

2

3
1H 2022 Global Threat Landscape Report
4
1H 2022 Global Threat Landscape Report
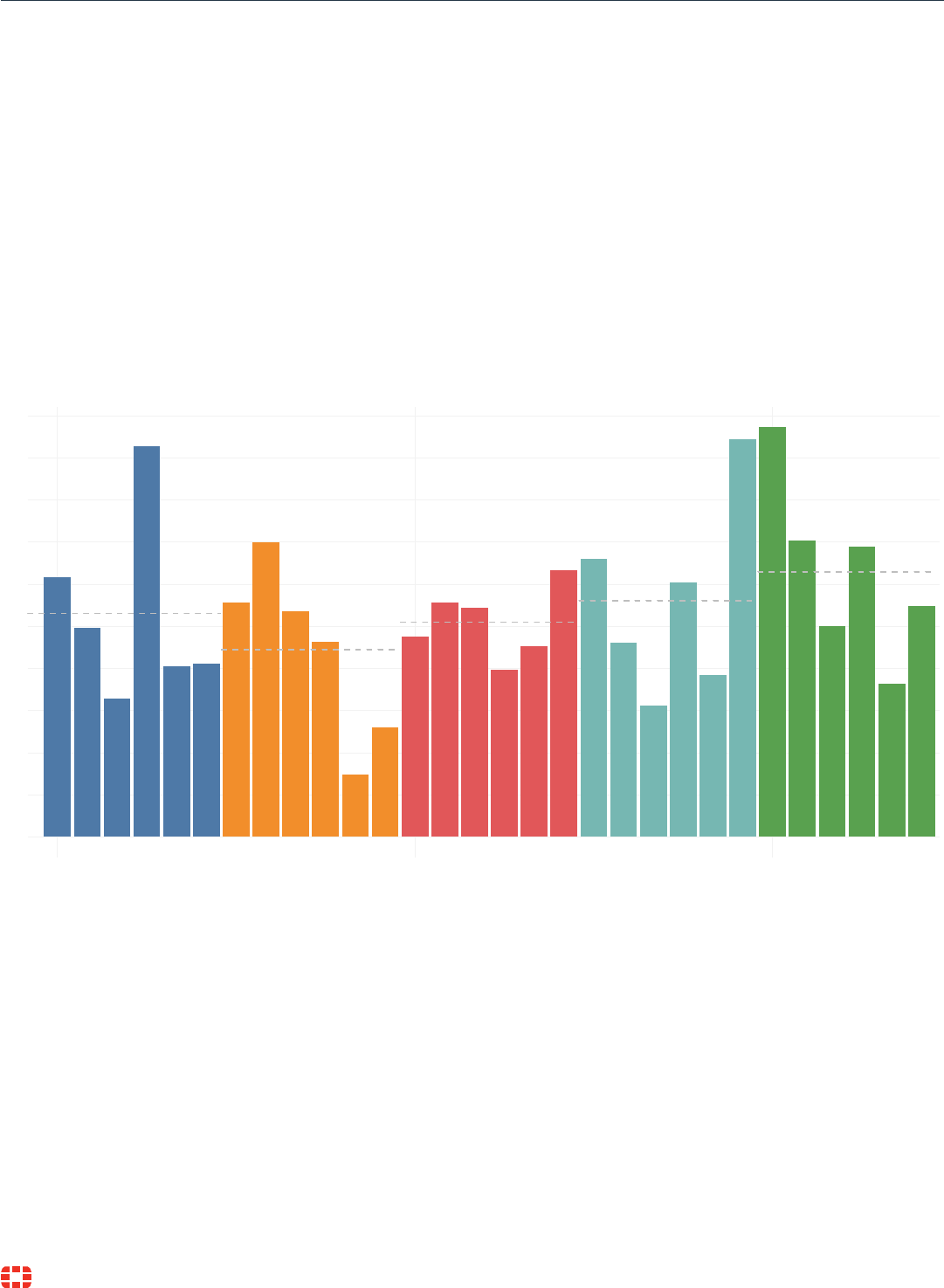
0
50
100
150
200
250
Jan 20 Jan 21 Jan 22
5
1H 2022 Global Threat Landscape Report
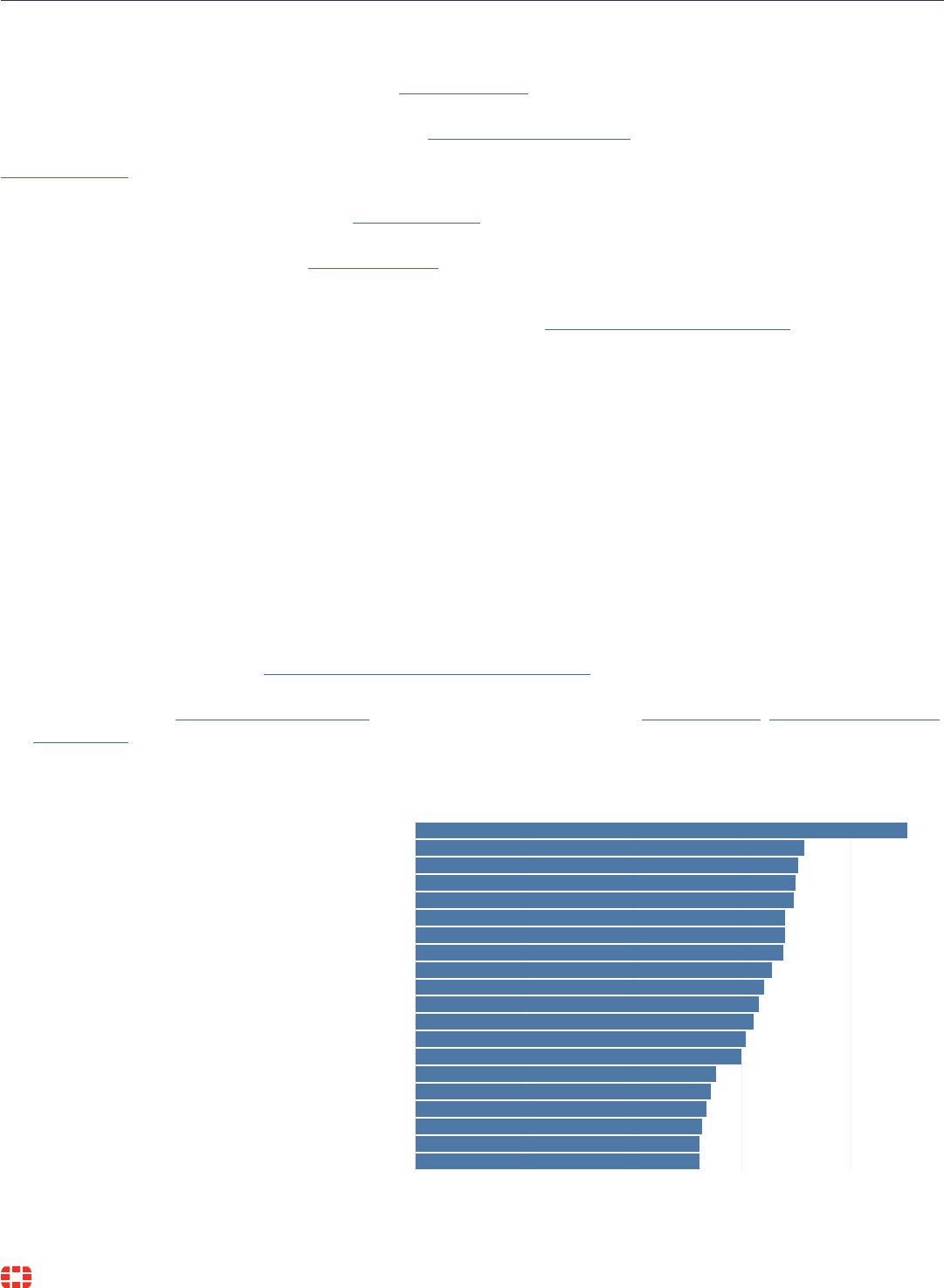
CVE(s): 2012-2311, 2012-1823
CVE(s): 2014-0160
CVE(s): 2019-10891, 2015-2051
CVE(s): 2017-5638
CVE(s): 2017-6639
CVE(s): 2017-9841
CVE(s): 2018-1273
CVE(s): 2018-10561, 2018-10562
CVE(s): 2019-9082, 2018-20062
CVE(s): 2019-11479, 2019-11478, 2019-11477
CVE(s): 2017-11357, 2019-18935, 2017-11317
CVE(s): 2021-31166
CVE(s): 2021-42013, 2021-41773
CVE(s): 2021-4104, 2021-45046, 2021-44228
26.3%
29.9%
27.2%
35.7%
27.6%
34.8%
26.7%
30.4%
34.9%
35.1%
33.9%
33.9%
31.1%
32.0%
31.5%
26.1%
26.1%
33.8%
32.7%
45.2%
Axis.SSI.camnbr.RCE
Spring.Boot.Actuator.Unauthorized.Access
HTTP.URI.SQL.Injection
Java.Debug.Wire.Protocol.Insecure.Configuration
OpenSSL.Heartbleed.Attack
JAWS.DVR.CCTV.Shell.Unauthenticated.Command.Execution
PHP.CGI.Argument.Injection
NETGEAR.DGN1000.CGI.Unauthenticated.RCE
Linux.Kernel.TCP.SACK.Panic.DoS
Telerik.Web.UI.RadAsyncUpload.Handling.Arbitrary.File.Upload
