
793
PRIVACY HARMS
DANIELLE KEATS CITRON
*
& DANIEL J. SOLOVE
**
ABSTRACT
The requirement of harm has significantly impeded the enforcement of
privacy law. In most tort and contract cases, plaintiffs must establish that they
have suffered harm. Even when legislation does not require it, courts have taken
it upon themselves to add a harm element. Harm is also a requirement to
establish standing in federal court. In Spokeo, Inc. v. Robins and TransUnion
LLC v. Ramirez, the Supreme Court ruled that courts can override
congressional judgment about cognizable harm and dismiss privacy claims.
Case law is an inconsistent, incoherent jumble with no guiding principles.
Countless privacy violations are not remedied or addressed on the grounds that
there has been no cognizable harm.
Courts struggle with privacy harms because they often involve future uses of
personal data that vary widely. When privacy violations result in negative
consequences, the effects are often small—frustration, aggravation, anxiety,
inconvenience—and dispersed among a large number of people. When these
minor harms are suffered at a vast scale, they produce significant harm to
individuals, groups, and society. But these harms do not fit well with existing
cramped judicial understandings of harm.
This Article makes two central contributions. The first is the construction of
a typology for courts to understand harm so that privacy violations can be
tackled and remedied in a meaningful way. Privacy harms consist of various
different types that have been recognized by courts in inconsistent ways. Our
*
Jefferson Scholars Foundation Schenck Distinguished Professor in Law, Caddell and
Chapman Professor of Law, University of Virginia School of Law; Vice President, Cyber
Civil Rights Initiative; 2019 MacArthur Fellow.
**
John Marshall Harlan Research Professor of Law, George Washington University Law
School.
We would like to thank research assistants Kimia Favagehi, Katherine Grabar, Jean Hyun,
Austin Mooney, Julia Schur, and Rebecca Weitzel. Many scholars provided extremely helpful
feedback, including Kenneth Abraham, Alessandro Acquisti, Rachel Bayefsky, Ryan Calo,
Ignacio Cofone, Bob Gellman, Woodrow Hartzog, Chris Hoofnagle, Lauren Scholz, Lior
Strahelivitz, Ari Waldman, Benjamin Zipursky, the participants at our workshop at the
Privacy Law Scholars Conference, and students in Neil Richards’s Advanced Privacy Law
and Theory class at Washington University School of Law. Jackson Barnett and fellow editors
at the Boston University Law Review provided superb feedback during our delightful editing
process.

794 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
typology of privacy harms elucidates why certain types of privacy harms should
be recognized as cognizable.
This Article’s second contribution is providing an approach to when privacy
harm should be required. In many cases, harm should not be required because
it is irrelevant to the purpose of the lawsuit. Currently, much privacy litigation
suffers from a misalignment of enforcement goals and remedies. We contend that
the law should be guided by the essential question: When and how should
privacy regulation be enforced? We offer an approach that aligns enforcement
goals with appropriate remedies.

2022] PRIVACY HARMS 795
CONTENTS
INTRODUCTION ............................................................................................... 796
I. COGNIZABLE HARMS: THE LEGAL RECOGNITION OF
PRIVACY HARMS ................................................................................. 799
A. Standing ....................................................................................... 800
B. Harm in Causes of Action ............................................................ 807
1. Contract Law ......................................................................... 807
2. Tort Law ................................................................................ 808
3. Statutory Causes of Action .................................................... 810
C. Harm in Regulatory Enforcement Actions .................................. 813
II. THE CHALLENGES OF PRIVACY HARMS .............................................. 816
A. Aggregation of Small Harms ....................................................... 816
B. Risk: Unknowable and Future Harms ......................................... 817
C. Individual vs. Societal Harms ...................................................... 818
III. REALIGNING PRIVACY ENFORCEMENT AND REMEDIES ...................... 819
A. The Goals of Enforcement ........................................................... 820
B. Aligning Remedies with Goals ..................................................... 820
1. The Problem of Misalignment ............................................... 820
2. The Value of Private Enforcement ........................................ 821
3. An Approach for Realignment .............................................. 822
IV. THE IMPORTANCE OF PROPERLY RECOGNIZING PRIVACY HARMS ..... 826
A. Properly Identifying the Interests at Stake .................................. 826
B. The Expressive Value of Recognizing Harm ............................... 828
C. Legislative and Regulatory Agenda ............................................. 829
V. A TYPOLOGY OF PRIVACY HARMS ...................................................... 830
A. Physical Harms ........................................................................... 831
B. Economic Harms ......................................................................... 834
C. Reputational Harms ..................................................................... 837
D. Psychological Harms ................................................................... 841
1. Emotional Distress ................................................................ 841
2. Disturbance ............................................................................ 844
E. Autonomy Harms ......................................................................... 845
1. Coercion ................................................................................ 846
2. Manipulation ......................................................................... 846
3. Failure to Inform ................................................................... 848
4. Thwarted Expectations .......................................................... 849
5. Lack of Control ..................................................................... 853
6. Chilling Effects ...................................................................... 854
F. Discrimination Harms ................................................................. 855
G. Relationship Harms ..................................................................... 859
CONCLUSION ................................................................................................... 861

796 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
INTRODUCTION
Harm has become one of the biggest challenges in privacy law.
1
The law’s
treatment of privacy harms is a jumbled, incoherent mess. Countless privacy
violations are left unremedied not because they are unworthy of being addressed
but because of the law’s failure to recognize harm.
2
As Ryan Calo has observed,
“courts and some scholars require a showing of harm in privacy out of
proportion with other areas of law.”
3
Privacy law in the United States is a sprawling patchwork of various types of
law, from contract and tort to statutes and other bodies of law.
4
As these laws
are enforced, especially in the courts, harm requirements stand as a major
impediment.
5
When cases are dismissed due to the lack of harm, wrongdoers
escape accountability.
6
The message is troubling—privacy commitments
enshrined in legislation and common law can be ignored.
In several ways, harm emerges as a gatekeeper in privacy cases. Harm is an
element of many causes of action.
7
Courts, however, refuse to recognize privacy
harms that do not involve tangible financial or physical injury.
8
But privacy
harms more often involve intangible injuries, which courts address
inconsistently and with considerable disarray.
9
Many privacy violations involve
1
Jacqueline D. Lipton, Mapping Online Privacy, 104 NW. U. L. REV. 477, 508 (2010)
(“Delineating remediable harms has been a challenge for law and policy makers since the
early days of the Internet.”).
2
Id. at 505 (explaining monetary damages compensate economic harm, but “[c]ourts and
legislatures have been slow to compensate plaintiffs for nonmonetary harms resulting from a
privacy incursion”).
3
Ryan Calo, Privacy Harm Exceptionalism, 12 COLO. TECH. L.J. 361, 361 (2014); see also
Ryan Calo, Privacy Law’s Indeterminacy, 20 THEORETICAL INQUIRIES L. 33, 48 (2019)
(“[C]ourts . . . do not understand privacy loss as a cognizable injury, even as they recognize
ephemeral harms in other contexts.”).
4
DANIEL J. SOLOVE & PAUL M. SCHWARTZ, INFORMATION PRIVACY LAW 2 (7th ed. 2021).
(“Information privacy law is an interrelated web of tort law, federal and state constitutional
law, federal and state statutory law, evidentiary privileges, property law, contract law, and
criminal law.”).
5
Calo, Privacy Harm Exceptionalism, supra note 3, at 362 (explaining, for example, that
in Federal Aviation Administration v. Cooper, the Supreme Court’s reading of the Privacy
Act to require “‘actual damages’ limited to pecuniary or economic harm” prevented plaintiff
from recovery (quoting Fed. Aviation Admin. v. Cooper, 566 U.S. 284, 292 (2012))).
6
Id. (citing instances where, absent a finding of cognizable harm, privacy actions were
dismissed for lack of standing).
7
Id. at 361 (noting harm is a “prerequisite to recovery in many contexts”).
8
Danielle Keats Citron, The Privacy Policymaking of State Attorneys General, 92 NOTRE
DAME L. REV. 747, 798-99 (2016) [hereinafter Citron, Privacy Policymaking] (“For most
courts, privacy and data security harms are too speculative and hypothetical, too based on
subjective fears and anxieties, and not concrete and significant enough to warrant
recognition.”).
9
Lipton, supra note 1, at 504-05 (explaining that economic loss is “readily cognizable”
but intangible harms like shame, embarrassment, ridicule, and humiliation are more difficult
to quantify).

2022] PRIVACY HARMS 797
broken promises or thwarted expectations about how people’s data will be
collected, used, and disclosed.
10
The downstream consequences of these
practices are often hard to determine in the here and now. Other privacy
violations involve flooding people with unwanted advertising or email spam. Or
people’s expectations may be betrayed, resulting in their data being shared with
third parties that may use it in detrimental ways—although precisely when and
how is unknown.
For many privacy harms, the injury may appear small when viewed in
isolation, such as the inconvenience of receiving an unwanted email or
advertisement or the failure to honor people’s expectations that their data will
not be shared with third parties. But when done by hundreds or thousands of
companies, the harm adds up. Moreover, these small harms are dispersed among
millions—and sometimes billions—of people.
11
Over time, as people are
individually inundated by a swarm of small harms, the overall societal impact is
significant. Yet these types of injuries do not fit well into judicial conceptions
of harm, which have an individualistic focus and heavily favor tangible physical
and financial injuries that occur immediately.
Some statutory laws recognize government agency or state attorney general
enforcement that is less constrained by judicial conceptions of harm, but these
enforcers have limited resources so they can only bring a handful of actions each
year.
12
To fill the anticipated enforcement gap, legislators have often included
statutory private rights of action.
13
The financial rewards of litigating and
winning cases work like a bounty system, encouraging private parties to enforce
the law.
14
To address the difficulties in establishing privacy harms, several
privacy statutes contain statutory damages provisions, which allow people to
recover a minimum amount of money without having to prove harm.
15
10
Id. at 498-99 (noting “the greatest harms in the present age often come from
unauthorized uses of private information online” including the improper collection,
aggregation, processing, and dissemination of information).
11
See, e.g., Brian Fung, T-Mobile Says Data Breach Affects More than 40 Million People,
CNN BUS. (Aug. 18, 2021, 8:07 AM), https://www.cnn.com/2021/08/18/tech/t-mobile-data-
breach/index.html [https://perma.cc/L6XV-6PUN] (reporting that one data breach “affect[ed]
as many as 7.8 million postpaid subscribers, 850,000 prepaid customers and ‘just over’ 40
million past or prospective customers who have applied for credit with T-Mobile”).
12
Citron, Privacy Policymaking, supra note 8, at 799 (“Federal authorities cannot attend
to most privacy and security problems because their resources are limited and their duties ever
expanding. Simply put, federal agencies have too few resources and too many
responsibilities.” (footnote omitted)).
13
See infra notes 109-12 and accompanying text (listing several examples of federal and
state privacy laws with private rights of action).
14
See Crabill v. Trans Union, L.L.C., 259 F.3d 662, 665 (7th Cir. 2001) (“The award of
statutory damages could also be thought a form of bounty system, and Congress is permitted
to create legally enforceable bounty systems for assistance in enforcing federal laws . . . .”).
15
See infra notes 113-16 and accompanying text (explaining that, for example, under Fair
Credit Reporting Act, a person who willfully violates any part of the statute is liable for at
least $100 in damages, and listing other statutes which do not require a showing of harm).

798 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Courts, however, have wrought havoc on legislative plans for statutory
damages in privacy cases by adding onerous harm requirements. In Doe v.
Chao,
16
for example, the Supreme Court held that a statutory damages provision
under the federal Privacy Act of 1974 would only impose such damages if
plaintiffs established “actual” damages.
17
As a second punch, the Court held in
Federal Aviation Administration v. Cooper
18
that emotional distress alone was
insufficient to establish actual damages under the Privacy Act.
19
In a variation
of this theme, in Senne v. Village of Palatine,
20
the Seventh Circuit held that a
plaintiff had to prove harm to recover under a private right of action for a
violation of the federal Driver’s Privacy Protection Act (“DPPA”) even though
the provision lacked any harm requirement.
21
Courts have also injected harm as a gatekeeper to the enforcement of the law
through modern standing doctrine. The Supreme Court has held that plaintiffs
cannot pursue cases in federal court unless they have suffered an “injury in
fact.”
22
Specifically in the privacy law context, in 2016, the Supreme Court
concluded in Spokeo, Inc. v. Robins,
23
a case involving the Fair Credit Reporting
Act (“FCRA”), that courts could deny standing to plaintiffs seeking to recover
under private rights of action in statutes.
24
The court stated that, even if a
legislature granted plaintiffs a right to recover without proving harm, courts
could require a plaintiff to prove harm to establish standing.
25
Due to judicial intervention, the requirement of privacy harm is inescapable.
Even when legislation does not require proof of harm, courts exert their will to
add it in, turning the enforcement of privacy law into a far more complicated
task than it should be. Privacy harm is a conceptual mess that significantly
impedes U.S. privacy law from being effectively enforced. Even when
16
540 U.S. 614 (2004).
17
Id. at 616 (holding “[p]laintiffs must prove some actual damages to qualify for a
minimum statutory award”).
18
566 U.S. 284 (2012).
19
Id. at 299-304 (holding “the Privacy Act does not unequivocally authorize an award of
damages for mental or emotional distress” and adopting narrow interpretation of actual
damages limited to pecuniary harm).
20
784 F.3d 444 (7th Cir. 2015).
21
Id. at 448.
22
Friends of the Earth, Inc. v. Laidlaw Env’t Servs. (TOC), Inc., 528 U.S. 167, 181 (2000)
(declaring that injury-in-fact requirement is met only by showing “injury to the plaintiff”).
23
578 U.S. 330 (2016).
24
Id. at 341 (holding that plaintiffs alleging “bare procedural violation” of FCRA do not
satisfy injury-in-fact requirement of Article III and thus lack standing).
25
Id. at 337-38 (noting that Congress does not have power to give plaintiffs statutory right
to sue unless those plaintiffs also satisfy Article III standing requirements).

2022] PRIVACY HARMS 799
organizations have engaged in clear wrongdoing, privacy harm requirements
often result in cases being dismissed.
26
In this Article, we clear away the fog so that privacy harms can be better
understood and appropriately addressed.
27
We set forth a typology that explains
why particular harms should be legally cognizable. We show how concepts and
doctrines in other areas of law can be applied in the context of privacy harms.
In addition to the issue of what should constitute cognizable privacy harm,
we also examine the issue of when privacy harm should be required. In many
cases, harm should not be required because it is irrelevant to the purpose of the
lawsuit. The overarching question that the law should ask is: When and how
should various privacy laws be enforced? This question brings into focus the
underlying source of the law’s current malaise: the misalignment of enforcement
goals and remedies. We propose an approach that aligns enforcement goals with
appropriate remedies.
Properly recognizing privacy harm is not just essential for litigation. It is
essential for its expressive value as well as for legislation and regulatory
enforcement. Appropriately identifying the interests at stake is essential for the
law to balance and protect them.
This Article has five parts. Part I discusses when the law requires cognizable
harm in order to enforce privacy regulation. Part II examines several challenges
that make it difficult to recognize certain types of privacy harms. Part III
examines when privacy harm should be required in privacy litigation and how
the law should better align enforcement goals and remedies. Part IV discusses
the importance of recognizing privacy harm. Part V sets forth a typology of
privacy harms, explaining why each involves an impairment of important
interests, how the law tackles them, and why the law should do so.
I. COGNIZABLE HARMS: THE LEGAL RECOGNITION OF PRIVACY HARMS
Requirements to establish harm are major hurdles in privacy cases. Harms
involve injuries, setbacks, losses, or impairments to well-being.
28
They leave
people or society worse off than before their occurrence.
29
Frequently,
26
E.g., Senne, 784 F.3d at 448 (holding that even though defendant’s display of plaintiff’s
personal information amounted to a disclosure under DPPA, plaintiff could not recover absent
finding of harm).
27
Previously, we wrote an article about data breach harms. Daniel J. Solove & Danielle
Keats Citron, Risk and Anxiety: A Theory of Data-Breach Harms, 96 TEX. L. REV. 737 (2018)
[hereinafter Solove & Citron, Risk and Anxiety]. We write separately on privacy harms
because they are quite different. Data breach harms often involve either anxiety or a risk of
future identity theft or fraud. Privacy harms are more varied than data breach harms and
involve many other dimensions that pose challenges for the law.
28
A taxonomy of privacy developed by one of us (Solove) has focused on privacy
problems. DANIEL J. SOLOVE, UNDERSTANDING PRIVACY (2008). Problems are broader than
harms. Problems are undesirable states of affairs. Harms are a subset of problems.
29
JOEL FEINBERG, 1 THE MORAL LIMITS OF THE CRIMINAL LAW: HARM TO OTHERS 28, 34-
36 (1984) (defining harms as “setbacks to interest” and noting that “[t]he test . . . of whether

800 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
establishing harm is a prerequisite to enforcement for privacy violations in the
judicial system. A cognizable harm is harm that the law recognizes as suitable
for intervention.
30
Through harm requirements, courts have made the enforcement of privacy
laws difficult and, at times, impossible. They have added requirements for harm
via standing.
31
They have required harm for statutes that do not require such a
showing.
32
They have mandated proof of harm even for statutes that include
statutory damages, undercutting the purpose of these provisions.
33
They have
adopted narrow conceptions of cognizable harm to exclude many types of harm,
including emotional injury and dashed expectations.
34
Because courts lack a
theory of privacy harms or any guiding principles, they have made a mess of
things. This Part discusses the varied ways that harm is involved in privacy
cases.
A. Standing
To pursue a lawsuit in federal court, a plaintiff must have standing. Standing
is based on Article III of the U.S. Constitution, which states that courts are
limited to hearing “cases” or “controversies.”
35
In a series of cases starting in the
second half of the twentieth century, the Supreme Court placed harm at the
such an invasion has in fact set back an interest is whether that interest is in a worse condition
than it would otherwise have been in had the invasion not occurred at all”).
30
Id. at 34 (“It is only when an interest is thwarted through an invasion by self or others,
that its possessor is harmed in the legal sense . . . .”); see also OLIVER WENDELL HOLMES, THE
COMMON LAW 64 (Mark DeWolfe Howe ed., Harvard Univ. Press 1963) (1881) (“The
business of the law of torts is to fix the dividing lines between those cases in which a man is
liable for harm which he has done, and those in which he is not. But it cannot enable him to
predict . . . . [a]ll the rules that the law can lay down beforehand are rules for determining
conduct which will be followed by liability if it is followed by harm,—that is, the conduct
which a man pursues at his peril.”); Thomas C. Grey, Accidental Torts, 54 VAND. L. REV.
1225, 1272 (2001) (discussing Holmes’s harm-based approach).
31
See, e.g., Friends of the Earth, Inc. v. Laidlaw Env’t Servs. (TOC), Inc., 528 U.S. 167,
181 (2000) (holding proof of harm is necessary to satisfy “injury in fact” requirement in
Article III standing).
32
See, e.g., Senne v. Village of Palatine, 784 F.3d 444, 448 (7th Cir. 2015) (denying
plaintiff recovery on grounds that plaintiff did not prove harm even though statute plaintiff
was suing under lacked harm requirement).
33
See, e.g., Doe v. Chao, 540 U.S. 614, 627 (2004) (refusing to award plaintiff minimum
statutory damages under Privacy Act of 1974 on grounds that plaintiff did not sufficiently
show harm resulting in “actual damages”).
34
See, e.g., Fed. Aviation Admin. v. Cooper, 566 U.S. 284, 299 (2012) (adopting narrow
interpretation of “actual damages” such that only proven pecuniary harm suffices).
35
U.S. CONST. art. III, § 2.

2022] PRIVACY HARMS 801
center of standing doctrine.
36
State courts generally do not require proof of
standing.
37
The Supreme Court has developed a rather tortured body of standing doctrine,
which is restrictive in its view of harm as well as muddled and contradictory.
Under contemporary standing doctrine, plaintiffs must allege an “injury in
fact.”
38
The injury must be “concrete and particularized” and “actual or
imminent, not conjectural or hypothetical.”
39
If a plaintiff lacks standing to bring
a claim, a federal court cannot hear it.
40
Three cases decided during the past decade focused on privacy issues. In
2013, in Clapper v. Amnesty International,
41
a group of lawyers, journalists, and
activists challenged the constitutionality of surveillance by the National Security
Agency (“NSA”). The plaintiffs contended that because they were
communicating with foreign people whom the NSA was likely to deem
suspicious, they feared their communications would be wiretapped. The
plaintiffs took measures to avoid governmental surveillance that would pierce
attorney-client confidentiality, including spending time and money to travel in
person to talk to clients.
42
The Court held that the plaintiffs lacked standing
because they failed to prove that they were actually under government
surveillance or that such surveillance was “certainly impending.”
43
The
plaintiffs’ “speculation” about being under surveillance was insufficient.
44
In a
36
E.g., Friends of the Earth, 528 U.S. at 181.
37
Peter N. Salib & David K. Suska, The Federal-State Standing Gap: How to Enforce
Federal Law in Federal Court Without Article III Standing, 26 WM. & MARY BILL RTS. J.
1155, 1160 (2018) (“State courts are not subject to Article III and its standing requirement.”).
38
Friends of the Earth, 528 U.S. at 180-81 (citing Lujan v. Defenders of Wildlife, 504
U.S. 555, 560-61 (1992)) (noting that to satisfy Article III’s standing requirements, plaintiff
must show injury in fact, causation, and redressability).
39
Id. at 180.
40
Id. (“[The Court has] an obligation to assure [itself] that [plaintiff] had Article III
standing at the outset of the litigation”).
41
568 U.S. 398 (2013).
42
Id. at 415 (“Respondents claim . . . the threat of surveillance sometimes compels them
to avoid certain e-mail and phone conversations, to ‘tal[k] in generalities rather than
specifics,’ or to travel so that they can have in-person conversations.” (second alteration in
original)). For a thoughtful analysis of Clapper, see Neil M. Richards, The Dangers of
Surveillance, 126 HARV. L. REV. 1934 (2013).
43
Clapper, 568 U.S. at 422.
44
The Clapper case comes with a dose of cruel irony. Although the government
diminished the plaintiffs’ concerns about surveillance by arguing that the plaintiffs could not
prove that they were subject to it, the government knew the answer all along (it was surely
engaging in such surveillance), but because the program was classified as a state secret, the
plaintiffs did not and could not know for sure that they were being subject to surveillance. See
Seth F. Kreimer, “Spooky Action at a Distance”: Intangible Injury in Fact in the Information
Age, 18 U. PA. J. CONST. L. 745, 756-57 (2016) (describing the Bush Administration as
engaging in a “strategy of deep secrecy” which resulted in details of surveillance only being
known by a “charmed circle of initiates” who would not face legal scrutiny).

