

DIGITAL DECAY?
Tracing Change Over Time Among
English-Language Islamic State
Sympathizers on Twitter
BY
Audrey Alexander
October 2017
All rights reserved. Printed in the United States of America. No part of this publication
may be reproduced or transmitted in any form or by any means, electronic or mechanical,
including photocopy, recording, or any information storage and retrieval system, without
permission in writing from the publisher.
© 2017 by Program on Extremism
Program on Extremism
2000 Pennsylvania Avenue NW, Suite 2210
Washington, DC 20006
www.extremism.gwu.edu

Digital Decay? • iii
CONTENTS
Author’s Notes and About the Author · v
Executive Summary · vii
Introduction · 1
Background · 5
Method and Design · 11
Analysis of English-Language IS-Sympathizers on Twitter · 15
Conclusion · 45
List of Figures
1. IS Infographic · 1
2. Kibana’s Dashboard · 12
3. Breakdown of Time Segments · 12
4. Twee t Cou nt Per Week · 15
5. Twee t Frequenc y a nd Unique Sc reen Na mes By We ek · 17
6. Duration of Account Activity · 17
7. Follower Count by Chronological Segment · 18
8. Tracing Username Mentions by English-Language IS Sympathizers · 20
9. Example Tweets · 23
10. Twit ter Accounts · 24
11. Example Tweet · 24
12. Tracking Military Engagements Over Time · 25
13. Two-Week Snapshot of Mosu l a nd K irk uk (Oc tober 14 to 28, 2016) · 26
14. Top 3 Hashtags Per Week Highlighting Prevalence of Key Batt les · 28
15. Tracing Attacks Over Time · 30
16. Example Tweets · 31
17. Example Tweet · 31
18. Example Tweet · 33
19. Top 10 Hashtags on July 15 and July 16, 2016 · 34
20. Example Tweet · 35
21. Twe et Referencing A nt i-US St ate L eaders · 35
22. Example Tweet · 36
23. Example Tweet · 37
24. Top Hashtag Per Week · 38

Digital Decay? • v
AUTHOR’S NOTES
First and foremost, the author would like to thank Daniel Kerchner, and the team at Scholarly Technology Group (STG) of
the George Washington University Libraries, for their immeasurable contributions to this project since December 2015.
This report was made possible by the Program’s team of Research Assistants, particularly Alex Theodosiou; Sarah
Metz, Eleanor Anderson, Samantha Weirman, Mattisen Stonhouse, Adib Milani, Tanner Wrape, Mario Ayoub, Scott
Backman, Jenna Hopkins, and Elizabeth Yates also contributed to this report.
The author would also like to thank Dr. Ali Fisher for his constructive feedback, and Larisa Baste for formatting
this report.
ABOUT THE AUTHOR
Audrey Alexander specializes in the role of digital communications technologies in terrorism and studies the radicaliza-
tion of women. As a Research Fellow at the Program on Extremism at The George Washington University, she authored
Cruel Intentions: Female Jihadists in America and published articles in , the Washington Post , and Lawfare blog.
In this role, Alexander also maintains a database of nearly 3,000 pro-Islamic State social media accounts. Before joining
the Program on Extremism, she worked at King’s College London’s International Centre for the Study of Radicalisation
(ICSR) and with the Institute for Strategic Dialogue (ISD). Alexander holds a Masters in Terrorism, Security & Society
from the War Studies Department at King’s College.
The Program on Extremism
The Program on Extremism at George Washington University provides analysis on issues related to violent
and non-violent extremism. The Program spearheads innovative and thoughtful academic inquiry, producing
empirical work that strengthens extremism research as a distinct field of study. The Program aims to develop
pragmatic policy solutions that resonate with policymakers, civic leaders, and the general public.

Digital Decay? • vii
EXECUTIVE SUMMARY
Until 2016, Twitter was the online platform of choice for
English-language Islamic State (IS) sympathizers. As a
result of Twitter’s counter-extremism policies - includ-
ing content removal - there has been a decline in activity
by IS supporters. This outcome may suggest the com-
pany’s efforts have been effective, but a deeper analysis
reveals a complex, nonlinear portrait of decay. Such ob-
servations show that the fight against IS in the digital
sphere is far from over. In order to examine this change
over time, this report collects and reviews 845,646
tweets produced by 1,782 English-language pro-IS ac-
counts from February 15, 2016 to May 1, 2017.
This study finds that:
Twitter’s policies hinder sympathizers on the plat-
form, but counter-IS practitioners should not over-
state the impact of these measures in the broader
fight against the organization online.
‐ Most accounts lasted fewer than 50 days, and
the network of sympathizers failed to draw
the same number of followers over time.
‐ The decline in activity by English-language IS
sympathizers is caused by Twitter suspensions
and IS’ strategic shift from Twitter to messag-
ing platforms that offer encryption services.
‐ Silencing IS adherents on Twitter may pro-
duce unwanted side effects that challenge law
enforcement’s ability to detect and disrupt
threats posed by violent extremists.
The rope connecting IS’ base of sympathizers to
the organization’s top-down, central infrastruc-
ture is beginning to fray as followers stray from the
agenda set for them by strategic communicators.
While IS’ battlefield initiatives are a unify-
ing theme among adherents on Twitter, the
organization’s strategic messaging output about
these fronts receive varying degrees of attention
from sympathizers.
Terrorist attacks do little to sustain the conver-
sation among supporters on Twitter, despite sub-
stantive attention from IS leadership, central pro-
paganda, and even Western mass media.
‐ Over time, there has been a decline in tweets
following major attacks. This suggests that at-
tacks in the West have diminishing effects in
mobilizing support.
Current events – such as the attempted coup in
Tu r ke y a n d t h e 2 016 U. S . pre side nt i a l e le c t i on – a r e
among the most popular topics within the sample.
‐ Events unrelated directly to IS cause some of
the greatest spikes in activity.
‐ These discussions are ongoing despite
Twitter’s policies.
Conclusions and Policy Recommendations
‐ English-language IS sympathizers on Twitter
defy straightforward analysis and convenient
solutions.
‐ They are skilled problem-solvers in the digital
sphere. Rather than ruminating over losses,
angered adherents fight to be heard, either on
Twitter or other digital platforms.
‐ Counter-IS practitioners must show a similar
willingness to adapt and explore alternative
ventures.
‐ While some collaboration is beneficial, the
government cannot rely predominantly on
the efforts of tech companies to counter IS
and its supporters.
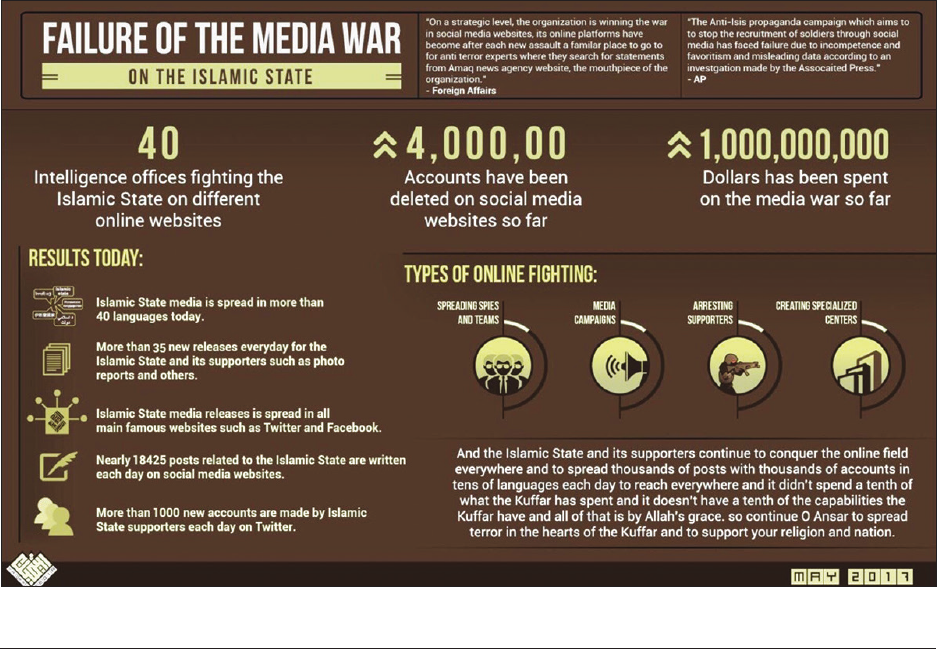
In May 2017, a pro-IS English-language infographic en-
titled “Failure of the Media War on the Islamic State” by
Yaqeen Media Foundation
1
circulated among some of the
movement’s sympathizers on social media (Figure 1).
With a healthy level of skepticism, the graphic highlights
the complexity of the ‘media war’ between IS and its ad-
versaries. On one hand, the image alludes to IS’ dynamic
media strategy, made to amplify the organization’s voice
through coordinated “campaigns” that disseminate con-
tent on “famous websites such as Twitter and Facebook.”
Simultaneously, however, the graphic touts in the bottom
left-hand corner that “More than 1,000 new accounts are
made by Islamic State supporters each day on Twitter.”
Figures from Twitter’s tenth #Transparency Report suggest
the company’s effort to suspend accounts for violations
related to the promotion of terrorism far exceeds a rate
of 1,000 accounts per day, challenging the infographic’s
evaluation of their opponents’ ‘failure’ in the fight against
IS on Twitter.
2
In light of these discrepancies, perhaps
binary measures of success and failure, like winning and
losing, have limited utility in the discourse surrounding
the fight against IS online.
Several conventional markers indicate that the foothold
of the self-styled caliphate is faltering on the ground in
Syria and Iraq. IS has lost considerable territory, putting
a tremendous strain on the organization’s internal rev-
enue streams, while casualties and a decrease in foreign
fighter travel continue to deplete its pool of combatants.
3
The decline in central media output is a symptom, and
perhaps also a cause, of depletion in the physical world.
4
Despite these setbacks, IS sympathizers continue to wage
Digital Decay? • 1
INTRODUCTION
IS Infographic
2 • The George Washington University Program on Extremism
Introduction
a protracted struggle in the digital sphere using a wealth
of digital communications technologies. Thus, the orga-
nization’s presence in the virtual theater is hard to gauge.
IS is strategically adept on social media because of slick
branding, masterful distribution, and effective agen-
da-setting.
5
On a strategic level, the group demonstrates
extraordinary dexterity in navigating the changing me-
dia landscape online.
6
From Facebook and Twitter to
Telegram and Tor, sympathizers fluidly cross between
broad-based platforms and more private, protected chan-
nels.
7
Reaping the benefit of a “two-tier production line”
of “official” and “user generated” content, IS’ propaganda is
accessible to a broad swathe of sympathizers.
8
Moreover,
the multi-lingual approach IS implements “has a clear
objective: targeting non-Arabic
speaking potential recruits.”
9
The
reach of these media products is
optimized by a mix of coordinat-
ed campaigns and the organic ral-
lying of IS’ online supporters.
Despite its competencies, IS is
vulnerable in the digital domain.
Much like the militant wings of
the organization, considerable
challenges confront IS’ networks
online. Due to the prosecution of IS supporters in the
West and targeted strikes on select f ighters in IS-held
territory, operational security is a growing concern
among many sympathizers. IS’ most prolific online re-
cruiter, British hacker Junaid Hussain, was reportedly
killed in 2015 after leaving an Internet cafe in Raqqa,
IS’ de facto capital.
10
A multitude of legal documents and
news media demonstrate the utility of virtual commu-
nications for investigating authorities in mapping the
international network of IS recruiters and recruits.
11
In addition to the actions of the military and law en-
forcement, public and private sector initiatives target IS
in the digital sphere and make it more difficult for ad-
herents to access information and communicate freely.
Existing approaches continue to yield mixed results, re-
lying predominantly on counter-messaging campaigns
and content-based regulation.
12
As it pertains to this report, Twitter regulates content
by suspending accounts that violate the company’s pol-
icies regarding the promotion of terrorism.
13
In the
‘Countering Violent Extremism’ section of the com-
pany’s tenth #Transparency Report, Twitter announced
the suspension of a total of 636,248 accounts between
August 1, 2015 and December 31, 2016.
14
According to
an official blog post published in early 2016, Twitter’s
terrorism-related suspensions were “primarily related
to ISIS.”
15
The company claims to investigate “accounts
similar to those reported” and “leverage[s] proprietary
spam-fighting tools to surface other potentially violat-
ing accounts for review.”
16
Twitter’s efforts to counter
extremism in the virtual sphere extend beyond con-
tent regulation and range from official preservation
requests from law enforcement
to the collaborative promotion
of counter-messaging efforts.
17
In December 2016, the company
announced a hashing-centric in-
formation-sharing partnership
with Facebook, Microsoft, and
YouTube to more effectively f lag
problematic materials with algo-
rithms to “help curb the spread
of extremist content online.”
18
While these indicators suggest IS’ presence has deteri-
orated online, policy makers, law enforcement officials,
and private companies have a limited and largely anec-
dotal understanding of how pro-IS online networks re-
spond to duress in the digital arena. Consequently, this
report will examine how an important cross-section of
English-language IS sympathizers on Twitter adapt to on-
line and offline initiatives aimed at weakening the wider
movement. After reviewing relevant literature, the report
examines change over time in a sample of 845,646 tweets
produced by 1,782 English-language pro-IS accounts on
Twitter between February 15, 2016, and May 1, 2017.
19
This 63-week dataset is among the largest time-bound
samples on the subject, but it only represents a snapshot
of IS’ activity on Twitter. The Program on Extremism
(PoE) collected this corpus of tweets with the support of
software developers in the Scholarly Technology Group
This report will examine how
an important cross-section of
English-language IS sympathizers
on Twitter adapt to online and
offline initiatives aimed at
weakening the wider movement.

Digital Decay? • 3
Audrey Alexander
(STG)
20
of the George Washington University Libraries.
This report is also part of an ongoing initiative tracking
the online efforts of IS in the West.
Despite some limitations, namely the applicability of the
findings to the wider conflict online and offline, this
unique resource offers an opportunity to examine shifts
in activity among English-language IS sympathizers on
Twitter. After contextualizing the broader fight against IS,
the background chapter discusses the synergistic interplay
between the physical, digital, and strategic elements of the
movement. The method chapter articulates PoE’s original
data collection process, identifies key caveats, and punc-
tuates the particular scope, transferability, and reliability
of the findings. The subsequent analysis of the data is split
into two overall sections. The first of these examines the
primary research question, namely: ‘How have Twitter’s
counter-extremism policies affected English-language IS
sympathizers on the platform?’ The second section poses
three supplementary questions to investigate how this de-
mographic of supporters engages with battles in Iraq and
Syria, terrorist attacks, and other current events. These
inquiries probe how English-language IS sympathizers
engage with matters in the physical world, especially con-
sidering the internal and external dynamics that guide
their behavior on Twitter. In tandem, these sections hint
that the dissipation of accessible communication channels
threatens the cohesion of IS’ sympathizers in the West.
Focusing on a small sliver of the broader population of
IS supporters worldwide, this report paints a complex
portrait of the struggle between English-language adher-
ents on Twitter, and the social media company’s efforts to
silence IS’ calls to support the self-proclaimed caliphate.
Rather than focusing exclusively on the numerical decline
in tweet frequency or the plummeting number of pro-
IS accounts, the following discussion strives to unpack
change over time and interrogate the implications for the
broader fight against IS in the digital sphere. Although
findings suggest that the term ‘decay’ best descibes the
effects of Twitter’s policy on the English-language IS
community on Twitter, growing evidence reveals that the
‘media war’ between IS and its adversaries is not nearing a
definitive end, it is just changing.
Notes
1. SITE Enterprise. 2017. “Yaqeen Media Center.” https://ent.
siteintelgroup.com/index.php?option=
com_customproperties&task=tag&tagId=209&
phpMyAdmin=31b32de8000cb1c40d5792b21dc9961a.
2. Tw it t er ’s te nt h #Transparency Report explains, “a total of 376,890
accounts were suspended for violations related to promotion
of terrorism” between July 1 and December 31, 2016. This
amounts to a rate of approximately 2,060 accounts per day.
“Government TOS Reports - July to December 2016.” 2017.
https://transparency.twitter.com/en/gov-tos-reports.html.
3. Jacob Shapiro, “A predictable failure: the political economy of
the decline of the Islamic State,”
9:9, 2016; Stefan Heißner, Peter R. Neumann, John
Holland-McCowan, Rajan Basra, “Caliphate in Decline: An
Estimate of Islamic State’s Financial Fortunes,” Report by the
International Centre for the Study of Radicalisation, 2017;
Lucy Pasha-Robinson, “ISIS loves ‘10,000 fighters and a quar-
ter of territory in 18 months,’” Independent, October 17, 2016.
4. Milton, Daniel. 2016. ‘Communication Breakdown:
Unraveling the Islamic State’s Media Efforts.’ Combating
Terrorism Center at West Point.
5. Koerner, Brendan. 2016. “Why ISIS Is Winning
the Social Media War—And How to Fight Back.”
WIRED, April. https://www.wired.com/2016/03/
isis-winning-social-media-war-heres-beat/.
6. Prucha, Nico. 2016. “IS and the Jihadist Information Highway
– Projecting Influence and Religious Identity via Telegram.”
Perspectives on Terrorism 10 (6), p.52 http://www.terrorismana-
lysts.com/pt/index.php/pot/article/view/556.
7. Alkhouri, Laith, and Alex Kassirer. 2016. “Tech for Jihad:
Dissecting Jihadists’ Digital Toolbox.” Flashpoint. https://
www.flashpoint-intel.com/wp-content/uploads/2016/08/
Tech ForJihad.p df.
8. Prucha, Nico. 2016. “IS and the Jihadist Information
Highway – Projecting Influence and Religious Identity via
Tel eg ram .” Perspectives on Terrorism 10 (6), p.54 http://www.
terrorismanalysts.com/pt/index.php/pot/article/view/556.
9. Prucha, Nico. 2016. “IS and the Jihadist Information Highway
– Projecting Influence and Religious Identity via Telegram.”
Perspectives on Terrorism 10 (6), p.54 http://www.terrorismana-
lysts.com/pt/index.php/pot/article/view/556.
10. Goldman, Adam, and Eric Schmitt. 2016. “One by One, ISIS
Social Media Experts Are Killed as Result of F.B.I. Program.” The
New York Times, November 24. https://www.nytimes.com/2016/
11/24/world/middleeast/isis-recruiters-social-media.html.
11. United States v. Munir Abdulkader (2016), Sentencing
Memorandum; United States v. David Daoud Wright (2017),
Second Superseding Indictment. Wilber, Del Quentin. 2017.
“Here’s How the FBI Tracked down a Tech-Savvy Terrorist
Recruiter for the Islamic State.” Los Angeles Times, April 13.

4 • The George Washington University Program on Extremism
Introduction
http://www.latimes.com/politics/la-fg-islamic-state-recruit-
er-20170406-story.html; Hughes, Seamus, and Alexander
Meleagrou-Hitchens. 2017. “The Threat to the United States
from the Islamic State’s Virtual Entrepreneurs” 10
(3). https://www.ctc.usma.edu/posts/the-threat-to-the-unit-
ed-states-from-the-islamic-states-virtual-entrepreneurs;
12. Google’s Jigsaw, for example, attempts to counter online
extremism with the Redirect Method, which, according to its
website, diverts supporters to “curated YouTube videos” that
confront IS’ recruitment themes. “The Redirect Method -
Jigsaw.” 2017. http://redirectmethod.org.
13. In the official ‘Twitter Rules,’ the company identifies “Violent
threats (direct or indirect)” as grounds for temporarily locking
and/or permanently suspending accounts, explaining, “You
may not make threats of violence or promote violence, in-
cluding threatening or promoting terrorism.” - “The Twitter
Rules.” 2017. Twitter Help Center. https://help.twitter.com/
articles/18311?lang=en.
14. “Government TOS Reports - July to December 2016.” 2017.
https://transparency.twitter.com/en/gov-tos-reports.html.
15. Please note that Twitter made this assertion prior to the
timeframe used in PoE’s report. Although subsequent
suspensions likely continued the trend, PoE cannot confirm
what percentage of the total number of suspensions relate
to IS specifically. “Combating Violent Extremism.” 2016.
Twitter Blogs. February 5. https://blog.twitter.com/2016/
combating-violent-extremism.
16. “Combating Violent Extremism.” 2016. Tw it t er Bl og s. February
5. https://blog.twitter.com/2016/combating-violent-extremism.
17. “Guidelines for Law Enforcement.” 2017. Twitter Help
Center. Accessed September 11. https://help.twitter.
com/articles/41949?lang=en. See also, “An Update
on Our Efforts to Combat Violent Extremism.” 2016.
Twitter Blogs. August 18. https://blog.twitter.com/2016/
an-update-on-our-efforts-to-combat-violent-extremism.
18. “Partnering to Help Curb the Spread of Terrorist Content
Online.” 2016. Twitter Blogs. December 5. https://blog.twitter.
com/2016/partnering-to-help-curb-the-spread-of-terrorist-
content-online.
19. In this context, accounts are distinguished by username rather
than ID number. For more information, this report articulates
the precise logistics of PoE’s approach in the method section.
20. For more information about the Scholarly Technology Group,
see https://library.gwu.edu/scholarly-technology.
Digital Decay? • 5
BACKGROUND
Although several jihadi groups gained online traction
prior to and during the Syrian civil war,
1
Abu Bakr
al-Baghdadi and his pool of supporters set a precedent
by expertly blending the online and offline battlefield.
Arguably more so than its jihadi predecessors and com-
petitors, IS and its media department “embraced the pop-
ularity of social media and other methods of reaching new
audiences,” moving away from hierarchical websites and
forums.
2
In this way, al-Baghdadi, the supposed ‘Caliph’
and a man of few words, encouraged the movement to
speak for itself.
Some analysts rightly question whether the effects of
social media are exaggerated,
3
but counter-terrorism
scholars and practitioners broad-
ly agree that digital communica-
tions technology, especially social
media, are a means by which IS
and its adherents engage with
each other.
4
Using a versatile
media apparatus, IS “managed to
leverage a combination of official
and unofficial actors in support
of its propaganda mission.”
5
This
method helped facilitate a global
movement, posing a real but amorphous threat to entities
inside and outside IS-controlled territory.
As IS gained traction in Syria and Iraq, social media re-
search revealed a burgeoning relationship between ac-
tivity on the ground and a broad base of sympathizers
worldwide. Works like #GreenBirds: Measuring Importance
by the
International Centre for the Study of Radicalisation
(ICSR) and ‘Tweeting the Jihad’ by Jytte Klausen laid
the foundation for research using social media as a lens
to examine the networks of Western foreign fighters.
6
Both studies articulate the relevance of actors outside
IS-controlled territory. Where ICSR emphasizes the in-
fluence of unofficial clerical authorities as ‘dissemina-
tors’ who inform foreign fighters, Klausen suggests that
organizations within extremist networks play a role in
driving jihadist networks.
7
Moreover, Klausen’s study
contends that official IS accounts are vital and tightly in-
tegrated with other types of Twitter profiles, indicating a
more centralized communication strategy.
8
These works,
among others,
9
illuminate how social media affords IS the
opportunity to implement top-down and bottom-up re-
cruitment procedures.
The nature of IS’ central communications continues to
evolve, especially since the group conducts targeted me-
dia initiatives in an effort to mobilize its base of sup-
porters worldwide. In
, Craig Whiteside succinctly
notes that for IS, “controlling the
message is a goal unto itself.”
10
In
pursuit of that aim, “the official
content put out by the Islamic
State is an amalgamation of prod-
ucts from a number of separate,
geographically-centered media
bureaus spread across the group’s
territory.”
11
Anecdotally, IS has
advanced targeted recruitment
by tailoring content to reach a
broader audience. The creation of
which publishes content in multiple languages, including
English, is a testament to IS’ desire to cast a wide net.
12
The
production of non-Arabic content “remains a high prior-
ity for IS” in addition to the continued stream of propa-
ganda targeting Arabic speaking sympathizers.
13
In 2017,
the pro-IS Yaqeen Media Foundation reports that “Islamic
State media [are] spread in more than 40 languages.”
14
Jihadists disseminate these messages across a range of
digital platforms: while some mediums are broad-based
and far-reaching, like Facebook and Twitter, others are
more insular and protected, like Telegram and Kik.
In Documenting the Virtual Caliphate: Understanding Islamic
, a report published in 2015, Charlie
Winter identifies several themes in IS’ ‘brand’ including
The nature of IS’ central
communications continues to
evolve, especially since the
group conducts targeted media
initiatives in an eort to mobilize
its base of supporters worldwide.

6 • The George Washington University Program on Extremism
Background
brutality, mercy, victimhood, war, belonging, and utopia-
nism.
15
Winter notes that IS’ propaganda output had “in-
creased significantly since June 2014.”
16
Multiple analyses
suggest that IS’ top-down propaganda effort reached its
height around July and August 2015.
17
In some instances,
changes in territory correlate with shifts in the aggre-
gate number of media products; this point is increasingly
apparent in the wake of significant losses. Aaron Zelin
notes, “there may be two reasons” for a decline in central
media output: “the killing of IS media operatives, and/
or the loss in territory.”
19
In Communication Breakdown:
, Daniel Milton
traces change over time in IS’ official propaganda dissem-
ination, observing a substantial decline in visual media
products from August 2015 to August 2016.
20
Using official, unofficial, and grassroots communication
channels, IS is often credited with ‘winning the war on
social media.’
21
Although this assertion has some validity,
precise measures of success and failure in the digital arena
are context dependent and difficult to operationalize. IS
uses an interconnected network to disseminate informa-
tion that is always changing and reconfiguring without
relying on the typical hierarchal structure, which is si-
multaneously beneficial and detrimental.
22
IS communi-
cators undoubtedly weathered numerous blows, but this
is not the same as defeat. In his discussion on official pro-
paganda, Milton notes, “setbacks suggest that the efficacy
of the media arm is not a foregone conclusion, but a sub-
jective reality contingent on a wide array of other factors
such as counterterrorism pressure, battlefield conditions,
and personnel availability.”
23
The subsequent discussion
about the dissemination efforts of IS sympathizers on
Twitter must adopt an equally nuanced approach and ac-
count for the major variables that may influence behavior
in the digital sphere.
Nico Prucha aptly articulates the predominant factors
contributing to the early 2016 shift among IS adherents
from Twitter to Telegram. In
Highway, Prucha highlights the dialectical process where-
by Twitter’s growing efficacy in banning sympathizers
led IS followers to pursue alternative means of commu-
nication in other, less regulated spaces.
24
The necessity of
this move is best illustrated by IS’ nostalgia for Twitter;
Prucha explains, “IS media operatives and sympathizers
miss” the platform and some of the group’s media outlets
“called for a return to Twitter.”
25
Furthermore, evidence
suggests that contemporary messaging campaigns “coor-
dinate distribution” on a “multiplatform zeitgeist,” which
often targets Twitter, highlighting the enduring impor-
tance of the medium.
26
Ultimately, despite the increased
operational security afforded by Telegram, the transition
to a platform other than Twitter impedes IS’ ability to ex-
pand online.
27
Despite setbacks, IS uses social media and other commu-
nications technology, to praise, claim, incite, and facilitate
violent activity outside IS-controlled territory. A 2017 re-
port confirms that since 2011, states in Europe and North
America are attractive targets for jihadi operatives.
28
Based on such activity in the United States alone, evidence
suggests that there is no monolithic digital footprint for
an IS sympathizer; they are just as idiosyncratic online as
they are in the real world, and use various forms of so-
cial media to participate in the movement.
29
Moreover,
although some social media platforms prove to be more
commonplace than others within the jihadisphere, sym-
pathizers do not necessarily use them in the same way.
In February 2016, for example, after tracking Safya
Yassin’s various Twitter, Google+, and Facebook accounts
over the span of several months, authorities arrested the
Missouri resident for transmitting threats to injure fed-
eral government employees.
30
In spite of multiple account
suspensions on Twitter, Yassin created new profiles to
disseminate content bolstering IS’ message of violent ji-
had.
31
On August 24, 2015, prior to her arrest, the FBI re-
corded Yassin tweeting personal information, including
the names, locations, and phone numbers, of three federal
employees listed under the title, “Wanted to Kill.”
32
By
January 27, 2016, the FBI identified 97 Twitter accounts
that were “likely” linked to Yassin.
33
Although Yassin’s po-
tential trajectory for physical mobilization and operation-
al links to IS remain unknown, her prolific presence on
social media, namely Twitter, has facilitative significance
because she amplified IS’ violent rhetoric to her sizable
base of followers.

