Privacy Impact Assessment for the VA IT System called:
Salesforce: VA Help Desk Application
Veterans Affairs Central Office (VACO)
Office of Information Technology (OIT)
Date PIA submitted for review:
11/4/2022
System Contacts:
System Contacts
Name
E-mail
Phone Number
Privacy Officer
Gina Siefert
Gina.siefert@va.gov
202-632-8430
Information System
Security Officer (ISSO)
James Boring
James.Boring@va.gov
215-842-200
Ext. 4613
Information System
Owner
Michael Domanski
Michael.Doman[email protected]
727-595-7291
Version Date: October 1, 2022
Page 1 of 24
Abstract
The abstract provides the simplest explanation for “what does the system do?” and will be published
online to accompany the PIA link.
This Veterans Affairs Help Desk Application provides the Salesforce Lightning interface to
efficiently and accurately show the requests submitted by System Integrators and Citizen
developers in response to Veterans Affairs requirements. This module includes help desk cases,
but also several project management tools to track release- and architecture-related information
for new and existing modules. The VA DTC documentation is in the VA DTC Salesforce help
desk chatter, service cases, modules, and data structures to support the system life cycle from
inception to delivery.
Overview
The overview is the most important section of the PIA. A thorough and clear overview gives the reader
the appropriate context to understand the responses in the PIA. The overview should contain the
following elements:
1 General Description
A. The IT system name and the name of the program office that owns the IT system.
The Veterans Affairs Help Desk Application is owned by the VHA Office of Information
Technology (OIT
B. The business purpose of the program, IT system, or technology and how it relates to the
program office and agency mission.
The purpose of the Help Desk Application is to track help desk cases, as well as leverage
several project management tools to track release- and architecture-related information for new
and existing modules.
C. Indicate the ownership or control of the IT system or project.
The Veterans Affairs Help Desk Application is owned by the VHA Office of Information
Technology (OIT
2. Information Collection and Sharing
D. The expected number of individuals whose information is stored in the system and a brief
description of the typical client or affected individual.
The typical help desk client will be VHA employees who require assistance with a technical
issue or problem. The number of help desk cases will vary depending on how many issues or
problems are reported.
E. A general description of the information in the IT system and the purpose for collecting this
information.
The VA Help Desk Application will collect and track the name and contact information (email
and phone) for those reporting issues or problems. This information is collected and stored so
Help Desk personnel can contact VA employees who report issues regarding their cas
Version Date: October 1, 2022
Page 2 of 24
F. Any information sharing conducted by the IT system. A general description of the modules
and subsystems, where relevant, and their functions.
The VA Help Desk Application does not share information collected with any other system.
G. Whether the system is operated in more than one site, and if so, a description of how use of
the system and PII is maintained consistently in all sites and if the same controls are used
across sites.
The Application is located and maintained in a single location.
3. Legal Authority and SORN
H. A citation of the legal authority to operate the IT system.
The VA Help Desk is a minor application that falls under the Salesforce Government
Cloud platform ATO authorized on 8/7/2020.
I. If the system is in the process of being modified and a SORN exists, will the SORN require
amendment or revision and approval? If the system is using cloud technology, does the SORN
for the system cover cloud usage or storage?
A System of Record Notice (SORN) is not required.
D. System Changes
J. Whether the completion of this PIA will result in circumstances that require changes to
business processes
Completion of this PIA will not result in changes to any business process.
K. Whether the completion of this PIA could potentially result in technology changes
Completion of this PIA will not result in any technologies changes.
Section 1. Characterization of the Information
The following questions are intended to define the scope of the information requested and collected as
well as the reasons for its collection as part of the program, IT system, or technology being developed.
1.1 What information is collected, used, disseminated, created, or maintained in the system?
Identify and list all Sensitive Personal Information (SPI) that is collected and stored in the system,
including Individually Identifiable Information (III), Individually Identifiable Health Information (IIHI),
Protected Health Information (PHI), and Privacy- Protected Information. For additional information on
these information types and definitions, please see VA Directives and Handbooks in the 6500 series
(https://vaww.va.gov/vapubs/). If the system creates information (for example, a score, analysis, or
report), list the information the system is responsible for creating.
If a requesting system receives information from another system, such as a response to a background
check, describe what information is returned to the requesting system.
This question is related to privacy control AP-1, Authority To Collect, and AP-2, Purpose Specification.
Version Date: October 1, 2022
Page 3 of 24
The information selected below must match the information provided in question 2.1 as well as the data
elements columns in 4.1 and 5.1.