802 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
footnote, the Court noted that, “in some instances,” a “‘substantial risk’ that the
harm will occur” would be sufficient to confer standing to a plaintiff.
45
The
Court never explained what would constitute a “substantial risk.”
Although Clapper had a significant impact on data breach cases, a subsequent
case took center stage for standing in privacy cases. In 2016, in Spokeo, Inc. v.
Robins, the Supreme Court attempted to elaborate on the types of harm that
could be sufficient to establish standing.
46
The Court focused on whether
statutory violations involving personal data constituted harm sufficient to
establish standing. The plaintiff alleged that Spokeo, a site supplying
information about people’s backgrounds, violated the federal FCRA when it
published incorrect data about him.
47
Spokeo’s profiles were used by employers
to investigate prospective hires, an activity regulated by the FCRA. The FCRA
mandates that firms take reasonable steps to ensure the accuracy of data in
people’s profiles.
48
The plaintiff’s dossier was riddled with falsehoods,
including that he was wealthy and married, had children, and worked in a
professional field.
49
According to the plaintiff, these errors hurt his employment
chances by indicating that he was overqualified for positions he sought or that
he might not be able to relocate because he had a family.
50
Although the district court held that the plaintiff properly sued under the
FCRA’s private right of action, it nevertheless held the plaintiff lacked standing
because he had not suffered an injury based on the erroneous information
included in his credit report.
51
The Ninth Circuit reversed on the grounds that
the statute resolved the question of whether a cognizable injury existed: the
FCRA explicitly allowed plaintiffs to sue for any violation of its provisions.
52
45
Clapper, 568 U.S. at 414 n.5 (citing Monsanto Co. v. Geertson Seed Farms, 561 U.S.
139, 153 (2010)). In Susan B. Anthony List v. Driehaus, the Court, quoting Clapper, held that
“[a]n allegation of future injury may suffice if the threatened injury is ‘certainly impending,’
or there is a ‘substantial risk’ that the harm will occur.” 573 U.S. 149, 158 (2014).
46
578 U.S. 330, 340-42 (2016) (noting that history and “judgment of Congress” are
meaningful in determining whether intangible harm amounts to injury in fact).
47
Id. at 333-34 (describing website as “people search engine” and explaining Robins’s
claim that site violated his (and other similarly situated individuals’) rights under the FCRA
when it published false information).
48
15 U.S.C. § 1681e(b) (mandating that consumer reporting agencies “follow reasonable
procedures to assure maximum possible accuracy of the information concerning the individual
about whom the report relates”).
49
Spokeo, 578 U.S. at 336.
50
Id. at 350 (Ginsburg, J., dissenting).
51
Id. at 336.
52
Robins v. Spokeo, Inc., 742 F.3d 409, 411-14 (9th Cir. 2014), vacated, 578 U.S. 330
(2016); see also 15 U.S.C. § 1681n (imposing civil liability for willful violations); Id. § 1681o
(imposing civil liability for negligent violations).

2022] PRIVACY HARMS 803
The Supreme Court took up the case, issuing an opinion purporting to clarify
standing doctrine but instead creating significant confusion.
53
Instead of
deferring to congressional judgment for when plaintiffs could sue for violations
of the FCRA, the Court added harm into the equation through standing.
54
Reversing and remanding the case to the Ninth Circuit, the Court explained that
harm must be “concrete” and that “intangible harm” could be sufficient in some
cases to establish injury.
55
According to the Court, a “risk of real harm” could
satisfy the concreteness inquiry because long-standing common law has
“permitted recovery by certain tort victims even if their harms may be difficult
to prove or measure.”
56
The question would turn on “whether an alleged
intangible harm has a close relationship to a harm that has traditionally been
regarded as providing a basis for a lawsuit in English or American courts.”
57
Unfortunately, the common law invoked by the Court points in different
directions. The Court’s discussion of “intangible harm” ended up creating
further confusion rather than clarity.
The Court confounded matters in yet another way—it instructed courts to
assess “the judgment of Congress” to figure out “whether an intangible harm
constitutes injury in fact.”
58
The Court began by noting:
[W]e said in Lujan that Congress may “elevat[e] to the status of legally
cognizable injuries concrete, de facto injuries that were previously
inadequate in law.” Similarly, Justice Kennedy’s concurrence in that case
explained that “Congress has the power to define injuries and articulate
chains of causation that will give rise to a case or controversy where none
existed before.”
59
Although Congress could independently define “concrete injury” in a way
that enlarged the concept, the Court also said that Congress could deviate only
so much:
Congress’ role in identifying and elevating intangible harms does not mean
that a plaintiff automatically satisfies the injury-in-fact requirement
whenever a statute grants a person a statutory right and purports to
authorize that person to sue to vindicate that right. Article III standing
requires a concrete injury even in the context of a statutory violation. For
that reason, Robins could not, for example, allege a bare procedural
53
Spokeo, 578 U.S. at 337-42 (deciding even where Congress created private right of
action for statutory violations, plaintiffs must show concrete and particularized harm to satisfy
injury-in-fact requirement of Article III standing).
54
Id. at 337-40.
55
Id. at 340-42.
56
Id. at 341.
57
Id.
58
Id. at 340-41.
59
Id. at 341 (first quoting Lujan v. Defenders of Wildlife, 504 U.S. 555, 578 (1992); and
then quoting Lujan, 504 U.S. at 580 (Kennedy, J., concurring)).

804 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
violation, divorced from any concrete harm, and satisfy the injury-in-fact
requirement of Article III.
60
As to how far Congress could deviate from courts in defining injuries, the
Court failed to provide a clear answer. As an example, the Court noted that
courts could reject a “bare procedural violation” of a statute as an injury, but this
example was muddled with further explanation: “[T]he violation of a procedural
right granted by statute can be sufficient in some circumstances to constitute
injury in fact. In other words, a plaintiff in such a case need not allege any
additional harm beyond the one Congress has identified.”
61
The Court thus said on one hand that a mere violation of a procedural right
can be sufficient for concrete injury without any additional harm. But, on the
other hand, a “bare procedural violation, divorced from any concrete harm”
cannot satisfy the harm requirement.
62
So, how are courts to distinguish between
when a violation of a procedural right is a concrete injury and when it is not?
The Court tried to explain its reasoning by noting that Congress passed the
FCRA “to curb the dissemination of false information,” so bare procedural
violations would not support standing if they did not operate to prevent such
inaccuracies.
63
The Court explained that consumers may not be able to sue a
consumer reporting agency for failing to provide notice required by the statute
if the information in their dossiers was accurate. The Court further complicated
matters by stating that “not all inaccuracies cause harm or present any material
risk of harm.”
64
The example provided by the Court was an incorrect zip code.
The Court explained, “It is difficult to imagine how the dissemination of an
incorrect zip code, without more, could work any concrete harm.”
65
The Court remanded the case to the Ninth Circuit to examine “whether the
particular procedural violations alleged in this case entail a degree of risk
sufficient to meet the concreteness requirement.”
66
The Court noted that it was
not taking a particular position about whether Robins properly alleged an
injury.
67
In the wake of Spokeo, courts issued a contradictory mess of decisions
regarding privacy harm and standing. On remand, the Ninth Circuit concluded
that Robins had suffered harm, justifying standing.
68
The court applied a test
60
Id.
61
Id. at 341-42.
62
Id. at 341.
63
Id. at 342.
64
Id.
65
Id.
66
Id. at 343 (Thomas, J., concurring).
67
See id. at 343 (majority opinion) (“We take no position as to whether the Ninth Circuit’s
ultimate conclusion¾that Robins adequately alleged an injury in fact¾was correct.”).
68
Robins v. Spokeo, Inc. (Spokeo II), 867 F.3d 1108, 1118 (9th Cir. 2017) (“We are
satisfied that Robins has alleged injuries that are sufficiently concrete for the purposes of
Article III.”), cert. denied, 138 S. Ct. 931 (2018).

2022] PRIVACY HARMS 805
from the Second Circuit that assessed whether a statutory provision was
designed to protect people’s concrete interests and whether those interests were
at risk of harm in a particular case.
69
Other courts have extracted a two-prong
test from the wreckage, first looking to a “historical inquiry” that “asks whether
an intangible harm ‘has a close relationship’ to one that historically has provided
a basis for a lawsuit,” and second, looking to a “congressional inquiry” that
“acknowledges that Congress’s judgment is ‘instructive and important’ because
that body ‘is well positioned to identify intangible harms that meet minimum
Article III requirements.’”
70
In the lower courts, no clear principles have emerged to guide the harm
inquiry for standing in privacy cases. Rather than a simple circuit split or other
clear disagreement in approach, courts have produced a jumbled mess by
grasping at inconsistent parts of Spokeo.
71
Predictably, courts have reached
opposing conclusions as to the very same or similar FCRA violations. In Dutta
v. State Farm Mutual Automobile Insurance,
72
the Ninth Circuit concluded that
an employer’s alleged FCRA violation—failing to provide the plaintiff with a
copy of his inaccurate credit report before disqualifying him from the hiring
process—was not a harm because the correct information in the credit report
prevented him from getting a job anyway.
73
By contrast, in Long v. Southeastern
Pennsylvania Transportation Authority,
74
the Third Circuit found the plaintiffs
had standing to sue an employer under the FCRA for its alleged failure to
provide them with copies of their fully accurate background checks before
rejecting them for a job.
75
As the Third Circuit stated in another case involving a FCRA violation,
In some cases, we have appeared to reject the idea that the violation of a
statute can, by itself, cause an injury sufficient for purposes of Article III
standing. But we have also accepted the argument, in some circumstances,
69
See id. at 1113 (citing Strubel v. Comenity Bank, 842 F.3d 181, 190 (2d Cir. 2016))
(holding the two-prong Strubel test “best elucidates the concreteness standards articulated by
the Supreme Court in Spokeo II” and applying it to Robins’s alleged harm).
70
Long v. Se. Pa. Transp. Auth., 903 F.3d 312, 321 (3d Cir. 2018) (quoting Spokeo, 578
U.S. at 341).
71
Jackson Erpenbach, Note, A Post-Spokeo Taxonomy of Intangible Harms, 118 MICH. L.
REV. 471, 473 (2019) (describing inconsistent findings of standing for intangible harms as
evidence of “significant confusion in the lower courts” caused by Spokeo).
72
895 F.3d 1166 (9th Cir. 2018).
73
Id. at 1175-76 (holding plaintiff “plausibly [pled] a violation of [FCRA]” by alleging
State Farm disqualified him before providing copy of his credit report but “fail[ed] to
demonstrate actual harm or a substantial risk of such harm” because disqualification was
based on report’s accurate information).
74
Long, 903 F.3d 312.
75
Id. at 316-17, 322-24 (finding “the use of Plaintiffs’ personal information . . . without
Plaintiffs being able to see or respond to it” was “sufficient concrete harm” to establish
standing).

806 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
that the breach of a statute is enough to cause a cognizable injury—even
without economic or other tangible harm.
76
Similarly, the Sixth Circuit declared when it dismissed a case for lack of
standing, “It’s difficult, we recognize, to identify the line between what
Congress may, and may not, do in creating an ‘injury in fact.’ Put five smart
lawyers in a room, and it won’t take long to appreciate the difficulty of the task
at hand.”
77
In its coup de grâce, the Supreme Court in 2021 revisited standing and the
FCRA in TransUnion LLC v. Ramirez.
78
TransUnion incorrectly labeled the
plaintiffs as potential terrorists in their credit reports. The Court held that only
the plaintiffs whose credit reports had been disclosed to businesses had standing;
plaintiffs whose credit reports had not yet been disseminated had not suffered a
concrete injury.
79
As the Court pithily concluded, “No concrete harm, no
standing.”
80
To determine whether harm is concrete, the Court reiterated the position it
had previously espoused in Spokeo: “Central to assessing concreteness is
whether the asserted harm has a ‘close relationship’ to a harm traditionally
recognized as providing a basis for a lawsuit in American courts . . . .”
81
Yet
still, the Court provided scant guidance about how close the relationship must
be to traditionally recognized harm. Another difficulty with this test is that harm
traditionally has not been required at all for violations of individual private
rights, as Justice Thomas pointed out in his dissent.
82
Additionally, the harms
that courts have recognized have evolved considerably in the common law.
83
Pointing to tradition means that the target is constantly moving.
76
In re Horizon Healthcare Servs. Inc. Data Breach Litig., 846 F.3d 625, 635 (3d Cir.
2017) (footnote omitted).
77
Hagy v. Demers & Adams, 882 F.3d 616, 623 (6th Cir. 2018).
78
141 S. Ct. 2190, 2200-02 (2021) (determining class action plaintiffs’ standing on claims
arising from TransUnion’s FCRA violations).
79
Id. at 2200 (holding 1,853 class members whose “misleading credit reports [were
provided] to third-party businesses” had “demonstrated concrete reputational harm and thus
had Article III standing,” while the remaining 6,332 did not).
80
Id. For more background about TransUnion LLC v. Ramirez and our extensive critique
of the decision, see Daniel J. Solove & Danielle Keats Citron, Standing and Privacy Harms:
A Critique of TransUnion v. Ramirez, 101 B.U. L. REV. ONLINE 62 (2021) [hereinafter Solove
& Citron, Standing and Privacy Harms].
81
TransUnion, 141 S. Ct. at 2200 (citing Spokeo, Inc. v. Robins, 578 U.S. 530, 341
(2016)).
82
See id. at 2217 (Thomas, J., dissenting) (“Where an individual sought to sue someone
for a violation of his private rights, . . . the plaintiff needed only to allege the violation. Courts
typically did not require any showing of actual damage.” (citation omitted))).
83
Solove & Citron, Standing and Privacy Harms, supra note 80, at 67-68 (critiquing
TransUnion’s reliance on “messy and inconsistent” common law that “is constantly
evolving”).

2022] PRIVACY HARMS 807
In the end, applying this test is difficult because the tradition of the common
law is complicated, nuanced, and ever-shifting. The Court in TransUnion
appeared to have a different conception of the tradition in mind, and other courts
will likely interpret the tradition in diverging ways. Ultimately, looking for a
close relationship to traditionally recognized harms leaves the door open for
courts to reach wildly different conclusions in cases. Standing doctrine in
privacy litigation will thus remain muddled and inconsistent.
B. Harm in Causes of Action
For plaintiffs in federal court, standing is just the first harm hurdle. The
second is showing harm as an element of claims alleged in the lawsuit.
Additionally, in state courts, although there is no constitutional standing
requirement,
84
most causes of action nevertheless have harm as one of the
elements. Different types of causes of action recognize cognizable harm
differently.
1. Contract Law
Contract law might seem to be a relevant body of law to regulate many
privacy issues, as many privacy violations involve organizations breaking
promises made in privacy policies.
85
These policies could be deemed contracts
or at least be subject to the doctrine of promissory estoppel. But, on the main,
courts have been reluctant to recognize privacy policies as contracts.
86
84
Salib & Suska, supra note 37, at 1169-72 (explaining states have “comparatively lax”
standing requirements because Article III does not apply (citing ASARCO Inc. v. Kadish, 490
U.S. 605, 617 (1989))).
85
See Bernard Chao, Privacy Losses as Wrongful Gains, 106 IOWA L. REV. 555, 559-64
(2021) (detailing various privacy policy violations by, inter alia, tech companies, retailers,
automobile producers, and nonprofits).
86
Courts have decided surprisingly few cases involving contract law theories for privacy
notices. Of those cases, few have held that privacy policies amount to enforceable contracts.
A group of academics published an empirical analysis of cases and concluded that many
courts were holding that privacy notices were contracts. See Oren Bar-Gill, Omri Ben-Shahar
& Florencia Marotta-Wurgler, Searching for the Common Law: The Quantitative Approach
of the Restatement of Consumer Contracts, 84 U. CHI. L. REV. 7, 28 (2017) (concluding that
“privacy policies are typically recognized as contracts”). These academics used their study
as part of their project with the American Law Institute, the Restatement of Consumer
Contracts. See id. at 8. However, Gregory Klass critiqued the study, finding that the cases
were incorrectly evaluated. See Gregory Klass, Empiricism and Privacy Policies in the
Restatement of Consumer Contract Law, 36 YALE J. ON REGUL. 45, 50, 67 (2019) (rejecting
Bar-Gill et al.’s conclusions because majority of cases upon which they relied did not classify
privacy policies as contracts and were decisions on motions to dismiss in federal district
courts). Klass found “little support” for any “trend towards contractual enforcement of privacy
notices.” See id. at 50 (quoting RESTATEMENT OF THE L. CONSUMER CONTS. § 1 Reporters’
Notes 15 (AM. L. INST., Discussion Draft No. 4 2017)). A subsequent analysis of the Bar-Gill
study sided with Klass. Adam J. Levitin, Nancy S. Kim, Christina L. Kunz, Peter Linzer,
Patricia A. McCoy, Juliet M. Moringiello, Elizabeth A. Renuart & Lauren E. Willis, The
Faulty Foundation of the Draft Restatement of Consumer Contracts, 36 YALE J. ON REGUL.

808 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Even if privacy policies were contracts, the plaintiffs would still lose due to
the absence of cognizable harm. Under contract law, courts typically require
harm amounting to economic loss.
87
Failing to fulfill promises made in privacy
policies and thus betraying people’s expectations has not counted as a
cognizable harm.
88
For example, in Smith v. Trusted Universal Standards in
Electronic Transactions, Inc.,
89
the court stated that the “[p]laintiff
must . . . plead loss flowing from the breach [of contract] to sustain a claim.”
90
In Rudgayzer v. Yahoo! Inc.,
91
the court held that “[m]ere disclosure of
[personal] information . . . without a showing of actual harm[] is insufficient” to
support a breach of contract claim.
92
2. Tort Law
Most tort claims require that plaintiffs establish harm.
93
As tort law developed
in the nineteenth century, a lively debate centered on whether tort law concerned
the recognition of wrongs or, alternatively, the redress of harms.
94
In The
Common Law, Oliver Wendell Holmes argued that tort law provided remedies
for activities “not because they are wrong, but because they are harms.”
95
Modern tort law has largely embraced the Holmesian approach.
96
The privacy torts grew out of Samuel Warren and Louis Brandeis’s influential
article in 1890, The Right to Privacy.
97
Warren and Brandeis primarily took a
447, 450 (2019) (noting authors’ own review of cases in which Klass disagreed with Bar-Gill
et al. led them to “conclude[] that Professor Klass’s readings were uniformly correct”).
87
Thomas B. Norton, Note, The Non-contractual Nature of Privacy Policies and a New
Critique of the Notice and Choice Privacy Protection Model, 27 FORDHAM INTELL. PROP.
MEDIA & ENT. L.J. 181, 193-94, 193 n.57 (citing numerous cases to show damages are “an
essential element of a breach of contract claim”).
88
See Joel R. Reidenberg, Privacy Wrongs in Search of Remedies, 54 HASTINGS L.J. 877,
881-84, 892-93 (2003) (framing thwarted expectations as privacy wrong and discussing lack
of judicial remedies for such wrongs).
89
No. 09-cv-04567, 2010 WL 1799456 (D.N.J. May 4, 2010).
90
Id. at *10.
91
No. 5:12-cv-01399, 2012 WL 5471149 (N.D. Cal. Nov. 9, 2012).
92
Id. at *6.
93
See JOHN C.P. GOLDBERG & BENJAMIN ZIPURSKY, RECOGNIZING WRONGS 28 (2020)
(“Every tort involves a person injuring another person in some way, or failing to prevent
another’s injury: every tort is an injury-inclusive wrong.”).
94
See John C.P. Goldberg, Unloved: Tort in the Modern Legal Academy, 55 VAND. L.
REV. 1501, 1505 n.15 (2002) (describing debates in nineteenth century concerning tort’s status
as a substantive area of law or merely “part of civil procedure and/or remedies”).
95
HOLMES, supra note 30, at 130.
96
See GOLDBERG & ZIPURSKY, supra note 93, at 5-6, 44 (noting Holmesian pragmatism,
including concept that purpose of tort law is to compensate victims for losses, is modern view
of many academics). There is a robust and important literature on tort law as the recognition
of wrongs. See generally id.
97
Samuel D. Warren & Louis D. Brandeis, The Right to Privacy, 4 HARV. L. REV. 193
(1890); see also Danielle Keats Citron, Mainstreaming Privacy Torts, 98 CALIF. L. REV. 1805,

2022] PRIVACY HARMS 809
rights-based approach rather than a harms-based approach to privacy,
conceiving of privacy as the protection of “individuals’ ability to develop their
‘inviolate’ personalities without unwanted interference.”
98
The judicial
development of the privacy torts can be attributed to William Prosser, the
leading torts scholar of the twentieth century, who played an enormous role in
mainstreaming and legitimizing the privacy torts.
99
Prosser made the turn to harm explicitly and clearly, and courts followed suit.
In 1960, in an article entitled Privacy, Prosser summed up a scattered body of
case law to identify four torts: (1) “Intrusion upon the plaintiff’s seclusion”;
(2) “Public disclosure of embarrassing private facts about the plaintiff”;
(3) “Publicity which places the plaintiff in a false light in the public eye”;
(4) “Appropriation, for the defendant’s advantage, of the plaintiff’s name or
likeness.”
100
As chief reporter on the influential American Law Institute’s
Restatement (Second) of Torts, Prosser added the four categories of privacy torts
to the Restatement.
101
Prosser followed the Holmesian harms-based approach in
constructing the privacy torts.
102
After Prosser’s article and the Restatement,
courts readily embraced the privacy torts.
103
Although Prosser strengthened the
privacy torts, his work ossified them.
104
No new privacy torts have been created
in the years following Prosser’s shining the spotlight on them.
1820-21 (2010) [hereinafter Citron, Privacy Torts] (“Shortly after the publication of The Right
to Privacy, courts adopted privacy torts in the manner that Warren and Brandeis suggested.”
(citing Edward J. Bloustein, Privacy as an Aspect of Human Dignity: An Answer to Dean
Prosser, 39 N.Y.U. L. REV. 962, 977, 979 (1964))).
98
Citron, Privacy Torts, supra note 97, at 1820 (quoting Warren & Brandeis, supra note
97, at 205).
99
Id. at 1809-10 (discussing Prosser’s theory of four privacy torts in Restatement (Second)
of Torts and its subsequent adoption by courts); Neil M. Richards & Daniel J. Solove,
Prosser’s Privacy Law: A Mixed Legacy, 98 CALIF. L. REV. 1887, 1888-90, 1917 (2010)
[hereinafter Richards & Solove, Prosser’s Privacy Law].
100
William L. Prosser, Privacy, 48 CALIF. L. REV. 383, 388-89 (1960) (identifying four
privacy torts from “over three hundred cases in the books”).
101
Richards & Solove, Prosser’s Privacy Law, supra note 99, at 1890 (“[Prosser] was also
the chief reporter for the Second Restatement of Torts, in which he codified his scheme for
tort privacy.”).
102
Citron, Privacy Torts, supra note 97, at 1821-24 (discussing Prosser’s adoption of
“Holmes’s focus on specific injuries caused by particular conduct”).
103
Richards & Solove, Prosser’s Privacy Law, supra note 99, at 1903-04 (observing
Prosser’s work on privacy torts in the span of four decades “transformed” privacy law “from
a curious minority rule to . . . a doctrine recognized by the overwhelming majority of
jurisdictions”).
104
Id. at 1904-07 (arguing Prosser’s efforts to ensure acceptance of his theory “fossilized
[tort privacy] and eliminated its capacity to change and develop”); see also G. EDWARD
WHITE, TORT LAW IN AMERICA: AN INTELLECTUAL HISTORY 175-76 (1980) (describing
development of Prosser’s privacy torts as “[a] classification made seemingly for convenience”
in 1941 that ultimately, by 1971, had become “synonymous with law”).

810 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Today, nearly all states recognize most of the privacy torts.
105
Courts rarely
question the existence of harm or the fact that the basis of harm for many privacy
torts is pure emotional distress. In fact, they tend to presume the existence of
harm.
106
And yet while the privacy torts handily address the privacy problems
of Warren and Brandeis’s time, such as invasions of privacy by the media, this
is not the case for modern privacy problems involving the collection, use, and
disclosure of personal data. Because courts cling rigidly to the elements of the
privacy torts as set forth in the Restatement, the privacy torts have little
application to contemporary privacy issues.
107
Other mainstream torts have been invoked to address privacy issues, such as
intentional infliction of emotional distress, breach of confidentiality, and
negligence. These torts are often limited by harm requirements, making it
difficult for plaintiffs to obtain redress. For example, the intentional infliction of
emotional distress tort requires proof of “severe emotional distress,” which can
be difficult to establish.
108
3. Statutory Causes of Action
Many state and federal privacy statutes provide for private rights of action.
Typically, the assumption is that a private right of action is a legislative
recognition of harm, though no rule or doctrine commands that all private rights
of action in statutes redress harm. Some might be there to facilitate private
enforcement of a law or to deter violations.
Countless federal and state privacy laws have private rights of action. At the
federal level, notable laws with private rights of action include the Telephone
Consumer Protection Act (“TCPA”), the Electronic Communications Privacy
Act, the Video Privacy Protection Act (“VPPA”), the FCRA, and the Cable
105
Richards & Solove, Prosser’s Privacy Law, supra note 99, at 1904 (“Today, due in
large part to Prosser’s influence, his ‘complex’ of four torts is widely accepted and recognized
by almost every state.” (citing ROBERT M. O’NEIL, THE FIRST AMENDMENT AND CIVIL
LIABILITY 77 (2001))).
106
Solove & Citron, Risk and Anxiety, supra note 27, at 768-70.
107
Citron, Privacy Policymaking, supra note 8, at 798 (“Overly narrow interpretations of
the privacy torts—intrusion on seclusion, public disclosure of private fact, false light, and
misappropriation of image—have prevented their ability to redress data harms.”); Citron,
Privacy Torts, supra note 97, at 1826-31 (arguing privacy torts fail to address modern data
breaches and leaks and preclude recovery with high burdens of proof).
108
See RESTATEMENT (SECOND) OF TORTS § 46 (AM. L. INST. 1965) (recognizing liability
for “[o]ne who by extreme and outrageous conduct intentionally or recklessly causes severe
emotional distress to another”). This tort was of particular interest to Prosser, who wrote a
key article about it in 1939. William L. Prosser, Intentional Infliction of Mental Suffering: A
New Tort, 37 MICH. L. REV. 874 (1939). In the first edition of his treatise on tort law, published
in 1941, Prosser noted that “the law has been slow to accept the interest in peace of mind as
entitled to independent legal protection, even against intentional invasions. It is not until
comparatively recent years that there has been any general admission that the infliction of
mental distress, standing alone, may serve as the basis of an action, apart from any other tort.”
WILLIAM L. PROSSER, HANDBOOK OF THE LAW OF TORTS 54 (1941).