Digital Decay? • 7
Audrey Alexander
In contrast, the case of attempted Garland shooter Elton
Simpson demonstrates a drastically different use of
Twitter (among other platforms) by an IS sympathizer. In
the U.S. On May 3, 2015, Simpson and Nadir Soofi, his
accomplice, drove from Arizona to Texas to attack the
Muhammad Art Exhibit and Contest with assault rifles;
both men were killed by law enforcement before breach-
ing the venue. Before the plot, Simpson had “direct con-
tact” with at least two jihadists abroad “using Twitter di-
rect message and SureSpot.”
34
Although the nature of such
communications vary, links to prolific IS-recruiter Junaid
Hussain and Mohamed Abdullahi Hassan (Mujahid
Miski), the notorious U.S.-linked member of Al-Shabaab,
are suggestive of a more operational connection to for-
malized jihadist groups.
35
On the day of the attack, using
the handle @atawaakul, Simpson allegedly alluded to an
emerging plot on Twitter, creating the hashtag “#texasat-
tack.”
36
According to news reports, Simpson also encour-
aged supporters on Twitter to follow @_AbuHu55ain,
an account tied to Junaid Hussain.
37
Shortly thereafter,
Hussain’s account tweeted statements suggesting that he
had prior knowledge of the attack.
38
Ultimately, Simpson’s
use of Twitter drastically differed from that of Safya
Yassin, demonstrating variance in IS sympathizers’ use of
social media platforms.
Even though IS sympathizers in the West use social me-
dia as a means to connect with the self-proclaimed ca-
liphate, whether operational or ideological, engagement
in the digital sphere varies. The geographic location of
the sympathizer may also influence the channel of en-
gagement which users pursue. Though not empirically
proven, IS sympathizers in the UK, for example, may be
less inclined to download jihadi propaganda than their
counterparts in the US due to differing laws on extremist
content. Admittedly, patterns of participation are likely
defined by operational security considerations, but exist-
ing laws and ease of engagement may factor into sympa-
thizers’ cost-benefit analysis of various means of digital
communications.
In response to the proliferation of violent extremists
online, Western governments, particularly the U.S. and
U.K., have relied much on the participation of tech com-
panies in the fight against IS in the digital domain. In the
U.S. for example, the ‘Madison Valleywood Project’ en-
courages tech and entertainment companies to assist in
the fight against terrorism with counternarratives and
stringent enforcement of their respective terms of ser-
vice.
39
While it is a necessary step to curb the dissemina-
tion of media products that advocate for violent agendas,
the precise impact of such attempts is difficult to quantify.
Even so, it is imperative to discuss the measures used by
tech companies to counter IS online.
The most prevalent contemporary approaches are con-
tent-based regulation and counter-messaging. Such pol-
icies range from stand-alone initiatives by one company
to collaborative engagement by several others. Despite
more recent partnerships with Facebook, Microsoft, and
YouTube, Twitter’s efforts to counter violent extremism
online focus on content-based regulation via account
suspension.
40
Though commendable, Twitter’s approach
produces mixed results. One study suggests that suspen-
sion efforts yield some success, particularly as returning
accounts fail to gain relative traction after suspension.
41
On the other hand, IS sympathizers create new accounts
every day and continue to demonstrate tremendous agili-
ty across multiple platforms. Consequently, the efficacy of
one tech company in silencing IS on its site may produce
negative results across other channels of communication.
Digital communications technologies remain instru-
mental in the exchange of ideas between IS supporters
on a global stage. But still, the flux in communications
between IS-central and its international base of support-
ers is subject to changing tides in the physical and digital
arena. In his discussion about IS media, Whiteside notes,
IS’ “desire to expand required an intensity and quantity
of messaging that might have invited failure due to a lack
of control.”
42
Similarly, although social media affords IS
innumerable opportunities for growth and mobilization,
these channels pose critical challenges to those who seek
to direct and advance the movement inside and outside
IS-controlled territory. In a recent analysis, Bryan Price
and Muhammad al-`Ubaydi highlight IS-central’s effort
to limit its fighters’ use of social media on the ground in
Iraq and Syria.
43
The authors explain, “This is not the first
time [IS] has warned against the use of social media by its
rank-and-file,” but the most recent endeavor in May 2017

8 • The George Washington University Program on Extremism
Background
is “its most forceful attempt to date.”
44
Like IS-central,
sympathizers worldwide adapt to initiatives that target
the movement online and offline, but little is known of
the impact these counter-IS measures have on IS’ online
diaspora. The subsequent study and analysis works to
unpack these dynamics using a sizable sample of English-
language IS sympathizers on Twitter.
Notes
1. Zelin, Aaron. 2013. “The State of Global Jihad Online.”
Washington, DC: New America Foundation. Prucha, Nico,
and Ali Fisher. 2013. “Tweeting for the Caliphate: Twitter
as the New Frontier for Jihadist Propaganda | Combating
Terrorism Center at West Point.”CTC Sentinel, 6 (6). https://
ctc.usma.edu/posts/tweeting-for-the-caliphate-twitter-as-the
-new-frontier-for-jihadist-propaganda.
2. Whiteside, Craig. 2016. “Lighting the Path:the Evolution of
the Islamic State Media Enterprise (2003-2016).” International
Centre for Counter-Terrorism - The Hague. Zelin, Aaron. 2013.
“The State of Global Jihad Online.” Washington, DC: New
America Foundation. Prucha, Nico, and Ali Fisher. 2013.
3. Gilsinan, Kathy. 2015. “Is ISIS’s Social-Media Power
Exaggerated?” The Atlantic, February 23. https://www.
theatlantic.com/international/archive/2015/02/
is-isiss-social-media-power-exaggerated/385726/.
4. Taylor, Harriet. “Most Young Terrorist Recruitment Is
Linked to Social Media, Said DOJ Official,” October 5, 2016.
http://www.cnbc.com/2016/10/05/most-young-terrorist-
recruitment-is-linked-to-social-media-said-doj-official.
html.; Rose, Steve. “The Isis Propaganda War: A Hi-Tech
Media Jihad.” The Guardian, October 7, 2014, sec. World
news. https://www.theguardian.com/world/2014/oct/07/
isis-media-machine-propaganda-war.
5. Milton, Daniel. 2016. ‘Communication Breakdown:
Unraveling the Islamic State’s Media Efforts’. Combating
Terrorism Center at West Point, p.V.
6. Carter, Joseph, Shiraz Maher, and Peter Neumann. 2014.
“#Greenbirds: Measuring Importance and Influence in
Syrian Foreign Fighter Networks.” International Centre for
the Study of Radicalisation. http://icsr.info/wp-content/
uploads/2014/04/ICSR-Report-Greenbirds-Measuring-
Importance-and-Infleunce-in-Syrian-Foreign-Fighter-
Networks.pdf. Jytte Klausen. 2015. ‘Tweeting the Jihad: Social
Media Networks of Western Foreign Fighters in Syria and
Iraq’, , 38:1.
7. Carter, Joseph, Shiraz Maher, and Peter Neumann. 2014.
“#Greenbirds: Measuring Importance and Influence in Syrian
Foreign Fighter Networks.” International Centre for the Study
of Radicalisation. http://icsr.info/wp-content/uploads/2014/04/
ICSR-Report-Greenbirds-Measuring-Importance-and-
Infleunce-in-Syrian-Foreign-Fighter-Networks.pdf; Jytte
Klausen. 2015. ‘Tweeting the Jihad: Social Media Networks of
Wester n Foreign Fighters i n Sy ria and Iraq,’
Ter ro ri sm , 38:1, p.19.
8. Jytte Klausen. 2015. ‘Tweeting the Jihad: Social Media
Networks of Western Foreign Fighters in Syria and Iraq,’
, 38:1, p.19.
9. Bodine-Baron, Elizabeth, Todd C. Helmus, Madeline
Magnuson, Zev Winkelman. 2016. “Examining ISIS Support
and Opposition on Twitter.” RAND Corporation. Berger,
J.M., and Jonathan Morgan. 2015. “The ISIS Twitter Census:
Defining and Describing the Population of ISIS Supporters on
Twitter.” Brookings Institution. https://www.brookings.edu/
wp-content/uploads/2016/06/isis_twitter_census_berger_
morgan.pdf.
10. Whiteside, Craig. 2016. “Lighting the Path: The Evolution of
the Islamic State Media Enterprise (2003-2016).” International
Centre for Counter-Terrorism - The Hague, p.26.
11. Milton, Daniel. 2016. ‘Communication Breakdown:
Unraveling the Islamic State’s Media Efforts.’ Combating
Terrorism Center at West Point, p.IV-V.
12. Joscelyn, Thomas. 2015. “Graphic Promotes the Islamic State’s
Prolific Media Machine.” . Accessed
November 25. http://www.longwarjournal.org/archives/
2015/11/graphic-promotes-islamic-states-prolific-media-
machine.php. Also cited in Whiteside, Craig. 2016. “Lighting
the Path: The Evolution of the Islamic State Media Enterprise
(2003-2016).” International Centre for Counter-Terrorism -
The Hague, p.18.
13. Prucha, Nico. 2016. “IS and the Jihadist Information
Highway – Projecting Influence and Religious Identity via
Teleg ra m.” Perspectives on Terrorism 10 (6), p.52 http://www.
terrorismanalysts.com/pt/index.php/pot/article/view/556.
14. Naturally, pro-IS propaganda infographics are not reliable
sources for statics. Even so, this example highlights IS’
eagerness to demonstrate its global reach. “Failure of the
Media War on the Islamic State” infographic. Yaqeen Media
Foundation, 2016.
15. Winter, Charlie. 2015. “‘Documenting the Virtual ‘Caliphate’:
Understanding Islamic State’s Propaganda,’” Quilliam Foundation.
16. Winter, Charlie. 2015. “‘Documenting the Virtual ‘Caliphate’:
Understanding Islamic State’s Propaganda,’” Quilliam Foundation.
17. In the month of Shawwal (July 17 to August 15, 2015),
IS-central released 892 unique items of propaganda. This,
according to Winter, was its peak. (This is compared to 570
individual media products between January 30 to February
28 in February, 2017.) Winter, Charlie. 2015. “Fishing and
Ultraviolence.” 2017. BBC News. http://www.bbc.co.uk/news/
resources/idt-88492697-b674-4c69-8426-3edd17b7daed;
Lakomy, Miron. 2017. “Cracks in the Online “Caliphate”:
How the Islamic State is Losing Ground in the Battle for
Cyberspace.” Perspectives on Terrorism, 11 (3), p.47; Winter,
Charlie. 2017. “ICSR Insight: The ISIS Propaganda Decline”

Digital Decay? • 9
Audrey Alexander
. March 23; Milton also notes that IS released 700 official
video products in August 2015, only 200 were released
in August 2016. Milton, Daniel. 2016. ‘Communication
Breakdown: Unraveling the Islamic State’s Media Efforts’.
Combating Terrorism Center at West Point.
18. http://icsr.info/2017/03/icsr-insight-isis-propaganda-
decline/
19. Zelin, Aaron. 2015. “ICSR Insight - The Decline in Islamic
State Media Output / ICSR.” . December 4. http://icsr.
info/2015/12/icsr-insight-decline-islamic-state-media-output/.
20. Milton, Daniel. 2016. ‘Communication Breakdown:
Unraveling the Islamic State’s Media Efforts.’ Combating
Terrorism Center at West Point. p.21.
21. Mazzetti, Mark, and Michael R. Gordon. 2015. “ISIS Is
Winning the Social Media War, U.S. Concludes.” The
New York Times. https://www.nytimes.com/2015/06/13/
world/middleeast/isis-is-winning-message-war-us-
concludes.html. Koerner, Brendan. 2016. “Why ISIS
Is Winning the Social Media War—And How to Fight
Back.” WIRED, April. https://www.wired.com/2016/03/
isis-winning-social-media-war-heres-beat/.
22. Fischer, Ali. 2014. “Eye of the Swarm: The Rise of
ISIS and the Media Mujahedeen.”
Diplomacy. https://uscpublicdiplomacy.org/blog/
eye-swarm-rise-isis-and-media-mujahedeen.
23. Milton, Daniel. 2016. ‘Communication Breakdown:
Unraveling the Islamic State’s Media Efforts.’ Combating
Terrorism Center at West Point, p.50.
24. Prucha, Nico. 2016. “IS and the Jihadist Information Highway
– Projecting Influence and Religious Identity via Telegram.”
Perspectives on Terrorism 10 (6), p.54 http://www.terrorismana-
lysts.com/pt/index.php/pot/article/view/556.
25. Prucha, Nico. 2016. “IS and the Jihadist Information Highway
– Projecting Influence and Religious Identity via Telegram.”
Perspectives on Terrorism 10 (6), p.54 http://www.terrorismana-
lysts.com/pt/index.php/pot/article/view/556.
26. Prucha, Nico. 2016. “IS and the Jihadist Information Highway
– Projecting Influence and Religious Identity via Telegram.”
Perspectives on Terrorism 10 (6), p.54 http://www.terrorismana-
lysts.com/pt/index.php/pot/article/view/556.
27. Prucha, Nico. 2016. “IS and the Jihadist Information Highway
– Projecting Influence and Religious Identity via Telegram.”
Perspectives on Terrorism 10 (6), p.56 http://www.terrorismana-
lysts.com/pt/index.php/pot/article/view/556.
28. Vidino, Lorenzo, Francesco Marone, and Eva Entenmann.
2017. “Fear Thy Neighbor Radicalization and Jihadists Attacks
in the West.” Program on Extremism, p.15-16.
29. Alexander, Audrey. 2017. “How to Fight ISIS Online.” Foreign
, April 7. https://www.foreignaffairs.com/articles/
middle-east/2017-04-07/how-fight-isis-online.
30. United States v. Safya Roe Yassin, Criminal Complaint and
Affidavit (2016).
31. United States v. Safya Roe Yassin, Criminal Complaint and
Affidavit (2016).
32. United States v. Safya Roe Yassin, Criminal Complaint and
Affidavit (2016).
33. United States v. Safya Roe Yassin, Criminal Complaint and
Affidavit (2016).
34. Using a mix of evidence, Hughes and Meleagrou-Hitchens link
Elton Simpson to Junaid Hussain and Mohamed Abdullahi
Hassan (Mujahid Miski). For more information about the
nature of these communications, see: “Virtual Entrepreneurs”
Hughes, Seamus, and Alexander Meleagrou-Hitchens. 2017.
“The Threat to the United States from the Islamic State’s
Virtual Entrepreneurs.” CTC Sentinel 10 (3). https://www.
ctc.usma.edu/posts/the-threat-to-the-united-states-from-
the-islamic-states-virtual-entrepreneurs.
35. “Virtual Entrepreneurs” Hughes, Seamus, and Alexander
Meleagrou-Hitchens. 2017. “The Threat to the United States
from the Islamic State’s Virtual Entrepreneurs.” CTC Sentinel
10 (3). https://www.ctc.usma.edu/posts/the-threat-to-the-
united-states-from-the-islamic-states-virtual-entrepreneurs.
36. Callimachi, Rukmini. 2015. “Clues on Twitter Show Ties
Between Texas Gunman and ISIS Network.” The New York
Times, May 11, sec. U.S. https://www.nytimes.com/2015/
05/12/us/twitter-clues-show-ties-between-isis-and-garland-
texas-gunman.html. See also the account linked to Elton
Simpson, Sharia is Light (@atawaakul). “The bro with me and
myself have given bay’ah to Amirul Mu’mineen. May Allah accept
us as mujahideen. Make dua #texasattack,” May 3, 2015. Tweet.
37. Callimachi, Rukmini. 2015. “Clues on Twitter Show Ties
Between Texas Gunman and ISIS Network.” The New York
Times, May 11, sec. U.S. https://www.nytimes.com/2015/
05/12/us/twitter-clues-show-ties-between-isis-and-garland-
texas-gunman.html.
38. “Virtual Entrepreneurs” Hughes, Seamus, and Alexander
Meleagrou-Hitchens. 2017. “The Threat to the United States
from the Islamic State’s Virtual Entrepreneurs.”
10 (3). https://www.ctc.usma.edu/posts/the-threat-to-the-
united-states-from-the-islamic-states-virtual-entrepreneurs.
39. Kang, Cecilia, and Matt Apuzzo. 2016. “U.S. Asks Tech and
Entertainment Industries Help in Fighting Terrorism.” The
New York Times, February 24. https://www.nytimes.com/
2016/02/25/technology/tech-and-media-firms-called-to-
white-house-for-terrorism-meeting.html.
40. “Partnering to Help Curb the Spread of Terrorist Content
Online.” 2016. Twitter Bl ogs. December 5. https://blog.
twitter.com/2016/partnering-to-help-curb-the-spread-of-
terrorist-content-online. Government TOS Reports - July to
December 2016.” 2017. https://transparency.twitter.com/en/
gov-tos-reports.html.

10 • The George Washington University Program on Extremism
Background
41. Berger, J.M., and Heather Perez. 2016. “The Islamic State’s
Diminishing Returns on Twitter: How suspensions are limit-
ing the social networks of English-speaking ISIS supporters.”
Program on Extremism. https://cchs.gwu.edu/sites/cchs.gwu.
edu/files/downloads/Berger_Occasional%20Paper.pdf.
42. Whiteside, Craig. 2016. “Lighting the Path: The Evolution of
the Islamic State Media Enterprise (2003-2016).” International
Centre for Counter-Terrorism - The Hague, p.26.
43. Price, Bryan, and Muhammad al-‘Ubaydi. 2017. “CTC
Perspectives: The Islamic State’s Internal Rifts and Social Media
Ban.” . https://ctc.usma.
edu/posts/ctc-perspectives-the-islamic-states-internal-rifts-
and-social-media-ban.
44. Price, Bryan, and Muhammad al-‘Ubaydi. 2017. “CTC
Perspectives: The Islamic State’s Internal Rifts and Social Media
Ban.” . https://ctc.usma.
edu/posts/ctc-perspectives-the-islamic-states-internal-rifts-
and-social-media-ban.

Digital Decay? • 11
METHOD AND DESIGN
Similar to any study that uses social media as a means to
understand a movement, the following investigation faces
inherent limitations on the scope, transferability, and re-
liability of the dataset. By focusing on English-language
sympathizers on Twitter, a small but substantive sliver of
IS’ online activity, this report adds to a growing body of
research that uses social media as a lens to comprehend
the mobilization efforts of violent extremists worldwide.
From the outset of the project, the author has made a con-
certed effort to implement a design that strives to miti-
gate the effects of such drawbacks. In short, this report
presents analysis on a sample of data gleaned from the
Program on Extremism’s (PoE) broader initiative exam-
ining IS’ use of social media. The following section pro-
vides an in-depth description of the Program’s general
approach to data collection, and then identifies the par-
ticular segment of content interrogated in this report.
Design for Broader Initiative:
Tracking IS’ Use of Social Media in the West
PoE first launched the project investigating the various ef-
forts of English-speaking IS sympathizers on Twitter after
the publication of its December 2015 report
From Retweets to Raqqa. The approach uses a two-step data
collection method to build a substantive, time-bound cor-
pus of tweets by English-language accounts; as of May
2017, the resource contained about one million tweets from
nearly 3,000 accounts. While not a comprehensive snap-
shot of English-language activity on Twitter, this content
allows PoE to cross-examine a spectrum of questions about
IS supporters’ use of social media in the West.
Inspired by a range of studies on the efforts of IS in the
digital sphere, the Program’s mixed method approach
yields a wealth of data apt for qualitative and quantita-
tive analyses. Since the project’s conception, research as-
sistants,
1
under the supervision of PoE fellows and asso-
ciates,
2
have been using open source practices to collect
a snowball sample of English-language accounts exud-
ing pro-IS sentiment via organic content and retweets.
3
When Twitter accounts satisfy the study’s predetermined
criteria,
4
researchers document the user’s name, handle,
link, location, and bio in a spreadsheet and archive digital
records in select circumstances.
5
Although focusing on English-language sympathizers on
Tw i t t er i n h eren t l y l i m i t s t he t r a n s fe r a bi l i t y o f t he s t u d y, t h e
author adopted this approach to build a manageable dataset
and streamline language requirements for the various cod-
ers identifying pro-IS accounts. Moreover, the connection
between IS in Iraq and Syria and its diaspora of sympathiz-
ers in the West requires rigorous examination, creating an
opportunity for more targeted analysis. On Twitter espe-
cially, this approach remains relevant due to IS’ prioritiza-
tion of non-Arabic content, particularly in English.
6
With the support of software developers in the Scholarly
Technology Group (STG)
7
of the George Washington
University Libraries, PoE collects and analyzes con-
tent produced by the running list of IS sympathizers on
Twitter. These accounts are difficult to monitor because
of Twitter’s ongoing efforts to suspend users that violate
their terms of service. To complement manual record
keeping, PoE uses software to archive content produced
by this sample of Twitter accounts around the clock.
Several times a week,
8
the author adds the latest iteration
of newly identified pro-IS handles to a running list of ac-
counts monitored by
Social Feed Manager (SFM),
9
open
source software developed by GWU Libraries. SFM cap-
tures raw data using Twitter’s Application Programming
Interface (API).
10
Every 30 minutes, SFM harvests tweets
posted by accounts that are still active.
11
In addition to the
sheer number of tweets collected by SFM, PoE benefits
from SFM’s collection of each tweet’s complete metadata -
providing investigators access to a wealth of information
that is not visible on Twitter’s web or mobile interface.
12
By saving the tweets as structured data, SFM captures it
in a form that is well-suited for quantitative analysis.
Next, STG maintains a flow of PoE data from SFM
to a data exploration environment where researchers
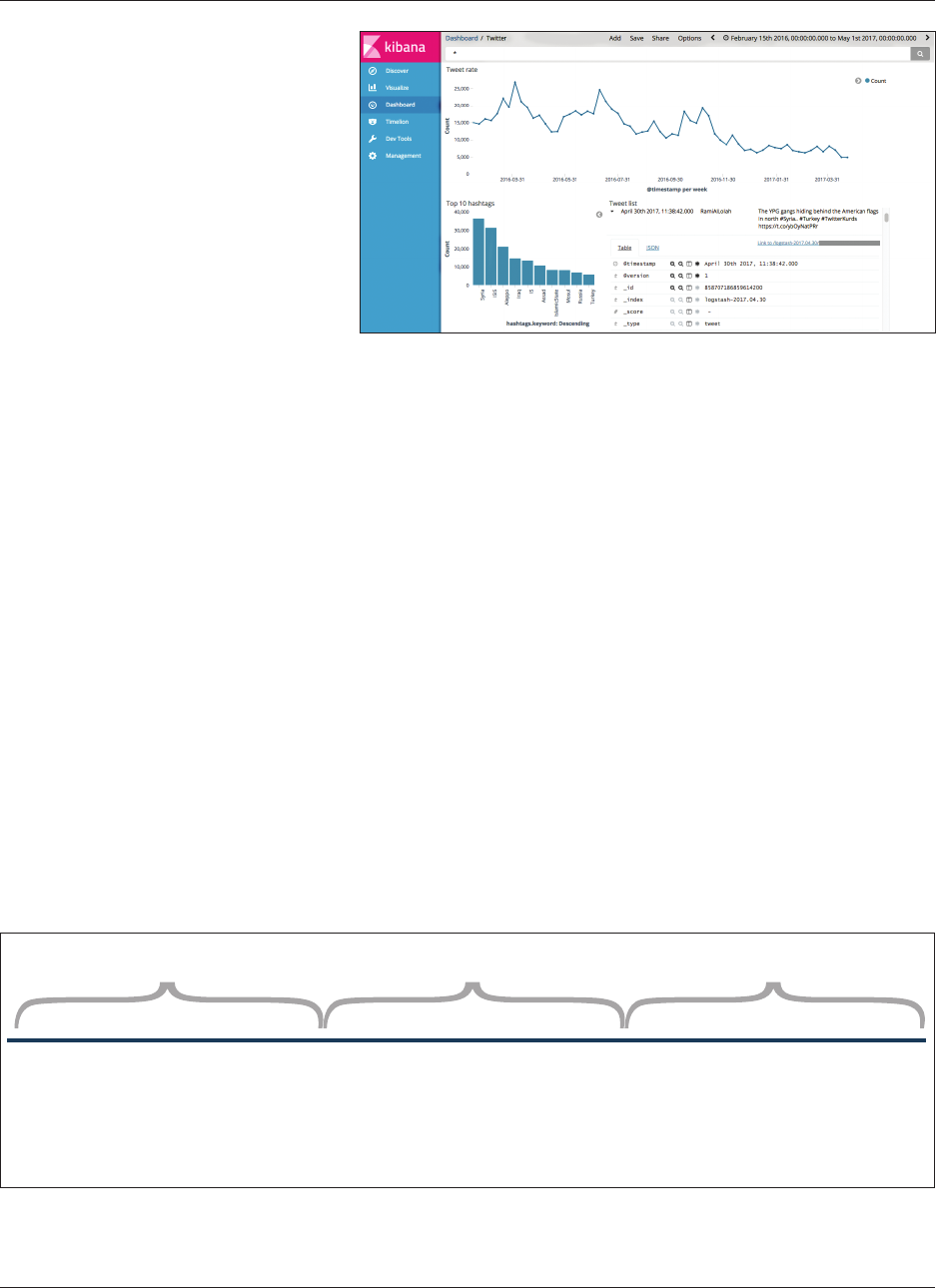
12 • The George Washington University Program on Extremism
Method and Design
can interact with the data using the
Kibana interface. The Kibana interface
is part of an ElasticStack (Elasticsearch,
Logstash, Kibana) server that has been
customized for examining social me-
dia data,
13
making it easy for analysts to
see graphics such as ‘tweet frequency’ or
‘top-ten hashtags’ (See Kibana image).
ElasticStack is a general-purpose frame-
work for exploring data and provides
support for loading, querying, analyz-
ing, and visualizing. SFM’s ElasticSearch
receives a continual stream of tweets as
they are collected by SFM, allowing PoE
to investigate the data in exciting ways
using custom analytics.
Method Employed in This Report
Rather than focusing on the full dataset, which includes a
sharp increase at the beginning due to project implementa-
tion, this report conducts a comprehensive analysis of a
63-week section of tweets ranging from February 15, 2016
at 00:00:00 to May 1, 2017 at 00:00:00. This sample con-
tains 845,646 tweets produced by 1,782 unique accounts of
English-language IS sympathizers on Twitter.
14
The au-
thor selected this time series because it encapsulates a sus-
tained period of account collection that lasts over one year.
This sample also divides neatly into three chronological
21-week segments (see Figure 3), which allows the parti-
tioning of data for comparative analysis of the first, second,
and third part of the dataset.
15
Despite efforts to mitigate these challenges, the most nota-
ble impediments to the comprehensiveness of the sample
stem from project design and implementation. The conti-
nuity of account selection, for example, is imperfect due
to the schedule of staff and volunteer research assistants
who could not devote the same amount of time to data
collection every day during the 63-week period. Twitter’s
regulations and efforts to suspend accounts that violate
their terms of service also appears to curb the quantity
February 15, 2016
February 22, 2016
February 29, 2016
March 7, 2016
March 14, 2016
March 21, 2016
March 28, 2016
April 4, 2016
April 11, 2016
April 18, 2016
April 25, 2016
May 2, 2016
May 9, 2016
May 16, 2016
May 23, 2016
May 30, 2016
June 6, 2016
June 13, 2016
June 20, 2016
June 27, 2016
July 4, 2016
July 11, 2016
July 18, 2016
July 25, 2016
August 1, 2016
August 8, 2016
August 15, 2016
August 22, 2016
August 29, 2016
September 5, 2016
September 12, 2016
September 19, 2016
September 26, 2016
October 3, 2016
October 10, 2016
October 17, 2016
October 24, 2016
October 31, 2016
November 7, 2016
November 14, 2016
November 21, 2016
November 28, 2016
December 5, 2016
December 12, 2016
December 19, 2016
December 26, 2016
January 2, 2017
January 9, 2017
January 16, 2017
January 23, 2017
January 30, 2017
February 6, 2017
February 13, 2017
February 20, 2017
February 27, 2017
March 6, 2017
March 13, 2017
March 20, 2017
March 27, 2017
April 3, 2017
April 10, 2017
April 17, 2017
April 24, 2017
February 15, 2016—July 11, 2016 July 11, 2016—December 5, 2016 December 5, 2016—May 1, 2017
SEGMENT A SEGMENT B SEGMENT C
Breakdown of Time Segments