Please check any information listed below that your system collects, uses, disseminates, creates, or
maintains. If additional SPI is collected, used, disseminated, created, or maintained, please list those in
the text box below:
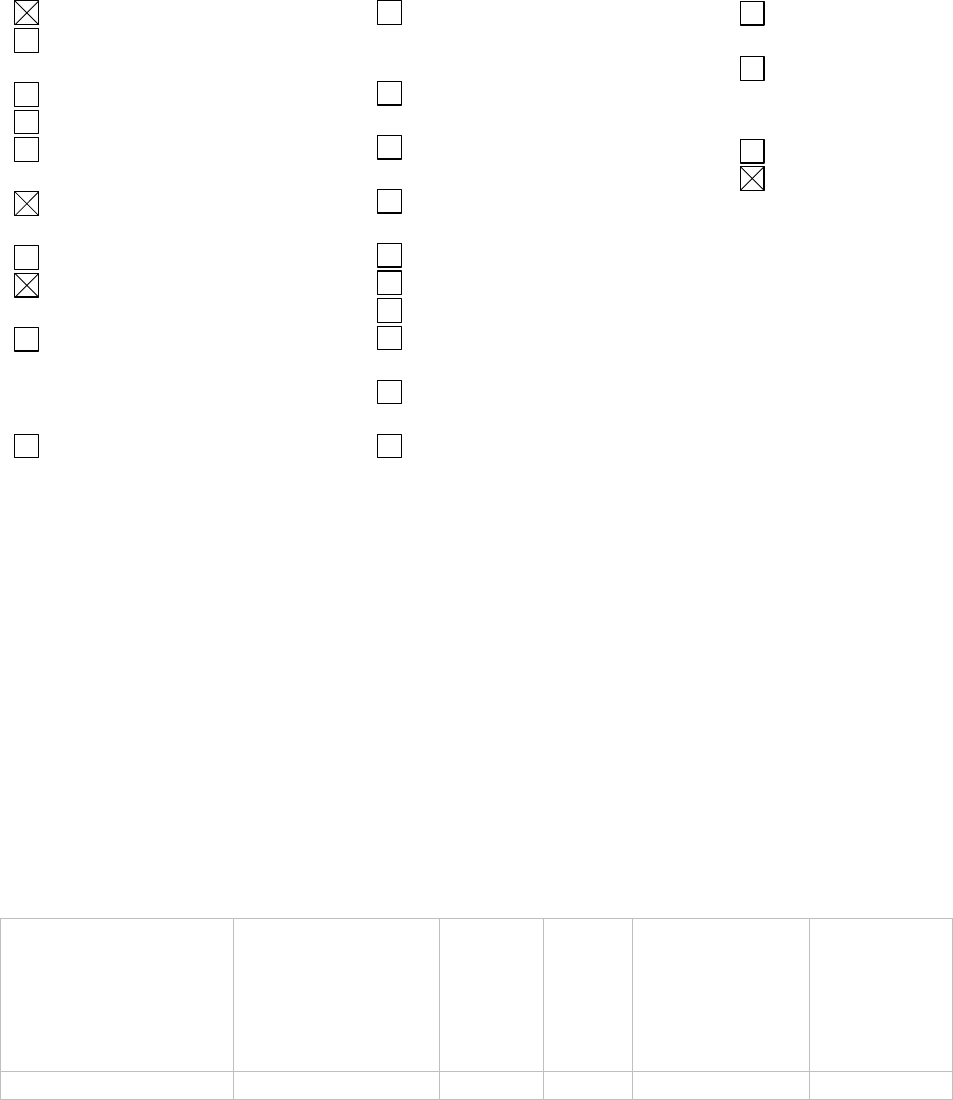
Name
Social Security
Number
Date of Birth
Mother’s Maiden Name
Personal Mailing
Address
Personal Phone
Number(s)
Personal Fax Number
Personal Email
Address
Emergency Contact
Information (Name, Phone
Number, etc. of a different
individual)
Financial Information
Health Insurance
Beneficiary Numbers
Account numbers
Certificate/License
numbers*
Vehicle License Plate
Number
Internet Protocol (IP)
Address Numbers
Medications
Medical Records
Race/Ethnicity
Tax Identification
Number
Medical Record
Number
Gender
Integrated Control
Number (ICN)
Military
History/Service
Connection
Next of Kin
Other Data Elements
(list below)
Additional unique identifying information collected: VA email and VA phone Number
*Specify type of Certificate or License Number (e.g. Occupational, Education, Medical)
PII Mapping of Components (Servers/Database)
The VA Help Desk Application does not interact with any external databases or systems.
Note: Due to the PIA being a public facing document, please do not include the server names in the table.
The first table of 3.9 in the PTA should be used to answer this question.
Internal Database Connections
Database Name of the
information system
collecting/storing PII
Does this system
collect PII?
(Yes/No)
Does
this
system
store
PII?
(Yes/No)
Type
of PII
(SSN,
DOB,
etc.)
Reason for
Collection/
Storage of PII
Safeguards
N/A
N/A
N/A
N/A
N/A
N/A
Version Date: October 1, 2022
Page 4 of 24
1.2 What are the sources of the information in the system?
These questions are related to privacy controls DI-1, Data Quality, and IP-1, Consent.
1.2a List the individual, entity, or entities providing the specific information identified above. For
example, is the information collected directly from the individual as part of an application for a
benefit, or is it collected from other sources such as commercial data aggregators?
The information or data contained in the VA Help Desk Application is collected from the VA
employees when they call in or fill out the online form to report an issue or problem. No additional
external data sources are used.
1.2b Describe why information from sources other than the individual is required. For example, if a
program’s system is using data from a commercial aggregator of information or data taken from
public Web sites, state the fact that this is where the information is coming from and then in question
indicate why the system is using this source of data.
No information from external sources is used.
1.2c If the system creates information (for example, a score, analysis, or report), list the system as a
source of information.
No analysis or reporting from external systems is conducted.
1.3 How is the information collected?
These questions are related to privacy controls DI-1, Data Quality, and IP-1, Consent.
1.3a This question is directed at the means of collection from the sources listed in question 1.2.
Information may be collected directly from an individual, received via electronic transmission from
another system, or created by the system itself. Specifically, is information collected through
technologies or other technologies used in the storage or transmission of information in identifiable
form?
The name and contact information of VA Employees reporting issues or problems is voluntarily
provided by them and collected by the VA Help Desk via the online form or by the Help Desk
employees entering it into the system.
1.3b If the information is collected on a form and is subject to the Paperwork Reduction Act, give the
form’s OMB control number and the agency form number.

Version Date: October 1, 2022
Page 5 of 24
The information is not subject to the Paperwork Reduction Act.
1.4 How will the information be checked for accuracy? How often will it be checked?
These questions are related to privacy controls DI-1, Data Quality, and DI-2, Data Integrity and
Integrity Board.
1.4a Discuss whether and how often information stored in the system is checked for accuracy. Is
information in the system checked against any other source of information (within or outside your
organization) before the information is used to make decisions about an individual? For example, is
there a computer matching agreement in place with another government agency? For systems that
receive data from internal data sources or VA IT systems, describe the system checks to ensure that
data corruption has not occurred during transmission.
The information collected from VA employees reporting issues or problems to the VA Help
Desk is not checked for accuracy utilizing a formal process or system. However, the contact
information for those reporting problems via the VA Help Desk may be updated by VA Help
Desk employees as they follow up on individual cases.
1.4b If the system checks for accuracy by accessing a commercial aggregator of information,
describe this process and the levels of accuracy required by the contract.