Shenzhen.TVT.DVR.RCE
Apache.HTTP.Server.cgi-bin.Path.Traversal
MS.Windows.HTTP.sys.UlpParseAcceptEncoding.Use.After.Free
ThinkPHP.Controller.Parameter.RCE
Dasan.GPON.RCE
Apache.Struts.2.Jakarta.Multipart.Parser.Code.Execution
PHPUnit.Eval-stdin.PHP.RCE
HTTP.URI.Java.Code.Injection
D-Link.Devices.HNAP.SOAPAction-Header.Command.Execution
Apache.Log4j.Error.Log.RCE
0% 10% 20% 30% 40%
6
1H 2022 Global Threat Landscape Report
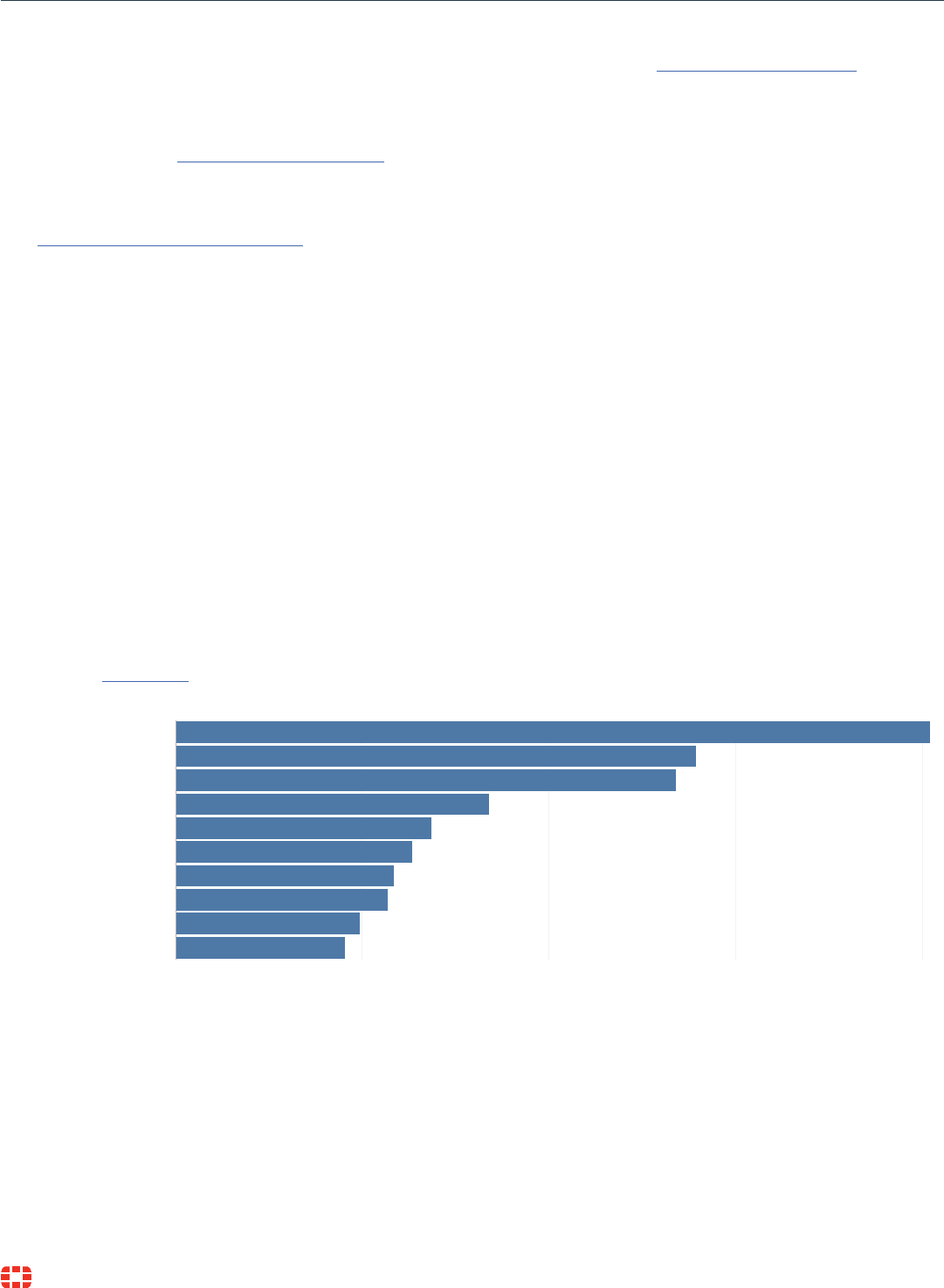
CVEs: 1,885
CVEs: 1,274
CVEs: 1,571
CVEs: 2,293
CVEs: 515
CVEs: 767
CVEs: 5,340
CVEs: 971
CVEs: 964
CVEs: 964
4b
2.8b
2.7b
1.7b
1.4b
1.3b
1.2b
1.1b
987m
907m
opensuse (70.5%)
redhat (64.6%)
fedoraproject (91.5%)
microsoft (87.0%)
canonical (65.8%)
netapp (71.4%)
adobe (33.4%)
debian (81.6%)
mozilla (48.2%)
oracle (84.0%)
0 1b 2b 3b 4b

7
1H 2022 Global Threat Landscape Report
2012-5081
oracle, sun
2013-0640
adobe
2013-0641
adobe
2013-1493
oracle, sun
2014-0457
many
2014-3566
many
2015-0204
openssl
2015-2590
oracle
2015-4000
many
2015-6099
microsoft
2016-3213
microsoft
2016-3236
microsoft
2016-3427
oracle
2017-11263
adobe
2017-16391
adobe
2021-22893
pulsesecure