Digital Decay? • 13
Audrey Alexander
and visibility of pro-IS content available for collection and
analysis. Additionally, while Twitter’s metadata provides
investigators countless opportunities, some useful vari-
ables like location and gender setting of each account is ei-
ther unattainable or unreliable. Such barriers and caveats
receive additional attention in subsequent analysis.
Despite key constraints and the narrow scope of the study,
this dataset allows PoE to test for digital decay over time
among a select demographic of IS supporters on Twitter.
After presenting some initial observations and the decline
in tweet frequency, this report poses one primary and
three supplementary questions to examine how English-
language IS sympathizers on Twitter fare in the face of
online and offline initiatives aimed at weakening the
wider movement.
16
The author selected these questions
from a running list of relevant inquiries that demand
further examination. Using Kibana, the above mentioned
data visualization interface, and a range of tools including
Python, Google Sheets, and Gephi, the study presents the
data and a wide range of findings that pertain to the lim-
inal space between IS’ centralized and decentralized ef-
forts on Twitter. Though dense and technical at times, the
following discussion presents key findings in a nuanced
but accessible way. Many of the graphs, for example, use
the square root on the y-axis to more clearly demonstrate
the relationship of different variables. In other instances,
observations are cross-examined with existing research
to highlight the data’s convergence and divergence with
existing lines of logic.
Notes
1. Special thanks to all the Research Assistants who helped build
PoE’s Twitter database, including: Adib Milani, Armand Jhala,
William Kiely, Graham Raby, Jacob Chereskin, Alexander
Bierman, Helen Powell, Sarah Kells, Nick Gallucci, Dillon
McGreal, Marco Olimpio, Ethan Santangelo, Jessie Gimpel,
Andrea Moneton, Sneha Bolisetty, Tinshan Fullop, Andrew
Walsh, Cole Swaffield, Sam Riccardi, Dan Heesemann.
2. PoE Research Fellows include Bennett Clifford and Katerina
Papatheodorou, and Research Associates include Prachi Vyas
and Sarah Gilkes.
3. In an effort to standardize the project’s data collection
process, research assistants receive extensive training and
ongoing supervision.
4. To be transparent, the author will further explain the account
selection criteria in the appendix.
5. Researchers archive accounts in a shared storage drive if they
meet at least one of the following benchmarks: If the user is
likely (or certainly) an American, if the user provides com-
mentary on U.S. domestic events or Western foreign policy,
if their kunya (a nom de guerre) contains “al-Amriki” (“the
American”), if they locate themselves within the U.S., if they
claim to be in ISIS-controlled territory, if he/she posts original
pro-ISIS content useful for media purposes, if the account has
more than 350 followers.
6. Fernandez, Alberto. 2015. “Here to Stay and growing:Combat-
ing ISIS Propaganda Networks.” The Brookings Project on U.S.
Relations with the Islamic World U.S.-Islamic World Forum
Papers 2015. Brookings Institution. https://www.brookings.edu/
wp-content/uploads/2016/06/IS-Propaganda_Web_English.pdf.
7. For more information about the Scholarly Technology
Group, see https://library.gwu.edu/scholarly-technology.
8. In some instances, accounts are shut down between the time
they are added to PoE’s dataset and fed into SFM. Consequently,
the number of unique accounts in PoE’s social media database
is greater than the number of accounts monitored by SFM.
Though unfortunate, the author does not believe this limitation
undermines the dataset as the majority of accounts are repre-
sented in both the social media database and SFM.
9. For more information on Social Feed Manager (SFM), visit
https://gwu-libraries.github.io/sfm-ui/
10. An Application Programming Interface (API) is a set of com-
mands, functions, protocols, and objects that programmers
can use to create software or interact with an external system.
11. In these cases, PoE’s manual collection method and record keep-
ing complement SFM’s automated process. For example, Twitter
limits the amount of data that it provides through the API, but
PoE’s screenshots helps capture content SFM cannot collect. In
some instances, PoE preserves records of accounts that are shut
down after researchers add it to the internal database but before
it is added to SFM. When a new account is added to SFM, the
Tw it t er AP I prov i de s SFM w i t h da t a in J SON for m at f or t he
account’s most recent 3,200 Tweets. Upon subsequent harvests,
SFM captures any new content produced by the user so long as
the account is active and public. If the account is made protected
(private), deactivated by the user, or suspended by Twitter, SFM
cannot harvest new content from the account.
12. For a description of the metadata contained in a tweet, see
https://dev.twitter.com/overview/api/tweets
13. The ELK Stack is a collection of three open-source products:
Elasticsearch, Logstash, and Kibana. Elasticsearch is a NoSQL
database that is based on the Lucene search engine. Logstash
is a log pipeline tool that accepts inputs from various sources,
executes different transformations, and exports the data to
various targets. Lastly, Kibana is a visualization layer that
works on top of Elasticsearch.

14 • The George Washington University Program on Extremism
Method and Design
14. For the sake of clarity, the number of accounts is calculated
using the number of unique usernames rather than unique
Twitter ID numbers.
15. Segment A spans from February 15, 2016 to July 11, 2016;
Segment B spans from July 11, 2016 to December 5, 2016;
Segment C spans from December 5, 2016 to May 1, 2017.
16. Question 1: How have Twitter’s counter-extremism policies
affected English-language IS sympathizers on the platform?;
Question 2: How do English-language IS sympathizers engage
with on-the-ground IS activity over time?; Question 3: How
do terrorist attacks drive discourse among English-language
IS sympathizers on Twitter?; Question 4: How do current
events influence the activity of English-language IS sympa-
thizers on Twitter?
Digital Decay? • 15
ANALYSIS OF ENGLISH-LANGUAGE IS SYMPATHIZERS ON TWITTER
Digital Decay? • 15
Due to the relative anonymity afforded by Twitter, it is
challenging to speculate about the entities operating be-
hind the 1,782 accounts discussed in this report. Even so,
the data suggest that there is tremendous diversity among
English-language sympathizers on Twitter, with accounts
tweeting from nearly every time zone.
1
For the most part,
accounts adopt demographically ambiguous usernames,
though some allude to factors like gender, nationality, and
familial status, hinting at a disparate array of IS adherents
that defy categorization. In every instance, it is difficult to
discern the authenticity of pro-IS accounts, and thus, the
sincerity of the actors operating them.
IS’ international base of adherents uses multiple lan-
guages to engage with and support the organization
online. Despite emphasizing content produced by
English-language sympathizers on Twitter, PoE’s data
demonstrates the diversity of users on the platform.
Unsurprisingly, over 87 percent of the sample set English
as the primary language of their account; however, tweets
posted by these accounts are not exclusively in English.
2
The other 13 percent represent 16 different languages
ranging from German
and Danish to Indonesian
and Chinese. Indonesian
makes up about 2.7 per-
cent of accounts, the
second most common
language in the dataset.
Somewhat surprisingly,
accounts with Arabic as
their primary language
amassed less than half
a percent. Within the
content produced by this
swathe of accounts tweet-
ing in English, the trans-
literation of Arabic words,
Islamic terms, and jihadi
phraseology are standard.
Accounts that employ
colloquial transliteration and words like ‘coconuts’
3
and
’
4
hark on religiopolitical concepts, actively defin-
ing membership to the English-language IS communi-
ty on Twitter. This demographic, and trends regarding
their use of Twitter over time, receive in-depth analysis
in the following discussion.
There are many ways to examine change over time in online
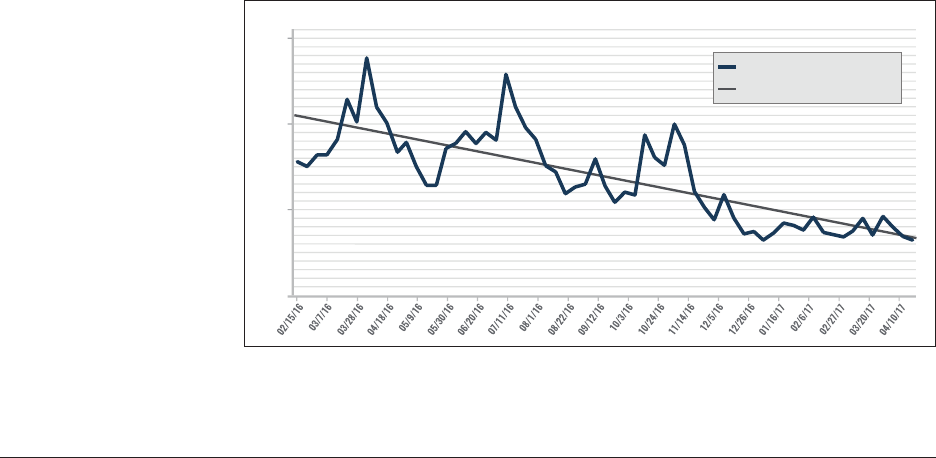
networks. This graph (Figure 4) demonstrates one initial
finding: despite notable fluctuations from week to week,
there is a dramatic decline in tweet frequency by English-
language IS sympathizers on Twitter. From the most active
week to the least active week, there is a 76 percent fall in the
number of tweets per week.
5
Though interesting, the sheer
amount of content disseminated by English-language sym-
pathizers on Twitter is only one measure of change over
time. This numerical decline is not a wholly reliable indi-
cator in isolation: for example, accounts with fewer tweets
may still be more impactful if they are seen by a greater
number of followers. As Ali Fisher notes in a blog post on
interpreting data about IS online, “this type of tactical-level
data can indicate success” in the online fight against IS, but
30,000
20,000
10,000
0
Tweet Count
Trendline for Tweet Count
Tweet Count Per Week

16 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
a more “robust interpretation of data at the strategic level”
is necessary.
6
With this point in mind, the subsequent sec-
tions strive to provide a mix of tactical-, operational-, and
strategic-level analyses.
The following discussion breaks into two analytical sec-
tions. The first strives to answer the question, ‘How have
Tw it te r’s c ou nte r- ex t re mi sm p olic ie s a f fe cted Eng li sh-
language IS sympathizers on the platform?’ With the ini-
tial findings in mind, the second section pursues three al-
ternative paths of inquiry to probe how English-language
IS sympathizers engage with matters in the real world,
especially in light of internal and external dynamics that
guide their behavior on Twitter. Even though it is difficult
to ascertain the precise impact of each cause, particularly
as the various factors may accentuate each other’s effects,
this report strives to determine the key elements shaping
activity by English-language IS sympathizers on Twitter.
Section 1: Key Question and Analysis
How have Twitter’s counter-extremism policies aected
English-language IS sympathizers on the platform?
Twitter’s mounting efforts to suspend accounts that
threaten or promote terrorism correlate with the decline
in tweet frequency found in PoE’s sample of English-
language IS sympathizers. As cited in the introduction,
Twitter “suspended a total of 636,248 accounts” between
August 1, 2015, and December 31, 2016.
7
These users
hailed from multiple extremist persuasions but an of-
ficial blogpost from Twitter asserted that the accounts
were “primarily related to ISIS.”
8
Although Twitter does
not necessarily report its rates of suspension, the compa-
ny published total figures on three separate occasions.
9
The estimates derived from these numbers and the cor-
responding dates reveal a substantial increase in the av-
erage number of accounts suspended per day, particularly
in 2016.
10
With these approximations alone, it is hard to
deduce the precise strategy or chronological implemen-
tation of a more robust initiative to suspend accounts.
Additionally, in a similar fashion to the decline in tweet
frequency, a numerical decline in accounts does not nec-
essarily translate to a reduction in reach.
As articulated in the methodology section, PoE strived to
maintain a consistent level of effort to supply SFM with
a continuous stream of English-language IS sympathiz-
ers’ accounts. This process became increasingly difficult
over the span of several months as accounts that met the
predetermined criteria began to disappear. Anecdotally,
the project manager noticed that a growing number of
accounts became inactive, likely due to suspension, with-
in the short window of time between account selection
and adding the new accounts to SFM.
11
As a result, PoE’s
data collection method may have inadvertently biased the
sample against exceptionally short-lived accounts, partic-
ularly those lasting only a few hours. While difficult to
parse out, it is crucial to consider how this might affect
the following analysis, especially in the context of coordi-
nated media campaigns utilizing Twitter.
Accounts, Tweet Frequency, and
Duration of Activity
Throughout the 63-week period used in this study, SFM
recorded content by 1,782 unique usernames . In the first
third of the dataset, SFM gleaned data from an average of
307 accounts per week. By the last third of the time se-
ries, this average dropped by nearly fifty percent as SFM
collected data from about 155 accounts per week. These
figures give little insight on the enduring centrality or
connectivity of the movement (or perhaps lack thereof),
but receive additional attention later in the discussion.
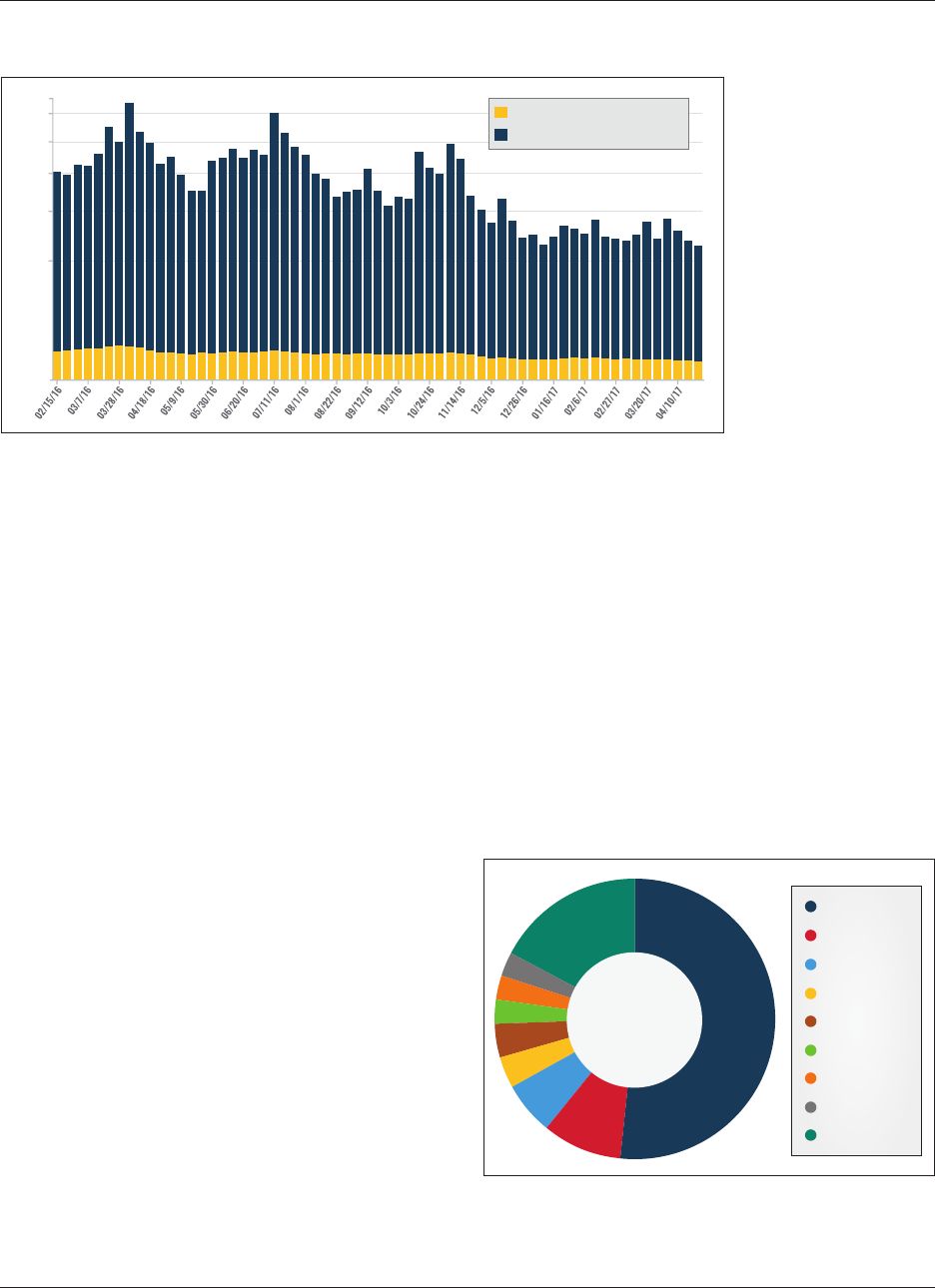
The fall in tweet frequency relates to the decline in the
number of active accounts collected by SFM each week
(See Figure 5).
12
During the 63-week period, 1,782 distinct
usernames tweeted at an average rate of approximately 56
tweets per week. In the last third of the dataset, the aver-
age number of tweets per week by account fell compared
to the first two-thirds of the time series. Although this
change was not dramatic, an observation supported by
basic calculations and likely subject to the pull of outliers,
it might suggest that English-language IS sympathizers on
Twitter share less content per week over time. One con-
tributing factor might be the migration of users to other
platforms, but no singular cause has led to this decline.
The duration of account activity is another factor that
requires consideration. In this context, a user’s ‘duration
Digital Decay? • 17
Audrey Alexander
of activity’ is quantified by the number of days between
an account’s first and last tweet. Twitter’s API does not
discern the date or time at which the company suspends
accounts, nor does it identify accounts that were created
and then subsequently abandoned by their respective us-
ers. Consequently, this measurement allows the study to
grasp the chronological span of sympathizers that actively
use the platform to share content. While overwhelmingly
skewed by outliers, the average lifespan for this sample
of English-language pro-IS accounts on Twitter was 251
days. It is critical to note, however, that dispersion of lifes-
pan is highly concentrated (see Figure 6). Approximately
51.7 percent of accounts did not remain active longer than
50 days. On the other hand, however, a substantive portion
of accounts lasted over a year, suggesting that Twitter’s at-
tempts to detect and suspend pro-IS account may be miss-
ing some long-term users. One possible explanation for
long-standing users relates to the data collection meth-
od, as researchers are more likely to identify accounts the
longer they are open.
13
Ultimately, accounts that opted to
leave the platform are likely included in this breakdown,
although multiple factors- including the threat of suspen-
sion- likely affect user activity in this regard.
In order to maintain their presence on Twitter, some
English language IS sympathizers appeared to have created
multiple accounts at the same time to avoid shutdowns. On
February 17, 2016, for example, four separate accounts were
fashioned from a core handle,
14
possibly from the same
individual. One account (@erhabi35) survived only eight
days, whereas another account (@Erhabi39) stayed active
for 62 days. Although the study attempted to annotate cases
where the same individual controlled multiple accounts, as
the trend is common, quantitative figures are generally not
reliable due to the relative anonymity Twitter affords users.
It is hard to ascertain whether users that demonstrate simi-
lar behavioral patterns are simply individuals attempting to
inoculate their digital presence against suspensions or are
0
5,000
10,000
15,000
20,000
25,000
Unique Count of Screen Name
Number of Tweets
0-50 Days
51-100 Days
101-150 Days
151-200 Days
201-250 Days
251-300 Days
301-350 Days
351-400 Days
*Over 401 Days
51.7%
16.9%
4.0%
6.1%
9.5%
shows how the relationship
per week changed over
like several others in the
represent the relationship
Tweet Frequency and Unique Screen Names By Week
(Figure 6) This chart depicts the duration of account activity,
meaning the number of days a pro-IS Twitter account was
active, and displays the breakdown in percentages.
Duration of Account Activity
18 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
part of an IS-coordinated initiative to influence discourse
on Twitter. Although these aims are not mutually exclu-
sive, it is critical to consider the varying drivers of engage-
ment on Twitter.
In a similar vein, some returning English-language IS
sympathizers proudly sport evidence of their previous
suspensions in their Twitter bios or tweets. Seemingly
operated by the same user, eleven iterations of the han-
dle @DriftOne appear in the dataset. In the bio for @
DriftOne154, one of the more recent accounts, the user
states to be on his or her “154th Account,” demonstrating
their resilience. In one analysis, Amarnath Amarasingam
explains, “Getting suspended is also an important way for
members of the Baqiya community [the broader online
IS network] to know that you are trustworthy, that you
have paid your dues.”
15
Previous studies have observed
communal rallying in the face of suspensions, a trend that
continues among many accounts within the dataset. Such
behaviors are often cast as efforts to rebuild a robust fol-
lowership after suspension.
16
Although English-language IS sympathizers try to com-
pensate for the impact of suspensions, further analysis
on follower count over time suggested that the network
is still affected by these policies. A decline in follower
numbers associated with each account at the time of its
last Tweet speaks to the efficacy of Twitter’s policy in
hindering the connectivity in the English-language ji-
hadisphere (see Figure 7). For this analysis, each account’s
number of followers was identified using the metadata
of the account’s last tweet. The follower count figures
were divided into three chronological buckets (see Figure
3) based on the date of the last tweet. Segment A spans
from February 15, 2016 to July 11, 2016; Segment B spans
from July 11, 2016 to December 5, 2016; Segment C spans
from December 5, 2016 to May 1, 2017. Next, the three
segments were plotted on a box and whiskers chart to
400
300
200
100
0
Follower Count
SEGMENT A SEGMENT B SEGMENT C
February 15, 2016 to
July 11, 2016
July 11, 2016 to
December 5, 2016
December 5, 2016 to
May 1, 2017
17
Follower Count by Chronological Segment

Digital Decay? • 19
Audrey Alexander
identify key trends (Figure 7). Of the accounts whose last
tweet fell in Segment A, the first 21-weeks of the sample,
the median follower count was 141. For Segment B, this
number fell to 108. By Segment C, the last 21-weeks of the
dataset, the median count was 82 followers. These find-
ings reveal a notable decline in the number of followers
accounts were able to amass over time: the median from
the data in the first third of the dataset fell 42 percent by
the last third of the series. The values associated with the
middle 50 percent of each segment also trended toward
decline (Figure 7). These findings support the notion that
Twitter’s policy deteriorates IS followers’ ability to gain
traction on the platform, likely hindering their reach to
potential recruits.
While difficult to operationalize, it is crucial to consid-
er how Twitter’s counter-terrorism initiatives might also
impact the logic of future decisions made by English-
language IS sympathizers on the company’s service.
Twitter is largely credited with hindering IS sympathiz-
ers on its platform,
18
but data in this study hints at a more
complex dynamic. If Twitter’s policies were responsible
for decline on the platform, then sympathizers might
have been pushed towards other communication chan-
nels. Using this logic, one reasonable hypothesis predicts
a positive relationship between the rise of suspensions
and discussion among English-language IS sympathizers
about suspensions, and more hospitable avenues for com-
munication. In the past, both IS propaganda and peer-to-
peer dialogue online proffered recommendations about
best practices regarding operational security and suspen-
sion avoidance. For example, IS released a 34-page guide-
book advising members on how to operate securely while
online. The guide gives suggestions on how to keep com-
munications and locations private in order to avoid sus-
pension on platforms like Twitter.
19
Colloquially known
as the “Baqiya family” on Twitter, English-language sym-
pathizers sometimes give new accounts of previously
suspended users a “shout-out” with Twitter’s ‘mention’
function to help the users fight back and “regain their
pre-suspension status.”
20
These various forms of content
may only account for a small portion of the broader dis-
cussion, but they have serious implications about the re-
silience of the movement.
Mentions
To further understand how factors like account activity
and the numerical decline in follower count might affect
sympathizers on Twitter, the analysis examined English-
language accounts’ use of mentions. On Twitter, the “@”
symbol is used to engage with and direct attention towards
other accounts. Though mentions are not comprehensive
indicators of influence and reach, they are the best option
afforded by PoE’s dataset.
21
Furthermore, approximately
72 percent of tweets by English-language sympathizers
mention another user. By discussing patterns regarding
Twitter mentions and studying the most cited accounts,
the study begins to parse out relevant actors in the com-
munity but further analysis is necessary.
To better understand the relationship between English-
language sympathizers and other Twitter users, research-
ers created a social network based on mentions in tweets
within the sample. In the dataset, some tweets mention
only one account, whereas others cite multiple at once. In
this analysis, the ‘mentions’ variable is divided into two
categories: usernames that are on the list of 1,782 accounts
in PoE’s sample, and those that are not.
22
Of the 1,782 ac-
counts, only 1,700 used the mention function on Twitter;
consequently, only these accounts are represented in the
network. Alternatively, there were 61,590 unique user-
names mentioned in the sample that do not fall within
PoE’s list of accounts. In the graphic above, the latter
usernames were aggregated into a singular node in the
network. The nodes that represent accounts within PoE’s
list remain distinct in order to demonstrate connectivity
through mentions among accounts in the sample. In in-
stances where an English-language IS sympathizer men-
tioned another username more than once, the edges be-
tween these nodes were condensed into a single, weighted
edge. On the most basic level, this allows the report to
explore how conversations occur amidst adherents and
extend beyond the finite list of accounts that are the focus
of this study.
Of the total sample, 85 percent of mentions referenced user-
names outside of PoE’s list of accounts (see Figure 8). While
this analysis is rudimentary, these measures suggest that
English-language sympathizers reach accounts that are not
definitively part of the English-language IS community on
20 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
Tw i t te r. A n e cdot a l l y, a d heren t s d i re c t at tent i on t ow a rds a
broad swathe of accounts on Twitter, ranging from news
organizations and terrorism scholars to other jihadis, in-
cluding other supporters of IS and Jabhat Fateh al-Sham.
23
The remaining 15 percent of mentions were directed at
other accounts within PoE’s list. This finding is especially
interesting given English-language sympathizers comprise
only 3 percent of all unique accounts cited in the sample of
mentions. Simply stated, there appears to be a meaningful
flow of communications between accounts engaging with
a nebulous pro-IS community on Twitter.
Next, it is useful to discuss the most mentioned accounts
by English-language sympathizers. The data show that the
most common mentions are highly concentrated. The top
ten accounts range from 4,244 to 18,700 mentions, then
rapidly curtail. In fact, only the top 25 manage to exceed
2,000 mentions. This point is especially striking consider-
ing the extensive list of 63,868 unique accounts. Ultimately,
no overarching trends aptly predict high mentions count,
though this subset of prolific accounts often disseminates
a substantial amount of content and attracts a large follow-
ing. Based on observation, the purpose of each account var-
ies in nature: some act as watchdogs ‘reporting’ IS-related
news, while others engage in political discourse as an in-
dividual rather than as an agency. Two accounts, using the
same naming convention, ‘RamiAlLolah,’ rank third and
sixth, grossing 17,005 mentions in total. According to one
of the RamiAlLolah accounts, the operator claims to be an
“Act iv ist & commentator cover ing & observ ing a ll news”
offering “exclusives & intelligence reports from the Middle
East conflict zones as well as the Islamic State affairs.”
25
In
this way, it is necessary to punctuate the idea that one enti-
ty, using multiple accounts, may occupy a significant por-
tion of the overarching discourse among English-language
sympathizers on Twitter.
Notably absent from the list of top mentions are the
accounts of users like Ahmad Musa Jibril and Musa
Cerantonio, whom ICSR identified in the #GreenBirds
study.
26
Similarly, additional accounts that were once
deemed influential by Klausen in Tweeting the Jihad, in-
cluding that of Anjem Choudary, were not prevalent
within the dataset.
27
This is not surprising, particularly
in light of the incarceration of Cerantonio and Choudary,
accompanied by the internet restriction imposed upon
Jibril by a federal judge in June 2014.
28
Even so, a prima-
ry survey of the most influential accounts in the dataset,
whether based on top follower count or mentions, does
not suggest that similar figures - especially accounts af-
filiated with prolific persons offline - have filled the void
and replaced Jibril, Cerantonio, and Choudary.
In the realm of more traditional, offline counter-terror-
ism, ‘decapitation’ initiatives strive to capture or kill the
leader of an organization in an effort to stymie the move-
ment.
29
Historically, such approaches tend to yield mixed
results, sometimes hindering an organization while si-
multaneously emboldening its adherents.
30
A derivative
of this phenomenon emerges online in the wake of digital
decapitation by way of silencing leadership figures online.
Although English-language IS sympathizers on Twitter
Mentions of unique
usernames within
PoE’s list of accounts
15%
(1,782)
85%
(61,590)
This node represents the
aggregate of all username
mentions directed toward
accounts outside of PoE’s
list of accounts
24
Tracing Username Mentions by
English-Language IS Sympathizers