The system does not utilize a commercial aggregator.
1.5 What specific legal authorities, arrangements, and agreements defined the collection of
information?
List the full legal authority for operating the system, specifically the authority to collect the
information listed in question 1.1. Provide the authorities in a manner understandable to any
potential reader, i.e., do not simply provide a legal citation; use statute names or regulations in
addition to citations. Legal authorities include Federal laws, regulations, statutes, and Executive
Orders. This question is related to privacy control AP-1, Authority to Collect
When VA employee signs a legal contract to work at the VA, they have agreed to have their contact
information collected. The Privacy Act of 1974, as amended, 5 U.S.C. § 552a, establishes a code of
fair information practices that governs the collection, maintenance, use, and dissemination of
information about individuals that is maintained in systems of records by federal agencies.
1.6 PRIVACY IMPACT ASSESSMENT: Characterization of the information
Consider the specific data elements collected and discuss the potential privacy risks and what steps,
if any are currently being taken to mitigate those identified risks. (Work with your System ISSO to
complete this section)

Version Date: October 1, 2022
Page 6 of 24
Consider the following Fair Information Practice Principles (FIPPs) when assessing the risk to
individual privacy:
Principle of Purpose Specification: Explain how the collection ties with the purpose of the
underlying mission of the organization and its enabling authority.
Principle of Minimization: Is the information directly relevant and necessary to accomplish the
specific purposes of the program?
Principle of Individual Participation: Does the program, to the extent possible and practical, collect
information directly from the individual?
Principle of Data Quality and Integrity: Are there policies and procedures for VA to ensure that
personally identifiable information is accurate, complete, and current?
This question is related to privacy control AR-1, Governance and Privacy Program, and AR-2,
Privacy Impact and Risk Assessment.
Follow the format below when entering your risk assessment:
Privacy Risk: VA Help Desk Application is a self-contained system that collects the name, phone
number and email for those using the application to report issues or problems or make a request.
Only the information needed to follow up is collected directly from the VA employees contacting the
help desk. The information collected is already available in the Global Access Locator (GAL)
system. So, no major risk exists if this information were to be accessed by someone outside the Help
Desk.
Mitigation: VA Help Desk Application employs the standard VA-required security measures for a
High-Impact System designed to ensure that the information is not inappropriately disclosed or
released. These security measures are specified in the controls VA Directive 6500. VA Handbook
6500 “Risk Management Framework for VA Information Systems – Tier 3: VA Information Security
Program.
Section 2. Uses of the Information
The following questions are intended to clearly delineate the use of information and the accuracy of
the data being used.
2.1 Describe how the information in the system will be used in support of the program’s
business purpose.
Identify and list each use (both internal and external to VA) of the information collected or
maintained. This question is related to privacy control AP-2, Purpose Specification.
Name: Used to identify the VA employee making a request, or reporting an issue or problem; VA
Work Phone number: Used for follow-up contact with VA employee making a request, or reporting
Version Date: October 1, 2022
Page 7 of 24
an issue or problem; VA Work Email: Used for follow-up contact with VA employee making a
request, or reporting an issue or problem; Personal Phone number: Used for follow-up contact with
VA employee making a request, or reporting an issue or problem; Personal Email: Used for follow-
up contact with VA employee making a request, or reporting an issue or problem
2.2 What types of tools are used to analyze data and what type of data may be produced?
These questions are related to privacy controls DI-1, Data Quality, DI-2, Data Integrity and
Integrity Board, and SE-1, Inventory of Personally Identifiable Information.
2.2a Many systems sift through large amounts of information in response to a user inquiry or
programmed functions. Systems may help identify areas that were previously not obvious and need
additional research by agents, analysts, or other employees. Some systems perform complex
analytical tasks resulting in, among other types of data, matching, relational analysis, scoring,
reporting, or pattern analysis. Describe any type of analysis the system conducts and the data that is
created from the analysis.
Information about the issue or problem being reported by the VA employee to the VA Help Desk
will be collected and analyzed using Salesforce to create reports regarding the types of requests
being made and issues and problems being reported.
2.2b If the system creates or makes available new or previously unutilized information about an
individual, explain what will be done with the newly derived information. Will it be placed in the
individual's existing record? Will a new record be created? Will any action be taken against or for
the individual identified because of the newly derived data? If a new record is created, will the newly
created information be accessible to Government employees who make determinations about the
individual? If so, explain fully under which circumstances and by whom that information will be
used.
Any new information about request being made or the issue or problem being reported by the VA
employee to the VA Help Desk will be attached to the existing issue. Any action taken based on the
new information will be to fulfill the request or resolve the issue or problem reported.
2.3 How is the information in the system secured?
These questions are related to security and privacy controls SC-9, Transmission Confidentiality, and
SC-28, Protection of Information at Rest.
2.3a What measures are in place to protect data in transit and at rest?
VA Help Desk Application (Salesforce) is an encrypted secure system. Data in transit are
protected by HTTPS site-to-site encryption.
2.3b If the system is collecting, processing, or retaining Social Security Numbers, are there
additional protections in place to protect SSNs?
OMB Memorandum M-06-15 applies to the policies for safeguarding sensitive personally
identifiable information. Minimal identifying information is being collected.

Version Date: October 1, 2022
Page 8 of 24
2.3c How is PII/PHI safeguarded in accordance with OMB Memorandum M-06-15?
PII data are encrypted at rest with Salesforce Shield encryption. which uses a FIPS 140-2 secure
connection.
2.4 PRIVACY IMPACT ASSESSMENT: Use of the information.
Describe any types of controls that may be in place to ensure that information is handled in
accordance with the uses described above. Example: Describe if training for users of the project
covers how to appropriately use information. Describe the disciplinary programs or system
controls (i.e. denial of access) that are in place if an individual is inappropriately using the
information.
Consider the following FIPPs below to assist in providing a response:
Principle of Transparency: Is the PIA and SORN, if applicable, clear about the uses of the
information?
Principle of Use Limitation: Is the use of information contained in the system relevant to the mission
of the project?
