credentials, which redirects you to the GitLab login page.
Figure 41. SaaS Application Tenant configuration
ZSCALER AND GITLAB DEPLOYMENT GUIDE
40©2024 Zscaler, Inc. All rights reserved.
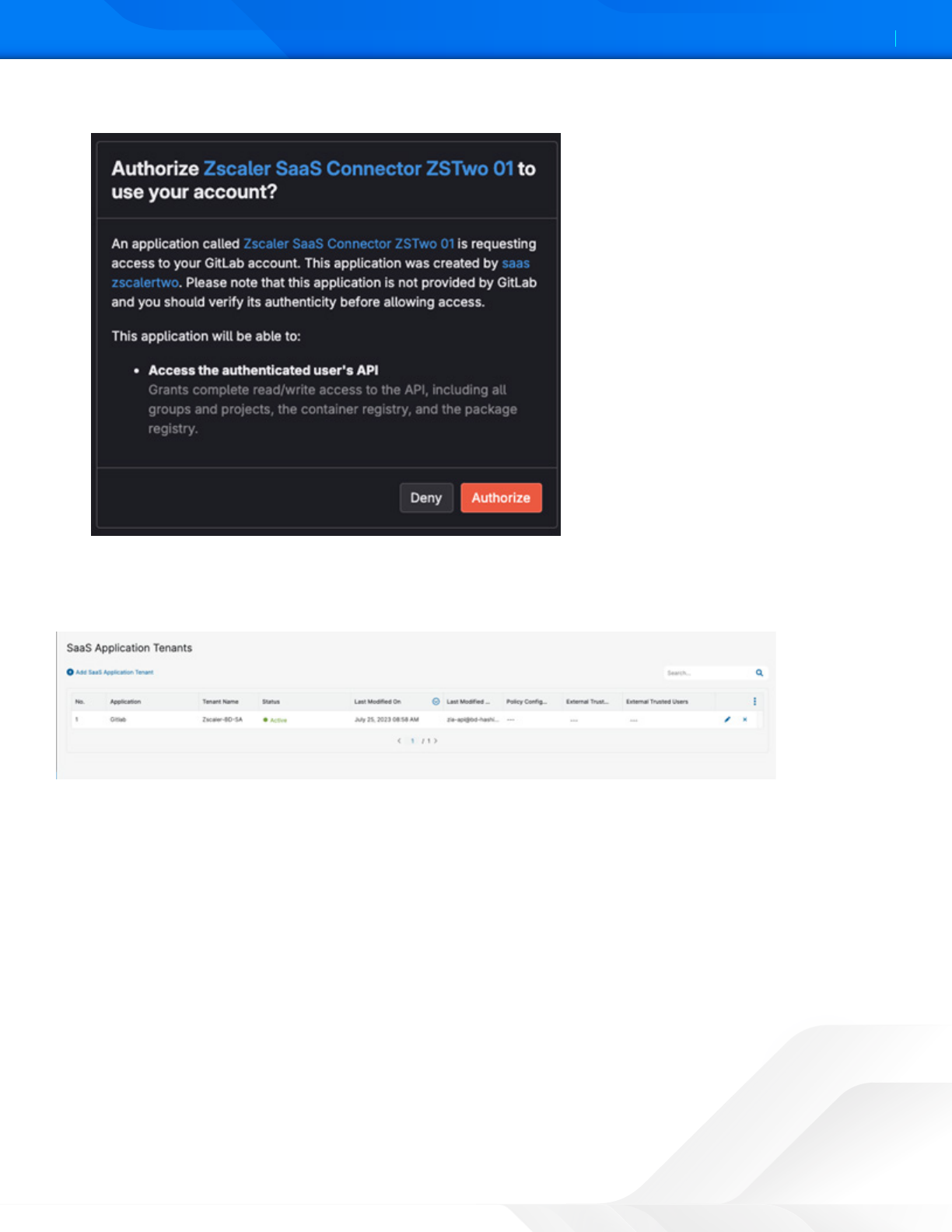
7. Click Authorize to give permission to Zscaler SaaS Connector.
Figure 42. Authorize Zscaler SaaS Connector
8. The Zscaler Onboard window is displayed. Click Save.
The completed and active GitLab API connector is displayed.
Figure 43. GitLab SaaS Tenant Activation Complete
ZSCALER AND GITLAB DEPLOYMENT GUIDE
41©2024 Zscaler, Inc. All rights reserved.
Configure GitLab Policies and Scan Configuration
Aer adding and configuring the GitLab tenant, configure the SaaS Security API to control DLP, malware policies, and scan
the configuration for the policies. You can also view reports and data for GitLab in analytics, SaaS security insights, and
logs.
Figure 44. SaaS Security API configuration
Scoping the Policies and Remediation
Zscaler SaaS security scans file aachments. This deployment guide configures a basic DLP policy and a malware policy.
The policies scan the GitLab files for matching content of the DLP policy and known malware for the malware policy. A
GitLab repository is created with malicious aachments and DLP violations to test the policies.
Zscaler SaaS security out-of-band data protection capabilities look inside the SaaS applications themselves through
API integrations to identify accidental or intentional data exposure and compliance violations that would otherwise go
unnoticed.
The DLP policy creates broadly identifies a spreadsheet with a list of US Social Security numbers. DLP is a subject of its
own, and this policy is only used for demonstration purposes. A true DLP policy review would need to be conducted to
minimize false positives and false negatives.
It is also important to note that SaaS DLP protection is only part of the Zscaler DLP solution and is used to scan data-
at-rest (like the GitLab files). This deployment guide doesn’t cover in-line data protection, exact data match, or indexed
document matching (document template fingerprinting), although they are integral pieces of a complete data protection
solution.
For next steps to test the DLP SaaS functionality, create a basic policy and apply it to the GitLab tenant. If you already have
DLP policies created, skip ahead to Configure a SaaS Malware Policy for GitLab.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
42©2024 Zscaler, Inc. All rights reserved.
Creating a DLP Policy
Create a custom dictionary (or use the available dictionaries) to identify the data the scan is going to look for.
Then create an engine that is the logical template for adding expressions and additional data. This is where you would
specify Social Security numbers and any other criteria for the policy. The engine provides the means to precisely add or
remove data to match violations and eliminate false positives.
A SaaS security DLP policy is created that allows you to specify the details about where, when, the action taken, and
whom to inform about violations.
Notice that you can create a custom DLP dictionary that contains your own paerns and phrases or use one of the
predefined dictionaries. This deployment guide focuses on predefined dictionaries.
Creating a DLP Engine
To create a DLP engine:
1. Select the DLP Engines tab.
2. Select Add DLP Engine.
Figure 45. Creating a DLP engine
ZSCALER AND GITLAB DEPLOYMENT GUIDE
43©2024 Zscaler, Inc. All rights reserved.
