
SED Management
• Security Policies for Self Encrypting Drives , on page 1
• Security Guidelines and Limitations for SED Management , on page 1
• Security Flags for Controller and Disk, on page 2
• Security Related Operations, on page 2
• Enabling Security on a Disk, on page 3
• Creating a Local Security Policy, on page 4
• Modifying the Security Policy from Local to Remote, on page 5
• Modifying the Security Key of a Local Security Policy, on page 6
• Remote Operations, on page 7
Security Policies for Self Encrypting Drives
Self-Encrypting Drives (SEDs) have special hardware that encrypts incoming data and decrypts outgoing data
in real-time. The data on the disk is always encrypted in the disk and stored in the encrypted form. The
encrypted data is always decrypted on the way out of the disk. A media encryption key controls this encryption
and decryption. This key is never stored in the processor or memory. Cisco UCS Manager supports SEDs on
Cisco UCS C-Series and S-Series servers.
SEDs are locked using a security key. The security key, which is also known as Key-Encryption Key or an
authentication passphrase, is used to encrypt the media encryption key. If the disk is not locked, no key is
required to fetch the data.
Cisco UCS Central enables you to configure security keys locally or remotely. When you configure the key
locally, you must remember the key. In case you forget the key, it cannot be retrieved and the data is lost.
You can configure the key remotely by using a key management server (also known as KMIP server). This
method addresses the issues related to safe-keeping and retrieval of the keys in the local management.
The encryption and decryption for SEDs is done through the hardware. Thus, it does not affect the overall
system performance. SEDs reduce the disk retirement and redeployment costs through instantaneous
cryptographic erasure. Cryptographic erasure will render all data on the SED unreadable when the encryption
key is destroyed.
Security Guidelines and Limitations for SED Management
The following security guidelines and limitations apply to SED management from Cisco UCS Central:
SED Management
1

• Storage operations get applied only when the server is powered on, and they do not trigger a server
reboot.
• A global service profile (GSP) with a security policy gets pushed to Cisco UCS Manager releases prior
to 3.1(3), and the security policies related operations are cleaned up and an unsecured LUN is created.
• A Cisco UCS Manager downgrade fails if a storage controller with Drive Security Enable is present in
the domain.
• A GSP association fails with a config-failure status/message if it is associated with an unsupported
server, or a supported server with unsupported firmware.
• A GSP association fails with a config-failure status/message if LUN security is set to Enabled
in the Disk Configuration Policy but if the Security policy is not created in the storage profile.
• A GSP association fails if the Security policy is deleted from the storage profile after the Storage Controller
is set to Drive Security Enable.
Security Flags for Controller and Disk
Security flags indicate the current security status of the storage controller and disks.
The storage controller and disks have the following security flags:
• Security Capable—Indicates that the controller, LUN, or disk is capable of supporting SED management.
• Security Enable—Indicates that the security key is programmed on the controller, disk, or LUN, and
security is enabled on the device. This flag is set when you configure a security policy and associate it
to a server, making the controller and disk secure. This flag is not set on a Cisco HyperFlex device.
• Secured—Indicates that the security key is programmed on the disk, and security is enabled on the Cisco
HyperFlex device.
The following security flags are exclusive to storage disks:
• Locked—Indicates that the disk key does not match the key on the controller. This happens when you
move disks across servers that are programmed with different keys. The data on a locked disk is
inaccessible and the operating system cannot use the disk. To use this disk, you must either unlock the
disk or secure erase the foreign configuration.
• Foreign Secured—Indicates that a secure disk is in foreign configuration. This happens when you unlock
a locked disk with the right key, but the disk is in a foreign configuration state and the data on it is
encrypted. To use this disk, you can either import or clear the foreign configuration.