This question is related to privacy control AR-4, Privacy Monitoring and Auditing, AR-5, Privacy
Awareness and Training, and SE-2, Privacy Incident response.
2.4a How is access to the PII determined?
Access to PII for this system is reserved for VA employees at the VA Help Desk. Administrators
must approve and provide users with access to the system. Administrators will be responsible for
monitoring and safeguarding the system. No data is shared either internally or externally.
2.4b Are criteria, procedures, controls, and responsibilities regarding access documented?
Yes.
2.4c Does access require manager approval?
Administrators must approve and provide users with access to the system.
2.4d Is access to the PII being monitored, tracked, or recorded?
Yes.
2.4e Who is responsible for assuring safeguards for the PII?
Version Date: October 1, 2022
Page 9 of 24
Administrators will be responsible for monitoring and safeguarding the system.
Section 3. Retention of Information
The following questions are intended to outline how long information will be retained after the initial
collection.
3.1 What information is retained?
Identify and list all information collected from question 1.1 that is retained by the system.
This question is related to privacy controls DM-1, Minimization of Personally Identifiable
Information, and DM-2, Data Retention and Disposal
Information such as name, work phone, work email, personal phone and personal email is retained in
this system.
3.2 How long is information retained?
In some cases VA may choose to retain files in active status and archive them after a certain period
of time. State active file retention periods, as well as archived records, in number of years, for the
information and record types. For example, financial data held within your system may have a
different retention period than medical records or education records held within your system,
please be sure to list each of these retention periods. The VA records officer should be consulted
early in the development process to ensure that appropriate retention and destruction schedules are
implemented. If the system is using cloud technology, will it be following the NARA approved
retention length and schedule? This question is related to privacy control DM-2, Data Retention and
Disposal.
Information is retained in this system until the request or issue reported to the VA Help Desk is
resolved. Information is kept for 4 years for historical reference.
3.3 Has the retention schedule been approved by the VA records office and the National
Archives and Records Administration (NARA)?
An approved records schedule must be obtained for any IT system that allows the retrieval of a
record via a personal identifier. The VA records officer will assist in providing a proposed schedule.
The schedule must be formally offered to NARA for official approval. Once NARA approves the
proposed schedule, the VA records officer will notify the system owner. Please work with the system
Privacy Officer and VA Records Officer to answer these questions.
This question is related to privacy control DM-2, Data Retention and Disposal.
3.3a Are all records stored within the system of record indicated on an approved disposition
authority?

Version Date: October 1, 2022
Page 10 of 24
Yes, the retention schedule for the Salesforce Development Platform (SFDP) also applies to VA Help
Desk. SFDP complies with all VA retention and disposal procedures specified in VA Handbook 6300
and VA Directive 6500. Records contained in the Salesforce FedRAMP cloud will be retained as
long as the information is needed in accordance with a NARA-approved retention period. VA
manages Federal records in accordance with NARA statues including the Federal Records Act (44
U.S.C. Chapters 21, 29, 31, 33) and NARA regulations (36 CFR Chapter XII Subchapter B). SFDP
records are retained according to Record Control Schedule 10-1 Section 4. (Disposition of Records)
The appropriate NARA records retention schedule is as follows: Skill set records, GRS 2.0 item 120.
Disposition instructions: Destroy when business use ceases. DAA-GRS-2017-0007-0018.
3.3b Please indicate each records retention schedule, series, and disposition authority.
SFDP records are retained according to Record Control Schedule 10-1 Section 4. (Disposition of
Records) The appropriate NARA records retention schedule is as follows: Skill set records, GRS 2.0
item 120. Disposition instructions: Destroy when business use ceases. DAA-GRS-2017-0007-001
3.4 What are the procedures for the elimination or transfer of SPI?
Explain how records are destroyed, eliminated or transferred to NARA at the end of their mandatory
retention period. Please give the details of the process. For example, are paper records shredded
on site, or by a shredding company and accompanied by a certificate of destruction, etc.? This
question is related to privacy control DM-2, Data Retention and Disposal.
No physical (paper) records exist.
3.5 Does the system, where feasible, use techniques to minimize the risk to privacy by using PII
for research, testing, or training?
Organizations often use PII for testing new applications or information systems prior to deployment.
Organizations also use PII for research purposes and for training. These uses of PII increase the
risks associated with the unauthorized disclosure or misuse of the information. Please explain what
controls have been implemented to protect PII used for testing, training and research. This question
is related to privacy control DM-3, Minimization of PII Used in Testing, Training and Research.
Yes, this system only uses information that is already stored within VA. No research or testing will
be done using the VA Help Desk database. Only employees within the office will receive training on
the system. The system, nor its data, will not be utilized for training for any unauthorized employees.
3.6 PRIVACY IMPACT ASSESSMENT: Retention of information
Discuss the risks associated with the length of time data is retained and what steps, if any, are
currently being taken to mitigate those identified risks. (Work with your System ISSO to complete all
Privacy Risk questions inside the document this section).
While we understand that establishing retention periods for records is a formal process, there are
policy considerations behind how long a project keeps information. The longer a project retains

Version Date: October 1, 2022
Page 11 of 24
information, the longer it needs to secure the information and assure its accuracy and integrity. The
proposed schedule should match the requirements of the Privacy Act to keep the minimum amount of
PII for the minimum amount of time, while meeting the Federal Records Act. The schedule should
align with the stated purpose and mission of the system.
Consider the following FIPPs below to assist in providing a response:
Principle of Minimization: Does the project retain only the information necessary for its purpose? Is
the PII retained only for as long as necessary and relevant to fulfill the specified purposes?
Principle of Data Quality and Integrity: Has the PIA described policies and procedures for how PII
that is no longer relevant and necessary is purged?
This question is related to privacy controls DM-1, Minimization of Personally Identifiable
Information, and DM-2, Data Retention and Disposal.