2022] PRIVACY HARMS 811
Communications Policy Act, among others.
109
At the state level, the California
Consumer Privacy Act has a private right of action, but only for data security
breaches.
110
Several state unfair and deceptive acts and practices laws (called
“UDAP” laws) have private rights of action.
111
The Illinois Biometric
Information Privacy Act (“BIPA”) also has a private right of action.
112
Congress has recognized statutory damages for these private rights.
113
Under
the FCRA, the federal law at issue in Spokeo,
114
any person who willfully
violates “any requirement” in the statute is liable in an amount equal to the sum
of damages sustained by the consumer or “damages of not less than $100 and
not more than $1,000.”
115
There is no harm requirement in the Wiretap Act, the
109
Telephone Consumer Protection Act, Pub. L. No. 102-243, 105 Stat. 2399 (1991)
(codified as amended at 47 U.S.C. § 277(c)(5)); Electronic Communications Privacy Act,
Pub. L. No. 99-508, 100 Stat. 1854 (1986) (codified as amended at 18 U.S.C. §§ 2520
(Wiretap Act), 2707 (Stored Communications Act)); Video Privacy Protection Act, Pub. L.
No. 100-618, 102 Stat. 3196 (1998) (codified as amended at 18 U.S.C. § 2710(c)); Fair Credit
Reporting Act, Pub. L. No. 91-508, 84 Stat. 1114 (1970) (codified as amended at 15 U.S.C.
§§ 1681n, 1681o) (providing cause of action to any consumer harmed by willful or negligent
violation, respectively); Cable Communications Policy Act, Pub. L. No. 98-549, 98 Stat. 2795
(1984) (codified as amended at 47 U.S.C. § 551(f)). For a more complete list of federal laws
with private rights of action, see DANIEL J. SOLOVE & PAUL M. SCHWARTZ, PRIVACY LAW
FUNDAMENTALS 160-61 (5th ed. 2019).
110
California Consumer Privacy Act, CAL. CIV. CODE § 1798.150 (West 2022) (providing
private right to of action to “[a]ny consumer” for breach of personal information “as a result
of the business’s violation of the duty to implement and maintain reasonable security
procedures”).
111
See Citron, Privacy Policymaking, supra note 8, at 798 (discussing applicability of
private UDAP actions to privacy claims). Many UDAP laws require or have been interpreted
to require a showing of injury. Id. at 754. Almost half of state UDAP laws restrict claims for
intangible injuries. See CAROLYN CARTER, CONSUMER PROTECTION IN THE STATES: A 50-
STATE EVALUATION OF UNFAIR AND DECEPTIVE PRACTICES LAWS 2, 40 (2018),
https://www.nclc.org/images/pdf/udap/udap-report.pdf [https://perma.cc/R9UY-RGWZ]
(noting that twenty-one states do not recognize intangible injuries under UDAP laws, and
twenty-two require economic loss).
112
Illinois Biometric Information Privacy Act, 740 ILL. COMP. STAT. 14/20 (2022)
(providing private right of action to “[a]ny person aggrieved by a violation of this Act”).
113
The meaning of a private right of action with statutory damages is debatable. Is a private
right of action a recognition of harm, with the statutory damages being imposed because harm
can be difficult for plaintiffs to establish? Or is the purpose of the statutory damages to enable
recovery in the absence of any harm because of other goals? Either way, the presence of
statutory damages means that courts do not have to hold bench or jury trials on the question
of recovery—lawmakers have supplied their judgment as to the appropriate extent of redress.
114
15 U.S.C. § 1681a(d)(1)(A)-(C), 1681b (regulating creation and use of consumer
reports by consumer reporting agencies for credit transactions, insurance, licensing,
consumer-initiated business transactions, and employment); see also Spokeo, Inc. v. Robins,
578 U.S. 330, 334-35 (2016) (discussing § 1681a(d)(1)(A)-(C) and § 1681b).
115
15 U.S.C. § 1681n(a)(1)(A).

812 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Stored Communications Act, the DPPA, the VPPA, and the Cable
Communications Policy Act.
116
The Supreme Court has complicated recovery under these private rights of
action by forcing plaintiffs to prove harm even though the statutes provide for
statutory damages. For example, the Supreme Court has made recovery of
damages under the federal Privacy Act exceedingly difficult. In Doe v. Chao,
the U.S. Department of Labor improperly disclosed the Social Security Numbers
of people filing for benefits under the Black Lung Benefits Act. A group of
plaintiffs sued under the Privacy Act. The lead plaintiff stated that he was
“torn . . . all to pieces” by the disclosure and was “greatly concerned and
worried.”
117
The U.S. Supreme Court held that the statutory damages provision
under the Privacy Act was only available if plaintiffs established actual
damages.
118
In a subsequent case, Federal Aviation Administration v. Cooper, the
Supreme Court held that emotional distress alone could not amount to actual
damages under the Privacy Act of 1974.
119
Justice Sotomayor dissented, joined
by Justices Ginsburg and Breyer. They argued that Congress passed the Privacy
Act to protect against an agency’s disclosure of personal information that could
result in “substantial harm, embarrassment, inconvenience, or unfairness to any
individual.”
120
The result of the Court’s holding was that a “federal agency could
intentionally or willfully forgo establishing safeguards to protect against
embarrassment and no successful private action could be taken against it for the
harm Congress identified.”
121
The overall effect of Chao and Cooper has been to drastically limit the
enforcement of the Privacy Act through private rights of action. Plaintiffs now
have to prove willful conduct as well as establish harm, and they are forbidden
from using emotional distress, which is a common type of harm in privacy
cases.
122
Congress created the private right of action with statutory damages as
an enforcement mechanism in the law, but the Court effectively nullified it. The
Privacy Act now has few enforcement actions.
Even when federal statutes do not mention having to prove damages, some
courts have taken it upon themselves to add a requirement of harm. Consider
116
Wiretap Act, 18 U.S.C. §§ 2510-2522; Stored Communications Act, 18 U.S.C.
§§ 2701-2709; Driver’s Privacy Protection Act, 18 U.S.C. §§ 2721-2725; Video Privacy
Protection Act, 18 U.S.C. § 2710; Cable Communications Policy Act, 47 U.S.C. §§ 521-573.
117
Doe v. Chao, 540 U.S. 614, 617-18 (2004).
118
Id. at 614; see Calo, Privacy Harm Exceptionalism, supra note 3, at 362-63 (discussing
the Court’s refusal to recognize emotional harm as a basis for statutory damages under Privacy
Act).
119
566 U.S. 284, 299 (2012) (“[The Court] adopt[s] an interpretation of ‘actual damages’
limited to proven pecuniary or economic harm.”).
120
Id. at 309 (Sotomayor, J., dissenting) (quoting 5 U.S.C. § 552a(e)(10)) (discussing
requirements for agencies under Privacy Act).
121
Id.
122
Calo, Privacy Harm Exceptionalism, supra note 3, at 362-63.

2022] PRIVACY HARMS 813
Senne v. Village of Palatine. In that case, the Seventh Circuit held that a plaintiff
could not pursue a private cause of action for a violation of the DPPA because
the plaintiff could not demonstrate injury.
123
The Village of Palatine had a
practice of including identifying information, such as people’s height and
weight, on parking tickets placed under their windshield wipers. Although the
Village’s practice was a clear DPPA violation, the court concluded that “we need
to balance the utility (present or prospective) of the personal information on a
parking ticket against the potential harm.”
124
The court acknowledged that “the
Act does not state that a permissible use can be offset by the danger that the use
will result in a crime or tort,” yet it created a harm requirement anyway.
125
The
court struck down the right to sue under the DPPA because the plaintiff failed to
provide evidence of harm, such as “stalking or any other crime (such as identity
theft),” “tort (such as invasion of privacy),” disclosure over the Internet, or the
involvement of “highly sensitive information” like a social security number.
126
Through interpretations like these, coupled with standing, courts are
undercutting the enforcement of privacy laws by creating harm requirements out
of whole cloth. Courts are generally supposed to be deferential to the legislative
policy goals, striking down laws only when they traduce a constitutional
boundary or infringe upon a right. But courts are trading deference for activism,
undermining laws in an underhanded way. Harm requirements are being
invented to prevent the enforcement of privacy protections.
To sum up, courts have blocked statutory private rights of action by:
(1) adding a requirement for harm via standing; (2) interpreting statutes with
statutory damages in ways that require proof of harm to obtain statutory
damages, thus undercutting the purpose of statutory damages provisions;
(3) interpreting statutory private rights of action to require harm even when they
do not have a harm requirement; and (4) adopting narrow conceptions of
cognizable harm to exclude many types of harm.
The enforcement of privacy laws is a challenging issue, and unfortunately,
courts are making a mess of things. Courts often lack a theory of privacy harms
or any guiding principles. As Lauren Scholz observes, in many cases, the
“analysis as to why a harm is not present is often superficial or absent.”
127
Decisions involving harm lack a coherent vision; they are creating mischief
rather than good policy.
C. Harm in Regulatory Enforcement Actions
Regulators are often much less constrained by harm requirements. In many
cases, the laws that they enforce do not require harm. The enforcement of
123
Senne v. Village of Palatine, 784 F.3d 444, 448 (7th Cir. 2015).
124
Id. at 447.
125
Id.
126
Id. at 448.
127
Lauren Henry Scholz, Privacy Remedies, 94 IND. L.J. 653, 662-63 (2019).

814 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
statutes by regulators often occurs outside of the judicial system, so the issue of
harm never arises.
128
However, there are circumstances where harm is a requirement for regulators
to enforce, most notably Federal Trade Commission (“FTC”) enforcement of
“unfair” acts or practices. Since the mid-1990s, the FTC has used its
enforcement power under section 5 of the FTC Act to address privacy issues.
129
Section 5 of the FTC Act prohibits “unfair or deceptive acts or practices in or
affecting commerce.”
130
A “deceptive” act or practice is a “representation,
omission or practice that is likely to mislead a consumer . . . . acting reasonably
in the circumstances . . . . to the consumer’s detriment.”
131
There is no mention
of harm in this definition, though it does indicate that the deception must be to
the “detriment” of the consumer.
The definition of unfairness is much more directly focused on harm. An
“unfair” act or practice is one that “causes or is likely to cause substantial injury
to consumers which is not reasonably avoidable by consumers themselves and
not outweighed by countervailing benefits to consumers or to competition.”
132
This definition explicitly includes “likely” harm. The FTC recognizes traditional
harms (and risks of such harms) such as economic and physical harms, but “more
subjective types of harm” such as emotional harm are usually not considered
substantial for unfairness purposes.
133
On the other hand, the FTC is able to
focus on harm to consumers generally, which allows it to look to harm in a
broader manner than most tort and contracts cases, which involve specific
individuals.
Although regulators are less constrained by the requirement of harm, they are
often limited in resources and must be highly selective about the matters they
enforce.
134
State attorneys general vary considerably on how actively they
128
See, e.g., A Brief Overview of the Federal Trade Commission’s Investigative, Law
Enforcement, and Rulemaking Authority, FTC, https://www.ftc.gov/about-ftc/what-we-
do/enforcement-authority [https://perma.cc/LQD3-YA7L] (last updated May 2021) (noting
that FTC may initiate enforcement action using either administrative or judicial process).
129
See Ryan P. Blaney, David A. Munkittrick & Brooke Gottlieb, Federal Trade
Commission Enforcement of Privacy, in PROSKAUER ON PRIVACY: A GUIDE TO PRIVACY AND
DATA SECURITY LAW IN THE INFORMATION AGE § 4:1 (Kristen J. Mathews ed., 2016)
(identifying section 5 as FTC’s primary means for taking action against privacy violations);
FTC, PREPARED STATEMENT OF THE FEDERAL TRADE COMMISSION: OVERSIGHT OF THE
FEDERAL TRADE COMMISSION 4 (2018), https://www.ftc.gov/system/files/documents/public
_statements/1423835/p180101_commission_testimony_re_oversight_senate_11272018_0.p
df [https://perma.cc/Y7TJ-2STS] (“Beginning in the mid-1990s, with the development of the
Internet as a commercial medium, the FTC expanded its focus on privacy . . . .”).
130
15 U.S.C. § 45(a)(1).
131
FTC, FTC POLICY STATEMENT ON DECEPTION (1983), appended to Cliffdale Assocs.,
Inc., 103 F.T.C. 110, 174 (1984).
132
15 U.S.C. § 45(n); see also FTC, FTC POLICY STATEMENT ON UNFAIRNESS (1980),
appended to Int’l Harvester Co., 104 F.T.C. 949, 1070 (1984).
133
FTC POLICY STATEMENT ON UNFAIRNESS, supra note 132, at 1073.
134
Citron, Privacy Policymaking, supra note 8, at 799.

2022] PRIVACY HARMS 815
enforce; some are aggressive whereas others have not brought any enforcement
actions under many privacy laws that they are authorized to enforce.
135
Because of these limitations, many privacy laws rely upon private litigants
for enforcement. The TCPA is a prime example of this type of enforcement
mechanism. The law restricts unsolicited commercial telemarketing calls,
robocalls, and faxes, and it is enforced by the Federal Communications
Commission (“FCC”) and state attorneys general.
136
To augment this
enforcement, the law includes a private right of action with statutory damages
of $500 for each violation and $1,500 for each knowing or willful violation.
137
Because the TCPA enforcement process is tedious and time-consuming and
because many TCPA cases involve small matters that do not make splashy
headlines, FCC enforcement has been modest.
138
In one year, for example, there
were 47,704 complaints, but the FCC only issued twenty-three citations.
139
In
practice, private litigation has become the primary source of TCPA
enforcement.
140
Litigation by private parties thus supplements enforcement by regulatory
agencies and state attorneys general, and in a number of instances, private
litigation serves as the primary enforcement mechanism of a law. Based on this
enforcement role, private parties enforcing a law through private litigation are
often referred to as “private attorneys general.”
141
As the Seventh Circuit aptly
explained:
The award of statutory damages could also be thought a form of bounty
system, and Congress is permitted to create legally enforceable bounty
systems for assistance in enforcing federal laws, provided the bounty is a
reward for redressing an injury of some sort (though not necessarily an
injury to the bounty hunter).
142
And these cases typically require a showing of harm, which is often the death
knell if plaintiffs cannot show financial or physical harm.
135
Id. at 755 (“In the past fifteen years, a core group of states have taken the lead on
privacy enforcement: California, Connecticut, Illinois, Indiana, Maryland, Massachusetts,
New Jersey, New York, North Carolina, Ohio, Pennsylvania, Texas, Vermont, and
Washington.”).
136
See 47 U.S.C. § 227(c)(3); see also Spencer Weber Waller, Daniel B. Heidtke & Jessica
Stewart, The Telephone Consumer Protection Act of 1991: Adapting Consumer Protection to
Changing Technology, 26 LOY. CONSUMER L. REV. 343, 358 (2014).
137
47 U.S.C. § 227(c)(5).
138
Waller et al., supra note 136, at 376-78.
139
Id. at 378.
140
Id. at 375 (“Private parties have largely been responsible for enforcement of the
TCPA.”).
141
See William B. Rubenstein, On What a “Private Attorney General” Is—and Why It
Matters, 57 VAND. L. REV. 2129, 2130 (2004).
142
Crabill v. Trans Union, L.L.C., 259 F.3d 662, 665 (7th Cir. 2001).

816 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
II. THE CHALLENGES OF PRIVACY HARMS
Privacy harms present several challenges that make their recognition
difficult.
143
One challenge is that many privacy harms are small and caused by a
multitude of actors. Privacy harms often involve increased risk of future harm,
and the law struggles mightily to grapple with the concept of risk.
144
Finally,
privacy harms often have a significant societal dimension, and the law
(especially in litigation) often has a highly individualistic focus.
A. Aggregation of Small Harms
A major complicating dimension of many privacy harms is that they are small
but numerous. When these harms happen to an individual repeatedly by different
actors, they become significantly more harmful. For example, receiving an
unwanted email is a minor inconvenience. Receiving hundreds of unwanted
emails becomes a major imposition and distraction.
Another aspect of this difficulty is that sometimes an organization will cause
a very small amount of harm but on a very large scale—to hundreds of thousands
or even millions of people. From the standpoint of each individual, the harm is
minor, but from the standpoint of society, where the harm to everyone is
aggregated, the total amount of harm is quite substantial.
Privacy harms often involve the aggregation of many small harms to each
individual, which is compounded by the aggregation of all these harms to many
individuals.
145
The result makes privacy violations large-scale problems that
cause a significant societal impact but do not readily fit into the traditional way
the law assesses harm.
FTC enforcement has successfully addressed this problem. In its policy
statement about unfairness injury, the FTC noted: “An injury may be sufficiently
substantial . . . if it does a small harm to a large number of people, or if it raises
a significant risk of concrete harm.”
146
However, when it comes to private litigation, for each individual, bringing a
lawsuit for a small harm is not worth the time or resources.
147
Class actions are
the predominant way to address this problem. They enable people to aggregate
143
See Ignacio N. Cofone & Adriana Z. Robertson, Privacy Harms, 69 HASTINGS L.J.
1039, 1041 (2018) (noting that “privacy harms are hard to pin down”).
144
Solove & Citron, Risk and Anxiety, supra note 27, at 751.
145
Daniel J. Solove, Privacy Self-Management and the Consent Dilemma, 126 HARV. L.
REV. 1880, 1890 (2013) [hereinafter Solove, Privacy Self-Management] (“[L]ittle bits of
innocuous data can say a lot in combination.”).
146
FTC POLICY STATEMENT ON UNFAIRNESS, supra note 132, at 1073 n.12 (“An injury may
be sufficiently substantial, however, if it does a small harm to a large number of people, or if
it raises a significant risk of concrete harm.”).
147
Eric Goldman, The Irony of Privacy Class Action Litigation, 10 J. TELECOMMS. & HIGH
TECH. L. 309, 313 (2012) (discussing cost-benefit analysis of individual lawsuits versus class
actions).

2022] PRIVACY HARMS 817
their small harms into a single lawsuit that is large enough to justify the costs of
litigation.
Class actions, however, are an imperfect vehicle to address privacy problems.
Cases often quickly settle because litigation expenses are high. The lawyers
often earn significant sums, maximizing their own financial interests.
148
Many
class actions become the equivalent of a shake down, with companies paying the
lawyers to go away.
If class actions do not settle, then there is another problem. Companies have
data on millions or billions of people, and even small damages can add up to
enormous sums that can put companies out of business. These sums can become
disproportionate to what the company did wrong. As we have previously stated,
“Judges are reluctant to recognize harm because it might mean bankrupting a
company just to give each person a very tiny amount of compensation.”
149
B. Risk: Unknowable and Future Harms
In many cases, the harm is not fully knowable, and the law struggles greatly
to address these situations. We explored this challenge for data breach harms in
Risk and Anxiety: A Theory of Data Breach Harms.
150
In that article, we noted
that a major complication in recognizing harm from a data breach is that often
plaintiffs have not yet suffered from identity theft or fraud.
151
Plaintiffs argue
that they suffer harm in the form of a future risk of injury. Courts are inconsistent
in recognizing future risk of injury as a cognizable harm.
152
Risk is involved with many different types of privacy harm. A credit report
with inaccurate information—like denoting someone as a terrorist as in
TransUnion LLC v. Ramirez
153
—poses a significant risk of economic and
reputational harm. Online posts that include someone’s home address present a
risk of physical attack. And yet even with privacy harms that courts widely
recognize, such as physical, economic, and reputational harms, courts are
reluctant to recognize them when there is only a risk that they will occur.
Privacy harms often not only involve a future risk of injury but also are
compounded by an additional dimension of complexity: the range of possible
future injuries is much more varied. To fully understand the implications of the
collection, use, or disclosure of personal data, one must know about the future
uses to which the data will be put. For example, if Company A improperly
discloses personal data to Company B, the harm will depend upon what
Company B does with the data. Company B might not immediately use the data
148
Id. at 314 (“[C]lass action lawyers often advance their own financial interests at the
expense of the class members’ interests.”).
149
Solove & Citron, Risk and Anxiety, supra note 27, at 783.
150
Id. at 750.
151
See id.
152
Id. at 739.
153
141 S. Ct. 2190, 2200 (2021).

818 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
in a harmful way and might not do so until after the statute of limitations expires.
Company B might never use the data in a harmful way.
Privacy harms are highly contextual, with the harm depending upon how the
data is used, what data is involved, and how the data might be combined with
other data. Sharing an innocuous piece of data with another company might
provide a key link to other data or allow for certain inferences to be made.
Because of these difficulties, many privacy statutes use statutory damages. It
is far easier to enforce laws with statutory damages than to try to figure out the
harm that would involve future uses that may or may not occur. Through
standing doctrine and cases like Spokeo and TransUnion, however, courts are
undermining statutory damages provisions by forcing tired old judicial concepts
of harm into the enforcement of these statutes. For cases not involving statutes
with statutory damages, harm can become quite a speculative matter if there is
uncertainty in one of two dimensions—the possibility of harm and the nature of
harm.
C. Individual vs. Societal Harms
Privacy harms often involve injury not just to individuals but to society.
Several scholars have argued that privacy is “constitutive” of society.
154
As Joel
Reidenberg contends, “Society as a whole has an important stake in the contours
of the protection of personal information.”
155
Robert Post argues that the privacy
torts promote “rules of civility that in some significant measure constitute both
individuals and community.”
156
According to Julie Cohen, privacy protects
individual autonomy and creativity that are essential for society to develop a rich
culture.
157
Paul Schwartz contends that privacy is essential to democracy and
freedom.
158
These considerations are often omitted from the law’s evaluation of harm
because they do not fit the individualistic focus that courts have for cognizable
harm. Although certain lawsuits seek mainly to vindicate individual interests,
154
See, e.g., PRISCILLA M. REGAN, LEGISLATING PRIVACY: TECHNOLOGY, SOCIAL VALUES,
AND PUBLIC POLICY 20 (1995) (arguing that privacy should be understood in terms of its social
benefits); Spiros Simitis, Reviewing Privacy in an Information Society, 135 U. PA. L. REV.
707, 709 (1987) (“[P]rivacy considerations no longer arise out of particular individual
problems; rather, they express conflicts affecting everyone.”).
155
Reidenberg, supra note 88, at 882-83. We have both emphasized the societal
significance of privacy in our separate scholarship. See generally DANIELLE KEATS CITRON,
HATE CRIMES IN CYBERSPACE (2014) [hereinafter CITRON, HATE CRIMES] (emphasizing
privacy’s inextricable relationship with equality); Danielle Keats Citron, Sexual Privacy, 128
YALE L.J. 1870 (2019); SOLOVE, UNDERSTANDING PRIVACY, supra note 28.
156
Robert C. Post, The Social Foundations of Privacy: Community and Self in the Common
Law Tort, 77 CALIF. L. REV. 957, 959 (1989).
157
Julie E. Cohen, Examined Lives: Informational Privacy and the Subject as Object, 52
STAN. L. REV. 1373, 1427 (2000).
158
Paul M. Schwartz, Privacy and Democracy in Cyberspace, 52 VAND. L. REV. 1609,
1613 (1999).