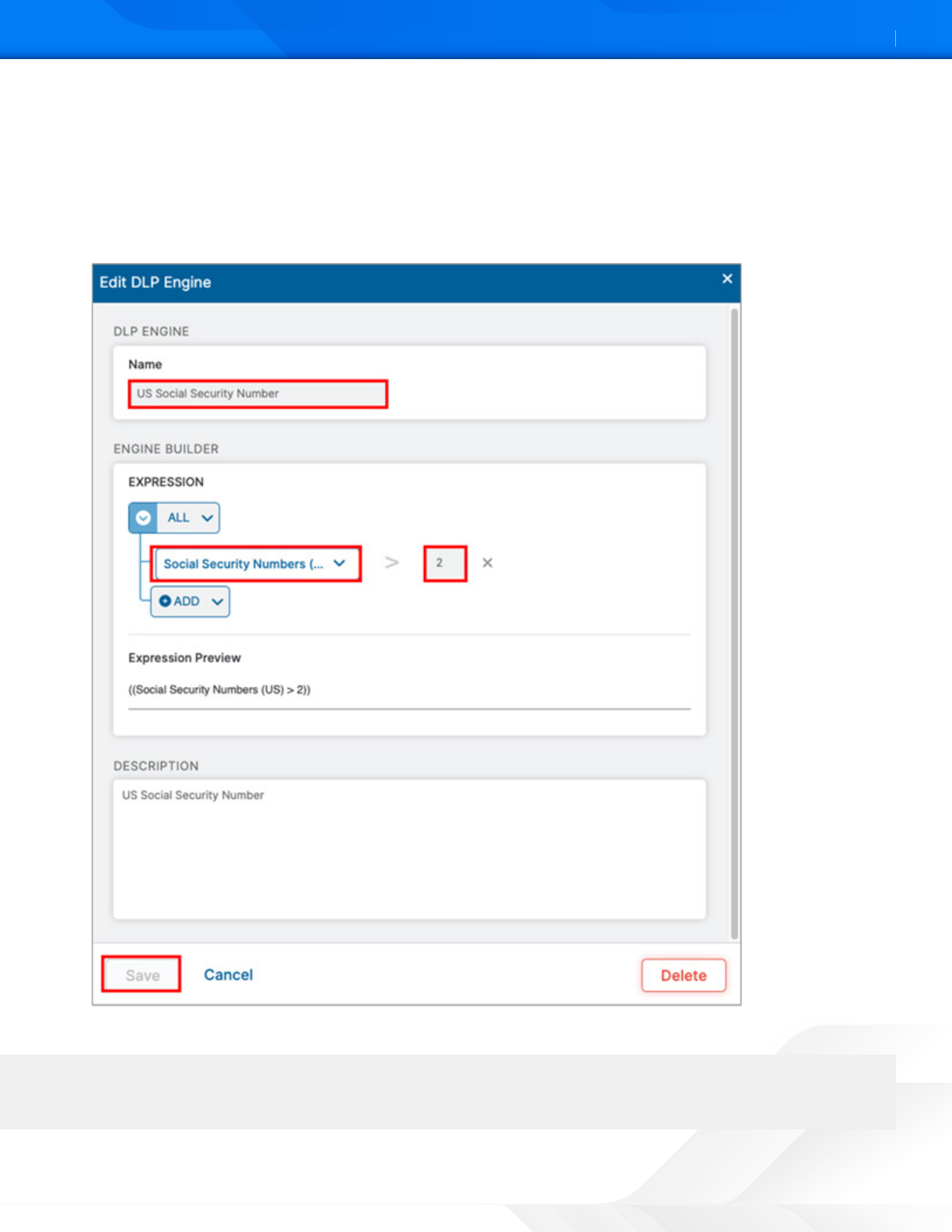
3. Give the DLP engine a Name.
4. In the Engine Builder under Expression, select the desired dictionary. In the following example, Social Security
Numbers (US) is selected.
5. Specify the Match Count, which is the minimum number of instances the data must occur in the file.
6. (Optional) Click Add to add the next dictionary and repeat the process.
7. Click Save, then Activate the configuration.
Figure 46. The DLP engine wizard
This policy triers when you see the third Social Security number. Again, this is a demonstration, and the criteria
is too general to be a production DLP rule.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
44©2024 Zscaler, Inc. All rights reserved.
Configure a SaaS DLP Policy for GitLab
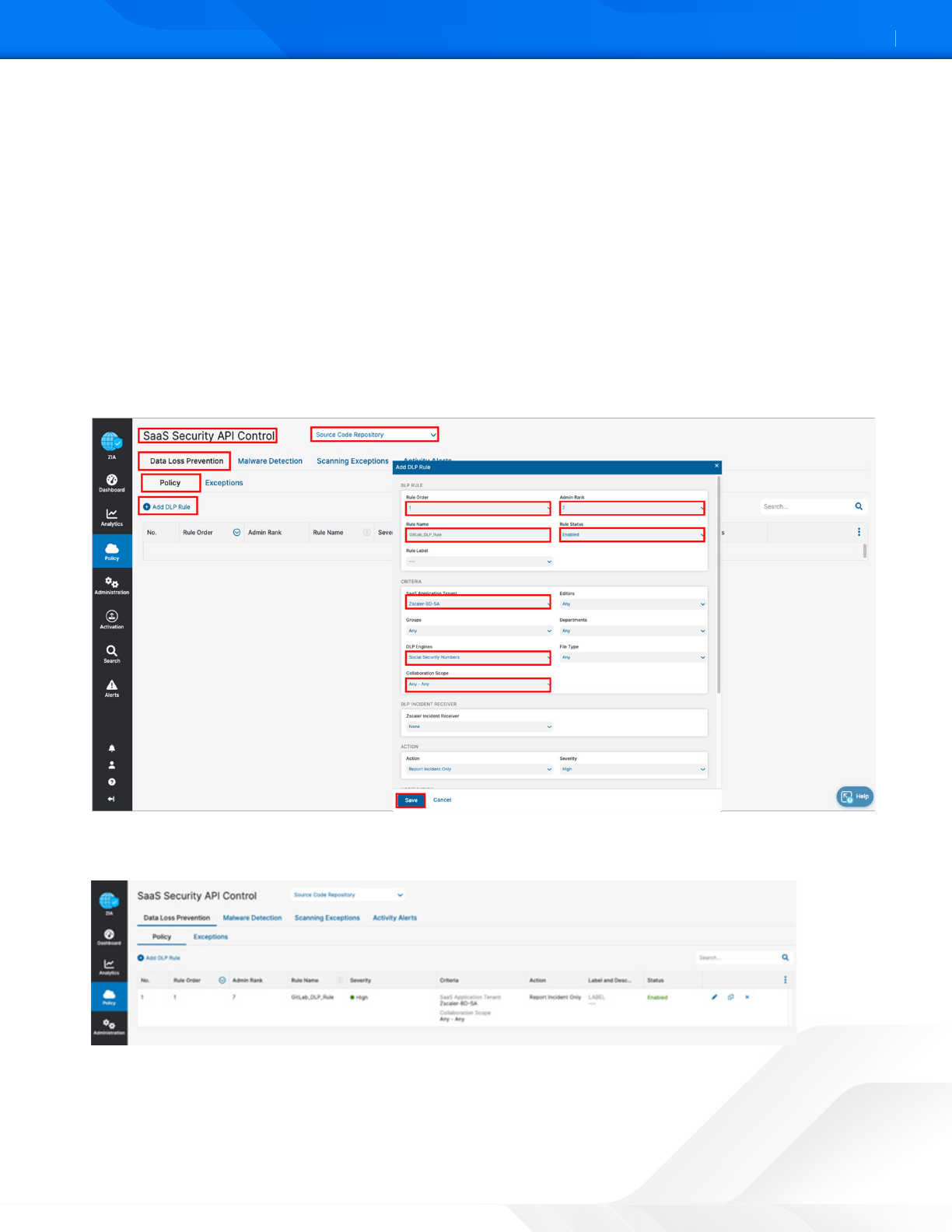
Apply the engine to a DLP policy used for the GitLab instance. Launch the Add DLP Rule wizard to start the process:
1. Go to Policy > SaaS Security API Control > Data Loss Prevention.
2. Select Source Code Repository.
3. Select Add DLP Rule.
4. Select the GitLab SaaS Tenant.
5. Select the DLP Engine created in GitLab SaaS Tenant Configuration Wizard
6. Select Any-Any for Collaboration Scope.
7. Select Report Incident Only as the Action.
8. Select High as Severity to allow for identification, searches, and tracking.
9. Click Save, and then Activate your configuration.
Figure 47. Launch the SaaS DLP Policy configuration wizard
The complete GitLab DLP rule is ready to be applied with a scanning schedule.