Follow the format below:
Privacy Risk: The risk exists that the contact information provided by VA employees making
requests or reporting issues to the VA Help Desk could be accessed by the public or unauthorized
individuals. Only the minimal data needed to contact the reporting employee is retai
Mitigation: The system utilizes Salesforce Shield 140-2 encryption and has periodic reviews of the
data collected. Periodic reviews of the data collected are conducted.
Section 4. Internal Sharing/Receiving/Transmitting and Disclosure
The following questions are intended to define the scope of information
sharing/receiving/transmitting within VA.
4.1 With which internal organizations is information shared/received/transmitted? What
information is shared/received/transmitted, and for what purpose? How is the information
transmitted?
NOTE: Question 3.9 (second table) on Privacy Threshold Analysis should be used to answer
this question.
Identify and list the names of any program offices, contractor-supported IT systems, and any other
organization or IT system within VA with which information is shared.
State the purpose for the internal sharing. If you have specific authority to share the information,
provide a citation to the authority.
For each interface with a system outside your program office, state what specific data elements
(PII/PHI) are shared with the specific program office, contractor-supported IT system, and any other
organization or IT system within VA.

Version Date: October 1, 2022
Page 12 of 24
Describe how the information is transmitted. For example, is the information transmitted
electronically, by paper, or by some other means? Is the information shared in bulk, on a case-by-
case basis, or does the sharing partner have direct access to the information?
This question is related to privacy controls AP-2, Purpose Specification, AR-3, Privacy Requirements
for Contractors and Service Providers, AR-8, Accounting of Disclosures, TR-1, Privacy Notice, and
UL-1, Internal Use.
Data Shared with Internal Organizations
List the Program
Office or IT System
information is
shared/received with
List the purpose of
the information
being shared
/received with the
specified program
office or IT system
List the specific PII/PHI
data elements that are
processed
(shared/received/transmitted)
with the Program Office or
IT system
Describe the
method of
transmittal
N/A
N/A
N/A
N/A
4.2 PRIVACY IMPACT ASSESSMENT: Internal sharing and disclosure
Discuss the privacy risks associated with the sharing of information within the Department and what
steps, if any, are currently being taken to mitigate those identified risks. (Work with your System
ISSO to complete all Privacy Risk questions inside the document this section).
This question is related to privacy control UL-1, Internal Use.
Follow the format below:
Privacy Risk: N/A
Mitigation: N/A
Section 5. External Sharing/Receiving and Disclosure
The following questions are intended to define the content, scope, and authority for information
sharing external to VA, which includes Federal, State, and local governments, and the private sector.
5.1 With which external organizations (outside VA) is information shared/received? What
information is shared/received, and for what purpose? How is the information transmitted and
what measures are taken to ensure it is secure?
Version Date: October 1, 2022
Page 13 of 24
Is the sharing of information outside the agency compatible with the original collection? If so,
is it covered by an appropriate routine use in a SORN? If not, please describe under what legal
mechanism the IT system is allowed to share the information in identifiable form or personally
identifiable information outside of VA.
NOTE: Question 3.10 on Privacy Threshold Analysis should be used to answer this question.
Identify and list the names of any Federal, State, or local government agency or private sector
organization with which information is shared.
For each interface with a system outside VA, state what specific data elements (PII/PHI) are shared
with each specific partner.
What legal mechanisms, authoritative agreements, documentation, or policies are in place detailing
the extent of the sharing and the duties of each party? For example, is the sharing of data compatible
with your SORN? Then list the SORN and the applicable routine use from the SORN. Is there a
Memorandum of Understanding (MOU), Computer Matching Agreement (CMA), or law that
mandates the sharing of this information?
Describe how the information is transmitted to entities external to VA and what security measures
have been taken to protect it during transmission.
This question is related to privacy control UL-2, Information Sharing with Third Parties
Data Shared with External Organizations
List External
Program Office
or IT System
information is
shared/received
with
List the
purpose of
information
being
shared /
received /
transmitted
with the
specified
program
office or IT
system
List the specific PII/PHI data
elements that are processed
(shared/received/transmitted)with
the Program or IT system
List the
legal
authority,
binding
agreement,
SORN
routine
use, etc.
that permit
external
sharing
(can be
more than
one)
List the
method of
transmission
and the
measures in
place to
secure data
N/A
N/A
N/A
N/A
N/A
5.2 PRIVACY IMPACT ASSESSMENT: External sharing and disclosure
Discuss the privacy risks associated with the sharing of information outside the Department and
what steps, if any, are currently being taken to mitigate those identified risks.
Discuss whether access controls have been implemented and whether audit logs are regularly
reviewed to ensure appropriate sharing outside of the Department. For example, is there a

Version Date: October 1, 2022
Page 14 of 24
Memorandum Of Understanding (MOU), contract, or agreement in place with outside agencies or
foreign governments.
Discuss how the sharing of information outside of the Department is compatible with the stated
purpose and use of the original collection.
This question is related to privacy control AR-2, Privacy Impact and Risk Assessment, AR-3, Privacy
Requirements for Contractors and Service Providers, and AR-4, Privacy Monitoring and Auditing
Follow the format below:
Privacy Risk: N/A
Mitigation: N/A
Section 6. Notice
The following questions are directed at providing notice to the individual of the scope of information
collected, the right to consent to uses of the information, and the right to decline to provide
information.
6.1 Was notice provided to the individual before collection of the information? If yes, please
provide a copy of the notice as an Appendix-A 6.1 on the last page of the document. Also
provide notice given to individuals by the source system (A notice may include a posted privacy
policy, a Privacy Act notice on forms, or a system of records notice published in the Federal
Register.) If notice was not provided, why not?
These questions are related to privacy control TR-1, Privacy Notice, and TR-2, System of Records
Notices and Privacy Act Statements, and TR-3, Dissemination of Privacy Program Information.
6.1a This question is directed at the notice provided before collection of the information. This refers
to whether the person is aware that his or her information is going to be collected. A notice may
include a posted privacy policy, a Privacy Act statement on forms, or a SORN published in the
Federal Register, Notice of Privacy Practice provided to individuals for VHA systems. If notice was
provided in the Federal Register, provide the citation.