2022] PRIVACY HARMS 819
many group lawsuits (such as class actions) also seek to protect broader societal
interests. Courts, however, often still fail to consider the societal impact of
privacy harms even in these cases.
159
III. REALIGNING PRIVACY ENFORCEMENT AND REMEDIES
With the law’s relentless focus on privacy harms, it is easy to overlook the
broader challenges afoot. Privacy harms are just a piece of a larger pie involving
the enforcement of privacy law. In addition to the question of what should
constitute cognizable privacy harm, we should also ask whether privacy harm
should even be required in particular circumstances. In many cases, harm is
irrelevant to the purposes of the litigation. To determine when privacy harm is
an issue that should even be part of a case, we must answer a broader overarching
question: When and how should privacy law be enforced?
Many of the law’s difficulties with handling privacy cases are due to
misalignments between enforcement goals and remedies. Configuring the proper
alignment will make the law more coherent and effective.
Privacy law enforcement has three predominant goals:
(1) Compensation—awarding monetary damages to people who have been
harmed;
(2) Deterrence—preventing future violations of the law; and
(3) Equity—making things right by means other than compensation.
Problems emerge when a remedy is misaligned with an enforcement goal. For
example, monetary damages are a proper remedy when compensation is the
goal. They are not a well-tailored remedy when deterrence or equity is the goal.
The law becomes messy and riddled with problems when it insists upon a single
remedy to address a multitude of goals. It is understandable why the law tries to
do this: sometimes multiple enforcement goals exist in the same case. If that is
so, then the law should address all of those goals. But trying to use a remedy
well suited for one goal but poorly suited for another is a recipe for failure.
An analogy can deepen our understanding of the point. A wrench is a great
tool for unscrewing a nut. One could also try to use a wrench to hammer in a
nail, but a wrench is a poor tool to use, as it might cause damage. The nail
requires a hammer for its installation. The law is akin to a bad repair person: it
is constantly trying to use the wrong tools to achieve enforcement goals. Just
because in a given situation there is a nut to unscrew and a nail to be hammered
does not mean that only a wrench or a hammer should be used. Both tools should
be used.
This point might seem obvious, but the law almost entirely misses it. Modern
tort law is premised on the notion that lawsuits to compensate people with
damages can also double as a means to achieve deterrence. Of course, it is
certainly true that compensatory damages can further the goal of deterrence, but
159
Solove & Citron, Risk and Anxiety, supra note 27, at 785.

820 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
this is akin to the use of the wrench to hammer in the nail—the wrench can be
used, but it is the wrong tool, and it will not work optimally. In privacy cases,
because of the challenging nature of privacy harms, the misfit in tools is
exacerbated.
A. The Goals of Enforcement
Understanding the goals of enforcement is essential to making progress
toward the effective enforcement of privacy law. Compensation involves
awarding a plaintiff with monetary damages to provide redress for wrongful
harm. The typical tort rule accords with this rationale by awarding damages
equal to a victim’s loss.
160
Corrective justice theory embraces an Aristotelian
concept of justice that requires injurers to make victims whole.
161
The goal is to
hold actors responsible for losses that they wrongfully caused.
162
Deterrence involves imposing a penalty that deters future wrongdoing.
Specific deterrence involves deterring wrongdoing by the particular wrongdoer
against whom enforcement is sought. General deterrence involves deterring
wrongdoing by other actors. The penalty imposed on a particular wrongdoer will
serve as a lesson to teach others to avoid wrongdoing. Many organizations will
only take laws seriously when there are likely and painful consequences for
failing to comply.
Equity involves righting wrongs in situations where compensation is not an
adequate way of addressing them. Equitable remedies aim to restore things to
their original state before the wrongdoing or to otherwise help fix situations
where damages will not. The law has a number of equitable remedies, such as
injunctions and specific performance.
163
B. Aligning Remedies with Goals
1. The Problem of Misalignment
The law suffers when it fails to align appropriate remedies with enforcement
goals. When compensation is the enforcement goal, compensatory damages are
the appropriate remedy, and these damages are based on harm. When deterrence
is the enforcement goal, private rights of action enable “private attorneys
160
See JULES L. COLEMAN, RISKS AND WRONGS 201 (1992).
161
Id. at 320 (explaining corrective justice “imposes the duty to repair the wrongs one
does”); ERNEST J. WEINRIB, THE IDEA OF PRIVATE LAW 56-57 (1995) (noting Aristotle’s
account of corrective justice involves “the direct transfer of resources from one party to the
other” representing plaintiff’s wrongful injury and defendant’s wrongful act).
162
COLEMAN, supra note 160, at 324 (“The duty of wrongdoers in corrective justice is to
repair the wrongful losses for which they are responsible.”).
163
One of us (Citron) has argued that injunctive relief is crucial for what it will say and do
for victims of intimate privacy violations. Danielle Keats Citron, Privacy Injunctions, EMORY
L.J. (forthcoming 2022) (manuscript at 11).

2022] PRIVACY HARMS 821
general” to enforce a law.
164
In such cases, compensatory damages are not
relevant. The remedy should be an amount that provides optimal general and
specific deterrence. When equity is the enforcement goal, appropriate equitable
remedies should be used. Harm should not be required. The main issue should
be whether there is a problem that can be fixed or ameliorated with legal
intervention.
Tort law attempts to achieve both the goals of compensation and deterrence
simultaneously. This attempt to do both might seem efficient, but the goals
differ. For example, when lawsuits are tied to compensatory damages, the
existence of liability insurance can complicate the goal of deterrence. When the
magnitude of the defendant’s insurance premiums does not track the magnitude
of the defendant’s liabilities, the threat of liability may fall short of promoting
optimal deterrence because the defendant can externalize the risk of liability
through the purchase of insurance.
On the flip side, liability for compensatory damages can be far greater than is
optimal for deterrence. Compensation even for very small harms can become
outsized if multiplied by millions of people. Deterrence is the more meaningful
goal, and compensation in these instances might be counterproductive. For
example, providing a few cents to a billion individuals might do little for their
social welfare, but could put companies out of business. It might result in
overdeterrence, leading companies to abandon socially beneficial personal data
practices.
2. The Value of Private Enforcement
In many instances, private litigation is used primarily as a vehicle to enforce
a law and thus to deploy law’s deterrence power. Legislatures often include a
private right of action in statutes so that plaintiffs acting as “private attorneys
general” will help enforce the law. The goal is to increase enforcement to deter
violations. In such cases, compensation is a secondary goal or a goal in only a
small number of cases. As the Illinois Supreme Court noted in Rosenbach v. Six
Flags Entertainment Corp.
165
regarding the Illinois BIPA, harm is not a
requirement of the statute, and the legislature included the private right of action
not just to compensate plaintiffs but because it is “integral to implementation of
the legislature’s objectives” to deter BIPA violations.
166
In other words, the
redress provides an incentive for plaintiffs and counsel to enforce the law—not
for compensation’s sake but for deterrence.
164
Solove & Citron, Standing and Privacy Harms, supra note 80, at 70 (noting private
rights of action “deputize ‘private attorneys general’” to help enforce law).
165
2019 IL 123186.
166
Id. ¶ 37 (“When private entities face liability for failure to comply with the law’s
requirements . . . those entities have the . . . incentive to conform to the law and prevent
problems before they occur and cannot be undone.”).

822 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Some courts, however, miss the point about private attorneys general. For
example, in Stoops v. Wells Fargo Bank, N.A.,
167
plaintiff Melody Stoops bought
thirty-five cell phones to try to ensnare companies that made telemarketing calls
in violation of the TCPA. The TCPA provides penalties of $500 for each
violation with penalties trebled for willful or knowing violations.
168
The court
dismissed her case for lack of harm: “Plaintiff’s privacy interests were not
violated when she received calls from Defendant. . . . Because Plaintiff has
admitted that her only purpose in using her cell phones is to file TCPA lawsuits,
the calls are not ‘a nuisance and an invasion of privacy.’”
169
According to the
court, “Plaintiff has not suffered an injury-in-fact because her privacy and
economic interests were not violated when she received calls from
Defendant.”
170
The court reasoned that “it cannot reasonably be assumed that
Congress intended to permit the suit” and that “it is unfathomable that Congress
considered a consumer who files TCPA actions as a business when it enacted
the TCPA.”
171
Stoops may have been opportunistic, but her motives do not negate the
wrongfulness of the defendant’s activity or the fact that she suffered a harm.
Trying to catch a wrongdoer does not mean that one is unharmed by the
wrongdoer’s actions in the process. Ultimately, however, harm should not be
relevant to the Stoops case. Congress wrote the private right of action under the
TCPA without a requirement of harm. Deterrence—not compensation—is the
goal. The fact that lawyers and plaintiffs benefit financially from enforcing
privacy laws is a necessary side effect of private rights of action. Litigation must
be sufficiently remunerative to incentivize private enforcement.
Contrary to the court’s view of Stoops’s actions, she engaged in crucially
important activity. She helped catch privacy violators and took the time to
enforce the TCPA, which is what federal lawmakers sought to incentivize. She
held privacy violators accountable when enforcement agencies did not. The
main benefit of a private right of action in a law is to encourage private
enforcement of that law because government agencies often lack the resources
to enforce a law rigorously and consistently enough.
3. An Approach for Realignment
In privacy cases, how should the law better align the goals of enforcement
with remedies? When should harm be required? In our view, harm should be an
167
197 F. Supp. 3d 782 (W.D. Pa. 2016).
168
47 U.S.C. § 227(c)(5) (stating court may use discretion and triple award if defendant
“willfully or knowingly violated the regulation”).
169
Stoops, 197 F. Supp. 3d at 800 (noting calls were not “‘the nuisance, invasion of
privacy, cost, and inconvenience’ from which Congress intended to protect consumers”).
170
Id. at 805 (noting purchasing cell phones with hope of receiving calls to collect statutory
damages inconsistent with purposes of TCPA).
171
Id. (citations and internal quotations omitted) (explaining plaintiff’s injury falls outside
zone of interests sought to be protected by TCPA).

2022] PRIVACY HARMS 823
issue only to the extent that compensation is the enforcement goal. In many
instances of privacy litigation, the enforcement goals involve deterrence and
equity, not compensation. For these cases, harm should be legally irrelevant. The
amount of damages in such cases should be tailored to the enforcement goal.
When the goal is deterrence, attempting to conjure up some amount of
compensation (often based on pretext) will not be optimal for achieving this
goal. The issue of harm just gets in the way and confuses matters when the
essential issue is clear: What amount of damages would be optimal for
deterrence?
For cases where equity is the goal, nonmonetary remedies should be imposed.
Redressing harm can certainly be one of the aims of equity, but goals of equity
extend far beyond traditional conceptions of harm. Equity is a way to right
wrongs—to stop wrongs from continuing without end.
More specifically, we propose the following approach: First, courts should
require harm to the extent that claims are brought to secure compensation.
Establishing harm should be restricted only to the ability to obtain compensatory
damages. To the extent that tort claims seek equitable relief, they should not turn
on harm.
Second, for contract cases, courts should enforce the contract. Courts should
use remedies, such as specific enforcement, restitution, or recission. Attorneys’
fees and some modest damages should be paid to compensate for the time and
hassle of having to litigate to make the defendant adhere to the contract.
Third, courts should not inject harm into cases involving privacy statutes that
have private rights of action. Modern standing doctrine has strayed too far from
the constitutional requirement of “cases” or “controversies” to shut the doors to
the courts to many cases that should be heard. Standing has become a conceptual
mess, with courts spending too much time questioning harm and losing sight of
the important issues.
Standing doctrine is a significant impediment to the coherent operation of
privacy laws. Standing forces harm into cases where it should not be required.
Spokeo is part of a lineage of Supreme Court cases that shifted to a harms-based
approach as a mechanism to shut off courts as vehicles to achieve social justice.
According to Cass Sunstein, modern standing doctrine is an attack on the
enforceability of much modern regulation: “[T]he very notion of ‘injury in fact’
is not merely a misinterpretation of the Administrative Procedure Act and
Article III but also a large-scale conceptual mistake.”
172
Sunstein argues that the
injury-in-fact requirement “injects common law conceptions of harm into the
Constitution.”
173
It purports to be a “purely factual inquiry” but is “inevitably a
product of courts’ value-laden judgments.”
174
172
Cass R. Sunstein, What’s Standing After Lujan? Of Citizen Suits, “Injuries,” and
Article III, 91 MICH. L. REV. 163, 166-67 (1992) (citing 5 U.S.C. § 702) (arguing modern
standing doctrine is “essentially an invention of federal judges”).
173
Id. at 167.
174
Id.

824 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Likewise, Felix Wu argues that “standing law seems to be serving no purpose
other than to constitutionalize a deregulatory agenda.”
175
“Until recently,” Wu
observes,
tangibility and other questions about the quality of the harm suffered by the
plaintiff simply were not part of the Supreme Court’s standing analysis.
Lower courts nevertheless incorporated such considerations into their
analyses of standing in privacy cases. The Supreme Court has now done
the same, thus shifting the law on standing, while professing that nothing
has changed.
176
As Rachel Bayefsky notes, before the shift in standing doctrine, instead of
requiring harm, courts required merely a “legal right” to bring a lawsuit based
on property, contract, tort, or statute.
177
Dissenting in TransUnion, Justice Thomas observes that the requirement of
concrete harm is a relatively late addition to standing doctrine and did not exist
for nearly two centuries.
178
At the founding, “[w]here an individual sought to
sue someone for a violation of his private rights, such as trespass on his land, the
plaintiff needed only to allege the violation.”
179
Justice Thomas also notes that
the First Congress enacted a copyright law that provided for damages without a
showing of monetary loss.
180
Spokeo and TransUnion’s invitation to courts to look to historically
recognized harms in the common law further ossifies the common law’s
protection of privacy beyond the ossification already caused by Prosser.
181
Warren and Brandeis aimed to generate new causes of action to rise to the
problems. Locking down privacy law to four narrow torts contravenes the very
spirit of their article. For Warren and Brandeis, the common law looks not just
backwards but forwards as well.
182
The common law is progressive, not
regressive.
The requirement of harm in standing that overrides private rights of action
invites judicial overreaching. Courts should approach statutory private rights of
175
Felix T. Wu, How Privacy Distorted Standing Law, 66 DEPAUL L. REV. 439, 440 (2017)
(arguing “unheralded expansion” of standing law entirely without justification).
176
Id. at 439-40 (noting while doctrinal shifts not necessarily problematic, “shifts that
occur without awareness or discussion run the risk of being unprincipled”).
177
Rachel Bayefsky, Constitutional Injury and Tangibility, 59 WM. & MARY L. REV. 2285,
2295 (2018) (explaining “injury-in-fact” replaced “legal right” as metric of individualized
interest in lawsuit for standing purposes).
178
TransUnion LLC v. Ramirez, 141 S. Ct. 2190, 2219 (2021) (Thomas, J., dissenting)
(observing court introduced injury in fact centuries after ratification of Article III and
therefore “it is worth pausing to ask why ‘concrete’ injury in fact should be the sole inquiry”).
179
Id. at 2217.
180
See id.
181
Matthew S. DeLuca, Note, The Hunt for Privacy Harms After Spokeo, 86 FORDHAM L.
REV. 2439, 2463-68 (2018).
182
Warren & Brandeis, supra note 97, at 193 (“[T]he common law, in its eternal youth,
grows to meet the demands of society.”).

2022] PRIVACY HARMS 825
action with more humility. Legislatures do not provide private rights of action
loosely. Private rights of action are one of the most contested elements of laws,
and when legislatures deem that violations of a law require the recognition of
private rights of action, judges ought to show more respect for the legislature’s
determination.
Nullifying a law’s enforcement component can thwart the way the law is
supposed to work. When Congress passes statutes, it will sometimes preempt
state laws on the same issue, so plaintiffs might be barred from suing in state
court for state law violations. Preemption is a kind of bargain, where plaintiffs
might lose out on pursuing actions in state court but will be allowed instead to
pursue actions based on the federal statute. This is how the FCRA works, as it
preempts certain state laws and directs plaintiffs to sue under its provisions.
183
When Congress enacted the FCRA, its private right of action was included in
exchange for restricting state privacy and defamation tort actions.
184
Plainly said,
the Supreme Court has turned an explicit trade by Congress into a gift to
defendants. Plaintiffs were stripped of their ability to seek tort redress but
provided a right to sue under federal law. Now, they are denied both tort redress
and its substitute because courts have decided that they lack standing to seek
redress under the alternative cause of action provided by the FCRA. By requiring
harm, courts are pulling the rug out from the bargain, leaving plaintiffs with
nowhere to pursue their cases.
Congress weighs various enforcement mechanisms from agency enforcement
to state attorney general enforcement to private rights of action. Many statutes
have a mix of different types of enforcement. Through those choices, Congress
has determined the efficacy of that particular enforcement mix. When courts
nullify a component of Congress’s enforcement mix, they undermine the
statutory recipe.
Focusing on individual harm for these latter types of lawsuits is missing the
point and purpose of the lawsuit. Many class action lawsuits would not be worth
the significant costs if their sole benefit were to compensate individuals for any
harm. For many class action lawsuits, the amount of compensation individuals
receive is trivial. If this were the main benefit of these lawsuits, then we ought
to reconsider whether they are worth the costs. The real value of many class
action lawsuits is that they hold defendants accountable for their wrongdoing. In
doing so, class actions deter specific defendants, and they generally deter other
similarly situated entities.
The law must break away from the rigid formalistic approach that favors
compensatory damages even for very small harms. The law should also eschew
its rigidity in dismissing cases when there is no cognizable harm. The rigidity
makes litigation fit poorly with enforcement goals.
183
15 U.S.C. § 1681h.
184
The FCRA provides partial immunity from lawsuits in state court based on defamation
and invasion of privacy. Plaintiffs can only sue when defendants acted “with malice or willful
intent to injure” plaintiff. Id. § 1681h(e).

826 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
In class action cases where there may be only a small harm to individuals,
courts should be able to fashion a remedy without resorting to compensatory
damages. Compensatory damages for large classes could end up adding to an
excessive sum beyond what is necessary to achieve optimal deterrence. At the
same time, a miniscule amount of damages for each class member will not
address the goal of compensation in a meaningful way. In such a situation, the
enforcement goal is the meaningful one, and this goal, rather than deterrence or
compensation, should be the driver of the appropriate remedy.
In other cases, the amount of compensatory damages might be too low for
optimal enforcement. If the compensation to the class is minimal, then
compensatory damages are not a meaningful remedy, and courts should be able
to fashion a more appropriate remedy with punitive damages or equitable relief.
To avoid unnecessary class action lawsuits, in statutory cases where only
deterrence is a goal and compensation is not involved, courts might be given the
option of evaluating the extent to which the statute has already been enforced. If
a regulatory agency has already effectively enforced a law for the violation, then
a statutory requirement for establishing harm might be appropriate, as the only
goal of a lawsuit under these circumstances would be compensation.
Legislatures could thus write laws to permit courts to dismiss lawsuits in
situations where regulatory enforcement has been sufficient for deterrence and
other enforcement goals are not present.
IV. THE IMPORTANCE OF PROPERLY RECOGNIZING PRIVACY HARMS
Under the current U.S. approach to privacy litigation, harm plays a central
gatekeeping role, and failing to recognize privacy harm shuts down important
cases and prevents many privacy statutes from being effectively enforced. Under
our proposed approach, harm would be required only if justified. Standing
doctrine would be restored to what it was before the Court dramatically twisted
it to the detriment of privacy policy and law. Harm would need to be established
only in cases involving compensatory damages.
Because our approach would require a rather substantial change in current
law, establishing harm is likely to remain a key component for most privacy
cases. Even if our approach were adopted, establishing harm still would play an
important role, just not its current oversized one.
Recognizing privacy harms is valuable for other reasons. Law is expressive.
It changes the social meaning of activities, thus shifting societal attitudes,
expectations, and practices. Lawmakers’ recognition of privacy harms helps
ensure that the law provides adequate protection while encouraging the
provision of adequate resources and the development of sufficient enforcement
strategies.
A. Properly Identifying the Interests at Stake
Under the current approach, some courts locate harm in trivial costs or use of
resources simply because they have to go through the exercise of finding harm.

2022] PRIVACY HARMS 827
Because courts require plaintiffs to allege tangible and concrete harms,
complaints endeavor to lay out concrete harms that are not the heart of the matter
at all. It is those harms that enable plaintiffs to get beyond motions to dismiss
even though they are miniscule and—crucially—do not capture why plaintiffs
are bringing suit in the first place.
One theory of harm that has gained traction is the loss of device battery life
and storage space. In In re iPhone Application Litigation,
185
plaintiffs alleged
that Apple breached promises in its privacy policy to protect users’ personal data
because its operating system readily facilitated the nonconsensual collection and
use of their data by apps. The court found that plaintiffs had sufficiently alleged
harm in claiming that the unauthorized transmission of data from their iPhones
taxed the phones’ resources by draining the battery and using up storage space
and bandwidth.
186
In Mey v. Got Warranty, Inc.,
187
the court held that unwanted calls to prepaid
cell phones “cause direct, concrete, monetary injury by depleting limited
minutes that the consumer has paid for” and also “deplete a cell phone’s battery,
and the cost of electricity to recharge the phone.”
188
The court noted that,
“[w]hile certainly small, the cost is real, and the cumulative effect could be
consequential.”
189
As another court noted, although the harm from “a single call
or text (whether from depleted battery life, wasted time, or annoyance) would
be de minimis,” the TCPA “is clear that a violation can occur from a single
call.”
190
As another court has noted: “Regardless of how small the harm is, it is
actual and it is real.”
191
In those cases, the actual harm to plaintiffs, however, was not lost storage
space or slightly drained resources. The problem wasn’t the cost of electricity or
phone minutes. The litigants invoked those costs because judicial decisions
forced their hand—while financial costs existed, the real privacy harms lay
elsewhere, as we shall explore in the next Part. Yes, those costs sounded in the
language that courts had chosen to accept but not because they fit what plaintiffs
suffered. We have seen the emergence of an odd sort of legal fiction, where the
law redresses “harm” that is not the real interest interfered with as a means to
redress a harm at the heart of the matter.
185
844 F. Supp. 2d 1040 (N.D. Cal. 2012).
186
Id. at 1056.
187
193 F. Supp. 3d 641 (N.D. W. Va. 2016).
188
Id. at 644-45.
189
Id. at 645 (noting such calls also cause intangible injuries, including fact “that they
required the plaintiff to tend to them and wasted the plaintiff’s time”); see also Martinez v.
TD Bank USA, N.A., 225 F. Supp. 3d 261, 270 (D.N.J. 2016) (finding plaintiff’s allegations
of economic injury “due to the need to recharge her phone as a result of depleted battery life
from fielding Defendants’ phone calls” to be sufficient injury).
190
Etzel v. Hooters of Am., LLC, 223 F. Supp. 3d 1306, 1312 (N.D. Ga. 2016) (emphasis
added).
191
LaVigne v. First Cmty. Bancshares, Inc., 215 F. Supp. 3d 1138, 1146 (D.N.M. 2016).