Digital Decay? • 21
Audrey Alexander
struggle to efficiently replace authoritative voices with
more anonymized, less legitimate accounts, IS adherents
online also mobilize in the wake of various decapitations.
While some users call for the reinstatement of suspended
users, others emulate key figures with copycat accounts.
URLs and Top-Level Domains
To f ur t he r prob e t he enga gement o f E ng l ish-la ng ua ge IS
sympathizers on Twitter, the study conducted a prelim-
inary content analysis of the hyperlinks disseminated by
the various accounts. Anecdotally, a wide range of sites are
shared, from blogs and social media to fundraising plat-
forms and news outlets. By isolating the top-level domain
and suffix of the shared links, the approach identified nota-
ble URLs for further analysis. After parsing the links with
basic queries, which were not wholly reliable due to the
truncated URLs, initial measures provided some insight
into the nature of link shares. News stories were among
the most commonly posted. While CNN, BBC, and the
New York Times drew about 900 posts respectively, RT,
the web-based Russian news outlet, grossed approximately
1,175 shares. Official, unofficial, and other pro-IS online
media is especially difficult to measure using hyperlinks
because of the diversity in domains. Links for Al-Bayan, IS’
radio station, came in various iterations including albayan-
radio.xyz, bayanradio.xyz, bayanradio.net, bayanradio.top,
al-bayan.pw, and bayanradio.ga. When domains such as
this are shut down or made inaccessible, it is hard to discern
the legitimacy and authenticity of the source.
File sharing services were especially common, but spe-
cific platforms varied in popularity. JustPaste.it, for ex-
ample, drew 3,133 shares and Archive.org drew 1,180
shares. These sites often contained more links that lead
readers to propaganda videos, graphics, and texts. Many
less cited, yet noteworthy, file sharing services received
fewer mentions: SoundCloud, top4top.net, and vid.me,
for example, garnered around 200 shares each. One fas-
cinating observation was the popularization of the blogs
of Western scholars of terrorism, particularly those who
shared primary documents pertaining to IS. Aaron Zelin’s
jihadology.net, for instance, was shared 339 times.
Blogs and social media platforms comprise an integral seg-
ment of URLs among English-language IS sympathizers on
Tw i t te r. Fo r b lo g s, Word Pres s i s e s pe ci a l ly popu l a r, n et t i ng
about 1,690 shares, whereas Blogspot and Tumblr drew
around 300 shares each. In the context of more traditional
social media sites, which often integrate file sharing fea-
tures, Twitter-related links were the most common. This
was likely due to sharing conventions within the medium.
While YouTube received 11,321 link-shares, Facebook
drew 3,540 URL posts, showing each platform’s enduring
relevance among English-language jihadists on Twitter. As
a complement to broad-based social media platforms, there
were a small but important number of URLs demonstrating
English-language IS sympathizers’ interest in anonymous
question-and-answer sites like ask.fm and curiouscat.me as
well as encrypted messaging platforms like Telegram.
While URLs provide some insight, it is crucial to acknowl-
edge how some mediums that are popular among jihadists
are not necessarily accessed through traditional search
engines. On one hand, English-language IS sympathizers’
use of the dark web is hard to gauge. Even so, within the
dataset, a handful of links referenced torproject.com, the
outward facing home page for the anonymous Tor brows-
er, and links with the domain suffix ‘.onion,’ which are
reachable only by using the Tor network. On the other
hand, messaging apps like Telegram, Surespot, and Kik
are widely accessed through app stores, even when they
have web-based platforms, likely changing how accounts
on Twitter share content about the apps themself. As
opposed to Twitter, once individuals download the app,
there is no need to return to the site to login to use the
tool. Consequently, these alternative means of communi-
cation, among others, require further consideration.
Discussion Regarding Other Digital Tools
In addition to hyperlinks, the text of each tweet affords
innumerable opportunities for subsequent analysis.
Within the scope of Twitter’s effects on English-language
IS sympathizers on the platform, discourse about alter-
native means of communications technologies is of par-
amount importance. In the face of mounting restrictions
on Twitter, among other platforms, evidence suggests
that jihadists “frequently leverage digital technologies to
circumvent these barriers.”
31
Although English-language
sympathizers on Twitter likely use a variety of mediums
that vary in nature, it is crucial to discuss their interest

22 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
in more protected channels of communication. Existing
research helps structure and inform this analysis.
In Flashpoint’s , Laith Alkhouri and Alex
Kassirer grouped a sample of digital tools into six typolo-
gies: secure browsers, virtual private networks (VPNs) and
proxy services, protected e-mail services, mobile security
applications, encrypted messengers, and mobile propagan-
da applications.
32
After querying the dataset for the “most
noteworthy tools and technologies” listed in ,
investigators manually combed through tweets to identify
a range of additional digital instruments used by English-
language IS supporters specifically. Despite diverging from
the “noteworthy” list at times, this list of tools and technol-
ogies fell into the six typologies discussed by Flashpoint.
Anecdotally, the most commonly discussed instruments
among sympathizers on Twitter were encrypted messen-
gers,
33
mobile security applications,
34
protected email ser-
vices,
35
and VPNs and proxy services.
36
Using the examples listed for the various instrument
types above, the author created a list of 17 tools used by
English-language supporters on Twitter. This list in-
cludes Telegram, Surespot, WhatsApp, Threema, Signal,
WeChat, Viber, FlashVPN, TurboVPN, SuperFreeVPN,
F-Secure Freedome, Veracrypt, Nextplus, GPG4USB,
Tutanota, Protonmail, and Hushmail. Upon investiga-
tion, a slight but compelling trend emerges: the propor-
tion of tweets that reference these tools recedes over time.
Although this sample does not encapsulate all digital in-
struments used by English-language IS sympathizers on
Twitter, these findings contradict the notion that the rise
in suspension correlates with a proportional increase in
content discussing challenges posed by Twitter’s policy.
While it is difficult to identify the precise cause of this nu-
merical and proportional decline, several indicators sug-
gest that it might be a product of users leaving the platform
of their own volition, which is not mutually exclusive from
suspension. If account suspensions on Twitter and ongoing
operational security concerns create a demand for an al-
ternative means of online engagement for pro-IS accounts,
it is hard to explain the decrease in references to less reg-
ulated or more protected and anonymizing forms of dig-
ital communications technology.
37
The decline in content
exploring alternatives to Twitter might suggest that some
English-language IS sympathizers moved away from the
platform, apparently in search of channels that better suit-
ed their needs for online engagement. As discussed in the
background section of this report, IS’ early 2016 strategic
shift from Twitter to Telegram
38
likely influenced these
findings. Furthermore, publicity surrounding events like
Tw i t te r ’s a n n ou ncemen t s of s us pe n sio ns,
39
and the FBI’s
unlocking of the San Bernardino shooters’ phone,
40
pos-
sibly dissuaded sympathizers from using the technologies
perceived to be insecure, including Twitter.
Within the dataset, some English-language IS supporters
express frustration, concern, and anger towards Twitter’s
policy and its effects on the online community. In some
instances, IS supporters leverage the expulsion of other
accounts to validate polarizing narratives about the per-
secution of Muslims. In the wake of a terrorist attack in
Brussels, Belgium, one English-language IS sympathizer
with the handle @we_r_back64 tweeted a screenshot of
its recently suspended account, @we_r_back63, with the
caption, “Hey kuffaar Worry about your belgium people,
instead of suspending us. Lolzzzz.”
41
On July 20, 2016, a
different IS supporter expressed their grievance in a tweet
stating, “Without a doubt Twitter suspensions are biased
against us. They hate us.”
42
On April 9, 2017, a now-sus-
pended English-language sympathizer with the handle
@ssvvah tweeted, “It seems people were suspended. I
would love to follow more but I can’t. So I just hope not ev-
eryone gets suspended.”
43
The adherents’ varying reactions
to Twitter’s counter-terrorism policy demonstrate how
suspensions affect the morale of some users. Therefore, it is
crucial to consider how the perception of persecution in the
digital sphere may push English-language IS sympathizers
towards other means of communication.
Key Findings
Tw it ter’s cou nter-ex tremism pol icies have a ffec ted
English-language IS sympathizers in a myriad of ways
on the platform, but the fight is far from over. The term
‘decay’ best characterizes the slow decomposition expe-
rienced by PoE’s sample of English-language supporters
on Twitter. Using various metrics to unpack the dataset,
the study punctuates the extent to which Twitter’s ap-
proach, particularly regarding suspension, yields mixed
Digital Decay? • 23
Audrey Alexander
results. Although English-language IS followers strug-
gle to maintain their hold on the platform, and fail to
attract the same degrees of followership after suspen-
sion, mounting evidence suggests that supporters con-
tinue to adapt to the online environment.
Tech companies, policy makers, and other counter-
terrorism practitioners should not underestimate the
agency of those who want to be vocal about their sup-
port of IS and participate in the movement. While some
English-language IS sympathizers rally in the face of
Twitter suspensions with new accounts, others seem to
cut their losses and migrate to more hospitable online en-
vironments. Each individual’s decision to remain on one
digital platform, or expand across multiple, likely entails a
cost-benefit analysis that accounts for the ease of engage-
ment, reach of the networks, and operational security of
various communications channels. Such preservative ac-
tions ensure a future for the English-language IS commu-
nity, whether on Twitter, or elsewhere in the ether.
To c ha l lenge t his spec if ic group, a cto rs f i ght i ng IS on-
line must respect the agility of sympathizers and work
(Figure 9) These screenshots illustrate the various ways in which
to understand their limitations on platforms oth-
er than Twitter. Although IS made a strategic shift
from Twitter to Telegram, this step was the product
of necessity. In
Miron Lakomy explains, “The biggest challenge that
the Islamic State faces nowadays in cyberspace con-
cerns the decreasing availability of online propaganda
distribution channels.”
44
Despite offering some bene-
fits, namely improved operational security, apps like
Telegra m l i mit t he reac h of IS co mpa re d to Tw it te r.
Similarly, blogs and file-sharing tools like JustPaste.
it have utility in content distribution, but are not net-
worked in the same way, thereby curbing the reach
and connectivity of the English-language “Baqiya
family.”
45
Like many preventative efforts, it is tricky to mea-
sure the precise impact of social media regulations
and shutdowns in combating the radicalization and
mobilization of recruits. The strongest evidence in
support of suspensions is that the approach tends
to make the dissemination of violent rhetoric harder to
broadcast, which might reduce the mobilization of ex-
tremist actors. In this context, suspending accounts that
distribute tactical manuals and official calls to action
likely reduce violence more than the expulsion of banal
followers that merely parrot the same content as other IS
supporters in the echo chamber. Broadly, however, con-
vincing data that links account suspensions with an over-
arching reduction in terrorist violence remains sparse.
Alternatively, it is hard to ignore the role of social media
and other virtual communications as evidence in legal cas-
es of persons arrested, indicted, and convicted on terrorism
related charges in the U.S. Twitter is relatively transparent
about its case-by-case cooperation with law enforcement,
especially compared to other companies, but it remains
tough (and often impossible) to access records through of-
ficial channels after accounts are suspended.
46
In Virginia,
law enforcement used “Twitter records and posts publicly
placed on Twitter” to help build a case against Haris Qamar,
a man accused of supporting IS in July 2016.
47
The investi-
gation revealed that Twitter closed “over 60 accounts that
included ‘newerajihadi,’” a handle linked to Qamar, and

24 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
notes that “shortly after,” new Twitter accounts replaced
the suspended ones.
48
In some ways, authorities were fortu-
nate to have this evidence at their disposal. If Qamar used
a platform inaccessible to law enforcement, Qamar could
have posed different barriers to the investigation of law
enforcement or circumvented detection altogether. While
challenging to confirm ownership, the dataset used in this
report contains six ‘newerajihadi’ accounts that were active
before Qamar’s arrest (see Figure 10).
In sum, these findings challenge the idea that either side,
IS or its adversaries, is ‘winning’ the war on Twitter,
much less anywhere else online. Though limited in scope,
data gleaned from English-language IS sympathizers on
Twitter suggest that this battlefield extends far beyond
the reach of major tech companies and Western gov-
ernments. Consequently, by working to understand the
dynamics at play on Twitter, discussion pushes to under-
stand how English-language sympathizers adapt during
times of duress. By unpacking how efforts to silence the
movement on Twitter have produced some benefits, but
also many unintended consequences, the data can help
identify more optimal steps for the fight against IS online,
particularly in the concluding discussion.
Section 2: Battles, Attacks, and Current Events
This section uses three separate inquiries to demonstrate
how English-language IS supporters engage with re-
al-world issues, especially considering internal and external
dynamics that guide the demographic’s behavior on Twitter.
The questions turn to examine the coherence of the move-
ment in light of fractured communications. The first inves-
tigates how English-language IS sympathizers on Twitter
engage with on-the-ground IS activity over time. The
second asks how terrorist attacks drive discourse among
this demographic of Twitter accounts. The third considers
how other current events influence the activity of English-
language IS sympathizers on Twitter. The inextricable link
between IS-central’s adaptive media strategy, territorial
losses in Iraq and Syria, and the death of propagandists like
Abu Muhammad al-Adnani, IS’ former chief strategist of
communications,
50
affect discussion among adherents on-
line. Consequently, the analysis will draw upon existing re-
search to help explore the study’s various findings.
2.1 How do English-language IS sympathizers on Twitter
engage with on-the-ground IS activity over time?
Emerging evidence posits a relationship between IS-
related events in Iraq and Syria and shifts in the corre-
sponding digital sphere, and some research has traced
the evolving relationship between material losses on
the ground and the online activity of IS supporters. This
49
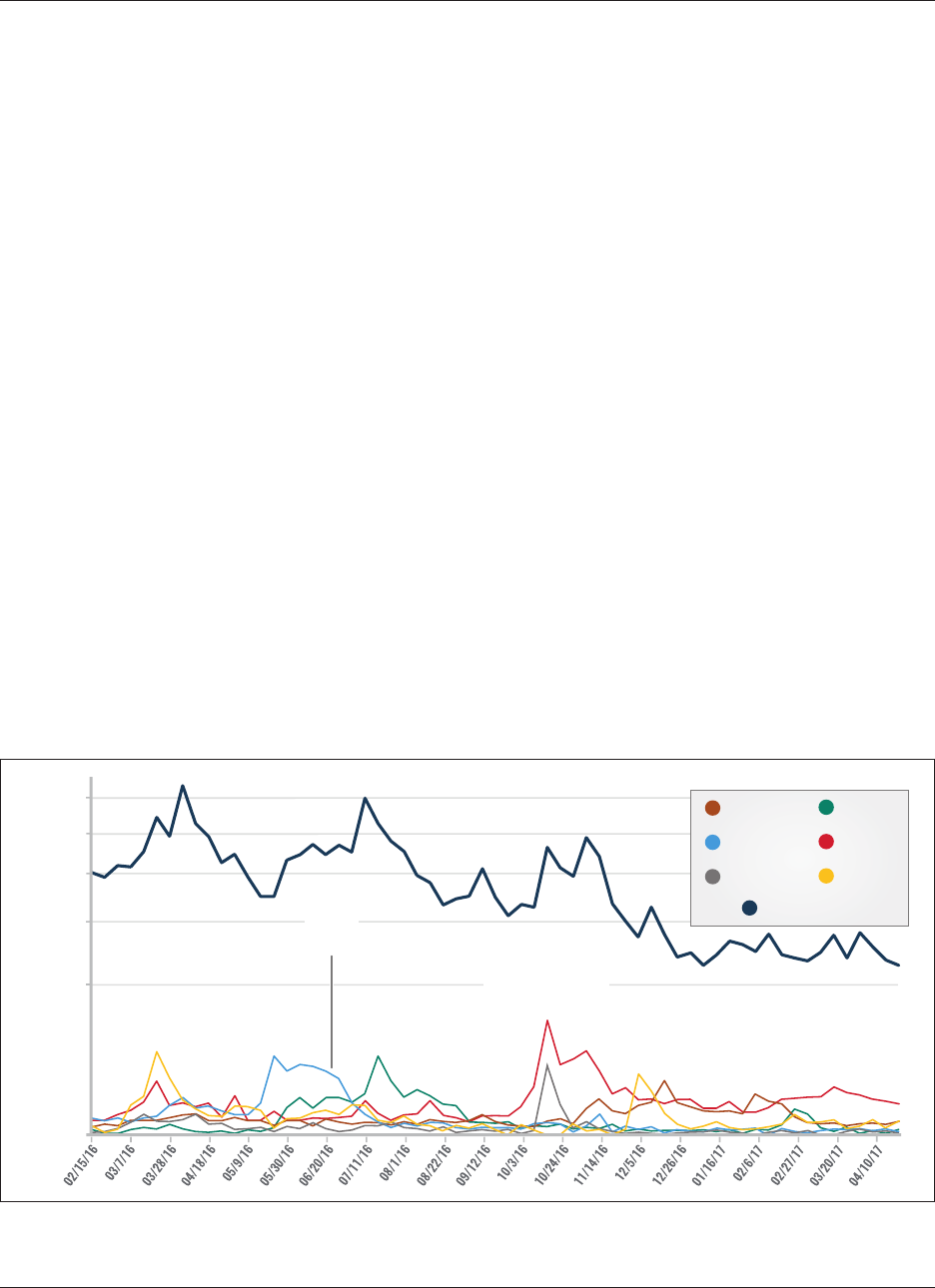
Digital Decay? • 25
Audrey Alexander
section uses content by English-language sympathizers on
Tw it te r to b et te r u nderst and how t h e g rou p’s a d he re nt s
in the West interact with issues like military engagement
and the ongoing battle over territory. As both official and
unofficial propaganda bridge the gap between the physical
and virtual theaters, it is necessary to probe the efficacy of
military-oriented media campaigns in engaging IS sym-
pathizers in the West. The proportion of content about
these matters is small, but it appears to be a noteworthy
measure of the overarching fight against IS online.
As examined in the background section of this report,
thematic research by Daniel Milton, Charlie Winter, and
Aaron Zelin identifies a notable shift in IS-central’s stra-
tegic communication efforts over time. Analyses by these
scholars, among others, are integrated throughout this
section to contextualize and cross examine key findings. In
Communication Breakdown, for example, Daniel Milton ob-
serves a shift away from central communications empha-
sizing governance, religion, and commerce, hypothesizing
that this change stems from IS’ “willing[ness] to sacrifice
these areas to maintain a focus on the military side of the
organization, at least in the production of media content.”
51
This shift in strategy can be used to unpack the nexus of IS’
central media strategy, military engagements, and English-
language contingent of sympathizers on Twitter.
For the sake of focus and clarity, the study selected a sample
of six critical battlefields
52
in Syria and Iraq that fell within
the time series for further examination. These fronts were
Palmyra, Fallujah, Manbij, Kirkuk, Mosul, and al-Bab.
53
Like any search terms in the report, it is hard to identify
every tweet discussing or alluding to each conflict zone;
English-language accounts also tweet veiled references to
military action without naming a specific campaign. Some
battles extend beyond the dates used in this study, such as
Mosul, and others overlap, like Fallujah and Manbij. These
events provide a ripe opportunity to explore the response
of English-language sympathizers over time (Figure 12).
Though confounding at times, particularly in the context
of IS’ media strategy, the data reveal a relationship between
military engagement and tweet frequency. Further evalua-
tion is required to parse out complexities and highlight the
overarching trends.
Manbij
Mosul
Palmyra
Bab
Fallujah
Kirkuk
Total Tweets
First Loss
of Palmyra
Iraqi Offensive
on Fallujah
Commences
IS Loses
Fallujah
Heavy
Fighting
for Manbij
IS Loses
Manbij
Iraqi Offensive on
Mosul Commences;
IS Attacks Kirkuk
IS Retakes
Palmyra
Second Loss of
Palmyra; IS
Loses al-Bab
25,000
20,000
15,000
10,000
5,000
0
Number of Tweets
(Figure 12) This graph shows how English-language IS sympathizers discuss key battles over time and contextualizes the
extent to which the topic relates to tweet frequency by week.
Tracking Military Engagements Over Time
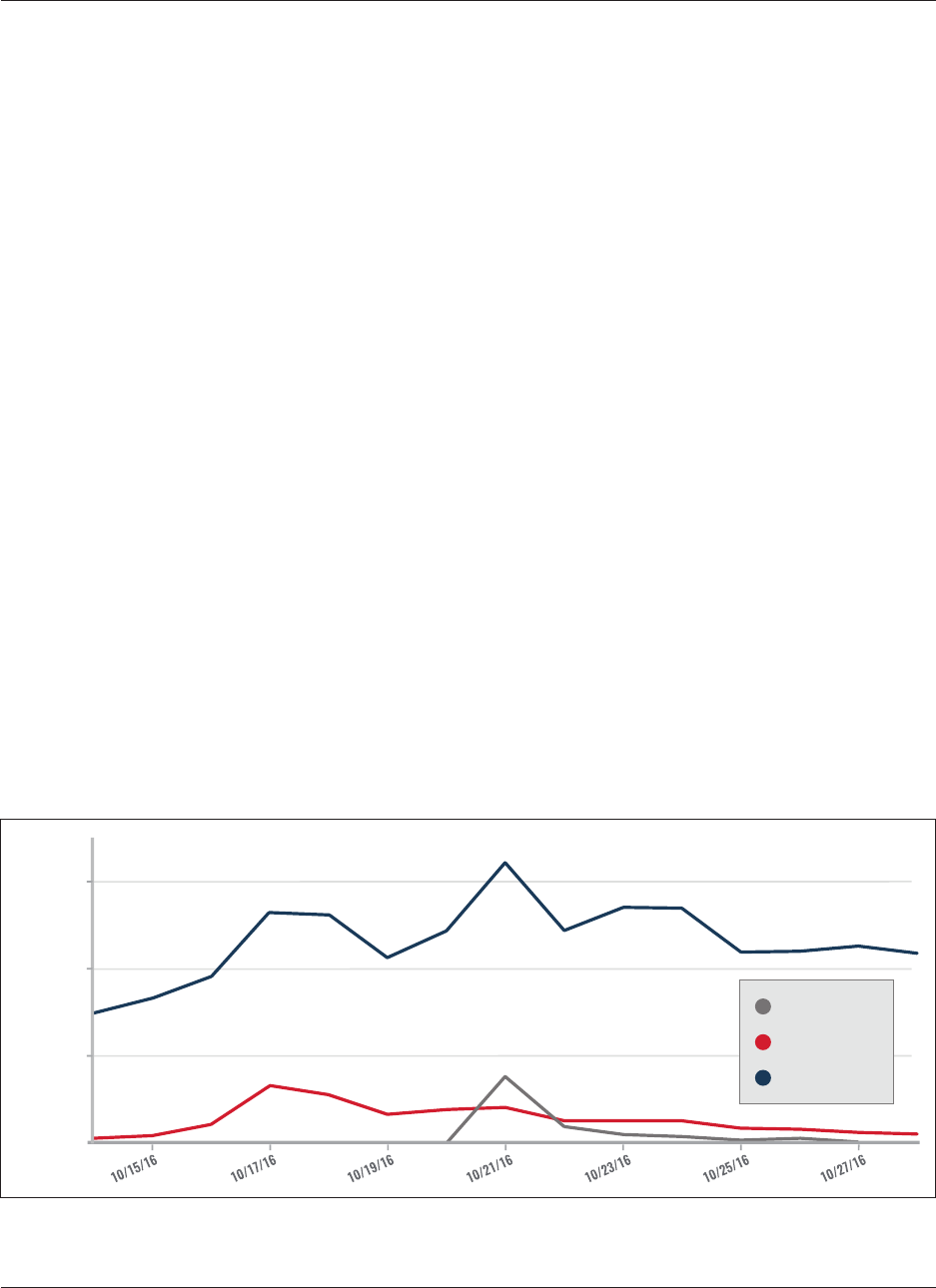
26 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
Fallujah and Manbij
Data on Fallujah and Manbij, two cities with chronologi-
cally overlapping battles during the spring and summer of
2016, reveal the importance of sustained messaging cam-
paigns in influencing English-language IS sympathizers. In
an initial review of the histogram, there is a stark differ-
ence in the rapid rise and slow decline in Twitter activity
pertaining to Fallujah (approximately May 22 to June 28,
2016) compared to the temporary hike in activity discuss-
ing Manbij (approximately May 31 to August 27, 2016). In
a series of tweets, Charlie Winter, one of the preeminent
researchers tracking IS’ strategic communications, notes
that central communications on Fallujah differ from fronts
like Manbij and Palmyra.
54
By way of contrast, Winter
identifies inconsistencies in IS-central’s media approach to
the battles, explaining that Fallujah was essentially “live-
blogged,” whereas Manbij received only “occasional men-
tions.”
55
Winter posits that differing media strategies relate
to the symbolic value of cities, likely dictating how the or-
ganization responds under duress.
56
When IS lost Fallujah around June 2016, there was a dis-
tinct military shift in focus from Fallujah to Manbij.
57
Given that the reported logics of IS-central’s media strate-
gy for battles in Fallujah and Manbij appear to be demon-
strated by thousands of tweets within PoE’s dataset, it
becomes apparent that the English-language sympathiz-
ers are somewhat subject to the tides of official IS agen-
da-setting in light of territorial shifts. This association
bears greater significance over time in the face of IS’ fal-
tering communications strategy.
Kirkuk and Mosul
In the wake of an IS initiative in Kirkuk (approximately
October 20 to 21, 2016)
58
and the concurrent start of the
Iraqi offensive to retake Mosul (October 16, 2016 - approxi-
mately July 20),
59
Twitter activity among English-language
IS sympathizers inadvertently veered from IS-central’s ef-
forts to control the broader narrative. In Kirkuk, IS mili-
tants launched a commando raid on less protected and less
critical targets.
60
Despite paling in comparison to other
operations, both in scale, efficacy, and duration, the attack
in Kirkuk received notable mention within the dataset.
ICSR’s Shiraz Maher notes that IS propaganda at this time
focused on Kirkuk, possibly in an effort “to pull focus away
from [IS] defeats in the heartland,” directing little attention
to the escalating conflict in Mosul.
61
In light of this exercise
of diversion, Winter observes a disproportion in strategic
output regarding Kirkuk and Mosul at a rate of four to one
on October 21, 2016.
62
Kirkuk
Mosul
Total Tweets
3,000
2,000
1,000
0
Number of Tweets
Two-Week Snapshot of Mosul and Kirkuk (October 14 to 28, 2016)