No notice is provided to VA employees interacting with the VA Help Desk.
6.1b If notice was not provided, explain why. If it was provided, attach a copy of the current notice.
No notice is provided because all information is taken from VA employees who volunteer to provide
the information. Data collected is limited to name, work phone number, work email, personal phone
number and personal emails.
6.1c Describe how the notice provided for the collection of information is adequate to inform those
affected by the system that their information has been collected and is being used appropriately.
Provide information on any notice provided on forms or on Web sites associated with the collection.

Version Date: October 1, 2022
Page 15 of 24
N/A
6.2 Do individuals have the opportunity and right to decline to provide information? If so, is a
penalty or denial of service attached?
This question is directed at whether the person from or about whom information is collected can
decline to provide the information and if so, whether a penalty or denial of service is attached. This
question is related to privacy control IP-1, Consent, IP-2, Individual Access, and IP-3, Redress.
The information collected is voluntarily provided and is information the VA employee would have
provided to the VA prior to working there, to include name, personal phone number and personal
email. No penalty exists for not providing their information. However, if the VA employee does not
provide their contact information, the VA Help Desk will not be able to contact them regarding the
request made or issue or problem they are reporting to the VA Help Desk.
6.3 Do individuals have the right to consent to particular uses of the information? If so, how
does the individual exercise the right?
This question is directed at whether an individual may provide consent for specific uses or the
consent is given to cover all uses (current or potential) of his or her information. If specific consent
is required, how would the individual consent to each use? This question is related to privacy control
IP-1, Consent.
Yes, individuals have consented to the use of this information through being employed by the VA.
By voluntarily providing their contact information to the VA Help Desk while making a request or
reporting the issue or problem they are experiencing, the VA employee further consents to the use of
their contact information by the VA Help Desk.
6.4 PRIVACY IMPACT ASSESSMENT: Notice
Describe the potential risks associated with potentially insufficient notice and what steps, if any, are
currently being taken to mitigate those identified risks. (Work with your System ISSO to complete all
Privacy Risk questions inside the document this section).
Consider the following FIPPs below to assist in providing a response:
Principle of Transparency: Has sufficient notice been provided to the individual?
Principle of Use Limitation: Is the information used only for the purpose for which notice was
provided either directly to the individual or through a public notice? What procedures are in place to
ensure that information is used only for the purpose articulated in the notice?

Version Date: October 1, 2022
Page 16 of 24
This question is related to privacy control TR-1, Privacy Notice, AR-2, Privacy Impact and Risk
Assessment, and UL-1, Internal Use.
Follow the format below:
Privacy Risk: The risk involves VA employees who voluntarily provide their personal information
being unaware that the system retains their name, work phone number, work email address, personal
phone number and personal email address. Only VA employees who have voluntarily provided their
information are included in the VA Help Desk system, so they have received sufficient notice of the
use of their personal identification information.
Mitigation: This system utilizes a FIPS 140-2 connection through Salesforce Shield and also
minimizes the PII in the system by using VA contact information. The VA Help Desk information is
used exclusively for the VA Help Desk system to contact the VA Employees regarding their reported
issues or problems. Their information will not be accessed by or provided to any other VA systems.
Section 7. Access, Redress, and Correction
The following questions are directed at an individual’s ability to ensure the accuracy of the
information collected about him or her.
7.1 What are the procedures that allow individuals to gain access to their information?
These questions are related to privacy control IP-2, Individual Access, and AR-8, Accounting of
Disclosures.
7.1a Cite any procedures or regulations your program has in place that allow access to information.
These procedures, at a minimum, should include the agency’s FOIA/Privacy Act practices, but may
also include additional access provisions. For example, if your program has a customer
satisfaction unit, that information, along with phone and email contact information, should be
listed in this section in addition to the agency’s procedures. See 5 CFR 294 and the VA FOIA Web
page at http://www.foia.va.gov/ to obtain information about FOIA points of contact and
information about agency FOIA processes.
An individual would have to be a VA employee and gain approval to access the system from the
system administrator, to have access to this information.
7.1b If the system is exempt from the access provisions of the Privacy Act, please explain the basis
for the exemption or cite the source where this explanation may be found, for example, a Final Rule
published in the Code of Federal Regulations (CFR).
The system is not exempt.
7.1c If the system is not a Privacy Act system, please explain what procedures and regulations are in
place that covers an individual gaining access to his or her information.

Version Date: October 1, 2022
Page 17 of 24
Specifically, only VA employees working in the OIT office responsible for the VA Help Desk
program will have access the VA Help Desk system. Those VA employees who have provided their
information can contact the OIT DTC Help Desk at (202) 921-0911 at any time regarding the status,
accuracy, and removal of their personal data from the database.
7.2 What are the procedures for correcting inaccurate or erroneous information?
Describe the procedures and provide contact information for the appropriate person to whom such
issues should be addressed. If the correction procedures are the same as those given in question 7.1,
state as much. This question is related to privacy control IP-3, Redress, and IP-4, Complaint
Management.
Those VA employees who have provided their information can contact the DTC Help Desk at (202)
921-0911 in the OIT office at any time regarding the status, accuracy, and removal of their personal
data from the database.
7.3 How are individuals notified of the procedures for correcting their information?
How are individuals made aware of the procedures for correcting his or her information? This may
be through notice at collection or other similar means. This question is meant to address the risk that
even if procedures exist to correct information, if an individual is not made fully aware of the
existence of those procedures, then the benefits of the procedures are significantly weakened.
This question is related to privacy control IP-3, Redress, and IP-4, Complaint Management.
VA employees who provided their contact information to the VA Help Desk, when they call the VA
Help Desk to inquire about correcting or removing their information, they will be told to contact
DTC Help Desk at (202) 921-0911 at any time regarding the status, accuracy, and removal of their
personal data from the database.
7.4 If no formal redress is provided, what alternatives are available to the individual?
Redress is the process by which an individual gains access to his or her records and seeks
corrections or amendments to those records. Redress may be provided through the Privacy Act and
Freedom of Information Act (FOIA), and also by other processes specific to a program, system, or
group of systems. Example: Some projects allow users to directly access and correct/update their
information online. This helps ensures data accuracy.