828 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
The law fails to focus on whether certain practices actually create privacy
problems that set back privacy interests that we care about. Lucky plaintiffs can
identify some minor tangible impact, which often has little to do with privacy.
By contrast, plaintiffs who can point to a severe problem that does not involve a
negligible tangible impact are out of luck. The law perversely redresses trivial
setbacks while ignoring major problems and real costs to individuals, groups,
and society.
It is essential to properly identify the interests at stake. Using concrete, yet ill-
fitting harms results in a balancing of interests based on fictions, leading to
haphazard results in cases. This is a recipe for an arbitrary and incoherent body
of law.
B. The Expressive Value of Recognizing Harm
We lose something important when courts fail to articulate privacy harms
appropriately. Looking for irrelevant financial or physical harms and ignoring a
vast array of real tangible and intangible privacy harms sends the message that
those real privacy harms do not matter. We lose the chance to harness the
educative power of law.
In addition to its coercive role, law has a crucial expressive character.
192
Law
serves as our teacher by creating “a public set of meanings and shared
understandings between the state and the public.”
193
It shapes the social meaning
of conduct.
194
It draws our attention to privacy violations and proclaims that they
are wrong and should not be tolerated. In creating and shaping social norms, law
has “an important cultural impact that differs from its more direct coercive
effects.”
195
Individuals whose privacy has been violated need to hear the message that
law is concerned with the harms they have suffered. Law’s recognition of
privacy harms tells individuals that their suffering is real and that it is not just a
fact of life that should be endured.
196
In this way, the law allows individuals to
see themselves as harmed.
192
One of us (Citron) has explored how education and law can help us combat destructive
social attitudes. CITRON, HATE CRIMES, supra note 155, at 95 (“Feminist activists and lawyers
taught judges, officers, legislators, and ordinary people about women’s suffering.”); Danielle
Keats Citron, Law’s Expressive Value in Combating Cyber Gender Harassment, 108 MICH.
L. REV. 373, 407 (2009) [hereinafter Citron, Law’s Expressive Value] (explaining that law
played important expressive role in “detrivializing workplace sexual harassment and domestic
violence during the last quarter of the twentieth century”).
193
Citron, Law’s Expressive Value, supra note 192, at 407-08 (noting media coverage of
sexual harassment following court rulings legitimated view that sexual harassment is harmful
and “deepened the public’s appreciation of the problem”).
194
Id. at 407.
195
Id.
196
Id.; see also Rachel Bayefsky, Remedies and Respect: Rethinking the Role of Federal
Judicial Relief, 109 GEO. L.J. 1263, 1266-68 (2021) (arguing federal judicial remedies for
parties that suffered dignitary harm should follow “expressive approach” that “acknowledges

2022] PRIVACY HARMS 829
In clarifying and recognizing privacy harms, the law provides lessons for
wrongdoers. It declares that the privacy harms that defendants inflict will not be
ignored, that they will have to face responsibility for their privacy violations. It
makes clear that wrongdoers must internalize the costs that they slough off onto
others.
197
Society receives the message too. With law as a guide, privacy harms would
become part of the risk calculus for any person or entity handling personal data.
Companies would design new gadgets and services with the knowledge that they
are responsible for the privacy harms these devices cause.
198
Failing to recognize privacy harm sends the opposite message, one that is
malignant. When cases are dismissed for lack of harm in the face of violations
of privacy law, the message is that these violations do not matter. Organizations
learn that they do not need to take the law seriously. Denials of standing for
statutory violations belittles protections in privacy statutes. These expressive
messages undermine compliance with laws.
C. Legislative and Regulatory Agenda
Lawmakers and law enforcers would benefit from clarity around privacy harm
as well. U.S. states have been actively working on new privacy laws.
199
Several
states, such as California, Virginia, and Colorado, have passed broad privacy
statutes within the past few years.
200
Many other states are showing an interest
as well. Crucial to those efforts is a clear understanding of privacy harm. If
lawmakers fail to appreciate the full breadth of the harm suffered by their
citizens, then they will draft laws that are insufficiently protective. Getting the
harm calculus right is all the more important given the heightened attention
being paid to privacy in state capitols.
The recognition of privacy harms also might affect the agenda for regulatory
enforcement agencies. Violations of privacy laws that are understood to cause
harm to consumers are more likely to spark an investigation and enforcement
action. Regulators have limited resources and can pursue only a fraction of
violations.
201
Failing to recognize harm for certain types of violations might lead
to precious enforcement resources being used elsewhere.
the plaintiff’s significance, full membership in a social group, and entitlement to avoid undue
exposure”).
197
See Citron, Sexual Privacy, supra note 155, at 1878.
198
See DANIELLE KEATS CITRON, THE FIGHT FOR PRIVACY: PROTECTING DIGNITY,
IDENTITY, AND LOVE IN THE DIGITAL AGE (forthcoming 2022) (on file with author) [hereinafter
CITRON, THE FIGHT FOR PRIVACY].
199
Taylor Kay Lively, US State Privacy Legislation Tracker, INT’L ASS’N OF PRIV. PROS.,
https://iapp.org/resources/article/us-state-privacy-legislation-tracker/
[https://perma.cc/B3ZS-GBD2] (last updated Feb. 17, 2022).
200
Id. (“After the California Consumer Privacy Act passed in 2018, multiple states
proposed similar legislation to protect consumers in their states.”).
201
See Citron, Privacy Policymaking, supra note 8, at 799 (“Simply put, federal agencies
have too few resources and too many responsibilities.”).

830 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
V. A TYPOLOGY OF PRIVACY HARMS
Privacy harms have been a challenge to conceptualize because they are so
varied. Privacy is an umbrella concept that encompasses different yet related
things.
202
It is no surprise that privacy harms involve different yet related
concerns. Privacy harms not only differ in type but also in their severity.
In this Part, we discuss the various types of privacy harms and whether the
law currently recognizes them.
203
For many types of privacy harms, the law lacks
clarity and consistency as to whether the harm is cognizable. We contend that in
most cases, these distinct types of harms should be treated as cognizable harms.
For several of these types of harms, there is support in case law and doctrines in
other contexts to support recognition of cognizable harm. In many
circumstances, courts recognize the direct harm for certain types of harm but fail
to recognize the risk of harm. Our typology of privacy harms is set forth in the
figure below.
202
SOLOVE, UNDERSTANDING PRIVACY, supra note 28, at 1 (“Currently, privacy is a
sweeping concept, encompassing (among other things) freedom of thought, control over one’s
body, solitude in one’s home, control over personal information, freedom from surveillance,
protection of one’s reputation, and protection from searches and interrogations.”).
203
The typology of privacy harms differs from the taxonomy of privacy problems that one
of us (Solove) has developed. See id. at 101-61. The taxonomy concerns the concept of
privacy, which involves attempts to deal with a set of related problems. Many of the problems
in the taxonomy can create the same type of privacy harm.
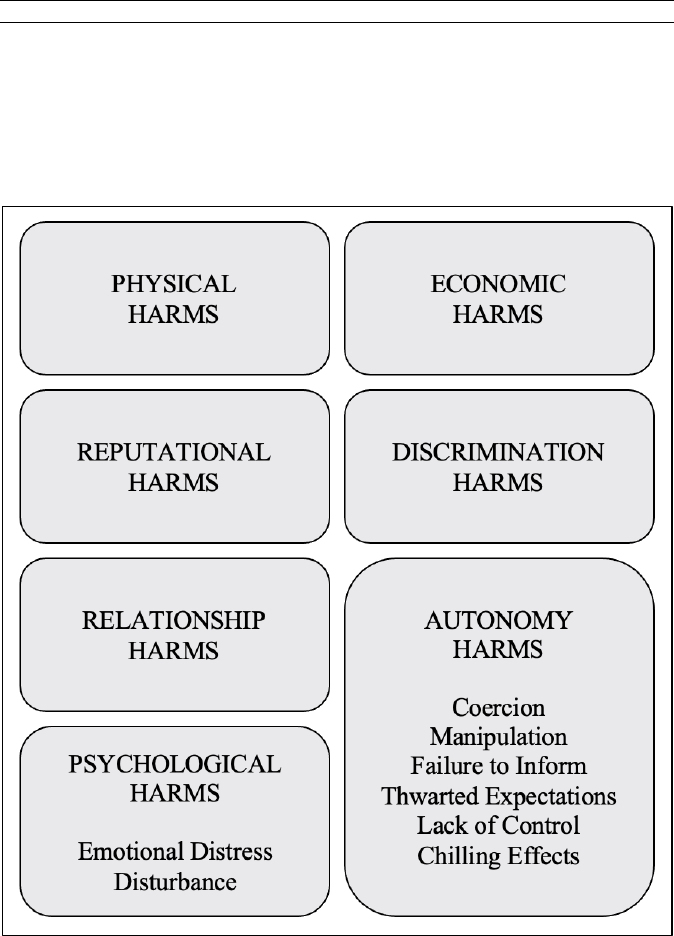
2022] PRIVACY HARMS 831
Figure 1. Typology of Privacy Harms.
Our typology groups privacy harms into seven basic types: (1) physical
harms; (2) economic harms; (3) reputational harms; (4) psychological harms;
(5) autonomy harms; (6) discrimination harms; and (7) relationship harms. We
identify several different distinct subtypes of psychological and autonomy
harms.
A. Physical Harms
Privacy violations can lead to physical harms, which are harms that result in
bodily injury or death. Physical harms are well recognized as cognizable under
the law. Indeed, setbacks to physical health, where clear and obvious, have rarely
been disputed as cognizable harms.

832 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
The improper sharing of personal data can create unique opportunities for
physical violence. Rebecca Schaeffer, a model and actress, was murdered after
a stalker obtained her home address with the help of a private investigator who
obtained it from California motor vehicles records.
204
The Internet has made it
even easier for such sharing of personal data to lead to physical assault. In
December 2009, an online advertisement on Craigslist featured a woman’s
photograph next to her interest in “a real aggressive man with no concern for
women.”
205
The woman’s ex-boyfriend Jebidiah Stipe wrote the post.
206
More
than 160 people responded to the ad, including Ty McDowell.
207
Stipe sent
McDowell text messages with the woman’s home address and falsely informed
him of her desire to be “humiliated, physically and sexually abused, and pimped
out to his friends.” McDowell attacked the woman as she returned home, forcing
his way inside. At knifepoint, he raped her and abused her with a knife
sharpener.
208
When caught by the police, McDowell said that the woman had
asked him to rape her.
209
Entities handling personal data have been found liable for negligently,
knowingly, or purposefully paving the way for a third party to physically injure
someone. In Remsburg v. Docusearch, Inc.,
210
a disturbed man named Liam
Youens purchased personal data about Amy Boyer from data broker
Docusearch.
211
To satisfy Youens’s request for the address of Boyer’s employer,
Docusearch hired a person to find out by calling Boyer, lying to her about the
reason for the call and inducing her to reveal the address.
212
Docusearch gave
the address to Youens who then confronted Boyer at work and killed her.
213
204
Drew Weisholtz & Philip Caulfield, Why Actress Rebecca Schaeffer’s 1989 Murder
Was Hollywood’s Wake-up Call, TODAY (July 8, 2019, 6:59 AM), https://www.today.com
/news/why-actress-rebecca-schaeffer-s-1989-murder-was-hollywood-s-t157444
[https://perma.cc/99SG-RNQ2].
205
Brian, Craigslist Rapists Get 60 to Life – Ad Seeking Someone with “No Regard for
Women” Led to Rape, VICTIMIZED OVER THE AOC (July 3, 2010),
http://victimsover18.blogspot.com/2010/07/craigslist-rapists-get-60-to-life-ad.html
[https://perma.cc/C5LZ-PHTK].
206
Id.
207
William Browning, Wyo. Craigslist Rape Victim Speaks for First Time, CASPER STAR-
TRIB. (Sept. 24, 2010, 4:30 PM), https://trib.com/news/local/craigslist-rape-victim-speaks-
for-first-time/article_488d2453-94d7-557e-8ca5-f021f6638ff5.html.
208
William Browning, Details Emerge in Web Rape Case, CASPER STAR-TRIB. (Feb. 5,
2010), http://trib.com/news/local/article_edb73077-0bbc-5bc2-b9ea-b3fe5c9aedce.html;
Pete Kotz, Jebidiah Stipe Used Craigslist Rape Fantasy Ad to Get Revenge on Ex-Girlfriend,
TRUE CRIME REP. (Feb. 9, 2010, 11:13 AM), https://web.archive.org/web/20170604015613
/http://www.truecrimereport.com/2010/02/jebidiah_stipe_used_craigslist.php.
209
DeeDee Correll, Craigslist Implicated in Rape Case: A Wyoming Man Is Accused of
Using the Website to Engineer an Ex-Girlfriend’s Assault, L.A. TIMES, Jan. 11, 2010, at A9.
210
816 A.2d 1001 (N.H. 2003).
211
Id. at 1005-06.
212
Id. at 1006.
213
Id.

2022] PRIVACY HARMS 833
The New Hampshire Supreme Court found that a data broker or private
investigator “owes a duty to exercise reasonable care not to subject the third
person to an unreasonable risk of harm.”
214
For the court, the risk of criminal
misconduct was sufficiently foreseeable so that an “investigator has a duty to
exercise reasonable care in disclosing a third person’s personal information to a
client.”
215
According to the court, data brokers should know that stalkers often
use their services to obtain personal data about victims.
216
Privacy claims involving the negligent enablement of physical injuries can be
traced to premises liability cases. In Kline v. 1500 Massachusetts Avenue
Apartment Corp.,
217
the plaintiff was attacked and robbed in the hallway just
outside her apartment. The landlord left the building unguarded even though
tenants had been assaulted and robbed in the building’s common areas.
218
The
court held that residential apartment owners had a duty to exercise reasonable
care to protect tenants from third-party violence.
219
The landlord was in a better
position than the tenant to adopt precautionary measures and better situated than
the police to diminish the risk of criminal assault on its premises.
220
Although courts clearly recognize harm from physical injuries, courts are
reluctant to hold online service providers responsible when their activities
promote, facilitate, or enable such harm. The physical harm facilitated via online
stalking is akin to the physical injuries that result when landlords fail to secure
their property. In cases involving owners of residential property, hospitals, day
care centers, and shopping malls, courts have extended liability to the owners
for a third party’s criminal acts.
221
Similar to these owners, online platforms and
service providers exercise control over the use and security of their services, yet
courts treat them differently.
222
Due in part to section 230 of the
Communications Decency Act and the legal shield it provides, courts have not
taken up the invitation to treat digital spaces with the same set of rules as with
physical places.
223
214
Id. at 1007.
215
Id. at 1008.
216
Id. at 1007 (“It is undisputed that stalkers, in seeking to locate and track a victim,
sometimes use an investigator to obtain personal information about the victims.”).
217
439 F.2d 477 (D.C. Cir. 1970).
218
Id. at 479.
219
Id. at 487.
220
Id. at 480.
221
Michael L. Rustad & Thomas H. Koenig, The Tort of Negligent Enablement of
Cybercrime, 20 BERKELEY TECH. L.J. 1553, 1582 (2005).
222
See Citron, Privacy Torts, supra note 97, at 1852.
223
CITRON, HATE CRIMES, supra note 155, at 141; Danielle Keats Citron, Cyber Mobs,
Disinformation, and Death Videos: The Internet as It Is (and as It Should Be), 118 MICH. L.
REV. 1073, 1089 (2020) (book review); Danielle Keats Citron & Benjamin Wittes, The
Internet Will Not Break: Denying Bad Samaritans Section 230 Immunity, 86 FORDHAM L.
REV. 401, 423 (2017).

834 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Courts sometimes struggle with cases involving the disclosure of personal
data that creates a risk of physical harm but that still has not resulted in actual
physical injury. Doxing—the disclosure of personal data to facilitate people
being located, contacted, and harassed—creates a serious threat of physical
harm. Courts often focus on the nature of the data involved, which is often
innocuous in the abstract, such as home addresses. Such information may
already be available online from other sources. But when this data is used to dox
victims, the data no longer is innocuous. Courts are generally reluctant to view
the disclosure of home addresses as harmful (or even as a violation of privacy)
unless plaintiffs have done everything that they can to keep their home addresses
from the public (such as removing their addresses from the white pages).
224
A few courts have recognized the harm. For example, in Planned Parenthood
v. American Coalition of Life Activists,
225
an anti-abortion activist group doxed
abortion doctors. Some of these doctors were murdered, and the living ones
whose personal information was posted online sued and argued that they feared
for their safety. The court sided with the doctors.
226
Cases like Planned
Parenthood are rare, however, and few plaintiffs have been able to use litigation
to combat doxing.
Doxing actually involves a fusion of two types of harm—a risk of physical
harm as well as psychological harm consisting of the fear that accompanies this
risk. In The Right to Privacy, Warren and Brandeis observed back in 1890 that
the law had matured sufficiently to recognize not just physical injuries as harms
but also the fear of such injuries. They noted that “with the recognition of the
legal value of sensations, the protection against actual bodily injury was
extended to prohibit mere attempts to do such injury; that is, the putting another
in fear of such injury. From the action of battery grew that of assault.”
227
They
observed that these developments in the law “came with the advance of
civilization.”
228
We will discuss psychological harms later on.
B. Economic Harms
Economic harms involve monetary losses or a loss in the value of something.
Privacy violations can result in financial losses that the law has long understood
as cognizable harm. Even small economic harms are deemed cognizable by
courts.
229
In cases involving identity theft, plaintiffs can prove harm when
224
See, e.g., Benz v. Wash. Newspaper Publ’g Co., No. 05-cv-01760, 2006 WL 2844896,
at *7 (D.D.C. Sept. 29, 2006) (refusing to dismiss plaintiff’s public disclosure claim stemming
from defendant’s publication of her home address online next to suggestion that she was
interested in sex because her home address was not listed in phone book).
225
290 F.3d 1058 (9th Cir. 2002) (en banc).
226
Id. at 1077.
227
Warren & Brandeis, supra note 97, at 193-94.
228
Id. at 195.
229
LaVigne v. First Cmty. Bancshares, Inc., 215 F. Supp. 3d 1138, 1146 (D.N.M. 2016)
(“Regardless of how small the harm is, it is actual and it is real.”).

2022] PRIVACY HARMS 835
identity thieves steal their personal data and use it to conduct fraudulent
transactions in their names.
230
Difficulties arise if plaintiffs are eventually able
to clear up the financial pollution left by identity thieves. Suppose an identity
thief takes out a credit card in a victim’s name. The victim spends a considerable
amount of time clearing up the mess and establishing that the debt is not the
victim’s responsibility. Victims might argue that their time, stress, and anxiety
to mitigate future economic harm should be compensated, but courts often look
askance at these things as bases for cognizable harm.
231
Many cases involving
economic harm are data breach cases. As we noted in our article on data breach
harms, plaintiffs have difficulty providing a causal link between particular data
breaches and identity theft.
232
Moreover, in many cases, the identity theft has
not yet occurred, and many courts refuse to recognize a harm for the risk of
future economic loss.
233
In cases involving the use and sharing of personal data, courts often refuse to
find economic harm. In Dwyer v. American Express Co.,
234
a group of
cardholders sued American Express for creating profiles of them based on their
spending habits and using these profiles for marketing. The cardholders argued
that this activity was a violation of the tort of appropriation of name or likeness.
They contended that American Express appropriated for its own use or benefit
their names or likenesses without their consent. The court, however, concluded
that although “each cardholder’s name is valuable to defendants,” the value of
the American Express lists was due to its “categorizing and aggregating these
names.”
235
American Express’s use of the information does “not deprive any of
the cardholders of any value their individual names may possess.”
236
Thus, the
cardholders could not establish harm.
Many privacy violations involve the loss of important opportunities rather
than direct financial injuries. We could not find any privacy cases recognizing a
harm for loss of productivity or time to deal with privacy violations. In other
contexts, however, courts readily recognize a similar type of harm. For example,
courts recognize loss of consortium, which is defined as “[t]he benefits that one
person, [especially] a spouse, is entitled to receive from another, including
companionship, cooperation, affection, aid, financial support, and (between
spouses) sexual relations.”
237
The concept of “consortium” translates the loss of
230
Solove & Citron, Risk and Anxiety, supra note 27, at 754-56 (“Along these lines, courts
have recognized claims for privacy violations only where redress is sought for tangible
financial losses.”).
231
Id. at 748-53.
232
Id. at 756-60.
233
Id. at 750-52.
234
652 N.E.2d 1351 (Ill. App. Ct. 1995).
235
Id. at 1356.
236
Id. For a different outcome in an action brought by the New York Attorney General
under state UDAP law, see Citron, Privacy Policymaking, supra note 8, at 772.
237
Consortium, BLACK’S LAW DICTIONARY (11th ed. 2019).

836 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
quality time into an economic harm. Although this concept has firm roots in the
law, it has not developed to encompass the loss of quality time more generally
and has not become part of privacy cases.
Another area of struggle in recognizing economic harms is when risk is
involved. As we argued extensively in our article, Risk and Anxiety: A Theory
of Data-Breach Harms, courts are often uncomfortable with risk, and they cling
to notions of vested harm even though risk is a concept thoroughly embraced in
other domains such as insurance, business, and public health, among others.
238
Several cases involve organizations that fail to follow security safeguards,
creating risks that make people more vulnerable to potential future harm. Courts
are inconsistent in finding harm under these circumstances. For example, the
FCRA mandates that no more than five digits from a credit card number can be
printed on a receipt, but far more digits are printed on receipts in violation of the
mandate. In cases where this provision is violated, some courts have held that
there is an injury, and other courts have concluded that there is none.
239
Consider these opposing findings. In Muransky v. Godiva Chocolatier,
Inc.,
240
the Eleventh Circuit held that printing more digits of a person’s credit
card on a receipt is an injury in fact because it is akin to a breach of
confidentiality.
241
However, in Bassett v. ABM Parking Services, Inc.,
242
the
Ninth Circuit concluded that printing more credit card digits on a receipt was
not a sufficient harm because “Bassett did not allege that another copy of the
receipt existed, that his receipt was lost or stolen, that he was the victim of
identity theft, or even that another person apart from his lawyers viewed the
receipt.”
243
At first blush, the Bassett court notes a number of things that seemingly make
the risk of future harm from the receipt low. But having the information on the
receipt presents a risk if the receipt is lost or thrown away. The law’s restriction
of the digits on the receipt is not to shield the data from the customer who bought
238
Solove & Citron, Risk and Anxiety, supra note 27, at 760 (“People have a meaningful
interest in avoiding risk. They will go to the doctor to monitor their health. They will pay for
insurance to insure against particular risks. Indeed, the insurance market is proof that
protection against risk has a monetary value.” (footnote omitted)).
239
Compare Guarisma v. Microsoft Corp., 209 F. Supp. 3d 1261, 1267 (S.D. Fla. 2016)
(finding failure to provide receipts with abbreviated credit card numbers a concrete harm),
with Bassett v. ABM Parking Servs., Inc., 883 F.3d 776, 780 (9th Cir. 2018) (finding no
concrete injury under “exposure” theory of harm), Crupar-Weinmann v. Paris Baguette Am.,
Inc., 861 F.3d 76 (2d Cir. 2017) (holding no standing existed for such violation), and Meyers
v. Nicolet Rest. of De Pere, LLC, 843 F.3d 724, 725 (7th Cir. 2016) (dismissing for lack of
subject matter jurisdiction).
240
922 F.3d 1175 (11th Cir. 2019).
241
Id. at 1191 (“Under these circumstances, we think the risk of disclosure bears a close
enough relationship to the disclosure of confidential information actionable at common law
to satisfy Article III.”).
242
883 F.3d 776 (9th Cir. 2018).
243
Id. at 783.