Security Related Operations
You can create security policies for Self-Encrypting Drives (SEDs) through a Storage Profile in Cisco UCS
Central. In addition to creating security policies, you can perform additional operations on the supported
servers. The following table lists the remote operations and their descriptions:
SED Management
2
SED Management
Security Flags for Controller and Disk
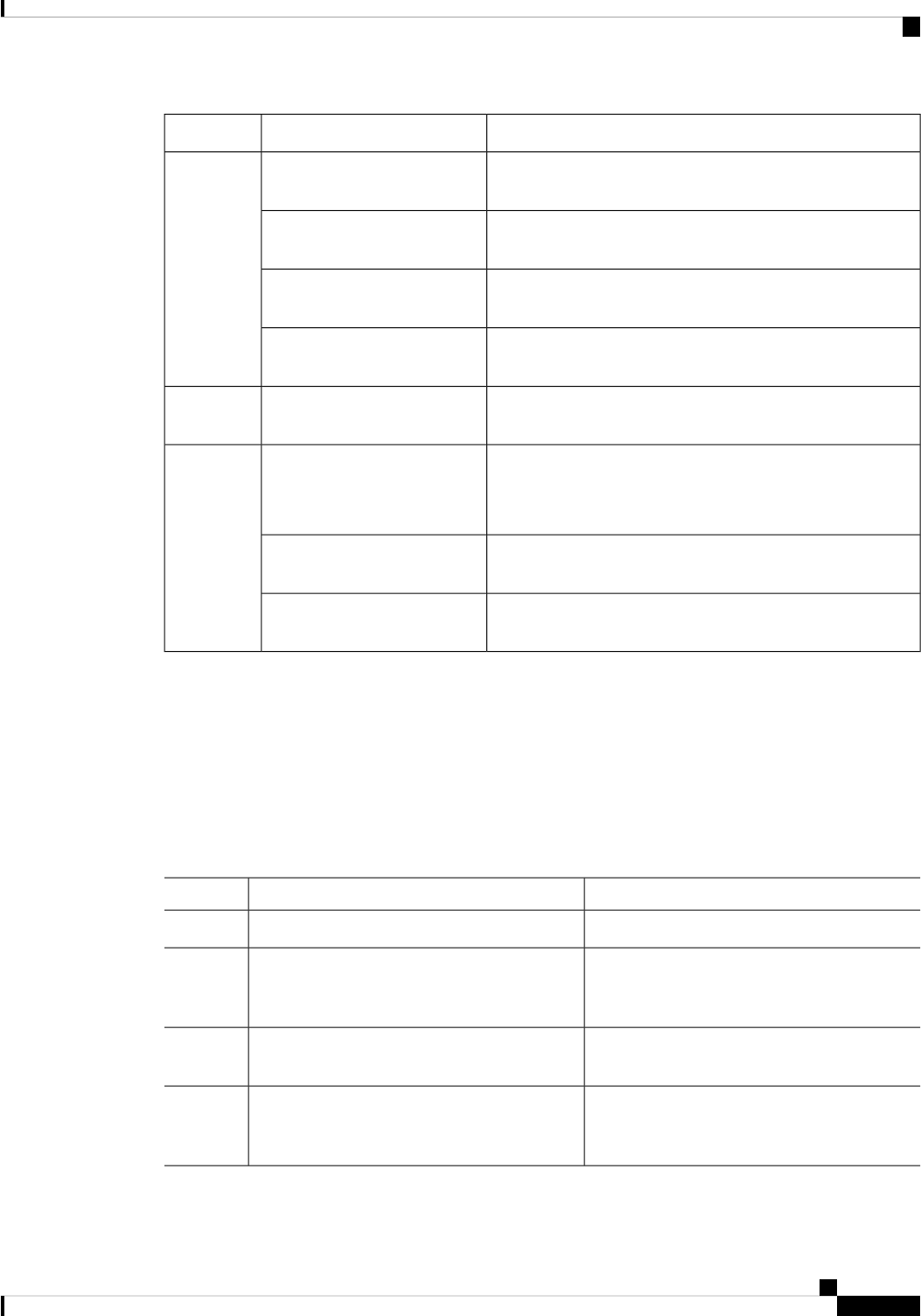
ActionRemote ActionComponent
Unlocks ForeignSecured and Locked Disks encrypted using
a Local Policy.
Unlock DiskController
Modifies the Key in the KMIP Server and fetches the new
Key for Encryption.
Modify Remote Key
Disables Security on the Controller when no Secured Disks
are present on Controller.
Disable Security
Unlocks ForeignSecured and Locked Disks encrypted using
a Remote Policy.
Unlock for Remote
Secures LUNs comprised only of SEDs when the Controller
is Security Enabled.
Secure Virtual DriveVirtual Disk
Used to Secure JBOD
Self-Encrypting Drive(SED) when Controller is Security
Enabled.
Enable EncryptionPhysical
Disk
Erases disk cryptographically to make it Unsecured and
Reusable.