Digital Decay? • 27
Audrey Alexander
Upon further investigation, IS’ efforts to divert atten-
tion to Kirkuk were somewhat successful, yet most were
un-sustained (see Figure 13). English-language support-
ers mentioned Kirkuk more than Mosul on the date the
raid took place; afterward, Kirkuk-related content rapidly
disappeared. PoE findings suggest that a decline in terri-
tory aligns with a degradation in material referencing the
matter, particularly in the context of episodic propaganda
campaigns. In the histogram charting the broader data-
set, however, the rate at which sympathizers mentioned
Mosul far exceeds discussion of Kirkuk. In fact, out of all
six battles, Mosul received the greatest number of tweets
per week (see Figure 12); this is particularly noteworthy
given IS’ supposed efforts to divert attention from the
campaign. Between the dates of October 17 and 24, 2016,
a week including both engagements, tweets referencing
Mosul appeared about 63 percent more than those men-
tioning Kirkuk.
63
The dilemma IS faces in achieving their
propaganda aims plausibly pertains to limited resourc-
es, as well as external factors, including coverage from
Western mass media. This shows that IS-central’s efforts
to control the narrative are not bulletproof.
Mosul and al-Bab
Although the analysis already addressed English-language
IS sympathizers unrestrained response to Mosul over
Kirkuk, comparative analysis between discussions of the
Mosul and al-Bab campaigns highlights another emerg-
ing trend. The content produced by English-language
supporters during the battles of al-Bab (November 6, 2016
to February 23, 2017)
64
and Mosul (October 16, 2016 to ap-
proximately July 20, 2017)
65
demonstrates how protracted
struggles accompanied by thematic media campaigns draw
and sustain discussion over time. In a study on the propa-
ganda decline of IS spanning from January to February
2017, predominantly after IS’ initiative in Kirkuk, Winter
notes, “most of the propagandists’ attention was devoted
to depicting the Islamic State’s efforts to defend the Iraqi
city of Mosul, and the Syrian town of Bab, a trend that
is broadly consistent with the last few months.”
66
These
findings are manifested in the data, as media campaigns
for the respective battles garnered an increased level of
attention from English-language sympathizers.
Despite extended fighting and prolonged media strate-
gies in both of these cities, compared to the short burst in
Kirkuk, there was eventually a decline in tweets mention-
ing Mosul and al-Bab. This fall is likely due to material
losses, particularly in al-Bab, and further compounded by
the decrease in central media output. Degradation related
to the nexus of strategic communications and territory,
by way of military engagement, emerges in the data ex-
amined in this report. Furthermore, since the onset of
the battle of Mosul, some resurgences occur in the digital
sphere, but PoE’s findings reveal a stronger correlation
with external factors more than IS-central media output.
The U.S. presidential election and a coalition bombing
that killed up to 200 civilians in Mosul
67
correlated with
hikes in activity whereas prolific propaganda videos like
‘Tank Hunters,’ featuring John Cantlie
68
and the slick-
ly-produced ‘Knights of the Departments’ video
69
repre-
sented only a conservative increase in tweets.
Palmyra
Lastly, the multiple battles for Palmyra present another
marked shift over time among English-language sympa-
thizers on Twitter. Beginning in May 2015, prior to the
time series used in this study, the engagement contin-
ued until late March 2016, when IS lost Palmyra for the
first time.
70
The defeat drew the attention of sympathiz-
ers, peaking at 430 tweets mentioning the city the day
of March 27, 2016. In early December 2016, IS’ initiative
to re-take Palmyra resulted in a brief but substantial rise
in the number of tweets discussing the city (reaching its
height at 322 tweets on December 11, 2016). Exceeding
the rate of mentions for the concurrent battle of Mosul
for only ten days, Palmyra expectedly drew some atten-
tion because it symbolized an increasingly rare military
success for IS.
71
Ultimately, however, this uptick waned
due to a shift in attention towards Mosul, Al-Bab, and
even Aleppo, a conflict outside the scope of this analysis
that nonetheless has vital regional importance and drew
significant global media attention. IS lost Palmyra for the
second time around late February and early March 2017;
English-language supporters failed to mention this loss at
a meaningful rate.
72
In addition to search queries, the study also looked
at top hashtags to further gauge the extent to which
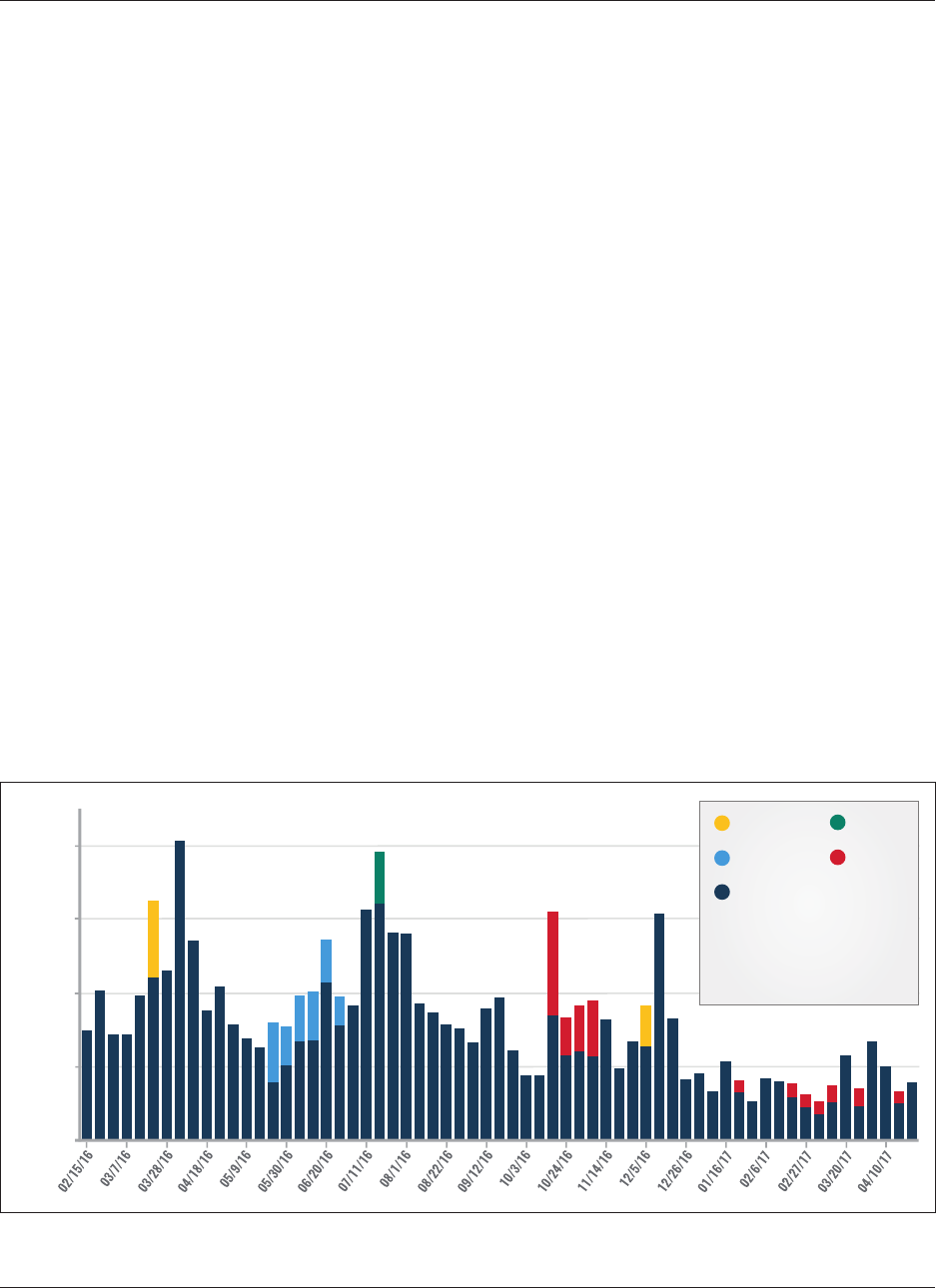
28 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
English-language IS sympathizers on Twitter remained
tapped into IS’ languishing efforts on the ground in Iraq
and Syria. As depicted in the graph below (Figure 14), four
of the six military engagements examined in this section
rank within the top three tweets per week at least once.
This pattern suggests that IS’ endeavors on the ground
are still a unifying priority among adherents on Twitter.
Mounting evidence suggests that IS’ strategic messaging
output is a noteworthy, but inconsistent component link-
ing English-language followers on Twitter to military en-
gagements in the region.
Paired with existing research on IS’ propaganda, partic-
ularly products geared towards Western audiences, the
data suggest that the group’s efforts to set the agenda
among English-language sympathizers on Twitter yield
mixed results. While protracted media campaigns at-
tract and sustain some conflict-related discourse, short-
lived messaging initiatives sometimes fail to divert
sympathizers’ focus in the desired direction. Additional
research is necessary, but this tendency might point to
a particular and perhaps growing cleavage between IS’
efforts on the ground and its base of English-language
supporters on Twitter.
Despite a numerical decline in tweets mentioning the
sample of six military engagements, the proportion of
content discussing military engagements stayed relatively
consistent throughout the dataset. Given the issues posed
by receding territory, namely fewer fronts for military en-
gagement, this finding is remarkable because it punctu-
ates the enduring relevance of fighting on the ground. A
leading factor in the sustained commentary on the battle
for Mosul by English-language sympathizers on Twitter
is likely the robust, thematic central media effort accom-
panying the ongoing campaign. Although the fight for
Raqqa began after the dates used in this study, it is crucial
to consider how multiple military fronts might hinder IS’
central messaging efforts by segmenting conflict-related
discourse among IS sympathizers on Twitter. Once IS in-
evitably loses military engagements in Raqqa, and even
Deir Ezzor, both strategically important cities, it is un-
clear what will take their place in the broader conversa-
tion among English-language IS sympathizers on Twitter.
Manbij
Mosul
Palmyra
Fallujah
Other Hashtags:
Syria, ISIS, Aleppo, IS,
Turkey, CloseIncirlik,
YPG, Hama, Assad,
Rohingya, DeirEzzor
4,000
3,000
2,000
0
Count of Hashtags
1,000
Top 3 Hashtags Per Week Highlighting Prevalence of Key Battles

Digital Decay? • 29
Audrey Alexander
2.2 How do terrorist attacks drive discourse among
English-language IS sympathizers on Twitter?
Though the majority of violent actions occur inside IS-
controlled territory, attacks perpetrated by actors outside
of the region are still critical to the organization’s efforts
worldwide. Research suggests that there is a link between
territorial losses on the ground in Iraq and Syria and an
increase in IS-related attacks outside of the territory con-
trolled by the group.
73
IS’ efforts to incite attacks abroad
is evident in the myriad of media products disseminat-
ed among supporters. The archetypal example of the call
comes from IS’ now-deceased spokesman Abu Mohammed
al-Adnani, who reportedly issued an audio statement be-
fore Ramadan in 2016, stating “Get prepared, be ready ...
to make it a month of calamity everywhere for the non-be-
lievers ... especially for the fighters and supporters of the ca-
liphate in Europe and America.”
74
Prolific English-language
propaganda, particularly and Rumiyah, parroted this
narrative.
75
Anecdotally, content by English-language sym-
pathizers rose in the immediate wake of terrorist attacks
with real or perceived links to the group. While some fol-
lowers opt to share press releases by IS-affiliated outlets
like Amaq News Agency, others praise the perpetrator(s)
and incite subsequent activity.
Upon initial analysis, there appears to be a correlation
between terrorist attacks and tweet frequency. In oth-
er words, the number of tweets per day (and sometimes
week) by English-language IS sympathizers on Twitter
rises after perpetrators with alleged links to the group
conduct attacks, particularly in the West. Consistent
with other findings in this report, such trends are nu-
anced and subject to change over time. This time series
encompasses a diverse number of plots with varying de-
grees of success, sophistication, and scale. Accompanied
by the broad range of targets, such considerations un-
doubtedly impact the online activity of sympathizers.
While striving to account for such variables, the fol-
lowing discussion faces limitations regarding compara-
tive analysis. Moreover, the specific sample of English-
language IS supporters on Twitter undoubtedly biases
discourse regarding attacks in the West.
For example, two separate IS-claimed terrorist at-
tacks within a month of each other might draw atten-
tion from English-language sympathizers on Twitter
for varying reasons. On June 13, 2016, Larossi Abballa
stabbed a French police commander and his partner
in Magnanville, France.
76
Though small in scope, the
significance of the attack stems from the perpetrator’s
target and supposed links to Rachid Kassim, a notori-
ous French IS recruiter.
77
By way of contrast, the July 1,
2016, attack in Dhaka, Bangladesh, might garner atten-
tion because of its complexity, including number of per-
petrators and sophisticated modes of operation which
included hostage-taking, bombing, and shooting.
78
These variants make it difficult to discern why and how
English-language supporters engage in discourse on
Tw it ter abou t ter ror ist att ac ks .
To better understand the relationship between IS-related
terrorist attacks and Twitter activity among sympathiz-
ers, the following analysis qualifies the trend and tests
for change over time. As discussed, IS-related perpetra-
tors conducted attacks in different countries around the
globe during this period. The following analysis focuses
predominantly on the effects of terrorist operations in
the U.S., Europe, Turkey, and Russia on Twitter activity.
Researchers chose these countries to narrow the scope of
discussion based on a data driven approach using relevant
search terms.
It is hard to glean the precise number of tweets about a
specific terrorist attack because accounts use different
terms to discuss the same event. For example, accounts
within the sample used the phrases “Pulse Nightclub
Attack,” “Pulse Nightclub Shooting,” “Orlando Nightclub
Shooting,” and “Orlando Attack,” in reference to the June
12, 2016, shooting by Omar Mateen.
79
The data show that
the traditional nomenclature for larger terrorist attacks
often reflects the city in which the attack occurred (see
‘Attack Nomenclature’ in the appendix for visual repre-
sentations of this phenomenon). Ultimately, this propen-
sity offers a baseline to compare tweet frequency in rela-
tion to various attacks.
After identifying eight large-scale attacks
80
in the U.S.,
Europe, Turkey, and Russia, the study queried and graphed
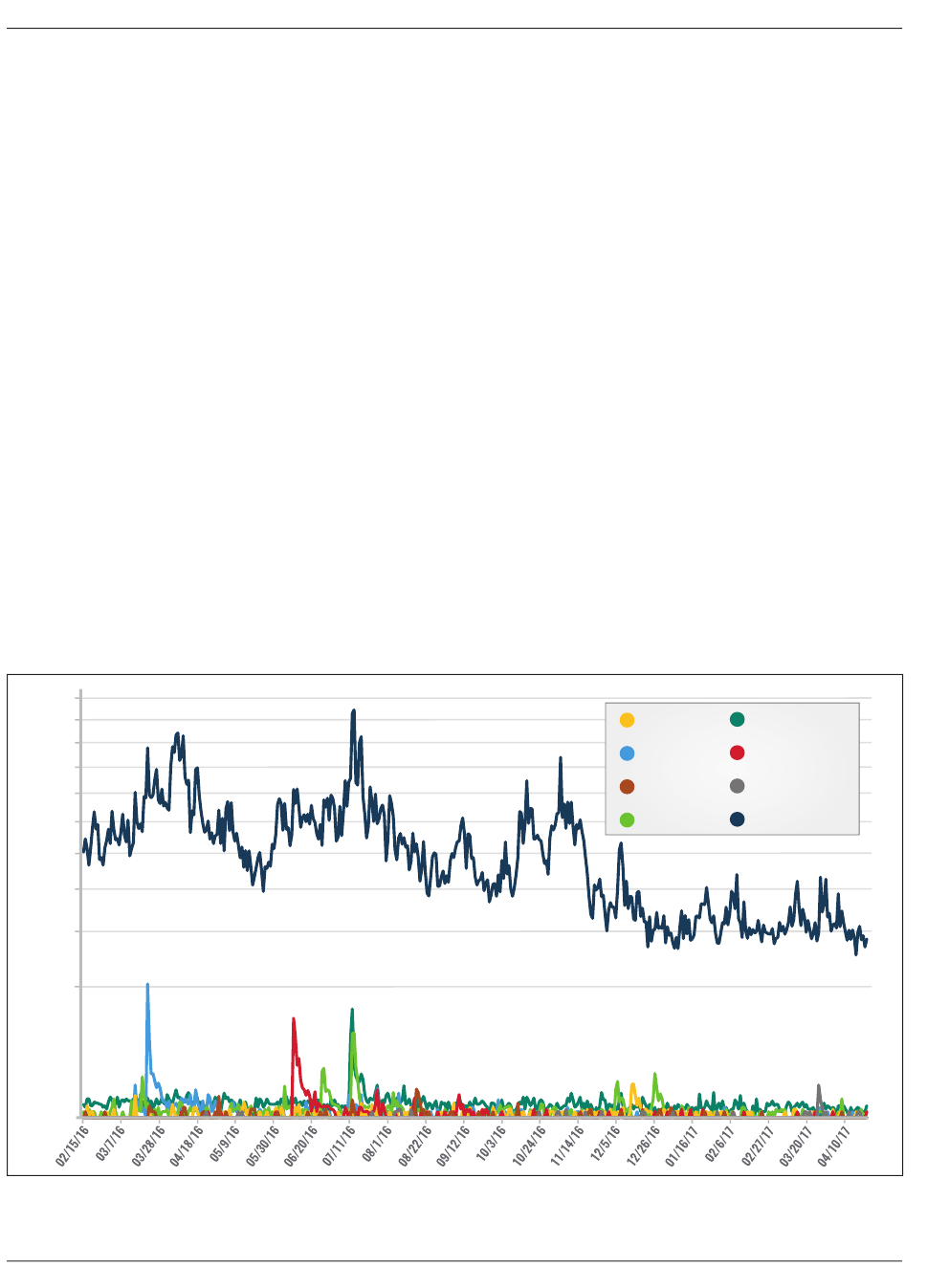
30 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
the corresponding seven cities to cross-examine the rela-
tionship between attacks and tweet frequency (see Figure
15). This list includes attacks in Brussels, Orlando, Nice,
Gaziantep, Berlin, St. Petersburg, and Istanbul.
81
As antic-
ipated, the data demonstrate a mostly positive relationship
between the tweet frequency and larger-scale terrorist at-
tacks in the U.S., Europe, Turkey, and Russia. Upon further
review, contributing factors such as lethality, complexity,
target, and operational links appear to be overwhelmingly
context dependent. In many instances, findings were coun-
terintuitive and lacked a common thread.
Brussels Bombings
As the first and most cited attack in the dataset, concur-
rent bombings in Brussels on March 22, 2016 provide a
sound opportunity for analysis.
82
Three assailants killed
32 people in the Brussels airport and Maalbeek metro.
83
Overall, there was a 25 percent hike in the total num-
ber of tweets on the day of the attack; this is the first
indicator that operations on Western targets positively
correlate with a broader rise in tweet frequency on the
day of attacks. Approximately 13 percent of tweets on
the day of the bombing overtly mentioned Brussels,
which suggests that an even larger percentage of tweets
discussed the attack using other terminology or veiled
references. Evidence shows that the effect of the bomb-
ing was short-lived as overarching tweet frequency fell
by approximately 24 percent the day after the attack;
this is supported by a sharp decline (approximately 66
percent) in the number of tweets mentioning Brussels
within the same timeframe.
These events likely drew unmatched attention on Twitter,
among other platforms, for several reasons. The attacks
occurred earlier in the study, when Twitter regulations
appeared to be less stringent. The bombings were also
sophisticated and coordinated by perpetrators with op-
erational connections to other IS operatives in Europe,
namely the 2015 Paris attackers.
84
Furthermore, in addi-
tion to the Amaq News Agency claim published the day
1,000
Number of Tweets About Attacks
1,500
500
2,000
2,500
3,000
3,500
4,000
4,500
5,000
0
Nice
Orlando
St. Petersburg
Total Tweets
Berlin
Brussels
Gaziantep
Istanbul
Tracing Attacks Over Time
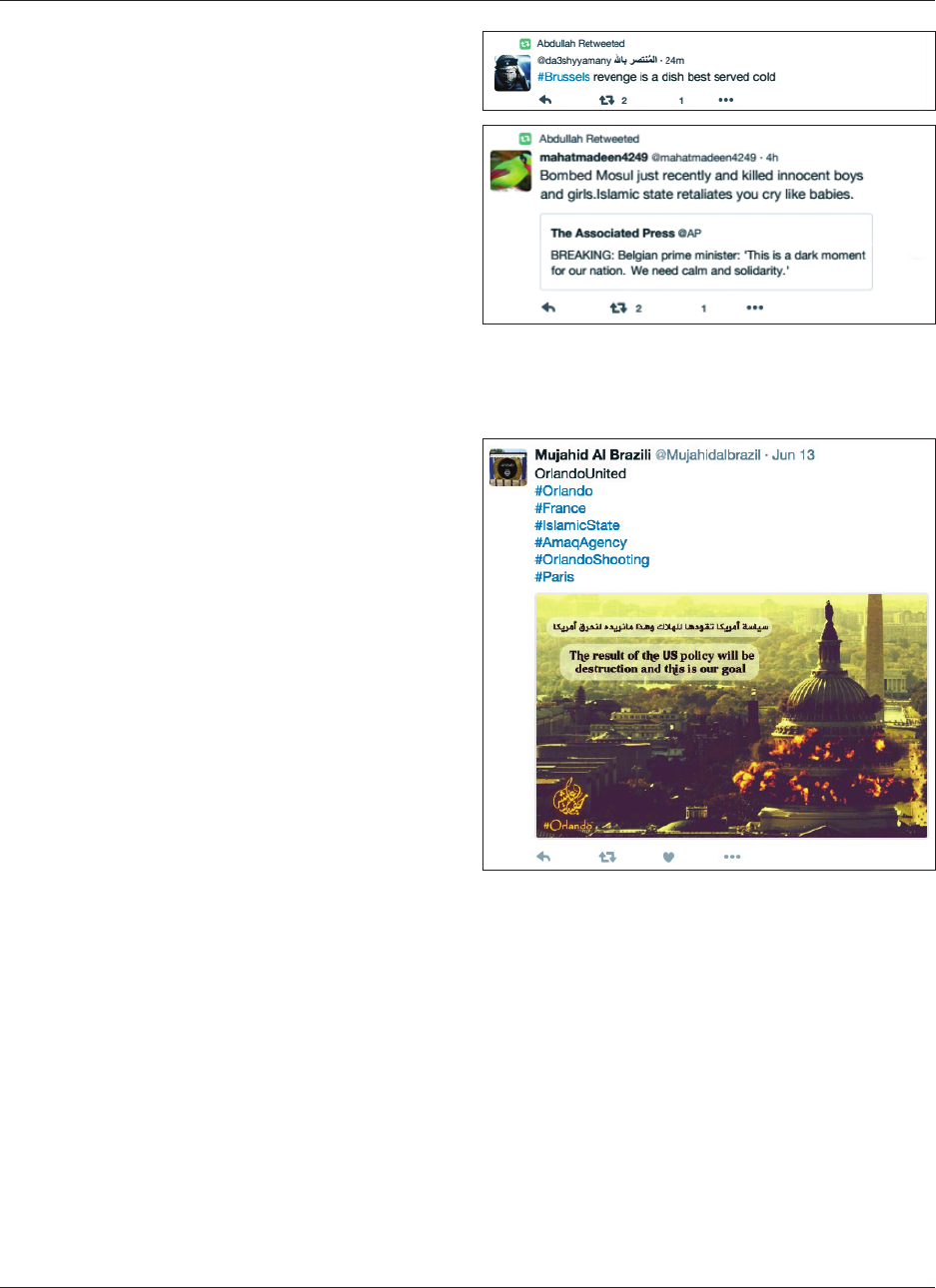
Digital Decay? • 31
Audrey Alexander
of the bombings, Belgium, and Brussels in particular,
received substantive coverage in official IS publications,
most notably the fourteenth issue of magazine. Such
attention suggests that the attack had enduring symbolic
value.
85
Regarding the Amaq Agency claim, it is crucial
to note that the narrative of revenge exemplified in the
Amaq News Agency press release was reflected in the
tweets of English-language sympathizers, illustrating
some semblance of congruity between top-down and
bottom-up campaigns.
Orlando Shooting
Close to three months later, Omar Mateen conducted the
Pulse Nightclub shooting in Orlando Florida, killing 49
in the early hours of June 12, 2016.
86
Despite yielding a
higher death toll, the Orlando attack drew less attention
than the Brussels bombing; while somewhat vexing,
this hints that there is not a direct relationship between
Tw it ter act iv it y a nd le tha lit y in t he contex t of ter ror ist
attacks. Instead, perhaps the lack of plot complexity in
Orlando compared to Brussels reduced the interest of
sympathizers online. Of the total number of tweets on
the day of the shooting, approximately 9 percent overt-
ly stated the city of Orlando.
87
Naturally, adherents may
have used terms other than ‘Orlando,’ as a 34 percent
rise in overall tweet frequency accompanied this event.
Although Amaq agency claimed some degree of affili-
ation to IS, the perpetrator himself, despite his oath of
fealty to al-Baghdadi during the attack, also previously
professed sympathy to Jabhat al-Nusra (now Jabhat Fateh
al-Sham) and even Hezbollah.
88
There is no obvious ev-
idence that Mateen’s murky allegiance to IS directly af-
fected the response of English-language sympathizers
on Twitter. Like Brussels, the attack in Orlando did not
sustain the uptick in tweet frequency over time. Even
so, a handful of IS-related media products mentioned the
attack, including the video by Wilayat al-Khayr called
“The Making of Illusion.”
89
Istanbul - Ataturk
Late in the evening on June 28, 2016, three gunmen
wearing explosive devices reportedly attacked the in-
ternational terminal at Ataturk Airport in Istanbul,
Tu rke y.
90
Although the assault was not claimed by any
group, including IS, officials questioned links to the or-
ganization as the mode of operation paralleled that of
the November 2015 Paris attacks. Unlike Brussels and
Orlando, the events in Istanbul did not correlate with an
increase in the total number of tweets that day; only 3
percent of tweets that day referenced Istanbul.
91
This rate
is notable given that the death toll falls between those of
Brussels and Orlando, further proving lethality does not
predictably influence the amount of content produced by