2022] PRIVACY HARMS 837
something and has the receipt. Instead, it is to enable everyone to be able to
throw away receipts without having to worry about shredding them. This
commitment promotes good security and alleviates the need for people to go to
greater lengths to protect themselves.
In contrast to courts, the FTC has brought enforcement actions against
companies with inadequate security in the absence of a data breach. For
example, in Microsoft Corp.,
244
the FTC faulted Microsoft for failing to follow
the promises it made about the security of a single login service.
245
In
Guess.com, Inc.,
246
the FTC enforced on a similar deception theory.
247
More
recently, in Zoom Video Communications, Inc.,
248
the FTC used an unfairness
theory to fault Zoom for “limiting the intended benefit of a privacy and security
safeguard provided by [the] Safari browser.”
249
This created a “vulnerability” on
users’ computers, but the enforcement actions were not based on any malicious
actors actually exploiting this vulnerability.
250
C. Reputational Harms
Reputational harms involve injuries to an individual’s reputation and standing
in the community. Privacy violations can result in reputational injuries, which
have a long history of recognition. Reputational harms impair a person’s ability
to maintain “personal esteem in the eyes of others” and can taint a person’s
image.
251
They can result in lost business, employment, or social rejection.
The law has treated reputational harms as distinct from physical and property
injuries. As Justice Potter Stewart remarked of defamation law, an individual’s
right to the protection of his good name reflects “our basic concept of the
244
Complaint at 2, Microsoft Corp., No. C-4069, FTC File No. 012-3240 (F.T.C. Dec. 20,
2002), https://www.ftc.gov/sites/default/files/documents/cases/2002/12/microsoftcmp.pdf
[https://perma.cc/2PRB-8XVM].
245
Id. at 2-3 (“In truth and in fact, respondent did not maintain a high level of online
security by employing sufficient measures reasonable and appropriate under the
circumstances to maintain and protect the privacy and confidentiality of personal information
obtained from or about consumers in connection with the Passport and Passport Wallet
services.”).
246
Complaint at 4, Guess?, Inc., No. C-4091, FTC File No. 022-3260 (F.T.C. filed July
30, 2003), https://www.ftc.gov/sites/default/files/documents/cases/2003/08/guesscomp.pdf
[https://perma.cc/E36F-82SN].
247
Id. (“In particular, Respondents failed to implement procedures that were reasonable
and appropriate to: (1) detect reasonably foreseeable vulnerabilities of their website and
application and (2) prevent visitors to the website from exploiting such vulnerabilities and
gaining access to sensitive consumer data.”).
248
Complaint at 2, Zoom Video Commc’ns, No. C-4731, FTC File No. 192-3167 (F.T.C.
filed Jan. 19, 2021), https://www.ftc.gov/system/files/documents/cases
/1923167zoomcomplaint_0.pdf [https://perma.cc/43P4-QEMG].
249
Id. at 8.
250
Id. (discussing user susceptibility to phishing).
251
SOLOVE, UNDERSTANDING PRIVACY, supra note 28, at 175.

838 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
essential dignity and worth of every human being.”
252
Under the umbrella of
defamation law, the torts of libel and slander impose liability when a person
makes a “false and defamatory statement concerning another.”
253
The tort of
false light, which emerged from Warren and Brandeis’s The Right to Privacy,
protects against widely publicizing “a matter concerning another that places the
other before the public in a false light” that is “highly offensive to a reasonable
person.”
254
A long-standing rule in defamation law is that certain defamatory
falsehoods—such as the claim that someone has a sexually transmitted
disease—warrant the recovery of damages without evidentiary proof.
255
Although presumed damages have been disallowed for defamation lawsuits by
public officials and public figures, such damages are permitted in a “vast number
of cases.”
256
Additionally, in other cases where plaintiffs must prove
reputational damage but cannot do so, they still may obtain “nominal
damages”—typically one dollar.
257
Although common in defamation cases,
nominal damages are not restricted to defamation.
258
As Megan Cambre notes,
“An award of nominal damages recognizes that a plaintiff’s right has been
violated. It further provides recovery for that legal wrong.”
259
There is currently
a circuit split on whether nominal damages are sufficient to confer standing.
260
In at least one case, Perkins v. LinkedIn Corp.,
261
a court recognized
reputational harm caused indirectly when personal data was misused by a social
media platform to grow membership in the platform’s user base.
262
In Perkins,
the professional social network site downloaded users’ email contacts and used
them without permission to ask users’ contacts to connect on the site. Users sued
252
Rosenblatt v. Baer, 383 U.S. 75, 92 (1966) (Stewart, J., concurring).
253
RESTATEMENT (SECOND) OF TORTS § 558 (AM. L. INST. 1977).
254
Id. § 652E.
255
Mike Steenson, Presumed Damages in Defamation Law, 40 WM. MITCHELL L. REV.
1492, 1492 (2014) (“Despite heavy criticism, the presumed damages rule has had remarkable
staying power in American law.”).
256
Id. (discussing how “the presumed damages rule continues to apply in many
jurisdictions” when there are no intersecting First Amendment interests).
257
Megan E. Cambre, Note, A Single Symbolic Dollar: How Nominal Damages Can Keep
Lawsuits Alive, 52 GA. L. REV. 933, 936-37 (2018) (“In a wide variety of cases, every federal
appellate court has upheld or granted awards that consist of only nominal damages.”).
258
Id. at 937.
259
Id. at 949 (footnote omitted).
260
Id. at 947-48 (discussing how nominal damages alone are insufficient to establish
standing in the Sixth Circuit but can establish standing in the Third Circuit). But see
Uzuegbunam v. Preczewski, 141 S. Ct. 792, 802 (2021) (holding “that a request for nominal
damages satisfies the redressability element of standing where a plaintiff’s claim is based on
a completed violation of a legal right”).
261
53 F. Supp. 3d 1222 (N.D. Cal. 2014).
262
Id. at 1252 (“‘This type of reputational harm,’ uniquely associated with LinkedIn’s
sending of reminder emails, ‘is precisely the harm against which the common law right to
publicity seeks to protect.’”).

2022] PRIVACY HARMS 839
LinkedIn on the grounds that sending repeated invitations to their contacts
caused them reputational harm because their contacts might think that they sent
the repeated invitations. The court concluded that they had alleged cognizable
harm: LinkedIn engaged in misleading commercial speech causing injury.
263
A significant risk of reputational harm can be created by sloppy, incomplete,
and incorrect records. Many privacy laws require that organizations adhere to
the principle of “data quality”—keeping data accurate, complete, and up-to-
date.
264
Courts are inconsistent in whether inaccuracies in data constitutes a
cognizable harm. To return to Spokeo, the Court was skeptical about whether
inaccurate data rose to the level of being cognizable. Recall that the plaintiff had
complained about errors in his consumer report that falsely stated that he was
married and had professional degrees. The Court did not examine the specific
errors that the plaintiff complained about. Instead, the Court spoke generally
about errors: “An example that comes readily to mind is an incorrect zip code.
It is difficult to imagine how the dissemination of an incorrect zip code, without
more, could work any concrete harm.”
265
Unfortunately, the Court chose a rather
poor example, as a lot can be inferred about a person based on their zip code,
including demographic generalizations about race, religion, ethnicity, and
income.
The Court remanded the case back to the Ninth Circuit to determine whether
the errors in the plaintiff’s records were sufficiently harmful.
266
On remand, the
Ninth Circuit held Robins had alleged a cognizable harm.
267
The court noted that
accuracy and other components of data quality involved “interests protected by
FCRA’s procedural requirements are ‘real,’ rather than purely legal
creations.”
268
According to the court, “given the ubiquity and importance of
consumer reports in modern life—in employment decisions, in loan
applications, in home purchases, and much more—the real-world implications
of material inaccuracies in those reports seem patent on their face.”
269
Further,
the court observed that “[c]ourts have long entertained causes of action to
vindicate intangible harms caused by certain untruthful disclosures about
263
Id. at 1252-55 (recognizing plaintiffs’ alleged reputational harm as cognizable and
denying LinkedIn’s motions to dismiss).
264
See, e.g., 15 U.S.C. § 1681i (describing, under the FCRA, consumer reporting agencies’
legal requirements related to data accuracy disputes); 20 U.S.C. § 1232g(a)(2) (making funds
contingent, under the Family Educational Rights and Privacy Act, on educational agencies
and institutions providing opportunity for parents of students to challenge inaccurate student
records and the correction or removal of inaccurate records).
265
Spokeo, Inc. v. Robins, 578 U.S. 330, 342 (2016).
266
Id. at 334 (“We therefore vacate the decision below and remand for the Ninth Circuit
to consider both aspects of the injury-in-fact requirement.”).
267
Robins v. Spokeo, Inc. (Spokeo II), 867 F.3d 1108, 1118 (9th Cir. 2017), cert. denied,
138 S. Ct. 931 (2018).
268
Id. at 1114.
269
Id.

840 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
individuals, and we respect Congress’s judgment that a similar harm would
result from inaccurate credit reporting.”
270
However, courts are more reluctant to find harm for errors in records without
disclosure to others. These situations involve a significant risk of harm, so they
are akin to the future risk of harm cases in data breach litigation. A key case
regarding erroneous records is the recent Supreme Court decision in
TransUnion.
271
As discussed earlier, TransUnion falsely noted in the plaintiffs’
credit records that they were potential terrorists. The Court held that even
information this damaging does not create a concrete injury unless it is disclosed
to third parties.
272
Finding specific harms for incorrect information in records can be challenging
because errors or omissions could lead to a variety of consequences at some
point in the future, long beyond the statute of limitations for most causes of
action.
273
Suppose, for example, that a credit report erroneously states that a
person went bankrupt. Whether the error causes any harm will depend upon how
the report is used. A wise person would likely refrain from seeking a loan while
the error remains in the report, as this could result in denial of the loan or a higher
interest rate. For example, in Sarver v. Experian Information Solutions,
274
the
court held that the plaintiff failed to establish actual damages based on an
inaccurate bankruptcy notation in his credit report because he had not yet applied
for credit from a third party.
275
But to have courts recognize harm, should a
person have to go through the charade of applying for a loan in order to generate
proof of economic harm?
In TransUnion, TransUnion’s FCRA violations also involved the failure to
notify the plaintiffs that their records labeled them as potential terrorists and to
inform them about their rights to respond to this matter. The Supreme Court’s
view that there is no harm for these violations prevents plaintiffs from enforcing
these provisions of the law, which exist to help people prevent harmful errors
from wreaking havoc on their lives. Such a view is akin to saying that cancer
does not cause harm until it metastasizes and spreads to vital organs.
Recognizing harm before it becomes more severe is essential to preventing
needless injury and suffering. To use another analogy, waiting until a train has
gone over a cliff is a foolhardy trigger for a corrective intervention. A clear risk
is sufficiently concrete.
270
Id. at 1115.
271
TransUnion LLC v. Ramirez, 141 S. Ct. 2190, 2200 (2021) (holding that only class
members for whom TransUnion provided “misleading credit reports to third-party
businesses” demonstrated reputational harm and consequently possessed standing to sue).
272
Id. (holding that majority of 8,185 class members did not have concrete injury because
TransUnion had not provided credit reports for these individuals to third-party businesses).
273
See, e.g., id. at 2210-11 (holding that plaintiffs’ whose credit reports were not provided
to third-party businesses failed to “demonstrate that the risk of future harm materialized”).
274
390 F.3d 969 (7th Cir. 2004).
275
Id. at 971.

2022] PRIVACY HARMS 841
Inaccuracies create risk of future harm that are difficult to predict, but they
are still harmful in the present day because they cause a loss of data hygiene.
276
Imagine that someone that you invited into your house takes all your clothes out
of the drawers and closets and throws them on the floor. The person removes all
your books from the shelves and shoves them in a corner. The person tracks dirt
all over your floors, though the dirt does not permanently stain them. No
structural damage is done to the house, but it is now a mess. You have been
harmed even though the value of your home is not diminished. You have
suffered a loss. You would likely find the mess and dirt in your home to be
unpleasant. You might not invite guests over to your home until it is cleaned.
The harm is not the diminishment in value of the house; it is the interference
with your enjoyment of your home as well as the time and expense to clean up
the mess. When data is sullied with misleading or incorrect information, there is
a similar mess—just one in digital space rather than in a physical place. And,
unlike in real space, the contamination can be difficult to eradicate. It can be
hard for individuals to find out about errors, and, when they do, third parties will
ignore requests to correct them without the real risk of litigation costs.
D. Psychological Harms
Psychological harms involve a range of negative mental responses, such as
anxiety, anguish, concern, irritation, disruption, or aggravation. Although there
is a wide array of feelings that can arise from privacy violations, most can be
categorized into one of two general types—emotional distress or disturbance.
Emotional distress involves painful or unpleasant feelings. Disturbance involves
disruption to tranquility and peace of mind.
1. Emotional Distress
One of the most common types of harm caused by privacy violations is
emotional distress.
277
Emotional distress encompasses a wide range of emotions,
including annoyance, frustration, fear, embarrassment, anger, and various
degrees of anxiety.
The impact of emotional harm varies depending upon the emotion triggered.
Fear can be among the most damaging emotions given its impact on people’s
life choices. One of us (Citron) has chronicled the devastating impact that fear
has had on women who faced a perfect storm of impersonation, doxing, nude
photos, and threats online.
278
Privacy violations can cause emotional distress that
276
See, e.g., Ann Carrns, More Consumers Complain About Errors on Their Credit
Reports, N.Y. TIMES (Oct. 1, 2021), https://www.nytimes.com/2021/02/19/your-
money/credit-report-errors.html (discussing consumers’ difficulties correcting their
inaccurate credit data).
277
See Solove & Citron, Risk and Anxiety, supra note 27, at 746 (discussing how vast
majority of states allow plaintiffs to recover for emotional distress under privacy tort law).
278
CITRON, HATE CRIMES, supra note 155, at 35-55 (describing threats and harassment
experienced online by prominent tech blogger, law student, and revenge porn victim);

842 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
can impede someone’s life as much as certain physical injuries. The emotional
toll of identity theft can adversely affect victims’ work and relationships.
279
Courts, however, have struggled with how to recognize emotional distress as
a cognizable harm, resulting in a messy and inconsistent body of case law.
280
In
one sphere of tort law—the privacy torts spawned from Warren and Brandeis’s
article—courts have consistently recognized emotional distress alone as
cognizable harm. The privacy torts, however, are more of an exception than the
rule. The special oasis afforded to the privacy torts likely is due to their genesis
from the Warren and Brandeis article, which emphatically noted that privacy
violations primarily involve an “injury to the feelings.”
281
Privacy invasions
interfered with a person’s “estimate of himself,” inflicting “mental pain and
distress, far greater than could be inflicted by mere bodily injury.”
282
Specifically addressing judicial reluctance to recognizing emotional harm,
Warren and Brandeis began by noting how the common law had matured to
recognize and redress a variety of types of intangible harms beyond physical
ones. “[I]n early times,” they wrote, “the law gave a remedy only for physical
interference with life and property.”
283
Subsequently, the law expanded to
recognize incorporeal injuries: “From the action of battery grew that of assault.
Much later there came a qualified protection of the individual against offensive
noises and odors, against dust and smoke, and excessive vibration. The law of
nuisance was developed.”
284
They noted how defamation law protected a
person’s name without requiring proof of financial or physical harm.
285
In
essence, Warren and Brandeis argued that recognition of emotional harm was a
sign of a more advanced civilization and that, by implication, failure to recognize
Danielle Keats Citron, Cyber Civil Rights, 89 B.U. L. REV. 61, 68-81 (2009) (describing how
anonymous mobs threaten, harass, and invade the privacy of women, among other Internet
users, online).
279
ERIKA HARRELL & LYNN LANGTON, BUREAU OF JUST. STAT., U.S. DOJ, VICTIMS OF
IDENTITY THEFT, 2012, at 8-9 (2013), http://www.bjs.gov/content/pub/pdf/vit12.pdf
[https://perma.cc/ZSQ2-EDTZ] (presenting survey results showing that, among identify theft
victims, approximately 1% reported “significant problems at work or school,” 4% reported
“significant problems with family members or friends,” and 36% reported that their level of
emotional distress was either moderate or severe).
280
Solove & Citron, Risk and Anxiety, supra note 27, at 746 (discussing how courts
frequently dismiss anxiety as a cognizable harm in the context of data-breach cases, while
accepting “various forms of emotional distress, including anxiety, as sufficient harm” in other
contexts).
281
Warren & Brandeis, supra note 97, at 197 (describing how law at the time did not
recognize any “principle upon which compensation can be granted for mere injury to the
feelings”).
282
Id. at 196-97.
283
Id. at 193.
284
Id. at 194 (footnote omitted).
285
Id. (describing the development of the law of slander and libel); RESTATEMENT
(SECOND) OF TORTS § 623 (AM. L. INST. 1977) (providing that defamation liability includes
redress for emotional distress caused by the defamatory publication).

2022] PRIVACY HARMS 843
emotional harm would be crude and uncivilized. Because Warren and Brandeis
tied the privacy torts so tightly to emotional harm, it would be somewhat odd
and nonsensical for courts to recognize the privacy torts but not allow pure
emotional harms for recovery.
Privacy tort cases readily allow emotional distress as the sole basis of harm.
286
Cases “collectively reject any suggestion that special damages or physical
injuries are a threshold pre-condition to recovery.”
287
Courts have recognized as
cognizable harms feelings of violation, mortification, fear, humiliation, and
embarrassment, among other things.
288
The Restatement (Second) of Torts
clearly indicates that plaintiffs can recover for emotional distress alone.
289
In countless privacy tort cases, courts do not question the viability of the
harm.
290
The issue is so clear and settled that courts do not even bother to
mention it. Oddly, beyond the four privacy torts, courts view pure emotional
distress with skepticism. Perhaps this odd disjunction is due to judges being
relatively unfamiliar with the Warren and Brandeis privacy torts, and thus
lacking an appreciation of the clear recognition of emotional distress in these
cases.
In contract law, courts have been reluctant to recognize emotional harm, but
they have shifted on this issue to move toward a greater allowance of recovery
for emotional harm. The general rule is that emotional distress damages are not
permitted for breach of contract.
291
The rule emerges from the famous English
case from 1854, Hadley v. Baxendale.
292
Although Hadley is the prevailing rule,
it was once considered a radical departure from the existing rule that damages
for breach of contract could encompass all losses suffered by the plaintiff,
including emotional distress.
293
Hadley was part of a general movement in
286
Brents v. Morgan, 299 S.W. 967, 971 (Ky. 1927) (holding that individual whose right
to privacy is violated “is entitled to recover substantial damages, although the only damages
suffered by him resulted from mental anguish”); Solove & Citron, Risk and Anxiety, supra
note 27, at 769-71 (discussing courts’ recognition of “harm based on pure emotional distress
or psychological impairment” in context of privacy torts and breach-of-confidentiality tort).
287
DAVID A. ELDER, PRIVACY TORTS § 3:8 (2020) (footnotes omitted).
288
Id. (listing types of emotional distress that courts have recognized as cognizable harms).
289
RESTATEMENT (SECOND) OF TORTS § 652H cmt. b (“The plaintiff may also recover
damages for emotional distress or personal humiliation that he proves to have been actually
suffered by him, if it is of a kind that normally results from such an invasion and it is normal
and reasonable in its extent.”).
290
Solove & Citron, Risk and Anxiety, supra note 27, at 769-71.
291
Charlotte K. Goldberg, Emotional Distress Damages and Breach of Contract: A New
Approach, 20 U.C. DAVIS L. REV. 57, 57-59 (1986) (discussing how traditionally under
contract law damages from emotional distress were unavailable).
292
(1854) 156 Eng. Rep. 145, 145; 9 Ex. 341, 341 (limiting damages for breach of contract
to those which each party reasonably would have anticipated when making contract).
293
See Mara Kent, The Common-Law History of Non-economic Damages in Breach of
Contract Actions Versus Willful Breach of Contract Actions, 11 TEX. WESLEYAN L. REV. 481,
486-91 (2005).

844 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
England to limit the discretion of juries and to shift more power to judges.
294
Justifications for the Hadley rule in U.S. contract law are based on fears of
fabricated claims, disproportionate compensation, and unforeseeable
damages.
295
Nonetheless, courts have been making a number of exceptions to the Hadley
rule, such as “when the breach is willful or wanton in nature or if the breach
causes bodily harm.”
296
Another exception is when the “contract is personal in
nature,” such as contracts to take photographs, to supply wedding dresses, or to
perform cosmetic surgery.
297
As one commentator has noted, “courts have
frequently allowed non-economic damages in breach of contract actions, despite
forging the limiting rule, and clearly ‘have not applied it inflexibly.’”
298
Although the law of recovery of emotional distress damages from breach of
contracts is in flux and does not clearly encompass privacy and security issues,
there is enough of a foundation in the law for courts to at least explore the issue
as law develops.
2. Disturbance
Disturbance involves unwanted intrusions that disturb tranquility, interrupt
activities, sap time, and otherwise serve as a nuisance. Many courts have held
that unsolicited telephone calls and text messages in violation of the TCPA
constitute injuries in fact sufficient for standing. As one court explained, the
harm can involve “wasting the consumer’s time” and “interruption and
distraction.”
299
In Van Patten v. Vertical Fitness Group LLC,
300
for example, the
Ninth Circuit noted that “[u]nsolicited telemarketing phone calls or text
messages, by their nature, invade the privacy and disturb the solitude of their
recipients.”
301
Other TCPA cases are similar.
302
As the Fourth Circuit explained
294
Id. at 486-91 (discussing judges’ increasing control in mid-19th century over setting
damages, a determination that had been “entirely the province of the jury”).
295
Id. at 493 (discussing justifications for “general rule” that damages for “mental or
emotional distress in breach of contract actions” are not available).
296
Id. (discussing exceptions to general rule that damages for breach of contract do not
encompass emotional distress); see also 11 ARTHUR LINTON CORBIN, CORBIN ON CONTRACTS
§ 59.1, at 539 (Joseph M. Perillo ed., rev. ed. 2005) (exceptions to Hadley rule include
“(1) cases where such suffering accompanies a bodily injury; and (2) where mental distress
was caused intentionally or in a manner that is wanton or reckless”).
297
Kent, supra note 293, at 501 (discussing how courts award noneconomic damages for
breach of personal contracts).
298
Id. at 493 (quoting E. ALLAN FARNSWORTH, CONTRACTS § 12.17 (3d ed. 1999)).
299
LaVigne v. First Cmty. Bancshares, Inc., 215 F. Supp. 3d 1138, 1146 (D.N.M. 2016).
300
847 F.3d 1037 (9th Cir. 2017).
301
Id. at 1043.
302
See, e.g., Susinno v. Work Out World Inc., 862 F.3d 346, 351-52 (3d Cir. 2017)
(holding that intangible injuries, such as nuisance and invasion of privacy, constituted very
harm that Congress sought to prevent in enacting the TCPA); Melito v. Experian Mktg. Sols.,
Inc., 923 F.3d 85, 88 (2d Cir. 2019) (holding that unsolicited text messages, like unwanted

2022] PRIVACY HARMS 845
in Krakauer v. Dish Network, L.L.C.,
303
the harm the TCPA addresses is
receiving calls that people “previously took steps to avoid.”
304
Rejecting the
notion that this harm was too intangible to be cognizable, the court stated: “There
is nothing ethereal or abstract about it.”
305
Some courts, however, have rejected harm for certain types of
communications under the TCPA, such as text messages. In Salcedo v.
Hanna,
306
the Eleventh Circuit found that the receipt of a single text message
does not constitute a concrete harm because a text message is different than a
phone call or fax because a text message was nothing more than a momentary
annoyance.
307
In contrast, in Gadelhak v. AT&T Services, Inc.,
308
the Seventh
Circuit concluded that unwanted text messages cause harm because the
“undesired buzzing of a cell phone from a text message, like the unwanted
ringing of a phone from a call, is an intrusion into peace and quiet in a realm that
is private and personal, [which] is the very harm that Congress addressed [in the
TCPA].”
309
Some courts have been skeptical of harm for the receipt of spam. In Cherny
v. Emigrant Bank,
310
the defendant bank improperly shared its customers’ email
addresses with third parties, in violation of its privacy policy.
311
As a result, the
plaintiff received spam. The plaintiff sued the bank based on breach of fiduciary
duty and breach of contract. The court held that “[t]he receipt of spam by itself,
however, does not constitute a sufficient injury entitling Cherny to compensable
relief.”
312
E. Autonomy Harms
Autonomy harms involve restricting, undermining, inhibiting, or unduly
influencing people’s choices. People are prevented from making choices that
advance their preferences. People are either directly denied the freedom to
decide or are tricked into thinking that they are freely making choices when they
are not.
There are many types of autonomy harms: (1) coercion—the impairment on
people’s freedom to act or choose; (2) manipulation—the undue influence over
calls or faxes, constitutes the kind of nuisance and privacy harm that Congress identified when
enacting the TCPA).
303
925 F.3d 643 (4th Cir. 2019).
304
Id. at 653.
305
Id.
306
936 F.3d 1162 (11th Cir. 2019).
307
Id. at 1167 (describing text messages as qualitatively different from types of
disturbances that give standing under Eleventh Circuit precedent).
308
950 F.3d 458 (7th Cir. 2020).
309
Id. at 462 n.1.
310
604 F. Supp. 2d 605 (S.D.N.Y. 2009).
311
Id. at 607 (describing bank’s alleged violation of their privacy policy).
312
Id. at 609.