Secure Erase
Erases ForeignSecured and Locked disks cryptographically
to make them Unsecured and Unconfigured Good
Secure Erase Foreign
Configuration
For more information about SED Management and security policies, see Cisco UCS Manager Storage
Management Guide.
Enabling Security on a Disk
You can configure the drive security settings for the Self Encrypting Disks using the Storage profile settings.
Procedure
PurposeCommand or Action
Enters policy manager mode.UCSC# connect policy-mgr
Step 1
Enters organization mode for the specified
organization. To enter the root organization
mode, type / as the org-name .
UCSC(policy-mgr)# scope org org-name
Step 2
Creates the specified storage profile and enters
organization storage profile mode.
UCSC(policy-mgr) /org # create
storage-profile profile-name
Step 3
Creates a security policy for the specified
storage profile and enters the security policy
mode.
UCSC(policy-mgr) /org/storage-profile* #
create security
Step 4
SED Management
3
SED Management
Enabling Security on a Disk
PurposeCommand or Action
Creates a drive security policy for the specified
storage profile security and enters the drive
security policy mode.
UCSC(policy-mgr)
/org/storage-profile/security* # create
drive-security
Step 5
Creates a local security policy for the specified
storage profile and enters the local policy mode.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security* #
create local
Step 6
Sets the specified security key for the local
policy. The security key must have 32
characters.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/local*
# set security-keysecurity-key
Step 7
Commits the transaction to the system
configuration.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/local*
# commit buffer
Step 8
Creating a Local Security Policy
Procedure
PurposeCommand or Action
Enters policy manager mode.UCSC# connect policy-mgr
Step 1
Enters organization mode for the specified
organization. To enter the root organization
mode, type / as the org-name .
UCSC(policy-mgr)# scope org org-name
Step 2
Creates the specified storage profile and enters
organization storage profile mode.
UCSC(policy-mgr) /org # create
storage-profile profile-name
Step 3
Creates a security policy for the specified
storage profile and enters the security policy
mode.
UCSC(policy-mgr) /org/storage-profile* #
create security
Step 4
Creates a drive security policy for the specified
storage profile security and enters the drive
security policy mode.
UCSC(policy-mgr)
/org/storage-profile/security* # create
drive-security
Step 5
Creates a local security policy for the specified
storage profile and enters the local policy mode.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security* #
create local
Step 6
Sets the specified security key for the local
policy. The security key must have 32
characters.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/local*
# set security-keysecurity-key
Step 7
Step 8
SED Management
4
SED Management
Creating a Local Security Policy
PurposeCommand or Action
Commits the transaction to the system
configuration.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/local*
# commit buffer
Step 9
Example
UCSC # connect policy mgr
UCSC(policy-mgr)# scope org
UCSC(policy-mgr)# create storage-profile stp-demo
UCSC(policy-mgr)/org/storage-profile* # create security
UCSC(policy-mgr)/org/storage-profile/security* # create drive-security
UCSC(policy-mgr)/org/storage-profile/security/drive-security* # create local
UCSC(policy-mgr)/org/storage-profile/security/drive-security/local* # set security-key
thereare32charactersinthisseckey
UCSC(policy-mgr)/org/storage-profile/security/drive-security/local* # commit-buffer
Modifying the Security Policy from Local to Remote
Procedure
PurposeCommand or Action
Enters policy manager mode.UCSC# connect policy-mgr
Step 1
Enters organization mode for the specified
organization. To enter the root organization
mode, type / as the org-name .
UCSC(policy-mgr)# scope org org-name
Step 2
Enters the specified storage profile
configuration mode for the specified storage
profile.
UCSC(policy-mgr) /org # scope
storage-profile profile-name
Step 3
Enters the security policy mode for the
specified storage profile.
UCSC(policy-mgr) /org/storage-profile #
scope security
Step 4
Enters the drive security policy mode for the
specified storage profile security.
UCSC(policy-mgr)
/org/storage-profile/security* # scope
drive-security
Step 5
Creates and enters the remote policy mode.UCSC(policy-mgr)
/org/storage-profile/security/drive-security #
create remote
Step 6
Specifies the existing key deployed on the
server.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
set deployed-security-keyexisting-security-key
Step 7
Sets the primary server hostname or IP address.UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
set primary-serverprimary-server-name
Step 8
SED Management
5
SED Management
Modifying the Security Policy from Local to Remote
PurposeCommand or Action
(Optional)
Sets the secondary server hostname or IP
address.