32 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
English-language sympathizers. Several factors, includ-
ing the non-Western geographic location of the attack
and the fact that IS media gave the attack scant publicity,
possibly impact this finding.
Nice Ramming
On July 14, 2016, Mohamed Lahouaiej-Bouhlel drove
a truck into the crowd celebrating Bastille Day in Nice,
France, killing 86.
92
Prior to the assault, jihadists and
counter-terrorism officials demonstrated an awareness of
the security challenges posed by this unsophisticated style
of attack.
93
Of the total number of tweets on the day of the
ramming, approximately 5 percent mentioned Nice.
94
One
caveat pertains to the inability of the search filter to dis-
tinguish the name of the city ‘Nice’ from the word ‘nice.’
95
Despite yielding the highest number of deaths in the sam-
ple, the rate for Nice falls behind attacks in Brussels (13
percent) and Orlando (9 percent), but ahead of those in
Istanbul at the Ataturk airport (3 percent). To some de-
gree, this sample, albeit small, shows a bias towards dis-
cussing violence directed at Western targets.
Anecdotally, it is hard to narrow the extent to which the
ramming influenced the broader tweet frequency within
this dataset because the attempted Turkish coup hijacked
the attention of English-language IS sympathizers the fol-
lowing day. This point is exemplified by the overlapping
rise in tweets mentioning Istanbul. As discussed earlier, five
of the top ten hashtags on July 15, 2016, related to Turkey
or the failed coup itself. This demonstrates the extent to
which other political events may seize the narrative among
IS followers in the wake of a ramming. On July 16, 2016,
more than 24 hours after the assault, Amaq News Agency
claimed responsibility for the attack, but this had no effect
in reviving the declining discussion of the operation.
96
Months later, English-language IS-propaganda, including
the January 2017 issue of Rumiyah, praised the Nice ram-
ming while inciting attacks in the West.
97
By revisiting the
attack months after the event, IS demonstrates a propensity
for eulogizing operations against Western targets in pro-
paganda geared towards English-language sympathizers.
In this capacity, IS media output acts as conduit between
operations outside IS-controlled territory and the grassroot
engagements on Twitter.
Gaziantep
Over a month after the ramming in Nice, a suicide
bomber targeted a wedding in Gaziantep, Turkey;
mixed reports suggest the attack killed over 50 people.
98
Despite becoming the second-most lethal attack in the
sample, the data suggest the event drew little atten-
tion from English-language IS sympathizers numeri-
cally or proportionally. Again, this probably relates to
the non-Western location of the assault. Gaziantep was
referenced in barely over 1 percent of the tweets on the
day of the bombings.
99
Although there was no official
claim from IS, President Erdogan reportedly believed
the group conducted the attack.
100
Berlin Ramming
On December 19, 2016, Anis Amri reportedly drove a
truck into a Berlin Christmas market, killing 12.
101
The
ramming was correlated with a temporary increase
in tweet frequency, like other attacks in the West.
Approximately 2 percent of the total number of tweets
on the day of the ramming overtly referenced Berlin.
102
The following day, with the perpetrator on the run,
Amaq News Agency issued a press release claiming affil-
iation.
103
Much like the slightly-delayed announcement
following the Bastille Day ramming in Nice, Amaq’s
claim had little effect on the dwindling discussion of
the attack in Berlin. While less lethal, Berlin received
numerically and proportionally more attention than the
bombing in Gaziantep. Even so, the Berlin ramming
drew few mentions from English-language sympathiz-
ers compared to other attacks on Western targets. As
this was later in the dataset, Twitter’s policy may have
curbed the rallying effect among adherents in the imme-
diate wake of terrorist attacks.
Istanbul - Nightclub
In the early hours of January 1, 2017, one gunman assaulted
the Reina nightclub in Istanbul, Turkey, reportedly killing
39.
104
Shortly thereafter, IS claimed responsibility through
its mouthpiece, Amaq News Agency.
105
Around 5 percent
of tweets on the day of the bombing mentioned Istanbul.
106
This finding initially complicates the assertion that
Wester n targets ga rner more at tention, since the n ightclub
shooting in Istanbul drew proportionally more discussion

Digital Decay? • 33
Audrey Alexander
than the Berlin Christmas market ramming (by 3 percent).
Nonetheless, a range of factors, including scale and symbol-
ic timing, may affect supporters’ rate of engagement. Such
metrics are undoubtedly shaped by the narrow scope of the
sample of English-language IS sympathizers.
Comparing the Istanbul nightclub attack to the previous
Ataturk Airport attack allows one to test decline over
time. Furthermore, because the operations produced
a similar number of fatalities (Ataturk International
Airport, over 40; Reina nightclub, 39), there is a control
on the effects this might have, although evidence sug-
gests the effects are limited. Broadly speaking, there is
a severe decrease in the total number of tweets on the
respective dates of the attacks.
107
However, a roughly
proportional number of tweets (3 percent and 5 percent),
mentioned Istanbul overtly on the day of each attack.
These rates are strikingly low considering IS’ continued
effort to discuss terrorist assaults in Turkey in official
media products.
108
St.Petersburg Metro Bombing
On April 3, 2017, a suicide bomber reportedly attacked a
Metro train station in St. Petersburg, Russia, killing at
least 14.
109
After the attack, terrorism analysts noted that
the event was unclaimed by IS.
110
The 3 percent of tweets
referencing ‘Petersburg’ (the simplified search term used
for St. Petersburg) on the day of the attack is notable, but
offers limited insight, as it is the only event in Russia
within the sample.
111
It appears to align with the broader
trend of decline in terrorism-related discussion over time.
Another consideration is the attack’s non-Western target,
which translates to less attention in some instances with-
in this dataset.
Concluding Observations
After considering the influence of many variables on the
mobilization of English-language IS sympathizers, the
effects of terrorist attacks appear largely unpredictable.
Counterintuitively, no single element of an operation
drives the discussion in the data: these factors include plot
sophistication, mode of operation, number of perpetra-
tors, lethality, link to IS, or claim of affiliation. Though
there are anomalies, as attacks on Western targets tend to
garner more attention than their counterparts in Turkey
and Russia. Of course, this sample only scratches the sur-
face of the issue, and further examination is required be-
cause of the samples bias towards matters pertaining to
Western audiences.
Despite the overarching volatility of English-language
sympathizers’ response to terrorist attacks, there are
substantive shifts in tweet frequency and proportion of
content directed towards the respective cities targeted by
terrorists. With the exception of the Ataturk bombing in
Istanbul, assaults occurring in the first half of the data-
set, including Brussels, Orlando, Nice, and Gaziantep, are
positively correlated with a rise in tweet frequency on the
day of the attack. Those in the latter half of the dataset,
including Istanbul (Reina nightclub), St. Petersburg, and
Berlin have a weaker, and sometimes negative relation-
ship with tweet frequency.
Despite the study’s attempts to select and analyze a man-
ageable sample of attacks, this approach is imperfect, as
the events are not entirely comparable due to a range of
influential variables. Ultimately, however, the data reveal
an underlying tendency for English-language IS support-
ers to direct more attention to Western attacks.
From the sample of incidents selected, tweets referenc-
ing the cities in which the attacks occurred declined
(Figure 18) This tweet typies
conventional discourse in the
wake of terrorist attacks that
integrates a broader discussion
on political events and foreign
policy in particular.
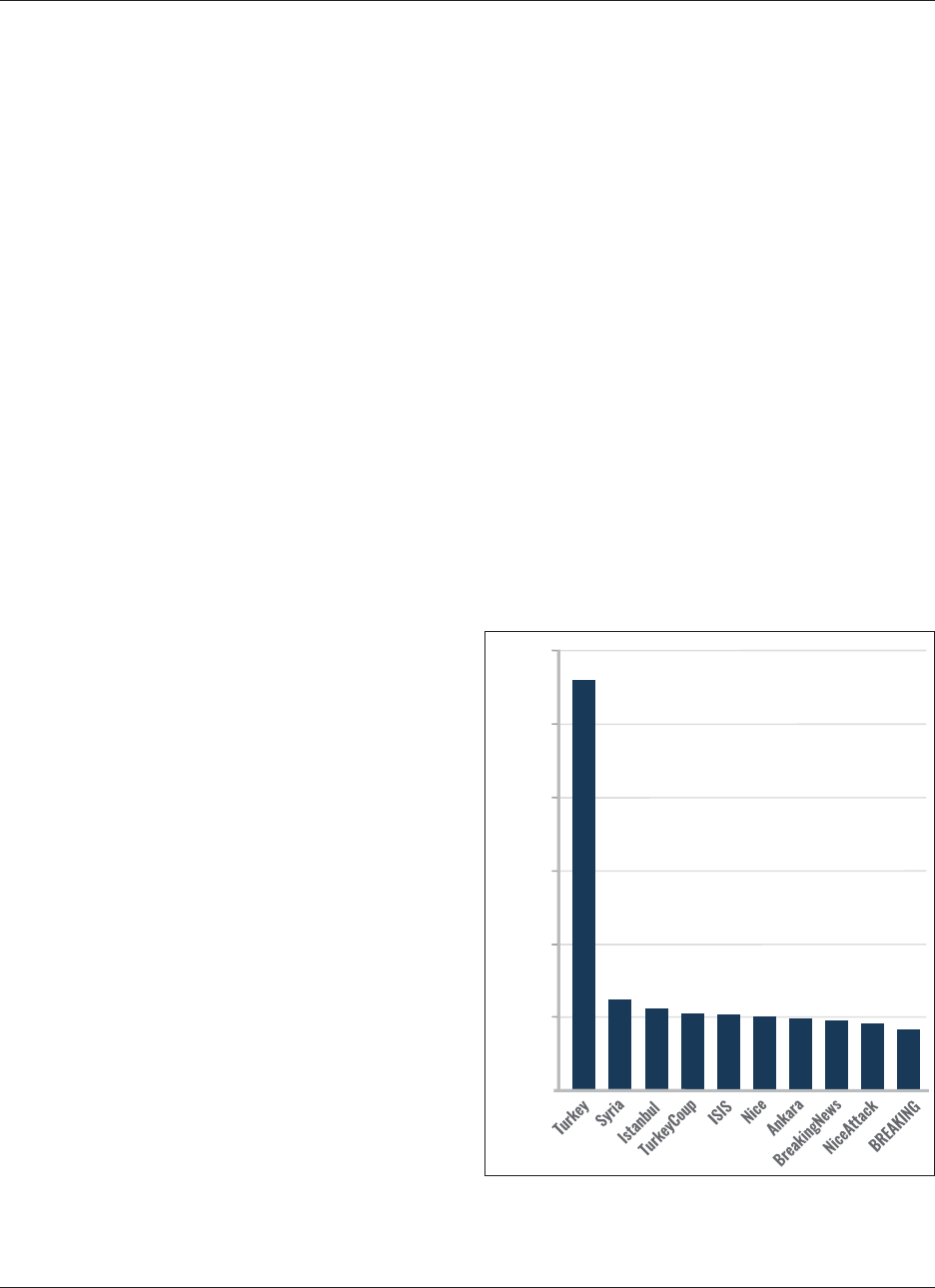
34 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
in absolute number and in proportion to the broader
conversation over time. The day events unfold, terror-
ist activity in the West appears to stimulate a broader
political dialogue on Twitter than attacks elsewhere.
Based on anecdotal observations of concurrent proj-
ects tracking IS’ use of other social media platforms,
including applications with encryption technology, this
analysis uncovers a diffuse rise in event-related content
in the wake of an attack. Despite publicity and main-
stream media attention, terrorist violence outside IS-
held territory occupies a small portion of the discussion
among English-language IS sympathizers on Twitter. To
emphasize this point, hashtags regarding a terrorist at-
tack never rank within the top five hashtags per week.
Ultimately, the effects of terrorist attacks in driving dis-
cussion on Twitter are sometimes influential, but always
un-sustained in this dataset. This finding is particularly
damning to an organization that relies on terrorism as a
tactic to advance its objectives.
2.3 How do current events inuence the activity of
English-language IS sympathizers on Twitter?
Amidst the broader decline over time, spikes throughout
this dataset reveal a notable fluctuation in the rate of ac-
tivity on Twitter by English-language IS sympathizers.
These shifts are visible in graphs tracing the frequency
per week, and even more striking from day to day. It is
crucial to identify which current events influence Twitter
activity by English-language supporters because the glob-
al base of IS adherents are subject to the changing tides
of the real world. Within this context, it is instructive to
observe the tendency for this demographic to depart from
the narrative and agenda set by IS-central. Moreover,
much like English-language sympathizers’ predisposition
towards Western attacks, it is crucial to consider how the
scope of the study influences findings.
Some influential events cover only a concentrated peri-
od of time, over a matter of hours or days, while others
span across longer durations. The July 15, 2016, failed
coup d’état in Turkey, for example, attracted significant
attention in a short timeframe.
112
In fact, the day of the
coup attempt contained the second highest number of
tweets per day in the entire dataset (4,613 tweets).
113
This
episode is particularly interesting, considering the ob-
servation that thematic English-language publications
like and Rumiyah do not prioritize the attempted
coup in their discussion of Erdogan and Turkey. In this
context, sympathizers’ interest in current events dras-
tically deviates from the overarching agenda set by IS
propaganda. It is hard to prove a direct link in the spike
in tweet frequency and the attempted Turkish coup as
multiple factors could contribute to this uptick includ-
ing the Bastille day terrorist attack in France the day
before. Even so, metrics like top hashtag help test for a
causal link. Within the 48-hours timespan between the
day of the event and the day after, four of the top ten
tweets clearly pertained to Turkey and “#Turkey” was
the most used hashtag (see Figure 19). This uptick still
had limited effects in driving the conversation over a
sustained period.
1,200
1,000
800
600
400
200
0
Count of Hashtags
Top 10 Hashtags on July 15 and July 16, 2016
(Figure 19) Of the top ten hashtags that were used by
English-language IS sympathizers on Twitter the day of and
after the attempted coups in Turkey, four pertained to Turkey.
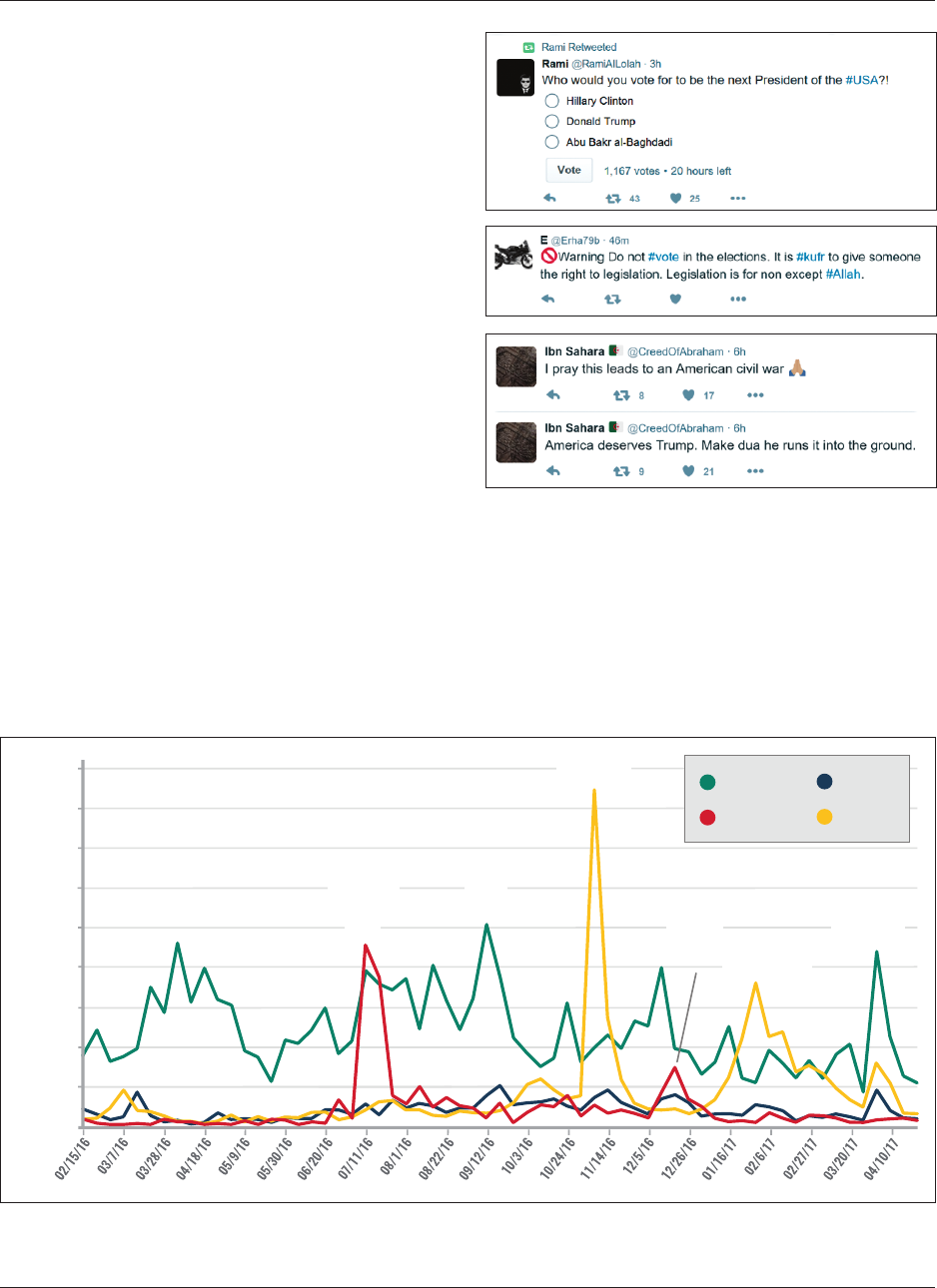
Digital Decay? • 35
Audrey Alexander
The 2016 presidential election in the U.S. also received
significant attention from supporters within the time
series (see Figure 20). Leading up to November 8, 2016,
accounts disseminated a wealth of tweets critiquing the
candidates, their policies, and the democratic process writ
large. Generally, IS-central English-language propaganda
dedicated scant commentary on the electoral proceedings.
On Twitter, however, despite ruminations on the subject
for months, activity culminated between election day
and the release of the results confirming the election of
then-candidate Donald Trump (November 8 and 9). This
48-hour period contained 6,289 tweets, an unusual spike
in the midst of otherwise dwindling activity. During this
time, Twitter activity by sympathizers rose then fell as
voters cast ballots and polling stations closed; the rate be-
gan to climb again as officials announced results.
In an effort to grasp IS sympathizers’ propensity to dwell
on matters that pertain to their adversaries, the investi-
gation graphed tweets mentioning four state leaders over
time: Assad, Trump, Putin, Erdogan (see Figure 21).
114
The decision to select these individuals stemmed from an
initial survey of the dataset. Though imperfect, as veiled
(Figure 20) Tweets demonstrating content by English-
language sympathizers on Twitter between November 8
and 9, 2016.
Putin
Trump
Assad
Erdogan
Syria Chemical
Attack; US
Missile Strikes
1,800
1,600
1,400
1,000
200
0
Number of Tweets
400
600
800
1,200
Trump’s
“Muslim Ban”
Russian
Ambassador
Killed in
Turkey
US Election
Syrian
Ceasefire
Attempted
Turkish
Coup
(Figure 21) This annotated graph traces the number of tweets referencing Assad, Erdogan, Putin, and Trump over time
and highlights some relevant current events.
Tweet Referencing Anti-IS State Leaders
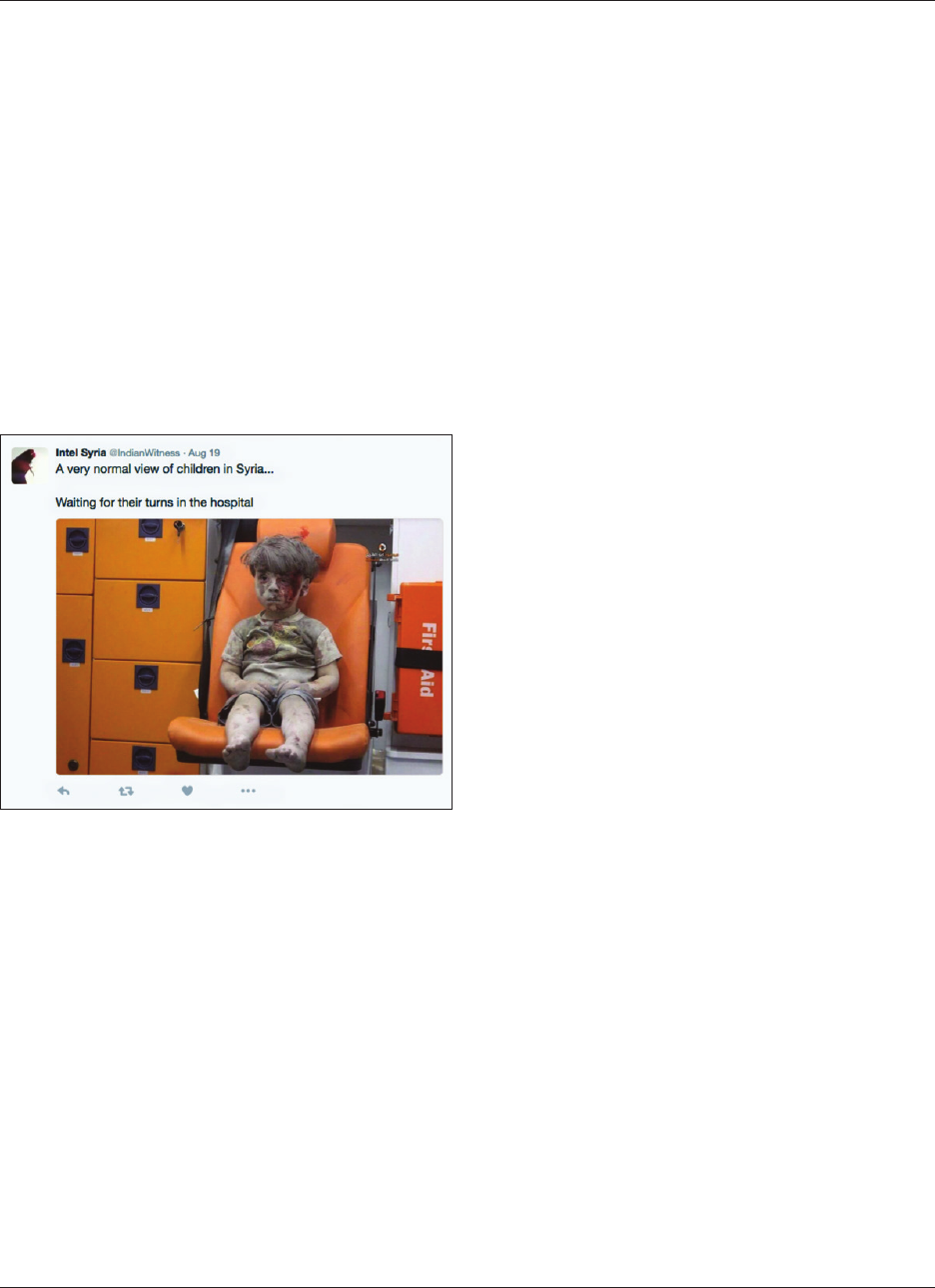
36 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
references are hard to detect with basic search filters,
this sample sufficiently streamlines the multiple political
events that states and their respective leaders experienced
during the time series. While mentions of these politi-
cians independently ebb and flow throughout the dataset,
concurrent rises are often indicative of events that affect
the various parties.
As anticipated, Syrian President Bashar al-Assad received
substantially more attention and sustained commentary
than his counterparts in the U.S., Turkey, and Russia.
This finding is unsurprising due to his relevance in the
conflict, and enduring presence in official IS propaganda.
Throughout the time series, sympathizers overtly refer-
enced Assad in 30,351 tweets; the greatest spike in tweet
frequency per week occurred the week of September 12,
2016, during the nationwide ceasefire in Syria.
115
Upon
further analysis, it is crucial to note that the highest num-
ber of tweets per day mentioning the Syrian president
transpired in the wake of well-publicized attacks on ci-
vilians. On August 18, 2016, an early spike in the dataset,
footage emerged showing rescue workers care for Omran
Daqneesh, a boy pulled from the rubble of his home after
surviving a regime airstrike in Aleppo (see Figure 22).
116
On the day of April 4, 2017, references to Assad temporar-
ily climbed after a chemical attack in the rebel-held town
of Khan Sheikhoun in Northwestern Syria.
117
As demon-
strated in the graph, this rise converges with increased
references to Trump and Putin: leaders with controversial
relations to the event.
The second most mentioned state leader was U.S.
President Donald Trump (10,587 tweets). Like Assad,
Trump gained traction among English-language sympa-
thizers after a chemical attack in Syria; in retaliation,
Trump reportedly authorized a missile strike on Syria’s
Al Shayrat airbase on April 6, 2017.
118
Before this event,
Trump received substantial attention on two occasions:
his election, and the announcement of a policy re-
stricting travel from select Muslim-majority countries.
Having already discussed a dramatic rise in activity in
the 48-hour period around the election, it is crucial to
highlight a shift in the discourse surrounding Trump’s
‘travel ban’ on January 27, 2017.
119
During the week of
January 23, 2017, ‘#MuslimBan’ ranked among the top
ten hashtags used by English-language adherents on
Tw it ter. Fur t her more, the sheer nu mber of t weet s men-
tioning Trump by name rose over 198 percent in the span
of three days after the release of the executive order.
These findings are particularly fascinating in light of
IS’ reportedly deliberate exclusion of Donald Trump in
official propaganda.
120
On a grassroots level, content by
English-language IS sympathizers diverges from this
strategy with frequent mentions of Trump. This in-
dicates a lack of cohesion between official propaganda
disseminators in IS-controlled territory and its base of
adherents in the West. Though not overtly problem-
atic, as IS followers opportunistically validated the
narrative of persecution using Trump’s rhetoric, this
disjunction is one of the many symbols of deterioration
in the digital sphere.
Despite the geopolitical significance of Turkey for IS, its
President, Recep Tayyip Erdogan, receives sporadic at-
tention from English-language IS followers on Twitter
(5,542 mentions in total). This observation is striking due
to the consistency with which official propaganda tar-
geting Western audiences mentions Erdogan. Aside from