Figure 48. Launch the SaaS DLP Policy configuration wizard
ZSCALER AND GITLAB DEPLOYMENT GUIDE
45©2024 Zscaler, Inc. All rights reserved.
SaaS DLP Policy Details
The SaaS DLP policy specifies the details on whom and what data this policy applies. You specify the rule order if you
have multiple DLP policies, which are processed in an ascending manner. The first rule that matches is the applied
rule. Specify the DLP engine you defined, any file owners, groups or departments, and the file types to inspect. The
collaboration scope and the action are unique to the SaaS DLP. Select Any Collaboration, and an Action of Remove
Sharing.
The Collaboration Scope includes the collaboration scopes and permissions for SaaS tenant files that contain sensitive
data. Select Any to apply the rule to files with all collaboration levels, or select one or more of the following collaboration
scopes and specify the permissions for each scope:
• External Collaborators: Files that are shared with specific collaborators outside of your organization.
• External Link: Files with shareable links that allow anyone outside your organization to find the files and have access.
• Internal Collaborators: Files that are shared with specific collaborators or are discoverable within your organization.
• Internal Link: Files with shareable links that allow anyone within your organization to find the files and have access.
• Private: Files that are only accessible to the owner.
• The Action: The rule takes upon detecting content that matches the criteria. The number of actions available
depends on the selected SaaS Application Tenant. For GitLab, the action is Report Only. This means that any
violations are reported in the Zscaler SaaS Analytics and Alerts are sent to Auditors if defined.
• Report Incident Only: The rule reports the incident only and makes no changes to the file’s collaboration scope.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
46©2024 Zscaler, Inc. All rights reserved.
Configure a SaaS Malware Policy for GitLab
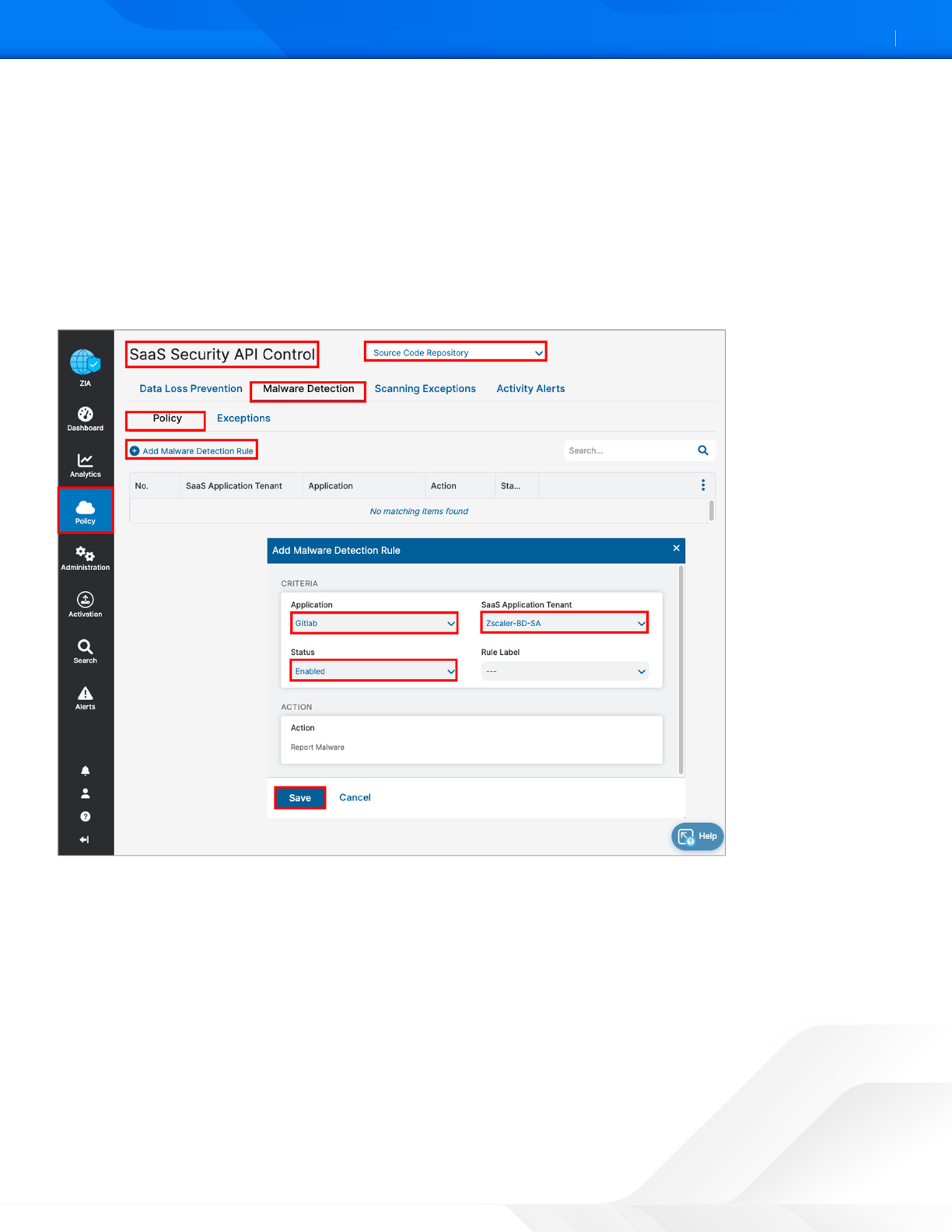
To launch the Malware Rule wizard:
1. Go to Policy > SaaS Security API Control > Malware Detection.
2. Select Source Code Repository.
3. Select Add Malware Detection Rule. The SaaS Malware Detection policy is an all-encompassing policy and all files in
the tenant are scanned unless removed from the scope specifying any exemptions by selecting the Exemption tab
under Malware Detection. To add a malware policy, specify the application, the SaaS tenant, and the status.
The action for GitLab is limited to reporting malware only.
Figure 49. Launch the Malware Policy configuration Wizard
ZSCALER AND GITLAB DEPLOYMENT GUIDE
47©2024 Zscaler, Inc. All rights reserved.