2022-21907
microsoft
2022-26809
microsoft
2022-26925
microsoft
2022-26937
microsoft
CVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpointsCVE on more endpoints
CVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacksCVE among more attacks
80th
85th
90th
95th
100th
80th 85th 90th 95th 100th
IPS Volume (percentile)
Endpoint Volume (percentile)
Let’s take a moment here to
understand what we’re explicitly
talking about when it comes to
endpoints and vulnerabilities.
Not every exploit is related to
a vulnerability (meaning no
CVE was assigned), and not
every vulnerability has a public
PoC exploit. Vulnerability IDs
are how we group volume
measurements. However, it’s
not quite as simple as that. In
some cases, one vulnerability
ID can map to multiple CVEs, as
is the case with a vulnerability
ID created as an umbrella
term that can catch different
implementations of that
vulnerability across multiple
solutions. That being said, if
you see something on the chart
below that ranks high on IPS,
there is a pretty good chance
that it could be related to
something on the top of IPS. So
let’s now dive a little deeper into
why this matters.

8
1H 2022 Global Threat Landscape Report
3S-Smart
7-Technologies
ABB
Advantech
Allen
AzeoTech
Beckhoff
BlackIce
BMC
Broadwin
Cambium
Citect
CoDeSys
Cogent
Dahua
DATAC
Delta
Digium
Eaton
Ecava
Galil
GE
Geutebruck
Hikvision
Honeywell
Iconics
InduSoft
Intellicom
iRZ
KingScada
Measuresoft
Meinberg
Meteocontrol
Microsys
Mitsubishi
Moxa
mySCADA
Nordex
OMRON
OPC
Optima
Panasonic
PcVue
Phoenix
Progea
QNX
RealFlex
Rockwell
RSLogix
SafeNet
Samsung
Schneider
SearchBlox
Sielco
Siemens
Sierra
Sinapsi
Sunway
TeeChart
Triangle
Trihedral
Unitronics
VIPA
WECON
WellinTech
WindRiver
Wonderware
xArrow
Yokogawa
100
100k
100m
1 in
100k
1 in
10k
1 in
1k
1 in
100
1 in
10
Organizational Prevalence
Total Volume

9
1H 2022 Global Threat Landscape Report
XML
NSIS
LNK
RTF
PDF
XF
MSExcel
VBA
MSOffice
MSIL
W32
JS
HTML
XML
LNK
NSIS
MSOffice
VBA
PDF
RTF
XF
MSExcel
MSIL
W32
JS
HTML
10%
20%
30%
January February March April May June

10
1H 2022 Global Threat Landscape Report
24.3%
34.6%
6.9%
23.1%
21.2%
9.0%
6.3%
7.3%
10.1%
8.9%
5.3%
6.5%
5.7%
4.5%
6.0%
5.6%
5.3%
8.8%
12.8%
3.7%
14.5%
16.0%
5.5%
18.7%
7.1%
6.6%
6.2%
5.1%
6.4%