Digital Decay? • 37
Audrey Alexander
the aforementioned Turkish coup attempt, which gener-
ated considerable activity, the only other notable spike in
activity arose from the assassination of Andrey Karlov,
the Russian Ambassador to Turkey in December 2016.
121
Although the gunman’s precise allegiances remain un-
clear, reports suggested that various jihadist circles lauded
the attack.
122
According to this dataset, so too did English-
language IS sympathizers on Twitter. Lastly, as opposed
to their interest in the U.S. election, this demographic
gave little attention to the April 2017 constitutional ref-
erendum in Turkey.
Though slightly confounding, given Vladimir Putin’s
prominence in English-language IS propaganda, the
Russian President is mentioned overtly in only 5,256
tweets throughout the tested timeframe. The high-
est peak in Putin-related discussion occurred during
the week of the Russian elections in September 2016.
However, this flux is arguably driven by proximally pre-
ceding events including the Syrian ceasefire, Trump’s
well-publicized praise of Putin during the U.S. presiden-
tial election, and Putin’s meeting with Obama during the
G-20 Summit.
123
The second, and perhaps most inter-
esting upsurge in tweets citing Putin, emerged around
the aforementioned chemical attack in Syria, which oc-
curred the day after a bombing in St. Petersburg, Russia.
The compounding effects of these events led to a 455 per-
cent hike in the number of Putin-related tweets during
the week of April 3, 2017, compared to the week before.
Providing more evidence of IS’ lack of control over po-
litical narratives, it is useful to highlight the disconnect
between IS’ efforts to discuss Putin in English-language
propaganda compared to the lack of content mentioning
the politician on Twitter. A similar disconnect exists in
discourse surrounding Trump, and still, substantive ev-
idence of decay in the digital sphere.
Like other socio-political spheres on Twitter, IS sym-
pathizers rally around incidents that are relevant to the
group’s base of supporters. Admittedly, however, some of
the greatest hikes in activity are correlated with events
IS cannot assert control over. This inability to dictate
the outcome of current events is often two-pronged,
manifesting both online and offline. The reopening
of Incirlik Air Base to American forces offers a useful
example of this phenomenon. After the July 2016 coup
attempt in Turkey, the Turkish government allowed
the U.S. to resume missions from Incirlik Air Base af-
ter a temporary shutdown.
124
Incirlik is significant to
IS because it houses critical infrastructure to the U.S.’s
military efforts against fighters on the ground in Iraq
and Syria.
125
On Twitter, English-language IS followers
rally without direction from IS-central in response to
this event, as ‘#CloseIncirlik’ became the most popular
hashtag during the week of July 18, 2016. Unexpectedly,
this hashtag outshines every other top hashtag per week
across the entire time series (see Figure 24). This vexing
observation might reveal the efficacy of organic, bot-
tom-up mobilization or point to the influence of oth-
er external factors. Either way, such findings hint at a
dissonance between IS-central’s messaging efforts for
Western audiences and the rallying cries of English-
language sympathizers on Twitter.
(Figure 23) This screenshot shows how accounts discuss
various state leaders, sometimes mentioning more than
one in the same tweet.
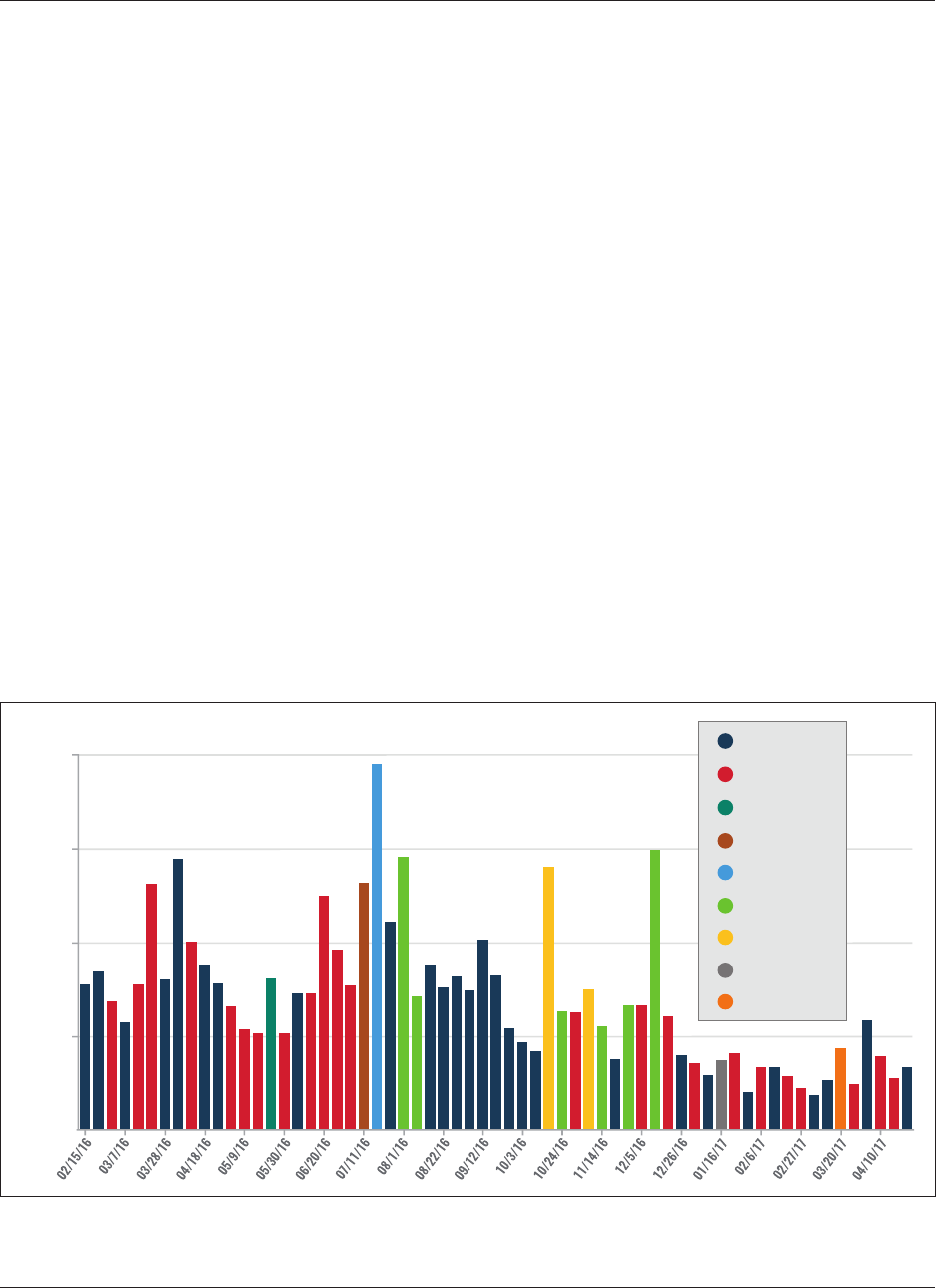
38 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
This section cannot provide an exhaustive analysis of
the range of global political events that drive the con-
versation online. Anecdotally, however, these matters
often fall into two camps: those concerning the global
Muslim community, and those regarding the group’s
adversaries. While this analysis focuses predominantly
on the latter, it is crucial to note supporters’ ongoing
engagement with events around the world, especially in
the Middle East, Africa, and Asia. The perceived and
experienced persecution of Muslim communities, like
the Rohingya in Myanmar, receive considerable atten-
tion from the broader base of English-language IS sym-
pathizers.
126
During the week of November 21, 2016,
for example, “#Rohingya” ranks within the top three
hashtags used by adherents.
In short, some notable current events drive tweet fre-
quency and discussion among English-language IS com-
munity on Twitter. Although a direct relationship be-
tween major political events and an increase in tweet
frequency is nonexistent, a broad swathe of occur-
rences concern this demographic. While some events
draw adherents in droves, others garner less attention.
Though difficult to measure, the aggregation of politi-
cal discussion accounts for the largest segment of con-
tent produced by English-language IS sympathizers on
Tw it ter. No ev idence suggest s t his d ia lo gue i s n ar row-
ing in the face of more stringent efforts to silence the
movement. While relevant tweets have declined in ab-
solute terms, like overall tweet frequency, the relative
proportion of political discourse remains substantial.
Notes
1. Like geolocation, most accounts to not specify a time zone
setting.
2. For example, and a notable segment of tweets use Somali,
a language that is not supported by Twitter. “Twitter for
Websites Supported Languages — Twitter Developers.” 2017.
https://dev.twitter.com/web/overview/languages.
3. A derogatory term used by extremists to describe moderate
Muslims. For more information, see: Bhogal, Gurwinder.
2017. “How Terrorists Are Creating a New Language.”
Medium. July 28. https://medium.com/@G_S_Bhogal/
how-terrorists-are-creating-a-new-language-595646a6e76d.
0
Syria
ISIS
Fallujah
Turkey
CloseIncirlik
Aleppo
Mosul
DeirEzzor
Hama
500
1,000
1,500
2,000
Count of Top Hashtag
Top Hashtag Per Week

Digital Decay? • 39
Audrey Alexander
4. Part of IS’ Arabic slogan “,” which means
“remaining and expanding.” For more information, see: Zelin,
Aaron. 2015. “The Islamic State’s Model.” The Washington
January
28. http://www.washingtoninstitute.org/policy-analysis/
view/the-islamic-states-model.
5. At its height during the week of April 4, 2016, this stream of IS
sympathizers shared 26,733 tweets. Conversely, the enduring
network of sympathizers reached its lowest point about a year
later during the week of April 24, 2017, producing 6,298 tweets.
6. Fisher, Ali. 2016. “Interpreting Data About ISIS Online | USC
Center on Public Diplomacy.” Center on Public Diplomacy
Blog. October 6. https://uscpublicdiplomacy.org/blog/
interpreting-data-about-isis-online.
7. “Government TOS Reports - July to December 2016.” 2017.
https://transparency.twitter.com/en/gov-tos-reports.html.
8. “Combating Violent Extremism.” 2016. Twit ter
Blogs. February 5. https://blog.twitter.com/2016/
combating-violent-extremism.
9. According to an official blog post, Twitter “suspended over
125,000 accounts for threatening or promoting terrorist
acts” from mid-2015 to February 5, 2016, prior to the dates
used in this study. “Combating Violent Extremism.” 2016.
Twit ter Bl ogs. February 5. https://blog.twitter.com/2016/
combating-violent-extremism. A subsequent update by Twitter’s
public policy team said the company shut down an additional
235,000 accounts between February 5 and August 18, 2016.
“An Update on Our Effort s to C ombat Violent E xtrem ism.”
2016. Twit te r Bl og s. August 18. https://blog.twitter.com/2016/
an-update-on-our-efforts-to-combat-violent-extremism. The
company’s tenth #Transparency Report notes that “During the
reporting period of July 1, 2016 through December 31, 2016, a
total of 376,890 accounts were suspended for violations related
to promotion of terrorism.” “Government TOS Reports - July
to December 2016.” 2017. https://transparency.twitter.com/en/
gov-tos-reports.html.
10. The suspension of 235,000 accounts between February 5 and
August 18, 2016 amounts to a rate of about 1,205 accounts per
day. The suspension of 376,890 accounts between July 1 and
December 31, 2016 amounts to a rate of about 2,060 accounts
per day. In other words, various figures from 2016 show a 71
percent increase in the average number of accounts suspended
per day for terrorism related activity. Though imperfect, as
the dates overlap and Twitter’s suspension rates likely vary
from day to day, these figures are important because they
support the claim that Twitter is increasing efforts to suspend
accounts that threaten or promote terrorist attacks.
11. In this context, suspension is operationalized as a status
change from active to inactive as per the API.
12. SFM pulls from a dynamic list of accounts that changes from
week to week based on input and concurrent suspension.
13. Additionally, PoE researchers on Telegram have observed
instances where IS supporters encouraged others to build a
followership on broad-based platforms with innocuous activ-
ity, followed by an subtle escalation in extremist content. This
could be another explanation for long-lasting accounts.
14. @erhabi35, @erhabi365, @erhabi37, and @Erhabi39.
15. Amarasingam, Amarnath. 2015. “What Twitter Really Means
for Islamic State Supporters.” War on the Rocks. December 30.
https://warontherocks.com/2015/12/what-twitter-really-
means-for-islamic-state-supporters/.
16. Vidino, Lorenzo, and Seamus Hughes. 2015. “ISIS in America:
From Retweets to Raqqa.” The GW Program on Extremism.
p.24; Amarasingam, Amarnath. 2015. “What Twitter Really
Means for Islamic State Supporters.” War on t he Ro cks. December
30. https://warontherocks.com/2015/12/what-twitter-really-
means-for-islamic-state-supporters/.
17. The maximum value for each segment extends far beyond 600,
which is why they are not included on this chart.
18. Berger, J.M., and Heather Perez. 2016. “The Islamic State’s
Diminishing Returns on Twitter: How suspensions are lim-
iting the social networks of English-speaking ISIS support-
ers.” Program on Extremism. https://cchs.gwu.edu/sites/cchs.
gwu.edu/files/downloads/Berger_Occasional%20Paper.pdf;
Larson, Selena. 2017. “Twitter Suspends 377,000 Accounts
for pro-Terrorism Content.” CNNMoney. March 21. http://
money.cnn.com/2017/03/21/technology/twitter-bans-terror-
ism-accounts/index.html.; Benner, Katie. “Twitter Suspends
235,000 More Accounts Over Extremism.” The New York
Times, August 18, 2016, sec. Technology. https://www.
nytimes.com/2016/08/19/technology/twitter-suspends-ac-
counts-extremism.html.
19. “Security Manual Reveals the OPSEC Advice ISIS Gives
Recruits.” 2017. https://www.wired.com/2015/11/
isis-opsec-encryption-manuals-reveal-terrorist-group-
security-protocols/.; “Several cyber security to protect your
network communication SOCIAL.” ISIS-OPSEC-Guide.
September 14, 2015. https://www.wired.com/wp-content/
uploads/2015/11/ISIS-OPSEC-Guide.pdf.
20. Vidino, Lorenzo, and Seamus Hughes. 2015. “ISIS in
America: From Retweets to Raqqa.” The GW Program on
Extremism. p.24; Amarasingam, Amarnath. 2015. “What
Tw it t er Re a ll y Me a ns fo r I sl a m ic S ta te Supp or t er s.” War on
the Rocks. December 30. https://warontherocks.com/2015/12/
what-twitter-really-means-for-islamic-state-supporters/.
21. At present, PoE does not use Twitter’s API to identify each
account’s specific list of followers.
22. For clarity and more substantive analysis, researchers listed
every single mention separately, identifying each instance
where a account in the sample mentioned another username.
23. Please note that Abu Muhammad Al-Julani, the leader of
Jabhat Al-Nusra, announced the rebranding of the orga-
nization (now Jabhat Fatah al-Sham) in July 2016, during

40 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
PoE’s data collection period. For more on the implications
of this event, see Byman, Daniel. 2016. “What’s in a Name?
The New Jabhat Al-Nusra and the Future of Al Qaeda.”
. October 24. https://www.lawfareblog.com/
whats-name-new-jabhat-al-nusra-and-future-al-qaeda.
24. Bastian M., Heymann S., Jacomy M. (2009). Gephi: an open
source software for exploring and manipulating networks.
International AAAI Conference on Weblogs and Social Media.
25. Rami (@RamiAlLolah) account bio as of July 28, 2017. https://
twitter.com/ramiailoiah?lang=en
26. Carter, Joseph, Shiraz Maher, and Peter Neumann. 2014.
“#Greenbirds: Measuring Importance and Influence in Syrian
Foreign Fighter Networks.” International Centre for the Study
of Radicalisation. http://icsr.info/wp-content/uploads/2014/04/
ICSR-Report-Greenbirds-Measuring-Importance-and-
Infleunce-in-Syrian-Foreign-Fighter-Networks.pdf.
27. Although ‘ShamiWitness’ was deemed influential in an earlier
study, the account received only 64 mentions in PoE’s entire
dataset. This pales in comparison to other accounts mentioned
by English-language IS sympathizers. Jytte Klausen. 2015.
‘Tweeting the Jihad: Social Media Networks of Western Foreign
Fighters in Syria and Iraq,’ , 38:1
28. BBC News. 2016. “Radical Preacher Anjem Choudary Jailed for
Five Years.” http://www.bbc.com/news/uk-37284199; Oakes,
Dan, and Sam Clark. 2016. “Men Arrested in Queensland over
Alleged Plan to Take Boat to Join IS.” ABC News. http://www.
abc.net.au/news/2016-05-11/preacher-among-five-arrested-
over-alleged-plan-to-join-is/7403344; Pegues, Jeff, 2015.
“Using Social Media to Track Extremists Online.” CBS News.
http://www.cbsnews.com/news/using-social-media-to-track-
extremists-who-advocate-jihad-online/.
29. Cronin, Audrey Kurth. 2009. How Terrorism Ends: Understanding
, 14-34.
30. Cronin, Audrey Kurth. 2009. How Terrorism Ends: Understanding
, 14-34.
31. Alkhouri, Laith, and Alex Kassirer. 2016. “Tech for Jihad:
Dissecting Jihadists’ Digital Toolbox.” Flashpoint. p.1 https://
www.flashpoint-intel.com/wp-content/uploads/2016/08/
Tech ForJihad.p df.
32. Alkhouri, Laith, and Alex Kassirer. 2016. “Tech for Jihad:
Dissecting Jihadists’ Digital Toolbox.” Flashpoint. https://
www.flashpoint-intel.com/wp-content/uploads/2016/08/
Tech ForJihad.p df.
33. Examples of protected encrypted messengers discussed by
English-language sympathizers on Twitter include Telegram,
Surespot, WhatsApp, Threema, Signal, WeChat, Viber.
34. Examples of mobile security applications discussed
by English-language sympathizers on Twitter include
F-Secure Freedome, VeraCrypt, Nextplus, and GPG4USB.
35. Examples of protected email services discussed by English-
language sympathizers on Twitter include Tutanota,
ProtonMail, and HushMail.
36. Examples of VPNS discussed by English-language sym-
pathizers on Twitter include FlashVPN, TurboVPN, and
SuperFreeVPN.
37. One speculative caveat is that Twitter’s proprietary software
might flag accounts that disseminate IS-related content and
mention alternative means of online engagement. As the
company does not make this information publically available,
it is impossible to discern whether or not such factors affect
the study’s results.
38. Prucha, Nico. 2016. “IS and the Jihadist Information Highway
– Projecting Influence and Religious Identity via Telegram.”
Perspectives on Terrorism 10 (6), p.54 http://www.terrorismanalysts.
com/pt/index.php/pot/article/view/556.
39. “Combating Violent Extremism.” 2016. Tw it ter B logs . February
5. https://blog.twitter.com/2016/combating-violent-extremism.
40. Hosenball, Mark. “FBI Paid under $1 Million to Unlock San
Bernardino iPhone: Sources.” Reuters 4 May 2016. Reuters. Web.
41. Abdullah (@we_r_back64). “Hey kuffaar Worry about your bel-
gium people, instead of suspending us . Lolzzzz.” 2017. Tweet.
42. Umm Radwa (@ummradwa3). “Without a doubt Twitter suspen-
sions are biased against us. They hate us.” July 20, 2016. Tweet.
43. (@ssvvah). “It seems people were suspended. I would love to fol-
low more but I can’t. So I just hope not everyone gets suspend-
ed:/ Anyhow any tips how to.” April 9, 2017. 10:42 AM. Tweet.
44. Lakomy, Miron. 2017. “Cracks in the Online “Caliphate”:
How the Islamic State is Losing Ground in the Battle for
Cyberspace.” Perspectives on Terrorism, 11 (3), p46.
45. Lakomy, Miron. 2017. “Cracks in the Online “Caliphate”:
How the Islamic State is Losing Ground in the Battle for
Cyberspace.” Perspectives on Terrorism, 11 (3), p47.
46. “Guidelines for Law Enforcement.” 2017. Twitter Help
Center. Accessed September 11. https://help.twitter.com/ar-
ticles/41949?lang=en. “Transparency Report.” 2017. Accessed
September 11. https://transparency.twitter.com/en.html.
47. United States v. Haris Qamar Criminal Complaint and
Affidavit (2016), p.3
48. United States v. Haris Qamar Criminal Complaint and
Affidavit (2016), p.3.
49. Although PoE’s database is not designed to connect social media
accounts with real-world persons facing terrorism charges,
researchers sometimes query usernames cited in Department of
Justice press releases and legal documents, and courtroom tran-
scripts. In instances where PoE finds social media records, staff
members use them to better understand specific cases and trends.
50. According to a press release from the U.S. Department of
Defense, Abu Muhammad al-Adnani was reportedly killed
on August 30, 2016 by a precision airstrike. “Statement from

Digital Decay? • 41
Audrey Alexander
Pentagon Press Secretary Peter Cook on Strike Against ISIL
Senior Leader.” 2016. . September 12.
51. Milton, Daniel. 2016. “Communication Breakdown:
Unraveling the Islamic State’s Media Efforts.” Combating
Terrorism Center at West Point, p.21.
52. Various works and tweets by subject matter experts suggest
that these six campaigns received varying degrees of attention
from IS-central and even Western mass media.
53. This section excludes analysis on tweets mentioning the town
of Dabiq, a symbolically important front meeting the criteria
for inclusion in this section, because the software’s filter
could not parse out references to the city versus the English-
language propaganda magazine, skewing the data.
54. Winter, Charlie (@charliewinter). “Worth noting that #IS’s
approach to media & battle of #Fallujah is totally different
to its media re battles for #Ramadi/#Palmyra/#Tikrit.” May
26 2016, 7:41AM. Tweet. https://twitter.com/charliewinter/
status/735843353556877312. On June 10, Winter, Charlie
(@charliewinter). “#Major discrepancies in how #IS is
reporting from #Manbij, #Sirt, and #Fallujah.” June 10
2016, 9:09AM. Tweet. https://twitter.com/charliewinter/
status/741301306032295937.
55. Winter, Charlie (@charliewinter). “#Fallujah - pretty much
live-blogging. #Manbij - occasional mentions now & then. Sirt
- stony silence.” 10 June 2016, 9:12AM. Tweet. https://twitter.
com/charliewinter/status/741302122772369408.
56. Winter, Charlie (@charliewinter). “Instead of imposing media
blackout (as it has done in the past), #IS is issuing regular si-
treps & photo reports.” 26 May 2016, 9:35AM. Tweet. https://
twitter.com/charliewinter/status/735872104055341056.
Winter, Charlie (@charliewinter). “It can’t be seen to abandon
#Fallujah - #Is heavily invested in city for years. To give
up w/o fight would fatally damage its narrative.” 26 May
2016, 9:36AM. Tweet. https://twitter.com/charliewinter/
status/735872337002762241.
57. “Fallujah Declared ‘Fully Liberated’ from Isis by Senior Iraqi
Army Commander” 2017. http://www.
independent.co.uk/news/world/middle-east/isis-fallujah-iraq
-liberated-islamic-state-daesh-iraqi-army-a7103931.html.
58. Chulov, Martin. 2016. “Isis Kills Dozens and Seizes Hostages
in Counter-Attack on Kirkuk.” The Guardian, October 22.
World news. https://www.theguardian.com/world/2016/
oct/21/isis-kill-dozens-and-seize-hundreds-in-counter-
attack-on-kirkuk.
59. Prickett, Ivor. 2017. “In Mosul, Revealing the Last ISIS
Stronghold.” The New York Times, August 1, sec. Middle East.
https://www.nytimes.com/2017/08/01/world/middleeast/
mosul-isis-survivors-rights.html.
60. Shaheen, Kareem. 2016. “Isis Attacks Kirkuk as Concerns
Mount over Fate of Civilians in Mosul.” The Guardian, October
21, sec. World news. https://www.theguardian.com/world/
2016/oct/21/kirkuk-police-compound-under-attack-militants-
iraq-isis-mosul; Knights, Michael (@Mikeknightsiraq).
“For general readers, the Kirkuk ISIL attacks are a couple
of determined assaults on less well/protected/less critical
sites.” 21 October 2016, 3:03AM. Tweet. https://twitter.com/
Mikeknightsiraq/status/789406709659820032.
61. “ISIS Attack in Kirkuk Is Reality Check Amid Mosul Offensive
- NBC News.” 2017. http://www.nbcnews.com/storyline/
isis-terror/isis-attack-kirkuk-reality-check-amid-mosul-
offensive-n670571.
62. Winter, Charlie (@charliewinter). “#IS comms today re
#Kirkuk outnumber comms re #Mosul by ratio of 4:1. These
attacks in #Kirkuk are about distraction, not territory.”
October 21 2016, 2:46AM. Tweet. https://twitter.com/
charliewinter/status/789402479460888576.
63. During the week of October 17 to 24, 2016, 2,884 tweets men-
tioned Mosul whereas 1,054 tweets referenced Kirkuk.
64. Loveluck, Louisa, and Liz Sly. 2017. “Turkey-Backed Rebels
Seize Islamic State’s Al-Bab Stronghold in Syria.” Washington
Post, February 23. https://www.washingtonpost.com/world/
middle_east/turkey-backed-rebels-enter-center-of-islamic-
states-al-bab-strongholdin-syria/2017/02/23/e389a506-f9c3-
11e6-9b3e-ed886f4f4825_story.html.
65. Prickett, Ivor. 2017. “In Mosul, Revealing the Last ISIS
Stronghold.” The New York Times, August 1, sec. Middle East.
https://www.nytimes.com/2017/08/01/world/middleeast/
mosul-isis-survivors-rights.html.
66. Winter, Charlie. 2017. “ICSR Insight: The ISIS Propaganda
Decline.” .
March 23. http://icsr.info/2017/03/icsr-insight-isis-
propaganda-decline/.
67. Arango, Tim, and Helene Cooper. 2017. “U.S. Investigating
Mosul Strikes Said to Have Killed Up to 200 Civilians.” The
New York Times, March 24, sec. Middle East. https://www.
nytimes.com/2017/03/24/world/middleeast/us-iraq-
mosul-investigation-airstrike-civilian-deaths.html.
68. “British Captive John Cantlie Appears in New Propaganda Video
from Mosul.” 2017. . http://www.longwar-
journal.org/archives/2016/12/british-captive-john-cantlie-
appears-in-new-propaganda-video-from-mosul.php.
69. Zelin, Aaron Y. 2017. “New Video Message from The Islamic
State: ‘Knights of the Departments – Wilāyat Nīnawā.’”
January 24. http://jihadology.net/2017/01/24/new-video-
message-from-the-islamic-state-knights-of-the-departments-
wilayat-ninawa/.
70. CNN, Kimberly Hutcherson and Faith Karimi. 2017. “Report:
Syrian Forces Retake Palmyra from ISIS.” CNN. http://www.
cnn.com/2016/03/27/middleeast/syria-forces-capture-palmyra-
city/index.html.
71. Winter, Charlie (@charliewinter). “Aside from those reports
& these pics, practically *no* #Mosul media over the weekend.
Focus firmly on #Palmyra (for obvious reasons).” December