GitLab SaaS Malware Policy Wizard
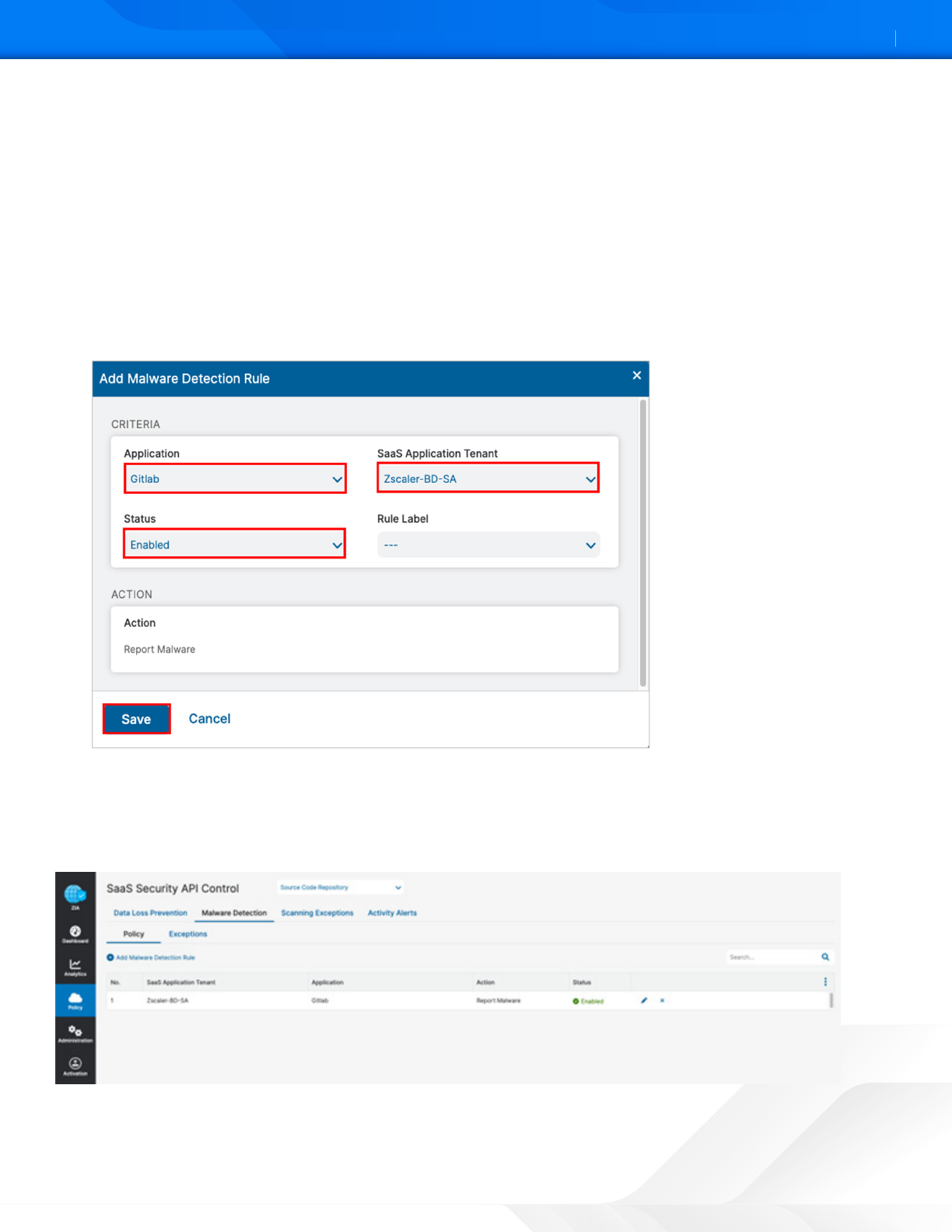
Configure the malware Rule wizard:
1. Go to Policy > SaaS Security API Control > Malware Detection.
2. Select Source Code Repository.
3. Select Add Malware Detection Rule.
4. Under Application, select GitLab as the application.
5. Select the GitLab SaaS tenant to apply the policy.
6. Select Enabled for Status.
7. Click Save.
Figure 50. The Malware Policy configuration wizard
GitLab SaaS Malware Policy
Apply the completed SaaS security malware policy for the GitLab SaaS tenant to the GitLab instance with a scanning
schedule. Activate your configuration.
Figure 51. The complete GitLab Malware Policy configuration
ZSCALER AND GITLAB DEPLOYMENT GUIDE
48©2024 Zscaler, Inc. All rights reserved.
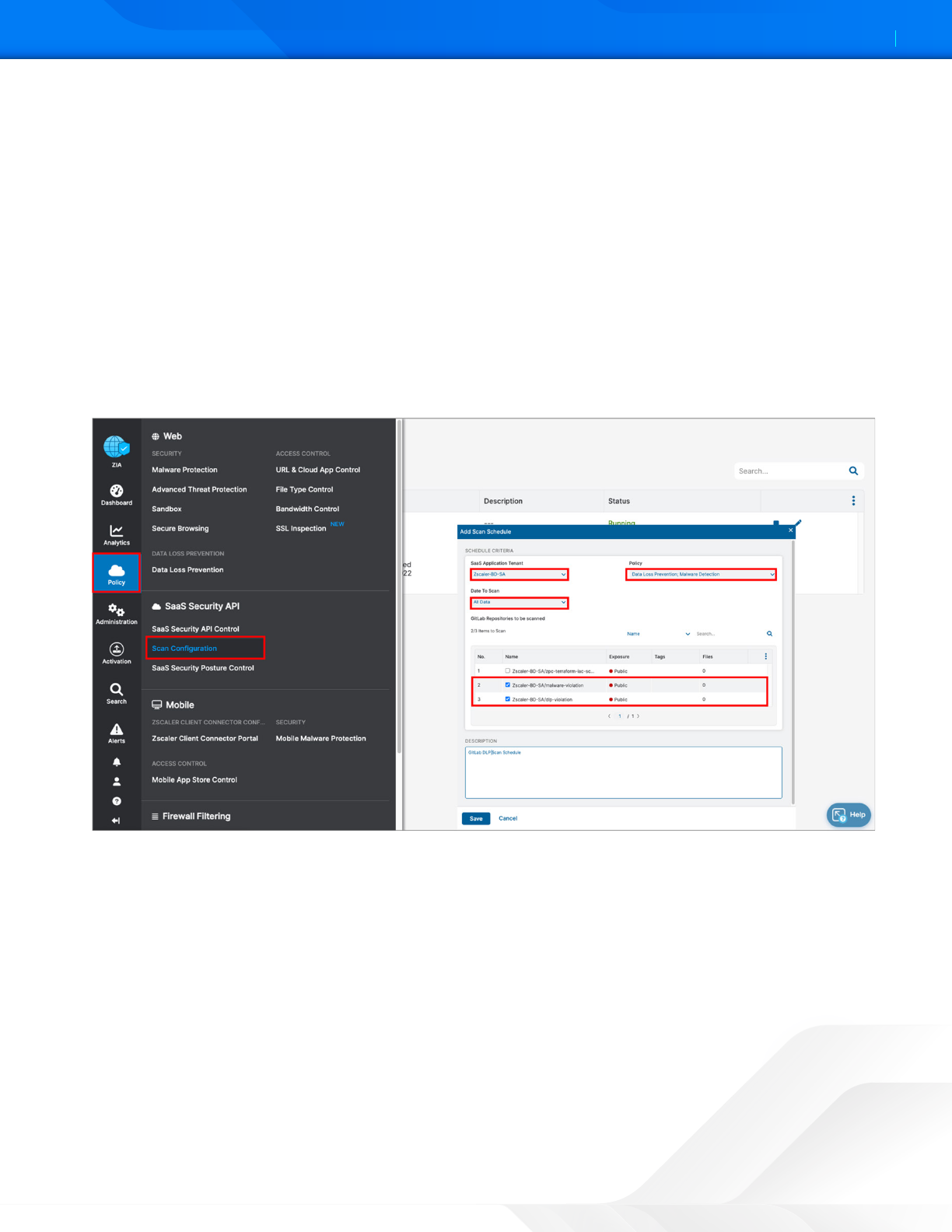
Configure a Scan Schedule Configuration for GitLab
The final configuration step is to create a Scan Configuration. Specify the tenant the Scan Configuration applies to, any
policies that are to be included in the scan, and what data to scan relative to a date. The options for Data to Scan are All
Data, Date Created or Modified Aer, or New Data Only. For this deployment guide, select All Data.