4.9%
0.1%
9.8%
2.0%
0.2%
0.5%
2.7%
0.1%
1.6%
5.8%
0.3%
0.2%
0.2%
2.1%
4.7%
3.4%
2.1%
3.0%
3.6%
0.4%
6.0%
2.1%
2.3%
1.5%
0.1%
W32 XF XML
MSExcel MSIL MSOffice
HTML JS LNK
LNK/Agent.CQ!tr
LNK/PSRunner.VPHQ!tr
LNK/Agent.AOZ!tr
LNK/Agent.AMY!tr.dldr
LNK/Agent.AJP!tr
LNK/Phishing.B166!tr
MSOffice/CVE_2017_0199.A!exploit
MSOffice/CVE_2018_0798!tr
MSOffice/Agent.GV!tr
MSOffice/CVE_2017_11882.DMP!exploit
MSOffice/CVE_2017_0199.536C!tr
MSOffice/CVE_2017_11882.C!exploit
XML/Agent.AWB!tr
XML/GenericKD.47434890!tr.dldr
XML/Dloader.04B1!tr
XML/Emotet.CC!tr.dldr
XML/Agent.DVV!tr
XML/Dloader.802!tr
JS/Agent.EY!tr
JS/Agent.PIV!tr
JS/ScrInject.B!tr
JS/Cryxos.5478!tr
JS/Agent.NDSW!tr
JS/SEARCHVITY.F8EB!tr
MSIL/GenKryptik.FVTU!tr
MSIL/Kryptik.AEPF!tr
MSIL/Kryptik.AEMX!tr
MSIL/GenKryptik.FVES!tr
MSIL/Kryptik.AECU!tr
MSIL/GenKryptik.FOWD!tr
XF/CoinMiner.S!tr
XF/Agent.DSF!tr.dldr
XF/Agent.NN!tr.dldr
XF/Agent.LG!tr.dldr
XF/Agent.EILU!tr.dldr
XF/CoinMiner.Z!tr
HTML/FakeAlert.TS!tr
HTML/Agent.CKH!tr
HTML/Redirect.FED5!tr
HTML/Redirector.PFB!tr
HTML/Refresh.250C!tr
HTML/Generic.31221958!tr
MSExcel/Agent.DVP!tr
MSExcel/CVE_2017_11882!exploit