42 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
12 2016, 6:30AM. Tweet. https://twitter.com/charliewinter/
status/808318164442501120.
72. Dearden, Lizzie. 2017. “ISIS is driven out of ancient Syrian city of
Palmyra for a second time.” Independent. March 2. http://www.
independent.co.uk/news/world/middle-east/isis-palmyra-
syria-driven-out-second-time-islamic-state-ancient-roman-
ruins-assad-executions-a7607351.html.
73. Jones, Seth G., James Dobbins, Daniel Byman, Christopher S.
Chivvis, Ben Connable, Jeffrey Martini, Eric Robinson, and
Nathan Chandler. 2017. “Rolling Back the Islamic State.” Product
Page. https://www.rand.org/pubs/research_reports/RR1912.
html. Ogun, Mehmet Nesip. 2017. “ISIS: Less Territory, More
Dangerous.” Text. The National Interest. http://nationalinterest.
org/feature/isis-less-territory-more-dangerous-18439.
74. Reuters. 2016. “Islamic State Calls for Attacks on the West
during Ramadan in Audio Message,” May 22. http://www.
reuters.com/article/us-mideast-crisis-islamicstate-
idUSKCN0YC0OG.
75. Rumiyah, for example, contains a series titled, “Just Terror
Tactics,” which offers readers various modes of operation in
consecutive issues of the magazine.
76. John, Tara. 2017. “Everything We Know About the Paris Knife
Attacker Inspired By ISIS.” Time. http://time.com/4367986/
larossi-abballa-isis-paris-killed-police/.
77. Zelin, Aaron Y. 2016. “GUEST POST: An Interview with Rachid
Kassim, Jihadist Orchestrating Attacks in France.” November 18.
http://jihadology.net/2016/11/18/guest-post-an-interview-with-
rachid-kassim-jihadist-orchestrating-attacks-in-france/.
78. Hammadi, Saad, Rosie Scammell and Alan Yuhas. 2016. “Dhaka
Cafe Attack Ends with 20 Hostages among Dead.”
July 3. World news. https://www.theguardian.com/world/2016/
jul/01/dhaka-bangladesh-restaurant-attack-hostages.
79. BBC News. 2016. “Orlando Nightclub Shooting: How the
Attack Unfolded,” June 15. http://www.bbc.com/news/
world-us-canada-36511778.
80. Defined as those killing 10 or more people excluding the
perpetrators.
81. The author chose select spelling conventions to reduce error.
For example, ‘Brussels’ instead of ‘Bruxelles.’
82. BBC News. 2016. “Brussels Explosions: What We Know about
Airport and Metro Attacks,” April 9. http://www.bbc.com/
news/world-europe-35869985.
83. BBC News. 2016. “Brussels Explosions: What We Know about
Airport and Metro Attacks,” April 9. http://www.bbc.com/
news/world-europe-35869985.
84. Henley, Jon, and Kareem Shaheen. 2016. “Suicide Bombers in
Brussels Had Known Links to Paris Attacks.” The Guardian,
March 23, sec. World news. https://www.theguardian.com/
world/2016/mar/23/belgium-awkward-questions-bombers-
links-to-paris-terror-cell.
85. , 14. 2016. “The Knights of Shahadah in Belgium”, p6-7.
86. Ellis, Ralph , Ashley Fantz, Faith Karimi and Eliott C.
McLaughlin. 2016. “49 Killed in Florida Nightclub Terror Attack.”
CNN, June 13. http://www.cnn.com/2016/06/12/us/orlando-
nightclub-shooting/index.html.
87. Like the other attacks discussed in this section, this figure
offers only a sample of the number of tweets discussing the
event as some tweets make no reference to the city.
88. “Ideology À La Carte: Why Lone Actor Terrorists Choose
and Fuse Ideologies.” 2016. . October 2. https://www.
lawfareblog.com/ideology-%C3%A0-la-carte-why-lone-
actor-terrorists-choose-and-fuse-ideologies. Ackerman,
Spencer. 2016. “Omar Mateen Described Himself as ‘Islamic
Soldier’ in 911 Calls to Police.” The Guardian, June 20, sec. US
news. https://www.theguardian.com/us-news/2016/jun/20/
omar-mateen-911-calls-orlando-shooting-fbi-release-isis.
89. Zelin, Aaron Y. 2016. “New Video Message from The Islamic
State: ‘Manufacturing of the Illusions – Wilāyat Al-Khayr.’”
September 12. http://jihadology.net/2016/09/12/new-video-
message-from-the-islamic-state-manufacturing-of-the-illusions-
wilayat-al-khayr/.
90. Tuy s u z , Gu l , Ho l ly Ya n a nd S te v e A l ma s y. 2 016 . “ Is t a nb u l
Airport Attack: 42 Killed; Flights Resume.”July 6. http://
www.cnn.com/2016/06/29/europe/turkey-istanbul-atat-
urk-airport-attack/index.html.
91. Like the other attacks discussed in this section, this figure
offers only a sample of the number of tweets discussing the
event as some tweets make no reference to the city.
92. Smith-Spark, Laura. 2016. “Nice Attack Victims: France Pays
Tribute 3 Mont hs on.” CNN, October 15. http://www.cnn.com/
2016/10/15/europe/france-nice-attack-memorial/index.html.
93. Daly, Michael. 2017. “Terror Mag Praised Ramming
Attacks Before Massacre in Nice.” The Daily Beast. January
30. http://www.thedailybeast.com/articles/2016/07/15/
terror-mag-praised-ramming-attacks.
94. Like the other attacks discussed in this section, this figure
offers only a sample of the number of tweets discussing the
event as some tweets make no reference to the city.
95. Though this challenge likely affects the broader number of
‘Nice’ mentions, the data show a notable uptick the day of the
attack, and the precise content of the tweets shows that it is
not a coincidence.
96. Rubin, Alissa J., and Aurelien Breeden. 2016. “ISIS Claims
Truck Attacker in France Was Its ‘Soldier.’” The New
York Times, July 16, sec. Europe. https://www.nytimes.
com/2016/07/17/world/europe/isis-nice-france-attack.html.
97. Rumiyah Issue 5, January 2017
98. Hume,Tim , Isil Sariyuce and Joe Sterling. 2017. “Turkey
Backtracks on Age of Wedding Bomber.” CNN, August 22.
http://www.cnn.com/2016/08/22/asia/turkey-gazian-
tep-blast/index.html; Al Jazeera. 2016. “Turkey: Suicide

Digital Decay? • 43
Audrey Alexander
Bomber Kills More than 50 at Wedding,” August 22. http://
www.aljazeera.com/news/2016/08/injured-blast-hits-wed-
ding-hall-gaziantep-160820204150494.html.
99. Like the other attacks discussed in this section, this figure
offers only a sample of the number of tweets discussing the
event as some tweets make no reference to the city.
100. Letsch, Constanze. 2016. “Erdoğan Blames Isis for Suspected
Suicide Attack at Wedding in Turkey”, August 22.
https://www.theguardian.com/world/2016/aug/20/several-
dead-in-suspected-terrorist-blast-at-wedding-in-turkey.
101. Pleitgen, Frederik, , Angela Dewan, James, Griffiths and
Catherine E. Shoichet. 2016. “Berlin Attack: ISIS Claims It
Inspired Truck Assault.” CNN, December 20. http://www.
cnn.com/2016/12/20/europe/berlin-christmas-market-truck/
index.html.
102. Like the other attacks discussed in this section, this figure
offers only a sample of the number of tweets discussing the
event as some tweets make no reference to the city.
103. Frederik Pleitgen, Angela Dewan, James Griffiths and Catherine
E. Shoichet. 2017. “Berlin Attack: ISIS Claims It Inspired Truck
Assault.” CNN. http://www.cnn.com/2016/12/20/europe/
berlin-christmas-market-truck/index.html.
104. Weise, Zia. 2017. “Istanbul Nightclub Attack: Man Suspected
of Killing 39 in New Year’s Eve Massacre Captured by
Police.” The Telegraph, January 16. http://www.telegraph.
co.uk/news/2017/01/16/istanbul-nightclub-attacker-killed-
39-new-years-eve-nightclub/.
105. McCallister, Doreen. 2017. “ISIS Claims Responsibility In
Tu rk i sh N ig h tc l ub At t a ck ; U. S . M a n A mo n g Wou n de d .”
org, January 2. http://www.npr.org/sections/thetwo-way/
2017/01/02/507848348/isis-claims-responsibility-in-
turkish-nightclub-attack-u-s-man-among-the-wounded.
106. Like the other attacks discussed in this section, this figure
offers only a sample of the number of tweets discussing the
event as some tweets make no reference to the city.
107. There were 2,092 tweets on the day of the attack on
Istanbul’s Ataturk Airport. There were 1,001 tweets on the
day of the attack on Istanbul’s nightclub.
108. Rumiyah Magazine, 5, January 2017.
109. Nechepurenko, Ivan, and Neil MacFarquhar. 2017. “St.
Petersburg Metro Attack Included Many Students Among
Victims.” The New York Times, April 5, sec. Europe. https://
www.nytimes.com/2017/04/05/world/europe/st-petersburg-
metro-attack-russia.html.
110. Amarasingam, Amarnath (@AmarAmarasingam). “6/6.
So, from April 3-7, we have attacks in Saint Petersburg,
Australia, and Stockholm - all of which have thus
far gone unclaimed by ISIS.” April 8 2017, 5:04PM.
Twe et. https://twitter.com/AmarAmarasingam/
status/850861931820974080.
111. Like the other attacks discussed in this section, this figure
offers only a sample of the number of tweets discussing the
event as some tweets make no reference to the city.
112. BBC News. 2016. “Turkey’s Coup Attempt: What You Need
to Know,” July 17, sec. Europe. http://www.bbc.com/news/
world-europe-36816045.
113. The highest number of tweets per day in the dataset was 4,694,
on July 16, 2016, the day after the attempted coup in Turkey.
114. Researchers selected these individuals based on an initial
survey of the data. Mentions of leaders like Angela Merkel
and Francois Hollande were notably absent from content by
English-language sympathizers.
115. Perry, Tom. 2016. “Syria Ceasefire Takes Effect
with Assad Emboldened, Opposition Wary.” Reuters,
September 13. http://www.reuters.com/article/
us-mideast-crisis-syria-idUSKCN11I1BX.
116. Barnard, Anne. 2016. “How Omran Daqneesh, 5, Became a
Symbol of Aleppo’s Suffering.” The New York Times, August
18, sec. Middle East. https://www.nytimes.com/2016/08/19/
world/middleeast/omran-daqneesh-syria-aleppo.html.
117. BBC News. 2017. “Syria Chemical ‘Attack’: What We Know,”
April 26, sec. Middle East. http://www.bbc.com/news/
world-middle-east-39500947.
118. Gordon, Michael R., Helene Cooper, and Michael D. Shear.
2017. “Dozens of U.S. Missiles Hit Air Base in Syria.” The New
York Times, April 6, sec. Middle East. https://www.nytimes.
com/2017/04/06/world/middleeast/us-said-to-weigh-
military-responses-to-syrian-chemical-attack.html.
119. “Executive Order Protecting The Nation From Foreign
Terrorist Entry Into The United States.” 2017. .
March 6. https://www.whitehouse.gov/the-press-office/
2017/03/06/executive-order-protecting-nation-for-
eign-terrorist-entry-united-states.
120. In an October 2016 interview, Charlie Winter explained,
“Unofficially, there has been a few instances in which Trump
has appeared in pro-ISIS propaganda. In terms of official ISIS
propaganda, though, there hasn’t been one mention of him;
he’s not appeared a single time. And that is quite incredible
really, that someone who so perfectly encapsulates ISIS’s
view of the world, has been routinely ignored in any of its
propaganda is very significant indeed, because this isn’t
happening by accident.” . 2017.
http://www.wnyc.org/story/isis-propaganda-slowdown.
121. Malsin, Jared. 2016. “Russian Ambassador to Turkey Is Shot
Dead in Ankara.” Time. December 19. http://time.com/
4606600/russian-ambassador-turkey-ankara/; CNN,
Catherine E. Shoichet, Nick Thompson and Emanuella
Grinberg. 2017. “Gunman Shouted ‘Do Not Forget Aleppo!’ as
He Shot Ambassador.” CNN. http://www.cnn.com/2016/12/19/
europe/turkey-russian-ambassador-shot/index.html.

44 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
122. “Pro-JFS Groups Laud Assassin of Russian Ambassador to
Turkey, Distribute List of Russian Embassies.” 2017. https://
news.siteintelgroup.com/Jihadist-News/pro-jfs-groups-laud-
assassin-of-russian-ambassador-to-turkey-distribute-list-of-
russian-embassies.html.
123. MacFarquhar, Neil. 2016. “Vladimir Putin Tightens Grip
on Russia’s Parliament With Election Rout.” The New York
Times, September 19, sec. Europe. https://www.nytimes.
com/2016/09/20/world/europe/vladimir-putin-united-
russia-parliament-elections.html.; Browne, Ryan, and Elise
Labott. 2016. “Kerry Announces US-Russia Deal on Syrian
Ceasefire - CNNPolitics.com.” CNN Politics. September 10.
http://www.cnn.com/2016/09/09/politics/syria-ceasefire-
kerry-lavrov/index.html.; Kaczynski, Andrew, Chris
Massie, and Nathan McDermott. 2017. “80 Times Trump
Talked about Put in.” CNN Politics. http://www.cnn.com/
interactive/2017/03/politics/trump-putin-russia-timeline/.;
Liptak, Kevin. 2016. “Obama Has ‘Blunt’ Meeting with Putin.”
CNN. September 5. http://www.cnn.com/2016/09/05/
politics/barack-obama-g20-summit-asia/index.html.
124. The New York Times. 2016. “Turkey Allows Resumption of
U.S. Missions From Incirlik Air Base,”
July 17. https://www.nytimes.com/2016/07/18/world/mid-
dleeast/turkey-allows-resumption-of-us-missions-from-
incirlik-air-base.html.
125. The New York Times. 2016. “Turkey Allows Resumption of
U.S. Missions From Incirlik Air Base,”
July 17. https://www.nytimes.com/2016/07/18/world/mid-
dleeast/turkey-allows-resumption-of-us-missions-from-
incirlik-air-base.html.
126. Zelin, Aaron Y. 2017. “New Video Message from The Islamic
State: ‘Then Fight The Leaders Of Disbelief – Wilāyat
Al-Khayr.’” February 11. http://jihadology.net/2017/02/11/
new-video-message-from-the-islamic-state-then-fight-the-
leaders-of-disbelief-wilayat-al-khayr/.
Digital Decay? • 45
CONCLUSION
The findings in this report chart an uncertain future for
existing policies geared towards dismantling IS online.
At first glance, declining tweet frequency, mounting ac-
count suspensions, and falling follower count initially in-
dicate that English-language IS sympathizers suffer at the
hand of the Twitter’s efforts to counter the group online.
Ultimately, however, growing evidence reveals a complex,
nonlinear portrait of decay, showing that the fight against
IS on Twitter is far from over. These results have significant
implications for many government-endorsed approaches to
countering violent extremism in the digital sphere.
This report analyzed 845,646 tweets produced by 1,782
English-language pro-IS accounts from February 15,
2016, to May 1, 2017. Through analyzing these accounts,
and the broad range of content they disseminate, the
study found that this sample of adherents was angry, ag-
ile, resilient, and committed to vocalizing their support
for IS on Twitter, despite online and offline efforts to
weaken the movement. After discussing the ambiguity
of demographics, language trends, and the overarch-
ing decline in tweet frequency
demonstrated by the dataset, the
first analytical section worked
to answer the question, “How
have Twitter’s counter-extrem-
ism policies affected English-
language IS sympathizers on
the platform?” This examina-
tion concluded that Twitter’s
policy hampered the efficacy of
English-language supporters on-
line but argued that tech companies, policy makers, and
other counter-terrorism practitioners should not equate
such results with conventional notions of success.
Although this sample of adherents struggled to keep
their grip on Twitter, findings revealed their propensity
to adapt to changing media landscapes.
This dataset aptly confirmed that the degradation in
Twitter activity by English-language IS sympathizers
was not only the product of Twitter’s policy, but also IS’
strategic shift from Twitter to platforms with encryption
technology, including Telegram. While some accounts
rallied in the face of shutdowns, others expressed interest
in migrating to online environments that were more hos-
pitable or optimal for extremist users. Those tasked with
countering IS online must recognize the agency of actors
in the movement. Swift moves to silence IS supporters
may inadvertently produce side effects that challenge the
efficacy of law enforcement in gauging and detecting the
threat posed by violent extremists. Moreover, such ac-
tions do not necessarily affect the core of the movement
and its leadership.
At the same time, however, counter-terrorism practi-
tioners and scholars must acknowledge the dexterity of
sympathizers and work to understand the challenges posed
by platforms other than Twitter. Despite offering some
benefits, namely regarding operational security, apps like
Telegram and file sharing services like JustPaste.it offer
fundamentally different methods
for interaction with like-mind-
ed individuals. Furthermore, the
reach of such tools varies signifi-
cantly from broad-based platforms
like Twitter, which is less optimal
for extremists and counter-mes-
saging practitioners alike.
Ultimately, these observations un-
dermined the classification that
IS or its adversaries could concretely ‘win’ the war on
Twitter, much less anywhere else online. Though narrow
in scope, data gleaned from English-language IS sympa-
thizers on Twitter suggest that this battlefield extends far
beyond the reach of major tech companies and Western
governments. This point is particularly concerning given
the West’s overwhelming reliance on tech enterprises in
the fight against IS online.
Counter-terrorism practitioners
and scholars must acknowledge
the dexterity of sympathizers
and work to understand the
challenges posed by platforms
other than Twitter.

46 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
To expand upon these findings, the second section of the
analysis posed three ancillary questions to investigate
how English-language IS sympathizers engage on Twitter
with real-world events. The first of these examined how
adherents on Twitter engage with IS activity on the
ground. This discussion revealed that IS’ endeavors on the
battlefield are still a unifying theme among sympathiz-
ers on Twitter and suggested that IS’ strategic messaging
output is a noteworthy, yet unreliable component link-
ing followers on Twitter to military engagements in the
region. Paired with existing research on IS’ propaganda,
particularly products geared towards Western audiences,
the data indicates that the group’s efforts to set the agen-
da among English-language followers on Twitter yielded
mixed results. While protracted media campaigns attract
and sustain some conflict-related discourse, short-lived
messaging initiatives fail to divert supporters’ focus in the
desired direction. Although additional research is neces-
sary, this tendency might point to a particular and per-
haps growing cleavage between IS’ efforts on the ground
and its base of English-language supporters on Twitter.
Once IS loses military engagements in its remaining
strongholds in Syria, especially around Raqqa and even
Deir Ezzor, it is unclear what specific topics will occupy
the feeds of English-language IS sympathizers on Twitter.
The second of these supplementary questions interrogat-
ed the manner in which IS-claimed terror attacks drive
discourse among English-language IS supporters on the
platform. Contrary to popular belief, the effect of terror-
ist operations on this demographic was proportionally
small and mostly unpredictable. This trend was feasibly
due to the fact that the majority of IS-related violent ac-
tivity occurs within IS-controlled territory. Though a rise
in tweet frequency accompanied some attacks, variables
like plot complexity and lethality did not consistently
influence the sample of attack-related discussion among
English-language sympathizers on Twitter. The clearest
trend that emerged was that Western targets - those in
Europe or North America - often garnered more atten-
tion than attacks elsewhere. Over time, there was a nu-
merical and proportional decline in attack-related tweets
that followed critical attacks, which suggests that terror-
ist operations’ effect in mobilizing English-language IS
supporters on Twitter is diminishing. Aside from notable
spikes on the dates of attacks, terrorist violence does little
to drive a sustained conversation among this demograph-
ic of supporters on Twitter, despite substantive attention
from IS leadership, central propaganda, and even Western
mass media. The engagement of online adherents is un-
sustained, indicating a disjunction between IS’ reliance
on the tactic and English-language sympathizers, who are
apathetic to terrorist episodes in the long term.
Finally, the third question discussed how current events
influence the activity of English-language sympathizers
on Twitter. Ultimately, real-world events affect IS adher-
ents whether they are inside or outside the IS-controlled
territory. In a similar fashion to other socio-political
spheres on Twitter, IS followers rally around incidents
that resonate with its base of supporters. Some of the
greatest hikes in activity correlated with events IS can-
not control, and its inability to dictate the outcome of
current events manifests both online and offline. While
some events drew adherents en masse, others garnered
less attention; though difficult to quantify with precision,
the sum of these discussions accounted for the largest
segment of content produced by English-language IS sup-
porters on Twitter. No evidence suggested this dialogue is
narrowing in the face of more stringent efforts to silence
the movement. Although relevant tweets have declined
in absolute terms, the proportion of political discourse
remains substantial.
Data in this study showed that English-language IS sym-
pathizers on Twitter defy straightforward analysis and
convenient solutions. These accounts and their content
are volatile, diverse, and continuously influenced by the
competing agendas of IS-central, states, Twitter, and the
users themselves. On Twitter, IS fights to be heard as the
company strives to silence violent rhetoric. While em-
bracing alternative platforms, especially Telegram, IS
followers lack coherence but ensure a future for the orga-
nization online. In the meantime, the window of oppor-
tunity for effective, far-reaching strategic communication
is closing for IS-central as supporters spread to various
platforms. This challenge is further compounded by a de-
cline in central media output, which is likely the product
of IS’ territorial losses and the death of propagandists like

Digital Decay? • 47
Audrey Alexander
Abu Muhammad al-Adnani, the organization’s former
chief strategist of communications.
1
Consequently, al-
though IS-central attempts to communicate its priorities
with a global base of supporters, some evidence suggested
that its English-language adherents on Twitter stray from
the path that is paved in targeted and tailored propaganda.
Like earlier iterations of the organization and many of
its competitors, IS faces many contemporary challenges
that will define its future in the political arena. At pres-
ent, the group’s ability to mobilize a base of supporters
worldwide is confronted by counter-terrorism efforts
both online and offline, ranging from content-based
regulation on Twitter to targeting killings in Syria. In
the face of such obstacles, IS’ media strategy remains
“intentional, broad, comprehensive and most of all - pa-
tient.”
2
Like the organization’s proclivity for “trial and
error,”
3
English-language sympathizers on Twitter ex-
hibit an uncanny aptitude for problem-solving in the
digital sphere. Rather than ruminating over losses, ad-
herents fight to be heard, whether on Twitter or one of
the myriad communications technologies embraced by
the organization.
To more effectively confront the threat posed by demo-
graphics like English-language IS supporters on Twitter,
and the digital sphere writ large, counter-IS practitioners
must show a similar willingness to adapt and explore al-
ternative options. First and foremost, relevant entities
should reconfigure their aims and definition of effica-
cy because total elimination of extremists on platforms
like Twitter, and the Internet in general, is an unattain-
able goal. As terrorists continue to use communications
technology to plan attacks, dialogue advocating for bans,
shut-downs, and back doors across various mediums is
escalating; these are “misguided” and counterproductive
approaches.
4
Telegram, along with other social media
companies, is increasingly following in Twitter’s foot-
steps with another iteration of content-based regulations
via shut-downs.
5
As anticipated, the cycle continues as IS
sympathizers adapt accordingly with rebounding chan-
nels and alternative means of communication.
Although the private sector is critical to the fight against
IS online, it is not the solution. The government should
collaborate with various industries, but it cannot rely
on the efforts of the tech industry to counter IS and its
supporters in the digital sphere. Understandably, collab-
oration is attractive when the interest of tech compa-
nies and states align. Realistically, however, the benefits
of such a relationship may be short-lived, particularly
when respective interests diverge. In the case of Twitter
and the U.S. government, for example, the promotion
of counter-narratives and swift expulsion of IS sym-
pathizers from the platform appealed to both parties.
Over time, this approach remained marginally favor-
able for Twitter, but proved counterproductive to the
U.S. government’s fight against IS online, since many IS
supporters migrated to other, less accessible channels of
communication. To its detriment, the U.S. government’s
emphasis on social media providers’ enforcement of their
respective terms of service also counteracts the govern-
ment’s simultaneous requests for the same providers
to promote counter-messages. These dynamics suggest
that states must account for long term considerations in
their development and appraisal of collaborative policies
with the tech industry.
Without sacrificing their autonomy, supporting large scale
information sharing, or relying on backdoors, social media
companies can do more to undercut the reach of violent ex-
tremists without hindering conventional investigative pro-
cesses. For example, social media companies should stop
monetizing radical content and re-examine algorithms that
optimize the connectivity of extremist users. Enterprises
in the private sector, including Twitter, should continue to
explore approaches that complement content-based regula-
tion and counter-messaging initiatives. Alternative models
might consider behavior-based incentives within the plat-
form or draw upon the various strategies companies are
developing to flag fake news and other disreputable sourc-
es. Rather than silencing users online, organizations can
implement safeguards that make it difficult, not impossible,
for users to gain traction if they violate a company’s pre-
scribed terms of service. These tools can be applied to miti-
gate the impact of online extremists of various persuasions.
Existing initiatives to counter IS online have also inad-
vertently made it difficult for law enforcement to detect
and disrupt plots, whereas threats made on social media,

48 • The George Washington University Program on Extremism
Analysis of English-Language IS Sympathizers on Twitter
including Twitter and Tumblr, were previously used in
criminal cases.
6
While legal redress is a fundamental
consideration, steps forward by all parties must seek to
balance security and civil liberties. Along these lines, pol-
icymakers and practitioners must remain cognizant of the
online-offline synergy that affects the mobilization of vi-
olent extremists worldwide. Policies that fail to traverse
the space between the two environments ignore the cli-
mate that dominates this arena.
IS’ future in the digital sphere is amorphous but undeni-
able. Observations concerning English-language adher-
ents on Twitter suggest that the company’s counter-ter-
rorism policy, in tandem with IS’ strategic shift away from
Twitter, facilitated the decay of the organization’s pres-
ence on the platform. While focusing on a small sliver
of the IS supporters, this report highlights contemporary
challenges to countering online extremism. Ultimately, IS
is the amalgamation of central leadership and a broad base
that arose in support of its agenda. Through strategic and
digital communications, particularly social media, these
two components have synergistically fused into an elusive
but proactive global movement. In the face of losses, IS
and its English-language sympathizers demonstrate resil-
ience, casting a wide net to guarantee survival, and live to
tweet another day.
Notes
1. According to a press release from the U.S. Department of
Defense, Abu Muhammad al-Adnani was reportedly killed
on August 30, 2016 by a precision airstrike. “Statement from
Pentagon Press Secretary Peter Cook on Strike Against ISIL
Senior Leader.” 2016. . September 12.
2. Whiteside, Craig. 2016. “Lighting the Path: The Evolution of
the Islamic State Media Enterprise (2003-2016).” International
Centre for Counter-Terrorism - The Hague. p.22.
3. Whiteside, Craig. 2016. “Lighting the Path: The Evolution of
the Islamic State Media Enterprise (2003-2016).” International
Centre for Counter-Terrorism - The Hague. p.4.
4. Brantly, Aaron, 2017. “Banning Encryption to Stop Terrorists:
A Worse Than Futile Excercise” 10 (7).
5. See section regarding content deletion, “Telegram F.A.Q.”
2017. Telegram. Accessed September 13. https://telegram.
org/faq.“Telegram, Once More Repeating Twitter’s Mistakes,
Suspended ISIS’ Main Arabic Channel, but New One Is
Already up.” 2017. News from War on ISIS in English from
Iraq, Syria - Deir Ez-Zur Operation, Raqqa Operation - Isis.
liveuamap.com. https://isis.liveuamap.com/en/2016/13-april-
telegram-once-more-repeating-twitters-mistakes-suspended.
6. Consider, for example, the aforementioned case of Safya Yassin.
More recently, Terrence McNeil was sentenced to 20 years for
soliciting the murder of U.S. service members on social media.
United States Department of Justice. 2017. “ISIS Supporter from
Akron Sentenced to 20 Years in Prison for Soliciting Murder of
U.S. Service Members.” Accessed August 8. https://www.justice.
gov/usao-ndoh/pr/isis-supporter-akron-sentenced-20-years-pri
son-soliciting-murder-us-service-members.

GW Program on Extremism · extremism.gwu.edu · @gwupoe