However, if this is a Proof of Value (POV) or a Trial, the only option available is New Data Only.
To add a Scan Schedule:
1. Go to Policy > SaaS Security API Control > Scan Configuration > Add Scan Schedule.
2. Select the GitLab SaaS tenant for the SaaS Application Tenant.
3. Select the data loss policy and the malware policy created in prior procedures.
4. Select All Data, or for a POV or Trial, select New Data Only.
5. Click Save, and then Activate the configuration.
Figure 52. Create and enable a scan for the GitLab SaaS tenant
ZSCALER AND GITLAB DEPLOYMENT GUIDE
49©2024 Zscaler, Inc. All rights reserved.
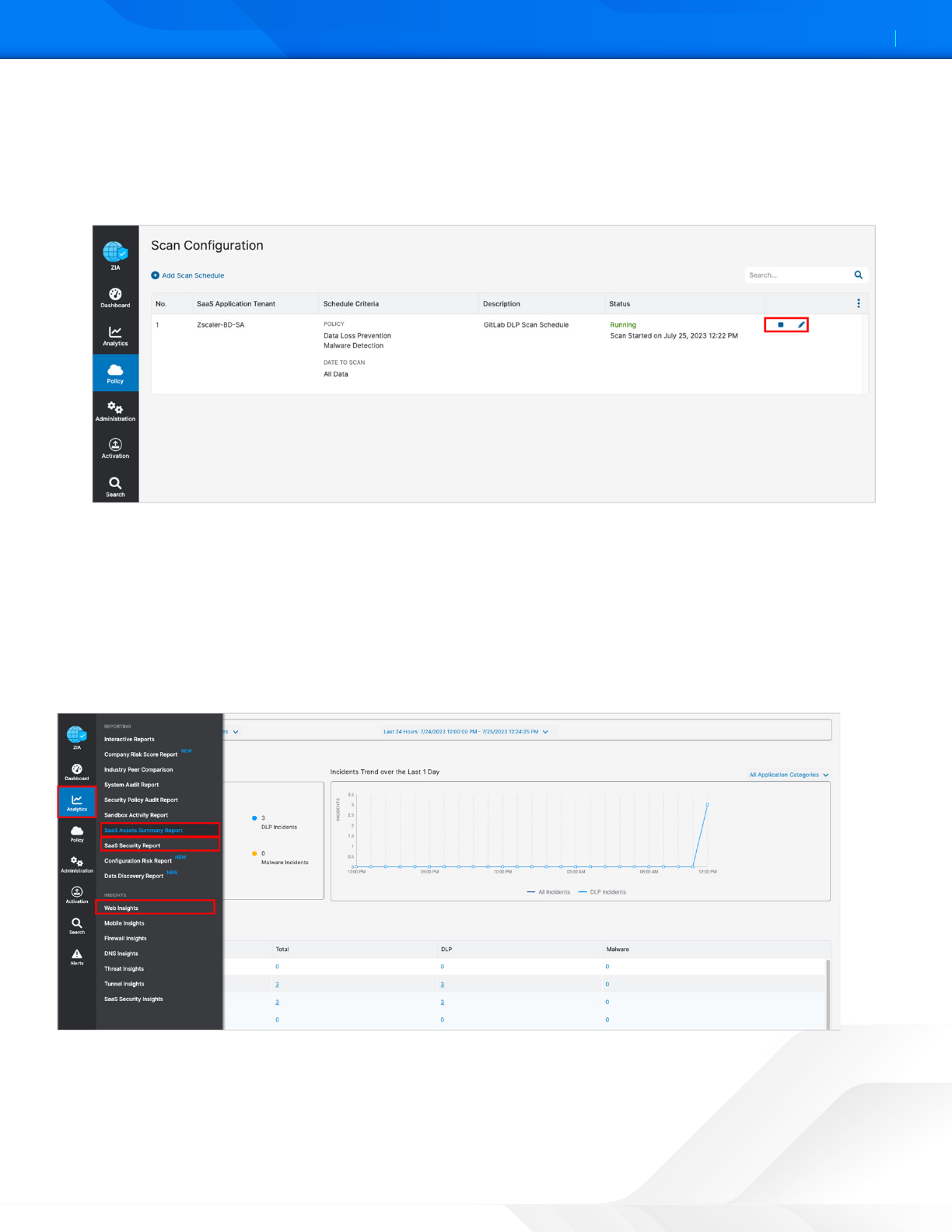
Start the Scan Schedule for GitLab
Aer the schedule has been configured and saved, start the scan for the DLP policy and malware policy to be applied.
1. Select the Start icon on the scan configuration to start SaaS Security API on the GitLab tenant.
2. Review the Status column and ensure it is Running with a start date and a latest scan date.
Figure 53. Starting the GitLab Scan Schedule
GitLab Reporting and Visibility
Zscaler analytics provide detailed reporting of all user activity down to each session created by the user when visiting a
destination. Zscaler extends that visibility to include reporting of activity, malware incidents, and DLP violations of data
at-rest associated with the user. Zscaler has reports and SaaS security insights, which provide visibility from a high-level
overview to management of the individual logs and violations.
To learn more, see SaaS Security Insights.
Figure 54. SaaS security visibility
ZSCALER AND GITLAB DEPLOYMENT GUIDE
50©2024 Zscaler, Inc. All rights reserved.