(Optional) UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
set secondary-serversecondary-server-name
Step 9
Sets the port number of the KMIP server.
KMIP server port numbers can range from
1024 to 65535.
(Optional) UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
set portkmip-server-port-number
Step 10
Sets the KMIP certificate to the remote security
policy.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
set server-certificate
Step 11
Sets the number of seconds in which
communication between the storage and the
(Optional) UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
set timeout timeout
Step 12
KMIP server times out. Timeout can range
from 5 seconds to 20 seconds.
Commits the transaction to the system
configuration.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
commit-buffer
Step 13
Enters the drive security policy mode.UCSC(policy-mgr)
/org/storage-profile/security/drive-security/remote*#
exit
Step 14
Modifying the Security Key of a Local Security Policy
Procedure
PurposeCommand or Action
Enters policy manager mode.UCSC# connect policy-mgr
Step 1
Enters organization mode for the specified
organization. To enter the root organization
mode, type / as the org-name .
UCSC(policy-mgr)# scope org org-name
Step 2
Enters the specified storage profile
configuration mode for the specified storage
profile.
UCSC(policy-mgr) /org # scope
storage-profile profile-name
Step 3
Enters the security policy mode for the specified
storage profile.
UCSC(policy-mgr) /org/storage-profile # scope
security
Step 4
Enters the drive security policy mode for the
specified storage profile security.
UCSC(policy-mgr)
/org/storage-profile/security* # scope
drive-security
Step 5
SED Management
6
SED Management
Modifying the Security Key of a Local Security Policy
PurposeCommand or Action
Enters the local policy mode for the the
specified storage profile.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security #
scope local
Step 6
Specifies the existing key deployed on the
server to configure a new key.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/local*#
set deployed-security-keyexisting-security-key
Step 7
Sets the new security key for the local policy.UCSC(policy-mgr)
/org/storage-profile/security/drive-security/local*#
set security-keynew-security-key
Step 8
Commits the transaction to the system
configuration.
UCSC(policy-mgr)
/org/storage-profile/security/drive-security/local*#
commit-buffer
Step 9
Remote Operations
This section describes the options for configuring security related operations on the controller, local disk, or
virtual disk. For more information on the permitted operations, see Security Related Operations, on page 2.
Procedure
PurposeCommand or Action
Enters organization mode for the specified
organization. To enter the root organization
mode, type / as the org-name .
UCSC(resource-mgr)# scope org org-name
Step 1
Enters the specified UCS domain.UCSC(resource-mgr)/domain-mgmt# scope
ucs-domain name
Step 2
Enters the specific chassis.UCSC(resource-mgr)/domain-mgmt/ucs-domain#
scope chassis name
Step 3
Enters the specific server.UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis#
scope server name
Step 4
Enters the RAID controller mode.UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server#
scope raid-controller raid-controller-id
Step 5
Set an admin state for the RAID controller.
See Security Related Operations, on page 2
for a list of the permitted security operations.
UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server#
set admin-state name
Step 6
Unlock Disk for a Local Security Policy
requires a Key as a parameter. The Key must
be 32 characters long.
(Controller)
UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server/
raid-controller # set admin-state
unlock-diskname
Step 7
Commits the transaction to the system
configuration.
UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server/
raid-controller # commit buffer
Step 8
SED Management
7
SED Management
Remote Operations
PurposeCommand or Action
Unlock Disk for a Remote Security Policy does
not require a Key as a parameter.
(Controller) (Optional)
UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server/
raid-controller # set admin-state unlock-disk
Step 9
Set security for the local disk.(Local-Disk)(Optional)
UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server/
Step 10
raid-controller/local-disk # set admin-state
enable-security
These choices are available for a local disk:(Local-Disk)(Optional)
UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server/
Step 11
raid-controller/local-disk # set admin-state
clear name
• secure-drive - Equivalent to Secure Erase
in the Cisco UCS Central GUI.
• secure-foreign-config-drive - Equivalent
to Secure Erase Foreign Configuration in
the Cisco UCS Central GUI.
(Virtual-Disk)(Optional)
UCSC(resource-mgr)/domain-mgmt/ucs-domain/chassis/server/
Step 12
raid-controller/virtual-drive # set admin-state
secure-drive-group
SED Management
8
SED Management
Remote Operations