This question is related to privacy control IP-3, Redress, and IP-4, Complaint Management.
Users can edit their information, by contacting DTC Help Desk at (202) 921-0911 in the OIT office
at any time regarding the status, accuracy, and removal of their personal data from the database.
7.5 PRIVACY IMPACT ASSESSMENT: Access, redress, and correction

Version Date: October 1, 2022
Page 18 of 24
Discuss what risks there currently are related to the Department’s access, redress, and correction
policies and procedures for this system and what, if any, steps have been taken to mitigate those
risks. For example, if a project does not allow individual access, the risk of inaccurate data needs
to be discussed in light of the purpose of the project. For example, providing access to ongoing law
enforcement activities could negatively impact the program’s effectiveness because the individuals
involved might change their behavior. (Work with your System ISSO to complete all Privacy Risk questions
inside the document this section).
Consider the following FIPPs below to assist in providing a response:
Principle of Individual Participation: Is the individual provided with the ability to find out whether a
project maintains a record relating to him?
Principle of Individual Participation: If access and/or correction is denied, then is the individual
provided notice as to why the denial was made and how to challenge such a denial?
Principle of Individual Participation: Is there a mechanism by which an individual is able to prevent
information about him obtained for one purpose from being used for other purposes without his
knowledge?
This question is related to privacy control IP-3, Redress.
Follow the format below:
Privacy Risk: VA employees who have reached out to the OIT VA Help Desk for assistance will
have their contact info listed in the system. Minimal risk exists because the system is accessed by a
small number of VA employees and can be readily updated at any time.
Mitigation: This information is protected with Salesforce Shield and any incorrect information can
be corrected by an individual notifying the OIT VA Help Desk. VA employees who have provided
their information to the VA Help Desk system can contact the OIT office at any time regarding the
status, accuracy, and removal of their personal data from the database.
Section 8. Technical Access and Security
The following questions are intended to describe technical safeguards and security measures.
8.1 What procedures are in place to determine which users may access the system, and are they
documented?
These questions are related to privacy control AR-7, Privacy-Enhanced System Design and
Development.
8.1a Describe the process by which an individual receives access to the system.
Role-based hierarchy is used for users to access the VA Help Desk application. VA employees can
access the tool only after the administrator grants access.
8.1b Identify users from other agencies who may have access to the system and under what roles
these individuals have access to the system. Who establishes the criteria for what PII can be shared?
Version Date: October 1, 2022
Page 19 of 24
No other agencies or users will have access to the system.
8.1c Describe the different roles in general terms that have been created to provide access to the
system. For example, certain users may have "read-only" access while others may be permitted to
make certain amendments or changes to the information.
The roles that have been created are a DTC Administrator role that works on the help desk tickets,
and a System Integrator/Citizen Developer role that uses the other object that tracks the development
activities in the DTC Application/enhancement functions.
8.2 Will VA contractors have access to the system and the PII? If yes, what involvement will
contractors have with the design and maintenance of the system? Has a contractor
confidentiality agreement, Business Associate Agreement (BAA), or a Non-Disclosure
Agreement (NDA) been developed for contractors who work on the system?
If so, how frequently are contracts reviewed and by whom? Describe the necessity of the access
provided to contractors to the system and whether clearance is required. If Privacy Roles and
Responsibilities have been established to restrict certain users to different access levels, please
describe the roles and associated access levels. Explain the need for VA contractors to have access
to the PII. This question is related to privacy control AR-3, Privacy Requirements for Contractors
and Service Providers.
VA contract employee access is verified through VA personnel before access is granted to any
contractor. Contracts and contractor access are reviewed annually at a minimum. The contractors
Version Date: October 1, 2022 Page 19 of 24 who provide support to the system are required to
complete annual VA Privacy and Information Security and Rules of behavior training via TMS. All
contractors are cleared using the VA background investigation process and must obtain the
appropriate background investigation for their role. Contractors with systems administrative access
are required to complete additional role-based training prior to gaining system administrator
access.
8.3 Describe what privacy training is provided to users either generally or specifically relevant
to the program or system?
VA offers privacy and security training. Each program or system may offer training specific to the
program or system that touches on information handling procedures and sensitivity of information.
Please describe how individuals who have access to PII are trained to handle it appropriately.
This question is related to privacy control AR-5, Privacy Awareness and Training.
All users of this system have undergone the general VA Privacy Training.
Version Date: October 1, 2022
Page 20 of 24
8.4 Has Authorization and Accreditation (A&A) been completed for the system?
8.4a If Yes, provide:
1. The Security Plan Status: Please provide response here
2. The System Security Plan Status Date: Please provide response here
3. The Authorization Status: Please provide response here
4. The Authorization Date: Please provide response here
5. The Authorization Termination Date: Please provide response here
6. The Risk Review Completion Date: Please provide response here
7. The FIPS 199 classification of the system (LOW/MODERATE/HIGH): Please provide response
here
Please note that all systems containing SPI are categorized at a minimum level of “moderate” under
Federal Information Processing Standards Publication 199.
8.4b If No or In Process, provide your Initial Operating Capability (IOC) date.
1. The Security Plan Status: Approved 2. The Security Plan Status Date: 02/24/2021 3. The
Authorization Status: ATO 4. The Authorization Date: 08/07/2020 5. The Authorization Termination
Date: 12/17/2023 6. The Risk Review Completion Date: 03/12/2021 7. The FIPS 199 classification
of the system – Pending 8. Initial Operating Capability (IOC): 06/20/2017 (legacy System)
Section 9 – Technology Usage
The following questions are used to identify the technologies being used by the IT system or project.