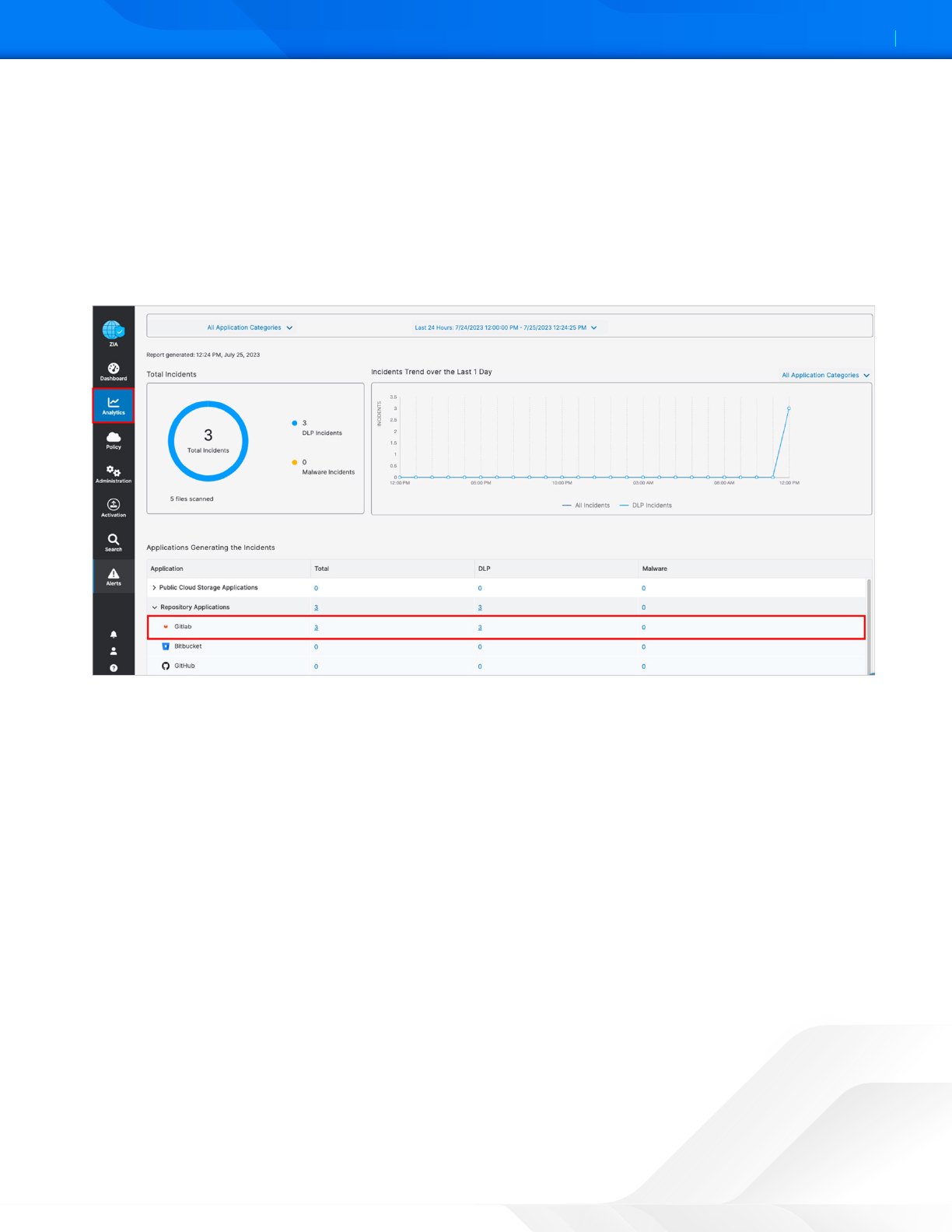
SaaS Assets Summary Report
A SaaS Assets Summary Report provides all activity and violations in a quick glance. The report identifies all SaaS tenant
information from a single screen. Although your GitLab activity over the creation of this deployment guide is shown, any
tenant configured is displayed on this summary screen. The data is hyperlinked, and you can easily pivot from a summary
to individual logs and activities provided by SaaS security insights.
1. Select the Total incidents number next to the GitLab icon to pivot to SaaS security insights.
2. On the Security Logs window, review the log data for each violation containing over 30 metadata points of
information.
Figure 55. GitLab SaaS Assets Summary reports
ZSCALER AND GITLAB DEPLOYMENT GUIDE
51©2024 Zscaler, Inc. All rights reserved.
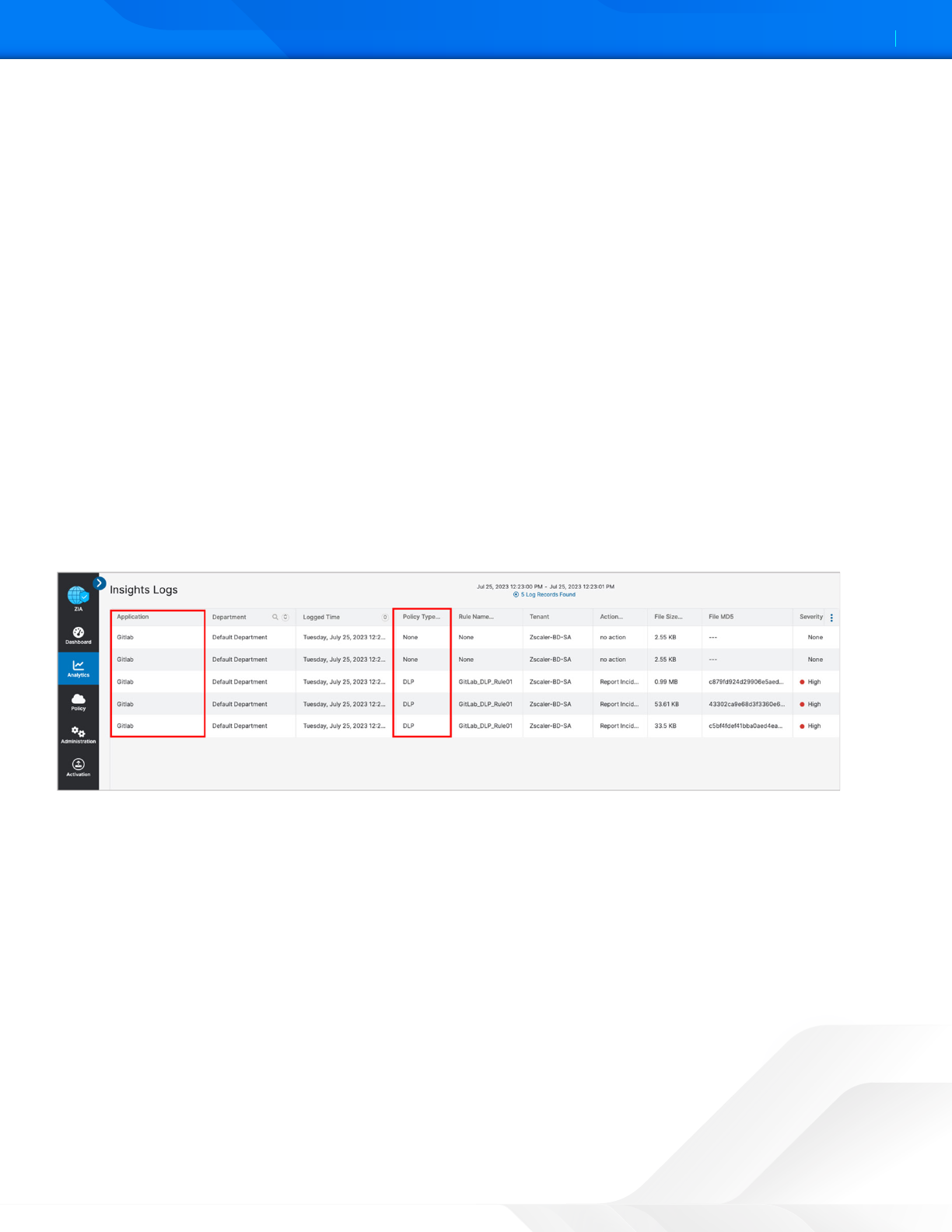
SaaS Security Insights
The SaaS Security Insights Log window allows you to select information fields for closer viewing when analyzing files
scanned through charts. These logs provide the detail of the policy that found the violation, the threat name, the owner,
and over 30 data points for identification and threat hunting.