846 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
people’s behavior or decision-making; (3) failure to inform—the failure to
provide people with sufficient information to make decisions; (4) thwarted
expectations—doing activities that undermine people’s choices; (5) lack of
control—the inability to make meaningful choices about one’s data or prevent
the potential future misuse of it; (6) chilling effects—inhibiting people from
engaging in lawful activities.
1. Coercion
Coercion involves a constraint or undue pressure on one’s freedom to act or
choose. For example, the Health Insurance Portability and Accounting Act of
1996 prohibits conditioning medical treatment on agreeing to provide data for
marketing or other uses.
313
The California Consumer Privacy Act restricts
penalizing people who exercise their privacy rights with higher prices.
314
We could not find many cases involving coercion, but we surmise that
coercion would readily be recognized as causing harm. Coercion is visceral. It
has all of the classical attributes that make it readily cognizable. Many
problematic privacy practices, however, are manipulative rather than coercive,
and manipulation exists more in the hazy zone for recognizing harm.
2. Manipulation
Manipulation involves undue influence over a person’s behavior or decision-
making. Manipulation is one of the most prevalent forms of autonomy harm in
the consumer privacy context. There is a spectrum of ways to influence decisions
and behavior. Distinguishing between acceptable influencing (persuasion and
nudging) and unacceptable influencing (manipulation) is challenging and
contestable.
Ido Kilovaty contends that manipulation “impairs the ability of individuals to
make independent and informed opinions and decisions. . . . It effectively
deprives individuals of their agency by distorting and perverting the way in
which individuals typically make decisions.”
315
According to Daniel Susser,
Beate Roessler, and Helen Nissenbaum, manipulation “is a kind of influence—
an attempt to change the way someone would behave absent the manipulator’s
interventions.”
316
They distinguish manipulation from persuasion and coercion:
“Persuading someone leaves the choice of the matter entirely up to them, while
coercing someone robs them of choice.”
317
A coerced person understands that
they are coerced; on the other hand, a manipulated person might not realize that
they are being turned into a puppet:
313
42 U.S.C. § 1320d-6.
314
California Consumer Protection Act, CAL. CIV. CODE § 1798.125 (West 2022).
315
Ido Kilovaty, Legally Cognizable Manipulation, 34 BERKELEY TECH. L.J. 449, 469
(2019) (footnotes omitted).
316
Daniel Susser, Beate Roessler & Helen Nissenbaum, Online Manipulation: Hidden
Influences in a Digital World, 4 GEO. L. TECH. REV. 1, 13 (2019).
317
Id. at 15.

2022] PRIVACY HARMS 847
Coercion is blunt and forthright: one almost always knows one is being
coerced. Manipulation is subtle and sneaky. Rather than simply depriving
a person of options as the coercer does, the manipulator infiltrates their
decision-making process, disposing it to the manipulator’s ends, which
may or may not match their own.
318
According to Cass Sunstein, manipulation involves “an effort to influence
people’s choices counts as manipulative to the extent that it does not sufficiently
engage or appeal to their capacity for reflection and deliberation.”
319
In a survey of various definitions of manipulation, Shaun Spencer observes
that they all share some common elements: “[T]hey all contain the notion of
circumventing the subject’s rational decision-making process” and most require
intent to manipulate.
320
Drawing from these definitions, Spencer defines
manipulation as “an intentional attempt to influence a subject’s behavior by
exploiting a bias or vulnerability.”
321
Ryan Calo contends that manipulation “creates subjective privacy harms
insofar as the consumer has a vague sense that information is being collected
and used to her disadvantage, but never truly knows how or when.”
322
Manipulation “also creates objective privacy harm when a firm uses personal
information to extract as much rent as possible from the consumer.”
323
According to Sunstein, the harm of manipulation “is that it can violate people’s
autonomy (by making them instruments of another’s will) and offend their
dignity (by failing to treat them with respect).”
324
Tal Zarsky contends that
manipulation is harmful because “[m]anipulative practices impair the process of
choosing, subjecting it to the preferences and influences of a third party, as
opposed to those of the individuals themselves.”
325
Manipulation can affect not just individuals but also create societal harm, as
people’s decisions can affect not just themselves but society as well. The
Cambridge Analytica incident involved the use of personal data on a mass scale
to influence people’s decisions in the 2016 U.S. presidential election and in the
United Kingdom’s vote for Brexit.
326
318
Id. at 17.
319
Cass R. Sunstein, Fifty Shades of Manipulation, 1 J. MKTG. BEHAV. 213, 216 (2015)
(emphasis omitted).
320
Shaun B. Spencer, The Problem of Online Manipulation, 2020 U. ILL. L. REV. 959, 989.
321
Id. at 990.
322
Ryan Calo, Digital Market Manipulation, 82 GEO. WASH. L. REV. 995, 1029 (2014).
323
Id.
324
Sunstein, supra note 319, at 217.
325
Tal Z. Zarsky, Privacy and Manipulation in the Digital Age, 20 THEORETICAL
INQUIRIES L. 157, 174 (2019).
326
See Carole Cadwalladr, The Great British Brexit Robbery: How Our Democracy Was
Hijacked, GUARDIAN (July 13, 2021), https://www.theguardian.com/technology
/2017/may/07/the-great-british-brexit-robbery-hijacked-democracy [https://perma.cc/2L67-
ZJG5]; see also Bobby Chesney & Danielle Citron, Deep Fakes: A Looming Challenge for
Privacy, Democracy, and National Security, 107 CALIF. L. REV. 1753, 1816 (2019).

848 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
The FTC has recognized that trade practices that prevent consumers from
“effectively making their own decisions” are ones that cause substantial
injury.
327
“Most of the Commission’s unfairness matters are brought under these
circumstances. They are brought, not to second-guess the wisdom of particular
consumer decisions, but rather to halt some form of seller behavior that
unreasonably creates or takes advantage of an obstacle to the free exercise of
consumer decisionmaking.”
328
When it comes to private litigation, manipulation has not been the subject of
many privacy cases. As Cass Sunstein notes, “[b]ecause of the pervasiveness of
manipulation, and because it often does little or no harm, the legal system
usually does not attempt to prevent it.”
329
Spencer is also skeptical about the
law’s ability to regulate manipulation because “it will be difficult, if not
impossible, to establish that the allegedly manipulative stimulus caused the
consumer harm.”
330
People respond very differently to manipulation, and people
might not even realize that they are being manipulated.
3. Failure to Inform
Failure to inform involves failing to provide individuals with information to
assist them in making informed choices about their personal data or exercise of
their privacy rights. Failure to inform involves autonomy because it limits
people’s ability to make choices consistent with their preferences.
Courts are inconsistent in recognizing harm for failing to inform. In Robertson
v. Allied Solutions, LLC,
331
for example, the plaintiff Robertson applied for a job
at Allied. Allied obtained a background check on Robertson. Although the
FCRA requires that applicants be provided a copy of the report and information
about their FCRA rights, Allied failed to provide either to Robertson. The
Seventh Circuit held that she was harmed because she “was denied information
that could have helped her craft a response to Allied’s concerns.”
332
Even if the
information in the report is true, the court noted, a consumer might want to
“bring additional facts to the employer’s attention that put matters in a better
light for the consumer.”
333
In Long v. Southeastern Pennsylvania Transportation Authority,
334
an
employer rejected applicants based on background checks that turned up
information about convictions involving illegal drugs. Although the FCRA
requires that the applicants be provided a copy of their background check report
and a written statement of their FCRA rights, the employer failed to provide
327
FTC POLICY STATEMENT ON UNFAIRNESS, supra note 132, at 1074.
328
Id.
329
Sunstein, supra note 319, at 219.
330
Spencer, supra note 320, at 997.
331
902 F.3d 690 (7th Cir. 2018).
332
Id. at 697.
333
Id. at 696.
334
903 F.3d 302 (3d Cir. 2018).

2022] PRIVACY HARMS 849
these things.
335
The court concluded that the failure to provide a copy of the
reports harmed plaintiffs by denying them the right to “see or respond” to
them.
336
But regarding the failure to inform the applicants about their FCRA
rights, the court concluded that they lacked standing because the plaintiffs knew
their FCRA rights “to file this lawsuit within the prescribed limitations period,
so they were not injured.”
337
When individuals are not informed of their rights or not given important
information, they are harmed because they lose their ability to assert their rights
at the appropriate times, to respond effectively to issues involving their personal
data, or to make meaningful decisions regarding the use of their data. Laws that
mandate that people be informed of their rights are designed to empower
individuals and arm them with appropriate knowledge. The holding in Long
creates a closed circle where plaintiffs will never be able to enforce the FCRA’s
rights disclosure requirement. If the plaintiffs do not know about their rights,
then they likely will not know they can bring a lawsuit. If they bring a lawsuit,
then courts will throw it out because they knew enough about their rights to sue.
In cases where people are not informed that their personal data was used to
make a decision about them, they are harmed because informing them is to allow
them to understand how their data affected a decision and to give them an
opportunity to respond. This response might not be a direct refutation of the data.
The response could take many forms, from providing additional data to
explaining a situation to raising other unrelated considerations that might
outweigh the negative impact of the data. Even if the response might fail to
change minds, people should still have a chance to make their case. By way of
analogy, denial of people’s day in court is harmful even if they would likely
have lost their case. The harm is in their losing their right to be heard.
4. Thwarted Expectations
The harm caused by thwarted expectations involves the undermining of
people’s choices, such as breaking promises made about the collection, use, and
disclosure of personal data. Thwarted expectations is an autonomy harm because
it results in people’s inability to make choices in accordance with their
preferences.
Courts are generally dismissive of thwarted expectations as a cognizable harm
unless it is accompanied by other harms, such as reputational, economic, or
emotional harm. As Margot Kaminski aptly observes, “in the information
privacy context, the Supreme Court and others have repeatedly asked for privacy
plaintiffs to show something more.”
338
335
Id. at 317.
336
Id. at 324.
337
Id. at 325.
338
Margot E. Kaminski, Standing After Snowden: Lessons on Privacy Harm from National
Security Surveillance Litigation, 66 DEPAUL L. REV. 413, 416 (2017).

850 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
When data is used improperly without people’s consent, courts tend to look
for economic harm rather than recognize that improper use of personal data can
be harmful to autonomy. In In re Google, Inc. Privacy Policy Litigation,
339
plaintiffs sued Google for using their personal data in different ways than had
been promised, but the court found that they lacked standing because they failed
to allege how Google’s “use of the information deprived the plaintiff of the
information’s economic value.”
340
In Fraley v. Facebook, Inc.,
341
the court also
focused on economic value when it concluded that plaintiffs suffered harm when
Facebook used their “likes” to promote products without their permission.
342
The court held that “personalized endorsement” to friends “has concrete,
provable value in the economy at large.”
343
Generally, courts have not found harm when companies share personal data
with third parties in violation of their privacy policies. In Smith v. Chase
Manhattan Bank,
344
for example, the court concluded that plaintiffs suffered no
harm when a bank sold their personal data to third parties in violation of its
privacy policy: “[C]lass members were merely offered products and services
which they were free to decline. This does not qualify as actual harm.”
345
Plaintiffs have fared better when statutes are the source of the expectation that
data will not be shared. In In re Nickelodeon Consumer Privacy Litigation,
346
the court concluded that Viacom’s improper collection of personal data about
the videos people watched on its website and its disclosure of the data to Google
was a cognizable harm. The court noted that “when it comes to laws that protect
privacy, a focus on ‘economic loss is misplaced’” and that “the unlawful
disclosure of legally protected information” was “a clear de facto injury.”
347
In
Eichenberger v. ESPN, Inc.,
348
the Ninth Circuit concluded that sharing personal
data with a third party in violation of the VPPA was a harm because “both the
common law and the literal understanding of privacy encompass the individual’s
control of information concerning his or her person.”
349
In contract law, courts are adamant about focusing on economic harm. In In
re Google Inc. Cookie Placement Privacy Litigation,
350
Google tracked users’
Internet activity in violation of its promise to respect users’ “do not track”
339
No. 12-cv-01382, 2013 WL 6248499 (N.D. Cal. Dec. 3, 2013).
340
Id. at *5.
341
830 F. Supp. 2d 785 (N.D. Cal. 2011).
342
Id. at 799-801.
343
Id. at 799.
344
741 N.Y.S. 2d 100 (App. Div. 2002).
345
Id. at 102.
346
827 F.3d 262 (3d Cir. 2016).
347
Id. at 272-74.
348
876 F.3d 979 (9th Cir. 2017).
349
Id. at 983 (quoting U.S. DOJ v. Reps. Comm. for Freedom of the Press, 489 U.S. 749,
763 (1989)).
350
988 F. Supp. 2d 434 (D. Del. 2013).

2022] PRIVACY HARMS 851
settings. The court held that the plaintiffs could not prove harm because they
could not demonstrate that Google interfered with their ability to monetize their
personal data.
351
In a series of cases involving airlines that shared passenger data
with the government in violation of their privacy policies, courts held that the
plaintiffs failed to show harm.
352
For example, in In re Jet Blue Airways Corp.
Privacy Litigation,
353
the court held that recovery in contract “allows only for
economic losses.”
354
Many courts fixate on whether plaintiffs have read and relied on the privacy
policy of a company, but the privacy policy plays a small role in forming
people’s privacy expectations.
355
This is especially true because hardly anyone
reads privacy policies, and it is not rational to do so given the vast number of
organizations collecting data about people.
356
Instead of focusing on the
promises in privacy policies in isolation, courts should consider more broadly
people’s reasonable expectations regarding privacy. Website or browser privacy
settings, company advertising, statements, and other design elements have an
influence on people’s expectations.
357
Courts, however, will not go this far, and
cases to date have focused mainly on violations of explicit promises in privacy
policies or statutory requirements.
358
However, there is a basis in contract law to recognize thwarted expectations
as a harm. When a party to a contract fails to perform a term in a contract, even
if it is a matter of mere personal taste that lacks value, courts will still enforce
the term. In construction contract cases, for example, the difference in the value
of property with and without the plaintiff’s preferences might be slight or nil.
Instead of assessing damages based on the difference in actual value, courts
assess damages for the “cost of completion” because the “fair market value of a
home does not necessarily reflect the value to the homeowner.”
359
As Judge
351
Id. at 442 (noting that their ability to monetize was neither “diminished or lost”).
352
In re Jet Blue Airways Corp. Priv. Litig., 379 F. Supp. 2d 299, 326 (E.D.N.Y. 2005);
In re Nw. Airlines Priv. Litig., No. 04-cv-00126, 2004 WL 1278459, at *4-5 (D. Minn. June
6, 2004); Dyer v. Nw. Airlines Corps., 334 F. Supp. 2d 1196, 1200 (D.N.D. 2004).
353
In re Jet Blue, 379 F. Supp. 2d 299.
354
Id. at 326 (quoting Young v. DOJ, 882 F.2d 633, 641 (2d Cir. 1989)).
355
Woodrow Hartzog, Website Design as Contract, 60 AM. U. L. REV. 1635, 1636 (2011).
356
Solove, Privacy Self-Management, supra note 145, at 1881.
357
Hartzog, supra note 355, at 1650.
358
Id. at 1653.
359
Willie’s Constr. Co. v. Baker, 596 N.E.2d 958, 961 (Ind. Ct. App. 1992) (describing
how “[o]rdinarily, in a breach of contract case the injured party’s damages are measured by
the loss of value to him of the other party’s failure to perform”); see also Lyon v. Belosky
Constr., Inc., 669 N.Y.S.2d 400, 402 (App. Div. 1998) (awarding “cost of performance”
damages in part based on the observation that “the aesthetic appearance of the home, both
inside and out, was of utmost importance to plaintiffs”); Am. Standard, Inc. v. Schectman,
439 N.Y.S.2d 529, 531 (App. Div. 1981) (contractor’s failure to complete work resulted in
$3,000 diminution in value but $90,000 in damages was awarded).

852 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Cardozo famously stated in Jacob & Youngs, Inc. v. Kent,
360
in a construction
contract, “[t]here is no general license to install whatever, in the builder’s
judgment, may be regarded as ‘just as good.’”
361
These cases suggest that, while
the failure to respect people’s preferences is a cognizable harm, even these
preferences do not add any economic value. For many people, their privacy
preferences are an important consideration about whether or not to use a
particular service or product.
In contrast to contract law, the FTC readily enforces for violations of privacy
policies. Under the FTC’s enforcement of the prohibition on “deceptive” acts or
practices under section 5 of the FTC Act, the FTC has viewed broken promises
in privacy notices to be sufficient for harm.
362
Deception need not just involve
statements made in privacy notices, as the FTC has found other statements about
privacy to be deceptive.
363
The very crux of deception as used in the context of
broken promises is that the harm is in personal data being used in ways that
differ from how companies informed people it would be used. One of us
(Solove) has argued that the FTC could and should extend its jurisprudence
further to pursue cases where people’s expectations were thwarted even if no
false statements are made.
364
Critics claim that the FTC should curtail the extent to which it recognizes
harm for thwarted expectations. James Cooper and Joshua Wright contend that
the FTC has become undisciplined about how it recognizes privacy harms.
365
They argue that “unexpected data practices do not always equate to privacy
harm.”
366
They use an example of a smart oven app that records oven usage data,
which is improperly shared with third parties. They argue that the FTC should
not recognize harm in this case because the app’s thwarting of privacy
expectations “may be mediated through the market or the legal system.”
367
They
argue that “a focus on expectations, rather than harm, necessarily will be overly
inclusive.”
368
The market, however, is not adequate to address the problems with the app.
When people use an app that thwarts their privacy expectations, people’s ability
to assess the risks of using the app is impeded. The market cannot work fairly if
people’s expectations are completely wrong, if people lack knowledge of
360
230 N.Y. 239 (1921).
361
Id. at 243.
362
Daniel J. Solove & Woodrow Hartzog, The FTC and the New Common Law of Privacy,
114 COLUM. L. REV. 583, 628-30 (2014).
363
Id. at 630-33.
364
Id. at 667-69.
365
James C. Cooper & Joshua D. Wright, The Missing Role of Economics in FTC Privacy
Policy, in THE CAMBRIDGE HANDBOOK OF CONSUMER PRIVACY 465, 479 (Evan Selinger, Jules
Polonetsky & Omer Tene eds., 2018).
366
Id. at 480.
367
Id.
368
Id.

2022] PRIVACY HARMS 853
potential future uses of their personal data, and if people have no way to balance
the benefits and risks of using products or services.
5. Lack of Control
Lack of control involves the inability to make certain choices about one’s
personal data or to be able to curtail certain uses of the data. Many statutes
provide certain rights or restrictions regarding the retention and use of personal
data independently from what is promised in an organization’s privacy policy.
The harm for violations of these rights or restrictions is not thwarted
expectations, as people might not have known about these statutes. Instead, the
harm involves the loss of control over personal data.
Courts have been inconsistent in recognizing the loss of control as a harm. In
Braitberg v. Charter Communications, Inc.,
369
for example, the Eighth Circuit
denied standing to plaintiffs in a class action lawsuit against a cable company
for failing to delete their personal data in violation of the Cable Communications
Policy Act.
370
The court concluded that the mere improper retention of data was
not sufficient, by itself, to create a “material risk of harm.”
371
In Gubala v. Time
Warner Cable, Inc.,
372
the court denied standing to a cable subscriber suing a
cable company for improperly retaining personal data under the Cable Act
because there was no harm for merely holding data.
373
Similarly, in Rivera v.
Google, Inc.,
374
the court denied standing to plaintiffs who sued Google for
storing their biometric data without their consent, a violation of the Illinois
BIPA.
375
The court concluded that there was no harm because the data was not
shared with anyone.
376
However, there are other courts that recognize the loss of
control as a harm sufficient to justify standing.
377
Losing control over our personal data constitutes an injury to our peace of
mind and our ability to manage risk. In the clutches of organizations, personal
data can be used for a wide array of purposes for an indefinite period of time.
Privacy laws seek to regulate data flows to protect individuals from potential
downstream uses. The practicalities of litigation, which are constrained by
369
836 F.3d 925 (8th Cir. 2016).
370
Id. at 930.
371
Id.
372
846 F.3d 909 (7th Cir. 2017).
373
Id. at 910-11.
374
366 F. Supp. 3d 998 (N.D. Ill. 2018).
375
Id. at 1005.
376
Id.
377
In contrast to Gubala and Rivera, the Illinois Supreme Court in Rosenbach v. Six Flags
Entertainment Corp. concluded that plaintiffs seeking relief under BIPA “need not allege
some actual injury or adverse effect” to be considered aggrieved persons. 2019 IL 123186,
¶ 40. Rosenbach diverges from Gubala and Rivera because it involves a holding that an actual
injury is not required by BIPA, and standing is not required in state court. Id.

854 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
statutes of limitation, require an assessment of the situation before the end of the
data life cycle.
Warren and Brandeis based their argument upon an English case from 1848—
Prince Albert v. Strange.
378
This case involved a suit at equity to prevent
William Strange from publishing a catalog describing etchings that the royal
couple made about their family.
379
The court enjoined the publication of the
catalog. Warren and Brandeis argued that the case involved the protection of
“inviolate personality.”
380
The case did not involve lurid images or embarrassing
secrets (they were endearing hand drawn images of a mother with her child), and
the couple had shared these personal etchings with loved ones.
381
Thus, the
harm, as imagined by Warren and Brandeis, was the undermining of control over
the extent to which personal information is circulated. This type of harm should
be enough.
6. Chilling Effects
Chilling effects involve harm caused by inhibiting people from engaging in
certain civil liberties, such as free speech, political participation, religious
activity, free association, freedom of belief, and freedom to explore ideas.
382
As
Frederick Schauer observes: “The very essence of a chilling effect is an act of
deterrence.”
383
According to Neil Richards, the failure to protect privacy can
chill individuals from engaging in reading or researching.
384
In cases involving
rights under the First Amendment to the U.S. Constitution, courts have
sometimes recognized harm when people are chilled from exercising rights, such
as free speech or free association.
385
Chilling effects have an impact on individual speakers and society at large as
they reduce the range of viewpoints expressed and the nature of expression that
is shared.
386
Monitoring of communications can make people less likely to
378
(1849) 64 Eng. Rep. 293; 2 DE G. & SM. 652.
379
Id. at 295; 2 DE G. & SM. at 656.
380
Warren & Brandeis, supra note 97, at 205.
381
See id. at 202.
382
See Daniel J. Solove, The First Amendment as Criminal Procedure, 82 N.Y.U. L. REV.
112, 142-43 (2007) [hereinafter Solove, First Amendment].
383
Frederick Schauer, Fear, Risk and the First Amendment: Unraveling the “Chilling
Effect,” 58 B.U. L. REV. 685, 689 (1978). For thoughtful, innovative scholarship on the
chilling effect, see the work of Professor Jonathon Penney, including, for example, Jonathon
W. Penney, Understanding Chilling Effects, MINN. L. REV. (forthcoming 2022) (available at
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3855619).
384
NEIL RICHARDS, INTELLECTUAL PRIVACY: RETHINKING CIVIL LIBERTIES IN THE DIGITAL
AGE 165 (2015).
385
Solove, First Amendment, supra note 382, at 143-51.
386
RICHARDS, supra note 384, at 180 (arguing that chilling effect pits “the intellectual
development of our citizenry at risk”); Neil M. Richards, Intellectual Privacy, 87 TEX. L. REV.
387, 419, 419 n.199 (2008) (describing how chilling free expression impedes “intellectual
exploration”); Cohen, supra note 157, at 1425 (“The opportunity to experiment with

2022] PRIVACY HARMS 855
engage in certain conversations, express certain views, or share personal
information.
387
Consider the impact of the news that the gay dating app Grindr
had shared subscribers’ HIV status with analytics firms. Subscribers expressed
profound dismay. Individuals told the press that they would no longer share that
information on that app or any dating app—it was simply not worth the
possibility that employers or others could find out their HIV status and hold it
against them.
388
Courts have been uneasy about recognizing chilling effects, and the law has
wavered. In Laird v. Tatum,
389
the Supreme Court limited the chilling effect
doctrine by concluding that “[a]llegations of a subjective ‘chill’ are not an
adequate substitute for a claim of specific present objective harm or a threat of
specific future harm.”
390
Courts have subsequently struggled to determine the
line between an objective and subjective chill.
391
Despite the somewhat murky status of the law, the concept of chilling is
widely accepted even if its precise contours remain unclear. Although the
chilling effect doctrine emerges from cases involving the First Amendment, the
concept could certainly be applied to other legal contexts.
392
F. Discrimination Harms
Discrimination harms involve entrenching inequality and disadvantaging
people based on gender, race, national origin, sexual orientation, age, group
membership, or other characteristics or affiliations. Discrimination harms thwart
people’s ability to have an equal chance to obtain and keep jobs, to secure
affordable insurance, to find housing, and to pursue other crucial life
opportunities. Because discrimination harms disproportionately affect
marginalized communities, they have systemic effects on these communities and
broader negative societal effects.
Discrimination often involves the curtailment of autonomy, but it differs from
autonomy harms in that discrimination involves unequal treatment that creates
shame and stigma as well as societal consequences of further entrenching
disadvantages to marginalized groups. Discrimination creates harm far beyond
lost opportunities; it leaves a searing wound of stigma, shame, and loss of esteem
preferences is a vital part of the process of learning, and learning to choose, that every
individual must undergo.”).
387
RICHARDS, supra note 384, at 180 (“When the right to privacy is eroded or stripped
away, people are more likely to abandon or curtail their exploration of unpopular and
unorthodox points of view.”).
388
See Danielle Keats Citron, A New Compact for Sexual Privacy, 62 WM. & MARY L.
REV. 1763, 1795 (2021) [hereinafter Citron, New Compact].
389
408 U.S. 1 (1972).
390
Id. at 13-14.
391
Solove, First Amendment, supra note 382, at 143-44 (describing how courts have not
found injury from surveillance without evidence of deterrence).
392
See generally Penney, supra note 383 (describing various types of legal chilling
effects).