MSExcel/Agent.DVP!tr.dldr
MSExcel/Agent.DKF!tr.dldr
MSExcel/CVE_2018_0798.F!exploit
MSExcel/CVE_2017_11882.F!exploit
W32/Injector.ERFW!tr
W32/Injector.EREA!tr
W32/GenKryptik.DPIE!tr
W32/PossibleThreat
W32/Malicious_Behavior.SBX
W32/Injector.EQPQ!tr
15.3%
4.8%
40.7%
11.3%
5.6%
16.2%
50.5%
7.4%
5.1%
7.5%
ELF/BalkanDoor
ELF/Tsunami
ELF/Dofloo
ELF/Setag
ELF/Xorddos
ELF/DDoS
ELF/Agent
ELF/Gafgyt
ELF/BitCoinMiner
ELF/Mirai

11
1H 2022 Global Threat Landscape Report
10.4%
5.0%
1.8%
59.2%
12.5%
0.9%
0.8%
9.4%
4.2%
6.6%
19.2%
4.2%
6.1%
6.6%
6.6%
26.1%
Tactic Technique
0% 20% 40% 60% 0% 20%
40% 60%
OS Credential Dumping
Input Capture
Command and Scripting Interpreter
Mshta
Scripting
Windows Management Instrumentation
Process Injection
System Binary Proxy Execution
Collection
Discovery
Privilege Escalation
Execution
Impact
Initial Access
Credential Access
Defense Evasion
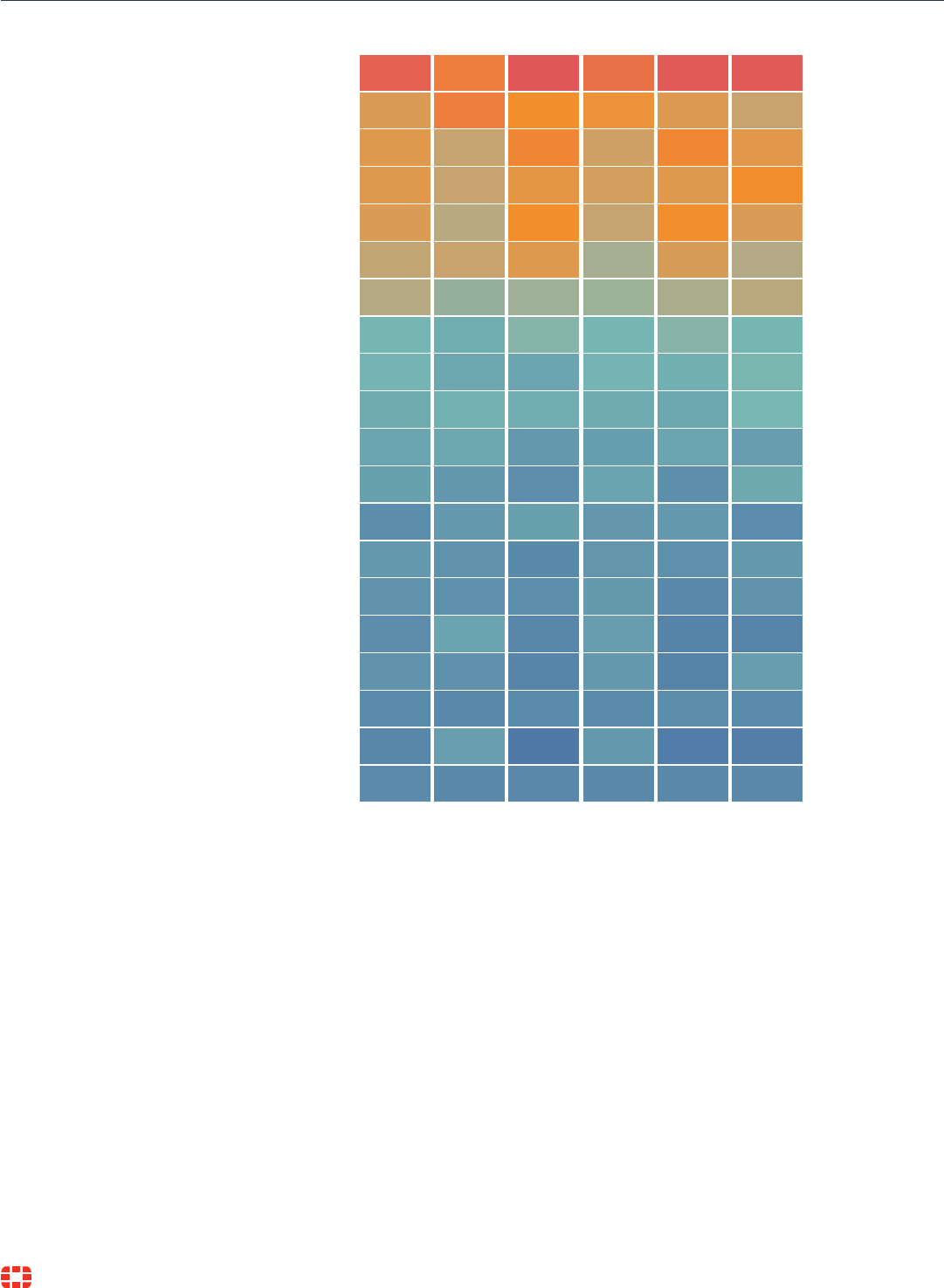
12
1H 2022 Global Threat Landscape Report
0.8% 1.0% 1.1%
1.5%
1.5%
1.5%
1.5%1.7%
1.7%
1.7%
1.7%
1.7% 1.8% 1.8%1.8%1.8%
1.8%
1.8%
1.9% 1.9% 1.9%1.9%
2.0%2.0%
2.0%
2.0%
2.1%
2.1% 2.2%
2.3%
2.3%
2.3%
2.3%
2.4%
2.5%
2.5%