The following are the SaaS Security data types.
• Application
• Application Category
• Department
• DLP Dictionary
• DLP Engine
• Incident Type
• Owner Name
• Severity
• Tenant
• Threat Category
• Threat Super Category
• User
Figure 56. GitLab SaaS security insight
ZSCALER AND GITLAB DEPLOYMENT GUIDE
52©2024 Zscaler, Inc. All rights reserved.
Cloud App Control
The following sections describe how to configure Cloud App Control for use with ServiceNow.
Cloud App Control Policy
Create the policy to allow specific users in a security group to access GitLab:
1. Sign into your organization’s ZIA Admin Portal with administrator credentials.
2. Select Policy.
3. Select URL & Cloud App Control.
4. Select the Cloud App Control Policy tab.
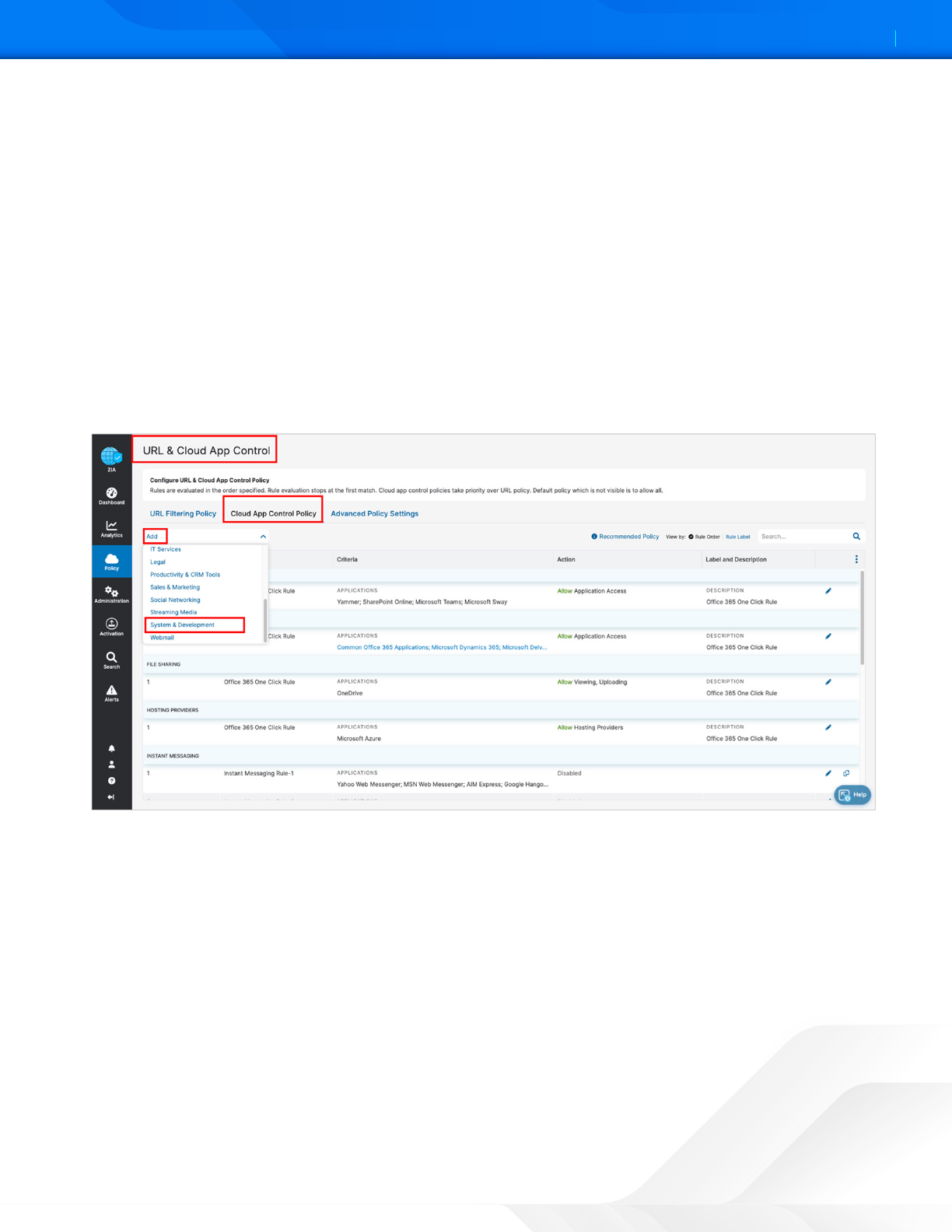
5. Select Add.
6. Select System & Development.
Figure 57. URL & Cloud App Control
Cloud App Control Policy Wizard
To create an Cloud App Control policy:
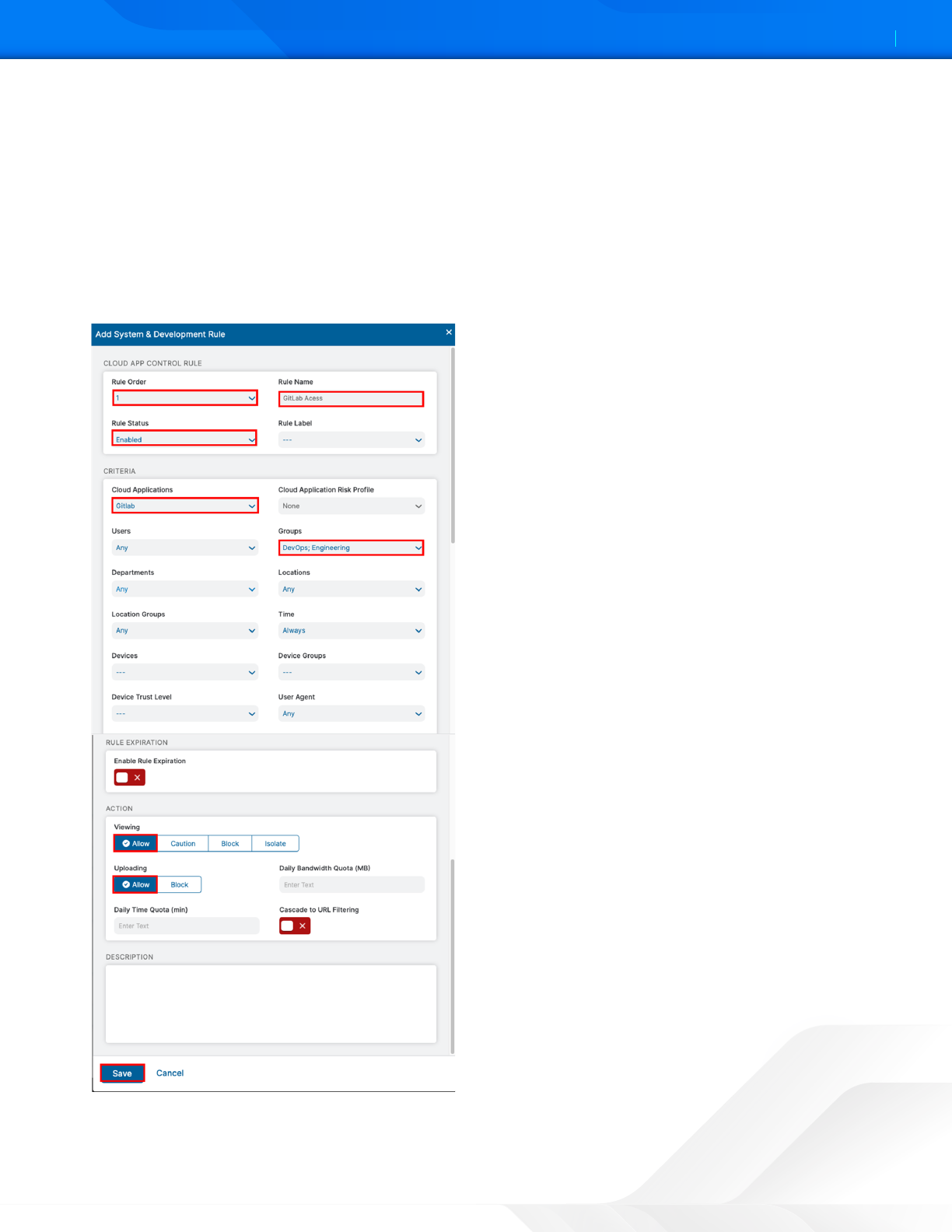
1. Set the Rule Order to 1.
2. Enter an intuitive Rule Name.
3. Select GitLab for the Cloud Application.
4. Select the security Group that contains the GitLab users.
ZSCALER AND GITLAB DEPLOYMENT GUIDE
53©2024 Zscaler, Inc. All rights reserved.
5. In Action, choose between the viewing and uploading actions.
a. Viewing:
• Allow. Allows users to view the content on the GitLab cloud applications.
• Caution. Warn users with a notification before they can proceed.
• Block. Block users.
• Isolate. Allow users to view the content of a GitLab repository remote browser Isolation.
b. Uploading. Allow or block users from uploading content to a GitLab repository.
6. Click Save and then Activate changes.
Figure 58. Create a Cloud App Control allow policy
ZSCALER AND GITLAB DEPLOYMENT GUIDE
54©2024 Zscaler, Inc. All rights reserved.
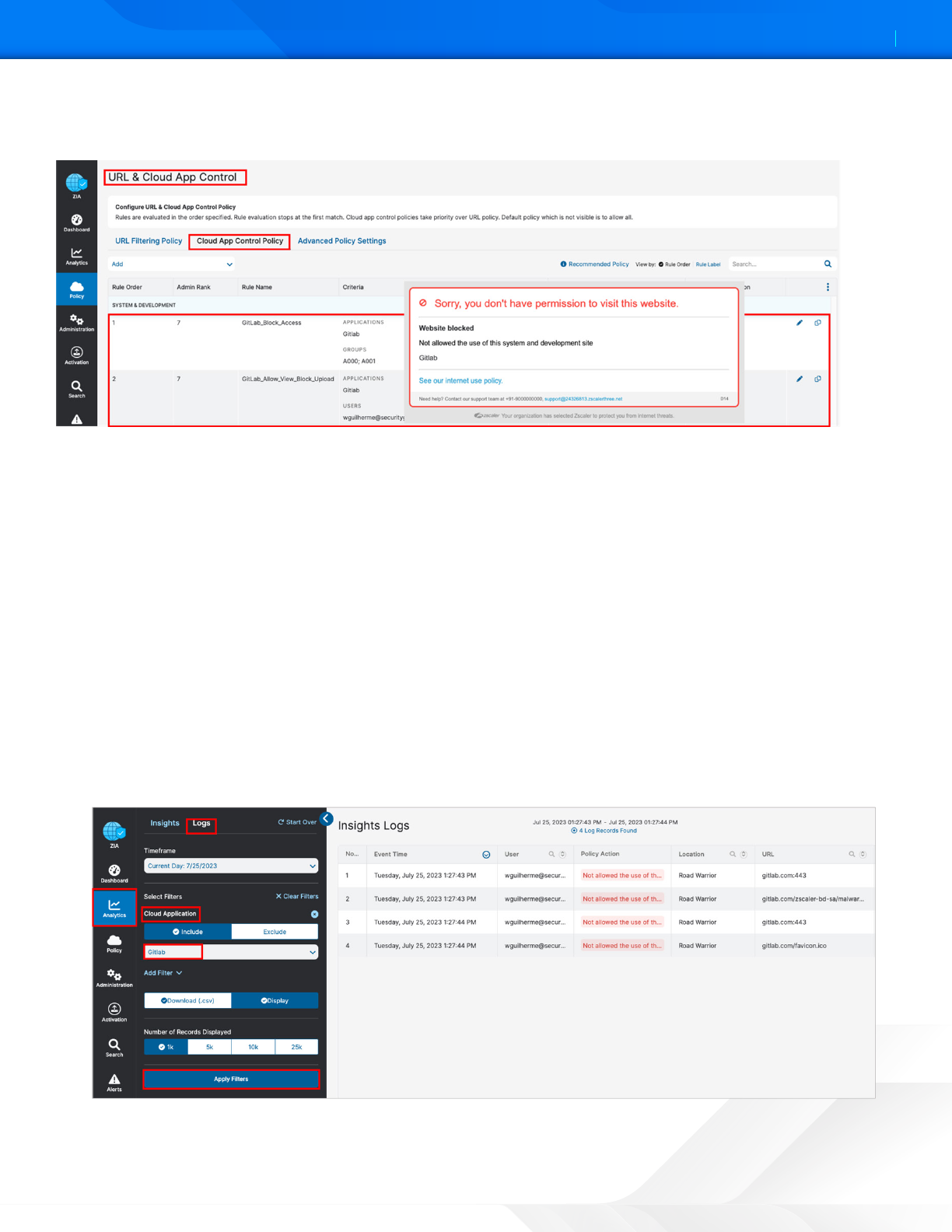
Users who try to access the GitLab application through Zscaler and do not have permission get the following Website
blocked window. Zscaler administrators receive alerts and logs about the event.
Figure 59. Create a Cloud App Control deny policy
Cloud App Control Logs
Zscaler analytics provide visibility to see any activity for GitLab access, or to get usage reports. To view the GitLab logs for a
certain time frame:
1. Sign into your organization’s ZIA Admin Portal with administrator credentials.
2. Select Analytics.
3. Select Web Insights.
4. Select the Logs tab.
5. Select the desired time frame, or custom time frame.
6. Select Add Filter.
7. Select Cloud Application.
8. Select GitLab.
9. Click Apply Filters.
Figure 60. Create a Cloud App Control log
ZSCALER AND GITLAB DEPLOYMENT GUIDE
55©2024 Zscaler, Inc. All rights reserved.
Appendix A: Requesting Zscaler Support
If you need Zscaler Support for provisioning certain services or to help troubleshoot configuration and service issues, it is
available 24/7/365. To contact Zscaler Support:
1. Go to the ZPC help and select Support from the le-side navigation.
2. Select Submit Ticket.
Figure 61. ZPC Help
3. In the Submit Ticket window, select Submit Ticket for Posture Control (ZPC).
Figure 62. ZPC Support
ZSCALER AND GITLAB DEPLOYMENT GUIDE
56©2024 Zscaler, Inc. All rights reserved.
4. In the ZPC - Submit Ticket window, fill in the required fields.
Figure 63. Submit ZPC ticket
5. Select the reCAPCHA checkbox, and click Submit. A Zscaler Support representative contacts you via the submied
contact information within 24 hours.