856 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
that can turn into permanent scars. It produces psychological harm of a distinct
and distinctly harmful type—knowing that one is viewed as less than human, as
not worthy of respect.
The misuse of personal data can be particularly costly to women, sexual and
gender minorities, and non-White people given the prevalence of destructive
stereotypes and the disproportionate surveillance of women and marginalized
communities in their intimate lives.
393
For example, employers and health
insurance companies can access information that women share with period-
tracking apps (including their moodiness and cramps), which could result in
raised premiums and denied promotions.
394
Women and minorities are often
disproportionately targeted for vicious online harassment, which often involves
doxing—the sharing of their personal data, such as home address and location—
in order to expose them to physical danger.
395
Harassers post victims’ nude
photos and embarrassing information about their sex lives or sexual health,
causing them substantial emotional and reputational harm.
396
Although these
types of harm are separate categories in our typology, there is a distinct and
additional dimension that they add: the entrenchment of existing patterns of
inequality.
In cases involving cyber mobs that inundate victims with crude, threatening,
and abusive comments, plaintiffs have sought to protect themselves by bringing
privacy tort cases.
397
But litigation is complicated by the fact that the harm is
often caused by the totality of the privacy-invasive comments and posts, making
it hard to allocate the harm among the multitude of commenters.
398
The members
of the mob are often anonymous, and it is difficult and expensive to identify
them.
399
Even when the perpetrators are tracked down, suing them is often
impractical because they often are unable to pay enough monetary damages to
393
Citron, New Compact, supra note 388, at 1770. One of us (Citron) has explored the
integral connection between privacy violations and discrimination throughout her scholarship.
See generally, e.g., CITRON, THE FIGHT FOR PRIVACY, supra note 198; CITRON, HATE CRIMES,
supra note 155; Citron, Sexual Privacy, supra note 155 ; Danielle Keats Citron, Spying Inc.,
72 WASH. & LEE L. REV. 1243 (2015); Citron, Cyber Civil Rights, supra note 278. That work
has been inspired by and built on the pathbreaking insights of privacy scholar Anita Allen.
See generally, e.g., ANITA L. ALLEN, UNPOPULAR PRIVACY: WHAT MUST WE HIDE? (2011);
ANITA L. ALLEN, UNEASY ACCESS: PRIVACY FOR WOMEN IN A FREE SOCIETY (1988).
394
Drew Harwell, Is Your Pregnancy App Sharing Your Intimate Data with Your Boss?,
WASH. POST (Apr. 10, 2019), https://www.washingtonpost.com/technology/2019
/04/10/tracking-your-pregnancy-an-app-may-be-more-public-than-you-think/.
395
CITRON, HATE CRIMES, supra note 155, at 53 (providing details of invasions of privacy
and harassment).
396
Id. at 54; Citron, Sexual Privacy, supra note 155, at 1914-15 (discussing up-skirt photos
taken and shared without victim’s consent).
397
CITRON, HATE CRIMES, supra note 155, at 133; Citron, Sexual Privacy, supra note 155,
at 1933.
398
CITRON, HATE CRIMES, supra note 155, at 136-37.
399
See, e.g., Doe I v. Individuals, 561 F. Supp. 2d 249, 251 (D. Conn. 2018).

2022] PRIVACY HARMS 857
incentivize lawyers to litigate.
400
To combat cyber mobs effectively, victims turn
to social media platforms to shut down the mob, but section 230 of the
Communications Decency Act immunizes these platforms from liability for
user-generated content.
401
Beyond doxing and threats targeted at people in marginalized groups, there
are less overt forms of discrimination harms. These harms are difficult to redress
because they often occur in the shadows. The decision-making process of
employers, insurance companies, landlords, and other powerful actors is opaque.
If an employer used a third-party hiring service to score candidates, then rejected
applicants will have no way to know that the hiring service relied upon their
intimate information (like their painful periods or infertility).
402
A key aspect of discrimination harms is the unequal frequency, extensiveness,
and impact of privacy violations on marginalized people. People of color are
disproportionately targeted by surveillance.
403
Algorithms that appear neutral
often have disproportionate effects on minorities.
404
Poor people are often
subjected to oppressive surveillance as part of public assistance bureaucracy.
Black mothers are “stripped of formal privacy rights claims by signing an
encompassing waiver” when applying for assistance.
405
As Khiara Bridges
contends, “poor mothers are not given privacy rights because society, and thus
the law, presumes that their enjoyment of privacy will realize no value or a
400
CITRON, HATE CRIMES, supra note 155, at 122 (“Even if victims can afford to sue their
attackers, they may be reluctant to do so if their attackers have few assets.”).
401
DANIEL J. SOLOVE, THE FUTURE OF REPUTATION: GOSSIP, RUMOR, AND PRIVACY ON THE
INTERNET 152 (2007); CITRON, HATE CRIMES, supra note 155, at 170-71; Citron, Cyber Civil
Rights, supra note 278, at 116.
402
Citron, New Compact, supra note 388, at 1798-1800. There is a wealth of scholarship
and research exploring the discriminatory impacts of algorithmic decision-making in the
commercial sector. See, e.g., Inioluwa Deborah Raji & Joy Buolamwini, Actionable Auditing:
Investigating the Impact of Publicly Naming Biased Performance Results of Commercial AI
Products, 2019 CONF. ON A.I. ETHICS & SOC’Y 429, 429 (discussing algorithmic audits);
Ifeoma Ajunwa, Algorithms at Work: Productivity Monitoring Applications and Wearable
Technology as the New Data-Centric Research Agenda for Employment and Labor Law, 63
ST. LOUIS U. L.J. 21, 44-46 (2018) (noting potential for discrimination arising from use of
wearable technology); Jeffrey Dastin, Amazon Scraps Secret AI Recruiting Tool That Showed
Bias Against Women, REUTERS (Oct. 10, 2018, 7:04 PM), https://www.reuters.com/article/us-
amazon-com-jobs-automation-insight/amazon-scraps-secret-ai-recruiting-tool-that-showed-
bias-against-women-idUSKCN1MK08G [https://perma.cc/5UH3-2KAP] (“[Amazon’s] new
system was not rating candidates for software developer jobs and other technical posts in a
gender-neutral way.”).
403
Alvaro M. Bedoya, Privacy as Civil Right, 50 N.M. L. REV. 301, 306 (2020).
404
ANDREW GUTHRIE FERGUSON, THE RISE OF BIG DATA POLICING: SURVEILLANCE, RACE,
AND THE FUTURE OF LAW ENFORCEMENT 47 (2017).
405
JOHN GILLIOM, OVERSEERS OF THE POOR: SURVEILLANCE, RESISTANCE, AND THE LIMITS
OF PRIVACY 71 (2001).

858 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
negative value.”
406
Mary Anne Franks notes that surveillance often does not
affect marginalized and nonmarginalized people equally: “For the less
privileged members of society, surveillance does not simply mean inhibited
Internet searches or decreased willingness to make online purchases; it can mean
an entire existence under scrutiny, with every personal choice carrying a risk of
bodily harm.”
407
Privacy torts and other tort claims lack the language and concepts to address
discrimination harms.
408
The disparate effects of certain privacy violations are
not considered as part of the harm equation. In contrast, federal statutes do
recognize privacy violations as producing discrimination harm, such as the
federal Genetic Information Nondiscrimination Act (“GINA”) and the
Americans with Disabilities Act (“ADA”). GINA prohibits employers from
requesting, requiring, or obtaining employees’ genetic information.
409
The ADA
limits the ability of employers to make medical examinations or inquiries of job
applicants under a number of circumstances.
410
The civil rights legal tradition has the capacity and vocabulary to address
discrimination harms—the denial of social and economic opportunities due to
one’s membership in a protected group.
411
Federal and state civil rights laws
secure the ability to work, attend school, use the telephone, secure housing, and
vote on equal terms.
412
But these laws still have not been applied sufficiently to
privacy violations. One of us (Citron) has proposed situating and treating privacy
as a civil right so discrimination harms caused by privacy violations can be
406
KHIARA M. BRIDGES, THE POVERTY OF PRIVACY RIGHTS 12 (2017); see also Danielle
Keats Citron, A Poor Mother’s Right to Privacy: A Review, 98 B.U. L. REV. 1139, 1142 (2018)
(book review).
407
Mary Anne Franks, Democratic Surveillance, 30 HARV. J.L. & TECH. 425, 453 (2017);
see also SCOTT SKINNER-THOMPSON, PRIVACY AT THE MARGINS 2 (2020).
408
See supra Section I.B.2.
409
42 U.S.C. § 2000ff-1(b) (“It shall be an unlawful employment practice for an employer
to request, require, or purchase genetic information with respect to an employee . . . .”).
410
42 U.S.C. § 12112(d)(1) (“The prohibition against discrimination as referred to in
subsection (a) shall include medical examinations and inquiries.”).
411
Title VII, Civil Rights Act of 1964, 42 U.S.C. § 2000e-2(a) (prohibiting employment
discrimination on basis of race, color, religion, sex, or national origin); Family Medical Leave
Act of 1993 (FMLA), 29 U.S.C. § 2612(a)(1) (entitling eligible employees to leave in order
to care for children and certain family members); Title IX, Civil Rights Act of 1964, 20 U.S.C.
§ 1681(a) (prohibiting discrimination in education on basis of sex); Americans with
Disabilities Act of 1990, 42 U.S.C. § 12112(a) (prohibiting employment discrimination on
basis of disability).
412
Danielle Citron & Mary Anne Franks, Cyber Civil Rights in the Time of COVID-19,
HARV. L. REV. BLOG (May 14, 2020), https://blog.harvardlawreview.org/cyber-civil-rights-
in-the-time-of-covid-19/ [https://perma.cc/9W5B-ECW9] (“The fight for civil rights in the
United States has historically focused on equal access to physical spaces: schools, workplaces,
lunch counters, hotels, voting booths.”).

2022] PRIVACY HARMS 859
addressed.
413
Existing civil rights laws admittedly do not cover all social goods
in need of protection
414
or all parties given the state action doctrine.
415
They
mostly do not constrain corporate handling of personal data.
416
Nonetheless,
situating private sector surveillance of intimate life as a matter of civil rights
helps begin the conversation about what those freedoms should be in the context
of privacy law specifically and civil rights law more generally.
G. Relationship Harms
Relationship harms involve the damage to relationships that are important for
one’s health, well-being, life activities, and functioning in society. Privacy
violations can harm personal and professional relationships as well as
relationships with organizations. People modulate personal relationships by
maintaining boundaries around their information or by withholding information
from some people and not others.
417
Strangers develop close relationships by
entrusting each other with deeply personal information. Consider
communications among people using fertility tracking apps. On apps like Clue,
subscribers gather online to explore struggles with miscarriages, abortions, and
infertility.
418
They often form bonds with each other. Their relationships depend
upon trusting each other to maintain the confidentiality of their information.
Relationship harms are twofold: most immediately, the loss of confidentiality
and in the longer term, damage to the trust that is essential for the relationship
413
See CITRON, THE FIGHT FOR PRIVACY, supra note 198; Citron, Cyber Civil Rights, supra
note 278, at 89 (“Traditional tort and criminal law fail to respond to such systemic harm and,
indeed, may obscure a full view of the damage.”).
414
In her important new book, Robin West calls for a transformative understanding of civil
rights that does not merely prohibit discrimination but that entails rights essential to the justice
of the nation. ROBIN L. WEST, CIVIL RIGHTS: RETHINKING THEIR NATURAL FOUNDATION 12
(2019). One of us (Citron) builds on West’s conception of civil rights to make the case for
intimate privacy as a civil right—understood as both a right owed to all of us and as protection
against invidious discrimination. CITRON, THE FIGHT FOR PRIVACY, supra note 198.
415
WEST, supra note 414, at 2-4 (exploring various ways that civil rights laws have failed
to fulfill their potential to protect social goods themselves).
416
As scholars have explored, antidiscrimination laws like Title VII are ill-suited to
address the use of discriminatory algorithms in employment matters. See Deborah Hellman,
Measuring Algorithmic Fairness, 106 VA. L. REV. 811, 846 (2020); Pauline T. Kim, Data-
Driven Discrimination at Work, 58 WM. & MARY L. REV. 857, 867 (2017); Solon Barocas &
Andrew D. Selbst, Big Data’s Disparate Impact, 104 CALIF. L. REV. 671, 675 (2016).
417
See ERVING GOFFMAN, THE PRESENTATION OF SELF IN EVERYDAY LIFE 19 (1959) (noting
that people wear “masks” and play “roles” as a natural and justifiable part of life); ERVING
GOFFMAN, STIGMA: NOTES ON THE MANAGEMENT OF SPOILED IDENTITY 107 (1963) (describing
how people need time to build trust in relationships before revealing secrets); ALAN F.
WESTIN, PRIVACY AND FREEDOM 35 (1967) (summarizing Goffman’s work to demonstrate
value of privacy).
418
Clue Period and Ovulation Tracker, CLUE, https://helloclue.com/period-tracker-app
[https://perma.cc/69GY-Y2YM] (last visited Feb. 17, 2022).

860 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
to continue.
419
As Nancy Levit remarks, the “development of protection for
relational interests evidences a communitarian view of the role of tort
law. . . . The vision being promoted is one of the responsible social interaction:
a commitment to the value of the permanency of relationships and to appropriate
treatment within those relationships.”
420
The law has recognized relationship harms, though it has done so
inconsistently. Evidentiary privileges restrict the disclosure of communications
between attorney and client, priest and penitent, husband and wife, and
psychotherapist and patient.
421
The point of protecting certain relationships is to
foster candid expression and the preservation of the relationships.
The breach of confidentiality tort extends to certain relationships—mostly
professional ones—but it fails to protect many other relationships, such as
personal and familial ones.
422
Courts have refused to treat companies as having
a duty to keep personal data confidential even though they are in a position of
trust and exercise power over individuals’ personal data.
423
The law of fiduciary relationships also safeguards against relationship harms.
A fiduciary relationship has long been part of the law of trusts and has been
recognized as a special relationship.
424
Because the trustee is in a “position of
special trust, the trustee owes certain special duties to the beneficiary.”
425
As one
of us (Solove) has noted, a wide array of relationships have been deemed to be
fiduciary ones, and the law is open-ended about recognizing such
relationships.
426
According to Jack Balkin, “[b]ecause of their special power
over others and their special relationships to others, information fiduciaries have
special duties to act in ways that do not harm the interests of the people whose
information they collect, analyze, use, sell, and distribute.”
427
Fiduciaries owe
419
See Danielle Keats Citron, Why Sexual Privacy Matters for Trust, 96 WASH. U. L. REV.
1189, 1192 (2019).
420
Nancy Levit, Ethereal Torts, 61 GEO. WASH. L. REV. 136, 150 (1992).
421
SOLOVE & SCHWARTZ, supra note 4, at 499-504.
422
Neil M. Richards & Daniel J. Solove, Privacy’s Other Path: Recovering the Law of
Confidentiality, 96 GEO. L.J. 123, 176-78 (2007).
423
Id. at 157-58.
424
ARI EZRA WALDMAN, PRIVACY AS TRUST: INFORMATION PRIVACY FOR AN INFORMATION
AGE 85 (2018); Neil Richards & Woodrow Hartzog, A Duty of Loyalty for Privacy Law, 99
WASH. U. L. REV. (forthcoming 2021) (on file with authors); Woodrow Hartzog & Neil
Richards, Privacy’s Constitutional Moment and the Limits of Data Protection, 61 B.C. L.
REV. 1687, 1750 (2020).
425
DANIEL J. SOLOVE, THE DIGITAL PERSON: TECHNOLOGY AND PRIVACY IN THE
INFORMATION AGE 102 (2004) [hereinafter SOLOVE, THE DIGITAL PERSON].
426
Id. at 103 (“The types of relationships that qualify as fiduciary ones are not fixed in
stone.”).
427
Jack M. Balkin, Information Fiduciaries and the First Amendment, 49 U.C. DAVIS L.
REV. 1183, 1186 (2016).

2022] PRIVACY HARMS 861
special duties including confidentiality, loyalty, transparency, care, and
others.
428
The list of relationships recognized as fiduciary ones is open-ended rather
than fixed. In breach of confidentiality cases, courts have recognized fiduciary
relationships between doctor and patient, lawyer and client, bank and customer,
as well as school and student.
429
One of us (Solove) has argued that the concept
of fiduciary relationships can be expanded to regulate consumer privacy because
“companies collecting and using our personal information stand in a fiduciary
relationship with us.”
430
Recently, a number of scholars have further developed this argument, most
notably Jack Balkin, Woodrow Hartzog, Neil Richards, and Lauren Scholz. As
Lauren Scholz observes, “Fiduciary law’s core goal [is] preventing opportunistic
behavior.”
431
She contends that “[i]mplying a fiduciary relationship has the
advantage of enabling courts and the justice system to allow and enforce
expectations as they are situated in concrete relationships.”
432
Thus far, however,
the application of the law of fiduciary relationships to privacy has developed
slowly, mainly in breach of confidentiality cases in a limited set of professional
relationships, but it certainly has potential to develop further in the future.
*****
As we have pointed out above, the law lacks coherence and consistency
regarding the recognition of cognizable privacy harms. Courts often fail to
recognize privacy harms and thwart the enforcement of privacy violations or
leave them unremedied. Our typology of privacy harms aims to help explain
why each type is harmful. We also have endeavored to show that there are
concepts in other legal contexts that could be applied to recognize certain types
of privacy harms.
CONCLUSION
A well-calibrated legal response to privacy cases would permit socially
beneficial personal data practices while requiring robust protections for the
handling of personal data. Its primary focus should be on the deterrence of
violations with the goal of encouraging widespread compliance. Compensation
is important for individuals who have suffered significant harm.
428
Lauren Henry Scholz, Fiduciary Boilerplate: Locating Fiduciary Relationships in
Information Age Consumer Transactions, 46 J. CORP. L. 143, 192 (2020) (“[Fiduciary duties]
may include duty of loyalty, duty of care, duty of disclosure and honesty, duty of
confidentiality, and a heightened duty of good faith.”).
429
Richards & Solove, supra note 422, at 157-58 (listing fiduciary relationships to which
courts have applied tort of breach of confidentiality).
430
SOLOVE, THE DIGITAL PERSON, supra note 425, at 103.
431
Scholz, supra note 428, at 193.
432
Id.

862 BOSTON UNIVERSITY LAW REVIEW [Vol. 102:793
Legal intervention should be designed to ensure that socially beneficial
information practices continue. Our economy depends upon the collection and
sharing of personal data. At the same time, personal data practices are inherently
risky. Privacy law aims to ensure that personal data is used properly, that
individuals have the ability to make decisions about their personal data, and that
there are meaningful guardrails and boundaries about how data is collected,
used, or disclosed.
But struggles with recognizing cognizable privacy harms have impeded the
law’s effectiveness. Failing to recognize harm caused by certain activities can
result in the failure to legislate to protect against such harms or develop
regulatory strategies that adequately enforce against them.
The most deleterious impact of failing to recognize harm has occurred in
litigation. Crabbed conceptions of harm have led courts to dismiss cases that are
a key lynchpin for privacy law enforcement. The common law as well as
litigation of private rights of action have much to contribute to the development
of privacy regulation. The common law remains underdeveloped. Although at
present, the common law has failed to develop adequate protections of privacy
in the digital age, the common law has doctrines, concepts, and remedies that
can be very effective tools for protecting privacy.
Private litigation can play a major role in effective privacy law enforcement,
and there are foundations in the law for it to develop in productive ways. For
example, one of us (Citron) has contended that strict liability has been
underutilized in privacy cases.
433
Strict liability obviates proving fault, and the
vast repositories of personal data that are being maintained about people can be
analogized to the ultrahazardous activities of the Industrial Age. Lauren Scholz
argues that restitution is a viable remedy for many privacy violations.
434
Restitution involves returning benefits that unjustly enriched a defendant.
Scholz also recommends that “[g]iven the cramped nature of the privacy torts, a
better avenue for tort law for data trafficking lies in torts related to wrongful
business practices. This family of torts has the aim of promoting basic fair play
in commerce.”
435
Scholars have recommended developing the protections of
fiduciary relationships to apply to companies that process personal data,
including one of the authors of this Article.
436
Moreover, various federal statutes
lacking a private right of action can still serve as the basis for the standard of
433
Danielle Keats Citron, Reservoirs of Danger: The Evolution of Public and Private Law
at the Dawn of the Information Age, 80 S. CAL. L. REV. 241, 245 (2007).
434
Scholz, supra note 127, at 659 (arguing that restitution provides most appropriate
remedy for many instances of privacy infringement).
435
Id. at 668 (footnote omitted).
436
See, e.g., SOLOVE, THE DIGITAL PERSON, supra note 425, at 103 (“I posit that the law
should hold that companies collecting and using our personal information stand in a fiduciary
relationship with us.”); Balkin, supra note 427, at 1186 (arguing that many technology
companies “should be seen as information fiduciaries toward their customers and end-users”);
Scholz, supra note 428, at 146 (arguing that “implying fiduciary relationships into consumer
contracts is feasible and desirable”).

2022] PRIVACY HARMS 863
care in common law tort actions, such as UDAP laws, negligence, breach of
confidentiality, and others.
437
The requirement of harm has been a significant impediment to the law’s
development. The rigid clinging to an approach where enforcement goals and
remedies are misaligned results in cases that are inconsistent and incoherent.
With the proper alignment, a broader recognition of privacy harms, a better
understanding of privacy problems, and a more flexible approach, the law can
more effectively protect privacy in ways that are fair to all stakeholders.
437
See supra text accompanying notes 109-16.