9.1 Does the system use cloud technology? If so, what cloud model is being utilized?
If so, Does the system have a FedRAMP provisional or agency authorization? If the system does
use cloud technology, but does not have FedRAMP authorization, explain how the Cloud Service
Provider (CSP) solution was assessed and what FedRAMP documents and processes were used
for the assessment in order to comply with VA Handbook 6517. Types of cloud models include:
Software as a Service (SaaS), Infrastructure as a Service (IaaS), Platform as a Service (PaaS),
Commercial off the Shelf (COTS), Desktop as a Service (DaaS), Mobile Backend as a Service
(MBaaS), Information Technology Management as a Service (ITMaaS). This question is related
to privacy control UL-1, Information Sharing with Third Parties.
Note: For systems utilizing the VA Enterprise Cloud (VAEC), no further responses are
required after 9.1. (Refer to question 3.3.1 of the PTA)
This system is a minor application under Salesforce Government Cloud ATO authorized
8/7/2020.
9.2 Does the contract with the Cloud Service Provider, Contractors and VA customers
establish who has ownership rights over data including PII? (Provide contract number
and supporting information about PII/PHI from the contract). (Refer to question 3.3.2 of
Version Date: October 1, 2022
Page 21 of 24
the PTA) This question is related to privacy control AR-3, Privacy Requirements for
Contractors and Service Providers.
Yes, the Cloud Service Provider agreement states that the VA owns the system and Salesforce
controls and operates the system. It is under the following agreement: Salesforce Subscription
Licenses, Maintenance and Support”, Contract Number: NNG15SD27B, Order Number:
36C10B9F0460.
9.3 Will the CSP collect any ancillary data and if so, who has ownership over the ancillary
data?
Per NIST 800-144, cloud providers hold significant details about the accounts of cloud
consumers that could be compromised and used in subsequent attacks. Ancillary data also
involves information the cloud provider collects or produces about customer-related activity in
the cloud. It includes data collected to meter and charge for consumption of resources, logs and
audit trails, and other such metadata that is generated and accumulated within the cloud
environment.
This question is related to privacy control DI-1, Data Quality.
No ancillary data is collected.
9.4 NIST 800-144 states, “Organizations are ultimately accountable for the security and
privacy of data held by a cloud provider on their behalf.” Is this principle described in
contracts with customers? Why or why not?
What are the roles and responsibilities involved between the organization and cloud provider,
particularly with respect to managing risks and ensuring organizational requirements are met?
This question is related to privacy control AR-3, Privacy Requirements for Contractors and
Service Providers.
Yes, the Cloud Service Provider agreement clearly states that this is a VA-owned, Salesforce-
controlled system.
9.5 If the system is utilizing Robotics Process Automation (RPA), please describe the role of the
bots.
Robotic Process Automation is the use of software scripts to perform tasks as an automated
process that executes in parallel with or in place of human input. For example, will the
automation move or touch PII/PHI information. RPA may also be referred to as “Bots” or
Artificial Intelligence (AI).
No RPA is utilized in the system.

Version Date: October 1, 2022
Page 22 of 24
Section 10. References
Summary of Privacy Controls by Family
Summary of Privacy Controls by Family
ID
Privacy Controls
AP
Authority and Purpose
AP-1
Authority to Collect
AP-2
Purpose Specification
AR
Accountability, Audit, and Risk Management
AR-1
Governance and Privacy Program
AR-2
Privacy Impact and Risk Assessment
AR-3
Privacy Requirements for Contractors and Service Providers
AR-4
Privacy Monitoring and Auditing
AR-5
Privacy Awareness and Training
AR-7
Privacy-Enhanced System Design and Development
AR-8
Accounting of Disclosures
DI
Data Quality and Integrity
DI-1
Data Quality
DI-2
Data Integrity and Data Integrity Board
DM
Data Minimization and Retention
DM-1
Minimization of Personally Identifiable Information
DM-2
Data Retention and Disposal
DM-3
Minimization of PII Used in Testing, Training, and Research
IP
Individual Participation and Redress
IP-1
Consent
IP-2
Individual Access
IP-3
Redress
IP-4
Complaint Management
SE
Security
SE-1
Inventory of Personally Identifiable Information
SE-2
Privacy Incident Response
TR
Transparency
TR-1
Privacy Notice
TR-2
System of Records Notices and Privacy Act Statements
TR-3
Dissemination of Privacy Program Information
UL
Use Limitation
UL-1
Internal Use
UL-2
Information Sharing with Third Parties

Signature of Responsible Officials
The individuals below attest that the information provided in this Privacy
Impact Assessment is true and accurate.
Version Date: October 1, 2022
Page 23 of 24
Privacy Officer, Gina Siefert
Information System Security Officer, James Boring
Information System Owner, Michael Domanski
Reviewed for accuracy by PIA Support Analyst
Gina A Siefert 273290
Digitally signed by Gina A Siefert
273290
Date: 2023.02.10 12:48:37 -06'00'
JAMES BORING
Digitally signed by JAMES BORING
Date: 2023.02.13 15:12:44 -05'00'
Michael S. Domanski
326889
Digitally signed by Michael S.
Domanski 326889
Date: 2023.02.13 14:24:52 -05'00'
JOHN WORSHAM
(Affiliate)
Digitally signed by JOHN WORSHAM
(Affiliate)
Date: 2023.02.13 15:26:12 -06'00'

Version Date: October 1, 2022
Page 24 of 24
APPENDIX A-6.1
Please provide a link to the notice or verbiage referred to in Section 6 (a notice may include a
posted privacy policy, a Privacy Act notice on forms).
HELPFUL LINKS:
Record Control Schedules:
https://www.va.gov/vhapublications/rcs10/rcs10-1.pdf
General Records Schedule 1.1: Financial Management and Reporting Records (FSC):
https://www.archives.gov/files/records-mgmt/grs/grs01-1.pdf
National Archives (Federal Records Management):
https://www.archives.gov/records-mgmt/grs
VHA Publications:
https://www.va.gov/vhapublications/publications.cfm?Pub=2
VA Privacy Service Privacy Hub:
https://dvagov.sharepoint.com/sites/OITPrivacyHub
Notice of Privacy Practice (NOPP):
VHA Notice of Privacy Practices
VHA Handbook 1605.04: Notice of Privacy Practices