2.6%
2.6%
2.7%
2.7%
2.7%
2.7%
2.7%
2.7%
2.8%
2.8%
2.8%
3.0%
3.0%
3.0%3.0%
3.1%
3.2%
3.2% 3.4%
3.4%
3.5%3.5%
3.5%
3.5%
3.6%
3.6%
3.8%
3.8%3.9% 3.9%
4.0%
4.1%
4.3%
4.4% 4.4%
4.4%4.5% 4.5%
4.6%
4.6%
4.9% 4.9%
5.2% 5.3%5.4%
5.6%
5.6%
5.9%
6.0%
6.0%
6.1%
6.4%
6.5%
6.5%
6.5%
6.6%
6.6%
6.8%
7.0%
7.2%
7.3%
7.3%
7.3%
7.4%
7.5% 7.5%
7.5%
7.5% 7.5%
7.7%
8.0%
8.3%
8.3%
8.3%
8.4%
8.8%8.9%
9.5%
9.5%
10.4%11.5% 11.9% 11.9%12.1%
File Deletion
Component Object Model and
Distributed COM
Hidden Files and Directories
Scheduled Task or Job
Obfuscated Files or
Information
Scripting
Registry Run Keys / Startup
Folder
Standard Application Layer
Protocol
Masquerading
User Execution
Process Discovery
Replication Through Removable
Media
Native API
Timestomp
Hidden Window
Process Hollowing
Disabling Security Tools
Hooking
Modify Registry
Process Injection
Europe,
Middle
East
Asia
Pacific
North
America
Africa Latin
America
Oceania
13
1H 2022 Global Threat Landscape Report
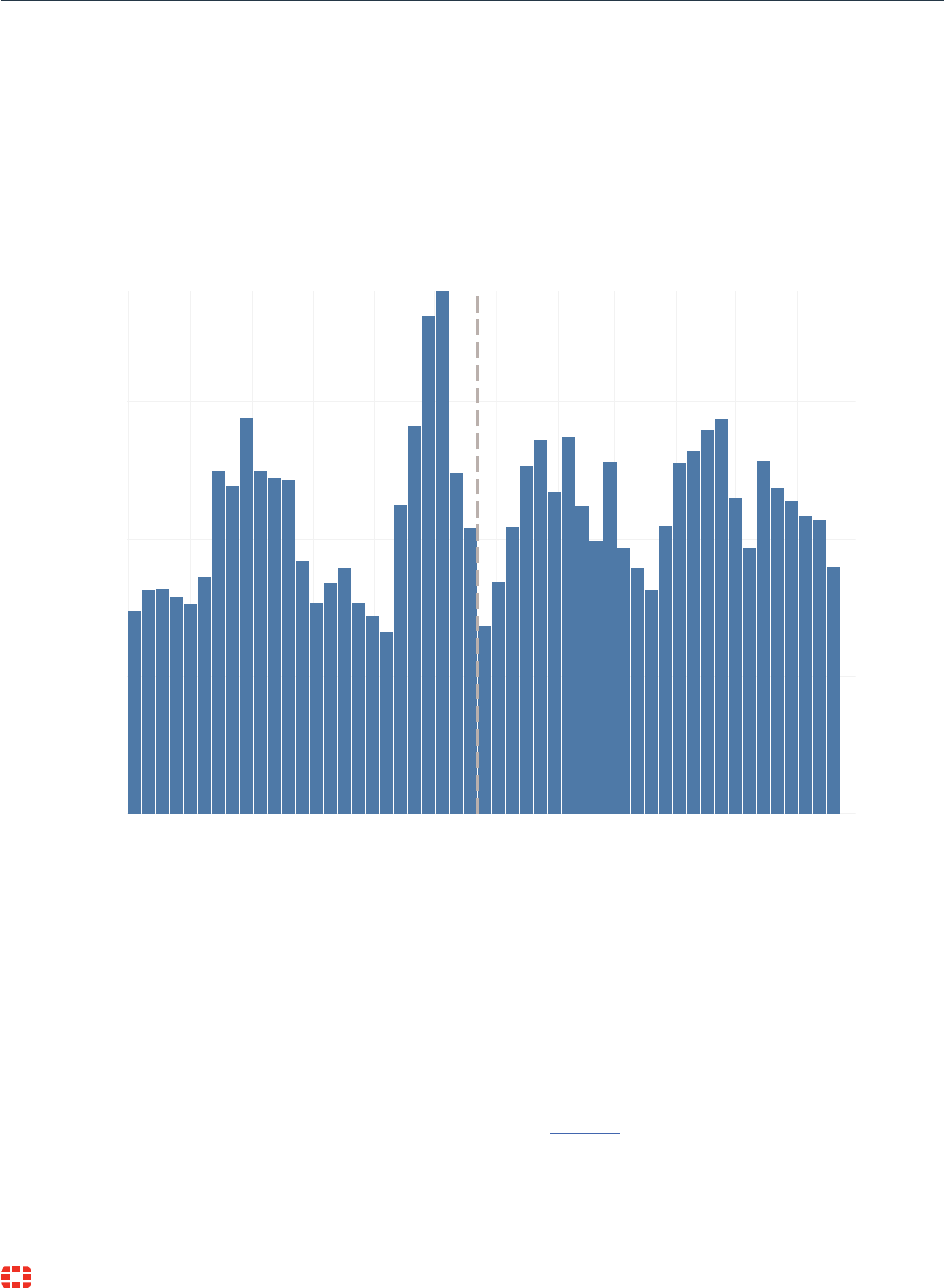
5,400 ransomware variants observed
during the second half of 2021.
10,666 ransomware variants observed
during the first half of 2022.
0k
50k
100k
150k
Jul Aug Sep Oct Nov Dec Jan Feb Mar Apr May Jun

14
1H 2022 Global Threat Landscape Report
15
1H 2022 Global Threat Landscape Report
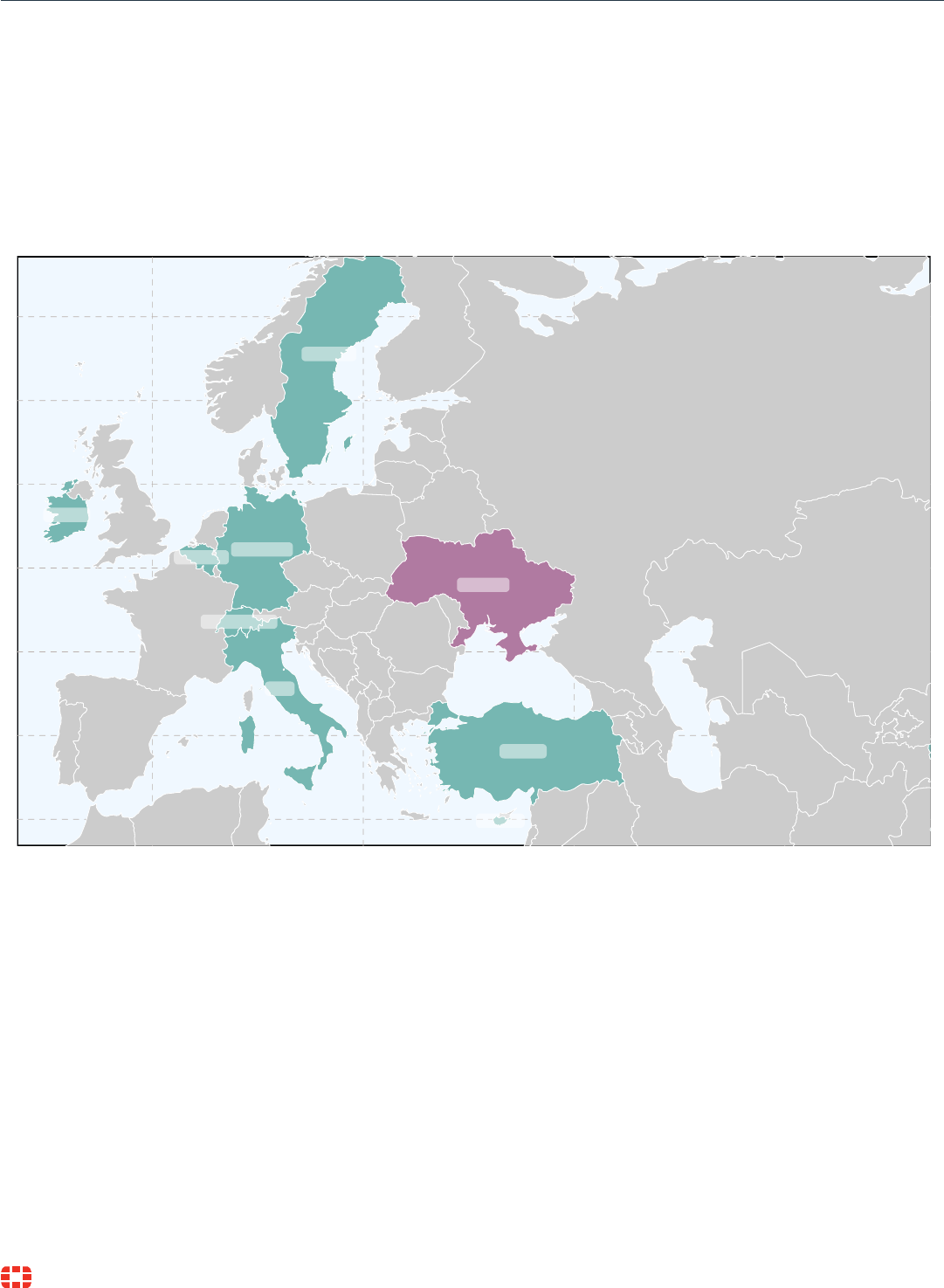
Belgium
Switzerland
Cyprus
Germany
Ireland
Italy
Sweden
Turkey
Ukraine

16
1H 2022 Global Threat Landscape Report
CaddyWiper
HermeticWiper
IsaacWiper
WhisperKill
WhisperGate
CaddyWiper
WhisperKill
IsaacWiper
WhisperGate
HermeticWiper
0.00%
0.01%
0.02%
0.03%
0.04%
Jan Feb Mar Apr May Jun

1H 2022 Global Threat Landscape Report
Copyright © 2022 Fortinet, Inc. All rights reserved. Fortinet
®
, FortiGate
®
, FortiCare
®
and FortiGuard
®
, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product
or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other
conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser
that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any
such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise
revise this publication without notice, and the most current version of the publication shall be applicable.
www.fortinet.com
1471550-0-0-EN
